Critical Reviewing AES and DES: A Comparative Analysis of Symmetric Block Ciphers
VerifiedAdded on 2024/06/04
|16
|4394
|157
AI Summary
This paper provides a critical review of two widely used symmetric block cipher algorithms: Data Encryption Standard (DES) and Advanced Encryption Standard (AES). It delves into the historical context of DES, its limitations, and the evolution of 3DES as a response to these limitations. The paper then explores the development of AES as a more robust and efficient alternative to DES. It examines the key features of AES, including its variable key length, multiple rounds of encryption, and its resistance to various cryptanalytic attacks. The paper also discusses the hardware-based implementation of AES on FPGAs, highlighting its advantages in terms of speed and efficiency. Furthermore, the paper explores the application of AES in image encryption, demonstrating its potential for securing sensitive visual data. By comparing and contrasting DES and AES, the paper provides a comprehensive understanding of the strengths and weaknesses of each algorithm, offering insights into their suitability for different security applications.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Critical Reviewing AES and DES
1
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Table of Figures................................................................................................................................3
Executive Summary.........................................................................................................................4
Introduction.....................................................................................................................................5
Literature Review.............................................................................................................................6
Methods and Solutions....................................................................................................................8
Experimental Analysis....................................................................................................................12
Future Scope..................................................................................................................................13
Conclusion......................................................................................................................................14
References.....................................................................................................................................15
Table of Figures
Figure 1 General Architecture DES Cryptographic Algorithm.........................................................7
Figure 2 Hardware based implementation of AES on FPGA............................................................8
Figure 3 Architecture of Expanded DES Algorithm........................................................................10
2
Table of Figures................................................................................................................................3
Executive Summary.........................................................................................................................4
Introduction.....................................................................................................................................5
Literature Review.............................................................................................................................6
Methods and Solutions....................................................................................................................8
Experimental Analysis....................................................................................................................12
Future Scope..................................................................................................................................13
Conclusion......................................................................................................................................14
References.....................................................................................................................................15
Table of Figures
Figure 1 General Architecture DES Cryptographic Algorithm.........................................................7
Figure 2 Hardware based implementation of AES on FPGA............................................................8
Figure 3 Architecture of Expanded DES Algorithm........................................................................10
2

Executive Summary
In this era of e-commerce and technical advancement by introducing various types of new
technologies it is important to have security as one of the key aspects that need to be
modified and improved so that the transmission of data over insecure networks can also be
made secure and private. To protect the data of customers and clients various security
measures have been adopted. Cryptography and encryption standard is one of those
measures that aim at providing security to the data by manipulating its outer look.
The various cryptographic algorithms have been reviewed in this paper. The two main
symmetric algorithms have been discussed are Data Encryption Standard and Advanced
Encryption Standard. The first block cipher algorithm introduced for data encryption is DES
but due to its incapability, new approach and techniques are developed leading to much
new development in this area. Triple DES or 3DES is an expanded version of DES that has
been developed to overcome the faults of DES. Later, a completely new algorithm called AES
has been developed to provide better and faster security and data encryption. The process
and methodologies of both these algorithms have been discussed in detail in this paper.
Along with the process involved with both of these algorithms the paper also discusses the
faults of both the algorithms and their future scope and applications. The algorithms can be
modified in a certain way to get better results and increase its application and use in the
commercial market. Critical analysis of the use of AES and DES algorithms have been
discussed to get a better overview of the concept and get a relevant contextual reference
dealing with the complete knowledge of the topic. This era needs a better opportunity to
deal with the security issue and its data encryption techniques (Gupta¸2017).
3
In this era of e-commerce and technical advancement by introducing various types of new
technologies it is important to have security as one of the key aspects that need to be
modified and improved so that the transmission of data over insecure networks can also be
made secure and private. To protect the data of customers and clients various security
measures have been adopted. Cryptography and encryption standard is one of those
measures that aim at providing security to the data by manipulating its outer look.
The various cryptographic algorithms have been reviewed in this paper. The two main
symmetric algorithms have been discussed are Data Encryption Standard and Advanced
Encryption Standard. The first block cipher algorithm introduced for data encryption is DES
but due to its incapability, new approach and techniques are developed leading to much
new development in this area. Triple DES or 3DES is an expanded version of DES that has
been developed to overcome the faults of DES. Later, a completely new algorithm called AES
has been developed to provide better and faster security and data encryption. The process
and methodologies of both these algorithms have been discussed in detail in this paper.
Along with the process involved with both of these algorithms the paper also discusses the
faults of both the algorithms and their future scope and applications. The algorithms can be
modified in a certain way to get better results and increase its application and use in the
commercial market. Critical analysis of the use of AES and DES algorithms have been
discussed to get a better overview of the concept and get a relevant contextual reference
dealing with the complete knowledge of the topic. This era needs a better opportunity to
deal with the security issue and its data encryption techniques (Gupta¸2017).
3

Introduction
Over the past years, cryptographic algorithms have been used extensively in fighting
security threats. Cryptography is the technique used to make a system secure from external
attacks. It transforms the message so that no unauthorized user can understand its meaning
and only the authorized receiver can decipher the message and get the relevant information
out of it. Secure systems are of utmost importance in recent times. Data transmission and
data storage need to be secure in all types of business. Security in systems is required from
high sensitive embedded devices to parallel computing devices for improving a system’s
overall performance. Hence, this requirement of performance enhancement has given birth
to diverse research in the field of encryption standards (Wadhwa, 2013).
One such cryptographic algorithm is Data Encryption Standard (DES) which is a block
algorithm that encrypts data in form of blocks with the help of symmetric keys such that the
same key is used for both encryption and decryption. Another cryptographic algorithm is
Advanced Encryption Standard (AES) that has been based on the symmetric key encryption
algorithm and has a huge base of applications. AES algorithm has been termed as a new
commercial algorithm that has been started to be widely used practically and commercially
in businesses and has replaced the traditional Data Encryption Standard (DES). AES has also
been known as Rijndael cipher algorithm. AES algorithm needs to be implemented as
hardware based because it is faster, secure and needs less power supply than its software-
based implementation.
The AES algorithm has been currently and widely used in the market to encrypt not only text
but also images and other forms of media. The use of Advanced Encryption Standard (AES)
has been increased with its aspect of encrypting an image. The resultant of encryption of an
image is a GIF that is not available for users to see until it has been successfully decrypted by
following a proper sequence of steps as followed during its encryption. Such innovations in
the field of data and media encryption have taken this field into a great consideration of
future scope (Gupta¸2017).
