Leadership and Software Engineering Report - Coursework Analysis
VerifiedAdded on 2019/09/30
|15
|3923
|122
Report
AI Summary
This report comprises two coursework assignments focusing on leadership in the digital age and software engineering principles. The first part requires a self-analysis of leadership strengths and weaknesses, utilizing various models and frameworks, and evaluating the impact of digital technical leadership on business performance. It includes an assessment of leadership capabilities for managing geographically dispersed teams, an evaluation of how digital technical leadership enhances business transformation, and a personal development plan with objectives, learning activities, and success criteria. The second part involves designing and developing a program prototype solution using Java based on a case study of a banking software, and a critical discussion of software engineering issues. The assignment necessitates the creation of use case and class diagrams, considering design patterns, and addressing ethical and social considerations.

COURSEWORK ASSESSMENT SPECIFICATION
Module Title: Leadership for a Digital Age
Module Number:
Module Tutor
Name(s):
Academic Year: 2018-19
% Weighting (to
overall module):
100%
Coursework Title: Report
Average Study
Time Required by
Student:
Approximately 50-55 study hours
Dates and Mechanisms for Assessment Submission and Feedback
Mechanism for Submission of Work by Student:
The report must be submitted Turnitin on Module Blackboard site.
Date by which Work, Feedback and Marks will be returned to Students:
Within twenty working days after the submission date.
Mechanism for return of assignment work, feedback and marks to students:
Formal feedback will be made available via Blackboard following completion of all reviews
and internal moderation of results.
Learning Outcomes tested in this assessment
This assignment will assess the following learning outcomes:
1. Demonstrate comprehensive understanding of key concepts, models and theories
relating to leadership and practice and critical appreciation of the uncertainty and
limits of this knowledge
2. Critically analyse the relationship between technical leadership and business
performance.
3. Demonstrate the ability to convey and translate technological concepts and data into
formats and business cases that are of value to strategic decision-makers
Module Title: Leadership for a Digital Age
Module Number:
Module Tutor
Name(s):
Academic Year: 2018-19
% Weighting (to
overall module):
100%
Coursework Title: Report
Average Study
Time Required by
Student:
Approximately 50-55 study hours
Dates and Mechanisms for Assessment Submission and Feedback
Mechanism for Submission of Work by Student:
The report must be submitted Turnitin on Module Blackboard site.
Date by which Work, Feedback and Marks will be returned to Students:
Within twenty working days after the submission date.
Mechanism for return of assignment work, feedback and marks to students:
Formal feedback will be made available via Blackboard following completion of all reviews
and internal moderation of results.
Learning Outcomes tested in this assessment
This assignment will assess the following learning outcomes:
1. Demonstrate comprehensive understanding of key concepts, models and theories
relating to leadership and practice and critical appreciation of the uncertainty and
limits of this knowledge
2. Critically analyse the relationship between technical leadership and business
performance.
3. Demonstrate the ability to convey and translate technological concepts and data into
formats and business cases that are of value to strategic decision-makers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4. Critically appraise the ethical, social and legal concerns and incorporate good
practice into technical leadership practice in diverse environments and/or teams.
General Information
This assignment constitutes 100% towards the final mark for this module. Any queries
relating to this assignment should be directed to Module tutor.
Type of the submission required
This is an INDIVIDUAL piece of work contributing towards the module assessment.
Deliverables should be assembled into a single report document, which includes (critical
appraisal, research, and snapshot evidences of tasks carried out and justification of
technologies used). Submission will be in the form of a MS word report (4000 words).
Formative Feedback
There will be an opportunity for formative feedback during the semester. You are advised to
start working on this assignment as early as possible so that you can seek clarification from
the module tutor regarding any questions you might have during the semester. Note that
tutors will not predict your grade, and you should not take the lack of comment on any
aspect of your work as indicating that it is correct. You should make every effort to take
advantage of formative feedback as tutors will not comment on draft work at other times.
Remember that you will get more useful feedback from us by asking specific questions than
just presenting us with your documentation and asking, ‘Is this right?’
