Configure, verify and Troubleshoot WAN links and IP services in a Medium Enterprise Network
VerifiedAdded on 2023/06/11
|10
|1032
|423
AI Summary
This study material from Desklib covers the configuration, verification and troubleshooting of WAN links and IP services in a medium enterprise network. It includes practical tasks, site-to-site VPN, DHCP, NAT and ACL configurations, and more. The content also discusses the advantages and disadvantages of ADSL and cable broadband technologies.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: ICTNWK506
ICTNWK506
Configure, verify and Troubleshoot WAN links and IP services in a
Medium Enterprise Network
Name of the Student
Name of the University
Author’s Note
ICTNWK506
Configure, verify and Troubleshoot WAN links and IP services in a
Medium Enterprise Network
Name of the Student
Name of the University
Author’s Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
ICTNWK506
Table of Contents
Assessment Task 1: Practical Tasks...........................................................................................2
Task 1: Prepare and Install Medium Enterprise WAN links..................................................2
Task 2: OHS and test report...................................................................................................2
Assessment Task 2: Configuration and verification of WAN Links.........................................2
Task 1: Network Configuration.............................................................................................2
Task 2: ADSL Connections...................................................................................................4
Assessment Task 3: Site to Site VPN........................................................................................5
Assessment Task 4: DHCP, NAT and ACL configurations......................................................5
Task 1: DHCP and NAT........................................................................................................5
Task 2: IPv6...........................................................................................................................6
Task 3: ACLs.........................................................................................................................6
Task 4: WAN issues...............................................................................................................7
Bibliography...............................................................................................................................9
ICTNWK506
Table of Contents
Assessment Task 1: Practical Tasks...........................................................................................2
Task 1: Prepare and Install Medium Enterprise WAN links..................................................2
Task 2: OHS and test report...................................................................................................2
Assessment Task 2: Configuration and verification of WAN Links.........................................2
Task 1: Network Configuration.............................................................................................2
Task 2: ADSL Connections...................................................................................................4
Assessment Task 3: Site to Site VPN........................................................................................5
Assessment Task 4: DHCP, NAT and ACL configurations......................................................5
Task 1: DHCP and NAT........................................................................................................5
Task 2: IPv6...........................................................................................................................6
Task 3: ACLs.........................................................................................................................6
Task 4: WAN issues...............................................................................................................7
Bibliography...............................................................................................................................9

2
ICTNWK506
Assessment Task 1: Practical Tasks
Task 1: Prepare and Install Medium Enterprise WAN links
For the installation of the Medium enterprise WAN link serial connection should be used for
interconnecting the routers with each other and copper straight through cable is used for the
management of the distribution of the network. The prototype of the network is created in
cisco packet tracer and it is tested for checking the connection between the devices and
eliminating the errors in the configuration.
Task 2: OHS and test report
The simulation option is started and packets are sent from different devices in the network for
testing the configuration of the network. The take for the data packet to reach the destination
location is noted with the path selected for the transmission.