4
Over the past years, cryptographic algorithms have been used extensively in fighting
security threats. Cryptography is the technique used to make a system secure from external
attacks. It transforms the message so that no unauthorized user can understand its meaning
and only the authorized receiver can decipher the message and get the relevant information
out of it. Secure systems are of utmost importance in recent times. Data transmission and
data storage need to be secure in all types of business. Security in systems is required from
high sensitive embedded devices to parallel computing devices for improving a system’s
overall performance. Hence, this requirement of performance enhancement has given birth
to diverse research in the field of encryption standards (Wadhwa, 2013).
One such cryptographic algorithm is Data Encryption Standard (DES) which is a block
algorithm that encrypts data in form of blocks with the help of symmetric keys such that the
same key is used for both encryption and decryption. Another cryptographic algorithm is
Advanced Encryption Standard (AES) that has been based on the symmetric key encryption
algorithm and has a huge base of applications. AES algorithm has been termed as a new
commercial algorithm that has been started to be widely used practically and commercially
in businesses and has replaced the traditional Data Encryption Standard (DES). AES has also
been known as Rijndael cipher algorithm. AES algorithm needs to be implemented as
hardware based because it is faster, secure and needs less power supply than its software-
based implementation.
The AES algorithm has been currently and widely used in the market to encrypt not only text
but also images and other forms of media. The use of Advanced Encryption Standard (AES)
has been increased with its aspect of encrypting an image. The resultant of encryption of an
image is a GIF that is not available for users to see until it has been successfully decrypted by
following a proper sequence of steps as followed during its encryption. Such innovations in
the field of data and media encryption have taken this field into a great consideration of
future scope (Gupta¸2017).
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Literature Review
According to Mankotia and Sood (2015), the various symmetric key block cipher
cryptographic techniques have been reviewed. The two techniques that are important in the
context of this research paper are Data Encryption Standard (DES) and Advanced Encryption
Standard (AES). Data Encryption Standard is an encryption technique that encrypts the data
in blocks of 64 bits with the help of a 56-bit key. It is a symmetric key algorithm; hence the
same key will be used for encryption and decryption. The key is permuted to 16 48 bit keys
for 16 rounds of encryption by using a different combination of the key at each time.
Advanced Encryption Standard has been developed to overcome the incapability of DES to
make a system completely secure. AES encrypts 128-bit long data block with variable key
length and a variable number of encryption rounds depending on the length of the key.
According to Kaur (2017), Data encryption standard has been widely used technique over
years. The main components of any cryptographic algorithm are a key generation,
encryption, and decryption. The basic terms used in cryptography are plain text that
represents the messages and text that needs to be encrypted to protect it from leakage and
access by the unauthorized users, cipher text is the text that will be received once the plain
text is encrypted by using any algorithm, encryption which is a process that converts the
plain text into an unreadable format, decryption that again converts the cipher text into
plain text by converting the unreadable format into the readable format, and key which is a
certain bit block that is used with plain to encrypt it into cipher text, in case of symmetric
encryption the same key is used for decryption and in case of asymmetric encryption a
different key is used for both encryption and decryption.
According to Farooq, Aslaam(2017), Hardware-based implementation of AES are more used
for its better results than software-based implementation. Field Programmable Gate Arrays
(FPGA) is used to test hardware implementation of AES. This paper reviewed many other
implementation techniques for AES. FPGAs are used to implement many complex
applications and have seen a tremendous growth in its usage and capability over years
because it requires less time to implement. The design developed by implementing AES on
FPGA has resulted well for small embedded devices. Resource mapping plays an important
role while using FPGA as an implementation technique.
5
According to Mankotia and Sood (2015), the various symmetric key block cipher
cryptographic techniques have been reviewed. The two techniques that are important in the
context of this research paper are Data Encryption Standard (DES) and Advanced Encryption
Standard (AES). Data Encryption Standard is an encryption technique that encrypts the data
in blocks of 64 bits with the help of a 56-bit key. It is a symmetric key algorithm; hence the
same key will be used for encryption and decryption. The key is permuted to 16 48 bit keys
for 16 rounds of encryption by using a different combination of the key at each time.
Advanced Encryption Standard has been developed to overcome the incapability of DES to
make a system completely secure. AES encrypts 128-bit long data block with variable key
length and a variable number of encryption rounds depending on the length of the key.
According to Kaur (2017), Data encryption standard has been widely used technique over
years. The main components of any cryptographic algorithm are a key generation,
encryption, and decryption. The basic terms used in cryptography are plain text that
represents the messages and text that needs to be encrypted to protect it from leakage and
access by the unauthorized users, cipher text is the text that will be received once the plain
text is encrypted by using any algorithm, encryption which is a process that converts the
plain text into an unreadable format, decryption that again converts the cipher text into
plain text by converting the unreadable format into the readable format, and key which is a
certain bit block that is used with plain to encrypt it into cipher text, in case of symmetric
encryption the same key is used for decryption and in case of asymmetric encryption a
different key is used for both encryption and decryption.
According to Farooq, Aslaam(2017), Hardware-based implementation of AES are more used
for its better results than software-based implementation. Field Programmable Gate Arrays
(FPGA) is used to test hardware implementation of AES. This paper reviewed many other
implementation techniques for AES. FPGAs are used to implement many complex
applications and have seen a tremendous growth in its usage and capability over years
because it requires less time to implement. The design developed by implementing AES on
FPGA has resulted well for small embedded devices. Resource mapping plays an important
role while using FPGA as an implementation technique.
5

According to Wadhwa, Hussain, Rizvi (2013), DES has been developed in the late 70s which
needs to be improved and a better cryptographic algorithm needs to be adopted for security
purposes. In this paper, AES and DES have been compared on security and speed basis to
get the best out of both the algorithms. The developing committee of DES has been accused
of providing a backdoor in the algorithm to decipher the data and leak it to unwanted
individuals. But the blames were not legally proved as no substantial evidence of the back
door has been presented. DES has been cracked due to small key length and more
computational power required while implementing the DES.
