Conducting a Security Analysis Baseline for Organizational Protection
VerifiedAdded on 2023/07/24
|17
|4323
|178
AI Summary
This text discusses the importance of conducting a security analysis baseline to establish an appropriate level of security for all systems in an organization. The author outlines the primary requirements for preliminary security baseline activity, including device access, routing infrastructure, network telemetry, network policy enforcement, and switching infrastructure. The text also describes various types of network attacks that organizations may face, such as worms, viruses, Trojans, denial of service attacks, social engineering, and session hijacking. The author emphasizes the importance of understanding the organization’s security posture and infrastructure to identify and address vulnerabilities. Regular enterprise testing is recommended to discover new threats and potential vulnerabilities.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running Head: RISK MANAGEMENT PLAN 1
Risk Management Plan
Student's Name
Institutional Affiliation
Date of Submission
Risk Management Plan
Student's Name
Institutional Affiliation
Date of Submission
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RISK MANAGEMENT PLAN 2
Risk Management
Conducting A Security Analysis Baseline
Security Requirements and Goals
Baseline security is the bare minimum of what an organization needs to safeguard itself
from threats and vulnerabilities while performing effectively sufficiently. Adequate network
security demands a comprehensive approach and hence the need to understand the company's
security posture. The primary requirements for preliminary security baseline activity are its
ability to establish an appropriate level of security for all systems in the organization. Other
conditions that should be considered include device access, routing infrastructure, network
Telemetry, Network policy enforcement, and switching infrastructure. Unless these fundamental
security elements are addressed, additional security controls and features are useless. The goal
for preliminary security baseline activity includes promoting and strengthening the security of
the whole organization computing assets (Chaturvedi, 2020).
Types of Attacks
Organizations rely on the internet for communication, making them vulnerable to various
network attacks such as worms, viruses, Trojans, denial of service attacks, social engineering,
and session hijacking. Denial of service attack involves flooding the network, servers, or system
with traffic to bombard and overwhelm the system, network or server, denying a legitimate user
the right to access the web due to delays or crashes. Social engineering comprises elaborate
methods in deception and trickery approaches that win the user's trust through their inherent
curiosity to gain access to private and confidential information. Some of the impacts these
network attacks have on the system and organization, in general, comprise financial loss, evident
Risk Management
Conducting A Security Analysis Baseline
Security Requirements and Goals
Baseline security is the bare minimum of what an organization needs to safeguard itself
from threats and vulnerabilities while performing effectively sufficiently. Adequate network
security demands a comprehensive approach and hence the need to understand the company's
security posture. The primary requirements for preliminary security baseline activity are its
ability to establish an appropriate level of security for all systems in the organization. Other
conditions that should be considered include device access, routing infrastructure, network
Telemetry, Network policy enforcement, and switching infrastructure. Unless these fundamental
security elements are addressed, additional security controls and features are useless. The goal
for preliminary security baseline activity includes promoting and strengthening the security of
the whole organization computing assets (Chaturvedi, 2020).
Types of Attacks
Organizations rely on the internet for communication, making them vulnerable to various
network attacks such as worms, viruses, Trojans, denial of service attacks, social engineering,
and session hijacking. Denial of service attack involves flooding the network, servers, or system
with traffic to bombard and overwhelm the system, network or server, denying a legitimate user
the right to access the web due to delays or crashes. Social engineering comprises elaborate
methods in deception and trickery approaches that win the user's trust through their inherent
curiosity to gain access to private and confidential information. Some of the impacts these
network attacks have on the system and organization, in general, comprise financial loss, evident

RISK MANAGEMENT PLAN 3
in the cost of response and recovery, cost of investigation, lost revenue, legal and PR costs, and
reduced company valuation. Other impacts are attributed to loss of productivity, staff time lost
during the incident, and halting routine IT work. The organization suffers reputational damage as
stakeholders, and the public loses trust in the company (CISCO, 2021).
The Security Infrastructure and Posture
The security infrastructure posture constitutes components such as local area network,
metropolitan area network and vast area network. Such networks can have loopholes or
vulnerabilities that allow cybercriminals to attack the system or network. Some of the security
concerns in the current networks include physical networking issues such as outdated security
patches, failing to physically secure locking server in a rack closet, or securing entry point with a
turnstile. Misconfigured firewalls or operating systems is also a concern that allows default
policy to enable creating an attack point. Other issues include hidden backdoor programs,
automated scripts without virus checks, and unknown security bugs in software or programming
interfaces. The IT team can get a real-time understanding of its security posture by getting an
accurate IT asset inventory, mapping its attack surface and points, and understanding its cyber
risks effectively. Regular enterprise testing should conduce at least once every year to ensure
more consistent IT and network security management by discovering new threats and how
potential vulnerabilities can be exploited. Some techniques to test enterprise networks include
documentation, log, system configuration review, and network sniffing to discover
vulnerabilities. Target identification and analysis techniques identify systems, services, ports,
and potential loopholes and can be performed manually or using automated tools. Target
vulnerability validation techniques such as password cracking, penetration testing, social
in the cost of response and recovery, cost of investigation, lost revenue, legal and PR costs, and
reduced company valuation. Other impacts are attributed to loss of productivity, staff time lost
during the incident, and halting routine IT work. The organization suffers reputational damage as
stakeholders, and the public loses trust in the company (CISCO, 2021).