Assessment Task 2: Configuration and verification of WAN Links
Task 1: Network Configuration
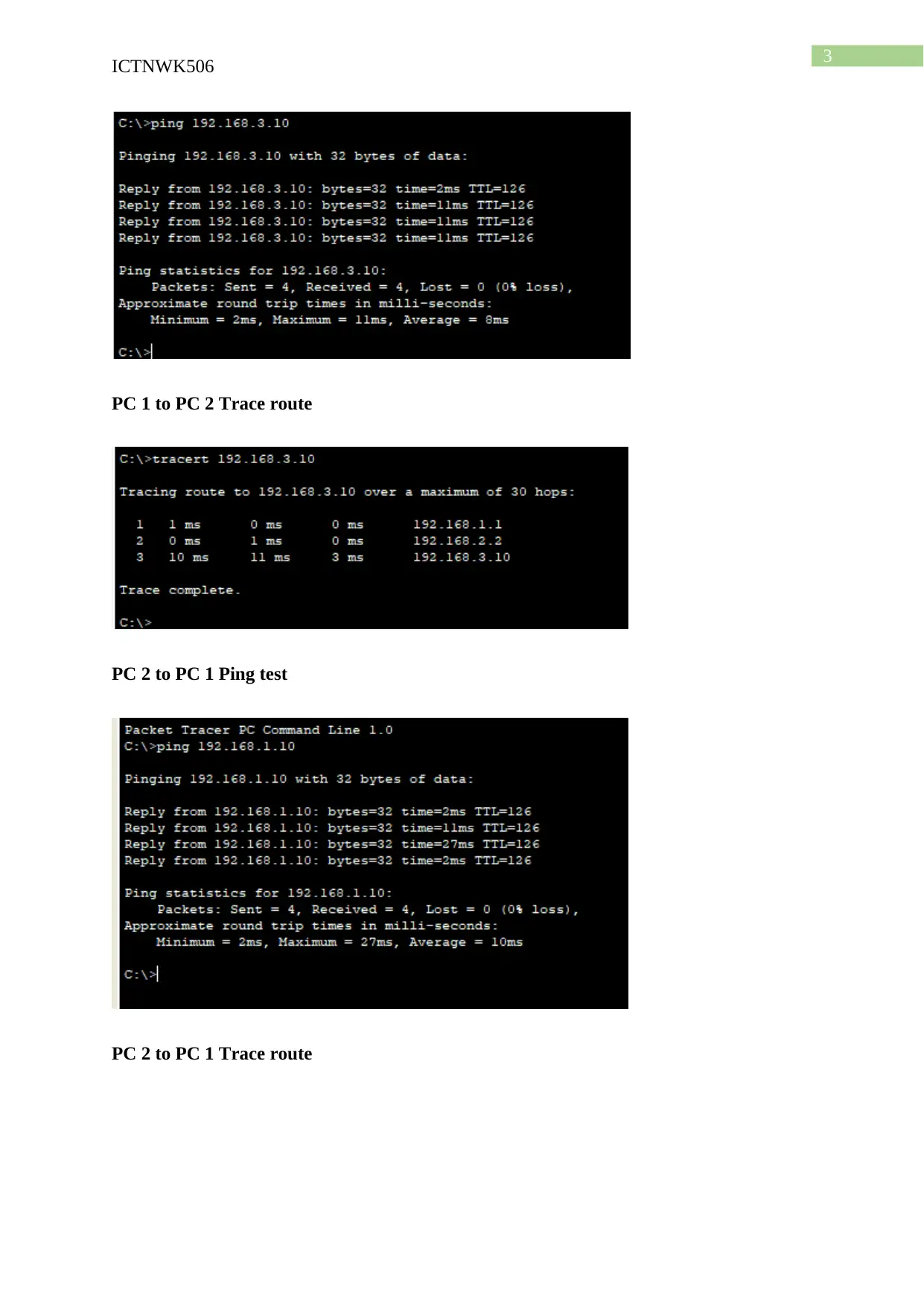
PC 1 to PC 2 Ping test
ICTNWK506
Assessment Task 1: Practical Tasks
Task 1: Prepare and Install Medium Enterprise WAN links
For the installation of the Medium enterprise WAN link serial connection should be used for
interconnecting the routers with each other and copper straight through cable is used for the
management of the distribution of the network. The prototype of the network is created in
cisco packet tracer and it is tested for checking the connection between the devices and
eliminating the errors in the configuration.
Task 2: OHS and test report
The simulation option is started and packets are sent from different devices in the network for
testing the configuration of the network. The take for the data packet to reach the destination
location is noted with the path selected for the transmission.