According to Gupta and Kaushik (2017), DES is the first standard algorithm for data security
and encryption and after that, it has been replaced by Rijndael algorithm which was named
as Advanced Encryption standard. This replacement is done to tackle more complex security
threats and attacks. It has the flexible key strength that is used for better implementation of
security protocols and manipulation of plain text while DES was incapable of the frequent
and variable transformation of data. The other most important algorithm other than AES
and DES is RSA which is a symmetric algorithm that uses different keys for encryption and
decryption.
According to Cruz and Domingo (2017), a distributed key search method has broken down
the first block cipher algorithm DES. Various new methods and approaches have been
adopted to modify the current DES algorithm. One such approach is to fuse DES algorithm
with Blowfish and Genetic algorithm. Another approach was to include Hamiltonian graphs
in DES and graph automorphism cycle to generate keys for encryption. The algorithm’s
strength lies in the fact that it does not fully depend on the secret key. Another approach
that has been tested is by manipulating each bit in the process by creating different truth
tables for the manipulation work.
6
needs to be improved and a better cryptographic algorithm needs to be adopted for security
purposes. In this paper, AES and DES have been compared on security and speed basis to
get the best out of both the algorithms. The developing committee of DES has been accused
of providing a backdoor in the algorithm to decipher the data and leak it to unwanted
individuals. But the blames were not legally proved as no substantial evidence of the back
door has been presented. DES has been cracked due to small key length and more
computational power required while implementing the DES.
According to Gupta and Kaushik (2017), DES is the first standard algorithm for data security
and encryption and after that, it has been replaced by Rijndael algorithm which was named
as Advanced Encryption standard. This replacement is done to tackle more complex security
threats and attacks. It has the flexible key strength that is used for better implementation of
security protocols and manipulation of plain text while DES was incapable of the frequent
and variable transformation of data. The other most important algorithm other than AES
and DES is RSA which is a symmetric algorithm that uses different keys for encryption and
decryption.
According to Cruz and Domingo (2017), a distributed key search method has broken down
the first block cipher algorithm DES. Various new methods and approaches have been
adopted to modify the current DES algorithm. One such approach is to fuse DES algorithm
with Blowfish and Genetic algorithm. Another approach was to include Hamiltonian graphs
in DES and graph automorphism cycle to generate keys for encryption. The algorithm’s
strength lies in the fact that it does not fully depend on the secret key. Another approach
that has been tested is by manipulating each bit in the process by creating different truth
tables for the manipulation work.
6
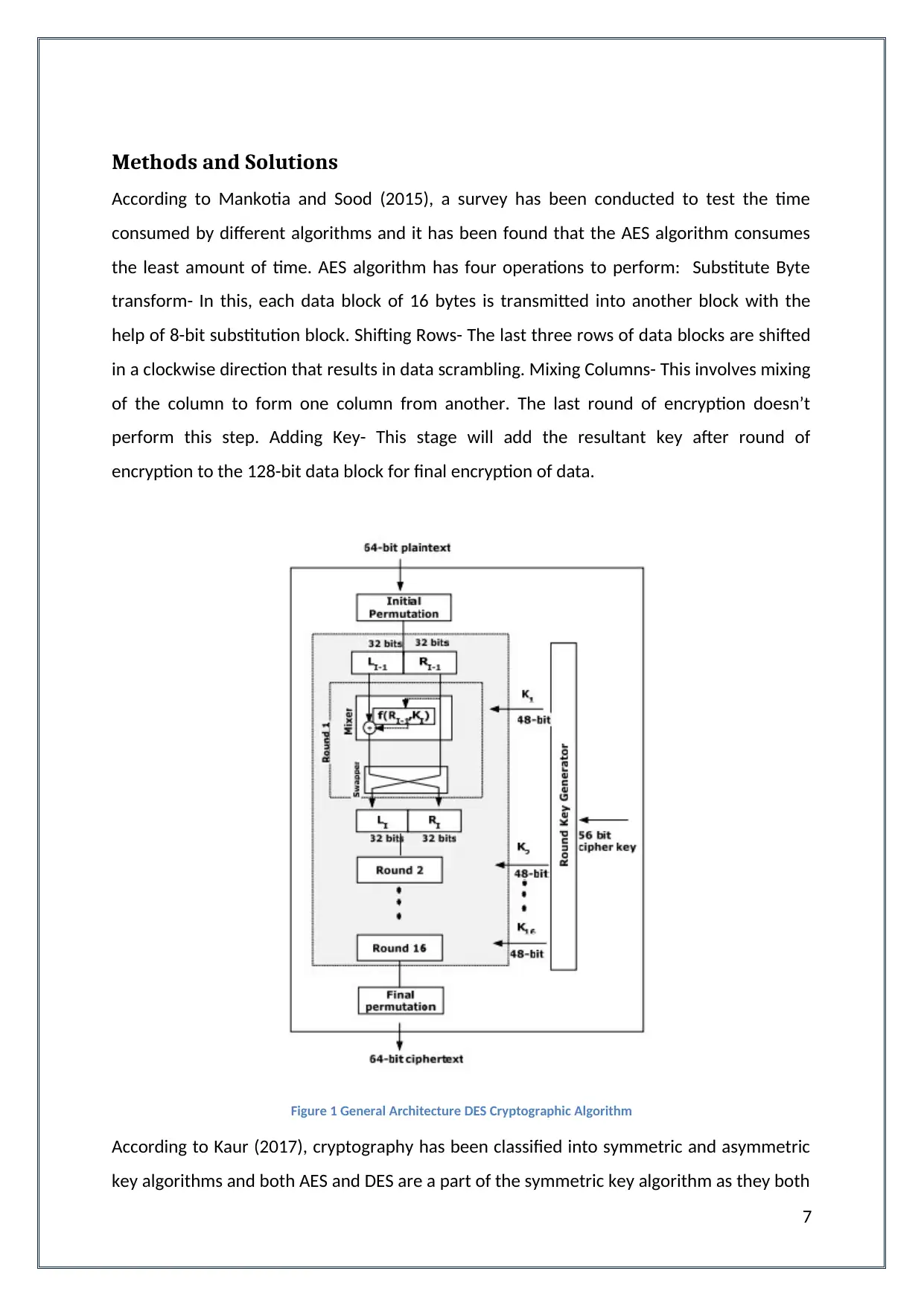
Methods and Solutions
According to Mankotia and Sood (2015), a survey has been conducted to test the time
consumed by different algorithms and it has been found that the AES algorithm consumes
the least amount of time. AES algorithm has four operations to perform: Substitute Byte
transform- In this, each data block of 16 bytes is transmitted into another block with the
help of 8-bit substitution block. Shifting Rows- The last three rows of data blocks are shifted
in a clockwise direction that results in data scrambling. Mixing Columns- This involves mixing
of the column to form one column from another. The last round of encryption doesn’t
perform this step. Adding Key- This stage will add the resultant key after round of
encryption to the 128-bit data block for final encryption of data.
