ICTICT418: Copyright, Ethics, and Privacy Compliance in ICT - ITA
VerifiedAdded on 2023/06/10
|10
|4399
|346
Homework Assignment
AI Summary
This assignment solution for ICTICT418 delves into the critical aspects of copyright, ethics, and privacy within the Information and Communications Technology (ICT) environment. It addresses key concepts such as national privacy principles, copyright legislation, and intellectual property rights, providing detailed explanations and examples. The assignment also examines the legal and regulatory landscape governing information technology, highlighting the importance of data protection and cybersecurity. Furthermore, it explores the development and implementation of organizational privacy policies, including conducting privacy audits and addressing ethical issues like defamation and conflicts of interest. The solution culminates in drafting a comprehensive privacy policy for Universal Global Services, ensuring compliance with relevant legislation and safeguarding stakeholder interests through robust codes of ethics and security measures.
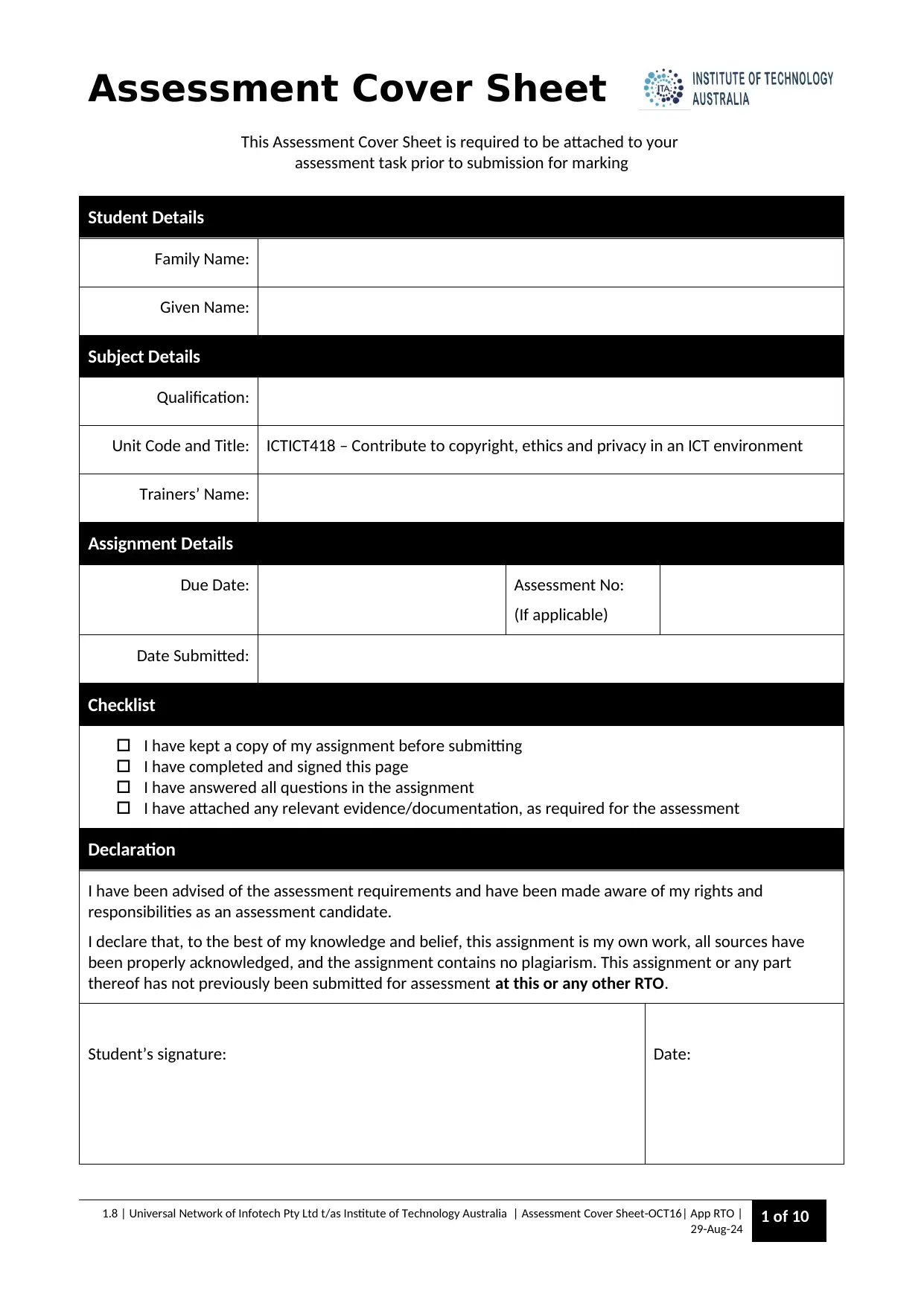
Assessment Cover Sheet
This Assessment Cover Sheet is required to be attached to your
assessment task prior to submission for marking
Student Details
Family Name:
Given Name:
Subject Details
Qualification:
Unit Code and Title: ICTICT418 – Contribute to copyright, ethics and privacy in an ICT environment
Trainers’ Name:
Assignment Details
Due Date: Assessment No:
(If applicable)
Date Submitted:
Checklist
I have kept a copy of my assignment before submitting
I have completed and signed this page
I have answered all questions in the assignment
I have attached any relevant evidence/documentation, as required for the assessment
Declaration
I have been advised of the assessment requirements and have been made aware of my rights and
responsibilities as an assessment candidate.
