Cryptography and Security: A Comprehensive Analysis of DES and AES
VerifiedAdded on 2024/05/20
|13
|2275
|71
AI Summary
This document delves into the intricacies of cryptography and security, focusing on two prominent encryption standards: DES (Data Encryption Standard) and AES (Advanced Encryption Standard). It explores the fundamental principles, working mechanisms, and practical implementations of these algorithms, highlighting their strengths and weaknesses. The document also examines the evolution of encryption standards, emphasizing the need for robust security measures in today's digital landscape. Through a comparative analysis, it sheds light on the key differences between DES and AES, providing insights into their suitability for various applications. The document concludes by emphasizing the importance of ongoing research and development in cryptography to counter evolving threats and ensure secure data communication.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

CSC8419
Cryptography and Security
Cryptography and Security
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Task 1.........................................................................................................................................2
Task 2- 5 general design decisions that have to be made while constructing secure systems...4
Task 3.........................................................................................................................................6
Task 4.........................................................................................................................................7
Task 5.........................................................................................................................................9
References................................................................................................................................12
1
Task 1.........................................................................................................................................2
Task 2- 5 general design decisions that have to be made while constructing secure systems...4
Task 3.........................................................................................................................................6
Task 4.........................................................................................................................................7
Task 5.........................................................................................................................................9
References................................................................................................................................12
1

Task 1
Computer systems provide various technological advantages over the traditional technology.
With the boom of the internet technology, its reach is limitless. The main concerns come in
terms of the security and protection of the data communication. The CIA (Confidentiality,
Integrity and Availability) also some time known as the CIA Triads is design to tackle this
type of issues. The CIA is the model which is designed to tackle the issues of the security
policies within the organization. The CIA sometimes are also called as AIC triad to avoid
confusion with the USA CIA agency.
All the three terms are the crucial pillars of the security in terms of security for data
communication. Confidentiality restricts the access to the crucial information. Integrity
ensures that the information is secure and has not been tempered. And the last reliability
guarantee that the information access is available the to the right person (Henderson, 2015).
Figure 1 The CIA Triad
Confidentiality
The confidentiality can also be comparable to the privacy. There are necessary steps taken to
ensure that the privacy or confidentiality of data will be maintained. It will prevent the
sensitive information getting into the wrong hands. There are various security policies and
technology will be used to maintain this processes continuously in the production network
environment.
2
Computer systems provide various technological advantages over the traditional technology.
With the boom of the internet technology, its reach is limitless. The main concerns come in
terms of the security and protection of the data communication. The CIA (Confidentiality,
Integrity and Availability) also some time known as the CIA Triads is design to tackle this
type of issues. The CIA is the model which is designed to tackle the issues of the security
policies within the organization. The CIA sometimes are also called as AIC triad to avoid
confusion with the USA CIA agency.
All the three terms are the crucial pillars of the security in terms of security for data
communication. Confidentiality restricts the access to the crucial information. Integrity
ensures that the information is secure and has not been tempered. And the last reliability
guarantee that the information access is available the to the right person (Henderson, 2015).
Figure 1 The CIA Triad
Confidentiality
The confidentiality can also be comparable to the privacy. There are necessary steps taken to
ensure that the privacy or confidentiality of data will be maintained. It will prevent the
sensitive information getting into the wrong hands. There are various security policies and
technology will be used to maintain this processes continuously in the production network
environment.
2