Assessment Task 2: Configuration and verification of WAN Links
Task 1: Network Configuration
PC 1 to PC 2 Ping test
3
ICTNWK506
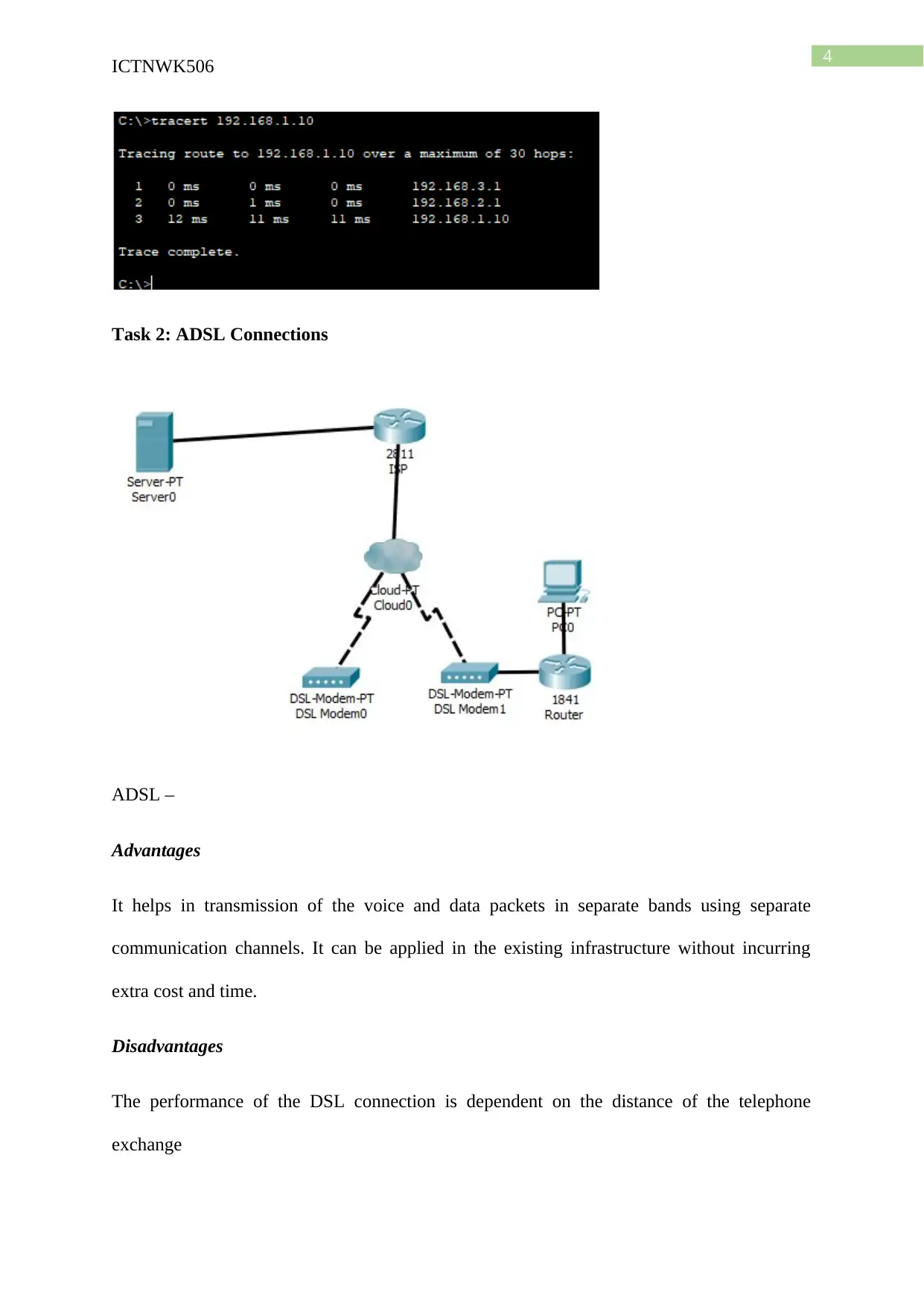
PC 1 to PC 2 Trace route
PC 2 to PC 1 Ping test
PC 2 to PC 1 Trace route
ICTNWK506
PC 1 to PC 2 Trace route
PC 2 to PC 1 Ping test
PC 2 to PC 1 Trace route