I declare that, to the best of my knowledge and belief, this assignment is my own work, all sources have
been properly acknowledged, and the assignment contains no plagiarism. This assignment or any part
thereof has not previously been submitted for assessment at this or any other RTO.
Student’s signature: Date:
1.8 | Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO |
29-Aug-24 1 of 10
This Assessment Cover Sheet is required to be attached to your
assessment task prior to submission for marking
Student Details
Family Name:
Given Name:
Subject Details
Qualification:
Unit Code and Title: ICTICT418 – Contribute to copyright, ethics and privacy in an ICT environment
Trainers’ Name:
Assignment Details
Due Date: Assessment No:
(If applicable)
Date Submitted:
Checklist
I have kept a copy of my assignment before submitting
I have completed and signed this page
I have answered all questions in the assignment
I have attached any relevant evidence/documentation, as required for the assessment
Declaration
I have been advised of the assessment requirements and have been made aware of my rights and
responsibilities as an assessment candidate.
I declare that, to the best of my knowledge and belief, this assignment is my own work, all sources have
been properly acknowledged, and the assignment contains no plagiarism. This assignment or any part
thereof has not previously been submitted for assessment at this or any other RTO.
Student’s signature: Date:
1.8 | Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO |
29-Aug-24 1 of 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Assessment Feedback
Result Satisfactory Not Satisfactory RPL RCC
NYC – New assessment date scheduled or FIR – Further information Required Date:
Trainers/Assessors signature: Date:
Student Comments
I have received my assessment result and am satisfied with the feedback given on this assessment
Student’s signature: Date:
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 2 of 10
Result Satisfactory Not Satisfactory RPL RCC
NYC – New assessment date scheduled or FIR – Further information Required Date:
Trainers/Assessors signature: Date:
Student Comments
I have received my assessment result and am satisfied with the feedback given on this assessment
Student’s signature: Date:
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 2 of 10

Questions:
1.1 There are 10 National Privacy Principles. Which of the privacy principles does the following
describe? What legislation and regulations deal with copyright and IP?
Ans: Following are the descriptions of the principles, such as individuals provided with general
rights to access personal information with permission. If the data is accessed without permission
then copyright claim can be made.
The law which deals with the copyright and IP is intellectual legislation. Intellectual
property law refers to maintaining the dignity of original creations of a particular individual or
organization. Intellectual property consists the literacy, inventions, artistic works, names, image or
any symbol (Pardo & Siemens, 2014). Copyright law is a legal procedure when any intellectual
property is used by others it can be applied then.
1.2 How does the legislation define copyright and intellectual property?
Ans: A copyright is a protection which is defined by the law of the countries. The individuals who
hold the copyright for a particular product can prevent others from copying his or her work (Janis,
Hovenkamp & Lemley, 2016). If someone copies the work of other without their concern then they
can be punished by the copyright law.
There are many legislation processes that can be applied on the intellectual property.
Intellectual property rights are one kind of rights which is given to an individual over their minds
creation. The creator mainly given the right to protect his or her creation from being modified or
copied.
1.3
Are there any laws or regulations specifically dealing with Information Technology? (Write a
report, no more than 3 or 4 paragraphs)
Ans: There are many laws and regulations that are associated with information technology.
Information technology laws deals with the online activities through connecting devices. The main
reason that these laws are imposed on the information security is the incidences of the recent
time that has lead to an increase in cybercrime.
The laws ensure the regulatory compliance of the information technology. There are
several lawyers who deal with these kinds of cases (Lloyd, 2017). Many of these cases come under
the process of IT laws like the copy of a licence product, copy of data, or any kind of cyber-crime
that affect the human and exploit their data.
Protecting the dignity of electronic or digital signature also comes under the information
technology law where data are stored in the network. The business organization has to make sure
that the data is safe. This is because the data is sensitive and it contains digital signature, digital
identity, and confidential information about an individual or a company. If the data breached then
the company can take legal action as per the countries cyber law. Therefore, it can be noticed
easily that there are strict laws and legislations implemented to protect the dignity of data in
information technology.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 3 of 10
1.1 There are 10 National Privacy Principles. Which of the privacy principles does the following
describe? What legislation and regulations deal with copyright and IP?
Ans: Following are the descriptions of the principles, such as individuals provided with general
rights to access personal information with permission. If the data is accessed without permission
then copyright claim can be made.
The law which deals with the copyright and IP is intellectual legislation. Intellectual
property law refers to maintaining the dignity of original creations of a particular individual or
organization. Intellectual property consists the literacy, inventions, artistic works, names, image or
any symbol (Pardo & Siemens, 2014). Copyright law is a legal procedure when any intellectual
property is used by others it can be applied then.