Integrity
The integrity is mainly responsible for the data accuracy, consistency and worthiness of the
critical information over a specific period of time. And the information data must not be
altered or changed during the transmission over the network lines. There are various policies
and controls will be involved to ensure the data integrity. And these are controlled by various
hardware and software resources to ensure it.
Availability
The availability is the key pillar of the security policies. Because of the data is not available
at the right time for the right user then it will be of no use. This is done by regular monitoring
of the hardware and software resources. And the system will be updated and patched on the
timely basis, so the service and data availability can be guaranteed to the end user without
any interruptions (Chai, 2012).
3
The integrity is mainly responsible for the data accuracy, consistency and worthiness of the
critical information over a specific period of time. And the information data must not be
altered or changed during the transmission over the network lines. There are various policies
and controls will be involved to ensure the data integrity. And these are controlled by various
hardware and software resources to ensure it.
Availability
The availability is the key pillar of the security policies. Because of the data is not available
at the right time for the right user then it will be of no use. This is done by regular monitoring
of the hardware and software resources. And the system will be updated and patched on the
timely basis, so the service and data availability can be guaranteed to the end user without
any interruptions (Chai, 2012).
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Task 2- 5 general design decisions that have to be made while
constructing secure systems
One of the most important thing in security process is system design. For maintaining
security system the techniques applied in the first step is this. The decision design that is
made while making the systems more secure:
Things to be controlled (data, operations or the users): The system design should
ponder upon the things such as user access controls, user specifications, management
of the credentials of the users; their personal information, management of data (either
informative or non-informative), management of its security and controlling the
vulnerability and also the operations that need to be carried on the data. The system
should be properly designed so that all the three elements are considered and that the
elements go in sync with each other. The system chart should consider all the
requirements of the users as well the data and operation management points.
On man-machine scale what is system’s working? The man-machine scale is there,
while on the left side, there is man-oriented with particular and the complex task,
while on the right side of scale machine oriented mechanisms that are generic are
present there. Therefore, system orientation is to be chosen by us, what we want for
the system.
In between centralized and decentralized control, only one should be selected whether
it is centralized or decentralized. For security purpose or central policy, this same
control is being implemented. For increasing efficiency, we have to take different
components and have to confirm, it, whether the policy definition is carried out
without any disturbance and the security, is well maintained.
In this last point, the lower layer protects the system by the attackers from
interrupting. Component categorization is needed to be done and system’s security
measure is to be decided so that the protection remains at its level and no attackers
4
constructing secure systems
One of the most important thing in security process is system design. For maintaining
security system the techniques applied in the first step is this. The decision design that is
made while making the systems more secure:
Things to be controlled (data, operations or the users): The system design should
ponder upon the things such as user access controls, user specifications, management
of the credentials of the users; their personal information, management of data (either
informative or non-informative), management of its security and controlling the
vulnerability and also the operations that need to be carried on the data. The system
should be properly designed so that all the three elements are considered and that the
elements go in sync with each other. The system chart should consider all the
requirements of the users as well the data and operation management points.
On man-machine scale what is system’s working? The man-machine scale is there,
while on the left side, there is man-oriented with particular and the complex task,
while on the right side of scale machine oriented mechanisms that are generic are
present there. Therefore, system orientation is to be chosen by us, what we want for
the system.
In between centralized and decentralized control, only one should be selected whether
it is centralized or decentralized. For security purpose or central policy, this same
control is being implemented. For increasing efficiency, we have to take different
components and have to confirm, it, whether the policy definition is carried out
without any disturbance and the security, is well maintained.
In this last point, the lower layer protects the system by the attackers from
interrupting. Component categorization is needed to be done and system’s security
measure is to be decided so that the protection remains at its level and no attackers
4

can attack the system. This layer must be strong enough so that no one is able to
breach it so that it is ensured that the system is secure.
We have to need to take decision for the proposed system. Proposed system may be
specific and simple or complex with rich system environments characteristic. Most of
the time, simple system environment contained in higher assurance with rich
environments characteristic but rich environment cannot get high-level assurance.
We have selected feature of the rich environment for the proposed system because it
offered security form the attackers and reduced the harm. For this, we must be hired
security experts that easily handle the system security.
5
breach it so that it is ensured that the system is secure.
We have to need to take decision for the proposed system. Proposed system may be
specific and simple or complex with rich system environments characteristic. Most of
the time, simple system environment contained in higher assurance with rich
environments characteristic but rich environment cannot get high-level assurance.
We have selected feature of the rich environment for the proposed system because it
offered security form the attackers and reduced the harm. For this, we must be hired
security experts that easily handle the system security.
5