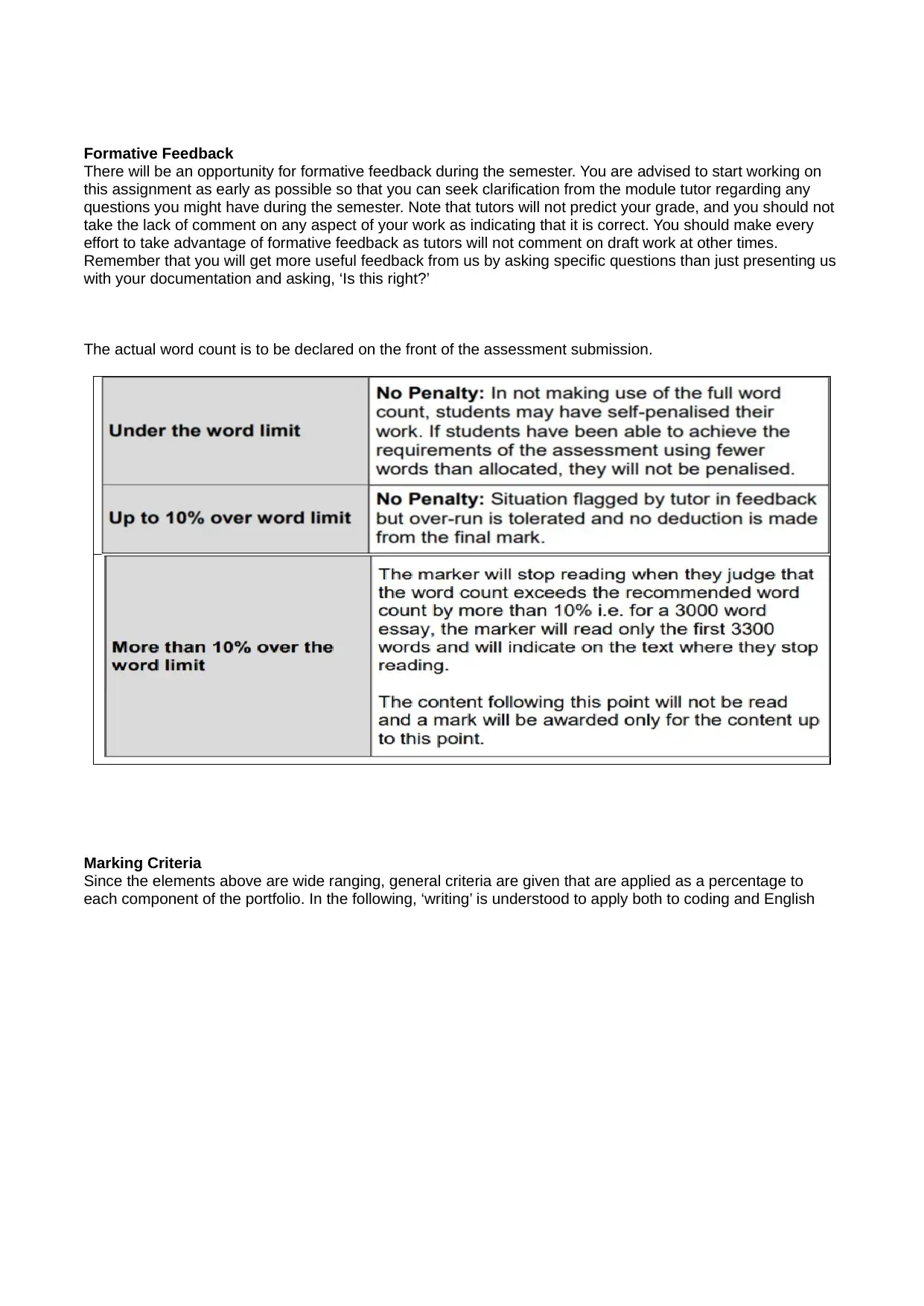
The actual word count is to be declared on the front of the assessment submission.
Under the word limit
No Penalty: In not making use of the full word count,
students may have self-penalised their work. If students
have been able to achieve the requirements of the
assessment using fewer words than allocated, they will not
be penalised.
Up to 10% over word limit
No Penalty: Situation flagged by tutor in feedback but over-
run is tolerated and no deduction is made from the final
mark.
More than 10% over the
word limit
The marker will stop reading when they judge that the
word count exceeds the recommended word count by
more than 10% i.e. for a 3000 word essay, the marker will
read only the first 3300 words and will indicate on the text
where they stop reading.
The content following this point will not be read and a mark
practice into technical leadership practice in diverse environments and/or teams.
General Information
This assignment constitutes 100% towards the final mark for this module. Any queries
relating to this assignment should be directed to Module tutor.
Type of the submission required
This is an INDIVIDUAL piece of work contributing towards the module assessment.
Deliverables should be assembled into a single report document, which includes (critical
appraisal, research, and snapshot evidences of tasks carried out and justification of
technologies used). Submission will be in the form of a MS word report (4000 words).
Formative Feedback
There will be an opportunity for formative feedback during the semester. You are advised to
start working on this assignment as early as possible so that you can seek clarification from
the module tutor regarding any questions you might have during the semester. Note that
tutors will not predict your grade, and you should not take the lack of comment on any
aspect of your work as indicating that it is correct. You should make every effort to take
advantage of formative feedback as tutors will not comment on draft work at other times.
Remember that you will get more useful feedback from us by asking specific questions than
just presenting us with your documentation and asking, ‘Is this right?’
The actual word count is to be declared on the front of the assessment submission.
Under the word limit
No Penalty: In not making use of the full word count,
students may have self-penalised their work. If students
have been able to achieve the requirements of the
assessment using fewer words than allocated, they will not
be penalised.
Up to 10% over word limit
No Penalty: Situation flagged by tutor in feedback but over-
run is tolerated and no deduction is made from the final
mark.
More than 10% over the
word limit
The marker will stop reading when they judge that the
word count exceeds the recommended word count by
more than 10% i.e. for a 3000 word essay, the marker will
read only the first 3300 words and will indicate on the text
where they stop reading.