The Security Infrastructure and Posture
The security infrastructure posture constitutes components such as local area network,
metropolitan area network and vast area network. Such networks can have loopholes or
vulnerabilities that allow cybercriminals to attack the system or network. Some of the security
concerns in the current networks include physical networking issues such as outdated security
patches, failing to physically secure locking server in a rack closet, or securing entry point with a
turnstile. Misconfigured firewalls or operating systems is also a concern that allows default
policy to enable creating an attack point. Other issues include hidden backdoor programs,
automated scripts without virus checks, and unknown security bugs in software or programming
interfaces. The IT team can get a real-time understanding of its security posture by getting an
accurate IT asset inventory, mapping its attack surface and points, and understanding its cyber
risks effectively. Regular enterprise testing should conduce at least once every year to ensure
more consistent IT and network security management by discovering new threats and how
potential vulnerabilities can be exploited. Some techniques to test enterprise networks include
documentation, log, system configuration review, and network sniffing to discover
vulnerabilities. Target identification and analysis techniques identify systems, services, ports,
and potential loopholes and can be performed manually or using automated tools. Target
vulnerability validation techniques such as password cracking, penetration testing, social

RISK MANAGEMENT PLAN 4
engineering, and application security testing corroborate the existence of vulnerabilities (Lumen
Learning, 2021).
With the advance in attack techniques used by cybercriminals, the current workforce
lacks prerequisite skills to address such adversities and hence the need to increase awareness on
cybersecurity and the possibility of attacks. There is no evident professional development
framework to update employees with the required skills to keep abreast with the changing needs
of cybersecurity and sophisticated attack methods used by cybercriminals. The company can use
various ways to detect malicious codes, such as signature-based, which scans and assesses feeds
of suspicious files. Check-summing is a modification of signature analysis based on calculating
Cyclic Redundancy Check (CRC). Other techniques encompass statistical analysis, know
plaintext cryptanalysis, and reduced masks. However, bad actors use advanced methods such as
obfuscation which involves concealing information such as files to be downloaded and sites
visited. Analyzing the security infrastructure as evidenced will allow the company to understand
its current security posture and the risks of cyber threats and vulnerabilities (Lumen Learning,
2021).
There is also a need to examine the private and public access areas and web access points
to ascertain the possibility of network weaknesses and threats. The sites can be vulnerable to
system weaknesses such as user administrator loopholes, including insider threats, social
engineering, easily compromised passwords, the careless or uninformed users. Physical hazards
in such access points include eavesdropping using cameras and critical loggers and destruction of
property. At the network points, vulnerabilities comprise DNS redirects, authentication hotspots,
and sniffers. Misconfigurations on hardware components such as routers and switches include
attack surfaces such as HTTPTS and SNMP exposure, allowing attackers to launch password-
engineering, and application security testing corroborate the existence of vulnerabilities (Lumen
Learning, 2021).
With the advance in attack techniques used by cybercriminals, the current workforce
lacks prerequisite skills to address such adversities and hence the need to increase awareness on
cybersecurity and the possibility of attacks. There is no evident professional development
framework to update employees with the required skills to keep abreast with the changing needs
of cybersecurity and sophisticated attack methods used by cybercriminals. The company can use
various ways to detect malicious codes, such as signature-based, which scans and assesses feeds
of suspicious files. Check-summing is a modification of signature analysis based on calculating
Cyclic Redundancy Check (CRC). Other techniques encompass statistical analysis, know
plaintext cryptanalysis, and reduced masks. However, bad actors use advanced methods such as
obfuscation which involves concealing information such as files to be downloaded and sites
visited. Analyzing the security infrastructure as evidenced will allow the company to understand
its current security posture and the risks of cyber threats and vulnerabilities (Lumen Learning,
2021).
There is also a need to examine the private and public access areas and web access points
to ascertain the possibility of network weaknesses and threats. The sites can be vulnerable to
system weaknesses such as user administrator loopholes, including insider threats, social
engineering, easily compromised passwords, the careless or uninformed users. Physical hazards
in such access points include eavesdropping using cameras and critical loggers and destruction of
property. At the network points, vulnerabilities comprise DNS redirects, authentication hotspots,
and sniffers. Misconfigurations on hardware components such as routers and switches include
attack surfaces such as HTTPTS and SNMP exposure, allowing attackers to launch password-
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RISK MANAGEMENT PLAN 5
guessing and traffic interception. Weak authentication and lack of automatic updates policies in
routers. Networks, operating systems and servers are also prone to vulnerabilities, mainly when
data is transmitted across networks. For instance, endpoint access vulnerabilities can be
attributed to compromised installed applications and outdated or missing operating system
patches. External storage weaknesses exist because personal devices such as laptops,
smartphones, and flash drives have weak authentication techniques. An attacker can access such
devices and alter or steal data being transmitted. Old versions of VPN, an outdated firmware that
allows hacking attempts, can also make an organization prone to VPN hacking. There is also a
need to analyze the risks of BYOD policies because the company will adopt the policy or
efficient operations (Bansode & Girdhar, 2021).
Security Measures
The analysis of the security infrastructure and hence current posture of the organizations
reveals that the company is prone to Nemours network and system attacks due to existing
vulnerabilities in various network points. Therefore, it is crucial to develop and analyze a
strategic framework that outlines the measures to address the obvious security risks. The step
comprises remediation, mitigation, countermeasures, and recovery. Remediation will involve
actions taken to eradicate a threat before it causes damage, while mitigation occurs when a threat
has happened hence addressing the damages of the attack. The countermeasures will include
developing strong authentication policies such as password protocols, multi-factor
authentications, physical and logical access controls, cryptography, and encryption techniques.