Figure 1 General Architecture DES Cryptographic Algorithm
According to Kaur (2017), cryptography has been classified into symmetric and asymmetric
key algorithms and both AES and DES are a part of the symmetric key algorithm as they both
7
According to Mankotia and Sood (2015), a survey has been conducted to test the time
consumed by different algorithms and it has been found that the AES algorithm consumes
the least amount of time. AES algorithm has four operations to perform: Substitute Byte
transform- In this, each data block of 16 bytes is transmitted into another block with the
help of 8-bit substitution block. Shifting Rows- The last three rows of data blocks are shifted
in a clockwise direction that results in data scrambling. Mixing Columns- This involves mixing
of the column to form one column from another. The last round of encryption doesn’t
perform this step. Adding Key- This stage will add the resultant key after round of
encryption to the 128-bit data block for final encryption of data.
Figure 1 General Architecture DES Cryptographic Algorithm
According to Kaur (2017), cryptography has been classified into symmetric and asymmetric
key algorithms and both AES and DES are a part of the symmetric key algorithm as they both
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
use the same key for encryption and decryption. The DES runs in several rounds and in each
round the key is encrypted with different techniques and in the final round, the resultant
key is applied to the plaintext to convert it into ciphertext. AES algorithm is used to secure
sensitive, confidential and unclassified material. This algorithm is used worldwide and offer
security for ages up to 20 to 30 years in a row. It is easy to implement in hardware and
software environments.
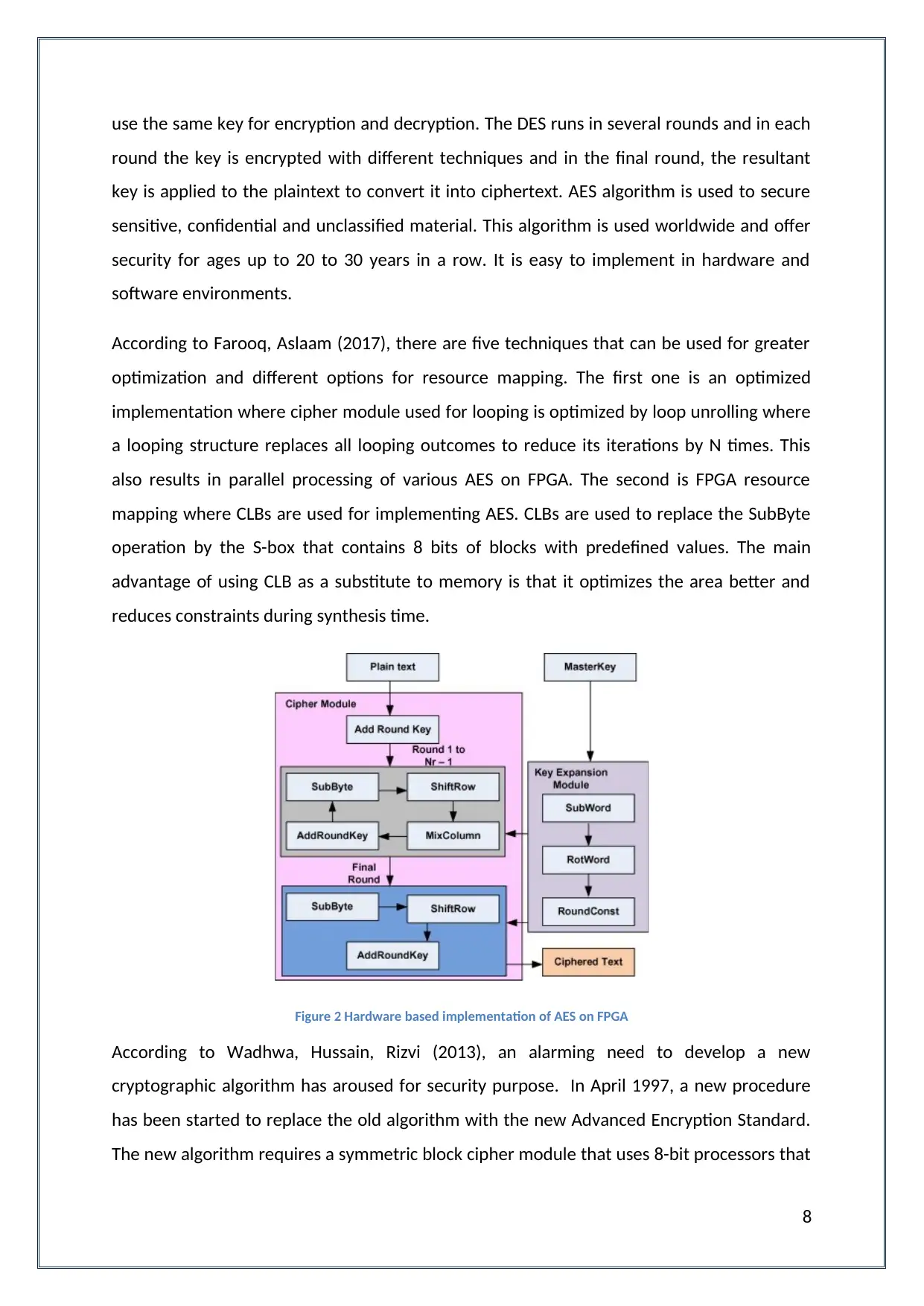
According to Farooq, Aslaam (2017), there are five techniques that can be used for greater
optimization and different options for resource mapping. The first one is an optimized
implementation where cipher module used for looping is optimized by loop unrolling where
a looping structure replaces all looping outcomes to reduce its iterations by N times. This
also results in parallel processing of various AES on FPGA. The second is FPGA resource
mapping where CLBs are used for implementing AES. CLBs are used to replace the SubByte
operation by the S-box that contains 8 bits of blocks with predefined values. The main
advantage of using CLB as a substitute to memory is that it optimizes the area better and
reduces constraints during synthesis time.