The content following this point will not be read and a mark
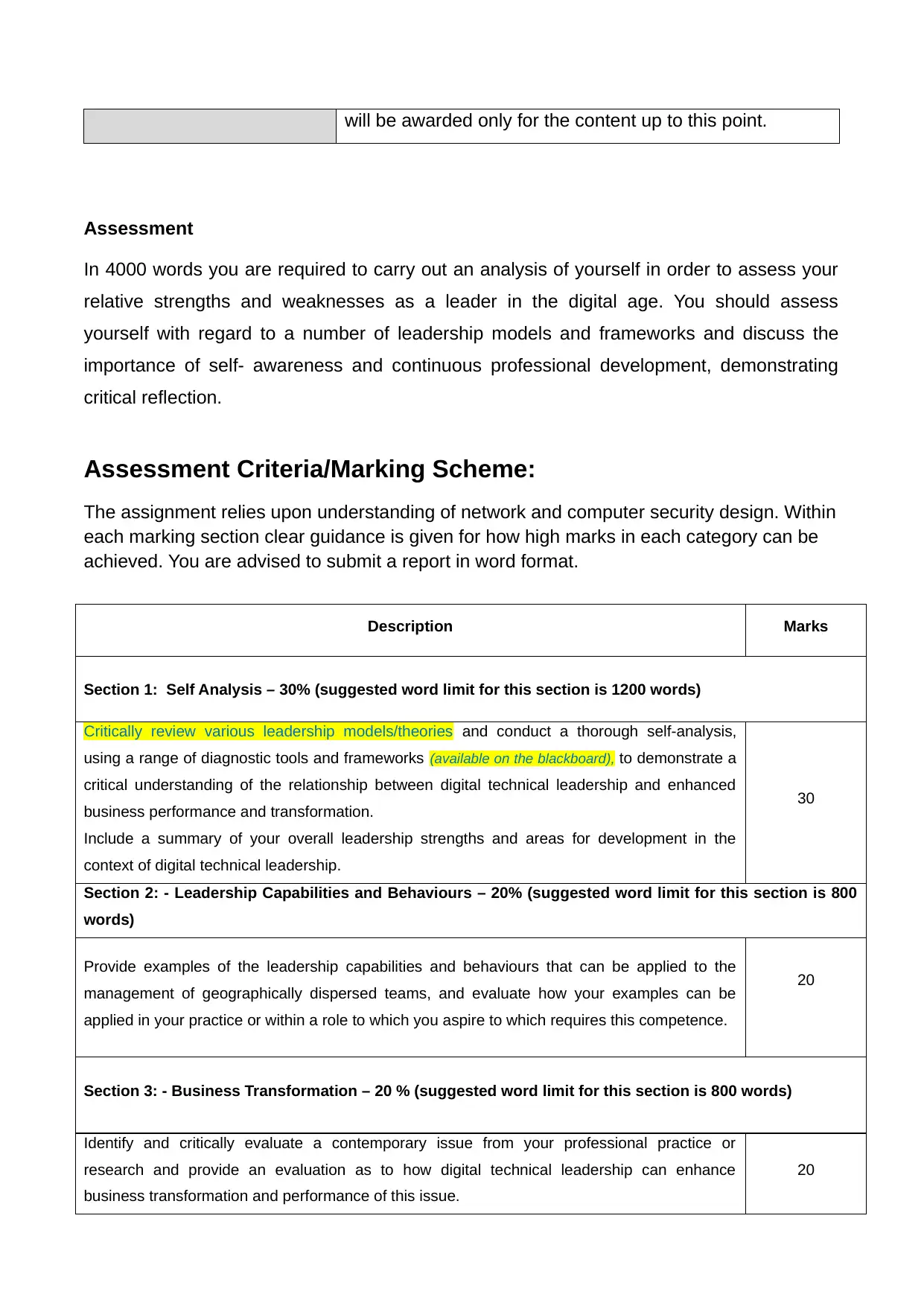
will be awarded only for the content up to this point.
Assessment
In 4000 words you are required to carry out an analysis of yourself in order to assess your
relative strengths and weaknesses as a leader in the digital age. You should assess
yourself with regard to a number of leadership models and frameworks and discuss the
importance of self- awareness and continuous professional development, demonstrating
critical reflection.
Assessment Criteria/Marking Scheme:
The assignment relies upon understanding of network and computer security design. Within
each marking section clear guidance is given for how high marks in each category can be
achieved. You are advised to submit a report in word format.
Description Marks
Section 1: Self Analysis – 30% (suggested word limit for this section is 1200 words)
Critically review various leadership models/theories and conduct a thorough self-analysis,
using a range of diagnostic tools and frameworks (available on the blackboard), to demonstrate a
critical understanding of the relationship between digital technical leadership and enhanced
business performance and transformation.
Include a summary of your overall leadership strengths and areas for development in the
context of digital technical leadership.
30
Section 2: - Leadership Capabilities and Behaviours – 20% (suggested word limit for this section is 800
words)
Provide examples of the leadership capabilities and behaviours that can be applied to the
management of geographically dispersed teams, and evaluate how your examples can be
applied in your practice or within a role to which you aspire to which requires this competence.
20
Section 3: - Business Transformation – 20 % (suggested word limit for this section is 800 words)
Identify and critically evaluate a contemporary issue from your professional practice or
research and provide an evaluation as to how digital technical leadership can enhance
business transformation and performance of this issue.