The recovery procedure can consist of determining what has been lost, addressing vulnerabilities
by replacing the old with new systems, halting operations and identifying the attacking virus and
preventing its spread, and updating access controls (Bansode & Girdhar, 2021).
guessing and traffic interception. Weak authentication and lack of automatic updates policies in
routers. Networks, operating systems and servers are also prone to vulnerabilities, mainly when
data is transmitted across networks. For instance, endpoint access vulnerabilities can be
attributed to compromised installed applications and outdated or missing operating system
patches. External storage weaknesses exist because personal devices such as laptops,
smartphones, and flash drives have weak authentication techniques. An attacker can access such
devices and alter or steal data being transmitted. Old versions of VPN, an outdated firmware that
allows hacking attempts, can also make an organization prone to VPN hacking. There is also a
need to analyze the risks of BYOD policies because the company will adopt the policy or
efficient operations (Bansode & Girdhar, 2021).
Security Measures
The analysis of the security infrastructure and hence current posture of the organizations
reveals that the company is prone to Nemours network and system attacks due to existing
vulnerabilities in various network points. Therefore, it is crucial to develop and analyze a
strategic framework that outlines the measures to address the obvious security risks. The step
comprises remediation, mitigation, countermeasures, and recovery. Remediation will involve
actions taken to eradicate a threat before it causes damage, while mitigation occurs when a threat
has happened hence addressing the damages of the attack. The countermeasures will include
developing strong authentication policies such as password protocols, multi-factor
authentications, physical and logical access controls, cryptography, and encryption techniques.
The recovery procedure can consist of determining what has been lost, addressing vulnerabilities
by replacing the old with new systems, halting operations and identifying the attacking virus and
preventing its spread, and updating access controls (Bansode & Girdhar, 2021).

RISK MANAGEMENT PLAN 6
The National Institute of Standards and Technology Special Publication 800-53 (NIST
800-53) outline various security controls that can be applied to the current risks identified in the
IT infrastructure. The security controls comprise access controls, awareness and training, audit
and accountability, contingency planning, configuration management, identification and
authentication, and incidence response. Other security measures highlighted by the non-
regulatory agency encompass media protection, maintenance, personal security, risk assessment,
and program management. All these standards are vital in addressing the identified risks, security
threats, and vulnerabilities. The protocols are both proactive, reactive, and post-incident recovery
that capture all security needs of the organization (Scarfone, 2008).
Network Defense Strategy
Determining a network defense strategy will require testing violations identified in the
previous phase and assessing the effectiveness of these tests. In particular, using methodologies
recommended by NIST 800-53A would be suitable in identifying violations such as threats,
vulnerabilities and risks. Specifically, methods such as testing, examining, and interviewing.
Testing denotes the process of exerting one or more assessment objects to reinforce under
predetermined conditions to compare current and expected results. Examination or assessment
refers to the procedure of checking, inspecting, and achieving clarification, thereby obtaining
evidence of the possible vulnerabilities or weak points in the network or systems. Interviewing
focuses on conducting discussions with specific groups in the company to reinforce awareness,
achieve clarity, or discover the location of evidence. Using a phased information security
assessment technique that includes planning, execution, and post-execution can help assess the
effectiveness of the security controls and tests being conducted (Scarfone, 2008).
The National Institute of Standards and Technology Special Publication 800-53 (NIST
800-53) outline various security controls that can be applied to the current risks identified in the
IT infrastructure. The security controls comprise access controls, awareness and training, audit
and accountability, contingency planning, configuration management, identification and
authentication, and incidence response. Other security measures highlighted by the non-
regulatory agency encompass media protection, maintenance, personal security, risk assessment,
and program management. All these standards are vital in addressing the identified risks, security
threats, and vulnerabilities. The protocols are both proactive, reactive, and post-incident recovery
that capture all security needs of the organization (Scarfone, 2008).
Network Defense Strategy
Determining a network defense strategy will require testing violations identified in the
previous phase and assessing the effectiveness of these tests. In particular, using methodologies
recommended by NIST 800-53A would be suitable in identifying violations such as threats,
vulnerabilities and risks. Specifically, methods such as testing, examining, and interviewing.
Testing denotes the process of exerting one or more assessment objects to reinforce under
predetermined conditions to compare current and expected results. Examination or assessment
refers to the procedure of checking, inspecting, and achieving clarification, thereby obtaining
evidence of the possible vulnerabilities or weak points in the network or systems. Interviewing
focuses on conducting discussions with specific groups in the company to reinforce awareness,
achieve clarity, or discover the location of evidence. Using a phased information security
assessment technique that includes planning, execution, and post-execution can help assess the
effectiveness of the security controls and tests being conducted (Scarfone, 2008).

RISK MANAGEMENT PLAN 7
In particular, the company's technical assessment techniques to test the effectiveness of
security controls can be attributed to review procedures, target identification and assessment
methods, and target vulnerability validation approaches. The review techniques are used to
assess the security posture of the networks and systems and focus on evaluating applications,
networks, policies, and processes to identify vulnerabilities. They include network sniffing,
documentation, ruleset, and log. Target Identification and Analysis methods specialize in
identifying systems, servers, and ports with potential vulnerabilities. The encompass network
discovery, vulnerability scanning, and wireless scanning. Target vulnerability validation
approaches involve testing techniques that confirm the possibility of openness and are conducted
both manually and using automated tools. Some involve penetration testing, phishing, password
cracking, and application security testing (Scarfone, 2008).
