Cryptography Report for MITS5004: Public Key and Secret Key Systems
VerifiedAdded on 2022/10/11
|8
|559
|16
Report
AI Summary
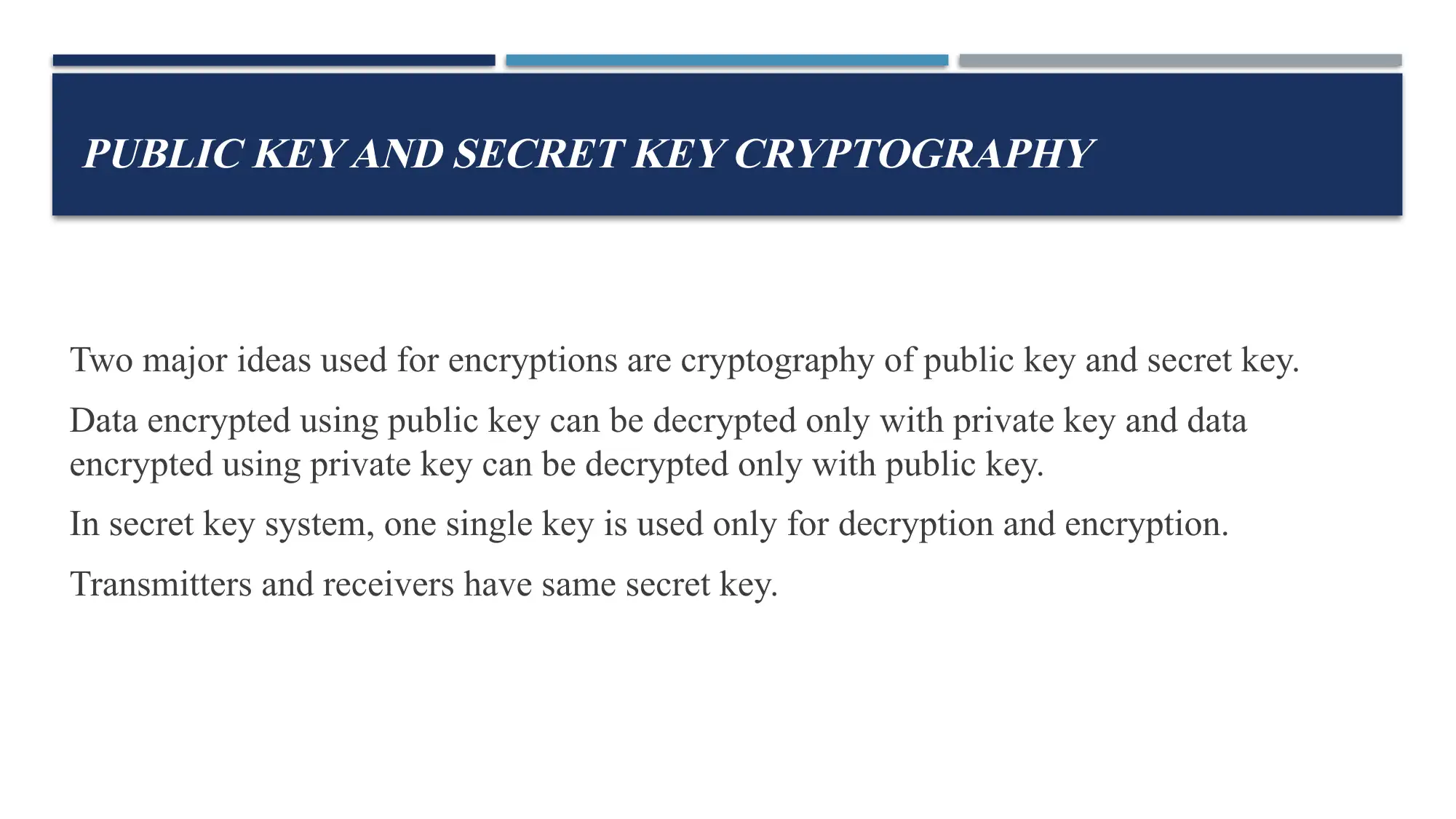
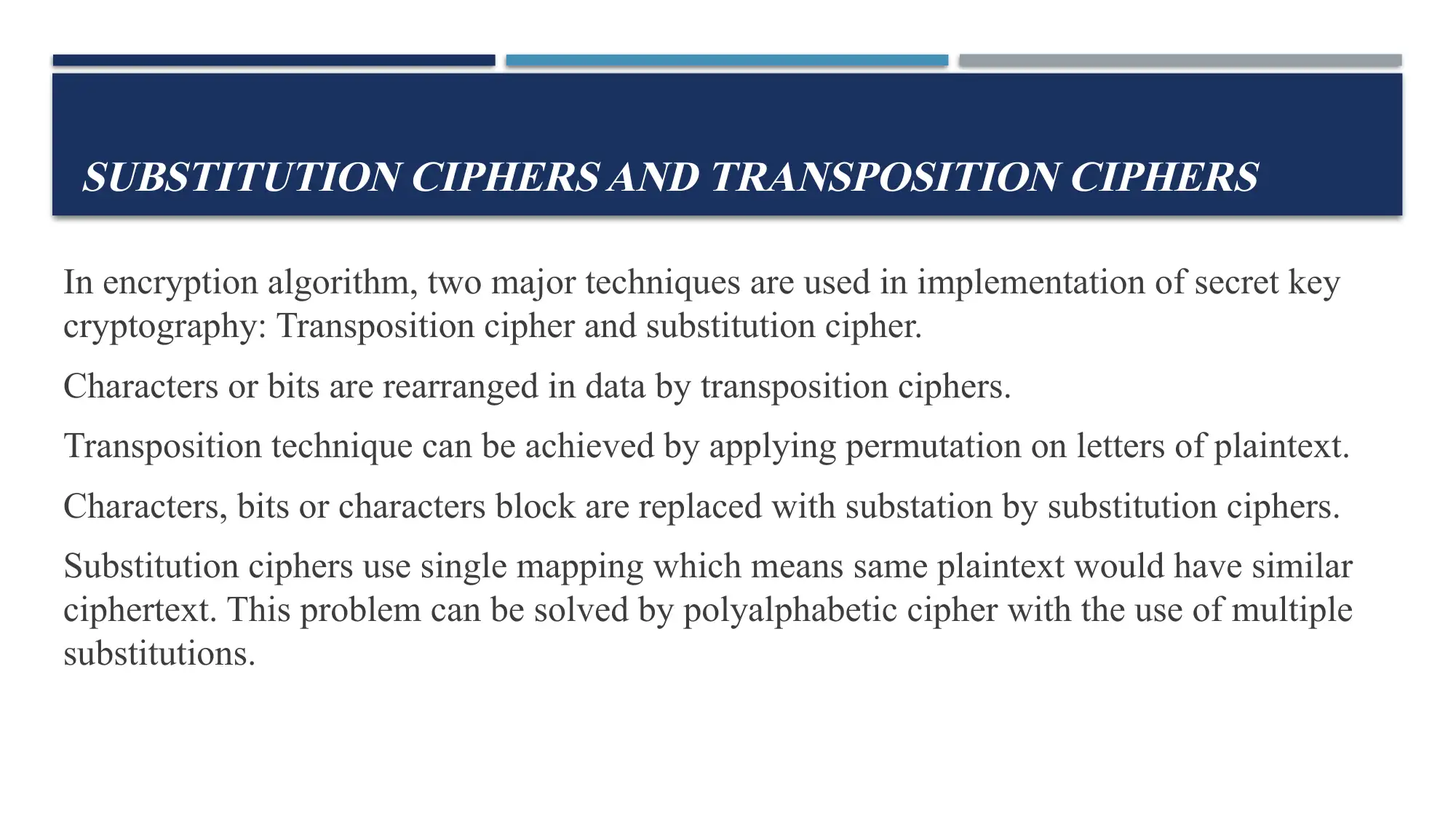
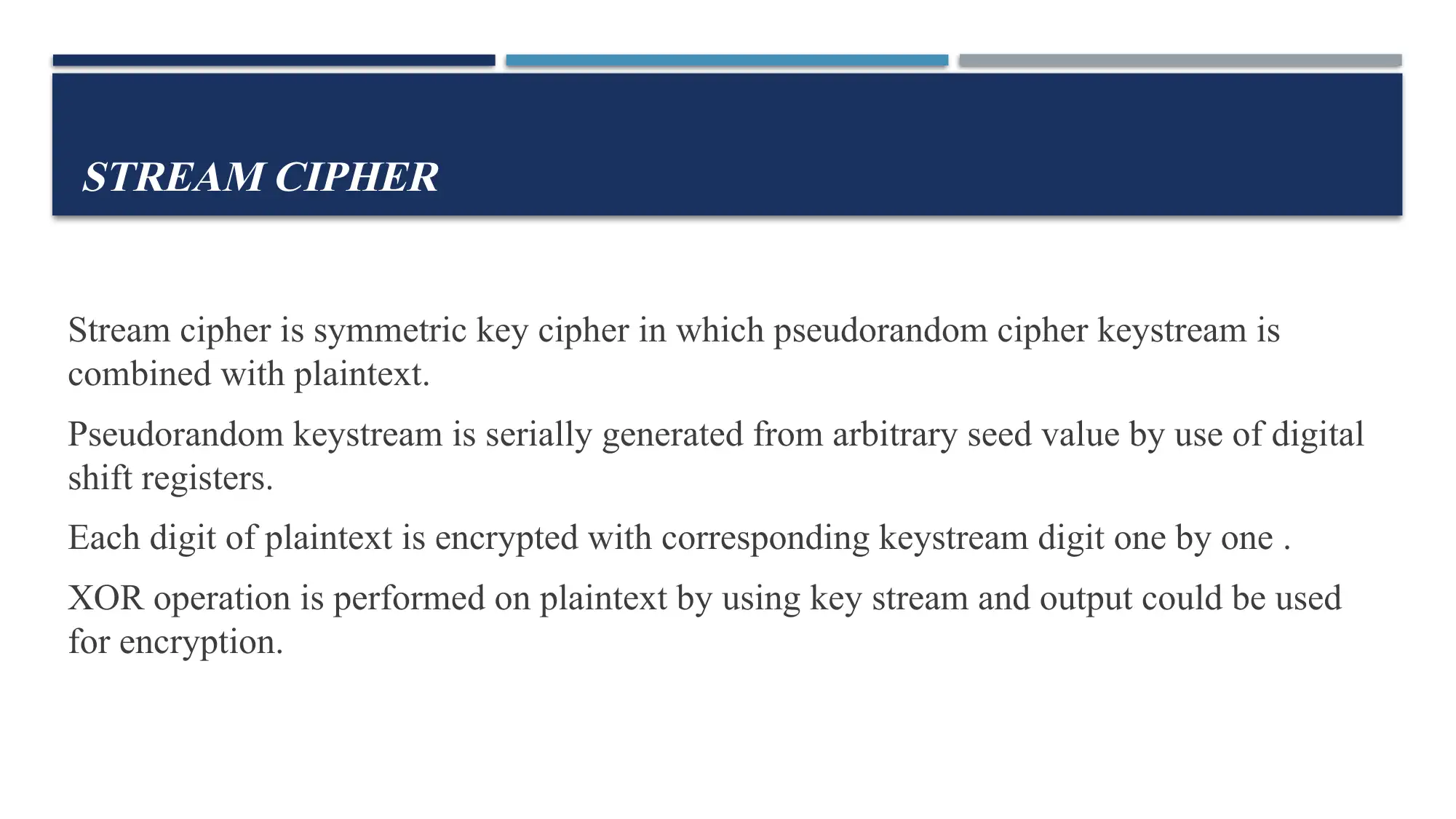
This report provides a comprehensive overview of cryptography, focusing on public key and secret key encryption methods. It details the differences between these approaches, explaining how data is encrypted and decrypted using either public or private keys. The report then delves into secret key cryptography, exploring the use of substitution and transposition ciphers as core techniques. Furthermore, it examines block ciphers and stream ciphers, highlighting their distinct characteristics and applications. The report also discusses the hybrid algorithm PGP (Pretty Good Privacy), which combines the advantages of both public and secret key systems. References to academic papers are included to support the information presented. This assignment is a report for MITS5004 IT Security.
1 out of 8











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)