Understanding DNS Server and Installing Bind for Ubuntu VM
VerifiedAdded on 2023/04/26
|137
|4018
|171
AI Summary
In this docx we will discuss about networking and below are the summaries point:-
Part 1 discusses the DNS server, which interprets common names to IP addresses and communicates with other servers using protocols.
It explains that the DNS server can be used for primary and secondary server redundancy and for running and executing process databases.
Part 1 also includes instructions for installing and configuring the Bind box for the Ubuntu VM.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Networking
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Part: 1.........................................................................................................................................................1
Part: 2.......................................................................................................................................................45
Part: 3.....................................................................................................................................................118
Creating the FTP User..................................................................................................................122
Providing the Permissions for the Directory...............................................................................125
Configuring vsftpd........................................................................................................................126
Testing FTP....................................................................................................................................132
Part: 4.....................................................................................................................................................132
Part: 1.........................................................................................................................................................1
Part: 2.......................................................................................................................................................45
Part: 3.....................................................................................................................................................118
Creating the FTP User..................................................................................................................122
Providing the Permissions for the Directory...............................................................................125
Configuring vsftpd........................................................................................................................126
Testing FTP....................................................................................................................................132
Part: 4.....................................................................................................................................................132

Part: 1
DNS Sever
DNS server comprises of PC server's IP address, database and some related host names
utilized for the most cases which interprets the common names to the IP delivers. The IP delivers
are asked for the databases' records, for the uncommon server programming and they speak with
one another by utilizing the protocols. DNS server could discover the sort of arrangements and
can be utilized to provoke the direction for running and executing the procedure database. It can
be utilized as the principal marked for the framework database server of the essential DNS
server, thus it is the main location which can execute the directions prompted by the information
server. The auxiliary DNS server is the utilized hosts' names and the web spaces to the
information server's IP address. For the essential server repetition, the optional DNS server must
be designed from the zone. The DNS server can run and execute the directions prompted which
are utilized for the presentation on the blunder messages. This message will diminish when an
individual attempts to interface with the web, and the association may fall flat as the Trouble-
shooter is run by encountering a mistake. Here, the gadget or assets don't react. The correct
blunder will be redressed in the DNS server. Then, the DNS server can be utilized for the
location of the web protocol i.e., it can be utilized for the registry to decipher the space names
and the protocol address. The area names of the recollected people's groups are the important PC
or machines to access the direction provoking, based on the IP address.
Installation
The Ubuntu VM process installs, locates DNS server and the SSH server. The following
steps are contained, where initially the system must be updated by the user. These steps are
shown in the below figures. The commands used are also represented in the following section.
1
DNS Sever
DNS server comprises of PC server's IP address, database and some related host names
utilized for the most cases which interprets the common names to the IP delivers. The IP delivers
are asked for the databases' records, for the uncommon server programming and they speak with
one another by utilizing the protocols. DNS server could discover the sort of arrangements and
can be utilized to provoke the direction for running and executing the procedure database. It can
be utilized as the principal marked for the framework database server of the essential DNS
server, thus it is the main location which can execute the directions prompted by the information
server. The auxiliary DNS server is the utilized hosts' names and the web spaces to the
information server's IP address. For the essential server repetition, the optional DNS server must
be designed from the zone. The DNS server can run and execute the directions prompted which
are utilized for the presentation on the blunder messages. This message will diminish when an
individual attempts to interface with the web, and the association may fall flat as the Trouble-
shooter is run by encountering a mistake. Here, the gadget or assets don't react. The correct
blunder will be redressed in the DNS server. Then, the DNS server can be utilized for the
location of the web protocol i.e., it can be utilized for the registry to decipher the space names
and the protocol address. The area names of the recollected people's groups are the important PC
or machines to access the direction provoking, based on the IP address.
Installation
The Ubuntu VM process installs, locates DNS server and the SSH server. The following
steps are contained, where initially the system must be updated by the user. These steps are
shown in the below figures. The commands used are also represented in the following section.
1

Later, ensure installing the Bind with the help if the following steps.
The command lines used are shown in the below figure.
2
The command lines used are shown in the below figure.
2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Next, the Bind box must be installed to successfully execute the system. The following code line
was used.
3
was used.
3

Ipv4 mode must appear as the following step. Then, in the OPTIONS variable include "-4". The
variable is saved and from the options it exits. Thus, for configuring the DNS server the BIND
must be installed now.
After the installation completes, allow it to show the results from the BIND installation,
especially before the bind restarts the system. This step is represented below.
4
variable is saved and from the options it exits. Thus, for configuring the DNS server the BIND
must be installed now.
After the installation completes, allow it to show the results from the BIND installation,
especially before the bind restarts the system. This step is represented below.
4

Initial Configuration of DNS Server
The BIND’s configuration comprises various files to be handled, then BIND runs the
configuration and the options file will be started. This start of option file blocks the line of the
preceding steps.
5
The BIND’s configuration comprises various files to be handled, then BIND runs the
configuration and the options file will be started. This start of option file blocks the line of the
preceding steps.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The subsequent steps of the compliment codes will be similar.
6
6

When the system's directory directive is present, the generated output's steps will be shown,
which could possibly include the lines that are highlighted in the configuration's IP address of the
utilized ns1 that the substitutes uses in the configuration. The substitutes are utilized because
they look like the process’s order.
7
which could possibly include the lines that are highlighted in the configuration's IP address of the
utilized ns1 that the substitutes uses in the configuration. The substitutes are utilized because
they look like the process’s order.
7

Once the configuration file’s option is completed, the local file must be configured as shown in
the below mentioned results of the display file system.
8
the below mentioned results of the display file system.
8
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

The below mentioned commend lines give the IP address.
9
9

Creation of Forward Zone File
Forward zone file is created here by following the below mentioned steps.
10
Forward zone file is created here by following the below mentioned steps.
10

11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Actually, the following looks as if it could show the configuration commands as follows,
12
12

Now, the end of the file deletes 3 set of files along with SOA file. However, the deleted
line could be utilized as if it is deleted and marked using the lines. The server file’s end of the
name would contain the following lines, which could be replaced for specifying the names of the
second column. Thus, the "NS" files will be displayed.
13
line could be utilized as if it is deleted and marked using the lines. The server file’s end of the
name would contain the following lines, which could be replaced for specifying the names of the
second column. Thus, the "NS" files will be displayed.
13

Creation of reverse Zone file(S)
The configure file of the file reverse zone is created with the help of the following steps.
14
The configure file of the file reverse zone is created with the help of the following steps.
14
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

The reverse zone file appears as follows.
15
15

BIND Configuration Syntax Check
Syntax of the BIND configurations are checked with the help of the following steps.
16
Syntax of the BIND configurations are checked with the help of the following steps.
16

17
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

BIND Restarting
Similar to the code file commends, restart the BIND commands, for restarting the configuration
of the IP address.
18
Similar to the code file commends, restart the BIND commands, for restarting the configuration
of the IP address.
18