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4
ICTNWK506
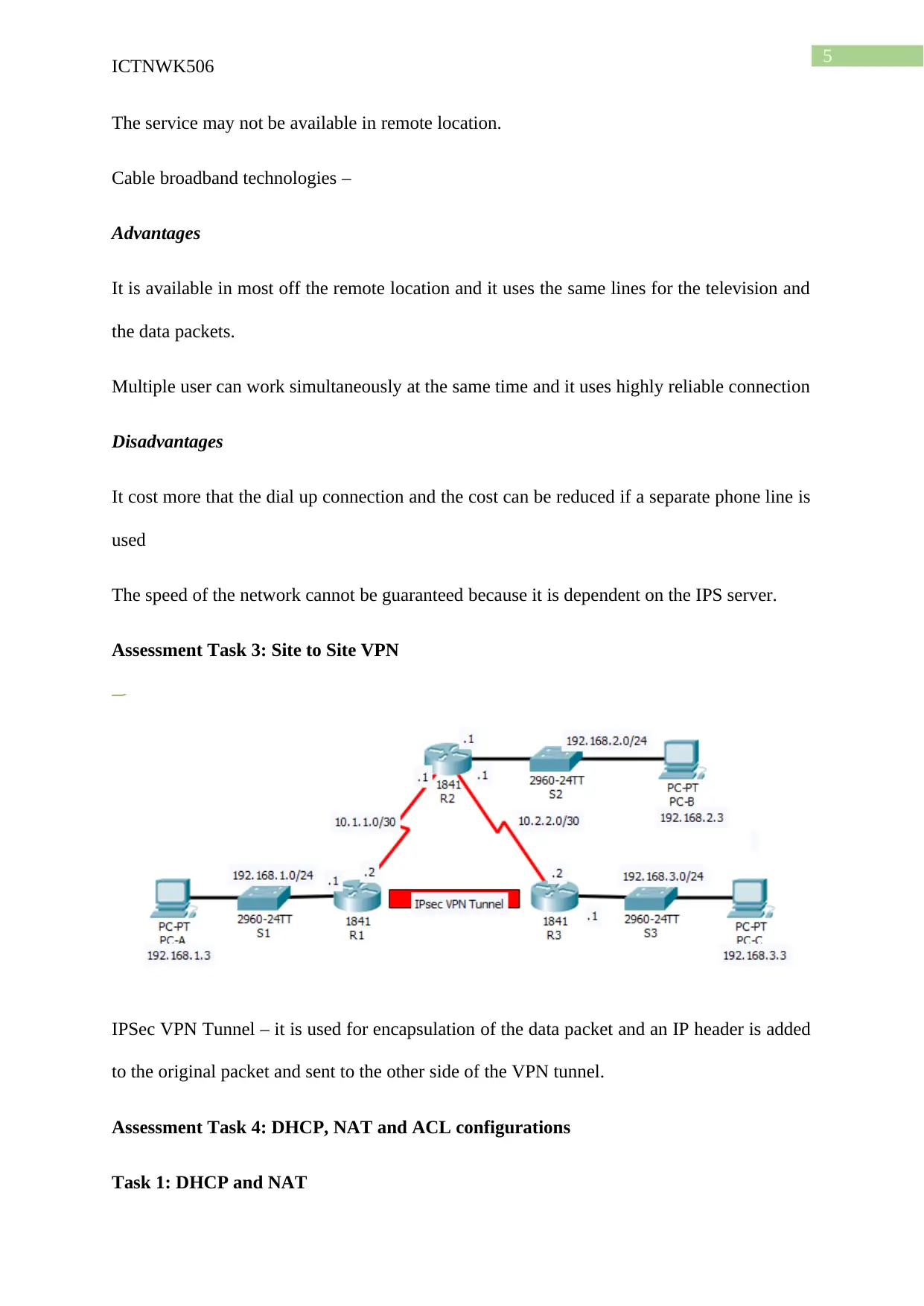
Task 2: ADSL Connections
ADSL –
Advantages
It helps in transmission of the voice and data packets in separate bands using separate
communication channels. It can be applied in the existing infrastructure without incurring
extra cost and time.