1.2 How does the legislation define copyright and intellectual property?
Ans: A copyright is a protection which is defined by the law of the countries. The individuals who
hold the copyright for a particular product can prevent others from copying his or her work (Janis,
Hovenkamp & Lemley, 2016). If someone copies the work of other without their concern then they
can be punished by the copyright law.
There are many legislation processes that can be applied on the intellectual property.
Intellectual property rights are one kind of rights which is given to an individual over their minds
creation. The creator mainly given the right to protect his or her creation from being modified or
copied.
1.3
Are there any laws or regulations specifically dealing with Information Technology? (Write a
report, no more than 3 or 4 paragraphs)
Ans: There are many laws and regulations that are associated with information technology.
Information technology laws deals with the online activities through connecting devices. The main
reason that these laws are imposed on the information security is the incidences of the recent
time that has lead to an increase in cybercrime.
The laws ensure the regulatory compliance of the information technology. There are
several lawyers who deal with these kinds of cases (Lloyd, 2017). Many of these cases come under
the process of IT laws like the copy of a licence product, copy of data, or any kind of cyber-crime
that affect the human and exploit their data.
Protecting the dignity of electronic or digital signature also comes under the information
technology law where data are stored in the network. The business organization has to make sure
that the data is safe. This is because the data is sensitive and it contains digital signature, digital
identity, and confidential information about an individual or a company. If the data breached then
the company can take legal action as per the countries cyber law. Therefore, it can be noticed
easily that there are strict laws and legislations implemented to protect the dignity of data in
information technology.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 3 of 10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2.1 What form should the comparison between an organisation’s policies and procedures with
privacy legislation take? A privacy audit is? All organisations are required to do a privacy
audit. The three steps in conducting an audit are? (Choose 3) Find out about the Copyright
Policy at Universal Global Services. • What areas does it cover? Match with current industry
standards.
Ans: The companies have their own policies for the privacy legislation. The privacy policy covers
several things in the company. It collects the information and make sure who can access the
information and for which purpose.
Privacy audit is a procedure which assesses the privacy protection of the organization
against the regulatory requirements.
The three steps that are chosen from the list of auditing steps are requesting of document,
prepare a plan to audit, conducting the field work.
There are nothing specific as the copyright policy at global services. Different countries
have their own rules and regulation of copyright (Greenaway, Chan &Crossler, 2015). The copyright
policy covers each of the intellectual properly like the inventions, songs, movies technology,
software or any creation of minds. As these are the [product that are running the current
standards of the industry.
2.2
Discuss whether all personnel should be familiar with new policies and procedures. Because we
are dealing with privacy issues, what means should new policies and procedures be communicated
to personnel?
Ans: It is necessary to familiar all the personnel with the all new policies and procedures. As in the
recent time the amount of privacy issues are increased and it affects the personnel. So if the
personnel in the organization are aware of the new rules and regulations they can be sure of the
issues that are going to affect the organization (Peltier, 2016). The personnel will be able to take the
pre measurement from having the issue or if the issue occurs then they can able to take certain
action as per the information technology rules and regulation. So it is necessary to communicate
with the personnel so that they will be aware the rules and the regulation that is proposed for the
information technology.
3.1
What is the next step after reviewing legislation against the organization’s privacy policies and
legislation and finding gaps and/or non-compliances? What is the most common way of
implementing a privacy policy on the internet? How does P3P work to control the use of personal
information on websites?
Ans: The next step is to take action by the rules and the regulation against the gaps and the non-
compliance.
The most common way to implement privacy policy on the internet is by securing the
device properly by locking the hardware and installing updated security measurement for data
security.
P3P is a protocol that is obsolete and allows the websites to use the data of the user who
browse the web browsers. It gathers the information about the users to see whether the usage is
authorised or not (Abdmouleh, Alammari&Gastli, 2015). It tracks the cookies of the user who is
browsing the websites. Some users see this act as an invasion and turn off the ‘http’ cookies or
they use proxy server to stop this P3P works.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 4 of 10
privacy legislation take? A privacy audit is? All organisations are required to do a privacy
audit. The three steps in conducting an audit are? (Choose 3) Find out about the Copyright
Policy at Universal Global Services. • What areas does it cover? Match with current industry
standards.
Ans: The companies have their own policies for the privacy legislation. The privacy policy covers
several things in the company. It collects the information and make sure who can access the
information and for which purpose.
Privacy audit is a procedure which assesses the privacy protection of the organization
against the regulatory requirements.
The three steps that are chosen from the list of auditing steps are requesting of document,
prepare a plan to audit, conducting the field work.
There are nothing specific as the copyright policy at global services. Different countries
have their own rules and regulation of copyright (Greenaway, Chan &Crossler, 2015). The copyright
policy covers each of the intellectual properly like the inventions, songs, movies technology,
software or any creation of minds. As these are the [product that are running the current
standards of the industry.
2.2
Discuss whether all personnel should be familiar with new policies and procedures. Because we
are dealing with privacy issues, what means should new policies and procedures be communicated
to personnel?