20
Assessment
In 4000 words you are required to carry out an analysis of yourself in order to assess your
relative strengths and weaknesses as a leader in the digital age. You should assess
yourself with regard to a number of leadership models and frameworks and discuss the
importance of self- awareness and continuous professional development, demonstrating
critical reflection.
Assessment Criteria/Marking Scheme:
The assignment relies upon understanding of network and computer security design. Within
each marking section clear guidance is given for how high marks in each category can be
achieved. You are advised to submit a report in word format.
Description Marks
Section 1: Self Analysis – 30% (suggested word limit for this section is 1200 words)
Critically review various leadership models/theories and conduct a thorough self-analysis,
using a range of diagnostic tools and frameworks (available on the blackboard), to demonstrate a
critical understanding of the relationship between digital technical leadership and enhanced
business performance and transformation.
Include a summary of your overall leadership strengths and areas for development in the
context of digital technical leadership.
30
Section 2: - Leadership Capabilities and Behaviours – 20% (suggested word limit for this section is 800
words)
Provide examples of the leadership capabilities and behaviours that can be applied to the
management of geographically dispersed teams, and evaluate how your examples can be
applied in your practice or within a role to which you aspire to which requires this competence.
20
Section 3: - Business Transformation – 20 % (suggested word limit for this section is 800 words)
Identify and critically evaluate a contemporary issue from your professional practice or
research and provide an evaluation as to how digital technical leadership can enhance
business transformation and performance of this issue.
20
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Section 4 – Personal Development Plan – 30% (1200 words)
Complete a personal development plan identifying a range of personal development objectives
that would evidence your ability to demonstrate the competences to be an effective leader in
the digital age. You should draw on your findings in the earlier sections to contextualise and
justify how these objectives will enable you to be an effective Leader in Digital Age to your
current role or role to which you aspire to.
This plan should set out objectives for your future approach to leadership with a range of
learning activities, success criteria and timescales.
30
Total 100
Grading Guidance
Fail: A fail submission will show lack of understanding of deliverable. There will be clear
gaps in the response across the listed tasks, some of the areas are not covered or covered
in limited detail at the descriptive level. There will be inadequate evidences of design, and
testing of a network and computer security. Design will be either incomplete or below the
expected standards, there will be no enough evidence to show steps taken for design and
work lacks critical evaluation of the design principles and ethical considerations. Incomplete
submission.
Pass: A Pass submission would show effective use of appropriate research of design
principles, technologies and a working design should include effective use of hardware
devices, configuration evidences and problem solving. The assignment should also include
evidence of research and understanding of network design principles, security
implementation and critical thinking.
Commendation: A commendation submission would show significant evidence of
research, critical thinking and understanding of design and security. This includes
demonstrating in-depth design and configuration understanding, decision making, creative,
critical thinking, problem solving and methodology. Report should also include critical
appraisal of the research and social, ethical considerations and must include evidence of
referencing and appendix.
Distinction: A distinction submission would show an optimised design addressing security
challenges, critically evaluation of the technologies, security controls and social ethical
Complete a personal development plan identifying a range of personal development objectives
that would evidence your ability to demonstrate the competences to be an effective leader in
the digital age. You should draw on your findings in the earlier sections to contextualise and
justify how these objectives will enable you to be an effective Leader in Digital Age to your
current role or role to which you aspire to.
This plan should set out objectives for your future approach to leadership with a range of
learning activities, success criteria and timescales.
30
Total 100
Grading Guidance
Fail: A fail submission will show lack of understanding of deliverable. There will be clear
gaps in the response across the listed tasks, some of the areas are not covered or covered
in limited detail at the descriptive level. There will be inadequate evidences of design, and
testing of a network and computer security. Design will be either incomplete or below the
expected standards, there will be no enough evidence to show steps taken for design and
work lacks critical evaluation of the design principles and ethical considerations. Incomplete
submission.
Pass: A Pass submission would show effective use of appropriate research of design
principles, technologies and a working design should include effective use of hardware
devices, configuration evidences and problem solving. The assignment should also include
evidence of research and understanding of network design principles, security
implementation and critical thinking.
Commendation: A commendation submission would show significant evidence of
research, critical thinking and understanding of design and security. This includes
demonstrating in-depth design and configuration understanding, decision making, creative,
critical thinking, problem solving and methodology. Report should also include critical
appraisal of the research and social, ethical considerations and must include evidence of
referencing and appendix.
Distinction: A distinction submission would show an optimised design addressing security
challenges, critically evaluation of the technologies, security controls and social ethical
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
considerations related to compliance. The report includes evidence off design
implementation and testing, walk through screen shots to provide rigorous understanding of
the steps taken and validation results. A demonstration of excellence in research, design,
testing and compliance. Work should include evidence of rigorous research conducted for
each deliverable, particularly reference to latest journals on computer and network security.
implementation and testing, walk through screen shots to provide rigorous understanding of
the steps taken and validation results. A demonstration of excellence in research, design,
testing and compliance. Work should include evidence of rigorous research conducted for
each deliverable, particularly reference to latest journals on computer and network security.