19
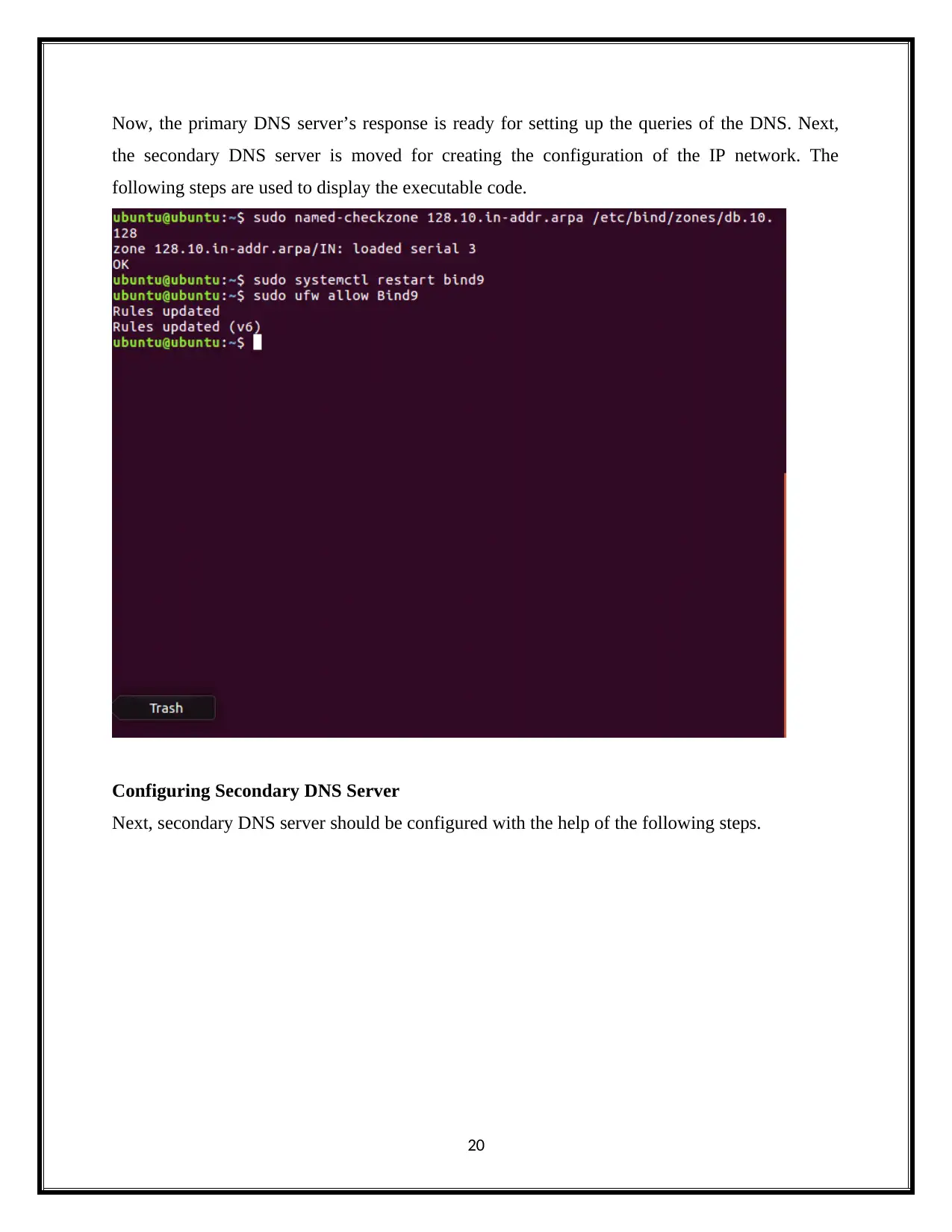
Now, the primary DNS server’s response is ready for setting up the queries of the DNS. Next,
the secondary DNS server is moved for creating the configuration of the IP network. The
following steps are used to display the executable code.
Configuring Secondary DNS Server
Next, secondary DNS server should be configured with the help of the following steps.
20
the secondary DNS server is moved for creating the configuration of the IP network. The
following steps are used to display the executable code.
Configuring Secondary DNS Server
Next, secondary DNS server should be configured with the help of the following steps.
20
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

21

22

23
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DNS Clients’ Configuration
To configure the DNS servers, configure the name server’s reach which is utilized for ns1 and
ns2 that actually depends on the Operating System. The distributions involve including the name
servers.
DNS clients are being configured here with the help of the following steps.
24
To configure the DNS servers, configure the name server’s reach which is utilized for ns1 and
ns2 that actually depends on the Operating System. The distributions involve including the name
servers.
DNS clients are being configured here with the help of the following steps.
24

25

26
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

27

Clients
28
28

29
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
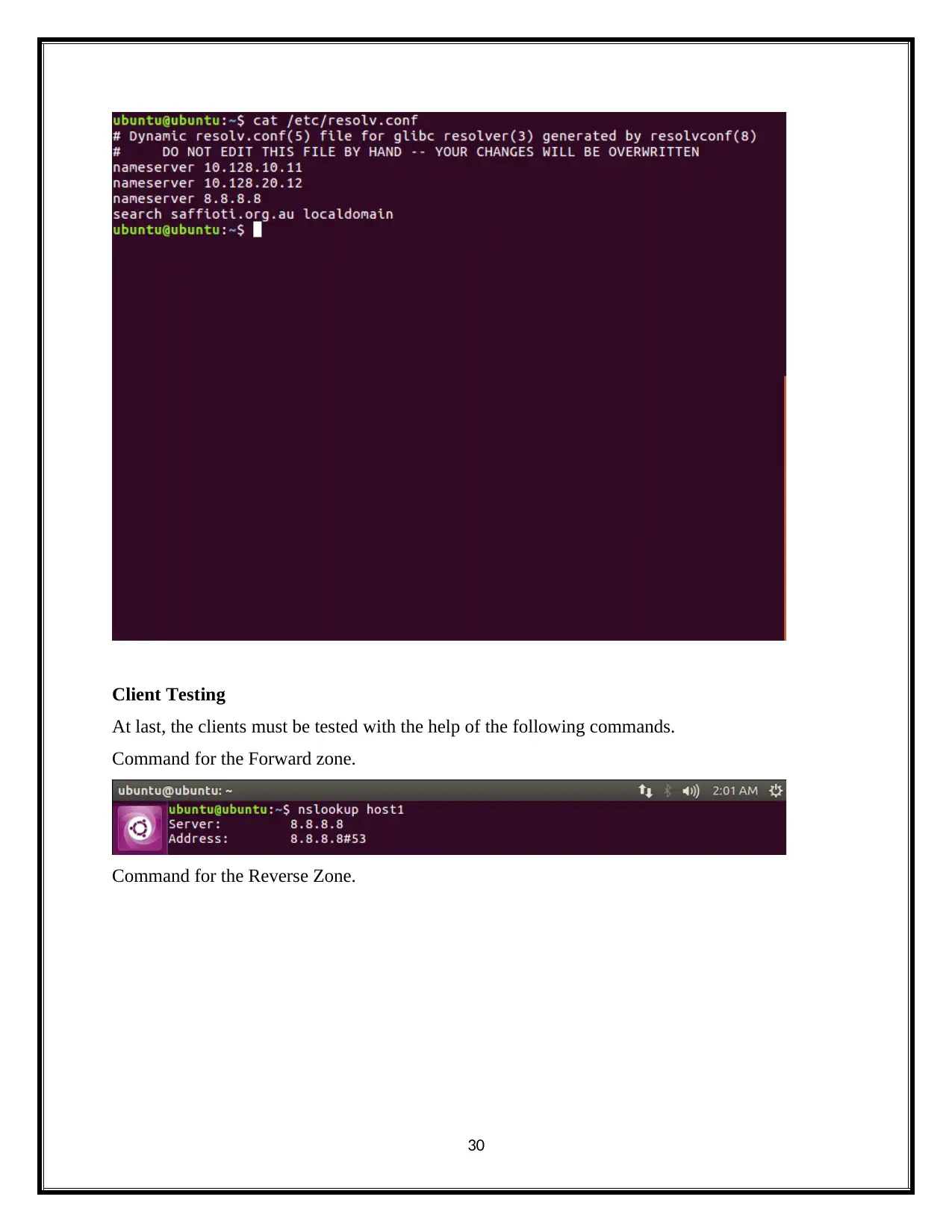
Client Testing
At last, the clients must be tested with the help of the following commands.
Command for the Forward zone.
Command for the Reverse Zone.
30
At last, the clients must be tested with the help of the following commands.
Command for the Forward zone.
Command for the Reverse Zone.
30

The configuration files must also be tested with the help of the following commands.
31
31

