Contemporary Cyber Security Issues
VerifiedAdded on 2023/01/05
|14
|2593
|52
AI Summary
This report evaluates the contemporary cyber security issues faced by organizations and their impact on work structures. It discusses ransomware attacks, specifically the WannaCry ransomware attack, and provides information on when the attack occurred, its outcome, and the security actions taken by organizations. The report also highlights the impact of the attack and the security breaches that occurred.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CONTEMPORARY CYBER SECURITY ISSUSES
CONTEMPORARY CYBER SECURITY ISSUSES
Name of the Student
Name of the University
Author note
CONTEMPORARY CYBER SECURITY ISSUSES
Name of the Student
Name of the University
Author note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CONTEMPORARY CYBER SECURITY ISSUSES
Table of Contents
Introduction: 2
Discussion: 2
Chosen Malware type- Ramsomware: 2
When did the malware attack occur and was it given a specific name? 4
Outcome of the incident: 6
The impact of the incident: 8
Security breached and the resultant consequences: 8
Security actions taken by the organizations: 9
Conclusion: 11
References: 12
Table of Contents
Introduction: 2
Discussion: 2
Chosen Malware type- Ramsomware: 2
When did the malware attack occur and was it given a specific name? 4
Outcome of the incident: 6
The impact of the incident: 8
Security breached and the resultant consequences: 8
Security actions taken by the organizations: 9
Conclusion: 11
References: 12

CONTEMPORARY CYBER SECURITY ISSUSES
Introduction:
The aim of the report is to evaluate the Contemporary cyber security issues that are
faced by the whole world and has impacted on the organizations and their work structures.
The impact of contemporary computer applications is typically seen by 5 fundamental
characteristics, such as accessibility, precision, authenticity, confidentiality and integrity, of
safe computer and information systems. The ideas usually apply to government, enterprise,
education and private individuals ' normal lives (Kharraz et al., 2015). Normally expanded
internet apps are considered–hence the name has been kept "cybersecurity." It is a complex
method to achieve and ensure a safe cyberspace and that some of the issues are based
on personal identity, confidentiality, intellectual property, critical infrastructure and
organizational sustainability.
Despite a risk of viruses and malware almost from the early days of computer
technology, hackers have been given a real chance to test their ability by exposing so many
devices in the web–by shattering websites, robbing information, or fraud (Brewer, 2016). In
fact, hackers have been able to use their computer systems to ensure their safety and sanctity.
This is what cybercrime is termed.
Discussion:
Chosen Malware type- Ramsomware:
Ransomware is a type of malware that encrypts the documents of the victim. The
assailant then requests the recipient to pay for access to information. Directions for paying a
premium for the encryption key are sent out to users. The cost in Bitcoin can vary from a few
hundred dollars to thousands.
Introduction:
The aim of the report is to evaluate the Contemporary cyber security issues that are
faced by the whole world and has impacted on the organizations and their work structures.
The impact of contemporary computer applications is typically seen by 5 fundamental
characteristics, such as accessibility, precision, authenticity, confidentiality and integrity, of
safe computer and information systems. The ideas usually apply to government, enterprise,
education and private individuals ' normal lives (Kharraz et al., 2015). Normally expanded
internet apps are considered–hence the name has been kept "cybersecurity." It is a complex
method to achieve and ensure a safe cyberspace and that some of the issues are based
on personal identity, confidentiality, intellectual property, critical infrastructure and
organizational sustainability.
Despite a risk of viruses and malware almost from the early days of computer
technology, hackers have been given a real chance to test their ability by exposing so many
devices in the web–by shattering websites, robbing information, or fraud (Brewer, 2016). In
fact, hackers have been able to use their computer systems to ensure their safety and sanctity.
This is what cybercrime is termed.
Discussion:
Chosen Malware type- Ramsomware:
Ransomware is a type of malware that encrypts the documents of the victim. The
assailant then requests the recipient to pay for access to information. Directions for paying a
premium for the encryption key are sent out to users. The cost in Bitcoin can vary from a few
hundred dollars to thousands.