COURSEWORK ASSESSMENT SPECIFICATION
Module Title: Principles of Software Engineering
% Weighting (to
overall module):
100%
Coursework Title: Assignment
Dates and Mechanisms for Assessment Submission and Feedback
Mechanism for Handout to Students:
Blackboard
Date and Time of Submission by Student:
Date 05/09/2019 (14:00 hours)
Part A: Component 1: Software design and project prototype
Part B: Component 2: Critical-Evaluation
Mechanism for Submission of Work by Student:
The reports must be submitted via Turnitin. The source code MUST be uploaded to Blackboard
Date by which Work, Feedback and Marks will be returned to Students:
Within 20 working days after submission of this assignment
Mechanism for return of assignment work, feedback and marks to students:
Formal feedback will take place following completion of all reviews and internal moderation of results.
Module Title: Principles of Software Engineering
% Weighting (to
overall module):
100%
Coursework Title: Assignment
Dates and Mechanisms for Assessment Submission and Feedback
Mechanism for Handout to Students:
Blackboard
Date and Time of Submission by Student:
Date 05/09/2019 (14:00 hours)
Part A: Component 1: Software design and project prototype
Part B: Component 2: Critical-Evaluation
Mechanism for Submission of Work by Student:
The reports must be submitted via Turnitin. The source code MUST be uploaded to Blackboard
Date by which Work, Feedback and Marks will be returned to Students:
Within 20 working days after submission of this assignment
Mechanism for return of assignment work, feedback and marks to students:
Formal feedback will take place following completion of all reviews and internal moderation of results.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Learning Outcomes tested in this assessment:
The following learning outcomes will be assessed by this assignment:
1. Demonstrate critical knowledge and understanding of appropriate software engineering theories,
technologies and methodologies
2. Ability to apply software engineering knowledge to a complex business challenge or project
3. Critically reflect on professional, legal, social, security and ethical issues related to the design,
development and use of software in an organisational context.
4. Ability to critically evaluate your Software Engineering skills
5. Demonstrate problem solving skills in complex situations in the context of the design, development
and use of software solution.
Assignment Overview:
The assignment is divided into two components as follows:
Practical Solution
Prototype
(50%)
Individual Work– design and development of a program prototype solution
using Java based on the case study given below. This activity assesses
module learning outcomes 1, 2 & 5. (2000 words)
Critical Discussion
(50%)
Individual work - critical discussion of some issues relating to Software
engineering. This activity assesses module learning outcome
3 & 4. (2000 words)
General description
Case Study Scenario:
Mechachrome software development ltd has been commissioned to develop the banking software for
NatioNarrow building society, a rapidly growing building society. You have been recruited as software architect
into a team of junior interface designers (Human computer interaction), business analysts, database
developers and System analysis designers who will be relying on your experience. You are expected to pro-
actively oversee and contribute across the team.
The program’s primary user will be the bank tellers whom must be logged in using valid credentials and then
on behalf customers, will perform functions such as making deposits, withdrawals and transfer. Customers
can come into the branch and request a bank statements based between two dates, showing all transactions
done on their accounts (deposits, withdrawals and transfers). Customers can also simply request a balance
update but must provide an answer to their secret question. Tellers should have the functionality to reverse
transactions but only immediately after they have happened (consider using design pattern) for this.
The bank manager while able to perform the same functions as the tellers should additionally able to, create
new user credentials (user logins and passwords) for access to the program in the event they have hired new
staff.
The manager can also approve and grant loans, open new bank accounts of which there are several types:
Current (0.98% interest)
Savings (2.98% interest)
ISA (5.2% interest)
Business (2.0% interest)
Student (0.5 % interest)
Child (Children under 18 years of age) (0.5% interest)
Every month, interest is paid on each of the accounts and penalties of £20 on accounts that are overdrawn.
This functionality should be automated and not done manually by any employee. (Consider a design pattern to
re-use existing methods). ISA accounts, when withdrawals >= £1000 are made, a penalty charge of 10% of
the withdrawal amount should be applied.
Tasks
Using the provided NatioNarrow Bank case study, develop a solution from a software architect’s perspective
that includes the following:
The following learning outcomes will be assessed by this assignment:
1. Demonstrate critical knowledge and understanding of appropriate software engineering theories,
technologies and methodologies
2. Ability to apply software engineering knowledge to a complex business challenge or project
3. Critically reflect on professional, legal, social, security and ethical issues related to the design,
development and use of software in an organisational context.
4. Ability to critically evaluate your Software Engineering skills
5. Demonstrate problem solving skills in complex situations in the context of the design, development
and use of software solution.
Assignment Overview:
The assignment is divided into two components as follows:
Practical Solution
Prototype
(50%)
Individual Work– design and development of a program prototype solution
using Java based on the case study given below. This activity assesses
module learning outcomes 1, 2 & 5. (2000 words)
Critical Discussion
(50%)
Individual work - critical discussion of some issues relating to Software
engineering. This activity assesses module learning outcome
3 & 4. (2000 words)
General description
Case Study Scenario:
Mechachrome software development ltd has been commissioned to develop the banking software for
NatioNarrow building society, a rapidly growing building society. You have been recruited as software architect
into a team of junior interface designers (Human computer interaction), business analysts, database
developers and System analysis designers who will be relying on your experience. You are expected to pro-
actively oversee and contribute across the team.