Figure 2 Hardware based implementation of AES on FPGA
According to Wadhwa, Hussain, Rizvi (2013), an alarming need to develop a new
cryptographic algorithm has aroused for security purpose. In April 1997, a new procedure
has been started to replace the old algorithm with the new Advanced Encryption Standard.
The new algorithm requires a symmetric block cipher module that uses 8-bit processors that
8
round the key is encrypted with different techniques and in the final round, the resultant
key is applied to the plaintext to convert it into ciphertext. AES algorithm is used to secure
sensitive, confidential and unclassified material. This algorithm is used worldwide and offer
security for ages up to 20 to 30 years in a row. It is easy to implement in hardware and
software environments.
According to Farooq, Aslaam (2017), there are five techniques that can be used for greater
optimization and different options for resource mapping. The first one is an optimized
implementation where cipher module used for looping is optimized by loop unrolling where
a looping structure replaces all looping outcomes to reduce its iterations by N times. This
also results in parallel processing of various AES on FPGA. The second is FPGA resource
mapping where CLBs are used for implementing AES. CLBs are used to replace the SubByte
operation by the S-box that contains 8 bits of blocks with predefined values. The main
advantage of using CLB as a substitute to memory is that it optimizes the area better and
reduces constraints during synthesis time.
Figure 2 Hardware based implementation of AES on FPGA
According to Wadhwa, Hussain, Rizvi (2013), an alarming need to develop a new
cryptographic algorithm has aroused for security purpose. In April 1997, a new procedure
has been started to replace the old algorithm with the new Advanced Encryption Standard.
The new algorithm requires a symmetric block cipher module that uses 8-bit processors that
8

are also used in smart cards and 32-bit processors for desktops. The two main
characteristics of AES over DES were its security and speed. There were fifteen algorithms
submitted by developers and researchers for the AES, all of which are compared on the
basis of two factors that is Speed and security. The fifteen algorithms are CAST that is
immune to many cryptanalytic attacks, Crypton that has almost double the speed of DES,
DEAL which is immune to key search and ciphertext attack, Decorrelated Fast Cipher that is
fast on 16 bit device than 8 bit device, Efficient Encryption, FROG, Hasty Pudding Cipher, LOK
197, and Magneta.
According to Wadhwa, Hussain, Rizvi (2013), the adopted technique for AES was commonly
called as Rijndael which is byte oriented block cipher that works on the principle of
substitution and permutation. Rijndael is immune to brutal attacks and performs quite well
in both hardware and software across a wide variety of computing devices. The differential
cryptanalysis attacked the rounded cryptographic algorithm with non-marginal complexity
of data. The combination of AES cryptanalysis data for rounds is 7 for AES-128, 8 rounds for
AES-192 and AES-256. Then it has been worked over to improve the process of key recovery.
The most important feature of this technique is that any square attack can’t reach the AES
security to threaten it until its power level is reached to break the Rijndael cipher. It has two
architecture one for 8 bit and second for 32 bit which both are good in architecture and
have great security margins. The other four finalists that have been chosen out of the fifteen
algorithms are MARS, RC6, Serpent, and Twofish, all of these algorithms are have their own
benefits that make them unique from each other and areas that need to be worked upon.
According to Gupta and Kaushik (2017), there are seven steps in the complete procedure of
AES cryptographic algorithm. In AES, for 128 bit key 10 encryption rounds is performed for
192 bit key 12 encryption rounds is performed, and for 256 bit key 14 encryption rounds is
performed. The steps involved in encryption of data are:
Step 1:- A plain text of 128 bytes will take as input and then negotiated as a block of plain
text of 16 bytes.
Step 2: - Add Round Key: - each block of 16 bytes will be integrated with a round of
encryption key using the bitwise XOR operation that will be performed on each byte.
9
characteristics of AES over DES were its security and speed. There were fifteen algorithms
submitted by developers and researchers for the AES, all of which are compared on the
basis of two factors that is Speed and security. The fifteen algorithms are CAST that is
immune to many cryptanalytic attacks, Crypton that has almost double the speed of DES,
DEAL which is immune to key search and ciphertext attack, Decorrelated Fast Cipher that is
fast on 16 bit device than 8 bit device, Efficient Encryption, FROG, Hasty Pudding Cipher, LOK
197, and Magneta.
According to Wadhwa, Hussain, Rizvi (2013), the adopted technique for AES was commonly
called as Rijndael which is byte oriented block cipher that works on the principle of
substitution and permutation. Rijndael is immune to brutal attacks and performs quite well
in both hardware and software across a wide variety of computing devices. The differential
cryptanalysis attacked the rounded cryptographic algorithm with non-marginal complexity
of data. The combination of AES cryptanalysis data for rounds is 7 for AES-128, 8 rounds for
AES-192 and AES-256. Then it has been worked over to improve the process of key recovery.
The most important feature of this technique is that any square attack can’t reach the AES
security to threaten it until its power level is reached to break the Rijndael cipher. It has two
architecture one for 8 bit and second for 32 bit which both are good in architecture and
have great security margins. The other four finalists that have been chosen out of the fifteen
algorithms are MARS, RC6, Serpent, and Twofish, all of these algorithms are have their own
benefits that make them unique from each other and areas that need to be worked upon.
According to Gupta and Kaushik (2017), there are seven steps in the complete procedure of
AES cryptographic algorithm. In AES, for 128 bit key 10 encryption rounds is performed for
192 bit key 12 encryption rounds is performed, and for 256 bit key 14 encryption rounds is
performed. The steps involved in encryption of data are:
Step 1:- A plain text of 128 bytes will take as input and then negotiated as a block of plain
text of 16 bytes.
Step 2: - Add Round Key: - each block of 16 bytes will be integrated with a round of
encryption key using the bitwise XOR operation that will be performed on each byte.
9

Step 3:- Byte Substitution: - the 16 bytes of the block after step 2 will then be substituted
using S box which then gives a result of a 4*4 matrix.
Step 4:- Shift row: - The resultant matrices of 4*4 rows and columns will then be shifted to
left and the leftmost entry will be shifted to right hence forming a cyclic left shift.
Step 5:- Mix Columns: -Each column of 4 bytes that has been created will be mixed and
altered by applying a mathematical function to it which is called as Galois Field.
Step 6:- Add Round Key: - The resultant 16 bytes matrix will be converted to 128 bits block
and then will be XORed with the round key again.
Step 7:- All the above steps will again be performed on the 128-bit block that has been
received in step 6.