CONTEMPORARY CYBER SECURITY ISSUSES
It is possible to access a laptop using several ransomware vectors. Phishing malware
— attachments that reach the victim through an email, masking as a file, is one of the most
popular delivery technologies. They can take over the laptop of the victim once they are
downloaded and opened, particularly when they have integrated-in social engineering
instruments that trick consumers to enable administrative access. Some other, more
aggressive ransomware types, such as NotPetya, use security holes to infect pcs without
tricking users (Sittig & Singh, 2016).
(Figure 1: Ransomware procedure)
Source: Brewer, 2016)
There are a few things the malware might do once it's taken over the victim's
computer, but by far the most common action is to encrypt some or all of the user's files. If
they want technical information, the Infosec Institute looks closely at how a variety of
ransomware documents are encrypted (Tuttle, 2016). But perhaps the most important thing to
understand would be that the files cannot be decrypted at the end of the process without a
math key that the attacker alone knows. The user is provided with a notification that his files
It is possible to access a laptop using several ransomware vectors. Phishing malware
— attachments that reach the victim through an email, masking as a file, is one of the most
popular delivery technologies. They can take over the laptop of the victim once they are
downloaded and opened, particularly when they have integrated-in social engineering
instruments that trick consumers to enable administrative access. Some other, more
aggressive ransomware types, such as NotPetya, use security holes to infect pcs without
tricking users (Sittig & Singh, 2016).
(Figure 1: Ransomware procedure)
Source: Brewer, 2016)
There are a few things the malware might do once it's taken over the victim's
computer, but by far the most common action is to encrypt some or all of the user's files. If
they want technical information, the Infosec Institute looks closely at how a variety of
ransomware documents are encrypted (Tuttle, 2016). But perhaps the most important thing to
understand would be that the files cannot be decrypted at the end of the process without a
math key that the attacker alone knows. The user is provided with a notification that his files
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CONTEMPORARY CYBER SECURITY ISSUSES
are obsolete now and will only be decrypted if the victim sends the attacker a non-traceable
Bitcoin payment.
When did the malware attack occur and was it given a specific name?
Security attacks of pcs seem to be endless these days, and worms, pishing attacks and
malware attacks are becoming more frequent. The various malware and viruses threaten
every system with malicious assaults. You can, however, by understanding how malware
attacks and how it extends to a system, prevent damages to a system. The word malware
includes Trojan horse viruses, worms and other system viruses (Mohurle & Patil, 2017).
Whenever you have an internet link to read your mails or to share documents on the web,
malware attacks are on your system.
Email malware infected attacks via email attachments File sharing is another way of
malware attacks, in which malware attacks through file sharing programmes. Instant
messages attack through IM attachments comparable to email attachments.
Once malware enters a system, it starts damaging the boot sector of the system, the
information files; the installed software, and even the BIOS. This corrupts your files and may
also shut down your system (Chen & Bridges, 2017). The primary issue is that the malicious
software is intended for system propagation.
are obsolete now and will only be decrypted if the victim sends the attacker a non-traceable
Bitcoin payment.
When did the malware attack occur and was it given a specific name?
Security attacks of pcs seem to be endless these days, and worms, pishing attacks and
malware attacks are becoming more frequent. The various malware and viruses threaten
every system with malicious assaults. You can, however, by understanding how malware
attacks and how it extends to a system, prevent damages to a system. The word malware
includes Trojan horse viruses, worms and other system viruses (Mohurle & Patil, 2017).
Whenever you have an internet link to read your mails or to share documents on the web,
malware attacks are on your system.
Email malware infected attacks via email attachments File sharing is another way of
malware attacks, in which malware attacks through file sharing programmes. Instant
messages attack through IM attachments comparable to email attachments.
Once malware enters a system, it starts damaging the boot sector of the system, the
information files; the installed software, and even the BIOS. This corrupts your files and may
also shut down your system (Chen & Bridges, 2017). The primary issue is that the malicious
software is intended for system propagation.