Disadvantages
The performance of the DSL connection is dependent on the distance of the telephone
exchange
ICTNWK506
Task 2: ADSL Connections
ADSL –
Advantages
It helps in transmission of the voice and data packets in separate bands using separate
communication channels. It can be applied in the existing infrastructure without incurring
extra cost and time.
Disadvantages
The performance of the DSL connection is dependent on the distance of the telephone
exchange
5
ICTNWK506
The service may not be available in remote location.
Cable broadband technologies –
Advantages
It is available in most off the remote location and it uses the same lines for the television and
the data packets.
Multiple user can work simultaneously at the same time and it uses highly reliable connection
Disadvantages
It cost more that the dial up connection and the cost can be reduced if a separate phone line is
used
The speed of the network cannot be guaranteed because it is dependent on the IPS server.
Assessment Task 3: Site to Site VPN
IPSec VPN Tunnel – it is used for encapsulation of the data packet and an IP header is added
to the original packet and sent to the other side of the VPN tunnel.
Assessment Task 4: DHCP, NAT and ACL configurations
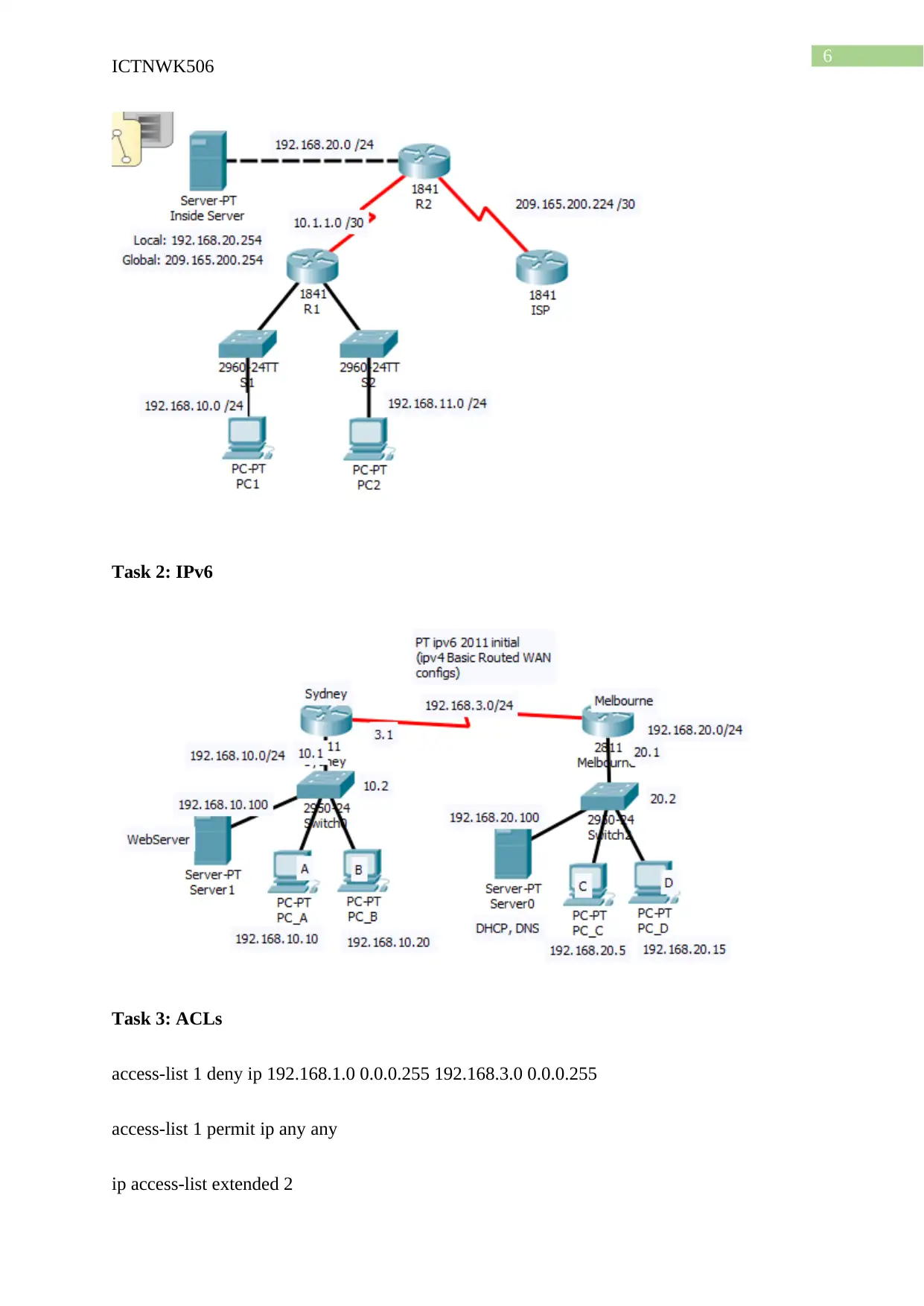
Task 1: DHCP and NAT
ICTNWK506
The service may not be available in remote location.
Cable broadband technologies –
Advantages
It is available in most off the remote location and it uses the same lines for the television and
the data packets.
Multiple user can work simultaneously at the same time and it uses highly reliable connection
Disadvantages
It cost more that the dial up connection and the cost can be reduced if a separate phone line is
used
The speed of the network cannot be guaranteed because it is dependent on the IPS server.
Assessment Task 3: Site to Site VPN
IPSec VPN Tunnel – it is used for encapsulation of the data packet and an IP header is added
to the original packet and sent to the other side of the VPN tunnel.
Assessment Task 4: DHCP, NAT and ACL configurations
Task 1: DHCP and NAT
6
ICTNWK506
Task 2: IPv6
Task 3: ACLs
access-list 1 deny ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
access-list 1 permit ip any any
ip access-list extended 2
ICTNWK506
Task 2: IPv6
Task 3: ACLs
access-list 1 deny ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
access-list 1 permit ip any any
ip access-list extended 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