Step 8:- After the completion of all the rounds with all the steps, a ciphertext will be
generated that will be our final product.
According to Cruz and Domingo (2017), the process of expanded DES is almost same as the
process of original DES with slight changes. The original DES is a 64-bit block system while
the expanded DES is a 128-bit block system and the swap after each round has been
converted to 64 bit from 32 bit. The difference in the process of both systems is for some
special cases where tables have been expanded to account for the increase in bits from 64
to 128. For the tables that have been created, dividers have been created to isolate the
parts of permutation. And in a similar way, all the tables have been modified to account the
change in the bits. The S box will also be modified to see the increase in the bits as it
doubles. The expansion table will also contain 96 bits from 48 bits. The expanded DES is a
better solution than original DES in providing security and better data encryption but its
popularity remained less as researchers wanted a long-term solution for the incapability of
DES. In the same way as encryption, the decryption process will also differ from the original
process to account for the increase in data block bits.
10
using S box which then gives a result of a 4*4 matrix.
Step 4:- Shift row: - The resultant matrices of 4*4 rows and columns will then be shifted to
left and the leftmost entry will be shifted to right hence forming a cyclic left shift.
Step 5:- Mix Columns: -Each column of 4 bytes that has been created will be mixed and
altered by applying a mathematical function to it which is called as Galois Field.
Step 6:- Add Round Key: - The resultant 16 bytes matrix will be converted to 128 bits block
and then will be XORed with the round key again.
Step 7:- All the above steps will again be performed on the 128-bit block that has been
received in step 6.
Step 8:- After the completion of all the rounds with all the steps, a ciphertext will be
generated that will be our final product.
According to Cruz and Domingo (2017), the process of expanded DES is almost same as the
process of original DES with slight changes. The original DES is a 64-bit block system while
the expanded DES is a 128-bit block system and the swap after each round has been
converted to 64 bit from 32 bit. The difference in the process of both systems is for some
special cases where tables have been expanded to account for the increase in bits from 64
to 128. For the tables that have been created, dividers have been created to isolate the
parts of permutation. And in a similar way, all the tables have been modified to account the
change in the bits. The S box will also be modified to see the increase in the bits as it
doubles. The expansion table will also contain 96 bits from 48 bits. The expanded DES is a
better solution than original DES in providing security and better data encryption but its
popularity remained less as researchers wanted a long-term solution for the incapability of
DES. In the same way as encryption, the decryption process will also differ from the original
process to account for the increase in data block bits.
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
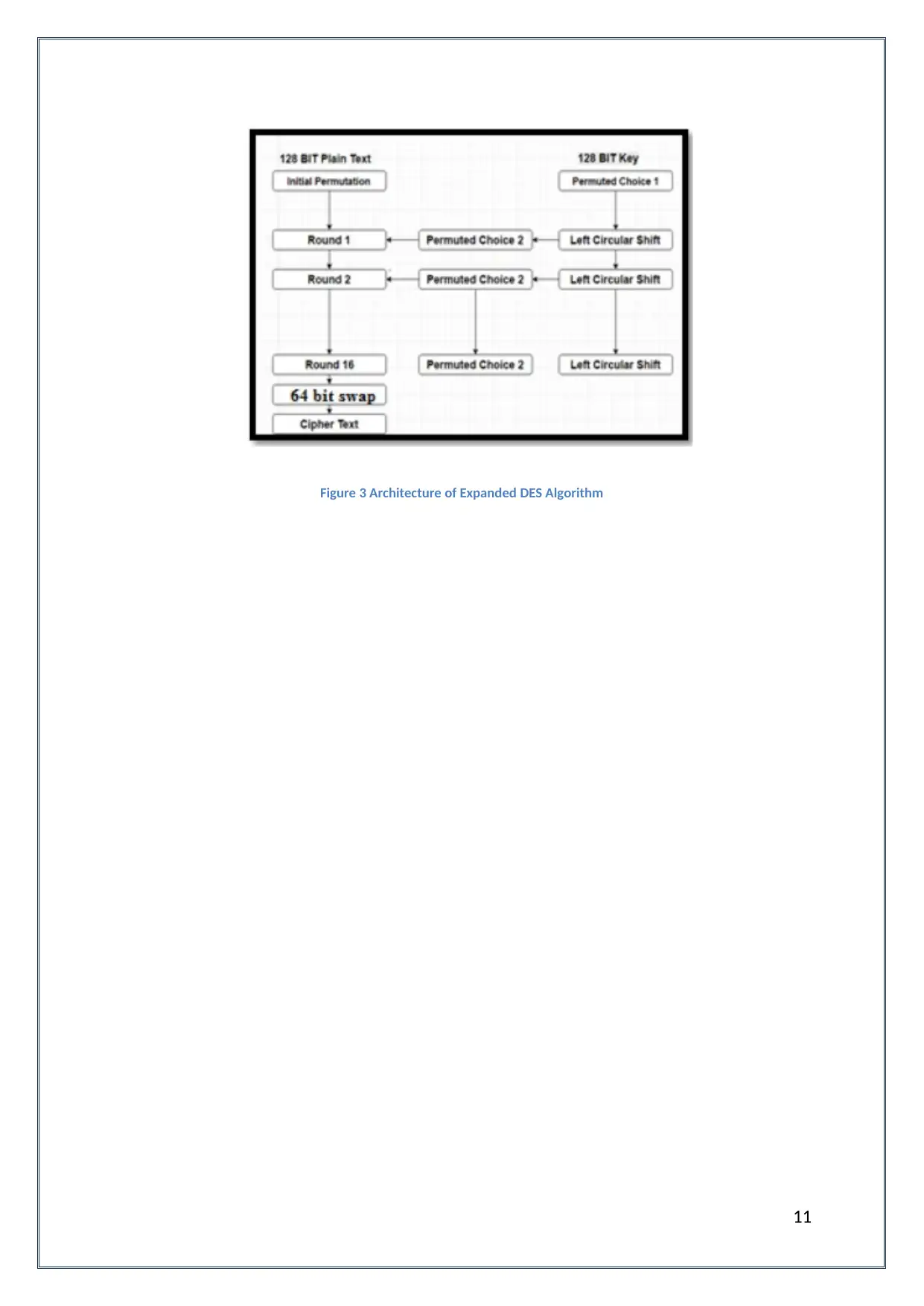
Figure 3 Architecture of Expanded DES Algorithm
11
11

Experimental Analysis
On the basis of above discussed various means of encrypting data using symmetric block
ciphers, critical analysis of both the cryptographic algorithms has been done. DES being the
first ever block cipher algorithm lacks some serious security measures and has some weak
points. It uses the same process and key for both encryption and decryption but with the
increase in computing speed, the usage of the 56-bit key is no more useful in handling brutal
attacks. Hence with this rapid development in computing leads to the development to triple
DES that has been designed with an increased key size from 56 bits to 112 bits and 168 bits
by using two and three keys together respectively without any need to make a new
algorithm. Although the original usage of DES differs from the way it is used in 3DES hence
the output of this algorithm is less in comparison to original DES. However, no security issue
has been detected in 3DES algorithm because of which it has been used in various Internet
protocols.