The organization can only be confident in its network and system security when it tests
the devices and applications to ascertain its security posture. Some of the testing types comprise
black box testing, white box, and grey box testing. The testing methods will help the
organization keep its networks and systems free from vulnerabilities and possible loopholes that
allow a cybercriminal to launch attacks. Black box testing will involve the IT team testing the
networks or security system without knowing the sources of vulnerabilities or internal structure
of the tested network. During this testing, the IT team or testers do not require insights into the
programming language or possible threats to perform the tests. The goal of the black box testing
involves not digging deep in the network infrastructure but interacting with the user interface,
make sure that the input and output of the system align with specified requirements, and test the
functionality of the network or system. The company can use the too to achieve network and
In particular, the company's technical assessment techniques to test the effectiveness of
security controls can be attributed to review procedures, target identification and assessment
methods, and target vulnerability validation approaches. The review techniques are used to
assess the security posture of the networks and systems and focus on evaluating applications,
networks, policies, and processes to identify vulnerabilities. They include network sniffing,
documentation, ruleset, and log. Target Identification and Analysis methods specialize in
identifying systems, servers, and ports with potential vulnerabilities. The encompass network
discovery, vulnerability scanning, and wireless scanning. Target vulnerability validation
approaches involve testing techniques that confirm the possibility of openness and are conducted
both manually and using automated tools. Some involve penetration testing, phishing, password
cracking, and application security testing (Scarfone, 2008).
The organization can only be confident in its network and system security when it tests
the devices and applications to ascertain its security posture. Some of the testing types comprise
black box testing, white box, and grey box testing. The testing methods will help the
organization keep its networks and systems free from vulnerabilities and possible loopholes that
allow a cybercriminal to launch attacks. Black box testing will involve the IT team testing the
networks or security system without knowing the sources of vulnerabilities or internal structure
of the tested network. During this testing, the IT team or testers do not require insights into the
programming language or possible threats to perform the tests. The goal of the black box testing
involves not digging deep in the network infrastructure but interacting with the user interface,
make sure that the input and output of the system align with specified requirements, and test the
functionality of the network or system. The company can use the too to achieve network and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK MANAGEMENT PLAN 8
application security essentially. The testing procedure should take place in real-time to find
vulnerabilities that can be exploited by an attacker (Scarfone, 2008).
The organization must also consider the adoption of White-Box Testing to focus on
security testing used to validate whether the network or application implementation follows the
intended design, implemented security functionality, and hence uncovered vulnerabilities. The
approaches will include data flow testing, control flow testing, and branch testing methods. Grey
testing approaches will focus on the strengths of both Black-Box testing and White Box testing
while minimizing their weaknesses. It will focus on integration testing suited for web
applications as they don't have binaries, making them challenging to test using the white-box
method. Matrix testing, pattern testing, and regression testing approaches will help the IT team
identify flaws and other vulnerabilities in the IT infrastructure and security posture of the
company (Scarfone, 2008).
Plan the Penetration Testing Engagement
The next step is vital in facilitating the success of penetration testing for the company IT
infrastructure. The testing must be conducted from three viewpoints; internal, external, and
physical penetration tests. The process should include various steps such as planning and
reconnaissance, scanning, gaining access, maintaining access, and analysis. The planning and
reconnaissance phase involves discussions with the organization's stakeholders that ordered the
test to gain insights into the goals and scope of the trial, the application or systems to be tested,
and testing techniques. For instance, some penetration testing can try specific malicious methods,
tactics, and procedures (TTP). It can also be open-minded. The scanning phase focuses on
automated techniques to assess the target systems. The testes will perform static analysis or
dynamic examination to check the system's code for security flaws or gaps. They will also run
application security essentially. The testing procedure should take place in real-time to find
vulnerabilities that can be exploited by an attacker (Scarfone, 2008).
The organization must also consider the adoption of White-Box Testing to focus on
security testing used to validate whether the network or application implementation follows the
intended design, implemented security functionality, and hence uncovered vulnerabilities. The
approaches will include data flow testing, control flow testing, and branch testing methods. Grey
testing approaches will focus on the strengths of both Black-Box testing and White Box testing
while minimizing their weaknesses. It will focus on integration testing suited for web
applications as they don't have binaries, making them challenging to test using the white-box
method. Matrix testing, pattern testing, and regression testing approaches will help the IT team
identify flaws and other vulnerabilities in the IT infrastructure and security posture of the
company (Scarfone, 2008).
Plan the Penetration Testing Engagement
The next step is vital in facilitating the success of penetration testing for the company IT
infrastructure. The testing must be conducted from three viewpoints; internal, external, and
physical penetration tests. The process should include various steps such as planning and
reconnaissance, scanning, gaining access, maintaining access, and analysis. The planning and
reconnaissance phase involves discussions with the organization's stakeholders that ordered the
test to gain insights into the goals and scope of the trial, the application or systems to be tested,
and testing techniques. For instance, some penetration testing can try specific malicious methods,
tactics, and procedures (TTP). It can also be open-minded. The scanning phase focuses on
automated techniques to assess the target systems. The testes will perform static analysis or
dynamic examination to check the system's code for security flaws or gaps. They will also run

RISK MANAGEMENT PLAN 9
vulnerability tests to identify unpatched or old components that can be exploited (Humphries,
2020).
Gaining access will then follow the scanning step where pen testers choose a weak point
in the system or network and penetrate. They can perform password cracking or brute-force
attacks targeting weak authentication, cross-site scripting or performing SQL injections to run
malware on the target network or system. Maintaining access is the fourth phase. The testers act
like an advanced persistent threat (APT) to look for ways to elevate privileges and perform the
lateral movement to gain access to personal assets. The approach will help the company identify
vulnerabilities of internal systems and malicious activity inside the network. The final phase is
the analysis, which includes a report including the identified vulnerabilities during penetration
testing, including those that were not exploited. The information should detail how they breached
the system and how the breach compromised data or internal systems. It should also explain
whether the violation was detected and how the company responded. Consequently, the
organization will use this report findings to remediate vulnerabilities, reinforce security
protocols, and modify security tool configuration (Bertoglio & Zorzo, 2017).