ICTNWK506
10 deny tcp host 192.168.0.0 0.0.0.255 any eq telnet
20 deny tcp 192.168.1.0 0.0.0.255 any eq 22
access-list 3 deny tcp host 192.168.0.10 host 192.168.10.1 eq 80
access-list 3 permit ip host 192.168.0.1 any
ip access-list extended 101
10 permit tcp 192.168.0.0 0.0.0.255 any eq 22
20 permit tcp 192.168.0.0 0.0.0.255 any eq 23
ip access-list extended 102
deny icmp 192.168.0.0 0.0.0.255 host 192.168.0.10 echo
permit ip any any
ip access-list extended 103
10 permit tcp host 192.168.0.0 0.0.0.255 any eq telnet
20 permit tcp 192.168.1.0 0.0.0.255 any eq 22
ip access-list extended BLOCL_1dot0
10 deny ip any 0.0.0.255 200.10.1.0
Task 4: WAN issues
There are different problems faced during the configuration of the network and it should be
mitigated for the development of the network framework. Different internet blogs and cisco
sites are visited for the analysis of the protocols that are needed for the configuration of the
routers. The links that are given in the document are verified for the WAN links and
resolving the connectivity issues. The different layers of the network and the address table of
ICTNWK506
10 deny tcp host 192.168.0.0 0.0.0.255 any eq telnet
20 deny tcp 192.168.1.0 0.0.0.255 any eq 22
access-list 3 deny tcp host 192.168.0.10 host 192.168.10.1 eq 80
access-list 3 permit ip host 192.168.0.1 any
ip access-list extended 101
10 permit tcp 192.168.0.0 0.0.0.255 any eq 22
20 permit tcp 192.168.0.0 0.0.0.255 any eq 23
ip access-list extended 102
deny icmp 192.168.0.0 0.0.0.255 host 192.168.0.10 echo
permit ip any any
ip access-list extended 103
10 permit tcp host 192.168.0.0 0.0.0.255 any eq telnet
20 permit tcp 192.168.1.0 0.0.0.255 any eq 22
ip access-list extended BLOCL_1dot0
10 deny ip any 0.0.0.255 200.10.1.0
Task 4: WAN issues
There are different problems faced during the configuration of the network and it should be
mitigated for the development of the network framework. Different internet blogs and cisco
sites are visited for the analysis of the protocols that are needed for the configuration of the
routers. The links that are given in the document are verified for the WAN links and
resolving the connectivity issues. The different layers of the network and the address table of

8
ICTNWK506
the router is analysed for the configuration of the access control list. The skills and
knowledge can act as a barrier for the development of the network solution and it should be