32
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

33

SSH Servers
SSH is a secured protocol that is used as the basic technique to remotely interface with
the Linux servers. It provides substance based interface by delivering a remote shell. Consequent
for interfacing all the bearings are the ones that you make in your adjacent terminal. The terminal
of the remote server that execute all the catalog of the IP deliver, where to partner the SSH
through the shell session into you will be dropped, which is a collaboration to the interface
content dependent on which you separate. For the SSH session’s length, any bearings which you
make into your close-by terminals are mixed that are sent via, a SSH of server of the windows
tunnel executed on your server’s IP address design. They are essential good positions provided
by the SSH over its precursors as the usage of encryption for ensuring secure trade of
information among the host and client. Host insinuates the remote server you are trying to get to,
whereas the client denotes the Personal Computer used to reach the host. 3 different encryption
developments are available that are used by the SSH and they are:
34
SSH is a secured protocol that is used as the basic technique to remotely interface with
the Linux servers. It provides substance based interface by delivering a remote shell. Consequent
for interfacing all the bearings are the ones that you make in your adjacent terminal. The terminal
of the remote server that execute all the catalog of the IP deliver, where to partner the SSH
through the shell session into you will be dropped, which is a collaboration to the interface
content dependent on which you separate. For the SSH session’s length, any bearings which you
make into your close-by terminals are mixed that are sent via, a SSH of server of the windows
tunnel executed on your server’s IP address design. They are essential good positions provided
by the SSH over its precursors as the usage of encryption for ensuring secure trade of
information among the host and client. Host insinuates the remote server you are trying to get to,
whereas the client denotes the Personal Computer used to reach the host. 3 different encryption
developments are available that are used by the SSH and they are:
34

a) Symmetrical encryption
b) Hashing
c) Lopsided encryption
The way in which the SSH functions is by making the usage of a client server model to
consider the affirmation of a couple of remote systems and data encryption that goes among
them. SSH server can use the server of the customers as the completed illustrate. The SSH server
in which it infers which server set up must run the bits of programming, if the remote machine is
called the SSH daemon. This is the IP address port of the specific framework items which the
servers tunes up the requests and checks the delivers, moreover to fit the conditions to right
customer accreditations. The customers’ PCs must have a SSH customers. The use of the SSH
tradition refers to know the bit of programming, to give the information and the information can
be given remotely to interface facilitating the username that is used to affirm, however it has
passed on this approval. The customers can use it to demonstrate certain bits of knowledge about
the server creation which needs to be set up.
Installation
Here, the SSH server is installed and configured by using the below steps.
35
b) Hashing
c) Lopsided encryption
The way in which the SSH functions is by making the usage of a client server model to
consider the affirmation of a couple of remote systems and data encryption that goes among
them. SSH server can use the server of the customers as the completed illustrate. The SSH server
in which it infers which server set up must run the bits of programming, if the remote machine is
called the SSH daemon. This is the IP address port of the specific framework items which the
servers tunes up the requests and checks the delivers, moreover to fit the conditions to right
customer accreditations. The customers’ PCs must have a SSH customers. The use of the SSH
tradition refers to know the bit of programming, to give the information and the information can
be given remotely to interface facilitating the username that is used to affirm, however it has
passed on this approval. The customers can use it to demonstrate certain bits of knowledge about
the server creation which needs to be set up.
Installation
Here, the SSH server is installed and configured by using the below steps.
35
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

36

37

Configuration
38
38
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
39
40

41
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

42
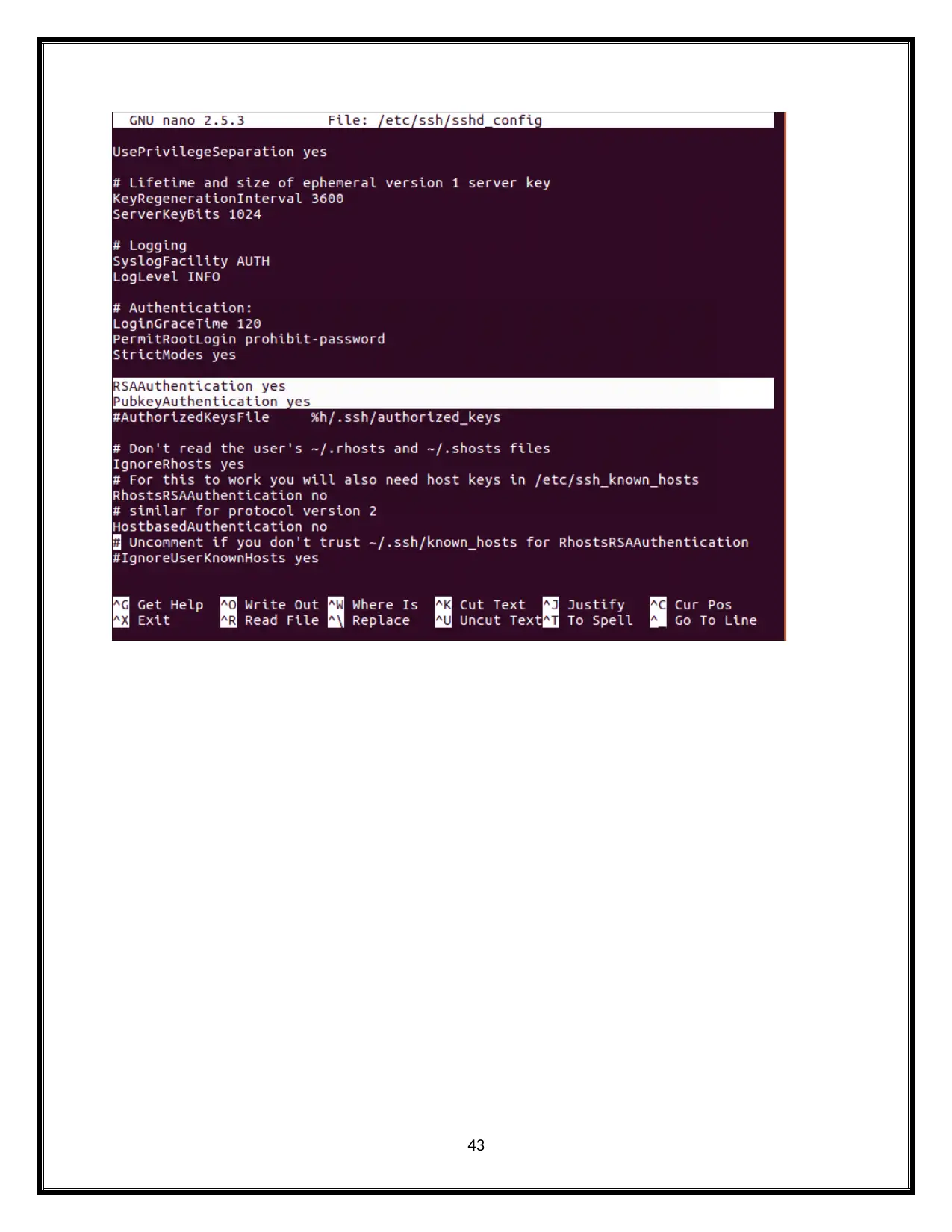
43

44
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Part: 2
Apache web server
Being the Web server, the Apache is accountable for enduring the vault (HTTP) asks for
from the Internet customers and sending them to their optimal information as archives and Web
pages. A huge piece of the Web's item and code is expected to work nearby the Apache's
features. The product engineers wearing down Web applications consistently make use of a
home adjustment of Apache to survey and test the code. Apache also has an ensured and secure
record sharing part, which empowers the customers to put the archives into the root list of their
Apache programming and offers them with various customers. The Apache server's impact on
the open-source programming system is to some degree elucidated by the novel allow through
which programming from the Apache Software Foundation is coursed. By a long shot the vast
majority of Apache HTTP Server events continue running on a Linux movement, yet current
structures moreover continue running on Windows and a wide combination of Unix-like
systems. So also, the past structures continued running on the OpenVMS, NetWare, OS/2 and the
other working systems. Apache supports an arrangement of features, many executed as collected
modules which extend the inside value. These can keep running from check intends to help the
server-side programming vernaculars, for instance, Perl, Python, Tcl and PHP. Here, the Apache
web server is introduced by utilizing the underneath steps (Edwards, 2013).
45
Apache web server
Being the Web server, the Apache is accountable for enduring the vault (HTTP) asks for
from the Internet customers and sending them to their optimal information as archives and Web
pages. A huge piece of the Web's item and code is expected to work nearby the Apache's
features. The product engineers wearing down Web applications consistently make use of a
home adjustment of Apache to survey and test the code. Apache also has an ensured and secure
record sharing part, which empowers the customers to put the archives into the root list of their
Apache programming and offers them with various customers. The Apache server's impact on
the open-source programming system is to some degree elucidated by the novel allow through
which programming from the Apache Software Foundation is coursed. By a long shot the vast
majority of Apache HTTP Server events continue running on a Linux movement, yet current
structures moreover continue running on Windows and a wide combination of Unix-like
systems. So also, the past structures continued running on the OpenVMS, NetWare, OS/2 and the
other working systems. Apache supports an arrangement of features, many executed as collected
modules which extend the inside value. These can keep running from check intends to help the
server-side programming vernaculars, for instance, Perl, Python, Tcl and PHP. Here, the Apache
web server is introduced by utilizing the underneath steps (Edwards, 2013).
45