Letter of Intent
Dear Stakeholders,
I would wish to inform you of the rules of engagement regarding penetration testing. Performing
assessment and tests in our networks and system infrastructure is crucial in identifying system
and network vulnerabilities to implement effective countermeasures. The rules of engagement
focus on explaining the manner and procedure the pen testers will follow to conduct the tests
depending on the functionality and scope of testing.
vulnerability tests to identify unpatched or old components that can be exploited (Humphries,
2020).
Gaining access will then follow the scanning step where pen testers choose a weak point
in the system or network and penetrate. They can perform password cracking or brute-force
attacks targeting weak authentication, cross-site scripting or performing SQL injections to run
malware on the target network or system. Maintaining access is the fourth phase. The testers act
like an advanced persistent threat (APT) to look for ways to elevate privileges and perform the
lateral movement to gain access to personal assets. The approach will help the company identify
vulnerabilities of internal systems and malicious activity inside the network. The final phase is
the analysis, which includes a report including the identified vulnerabilities during penetration
testing, including those that were not exploited. The information should detail how they breached
the system and how the breach compromised data or internal systems. It should also explain
whether the violation was detected and how the company responded. Consequently, the
organization will use this report findings to remediate vulnerabilities, reinforce security
protocols, and modify security tool configuration (Bertoglio & Zorzo, 2017).
Letter of Intent
Dear Stakeholders,
I would wish to inform you of the rules of engagement regarding penetration testing. Performing
assessment and tests in our networks and system infrastructure is crucial in identifying system
and network vulnerabilities to implement effective countermeasures. The rules of engagement
focus on explaining the manner and procedure the pen testers will follow to conduct the tests
depending on the functionality and scope of testing.

RISK MANAGEMENT PLAN 10
The types of testing will include Black-box, white test, and grey-box testing. The testing process
will be conducted from an external, internal, and physical point of view to identify vulnerabilities
in various network and system points. Some of the vulnerabilities being tested will include
endpoint, external storage, and media access vulnerabilities. The exploited hardware components
will comprise routers and switches, while the significant types of attack techniques will comprise
password cracking or brute-force attacks and SQL Injections.
The technical team on the client-side should be available throughout the testing process if the
process shuts down due to denial-of-service attacks. The tests will not be announced to the
support staff to enhance its authenticity, thereby defining the readiness of the IT support staff
towards similar attacks. Proper handling of sensitive data should be observed, and the team must
securely integrate communication measures such as encrypting, reports and full disk encryption
on the tester's devices.
There will be regular meetings and update reports between the testing team and client
organization to facilitate effective communication. The testes must present how far they have
gone and what vulnerabilities have been exploited. The organization will also confirm whether
the detection system has been triggered and what data has been altered, stolen, or destroyed.
Thank you for your time,
Information System Security Officer.
The types of testing will include Black-box, white test, and grey-box testing. The testing process
will be conducted from an external, internal, and physical point of view to identify vulnerabilities
in various network and system points. Some of the vulnerabilities being tested will include
endpoint, external storage, and media access vulnerabilities. The exploited hardware components
will comprise routers and switches, while the significant types of attack techniques will comprise
password cracking or brute-force attacks and SQL Injections.
The technical team on the client-side should be available throughout the testing process if the
process shuts down due to denial-of-service attacks. The tests will not be announced to the
support staff to enhance its authenticity, thereby defining the readiness of the IT support staff
towards similar attacks. Proper handling of sensitive data should be observed, and the team must
securely integrate communication measures such as encrypting, reports and full disk encryption
on the tester's devices.
There will be regular meetings and update reports between the testing team and client
organization to facilitate effective communication. The testes must present how far they have
gone and what vulnerabilities have been exploited. The organization will also confirm whether
the detection system has been triggered and what data has been altered, stolen, or destroyed.
Thank you for your time,
Information System Security Officer.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RISK MANAGEMENT PLAN 11
Control families from NIST SP 800-53A
Network penetration testing exposes a number of issues faced by the networks and the
degree of attention required to ensure the prevention of the issues. As such, the identified issues
in a network can be examined by identifying and assessing the violated control families from the
NIST SP 800-53A framework. The NIST SP 800-53A provides a catalog of controls that aim for
the development of the security and privacy of information systems and organizations (NIST,
2014). The control families in the NIST SP 800-53 framework are broken into three classes,
which include; low, moderate, and high. Besides, these control families are highly essential in
boosting the basis of the security of information systems by providing a fundamental baseline for
developing security in the organization's infrastructure.
Violated Control Families
i. Access Control
One of the violated control families from the NIST SP 800-53A framework is access control.
The access control family in the NIST framework entails the security requirements that detail the
logging into the system. This control family entails who has access to the particular assets and
reporting capabilities such as system privileges, account management, and remote access logging
Control families from NIST SP 800-53A
Network penetration testing exposes a number of issues faced by the networks and the
degree of attention required to ensure the prevention of the issues. As such, the identified issues
in a network can be examined by identifying and assessing the violated control families from the
NIST SP 800-53A framework. The NIST SP 800-53A provides a catalog of controls that aim for
the development of the security and privacy of information systems and organizations (NIST,
2014). The control families in the NIST SP 800-53 framework are broken into three classes,
which include; low, moderate, and high. Besides, these control families are highly essential in
boosting the basis of the security of information systems by providing a fundamental baseline for
developing security in the organization's infrastructure.
Violated Control Families
i. Access Control
One of the violated control families from the NIST SP 800-53A framework is access control.
The access control family in the NIST framework entails the security requirements that detail the
logging into the system. This control family entails who has access to the particular assets and
reporting capabilities such as system privileges, account management, and remote access logging

RISK MANAGEMENT PLAN 12
(NIST, 2014). The violation of this access control family occurs when the outsiders or non-
authorized users gain unauthorized access to the assets or data. Ideally, the outside breach is
often attributed to a lack of a proper control mechanism.