Later on, many new algorithms have been developed and came into the market which has
been used by many companies which also provided some better results in terms of speed
and security. Blowfish has been considered as the fastest algorithm but it also lacked some
points. The final algorithms that have been developed are AES which uses the concept of
encrypting a plaintext data block with the help of variable length key. The variable length
key provides flexibility to the algorithm and allows it to have a variable number of rounds
based on the size of the key.
For example, data blocks of size within range 128- 256 can use blocks in multiples of 32 bits
to perform the remaining procedure. AES has been designed as a better version of 3DES to
provide more efficiency (Farooq, 2017).
AES algorithm can also be used to encrypt and decrypt images by using CFB mode.PKCS5
padding is used for providing pads to clear texts into blocks of 8 bits. Encryption of image
text that is not a multiple of the 8-bit block is encrypted by first padding extra bits to it and
making it a multiple of 8-bit block. This methodology of encrypting images has been
developed with an inspiration of providing privacy while using video camera surveillance
services.
12
On the basis of above discussed various means of encrypting data using symmetric block
ciphers, critical analysis of both the cryptographic algorithms has been done. DES being the
first ever block cipher algorithm lacks some serious security measures and has some weak
points. It uses the same process and key for both encryption and decryption but with the
increase in computing speed, the usage of the 56-bit key is no more useful in handling brutal
attacks. Hence with this rapid development in computing leads to the development to triple
DES that has been designed with an increased key size from 56 bits to 112 bits and 168 bits
by using two and three keys together respectively without any need to make a new
algorithm. Although the original usage of DES differs from the way it is used in 3DES hence
the output of this algorithm is less in comparison to original DES. However, no security issue
has been detected in 3DES algorithm because of which it has been used in various Internet
protocols.
Later on, many new algorithms have been developed and came into the market which has
been used by many companies which also provided some better results in terms of speed
and security. Blowfish has been considered as the fastest algorithm but it also lacked some
points. The final algorithms that have been developed are AES which uses the concept of
encrypting a plaintext data block with the help of variable length key. The variable length
key provides flexibility to the algorithm and allows it to have a variable number of rounds
based on the size of the key.
For example, data blocks of size within range 128- 256 can use blocks in multiples of 32 bits
to perform the remaining procedure. AES has been designed as a better version of 3DES to
provide more efficiency (Farooq, 2017).
AES algorithm can also be used to encrypt and decrypt images by using CFB mode.PKCS5
padding is used for providing pads to clear texts into blocks of 8 bits. Encryption of image
text that is not a multiple of the 8-bit block is encrypted by first padding extra bits to it and
making it a multiple of 8-bit block. This methodology of encrypting images has been
developed with an inspiration of providing privacy while using video camera surveillance
services.
12

By this, only authorized users that have the key to decrypt the complete sequence of
images will be able to see the video footage and no unauthorized user will get hold of the
confidential and private video footages (Er, 2017).
By this paper, it can be reviewed that all the algorithms have their own good points and are
unique in their own way. They all also lack some other points and hence they can’t be said
to be complete individually. The best way to provide security is to use all the algorithms in
unison to get the most desired results.
13
images will be able to see the video footage and no unauthorized user will get hold of the
confidential and private video footages (Er, 2017).
By this paper, it can be reviewed that all the algorithms have their own good points and are
unique in their own way. They all also lack some other points and hence they can’t be said
to be complete individually. The best way to provide security is to use all the algorithms in
unison to get the most desired results.
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Future Scope
The emerging technologies in the market need to be protected and given proper security
measurements for data protection and encryption. Hence the future scope in this area
requires the need to improve the faults and errors in each of these algorithms to get the
better results. A complete performance analysis of each of the algorithms needs to be made
by taking into account different variable on which its performance depends and outline the
strengths and weakness of each algorithm. A thorough understanding is needed to be made
to get the knowledge of the shortcomings of each algorithm and future work can be done to
overcome these shortcomings. Apart from working on the old algorithms, there is a future
scope to understand the concept of each existing algorithm and taking into account the
strengths of each algorithm, new algorithms can be made that will focus on the strengths of
these algorithms and overcome their shortcomings.
Along with the improvements in encrypting the plaintext messages, algorithms for
encrypting image has also been developed. The image encryption AES algorithm can also be
expanded into encrypting video codes by taking MPEG formats into account. In present
scenarios, these methodologies are very costly to be provided as services to a company,
hence in future cheap and affordable solution for the same can be invented to even provide
it as open source software. An encryption technology for encrypting audio, video, and other
media forms will be a huge event in the success of the cryptographic field. Proper
amendments in existing algorithms can be made to get better algorithms as the scope of
cryptography and data encryptions will see a huge rise in future and will merge as one of the
highest grossing market in technical world because of the need of the companies to secure
their data in the best possible way (Mankotia, 2015).
14
The emerging technologies in the market need to be protected and given proper security
measurements for data protection and encryption. Hence the future scope in this area
requires the need to improve the faults and errors in each of these algorithms to get the
better results. A complete performance analysis of each of the algorithms needs to be made
by taking into account different variable on which its performance depends and outline the
strengths and weakness of each algorithm. A thorough understanding is needed to be made
to get the knowledge of the shortcomings of each algorithm and future work can be done to
overcome these shortcomings. Apart from working on the old algorithms, there is a future
scope to understand the concept of each existing algorithm and taking into account the
strengths of each algorithm, new algorithms can be made that will focus on the strengths of
these algorithms and overcome their shortcomings.