46

47
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

48

49

50
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
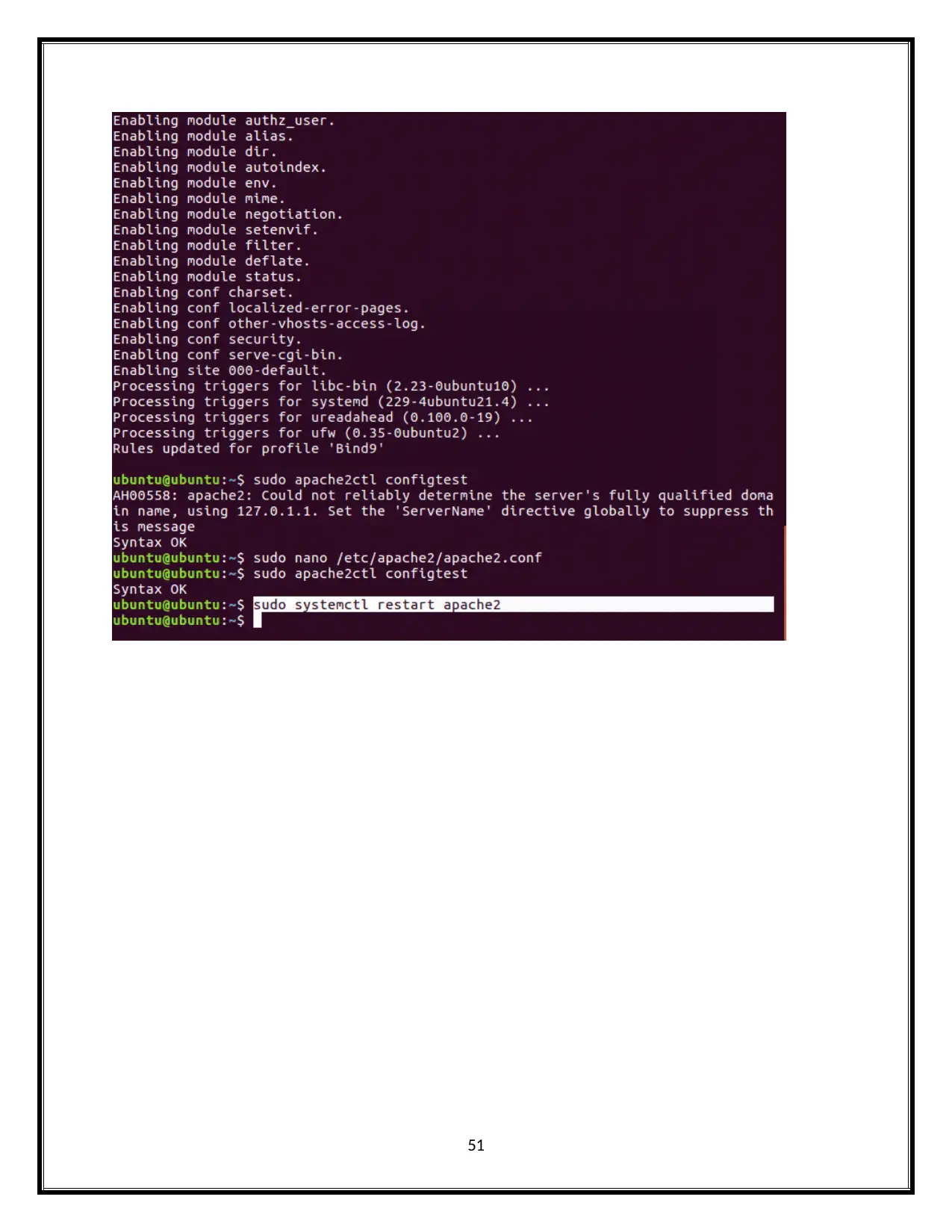
51

52

53
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

54

55

Making DNS Robust
The Ubuntu VM process installs, locates the DNS and the SSH server. The following
steps are included, where initially the system is updated by the user. This step is shown in the
below figures. The Domain name servers’ internet equivalents of the directory maintains and
translates to the addresses of the internet protocol. It is important despite the domain names can
be remembered easily by people, the computers are used for accessing the windows based on the
IP addresses. Domain name server can be standard by the names of using the internet are
corresponding to the IP addresses of the resolved public IPV4 address that allow communication
via, internet. The web address of the windows could be the DNS server’s browser for returning
the client server’s IP configuration address, linked with the name where it manages massive
database which maps the IP addresses’ domain names.
56
The Ubuntu VM process installs, locates the DNS and the SSH server. The following
steps are included, where initially the system is updated by the user. This step is shown in the
below figures. The Domain name servers’ internet equivalents of the directory maintains and
translates to the addresses of the internet protocol. It is important despite the domain names can
be remembered easily by people, the computers are used for accessing the windows based on the
IP addresses. Domain name server can be standard by the names of using the internet are
corresponding to the IP addresses of the resolved public IPV4 address that allow communication
via, internet. The web address of the windows could be the DNS server’s browser for returning
the client server’s IP configuration address, linked with the name where it manages massive
database which maps the IP addresses’ domain names.
56
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
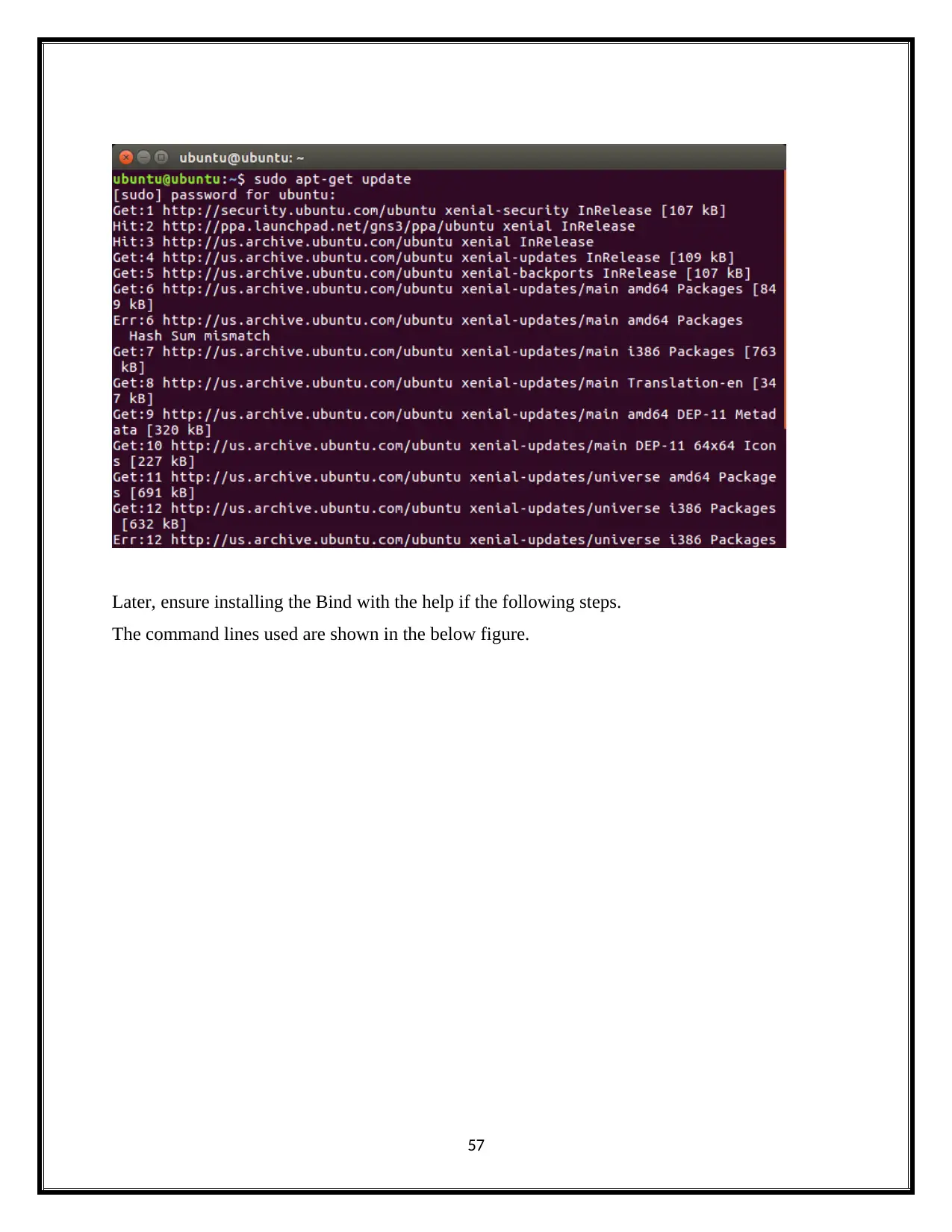
Later, ensure installing the Bind with the help if the following steps.
The command lines used are shown in the below figure.
57
The command lines used are shown in the below figure.
57