Ans: It is necessary to familiar all the personnel with the all new policies and procedures. As in the
recent time the amount of privacy issues are increased and it affects the personnel. So if the
personnel in the organization are aware of the new rules and regulations they can be sure of the
issues that are going to affect the organization (Peltier, 2016). The personnel will be able to take the
pre measurement from having the issue or if the issue occurs then they can able to take certain
action as per the information technology rules and regulation. So it is necessary to communicate
with the personnel so that they will be aware the rules and the regulation that is proposed for the
information technology.
3.1
What is the next step after reviewing legislation against the organization’s privacy policies and
legislation and finding gaps and/or non-compliances? What is the most common way of
implementing a privacy policy on the internet? How does P3P work to control the use of personal
information on websites?
Ans: The next step is to take action by the rules and the regulation against the gaps and the non-
compliance.
The most common way to implement privacy policy on the internet is by securing the
device properly by locking the hardware and installing updated security measurement for data
security.
P3P is a protocol that is obsolete and allows the websites to use the data of the user who
browse the web browsers. It gathers the information about the users to see whether the usage is
authorised or not (Abdmouleh, Alammari&Gastli, 2015). It tracks the cookies of the user who is
browsing the websites. Some users see this act as an invasion and turn off the ‘http’ cookies or
they use proxy server to stop this P3P works.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 4 of 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3.2
What are the objectives of a privacy audit? Look at the following table and list the discrepancies
between privacy legislation and organisational practice. List the persons who would be
appropriate to submit the audit report to. Why should privacy audit reports not be released to the
general public? Provide your reasons as to your obligations with regards to privacy policy and act
(Duncan & Whittington, 2016).
Ans: The main objective of privacy audit is to identify the privacy protection of the organization. It
assesses the policies that are related with the privacy in the organization.
The audit report is submitted to the privacy policy officers of the company and the upper
management people.
The audit report must not release to the general public because it is not their zone of
concern it will only take by the management for analysing the report and take action accordingly.
3.3
Using the internet research some ethical issues that are current e.g. defamation, acting in the
interests of the client. Incorporate these into a draft code of ethics for Universal Global Services.
Ans: One of the main ethical issues in the current scenario is the conflict of interest (Zhao, Qiang &
Zou, 2018). Universal Global services can have these ethical issues and when these kinds of conflict
of interest are regarded as legal action. In this area most of the lawyers are facing problem while
practicing. It is required to balance the requirement of the clients without making any interest
conflict.
3.4
Write a draft policy which addresses integrity, confidentiality and security as per client's
expectations.
Ans: Integrity, confidentiality and security comes under the code of ethics. The integrity of the
client data must be ensured by the organization so that the data stay safe in the company (Colesky,
Hoepman & Hillen, 2016). The client must expect their data integrity from the company.
The client expects that their data and information are kept confidential by the
organization. It is the duty of the organization to keep data confidential so that it cannot be used
by unauthorized users.
The security policy is maintained by the company so that the client expectation can be met
with secure measurement. While the digital identity and the information are being secured by the
company so that the informations of the client will not be violated by the unauthorised users.
3.5
Write procedure to protect the interests of stakeholders/clients and code of ethics to be followed
throughout the project.
Ans: The main way by which the stakeholder’s interest can be protected is by ensuring the rights
and the needs of the stakeholders are met properly (Bock, 2016). There are several techniques by
which the stakeholder interest is met for the project. There are several code of ethics that needed
to be followed by the project associated for the stakeholder’s management. The higher authorities
must make sure that any kind of discrimination or preferential condition does not raise while
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 5 of 10
What are the objectives of a privacy audit? Look at the following table and list the discrepancies
between privacy legislation and organisational practice. List the persons who would be
appropriate to submit the audit report to. Why should privacy audit reports not be released to the
general public? Provide your reasons as to your obligations with regards to privacy policy and act
(Duncan & Whittington, 2016).
Ans: The main objective of privacy audit is to identify the privacy protection of the organization. It
assesses the policies that are related with the privacy in the organization.
The audit report is submitted to the privacy policy officers of the company and the upper
management people.
The audit report must not release to the general public because it is not their zone of
concern it will only take by the management for analysing the report and take action accordingly.
3.3
Using the internet research some ethical issues that are current e.g. defamation, acting in the
interests of the client. Incorporate these into a draft code of ethics for Universal Global Services.
Ans: One of the main ethical issues in the current scenario is the conflict of interest (Zhao, Qiang &
Zou, 2018). Universal Global services can have these ethical issues and when these kinds of conflict
of interest are regarded as legal action. In this area most of the lawyers are facing problem while
practicing. It is required to balance the requirement of the clients without making any interest
conflict.
3.4
Write a draft policy which addresses integrity, confidentiality and security as per client's
expectations.
Ans: Integrity, confidentiality and security comes under the code of ethics. The integrity of the
client data must be ensured by the organization so that the data stay safe in the company (Colesky,
Hoepman & Hillen, 2016). The client must expect their data integrity from the company.
The client expects that their data and information are kept confidential by the
organization. It is the duty of the organization to keep data confidential so that it cannot be used
by unauthorized users.
The security policy is maintained by the company so that the client expectation can be met
with secure measurement. While the digital identity and the information are being secured by the
company so that the informations of the client will not be violated by the unauthorised users.