CONTEMPORARY CYBER SECURITY ISSUSES
(Figure 2: malware breakdown of WaannaCry)
(Source: Adamov & Carlsson, 2017)
Malware is not a tough job and almost every system has thousands of malware. Some
of them are the following: There are a number of ways malware can spread in a scheme:
1. Social networks: Be careful about third-party software and apps when you are
surfing the Internet. Also, you must be cautious to consent to third-party apps
to your profile when using social networking sites.
2. Pirated software: malicious codes are also used by pirated software on the
system. In the majority of instances, when you download them, software
appears valid, but it could be a large problem for your scheme (Zimba,
Simukonda & Chishimba, 2017).
3. Emails: If you read malware emails, it is always better to scan them before
downloading them. Emails are also available.
(Figure 2: malware breakdown of WaannaCry)
(Source: Adamov & Carlsson, 2017)
Malware is not a tough job and almost every system has thousands of malware. Some
of them are the following: There are a number of ways malware can spread in a scheme:
1. Social networks: Be careful about third-party software and apps when you are
surfing the Internet. Also, you must be cautious to consent to third-party apps
to your profile when using social networking sites.
2. Pirated software: malicious codes are also used by pirated software on the
system. In the majority of instances, when you download them, software
appears valid, but it could be a large problem for your scheme (Zimba,
Simukonda & Chishimba, 2017).
3. Emails: If you read malware emails, it is always better to scan them before
downloading them. Emails are also available.

CONTEMPORARY CYBER SECURITY ISSUSES
4. Removable media: USB sticks are another popular way of attacking and
spreading malware on a system. Even in computer lab systems may be
infected with malware, and the infection also occurs in your system when you
move documents from an infected system to your system with an USB stick
(Kao & Hsiao, 2018).
5. Websites: There are many websites that have malware that enter your laptop
when you visit them. There are several sites.
There are different types of the ransomware attacks happening all over the world. The
most significant type of the ransomware attack is named as the WannaCry Ransomware
attack.
Outcome of the incident:
The WannaCry Ransomware attack was a global cyber attack by WannaCry
ransomware crypto-worm in May 2017, aimed by Microsoft Windows operating system pcs
using the cryptocurrency crypto-coin encryption of information and ransom payments. It has
spread to older Windows systems through EternalBlue, the feat of the United States National
Security Agency.
4. Removable media: USB sticks are another popular way of attacking and
spreading malware on a system. Even in computer lab systems may be
infected with malware, and the infection also occurs in your system when you
move documents from an infected system to your system with an USB stick
(Kao & Hsiao, 2018).
5. Websites: There are many websites that have malware that enter your laptop
when you visit them. There are several sites.
There are different types of the ransomware attacks happening all over the world. The
most significant type of the ransomware attack is named as the WannaCry Ransomware
attack.