Next, the Bind box must be installed to successfully execute the system. The following code line
was used.
Ipv4 mode must appear as the following step. Then, in the OPTIONS variable include "-4". The
variable is saved and from the options it exits. Thus, for configuring the DNS server the BIND
must be installed now.
58
was used.
Ipv4 mode must appear as the following step. Then, in the OPTIONS variable include "-4". The
variable is saved and from the options it exits. Thus, for configuring the DNS server the BIND
must be installed now.
58

After the installation completes, allow it to show the results from the BIND installation,
especially before the bind restarts the system. This step is represented below.
59
especially before the bind restarts the system. This step is represented below.
59
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Initial Configuration of DNS Server
The BIND’s configuration comprises various files to be handled, then BIND runs the
configuration and the options file will be started. This start of option file blocks the line of the
preceding steps.
60
The BIND’s configuration comprises various files to be handled, then BIND runs the
configuration and the options file will be started. This start of option file blocks the line of the
preceding steps.
60

The subsequent steps of the compliment codes will be similar.
61
61

When the system's directory directive is present, the generated output's steps will be shown,
which could possibly include the lines that are highlighted in the configuration's IP address of the
utilized ns1 that the substitutes uses in the configuration. The substitutes are utilized because
they look like the process’s order.
62
which could possibly include the lines that are highlighted in the configuration's IP address of the
utilized ns1 that the substitutes uses in the configuration. The substitutes are utilized because
they look like the process’s order.
62
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Once the configuration file’s option is completed, the local file must be configured as shown in
the below mentioned results of the display file system.
63
the below mentioned results of the display file system.
63

The below mentioned commend lines give the IP address.
64
64

Creation of Forward Zone File
Forward zone file is created here by following the below mentioned steps.
65
Forward zone file is created here by following the below mentioned steps.
65
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

66

Actually, the following looks as if it could show the configuration commands as follows,
67
67

Now, the end of the file deletes 3 set of files along with SOA file. The deleted line can be
utilized as if it is deleted and marked using the lines. The end of the name server file would
contain the following lines, which could be replaced for specifying the names of the second
column. Thus, the "NS" files will be displayed.
68
utilized as if it is deleted and marked using the lines. The end of the name server file would
contain the following lines, which could be replaced for specifying the names of the second
column. Thus, the "NS" files will be displayed.
68
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Creation of reverse Zone file(S)
The configure file of the file reverse zone is created with the help of the following steps.
69
The configure file of the file reverse zone is created with the help of the following steps.
69

Reverse zone file appears as follows.
70
70

BIND Configuration Syntax Check
Syntax of the BIND configurations are checked with the help of the following steps.
71
Syntax of the BIND configurations are checked with the help of the following steps.
71
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

72

BIND Restarting
Similar to the code file commends, restart the BIND commands, for restarting the configuration
of the IP address.
73
Similar to the code file commends, restart the BIND commands, for restarting the configuration
of the IP address.
73

74
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Now, the primary DNS server’s response is ready for setting up the queries of the DNS. Next,
the secondary DNS server is moved for creating the configuration of the IP network. The
following steps are used to display the executable code.
Secondary DNS Server Configuration
Next, secondary DNS server must be configured with the help of the following steps.
(Edwards, 2013).
75
the secondary DNS server is moved for creating the configuration of the IP network. The
following steps are used to display the executable code.
Secondary DNS Server Configuration
Next, secondary DNS server must be configured with the help of the following steps.
(Edwards, 2013).
75

76

77
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

78

DNS Clients’ Configuration
To configure the DNS servers, configure the name server’s reach which is utilized for ns1 and
ns2 that actually depends on the Operating System. The distributions involve including the name
servers.
DNS clients are being configured here with the help of the following steps.
79
To configure the DNS servers, configure the name server’s reach which is utilized for ns1 and
ns2 that actually depends on the Operating System. The distributions involve including the name
servers.
DNS clients are being configured here with the help of the following steps.
79

80
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

81

82

Clients
83
83
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

84

Two Virtual Machines – DNS server
The Ubuntu VM process installs, locates the DNS and the SSH server. The following
steps are involved, where initially the system is updated by the user. This step is shown in the
below figures. The web service’s application could be utilized for Linux windows, especially for
interoperating the web services’ integration process, which actually refers to a process that
fractures the other internet applications. Such applications are modular and could be easily mixed
for providing distinct functionality. For the client server devices of PDAs, desktop computers,
and consumer devices which contains the embedded controllers, the end users can be developed,
for maintaining the client or the server applications. The web service’s Linux are embracing new
web technology and are not stuck in the language to be developed, as in the old client side they
only configure the IP address despite that the Linux is utilized for the development of network
integration. The configuration of the IP address could be utilized for the embedded products and
it must be developed inside the same huge organization, with some based on windows CE, some
85
The Ubuntu VM process installs, locates the DNS and the SSH server. The following
steps are involved, where initially the system is updated by the user. This step is shown in the
below figures. The web service’s application could be utilized for Linux windows, especially for
interoperating the web services’ integration process, which actually refers to a process that
fractures the other internet applications. Such applications are modular and could be easily mixed
for providing distinct functionality. For the client server devices of PDAs, desktop computers,
and consumer devices which contains the embedded controllers, the end users can be developed,
for maintaining the client or the server applications. The web service’s Linux are embracing new
web technology and are not stuck in the language to be developed, as in the old client side they
only configure the IP address despite that the Linux is utilized for the development of network
integration. The configuration of the IP address could be utilized for the embedded products and
it must be developed inside the same huge organization, with some based on windows CE, some
85

in Linux, some on configuration of the web service for information server. This is represented
with the utilized commands.
Later, ensure installing the Bind with the help if the following steps.
The command lines used are shown in the below figure.
86
with the utilized commands.
Later, ensure installing the Bind with the help if the following steps.
The command lines used are shown in the below figure.
86
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Next, the Bind box must be installed to successfully execute the system. The following code line
was used.
Ipv4 mode must appear as the following step. Then, in the OPTIONS variable include "-4". The
variable is saved and from the options it exits. Thus, for configuring the DNS server the BIND
must be installed now.
87
was used.
Ipv4 mode must appear as the following step. Then, in the OPTIONS variable include "-4". The
variable is saved and from the options it exits. Thus, for configuring the DNS server the BIND
must be installed now.
87

After the installation completes, allow it to show the results from the BIND installation,
especially before the bind restarts the system. This step is represented below.
88
especially before the bind restarts the system. This step is represented below.
88

Initial Configuration of DNS Server
The BIND’s configuration comprises various files to be handled, then BIND runs the
configuration and the options file will be started. This start of option file blocks the line of the
preceding steps.
89
The BIND’s configuration comprises various files to be handled, then BIND runs the
configuration and the options file will be started. This start of option file blocks the line of the
preceding steps.
89
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The subsequent steps of the compliment codes will be similar.
90
90

When the system's directory directive is present, the generated output's steps will be shown,
which could possibly include the lines that are highlighted in the configuration's IP address of the
utilized ns1 that the substitutes uses in the configuration. The substitutes are utilized because
they look like the process’s order.
91
which could possibly include the lines that are highlighted in the configuration's IP address of the
utilized ns1 that the substitutes uses in the configuration. The substitutes are utilized because
they look like the process’s order.
91

Once the configuration file’s option is completed, the local file must be configured as shown in
the below mentioned results of file system.
92
the below mentioned results of file system.
92
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Below mentioned commend lines give the IP address.
93
93

Creation of Forward Zone File
Forward zone file is created here with the following steps.
94
Forward zone file is created here with the following steps.
94

95
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Actually, the following looks as if it could show the configuration commands as follows,
96
96

Now, the end of the file deletes 3 set of files along with SOA file. The deleted line can be
utilized as if it is deleted and marked using the lines. The end of the name server file would
contain the following lines, which could be replaced for specifying the names of the second
column. Thus, the "NS" files will be displayed.
97
utilized as if it is deleted and marked using the lines. The end of the name server file would
contain the following lines, which could be replaced for specifying the names of the second
column. Thus, the "NS" files will be displayed.
97