The program’s primary user will be the bank tellers whom must be logged in using valid credentials and then
on behalf customers, will perform functions such as making deposits, withdrawals and transfer. Customers
can come into the branch and request a bank statements based between two dates, showing all transactions
done on their accounts (deposits, withdrawals and transfers). Customers can also simply request a balance
update but must provide an answer to their secret question. Tellers should have the functionality to reverse
transactions but only immediately after they have happened (consider using design pattern) for this.
The bank manager while able to perform the same functions as the tellers should additionally able to, create
new user credentials (user logins and passwords) for access to the program in the event they have hired new
staff.
The manager can also approve and grant loans, open new bank accounts of which there are several types:
Current (0.98% interest)
Savings (2.98% interest)
ISA (5.2% interest)
Business (2.0% interest)
Student (0.5 % interest)
Child (Children under 18 years of age) (0.5% interest)
Every month, interest is paid on each of the accounts and penalties of £20 on accounts that are overdrawn.
This functionality should be automated and not done manually by any employee. (Consider a design pattern to
re-use existing methods). ISA accounts, when withdrawals >= £1000 are made, a penalty charge of 10% of
the withdrawal amount should be applied.
Tasks
Using the provided NatioNarrow Bank case study, develop a solution from a software architect’s perspective
that includes the following:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Practical Solution (prototype) and commentary
Produce a use case model to model the functional requirements from the scenario narrative.
o Showing actors and the use cases they perform.
o Use inheritance where necessary of both use cases and actors.
o Use of <<includes>> and <<extends>> where necessary.
Produce a class diagram to model the system structure you propose for your potential solution.
Decouple as much as possible with Boundary, Control and Entity classes. Only one instance of the
control classes should be allowed to be created. Consider a design pattern for this (In your
commentary, justify the use the chosen design pattern, on the other hand, if you do not use it, justify
why).
o Detailed classes with all global variables and datatypes with access modifiers (private, public
or protected) clearly shown in adherence to encapsulation principal of OOP and multiplicities
of the relationships.
o Procedures or functions with (parameters and their datatypes shown) as well as return type
for the class functions. (see diagram below)
o Use of class relationships (dependency, aggregation, composition, inheritance and
realisation).
o Show inheritance where applicable.
o Consider the use of design patterns in your proposed solution.
Produce a use case model to model the functional requirements from the scenario narrative.
o Showing actors and the use cases they perform.
o Use inheritance where necessary of both use cases and actors.
o Use of <<includes>> and <<extends>> where necessary.
Produce a class diagram to model the system structure you propose for your potential solution.
Decouple as much as possible with Boundary, Control and Entity classes. Only one instance of the
control classes should be allowed to be created. Consider a design pattern for this (In your
commentary, justify the use the chosen design pattern, on the other hand, if you do not use it, justify
why).
o Detailed classes with all global variables and datatypes with access modifiers (private, public
or protected) clearly shown in adherence to encapsulation principal of OOP and multiplicities
of the relationships.
o Procedures or functions with (parameters and their datatypes shown) as well as return type
for the class functions. (see diagram below)
o Use of class relationships (dependency, aggregation, composition, inheritance and
realisation).
o Show inheritance where applicable.
o Consider the use of design patterns in your proposed solution.
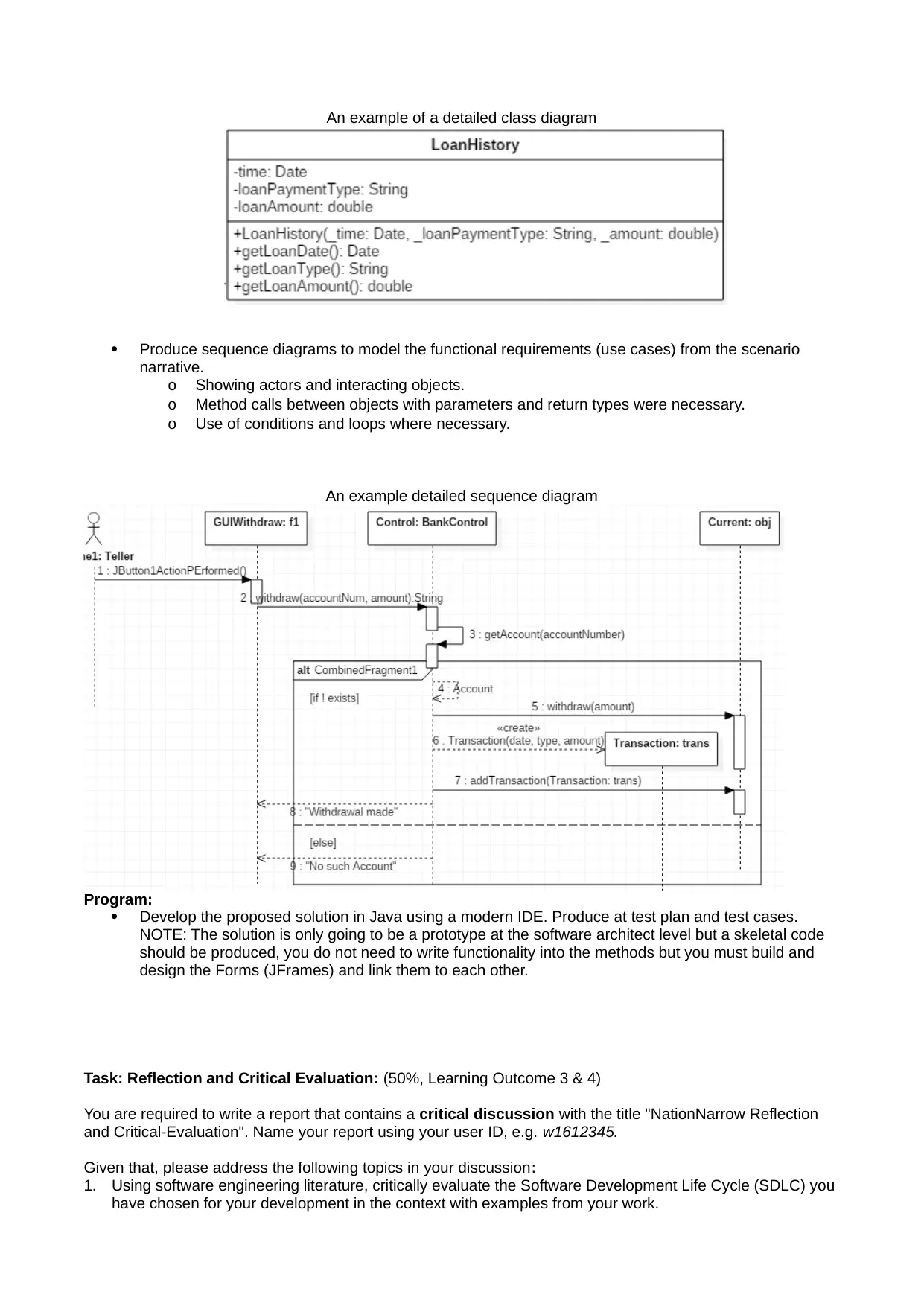