This violation can be mitigated by enhancing the framework of access to the systems. One of the
key measures that can help in the management of these issues is the verification and
enhancement of login credentials. In this case, passwords should be introduced to help protected
access to unauthorized locations. Besides, the strength of these measures can be enhanced with
the use of two-factor or multi-factor authentication. PINs and security tokens are other measures
that can be used to improve access control in the organization.
ii. Awareness and Training
Awareness and training is another important component of the NIST SP 800-53A. Effective
awareness and training in an organization help the employees understand the importance of
cyber hygiene and the possible security risks that can be encountered in association with
mitigation actions and measures (NIST, 2014). The violation of the element of awareness and
training in an organization results in the possible occurrence of breaches and attacks of systems.
For example, when the employees are unaware of the importance of not sharing passwords, the
restricted access areas can be vulnerable to attack.
The violation of this control family can be mitigated through the training and education of the
employees. The organization should educate the employees on the various cyber security risks
and the measures that should be taken to ensure that occurrence of the risks is prevented. In the
organization, that the employees should be aware of various control measures (NIST, 2014).
These controls can include; setting up strong passwords and changing passwords to enhance the
(NIST, 2014). The violation of this access control family occurs when the outsiders or non-
authorized users gain unauthorized access to the assets or data. Ideally, the outside breach is
often attributed to a lack of a proper control mechanism.
This violation can be mitigated by enhancing the framework of access to the systems. One of the
key measures that can help in the management of these issues is the verification and
enhancement of login credentials. In this case, passwords should be introduced to help protected
access to unauthorized locations. Besides, the strength of these measures can be enhanced with
the use of two-factor or multi-factor authentication. PINs and security tokens are other measures
that can be used to improve access control in the organization.
ii. Awareness and Training
Awareness and training is another important component of the NIST SP 800-53A. Effective
awareness and training in an organization help the employees understand the importance of
cyber hygiene and the possible security risks that can be encountered in association with
mitigation actions and measures (NIST, 2014). The violation of the element of awareness and
training in an organization results in the possible occurrence of breaches and attacks of systems.
For example, when the employees are unaware of the importance of not sharing passwords, the
restricted access areas can be vulnerable to attack.
The violation of this control family can be mitigated through the training and education of the
employees. The organization should educate the employees on the various cyber security risks
and the measures that should be taken to ensure that occurrence of the risks is prevented. In the
organization, that the employees should be aware of various control measures (NIST, 2014).
These controls can include; setting up strong passwords and changing passwords to enhance the

RISK MANAGEMENT PLAN 13
level of security. Besides, the organization should also educate the employees on the importance
of installation the proper security measures that can help in the prevention of malware and
viruses in the systems (NIST, 2014). As such, the training and awareness should be extended to
cover all the proper areas and ensure that the security foundation of the organization is improved
(NIST, 2014). For successful training and awareness, the organization should define the roles
and personnel to who the procedures can be disseminated. Besides, the current security
awareness and training in the organization should be reviewed and updated (NIST, 2014).
iii. Identification and Authentication
Another NIST control family member is the Identification and Authentication. Identification and
authentication are two essential elements that mark the initial phases of allowing access to the
system. Ideally, identification is identified as the ability to uniquely identify the use of an
application or system. Authentication, on the other hand, is defined as the ability to prove that
the individual requesting access to the system is a genuine user. For example, in any typical login
system, a user has often requested to input an ID or username and a matching password. In this
case, the username is used to provide an indication of the user and the password is used to verify
that the user is genuine. When the username and password match, the user is provided access to
the system.
Violation of identification and authentication is not uncommon. Ideally, the violation of these
elements is often evident in breach of information, manipulation, and even loss of information in
the systems. As such, this violation can be mitigated and prevented by adopting more supporting
authentication measures. For example, 2-factor authentication and multi-factor authentication are
essential measures that can be used to boost authentication. Ideally, these measures can be used
to verify that the individual entering the right password is genuine before granting access to the
level of security. Besides, the organization should also educate the employees on the importance
of installation the proper security measures that can help in the prevention of malware and
viruses in the systems (NIST, 2014). As such, the training and awareness should be extended to
cover all the proper areas and ensure that the security foundation of the organization is improved
(NIST, 2014). For successful training and awareness, the organization should define the roles
and personnel to who the procedures can be disseminated. Besides, the current security
awareness and training in the organization should be reviewed and updated (NIST, 2014).
iii. Identification and Authentication
Another NIST control family member is the Identification and Authentication. Identification and
authentication are two essential elements that mark the initial phases of allowing access to the
system. Ideally, identification is identified as the ability to uniquely identify the use of an
application or system. Authentication, on the other hand, is defined as the ability to prove that
the individual requesting access to the system is a genuine user. For example, in any typical login
system, a user has often requested to input an ID or username and a matching password. In this
case, the username is used to provide an indication of the user and the password is used to verify
that the user is genuine. When the username and password match, the user is provided access to
the system.
Violation of identification and authentication is not uncommon. Ideally, the violation of these
elements is often evident in breach of information, manipulation, and even loss of information in
the systems. As such, this violation can be mitigated and prevented by adopting more supporting
authentication measures. For example, 2-factor authentication and multi-factor authentication are
essential measures that can be used to boost authentication. Ideally, these measures can be used
to verify that the individual entering the right password is genuine before granting access to the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK MANAGEMENT PLAN 14
system. Besides, the prevention of password re-usage is another technique that can be used to
mitigate the violation of this security control. In this case, the login system should be designed in
a manner that prevents a user from re-using passwords. In this case, the cyber attackers would
not be able to guess the password and gain access to the system.
iv. Risk Assessment
The other important component in the NIST framework is risk assessment. Essentially, risk
assessment entails the identification of the various information components that could be at risk
of cyber-attack. For example, these components can be software, hardware, consumer
information, systems, employee information, and intellectual property that can be at risk of
attack. Essentially, risk assessment plays an essential role in the development of a basis of cyber
security training and awareness in an organization (NIST, 2014). With risk assessment, an
organization is able to identify and locate any possible threats that should be prevented. The
violation of the risk assessment control is often evident in the occurrence of cyber security
breaches and attackers. When an organization fails to examine the possible risks, the system is
exposed to cyber security threats and attacks.