3.5
Write procedure to protect the interests of stakeholders/clients and code of ethics to be followed
throughout the project.
Ans: The main way by which the stakeholder’s interest can be protected is by ensuring the rights
and the needs of the stakeholders are met properly (Bock, 2016). There are several techniques by
which the stakeholder interest is met for the project. There are several code of ethics that needed
to be followed by the project associated for the stakeholder’s management. The higher authorities
must make sure that any kind of discrimination or preferential condition does not raise while
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 5 of 10

project is being developed. The commitment made for the project needs to be fulfilled so that the
stakeholder will be satisfied. Particular rules and regulations needed to be made so that the
stakeholder rights will not be violated. The relationship with the stakeholders needed to be
maintained properly in order to maintain he interest and it had to be done with regarding the
code of ethics. The mechanism that is made for protecting the interest of the stakeholder must be
disclosed fully.
4.1
Write a draft privacy policy for Universal Global Services which addresses any deficiencies in the
current policy and includes relevant points from the legislation.
Ans. There are several rules and regulations to protect the intellectual properties of the individuals
or the organizations. If the laws are violated then according to the law actions will be take. The
policies have security but there are some limitations that are associated with the policies (Henze,
Hermerschmidt & Kerpen, 2016). The providers those provides the copyright puts several powerful
and critical rights over their individual work. The deficiencies in the privacy policy is mainly
depends on the several aspects like the failure in the market, after a time period the policies are
expired then the policies will not be applicable. There are many things on which the policies will
not be applicable. The copyright does not provide any policies for the too short or too big works.
In a project the project title, phrases and the sentences cannot be provided with copyright.
A draft needed to be make so that it can be ensured that every project will have the ability
to implement copyright on the project works. A proper plan is needed to be made so that the
deficiencies with the policies will be corrected and new policies will be provided for the privacy
policy.
4.2
You are required to develop web pages to capture customer or stakeholders details for the
development of a mailing list. This page should mail current policies and procedures to mailing list
on release of new or revised policies.
4.3
You are required to develop an action plan based on your recommendations. The action plan
needs to list the tasks that need to be implemented. You need to consider: costs, legal and HR
issues, internal and external operating environment etc. Obtain feedback from client by mailing
updates to list available on website mailing list.
4.4
Write a procedure which addresses integrity, confidentiality and security as per client's
expectations.
Ans: For every project it is necessary to maintain three goals. These are to protect the integrity,
confidentiality and security of the data. By achieving these three goals the project will be able to
meet the expectation of the client and because of that more client will come to the project.
Integrity model is made to protect the integrity of the client data as per expectations
(Schmidt, 2016). It can be provided by securing the system where the data is stored. The integrity
model has several objectives. The integrity models prevents the users that are unauthorized from
accessing or modifying the programmes or the data.
Confidentiality provides to secure the information of the user as per their expectation. The
confidentiality policy mainly address that how the data can be protect.
Security is the main aspect that is required by the client to the developers of the project.
As per the expectations of the client security must be provided to their data and information.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 6 of 10
stakeholder will be satisfied. Particular rules and regulations needed to be made so that the
stakeholder rights will not be violated. The relationship with the stakeholders needed to be
maintained properly in order to maintain he interest and it had to be done with regarding the
code of ethics. The mechanism that is made for protecting the interest of the stakeholder must be
disclosed fully.
4.1
Write a draft privacy policy for Universal Global Services which addresses any deficiencies in the
current policy and includes relevant points from the legislation.
Ans. There are several rules and regulations to protect the intellectual properties of the individuals
or the organizations. If the laws are violated then according to the law actions will be take. The
policies have security but there are some limitations that are associated with the policies (Henze,
Hermerschmidt & Kerpen, 2016). The providers those provides the copyright puts several powerful
and critical rights over their individual work. The deficiencies in the privacy policy is mainly
depends on the several aspects like the failure in the market, after a time period the policies are
expired then the policies will not be applicable. There are many things on which the policies will
not be applicable. The copyright does not provide any policies for the too short or too big works.
In a project the project title, phrases and the sentences cannot be provided with copyright.
A draft needed to be make so that it can be ensured that every project will have the ability
to implement copyright on the project works. A proper plan is needed to be made so that the
deficiencies with the policies will be corrected and new policies will be provided for the privacy
policy.
4.2
You are required to develop web pages to capture customer or stakeholders details for the
development of a mailing list. This page should mail current policies and procedures to mailing list
on release of new or revised policies.
4.3
You are required to develop an action plan based on your recommendations. The action plan
needs to list the tasks that need to be implemented. You need to consider: costs, legal and HR
issues, internal and external operating environment etc. Obtain feedback from client by mailing
updates to list available on website mailing list.
4.4
Write a procedure which addresses integrity, confidentiality and security as per client's
expectations.
Ans: For every project it is necessary to maintain three goals. These are to protect the integrity,
confidentiality and security of the data. By achieving these three goals the project will be able to
meet the expectation of the client and because of that more client will come to the project.