An example of a detailed class diagram
Produce sequence diagrams to model the functional requirements (use cases) from the scenario
narrative.
o Showing actors and interacting objects.
o Method calls between objects with parameters and return types were necessary.
o Use of conditions and loops where necessary.
An example detailed sequence diagram
Program:
Develop the proposed solution in Java using a modern IDE. Produce at test plan and test cases.
NOTE: The solution is only going to be a prototype at the software architect level but a skeletal code
should be produced, you do not need to write functionality into the methods but you must build and
design the Forms (JFrames) and link them to each other.
Task: Reflection and Critical Evaluation: (50%, Learning Outcome 3 & 4)
You are required to write a report that contains a critical discussion with the title "NationNarrow Reflection
and Critical-Evaluation". Name your report using your user ID, e.g. w1612345.
Given that, please address the following topics in your discussion:
1. Using software engineering literature, critically evaluate the Software Development Life Cycle (SDLC) you
have chosen for your development in the context with examples from your work.
Produce sequence diagrams to model the functional requirements (use cases) from the scenario
narrative.
o Showing actors and interacting objects.
o Method calls between objects with parameters and return types were necessary.
o Use of conditions and loops where necessary.
An example detailed sequence diagram
Program:
Develop the proposed solution in Java using a modern IDE. Produce at test plan and test cases.
NOTE: The solution is only going to be a prototype at the software architect level but a skeletal code
should be produced, you do not need to write functionality into the methods but you must build and
design the Forms (JFrames) and link them to each other.
Task: Reflection and Critical Evaluation: (50%, Learning Outcome 3 & 4)
You are required to write a report that contains a critical discussion with the title "NationNarrow Reflection
and Critical-Evaluation". Name your report using your user ID, e.g. w1612345.
Given that, please address the following topics in your discussion:
1. Using software engineering literature, critically evaluate the Software Development Life Cycle (SDLC) you
have chosen for your development in the context with examples from your work.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2. Critically reflect on professional, legal, social, security and ethical issues related to the design,
development and use of software in an organisational context.
References
leading information sources in Computing. Since Computer Science is highly dynamic, recent references to
conference and journal papers from the last five years are preferred.
This is meant to be a critical discussion and not just a description of things such as Java. Your discussion
should not be limited to your practical system, but a discussion of the broader issues involved.
Your discussion for the practical solution commentary should contain 2000 words and for the critical
evaluation 2000 words and should be presented in the form of a word document and submitted to
Blackboard.
References must be used in order to strengthen any points that you raise in your discussion.
Your discussion must be your own words and, where you have used someone else’s words (quotations), they
should be correctly quoted and referenced in accordance to the Harvard or APA System. If you require
guidance on citation, please use the booklet ‘Cite Them Right’ available from the City Campus library.
Your Reference list is not included in the word count.
Additional Programming Requirements:
Your code must comply with the following requirements:
1. The Java standard should be used as the programming language.
2. Use an industrial strength IDE
3. The program should be executable (i.e. no compile time errors that prevent it from being executed).
4. Project directory should be attached to your word document with the commentary in a zip file. Simply
submitting individual .java files will receive a mark of Zero for the program section.