Creation of reverse Zone file(S)
The configure file of the file reverse zone is created with the help of the following steps.
98
The configure file of the file reverse zone is created with the help of the following steps.
98
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Reverse zone file appears as follows.
99
99

BIND Configuration Syntax Check
Syntax of the BIND configurations are checked with the help of the following steps.
100
Syntax of the BIND configurations are checked with the help of the following steps.
100

101
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Restarting BIND
BIND Restarting
Similar to the code file commends, restart the BIND commands, for restarting the configuration
of the IP address.
102
BIND Restarting
Similar to the code file commends, restart the BIND commands, for restarting the configuration
of the IP address.
102

103

Now, the primary DNS server’s response is ready for setting up the queries of the DNS. Next,
the secondary DNS server is moved for creating the configuration of the IP network. The
following steps are used to display the executable code.
Secondary DNS Server Configuration
Next, secondary DNS server must be configured with the help of the following steps.
104
the secondary DNS server is moved for creating the configuration of the IP network. The
following steps are used to display the executable code.
Secondary DNS Server Configuration
Next, secondary DNS server must be configured with the help of the following steps.
104
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

105

106

107
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DNS Clients’ Configuration
To configure the DNS servers, configure the name server’s reach which is utilized for ns1 and
ns2 that actually depends on the Operating System. The distributions involve including the name
servers.
DNS clients are being configured here with the help of the following steps.
108
To configure the DNS servers, configure the name server’s reach which is utilized for ns1 and
ns2 that actually depends on the Operating System. The distributions involve including the name
servers.
DNS clients are being configured here with the help of the following steps.
108

109

110
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

111

Clients
112
112

113
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
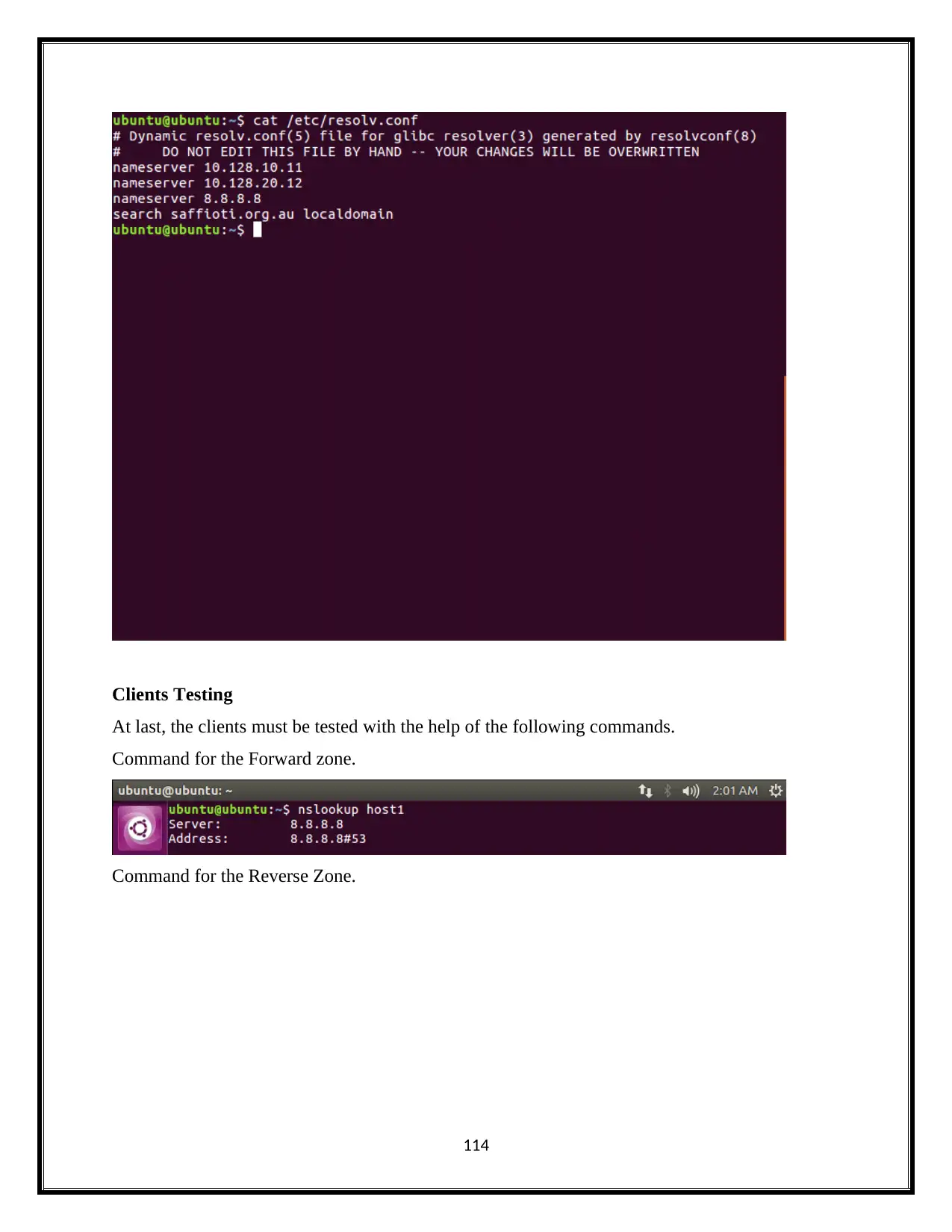
Clients Testing
At last, the clients must be tested with the help of the following commands.
Command for the Forward zone.
Command for the Reverse Zone.
114
At last, the clients must be tested with the help of the following commands.
Command for the Forward zone.
Command for the Reverse Zone.
114

The configuration files must also be tested with the help of the following commands.
115
115