Integrity model is made to protect the integrity of the client data as per expectations
(Schmidt, 2016). It can be provided by securing the system where the data is stored. The integrity
model has several objectives. The integrity models prevents the users that are unauthorized from
accessing or modifying the programmes or the data.
Confidentiality provides to secure the information of the user as per their expectation. The
confidentiality policy mainly address that how the data can be protect.
Security is the main aspect that is required by the client to the developers of the project.
As per the expectations of the client security must be provided to their data and information.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 6 of 10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

5.1
Identify where a current policies and procedures fall short of requirements of the act. You must
change the policies and procedures of the organisation so that they do conform to the legislation.
Ans: The current policies and the procedures fall short in many cases like the policies do not have
fixed zone where it can be applied (Satrjeenpong, Tapuria & Curcin, 2018). It is necessary to develop a
policy plan on which it will be assessed that the policies and the procedure implementation list.
Some changes are needed to be making in the policies so that they can be implemented in every
part and the expiration date also needs to be extended and a renewal system also needs to be
developed.
5.2
Develop feedback mechanism to address integrity, confidentiality and security as per client's
expectations.
5.3
Identify where a current work practices fall short of requirements of the privacy policy. You must
change the policies and procedures of the organisation work practices so that they do conform to
the legislation.
Ans. same as the question no 5.1
6.1
Using the internet research some ethical issues that are current e.g. defamation, acting in the
interests of the client. Incorporate these into a draft code of ethics for Universal Global Services.
Ans: In the ethics of the Universal Global Service, it is necessary to assess the ethical issue that are
raised. These ethical issues need to be mitigated for the project to work properly (Dang, Tran &
Nguyen, 2015). Maintaining the fame of the people is necessary. However, to get success it is not
necessary to defame an organization or the individuals. This behaviour is beyond ethics.
It is necessary for the project associates to act as per the client’s interest. It is necessary for
the project manager to maintain the interest of the client rather than putting their own interest. If
the project manager does not act as per the interest of the client then the work will be beyond
code of the ethics. To maintain a project properly, it is required to maintain the code of ethics.
6.2
You are required to distribute new ethics code to stakeholders mailing list on website database on
each update and develop feedback form to send as a link to client.
6.3
Write procedure to address ethical works requirement in organisation and develop feedback form
for internal assessment.
Ans: Thinking about having good values for the organization, it is also necessary to work as per
ethics.
If the organization has a good reputation for their service, they must also follow the ethics to do
the work (Henze, Hermerschmidt & Kerpen, 2016). There are several methods to identify the ethics in
work place for different organizations. Difference organizations have varied requirements of the
work and it is necessary for the staffs of the organization to work as per the ethics and
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 7 of 10
Identify where a current policies and procedures fall short of requirements of the act. You must
change the policies and procedures of the organisation so that they do conform to the legislation.
Ans: The current policies and the procedures fall short in many cases like the policies do not have
fixed zone where it can be applied (Satrjeenpong, Tapuria & Curcin, 2018). It is necessary to develop a
policy plan on which it will be assessed that the policies and the procedure implementation list.
Some changes are needed to be making in the policies so that they can be implemented in every
part and the expiration date also needs to be extended and a renewal system also needs to be
developed.
5.2
Develop feedback mechanism to address integrity, confidentiality and security as per client's
expectations.
5.3
Identify where a current work practices fall short of requirements of the privacy policy. You must
change the policies and procedures of the organisation work practices so that they do conform to
the legislation.
Ans. same as the question no 5.1
6.1
Using the internet research some ethical issues that are current e.g. defamation, acting in the
interests of the client. Incorporate these into a draft code of ethics for Universal Global Services.
Ans: In the ethics of the Universal Global Service, it is necessary to assess the ethical issue that are
raised. These ethical issues need to be mitigated for the project to work properly (Dang, Tran &
Nguyen, 2015). Maintaining the fame of the people is necessary. However, to get success it is not
necessary to defame an organization or the individuals. This behaviour is beyond ethics.
It is necessary for the project associates to act as per the client’s interest. It is necessary for
the project manager to maintain the interest of the client rather than putting their own interest. If
the project manager does not act as per the interest of the client then the work will be beyond
code of the ethics. To maintain a project properly, it is required to maintain the code of ethics.
6.2
You are required to distribute new ethics code to stakeholders mailing list on website database on
each update and develop feedback form to send as a link to client.
6.3
Write procedure to address ethical works requirement in organisation and develop feedback form
for internal assessment.
Ans: Thinking about having good values for the organization, it is also necessary to work as per
ethics.
If the organization has a good reputation for their service, they must also follow the ethics to do
the work (Henze, Hermerschmidt & Kerpen, 2016). There are several methods to identify the ethics in
work place for different organizations. Difference organizations have varied requirements of the
work and it is necessary for the staffs of the organization to work as per the ethics and
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 7 of 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

requirement. Following this, the value of the company will increase and the reputation too, which
will be beneficial for the company.
6.4
Assessment is necessary in order to review ethical codes set out within an organisation. This is to
minimise risk. Provide a progressive plan of review schedule
Ans: For every organisation, it is necessary to have a code of ethics. The code of ethics will help the
company to gain benefit (Satrjeenpong, Tapuria & Curcin, 2018). Code of ethics shows the value of
integrity of the customers. It also defines ethical behaviour and helps to make better decisions for
the organization.