improved for the development of the network framework.
ICTNWK506
the router is analysed for the configuration of the access control list. The skills and
knowledge can act as a barrier for the development of the network solution and it should be
improved for the development of the network framework.

9
ICTNWK506
Bibliography
Carthern, C., Wilson, W., Bedwell, R., & Rivera, N. (2015). Network Address Translation
and Dynamic Host Configuration Protocol. In Cisco Networks (pp. 255-272). Apress,
Berkeley, CA.
Chate, A. B., & Chirchi, V. R. (2015). Access Control List Provides Security in
Network. International Journal of Computer Applications, 121(22).
Livadariu, I., Benson, K., Elmokashfi, A., Dainotti, A., & Dhamdhere, A. (2018). Inferring
carrier-grade NAT deployment in the wild. In IEEE Conference on Computer
Communications (INFOCOM).
Ruj, S., Stojmenovic, M., & Nayak, A. (2014). Decentralized access control with anonymous
authentication of data stored in clouds. IEEE transactions on parallel and distributed
systems, 25(2), 384-394.
Takeda, T., Ueda, K., Nakagawa, A., Manabe, S., Okada, K., Mihara, N., & Matsumura, Y.
(2017). A Document-Based EHR System That Controls the Disclosure of Clinical
Documents Using an Access Control List File Based on the HL7 CDA
Header. Studies in health technology and informatics, 245, 1238-1238.
ICTNWK506
Bibliography
Carthern, C., Wilson, W., Bedwell, R., & Rivera, N. (2015). Network Address Translation
and Dynamic Host Configuration Protocol. In Cisco Networks (pp. 255-272). Apress,
Berkeley, CA.
Chate, A. B., & Chirchi, V. R. (2015). Access Control List Provides Security in
Network. International Journal of Computer Applications, 121(22).
Livadariu, I., Benson, K., Elmokashfi, A., Dainotti, A., & Dhamdhere, A. (2018). Inferring
carrier-grade NAT deployment in the wild. In IEEE Conference on Computer
Communications (INFOCOM).
Ruj, S., Stojmenovic, M., & Nayak, A. (2014). Decentralized access control with anonymous
authentication of data stored in clouds. IEEE transactions on parallel and distributed
systems, 25(2), 384-394.
Takeda, T., Ueda, K., Nakagawa, A., Manabe, S., Okada, K., Mihara, N., & Matsumura, Y.
(2017). A Document-Based EHR System That Controls the Disclosure of Clinical
Documents Using an Access Control List File Based on the HL7 CDA
Header. Studies in health technology and informatics, 245, 1238-1238.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