As such, this violation can be mitigated by initiating the proper measures of risk assessment in
the organization. The organization should begin the risk assessment by first identifying the value
of information in the systems. The next step entails identifying and prioritizing the assets in the
organization. Risk assessment in the organization will also involve prioritizing and identification
of the assets in the organization. Upon identifying the assets, the next approach entails locating
system. Besides, the prevention of password re-usage is another technique that can be used to
mitigate the violation of this security control. In this case, the login system should be designed in
a manner that prevents a user from re-using passwords. In this case, the cyber attackers would
not be able to guess the password and gain access to the system.
iv. Risk Assessment
The other important component in the NIST framework is risk assessment. Essentially, risk
assessment entails the identification of the various information components that could be at risk
of cyber-attack. For example, these components can be software, hardware, consumer
information, systems, employee information, and intellectual property that can be at risk of
attack. Essentially, risk assessment plays an essential role in the development of a basis of cyber
security training and awareness in an organization (NIST, 2014). With risk assessment, an
organization is able to identify and locate any possible threats that should be prevented. The
violation of the risk assessment control is often evident in the occurrence of cyber security
breaches and attackers. When an organization fails to examine the possible risks, the system is
exposed to cyber security threats and attacks.
As such, this violation can be mitigated by initiating the proper measures of risk assessment in
the organization. The organization should begin the risk assessment by first identifying the value
of information in the systems. The next step entails identifying and prioritizing the assets in the
organization. Risk assessment in the organization will also involve prioritizing and identification
of the assets in the organization. Upon identifying the assets, the next approach entails locating
RISK MANAGEMENT PLAN 15
any threats and vulnerabilities faced by the assets. For better management of the threats, the risk
assessment should be conducted continuously to ensure that any new or upcoming threats and
identified and mitigated.
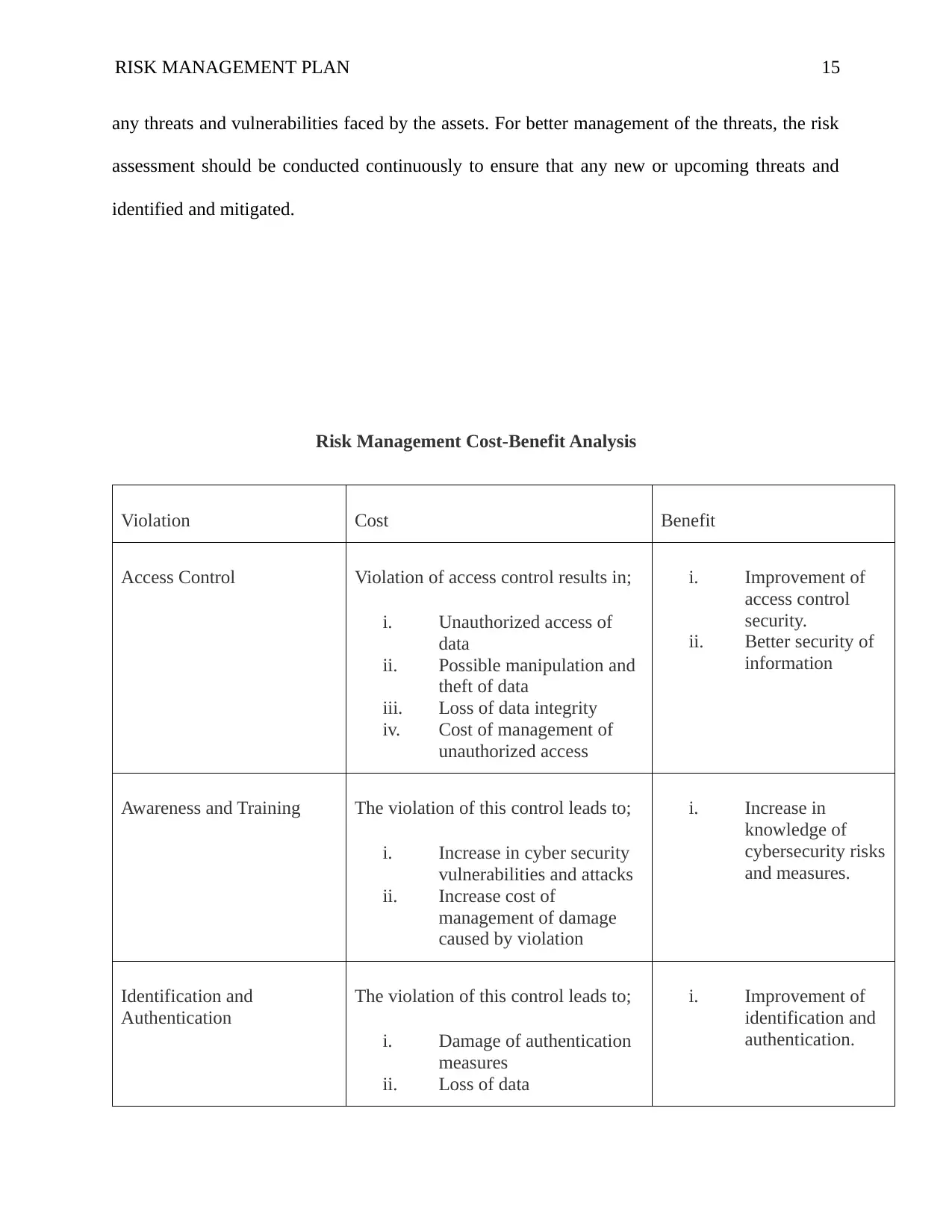
Risk Management Cost-Benefit Analysis
Violation Cost Benefit
Access Control Violation of access control results in;
i. Unauthorized access of
data
ii. Possible manipulation and
theft of data
iii. Loss of data integrity
iv. Cost of management of
unauthorized access
i. Improvement of
access control
security.