Outcome of the incident:
The WannaCry Ransomware attack was a global cyber attack by WannaCry
ransomware crypto-worm in May 2017, aimed by Microsoft Windows operating system pcs
using the cryptocurrency crypto-coin encryption of information and ransom payments. It has
spread to older Windows systems through EternalBlue, the feat of the United States National
Security Agency.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CONTEMPORARY CYBER SECURITY ISSUSES
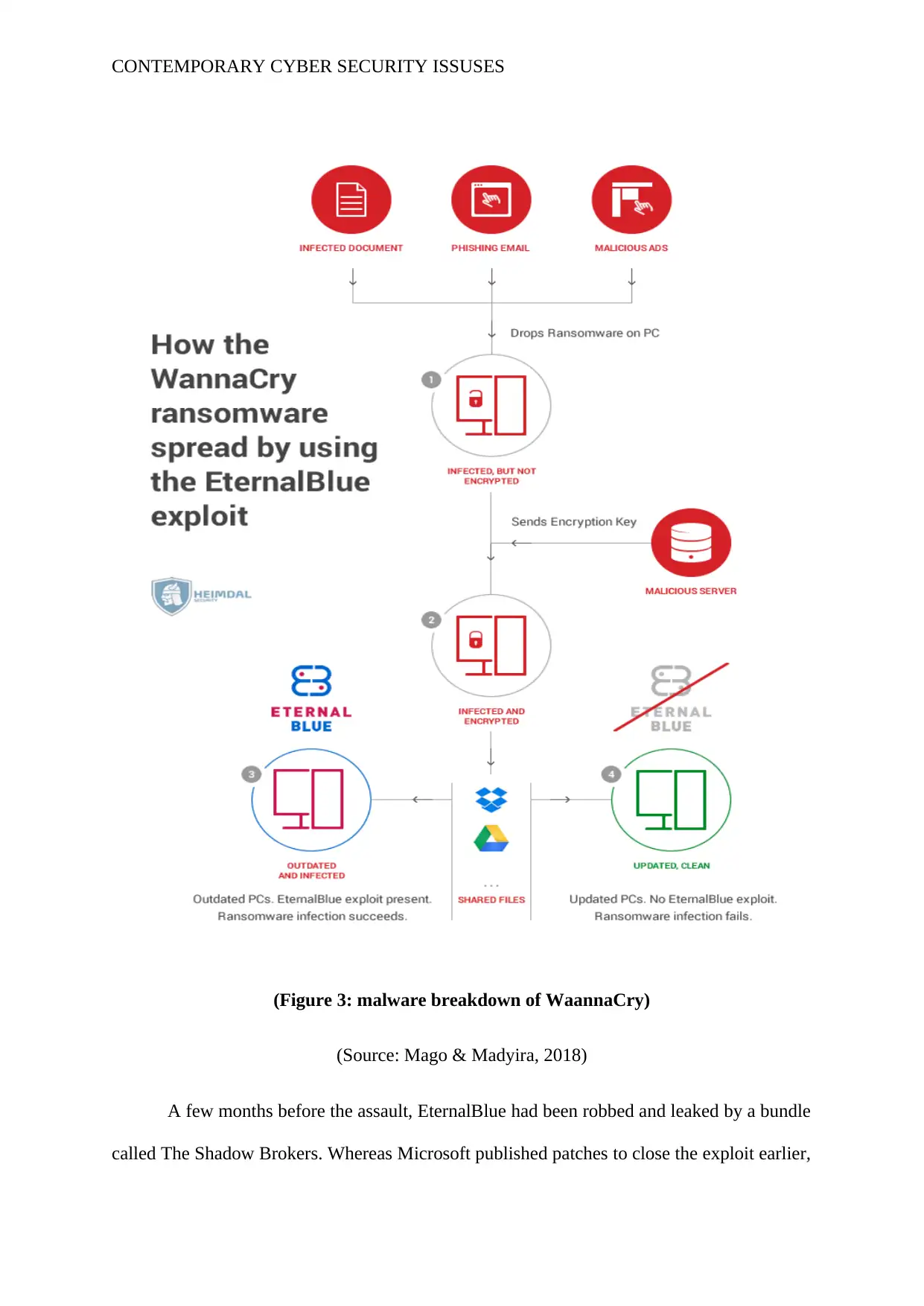
(Figure 3: malware breakdown of WaannaCry)
(Source: Mago & Madyira, 2018)
A few months before the assault, EternalBlue had been robbed and leaked by a bundle
called The Shadow Brokers. Whereas Microsoft published patches to close the exploit earlier,
(Figure 3: malware breakdown of WaannaCry)
(Source: Mago & Madyira, 2018)
A few months before the assault, EternalBlue had been robbed and leaked by a bundle
called The Shadow Brokers. Whereas Microsoft published patches to close the exploit earlier,

CONTEMPORARY CYBER SECURITY ISSUSES
much of WannaCry has been distributed by organisations, which have not used or used older,
end-of-life Windows systems (Adamov & Carlsson, 2017). WannaCry also used backdoors
on infected devices to be installed.