116
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

117

Part: 3
Transferring the Files Securely with the help of SCP
For the reports which could download to modify the PC's system’s document Transfer
protocol access, the transfer control protocol could be used. Later, it was used to exchange the
records, where the encryption methodology was not used, which accredited the customers and
the data and if moved freely can be caught easily. Thus, if you are looking for a solution for
dealing with the record exchange and download records, then refer the section related to, Open
SSH in Remote Administration. The customer server is harmed by the FTP and also it will be
showed. The FTP daemon is also known as, section of server. It always utilizes the remote
customers' servers. At the arrange point’s IP address, when the server seems interested it will
manage and setup the login. The FTP customer in wording and the condition can execute any
headings for sending the IP arrange to the FTP customers. The FTP server’s access could be
regulated in a couple of different methods such as, Anonymous and Confirmed.
118
Transferring the Files Securely with the help of SCP
For the reports which could download to modify the PC's system’s document Transfer
protocol access, the transfer control protocol could be used. Later, it was used to exchange the
records, where the encryption methodology was not used, which accredited the customers and
the data and if moved freely can be caught easily. Thus, if you are looking for a solution for
dealing with the record exchange and download records, then refer the section related to, Open
SSH in Remote Administration. The customer server is harmed by the FTP and also it will be
showed. The FTP daemon is also known as, section of server. It always utilizes the remote
customers' servers. At the arrange point’s IP address, when the server seems interested it will
manage and setup the login. The FTP customer in wording and the condition can execute any
headings for sending the IP arrange to the FTP customers. The FTP server’s access could be
regulated in a couple of different methods such as, Anonymous and Confirmed.
118
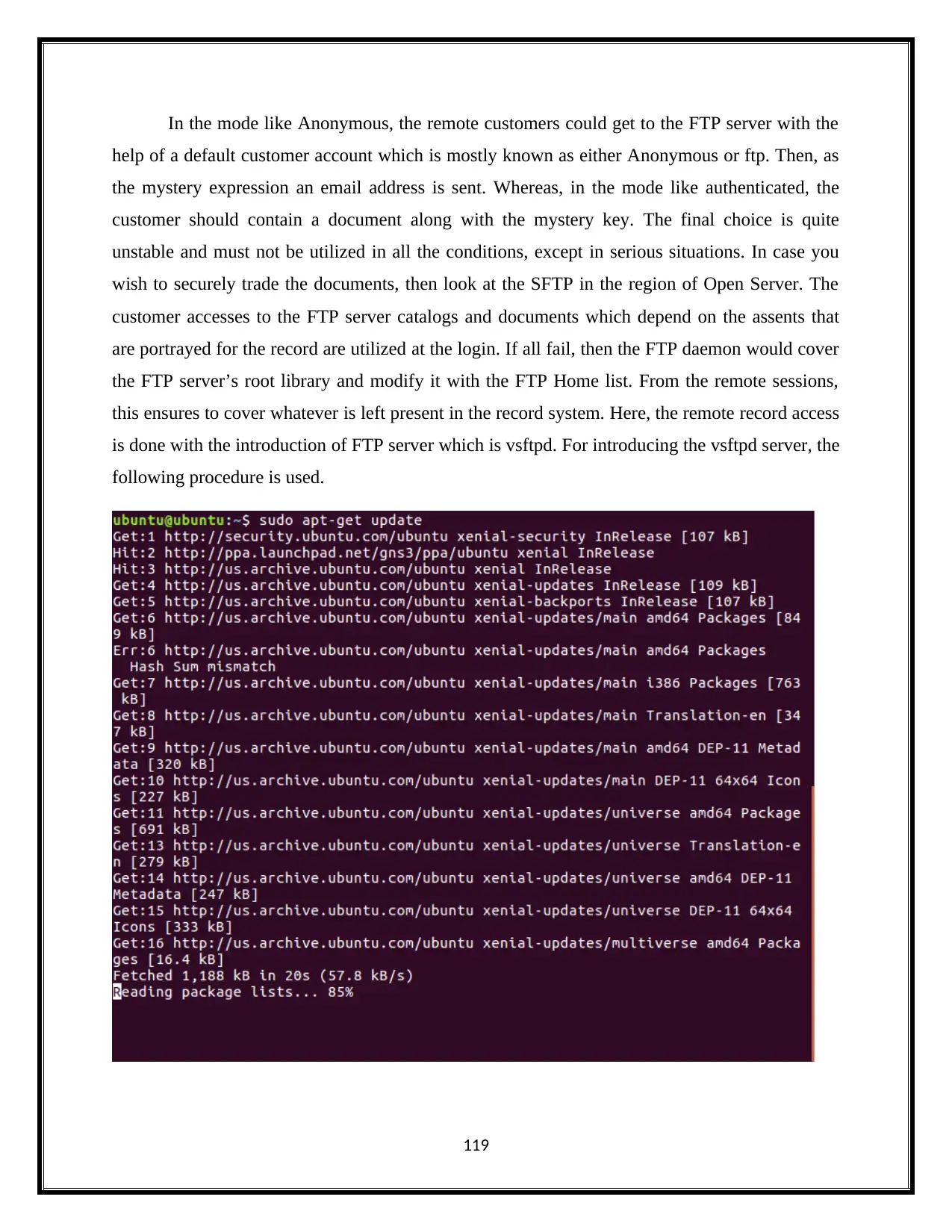
In the mode like Anonymous, the remote customers could get to the FTP server with the
help of a default customer account which is mostly known as either Anonymous or ftp. Then, as
the mystery expression an email address is sent. Whereas, in the mode like authenticated, the
customer should contain a document along with the mystery key. The final choice is quite
unstable and must not be utilized in all the conditions, except in serious situations. In case you
wish to securely trade the documents, then look at the SFTP in the region of Open Server. The
customer accesses to the FTP server catalogs and documents which depend on the assents that
are portrayed for the record are utilized at the login. If all fail, then the FTP daemon would cover
the FTP server’s root library and modify it with the FTP Home list. From the remote sessions,
this ensures to cover whatever is left present in the record system. Here, the remote record access
is done with the introduction of FTP server which is vsftpd. For introducing the vsftpd server, the
following procedure is used.
119
help of a default customer account which is mostly known as either Anonymous or ftp. Then, as
the mystery expression an email address is sent. Whereas, in the mode like authenticated, the
customer should contain a document along with the mystery key. The final choice is quite
unstable and must not be utilized in all the conditions, except in serious situations. In case you
wish to securely trade the documents, then look at the SFTP in the region of Open Server. The
customer accesses to the FTP server catalogs and documents which depend on the assents that
are portrayed for the record are utilized at the login. If all fail, then the FTP daemon would cover
the FTP server’s root library and modify it with the FTP Home list. From the remote sessions,
this ensures to cover whatever is left present in the record system. Here, the remote record access
is done with the introduction of FTP server which is vsftpd. For introducing the vsftpd server, the
following procedure is used.
119
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

120
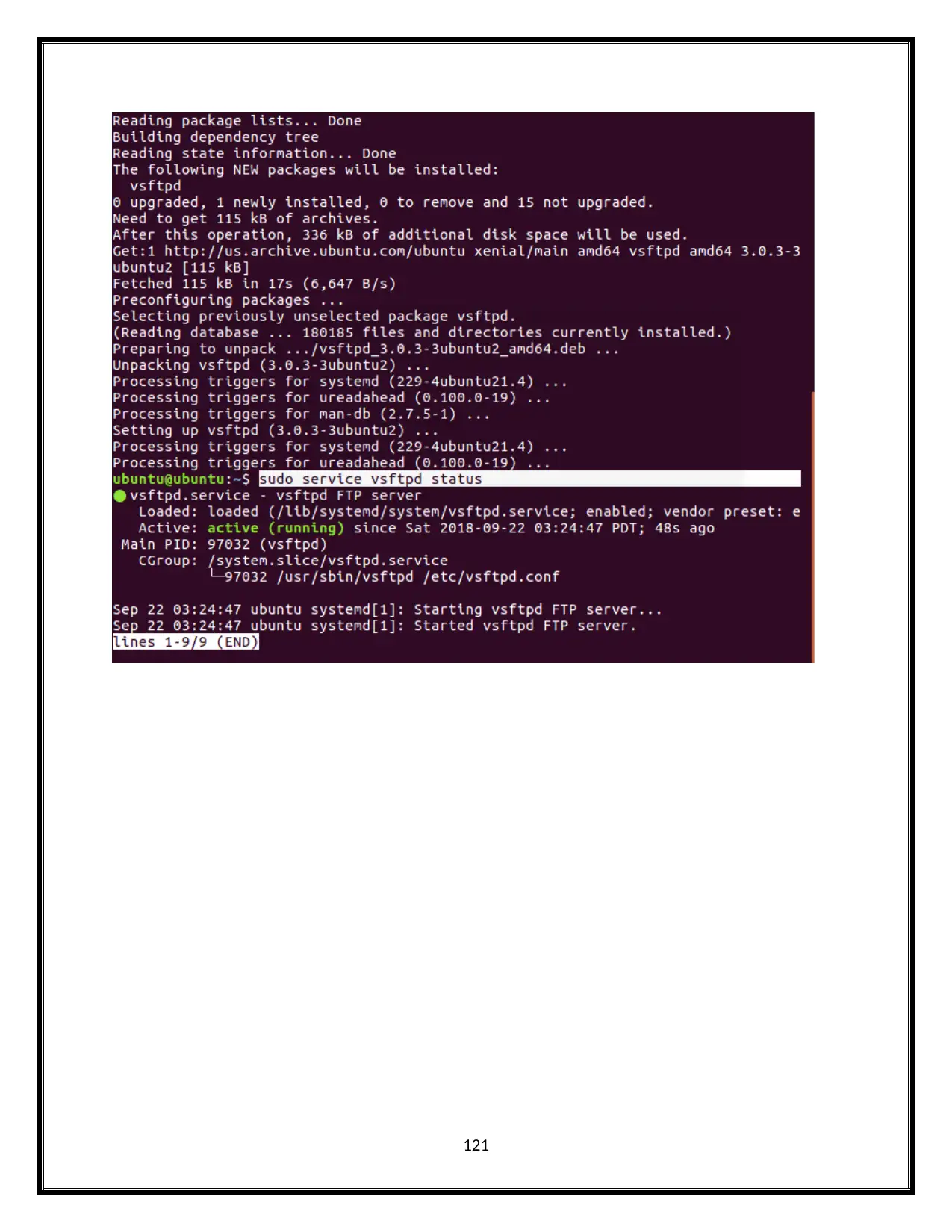
121

Creating the FTP User
122
122
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