ii. Better security of
information
Awareness and Training The violation of this control leads to;
i. Increase in cyber security
vulnerabilities and attacks
ii. Increase cost of
management of damage
caused by violation
i. Increase in
knowledge of
cybersecurity risks
and measures.
Identification and
Authentication
The violation of this control leads to;
i. Damage of authentication
measures
ii. Loss of data
i. Improvement of
identification and
authentication.
any threats and vulnerabilities faced by the assets. For better management of the threats, the risk
assessment should be conducted continuously to ensure that any new or upcoming threats and
identified and mitigated.
Risk Management Cost-Benefit Analysis
Violation Cost Benefit
Access Control Violation of access control results in;
i. Unauthorized access of
data
ii. Possible manipulation and
theft of data
iii. Loss of data integrity
iv. Cost of management of
unauthorized access
i. Improvement of
access control
security.
ii. Better security of
information
Awareness and Training The violation of this control leads to;
i. Increase in cyber security
vulnerabilities and attacks
ii. Increase cost of
management of damage
caused by violation
i. Increase in
knowledge of
cybersecurity risks
and measures.
Identification and
Authentication
The violation of this control leads to;
i. Damage of authentication
measures
ii. Loss of data
i. Improvement of
identification and
authentication.

RISK MANAGEMENT PLAN 16
iii. Liability costs
Risk assessment i. Occurrence of cyber
attacks
ii. Possible liability costs
iii. Financial costs from the
need to resolve cyber
security issues.
i. Prevention of
cyber security
risks
ii. Prevention of
cyber security
attacks.
References
Bansode, R., & Girdhar, A. (2021). Common Vulnerabilities Exposed in VPN- A survey.
Journal of Physics: Conference Series, 1714, 1-8. doi:10.1088/1742-6596/1714/1/012045
Bertoglio, D., & Zorzo, A. (2017). Overview and Open Issues on Penetration Test. Journal of
the Brazilian Computer Society, 23(2), 1-16. doi:10.1186/s13173-017-0051-1
Chaturvedi, M. (2020). Study of Baseline Cyber Security for Various Application Domains. IOP
Conference Series, 1099. Retrieved from https://iopscience.iop.org/article/10.1088/1757-
899X/1099/1/012051/meta
CISCO. (2021). What is a Cyberattack? Retrieved from CISCO:
https://www.cisco.com/c/en/us/products/security/common-cyberattacks.html
Humphries, S. (2020, February 27). Penetration Testing: Process and Tools. Retrieved from
Exabeam: https://www.exabeam.com/security-operations-center/penetration-testing/
iii. Liability costs
Risk assessment i. Occurrence of cyber
attacks
ii. Possible liability costs
iii. Financial costs from the
need to resolve cyber
security issues.
i. Prevention of
cyber security
risks
ii. Prevention of
cyber security
attacks.
References
Bansode, R., & Girdhar, A. (2021). Common Vulnerabilities Exposed in VPN- A survey.
Journal of Physics: Conference Series, 1714, 1-8. doi:10.1088/1742-6596/1714/1/012045
Bertoglio, D., & Zorzo, A. (2017). Overview and Open Issues on Penetration Test. Journal of
the Brazilian Computer Society, 23(2), 1-16. doi:10.1186/s13173-017-0051-1
Chaturvedi, M. (2020). Study of Baseline Cyber Security for Various Application Domains. IOP
Conference Series, 1099. Retrieved from https://iopscience.iop.org/article/10.1088/1757-
899X/1099/1/012051/meta
CISCO. (2021). What is a Cyberattack? Retrieved from CISCO:
https://www.cisco.com/c/en/us/products/security/common-cyberattacks.html
Humphries, S. (2020, February 27). Penetration Testing: Process and Tools. Retrieved from
Exabeam: https://www.exabeam.com/security-operations-center/penetration-testing/
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RISK MANAGEMENT PLAN 17
Lumen Learning. (2021). Where are Vulnerabilities? Understanding the Weaknesses. Retrieved
from Lumen Information Systems: https://courses.lumenlearning.com/santaana-
informationsystems/chapter/where-are-vulnerabilities-understanding-the-weaknesses/
NIST. (2014). Assessing Security and Privacy Controls in Federal Information Systems and
Organizations. NIST Special Publication 800-53A.
Scarfone, K. (2008). Technical Guide to Information Security Testing and Assessment. Retrieved
from National Institute of Standards and Technology:
https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-115.pdf
Lumen Learning. (2021). Where are Vulnerabilities? Understanding the Weaknesses. Retrieved
from Lumen Information Systems: https://courses.lumenlearning.com/santaana-
informationsystems/chapter/where-are-vulnerabilities-understanding-the-weaknesses/
NIST. (2014). Assessing Security and Privacy Controls in Federal Information Systems and
Organizations. NIST Special Publication 800-53A.
Scarfone, K. (2008). Technical Guide to Information Security Testing and Assessment. Retrieved
from National Institute of Standards and Technology:
https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-115.pdf
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