A proper schedule needs to be maintained by the organization for the code of ethics.
Firstly, the mission, goals and the values of the organization including the sustainability position
needs to be set. Then a language is set for the codes so that everyone can be aware of the codes
and these must be user friendly too. In the third stage expectations will be added as per the work
general conduct and the examples of unethical behaviour.
7.1
Prepare a detail schedule outlining client’s responsibilities and your responsibilities in order to
perform regular checks in accordance with the code of ethics.
Ans.
7.2
There are several aspects of ensuring that organisation has proper systems in place in terms of
grievance procedure. These may involve: Allocation of work or development opportunities, Work
place communication and interpersonal conflict, Changes in technology work processes or
locations, Occupational Health and Safety issues. Establish the confidential methods of reporting.
Ans. It is necessary for the organizations to have their own grievance system such that any kind of
issues associated with the project would be easier to address and mitigate. The staff and the user
associated with the organization need to act proactively to raise these issues (Satrjeenpong, Tapuria
& Curcin, 2018). It is necessary that the staff detail remains confidential so that the identity of the
people complaining against the system remains under wraps. In addition, to secure their identity a
confidential reporting system has to be established where the issues and the complaint will be
known by the particular employee of the organization and they will not disclose the identity.
7.3
Prepare a detail schedule outlining interview timings and follow up with stakeholders to ensure
consistent and quality services.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 8 of 10
will be beneficial for the company.
6.4
Assessment is necessary in order to review ethical codes set out within an organisation. This is to
minimise risk. Provide a progressive plan of review schedule
Ans: For every organisation, it is necessary to have a code of ethics. The code of ethics will help the
company to gain benefit (Satrjeenpong, Tapuria & Curcin, 2018). Code of ethics shows the value of
integrity of the customers. It also defines ethical behaviour and helps to make better decisions for
the organization.
A proper schedule needs to be maintained by the organization for the code of ethics.
Firstly, the mission, goals and the values of the organization including the sustainability position
needs to be set. Then a language is set for the codes so that everyone can be aware of the codes
and these must be user friendly too. In the third stage expectations will be added as per the work
general conduct and the examples of unethical behaviour.
7.1
Prepare a detail schedule outlining client’s responsibilities and your responsibilities in order to
perform regular checks in accordance with the code of ethics.
Ans.
7.2
There are several aspects of ensuring that organisation has proper systems in place in terms of
grievance procedure. These may involve: Allocation of work or development opportunities, Work
place communication and interpersonal conflict, Changes in technology work processes or
locations, Occupational Health and Safety issues. Establish the confidential methods of reporting.
Ans. It is necessary for the organizations to have their own grievance system such that any kind of
issues associated with the project would be easier to address and mitigate. The staff and the user
associated with the organization need to act proactively to raise these issues (Satrjeenpong, Tapuria
& Curcin, 2018). It is necessary that the staff detail remains confidential so that the identity of the
people complaining against the system remains under wraps. In addition, to secure their identity a
confidential reporting system has to be established where the issues and the complaint will be
known by the particular employee of the organization and they will not disclose the identity.
7.3
Prepare a detail schedule outlining interview timings and follow up with stakeholders to ensure
consistent and quality services.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 8 of 10

References
Abdmouleh, Z., Alammari, R. A., &Gastli, A. (2015). Review of policies encouraging renewable energy
integration & best practices. Renewable and Sustainable Energy Reviews, 45, 249-262.
Bock, K. (2016). Data protection certification: Decorative or effective instrument? Audit and seals as a way
to enforce privacy. In Enforcing Privacy (pp. 335-356). Springer, Cham.
Colesky, M., Hoepman, J. H., &Hillen, C. (2016, May). A critical analysis of privacy design strategies. In
Security and Privacy Workshops (SPW), 2016 IEEE (pp. 33-40). IEEE.
Dang, H. V., Tran, T. S., Nguyen, D. T., Bui, T. V., & Nguyen, D. T. (2015). Efficient privacy preserving data
audit in cloud. In Advanced Computational Methods for Knowledge Engineering (pp. 185-196).
Springer, Cham.
Duncan, R. A. K., & Whittington, M. (2016). Enhancing cloud security and privacy: the power and the
weakness of the audit trail. Cloud Computing 2016.
Greenaway, K. E., Chan, Y. E., &Crossler, R. E. (2015). Company information privacy orientation: a
conceptual framework. Information Systems Journal, 25(6), 579-606.
Henze, M., Hermerschmidt, L., Kerpen, D., Häußling, R., Rumpe, B., &Wehrle, K. (2016). A comprehensive
approach to privacy in the cloud-based Internet of Things. Future Generation Computer Systems,
56, 701-718.
Henze, M., Hermerschmidt, L., Kerpen, D., Häußling, R., Rumpe, B., &Wehrle, K. (2016). A comprehensive
approach to privacy in the cloud-based Internet of Things. Future Generation Computer Systems,
56, 701-718.