5. Use meaningful naming conventions for variables, methods and classes.
development and use of software in an organisational context.
References
leading information sources in Computing. Since Computer Science is highly dynamic, recent references to
conference and journal papers from the last five years are preferred.
This is meant to be a critical discussion and not just a description of things such as Java. Your discussion
should not be limited to your practical system, but a discussion of the broader issues involved.
Your discussion for the practical solution commentary should contain 2000 words and for the critical
evaluation 2000 words and should be presented in the form of a word document and submitted to
Blackboard.
References must be used in order to strengthen any points that you raise in your discussion.
Your discussion must be your own words and, where you have used someone else’s words (quotations), they
should be correctly quoted and referenced in accordance to the Harvard or APA System. If you require
guidance on citation, please use the booklet ‘Cite Them Right’ available from the City Campus library.
Your Reference list is not included in the word count.
Additional Programming Requirements:
Your code must comply with the following requirements:
1. The Java standard should be used as the programming language.
2. Use an industrial strength IDE
3. The program should be executable (i.e. no compile time errors that prevent it from being executed).
4. Project directory should be attached to your word document with the commentary in a zip file. Simply
submitting individual .java files will receive a mark of Zero for the program section.
5. Use meaningful naming conventions for variables, methods and classes.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Marking Scheme
The following marking scheme will be used for this assignment:
Description Marks
Practical Solution (50 %)
Use case model
Logical design showing:
Correct Actors
Efficiency showing inheritance of actors and use cases.
Re-use of use cases
10
Class diagram:
Logical design showing:
Encapsulation.
Efficient design (Inheritance where applicable).
Abstraction.
Functions and Procedures with parameters and return types
Use of design patterns. (Add colour to your design pattern classes to highlight
them)
10
Sequence diagram:
A logical design showing:
Method calls that match method names from your class diagrams.
Parameters and return types shown.
Following the rules of Boundary, control and entity interaction i.e. boundaries can only
talk to control and controls to entities.
10
Program:
A prototype which directly reflects the class diagram designs.
Use of coding standards, comments, OOP principals (inheritance, encapsulation, and
polymorphism) and design pattern classes in Java.
20
Critical Discussion (50%)
Introduction, Conclusion and Criticality 10
Critical self-reflection on your work 15
Critically reflect on professional, legal, social, security and ethical issues related to the
design, development and use of software in an organisational context.
15
Referencing and references 10
Total Marks Available: 100
Note: The marks awarded will be converted to a percentage in order to obtain the final mark for the
assignment.
The following marking scheme will be used for this assignment:
Description Marks
Practical Solution (50 %)
Use case model
Logical design showing:
Correct Actors
Efficiency showing inheritance of actors and use cases.
Re-use of use cases
10
Class diagram:
Logical design showing:
Encapsulation.
Efficient design (Inheritance where applicable).
Abstraction.
Functions and Procedures with parameters and return types
Use of design patterns. (Add colour to your design pattern classes to highlight
them)
10
Sequence diagram:
A logical design showing:
Method calls that match method names from your class diagrams.
Parameters and return types shown.
Following the rules of Boundary, control and entity interaction i.e. boundaries can only
talk to control and controls to entities.
10
Program:
A prototype which directly reflects the class diagram designs.
Use of coding standards, comments, OOP principals (inheritance, encapsulation, and
polymorphism) and design pattern classes in Java.
20
Critical Discussion (50%)
Introduction, Conclusion and Criticality 10
Critical self-reflection on your work 15
Critically reflect on professional, legal, social, security and ethical issues related to the
design, development and use of software in an organisational context.
15
Referencing and references 10
Total Marks Available: 100
Note: The marks awarded will be converted to a percentage in order to obtain the final mark for the
assignment.
Formative Feedback
There will be an opportunity for formative feedback during the semester. You are advised to start working on
this assignment as early as possible so that you can seek clarification from the module tutor regarding any
questions you might have during the semester. Note that tutors will not predict your grade, and you should not
take the lack of comment on any aspect of your work as indicating that it is correct. You should make every
effort to take advantage of formative feedback as tutors will not comment on draft work at other times.
Remember that you will get more useful feedback from us by asking specific questions than just presenting us
with your documentation and asking, ‘Is this right?’
The actual word count is to be declared on the front of the assessment submission.
Marking Criteria
Since the elements above are wide ranging, general criteria are given that are applied as a percentage to
each component of the portfolio. In the following, ‘writing’ is understood to apply both to coding and English
There will be an opportunity for formative feedback during the semester. You are advised to start working on
this assignment as early as possible so that you can seek clarification from the module tutor regarding any
questions you might have during the semester. Note that tutors will not predict your grade, and you should not
take the lack of comment on any aspect of your work as indicating that it is correct. You should make every
effort to take advantage of formative feedback as tutors will not comment on draft work at other times.
Remember that you will get more useful feedback from us by asking specific questions than just presenting us
with your documentation and asking, ‘Is this right?’
The actual word count is to be declared on the front of the assessment submission.
Marking Criteria
Since the elements above are wide ranging, general criteria are given that are applied as a percentage to
each component of the portfolio. In the following, ‘writing’ is understood to apply both to coding and English
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