Along with the improvements in encrypting the plaintext messages, algorithms for
encrypting image has also been developed. The image encryption AES algorithm can also be
expanded into encrypting video codes by taking MPEG formats into account. In present
scenarios, these methodologies are very costly to be provided as services to a company,
hence in future cheap and affordable solution for the same can be invented to even provide
it as open source software. An encryption technology for encrypting audio, video, and other
media forms will be a huge event in the success of the cryptographic field. Proper
amendments in existing algorithms can be made to get better algorithms as the scope of
cryptography and data encryptions will see a huge rise in future and will merge as one of the
highest grossing market in technical world because of the need of the companies to secure
their data in the best possible way (Mankotia, 2015).
14

Conclusion
This paper has been created to critically review the various cryptographic algorithms existed
in the market. The implementation techniques and amendments made in these algorithms
have also been discussed. DES and AES are the two encryption standard that has been
reviewed fully in this paper. The implementation of AES with FPGA was also reviewed in this
paper. The procedure of both these algorithms has been discussed in details along with their
shortcomings. The modification of DES into expanded DES and its journey to the
development of AES have all been reviewed in great detail to get the best insight into the
world of cryptographic and encryption methodologies. The techniques used for decryption
of the ciphertext have also been discussed along with their encryption process. As both of
these algorithms are symmetric key based, hence there was not any big difference in both
encryption and decryption process. The AES algorithm process used for encrypting images
have also been discussed in this paper.
15
This paper has been created to critically review the various cryptographic algorithms existed
in the market. The implementation techniques and amendments made in these algorithms
have also been discussed. DES and AES are the two encryption standard that has been
reviewed fully in this paper. The implementation of AES with FPGA was also reviewed in this
paper. The procedure of both these algorithms has been discussed in details along with their
shortcomings. The modification of DES into expanded DES and its journey to the
development of AES have all been reviewed in great detail to get the best insight into the
world of cryptographic and encryption methodologies. The techniques used for decryption
of the ciphertext have also been discussed along with their encryption process. As both of
these algorithms are symmetric key based, hence there was not any big difference in both
encryption and decryption process. The AES algorithm process used for encrypting images
have also been discussed in this paper.
15

References
Mankotia, S. and Sood, M., 2015. A Critical Analysis of Some Symmetric Key Block
Cipher Algorithms. International Journal of Computer Science and Information
Technologies, 6.
Er, M.K. and Er, J.K., 2017. Data Encryption Using Different Techniques: A
Review. International Journal of Advanced Research in Computer Science, 8(4).
Farooq, U., and Aslam, M.F., 2017. Comparative analysis of different AES
implementation techniques for efficient resource usage and better performance of
an FPGA. Journal of King Saud University-Computer and Information Sciences, 29(3),
pp.295-302.
WADHWA, N., HUSSAIN, S.Z. and RIZVI, S., REVIEW OF THE JOURNEY FROM DES TO
AES.
Gupta, A. and Kaushik, S., 2017. A Review: RSA and AES Algorithm. IITM Journal of
Management and IT, 8(1), pp.82-85.
Cruz, B.F., Domingo, K.N., De Guzman, F.E., Cotiangco, J.B. and Hilario, C.B., 2017.
Expanded 128-bit Data Encryption Standard.
Dixit, P., Gupta, A.K., Trivedi, M.C. and Yadav, V.K., 2018. Traditional and Hybrid
Encryption Techniques: A Survey. In Networking Communication and Data
Knowledge Engineering (pp. 239-248). Springer, Singapore.
Menon, C.B., Joy, A., Emmanuel, E., and Paul, V., 2017. Analysis of Symmetric
Algorithms. International Journal of Engineering Science, 5285.
Alahmadi, A., Abdelhakim, M., Ren, J., and Li, T., 2014. Defense against primary user
emulation attacks in cognitive radio networks using advanced encryption
standard. IEEE transactions on information forensics and security, 9(5), pp.772-781.
Chaturvedi, S. and Sharma, R., 2015. Securing text & image password using the
combinations of persuasive cued click points with improved advanced encryption
standard. Procedia Computer Science, 45, pp.418-427.
Saraf, K.R., Jagtap, V.P. and Mishra, A.K., 2014. Text and image encryption-
decryption using advanced encryption standard. International Journal of Emerging
Trends & Technology in Computer Science (IJETTCS), 3(3), pp.118-126.
16
Mankotia, S. and Sood, M., 2015. A Critical Analysis of Some Symmetric Key Block
Cipher Algorithms. International Journal of Computer Science and Information
Technologies, 6.
Er, M.K. and Er, J.K., 2017. Data Encryption Using Different Techniques: A
Review. International Journal of Advanced Research in Computer Science, 8(4).
Farooq, U., and Aslam, M.F., 2017. Comparative analysis of different AES
implementation techniques for efficient resource usage and better performance of
an FPGA. Journal of King Saud University-Computer and Information Sciences, 29(3),
pp.295-302.
WADHWA, N., HUSSAIN, S.Z. and RIZVI, S., REVIEW OF THE JOURNEY FROM DES TO
AES.
Gupta, A. and Kaushik, S., 2017. A Review: RSA and AES Algorithm. IITM Journal of
Management and IT, 8(1), pp.82-85.
Cruz, B.F., Domingo, K.N., De Guzman, F.E., Cotiangco, J.B. and Hilario, C.B., 2017.
Expanded 128-bit Data Encryption Standard.
Dixit, P., Gupta, A.K., Trivedi, M.C. and Yadav, V.K., 2018. Traditional and Hybrid
Encryption Techniques: A Survey. In Networking Communication and Data
Knowledge Engineering (pp. 239-248). Springer, Singapore.
Menon, C.B., Joy, A., Emmanuel, E., and Paul, V., 2017. Analysis of Symmetric
Algorithms. International Journal of Engineering Science, 5285.
Alahmadi, A., Abdelhakim, M., Ren, J., and Li, T., 2014. Defense against primary user
emulation attacks in cognitive radio networks using advanced encryption
standard. IEEE transactions on information forensics and security, 9(5), pp.772-781.
Chaturvedi, S. and Sharma, R., 2015. Securing text & image password using the
combinations of persuasive cued click points with improved advanced encryption
standard. Procedia Computer Science, 45, pp.418-427.
Saraf, K.R., Jagtap, V.P. and Mishra, A.K., 2014. Text and image encryption-
decryption using advanced encryption standard. International Journal of Emerging
Trends & Technology in Computer Science (IJETTCS), 3(3), pp.118-126.
16
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