Janis, M. D., Hovenkamp, H., Lemley, M. A., Leslie, C., & Carrier, M. A. (2016). IP and antitrust: an analysis of
antitrust principles applied to intellectual property law. Wolters Kluwer Law & Business.
Lloyd, I. (2017). Information technology law. Oxford University Press.
Pardo, A., & Siemens, G. (2014). Ethical and privacy principles for learning analytics. British Journal of
Educational Technology, 45(3), 438-450.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for effective
information security management. Auerbach Publications.
Satrjeenpong, P. S., Tapuria, A., Curcin, V., &Kalra, D. (2018, June). Identifying audit trail viewer
requirements for user-focused design: a qualitative focus group study. In 2018 IEEE International
Conference on Healthcare Informatics (ICHI) (pp. 405-406). IEEE.
Satrjeenpong, P. S., Tapuria, A., Curcin, V., &Kalra, D. (2018, June). Identifying audit trail viewer
requirements for user-focused design: a qualitative focus group study. In 2018 IEEE International
Conference on Healthcare Informatics (ICHI) (pp. 405-406). IEEE.
Schmidt, D. (2016). A security and privacy audit of KakaoTalk’s end-to-end encryption.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 9 of 10
Abdmouleh, Z., Alammari, R. A., &Gastli, A. (2015). Review of policies encouraging renewable energy
integration & best practices. Renewable and Sustainable Energy Reviews, 45, 249-262.
Bock, K. (2016). Data protection certification: Decorative or effective instrument? Audit and seals as a way
to enforce privacy. In Enforcing Privacy (pp. 335-356). Springer, Cham.
Colesky, M., Hoepman, J. H., &Hillen, C. (2016, May). A critical analysis of privacy design strategies. In
Security and Privacy Workshops (SPW), 2016 IEEE (pp. 33-40). IEEE.
Dang, H. V., Tran, T. S., Nguyen, D. T., Bui, T. V., & Nguyen, D. T. (2015). Efficient privacy preserving data
audit in cloud. In Advanced Computational Methods for Knowledge Engineering (pp. 185-196).
Springer, Cham.
Duncan, R. A. K., & Whittington, M. (2016). Enhancing cloud security and privacy: the power and the
weakness of the audit trail. Cloud Computing 2016.
Greenaway, K. E., Chan, Y. E., &Crossler, R. E. (2015). Company information privacy orientation: a
conceptual framework. Information Systems Journal, 25(6), 579-606.
Henze, M., Hermerschmidt, L., Kerpen, D., Häußling, R., Rumpe, B., &Wehrle, K. (2016). A comprehensive
approach to privacy in the cloud-based Internet of Things. Future Generation Computer Systems,
56, 701-718.
Henze, M., Hermerschmidt, L., Kerpen, D., Häußling, R., Rumpe, B., &Wehrle, K. (2016). A comprehensive
approach to privacy in the cloud-based Internet of Things. Future Generation Computer Systems,
56, 701-718.
Janis, M. D., Hovenkamp, H., Lemley, M. A., Leslie, C., & Carrier, M. A. (2016). IP and antitrust: an analysis of
antitrust principles applied to intellectual property law. Wolters Kluwer Law & Business.
Lloyd, I. (2017). Information technology law. Oxford University Press.
Pardo, A., & Siemens, G. (2014). Ethical and privacy principles for learning analytics. British Journal of
Educational Technology, 45(3), 438-450.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for effective
information security management. Auerbach Publications.
Satrjeenpong, P. S., Tapuria, A., Curcin, V., &Kalra, D. (2018, June). Identifying audit trail viewer
requirements for user-focused design: a qualitative focus group study. In 2018 IEEE International
Conference on Healthcare Informatics (ICHI) (pp. 405-406). IEEE.
Satrjeenpong, P. S., Tapuria, A., Curcin, V., &Kalra, D. (2018, June). Identifying audit trail viewer
requirements for user-focused design: a qualitative focus group study. In 2018 IEEE International
Conference on Healthcare Informatics (ICHI) (pp. 405-406). IEEE.
Schmidt, D. (2016). A security and privacy audit of KakaoTalk’s end-to-end encryption.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 9 of 10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Zhao, W., Qiang, L., Zou, H., Zhang, A., & Li, J. (2018, June). Privacy-Preserving and Unforgeable Searchable
Encrypted Audit Logs for Cloud Storage. In 2018 5th IEEE International Conference on Cyber
Security and Cloud Computing (CSCloud)/2018 4th IEEE International Conference on Edge
Computing and Scalable Cloud (EdgeCom) (pp. 29-34). IEEE.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 10 of
10
Encrypted Audit Logs for Cloud Storage. In 2018 5th IEEE International Conference on Cyber
Security and Cloud Computing (CSCloud)/2018 4th IEEE International Conference on Edge
Computing and Scalable Cloud (EdgeCom) (pp. 29-34). IEEE.
1.8 |Universal Network of Infotech Pty Ltd t/as Institute of Technology Australia | Assessment Cover Sheet-OCT16| App RTO 29-
Aug-24 10 of
10
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