More than 200,000 PCs from 150 nations were estimated to have been impacted by
the attack, with total damages varying from hundreds of millions to trillions (Bossert, 2017).
Security professionals thought that somehow the attack came from North Korea or from
organizations working for the nation from the provisional assessment of the worm.
The impact of the incident:
As per the Europol, the ransomware campaign was extraordinary, estimating that
approximately 200,000 computers were infected in 150 nations. Kaspersky Lab reports that
Russia, Ukraine, India and Taiwan are the four most impacted nations.
The National Health Service hospitals in England and Scotland were among the
biggest organizations involved, and up to 70 thousand machines, including pcs, MRI
scanners, blood store fridges, theater equipment, could have been impacted (Mago &
Madyira, 2018).
Compared to other prospective assaults of the same nature, the effect of the attack has
been comparatively small and could have been far worse, had Marcus Hutchins not found a
kill switch to be constructed by its makers or aimed specifically at extremely critical
infrastructures, such as nuclear energy plants, barracks or railway systems.
Security breached and the resultant consequences:
The effect of the attack is comparatively small compared with other prospective
assaults of the same kind and could have done so far worse had Marcus Hutchins not found
that its designers had built up a kill-switch or had targeted extremely critical infrastructure
much of WannaCry has been distributed by organisations, which have not used or used older,
end-of-life Windows systems (Adamov & Carlsson, 2017). WannaCry also used backdoors
on infected devices to be installed.
More than 200,000 PCs from 150 nations were estimated to have been impacted by
the attack, with total damages varying from hundreds of millions to trillions (Bossert, 2017).
Security professionals thought that somehow the attack came from North Korea or from
organizations working for the nation from the provisional assessment of the worm.
The impact of the incident:
As per the Europol, the ransomware campaign was extraordinary, estimating that
approximately 200,000 computers were infected in 150 nations. Kaspersky Lab reports that
Russia, Ukraine, India and Taiwan are the four most impacted nations.
The National Health Service hospitals in England and Scotland were among the
biggest organizations involved, and up to 70 thousand machines, including pcs, MRI
scanners, blood store fridges, theater equipment, could have been impacted (Mago &
Madyira, 2018).
Compared to other prospective assaults of the same nature, the effect of the attack has
been comparatively small and could have been far worse, had Marcus Hutchins not found a
kill switch to be constructed by its makers or aimed specifically at extremely critical
infrastructures, such as nuclear energy plants, barracks or railway systems.
Security breached and the resultant consequences:
The effect of the attack is comparatively small compared with other prospective
assaults of the same kind and could have done so far worse had Marcus Hutchins not found
that its designers had built up a kill-switch or had targeted extremely critical infrastructure

CONTEMPORARY CYBER SECURITY ISSUSES
such as nuclear plants, dams or railways. Attacks by Ransomware encrypt existing
information, which can take time. Therefore, while encryption is detectable, some mitigation
methods depend on it. Sadly, hackers have started randomizing hard drive code and even
encrypting it to speed up the process and decrease detection.
Control to their information is essential for particular sectors. Federal organizations
like hospitals and public organizations depend on patient information and provide public
services. It is not hyperbolic to say that lives are on the track when Ransomware attacks
occur to these organisations.
Security actions taken by the organizations:
Security sensitivity is both an excellent measure of prevention and one that can
minimize the effects of a information violation. With awareness training, the employees of a
company not only discover how they try to access the systems of the organization, but learn
how to deal with a violation.
Hardening the systems of a company is vital to preventing it. Security methods of an
organization should include roll-based access control, device encryption, safe password
policies and periodic updates of every application and software of the operating system
(Jansen & Jeschke, 2018). The software and processes for security should stay current and
should be reviewed on a regular basis.
such as nuclear plants, dams or railways. Attacks by Ransomware encrypt existing
information, which can take time. Therefore, while encryption is detectable, some mitigation
methods depend on it. Sadly, hackers have started randomizing hard drive code and even
encrypting it to speed up the process and decrease detection.