123
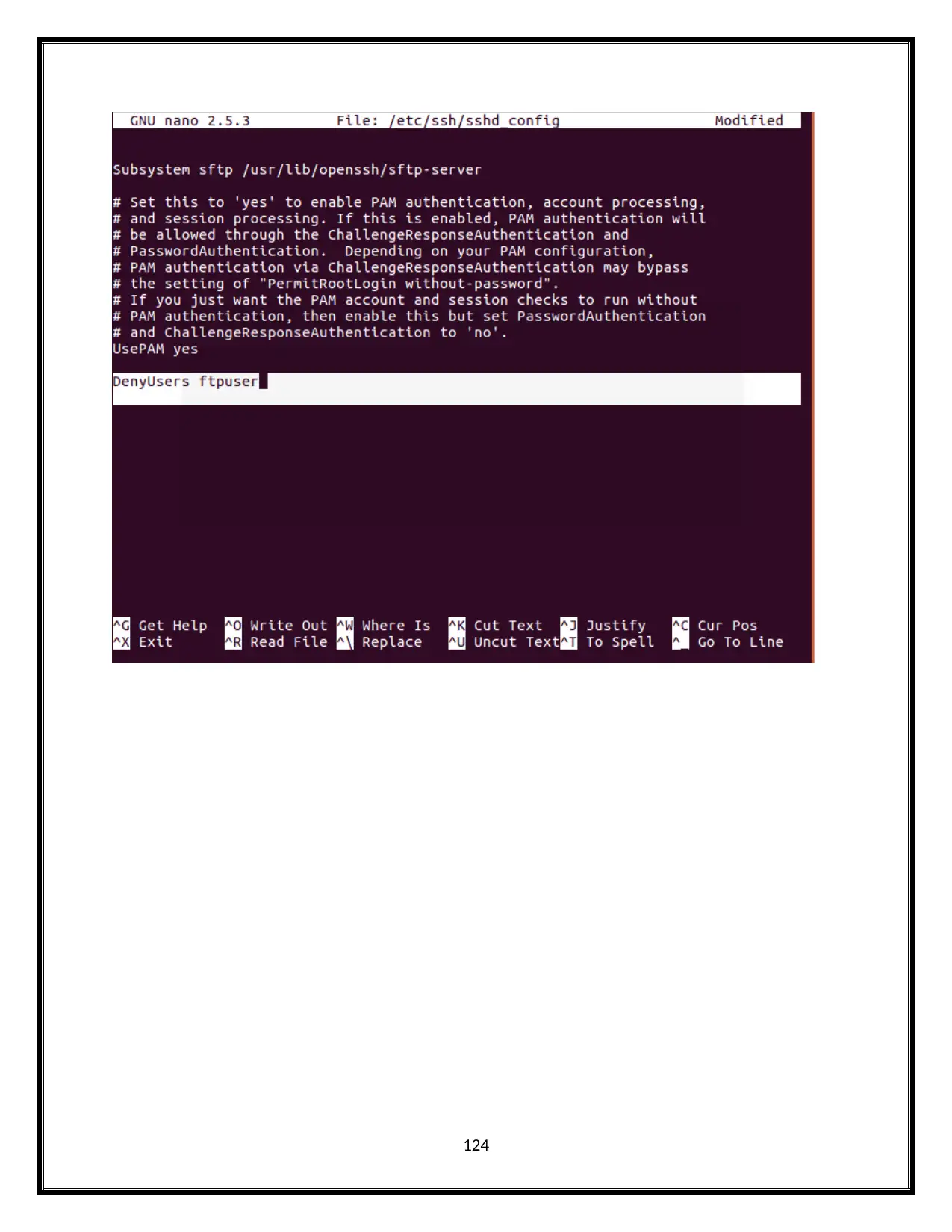
124
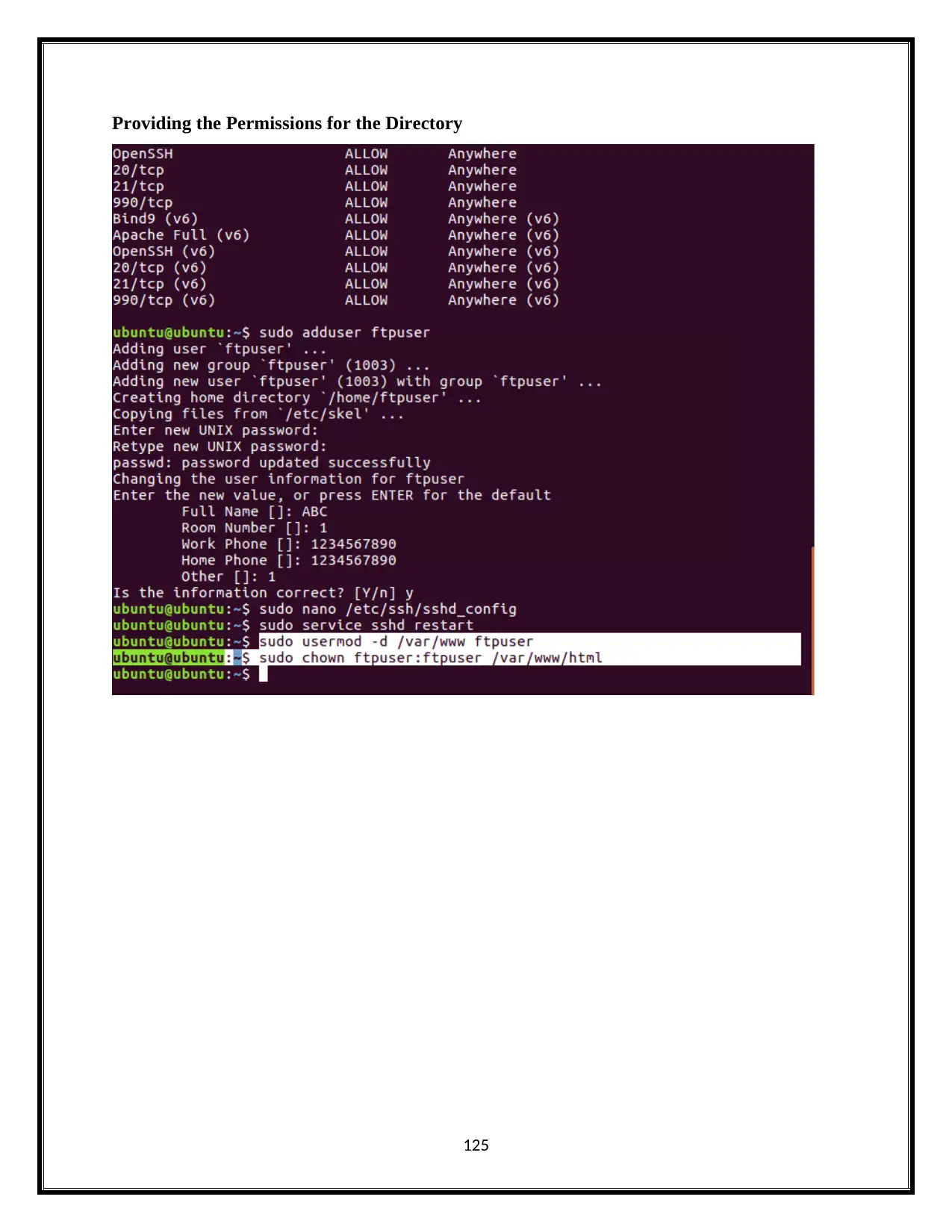
Providing the Permissions for the Directory
125
125
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Configuring vsftpd
126
126

127

128
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

129

130

131
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Testing FTP
Part: 4
Creating SSL certificate
The SSL certificate is used to secure the fundamental part and to authenticate the
webpage’s IP address. Moreover, the benefits of the web data’s unsigned certificate can be used
for the IIS server’s simpler past rendition. Encryption empowers the declaration to the traffic and
sends it to the IIS site, from data prevention and data sensitive assessment. It is used for the
client’s cryptography for opening the key which could be used to safely build the relationship.
The general population key of the scrambled could only depend on unscrambled with the private
key and it must be the other way around in the data server design.
Create SSL certificate with the help of the following steps.
Initially, on the server the SSL must be enabled.
132
Part: 4
Creating SSL certificate
The SSL certificate is used to secure the fundamental part and to authenticate the
webpage’s IP address. Moreover, the benefits of the web data’s unsigned certificate can be used
for the IIS server’s simpler past rendition. Encryption empowers the declaration to the traffic and
sends it to the IIS site, from data prevention and data sensitive assessment. It is used for the
client’s cryptography for opening the key which could be used to safely build the relationship.
The general population key of the scrambled could only depend on unscrambled with the private
key and it must be the other way around in the data server design.
Create SSL certificate with the help of the following steps.
Initially, on the server the SSL must be enabled.
132

133

134
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References
135
135
1 out of 137
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