Control to their information is essential for particular sectors. Federal organizations
like hospitals and public organizations depend on patient information and provide public
services. It is not hyperbolic to say that lives are on the track when Ransomware attacks
occur to these organisations.
Security actions taken by the organizations:
Security sensitivity is both an excellent measure of prevention and one that can
minimize the effects of a information violation. With awareness training, the employees of a
company not only discover how they try to access the systems of the organization, but learn
how to deal with a violation.
Hardening the systems of a company is vital to preventing it. Security methods of an
organization should include roll-based access control, device encryption, safe password
policies and periodic updates of every application and software of the operating system
(Jansen & Jeschke, 2018). The software and processes for security should stay current and
should be reviewed on a regular basis.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
CONTEMPORARY CYBER SECURITY ISSUSES
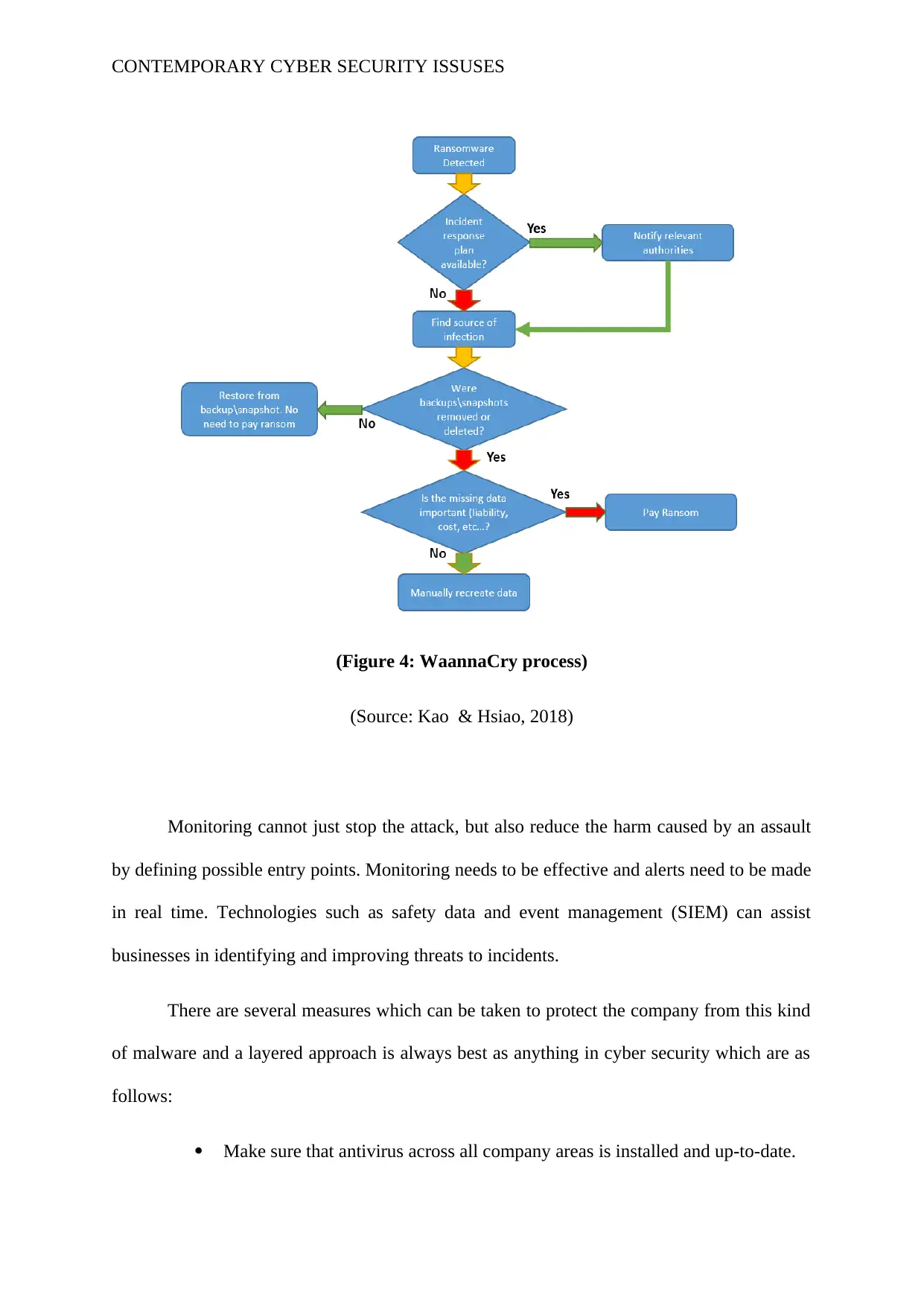
(Figure 4: WaannaCry process)
(Source: Kao & Hsiao, 2018)
Monitoring cannot just stop the attack, but also reduce the harm caused by an assault
by defining possible entry points. Monitoring needs to be effective and alerts need to be made
in real time. Technologies such as safety data and event management (SIEM) can assist
businesses in identifying and improving threats to incidents.
There are several measures which can be taken to protect the company from this kind
of malware and a layered approach is always best as anything in cyber security which are as
follows:
Make sure that antivirus across all company areas is installed and up-to-date.
(Figure 4: WaannaCry process)
(Source: Kao & Hsiao, 2018)
Monitoring cannot just stop the attack, but also reduce the harm caused by an assault
by defining possible entry points. Monitoring needs to be effective and alerts need to be made
in real time. Technologies such as safety data and event management (SIEM) can assist
businesses in identifying and improving threats to incidents.
There are several measures which can be taken to protect the company from this kind
of malware and a layered approach is always best as anything in cyber security which are as
follows:
Make sure that antivirus across all company areas is installed and up-to-date.

CONTEMPORARY CYBER SECURITY ISSUSES
Create safety sensitization campaigns that emphasize the prevention of email
connections and attachments.
Data backup. There are plenty of choices here, from supporting cloud-based
provider to local storage systems or even network-based drives. The external
storage device is imperative to remove when a backup has been taken, and it
will be impossible for Ransomware to touch the backup if the computer is
infected.
GPO limitation is not only an simple and inexpensive way to limit
ransomware but also malware from its installation in particular.
Patching frequently used software from third parties such as Java, Flash and
Adobe is certainly an obstacle to the success of many of these kinds of
assaults.
Restrict endpoint administrative rights.
Conclusion:
It can be concluded by the report that the new issues are constantly emerging in the
area of cyber security. One such difficulty is Ransomware. Even companies using perfect
cybersecurity practices can not deter a ransomware attack. Businesses would therefore be
ready to evaluate whether a ransomware attack is a information violation. In the event of a
rankings-related data breach, it can reduce response time and enable companies to comply
with all relevant legislation.
Create safety sensitization campaigns that emphasize the prevention of email
connections and attachments.
Data backup. There are plenty of choices here, from supporting cloud-based
provider to local storage systems or even network-based drives. The external
storage device is imperative to remove when a backup has been taken, and it
will be impossible for Ransomware to touch the backup if the computer is
infected.
GPO limitation is not only an simple and inexpensive way to limit
ransomware but also malware from its installation in particular.
Patching frequently used software from third parties such as Java, Flash and
Adobe is certainly an obstacle to the success of many of these kinds of
assaults.
Restrict endpoint administrative rights.
Conclusion:
It can be concluded by the report that the new issues are constantly emerging in the
area of cyber security. One such difficulty is Ransomware. Even companies using perfect
cybersecurity practices can not deter a ransomware attack. Businesses would therefore be
ready to evaluate whether a ransomware attack is a information violation. In the event of a
rankings-related data breach, it can reduce response time and enable companies to comply
with all relevant legislation.

CONTEMPORARY CYBER SECURITY ISSUSES
References:
Adamov, A., & Carlsson, A. (2017, September). The state of ransomware. Trends and
mitigation techniques. In 2017 IEEE East-West Design & Test Symposium
(EWDTS) (pp. 1-8). IEEE.
Bossert, T. P. (2017). It’s official: North Korea is behind WannaCry. The Wall Street
Journal.
Brewer, R. (2016). Ransomware attacks: detection, prevention and cure. Network
Security, 2016(9), 5-9.
Chen, Q., & Bridges, R. A. (2017, December). Automated behavioral analysis of malware: A
case study of wannacry ransomware. In 2017 16th IEEE International Conference on
Machine Learning and Applications (ICMLA) (pp. 454-460). IEEE.
Jansen, C., & Jeschke, S. (2018). Mitigating risks of digitalization through managed
industrial security services. AI & SOCIETY, 33(2), 163-173.
Kao, D. Y., & Hsiao, S. C. (2018, February). The dynamic analysis of WannaCry
ransomware. In 2018 20th International Conference on Advanced Communication
Technology (ICACT) (pp. 159-166). IEEE.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., & Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransomware attacks. In International
Conference on Detection of Intrusions and Malware, and Vulnerability
Assessment (pp. 3-24). Springer, Cham.
Mago, M., & Madyira, F. F. (2018). Ransomware Software: Case of WannaCry. Engineering
and Science, 3(1), 258-261.
References:
Adamov, A., & Carlsson, A. (2017, September). The state of ransomware. Trends and
mitigation techniques. In 2017 IEEE East-West Design & Test Symposium
(EWDTS) (pp. 1-8). IEEE.
Bossert, T. P. (2017). It’s official: North Korea is behind WannaCry. The Wall Street
Journal.
Brewer, R. (2016). Ransomware attacks: detection, prevention and cure. Network
Security, 2016(9), 5-9.
Chen, Q., & Bridges, R. A. (2017, December). Automated behavioral analysis of malware: A
case study of wannacry ransomware. In 2017 16th IEEE International Conference on
Machine Learning and Applications (ICMLA) (pp. 454-460). IEEE.
Jansen, C., & Jeschke, S. (2018). Mitigating risks of digitalization through managed
industrial security services. AI & SOCIETY, 33(2), 163-173.
Kao, D. Y., & Hsiao, S. C. (2018, February). The dynamic analysis of WannaCry
ransomware. In 2018 20th International Conference on Advanced Communication
Technology (ICACT) (pp. 159-166). IEEE.
Kharraz, A., Robertson, W., Balzarotti, D., Bilge, L., & Kirda, E. (2015, July). Cutting the
gordian knot: A look under the hood of ransomware attacks. In International
Conference on Detection of Intrusions and Malware, and Vulnerability
Assessment (pp. 3-24). Springer, Cham.
Mago, M., & Madyira, F. F. (2018). Ransomware Software: Case of WannaCry. Engineering
and Science, 3(1), 258-261.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CONTEMPORARY CYBER SECURITY ISSUSES
Mohurle, S., & Patil, M. (2017). A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
Sittig, D. F., & Singh, H. (2016). A socio-technical approach to preventing, mitigating, and
recovering from ransomware attacks. Applied clinical informatics, 7(02), 624-632.
Tuttle, H. (2016). Ransomware attacks pose growing threat. Risk Management, 63(4), 4.
Zimba, A., Simukonda, L., & Chishimba, M. (2017). Demystifying ransomware attacks:
Reverse engineering and dynamic malware analysis of wannacry for network and
information security. Zambia ICT Journal, 1(1), 35-40.
Mohurle, S., & Patil, M. (2017). A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
Sittig, D. F., & Singh, H. (2016). A socio-technical approach to preventing, mitigating, and
recovering from ransomware attacks. Applied clinical informatics, 7(02), 624-632.
Tuttle, H. (2016). Ransomware attacks pose growing threat. Risk Management, 63(4), 4.
Zimba, A., Simukonda, L., & Chishimba, M. (2017). Demystifying ransomware attacks:
Reverse engineering and dynamic malware analysis of wannacry for network and
information security. Zambia ICT Journal, 1(1), 35-40.
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