Task 3
Here are the substitutions of decimal no of 12.Representation in binary numbers of 12
is “11 00”. Therefore, these binary digits are representing here first two digits
represent a row, and second two digits represent a column. Therefore, “11” is
representing 3rdrow and “00” is representing the 1st column. Hence, the result here is
“0111” and this is equivalent to decimal no of 7.
Here are the substitutions of decimal no of 7.Representation in binary numbers of 7 is
“01 11”. Therefore, these binary digits are representing here first two digits represent
a row, and second two digits represent a column. Therefore, “01” is representing the
second row and “11” is representing the 3rd column. Hence, the result here is “1011”
and this is equivalent to decimal no of 11.
Here are the substitutions of decimal no of 2.Representation in binary numbers of 2 is
“0010”. Therefore, these binary digits are representing here first two digits represent a
row, and second two digits represent a column. Therefore, “00” is representing 1strow
and “10” is representing the 1st column. Hence, the result here is “1111” and this is
equivalent to decimal no of 15.
6
Here are the substitutions of decimal no of 12.Representation in binary numbers of 12
is “11 00”. Therefore, these binary digits are representing here first two digits
represent a row, and second two digits represent a column. Therefore, “11” is
representing 3rdrow and “00” is representing the 1st column. Hence, the result here is
“0111” and this is equivalent to decimal no of 7.
Here are the substitutions of decimal no of 7.Representation in binary numbers of 7 is
“01 11”. Therefore, these binary digits are representing here first two digits represent
a row, and second two digits represent a column. Therefore, “01” is representing the
second row and “11” is representing the 3rd column. Hence, the result here is “1011”
and this is equivalent to decimal no of 11.
Here are the substitutions of decimal no of 2.Representation in binary numbers of 2 is
“0010”. Therefore, these binary digits are representing here first two digits represent a
row, and second two digits represent a column. Therefore, “00” is representing 1strow
and “10” is representing the 1st column. Hence, the result here is “1111” and this is
equivalent to decimal no of 15.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Task 4:
To evaluate w [4], the given equation we will be used:
So here is given I is divisible by 4. Given algorithm for chipper key expansion of Nk.That’s
mean given that W[i] = w[I - Nk]
Given temp value after finding the rotword(). And the rotword()is an 8 bytes cyclic
permutation.
Like I = 4;
Then temp = 09cf4f3c
After this we foundrotword() =cf4f3c09
Therefore, that means we shifted starting two digits at last.Then we find subword() value
from rotword() match in given above table of keys.Subbytes(), every substitutes is eight bytes
and equal to eight bytes proposed in a S-box in the paper,
rotword() =8a84eb01;
After finding out of Subword() we will find “Rcon[i/Nk]”,
Rcon[i/nk] = 01000000;
After this we will find out XOR, in between them Subword() and rcon,
W[i-Nk] = 2b7e1516;
The final value is “w[i]”
W[i] = temp XOR w[i-Nk]
W[i] = 09cf4f3c XOR 2b7e1516 = a0fafe17;
So it is indivisible by 4 and ‘I’ is number of word.
Then we will find out Nk = 4, And I = 5,6,7
7
To evaluate w [4], the given equation we will be used:
So here is given I is divisible by 4. Given algorithm for chipper key expansion of Nk.That’s
mean given that W[i] = w[I - Nk]
Given temp value after finding the rotword(). And the rotword()is an 8 bytes cyclic
permutation.
Like I = 4;
Then temp = 09cf4f3c
After this we foundrotword() =cf4f3c09
Therefore, that means we shifted starting two digits at last.Then we find subword() value
from rotword() match in given above table of keys.Subbytes(), every substitutes is eight bytes
and equal to eight bytes proposed in a S-box in the paper,
rotword() =8a84eb01;
After finding out of Subword() we will find “Rcon[i/Nk]”,
Rcon[i/nk] = 01000000;
After this we will find out XOR, in between them Subword() and rcon,
W[i-Nk] = 2b7e1516;
The final value is “w[i]”
W[i] = temp XOR w[i-Nk]
W[i] = 09cf4f3c XOR 2b7e1516 = a0fafe17;
So it is indivisible by 4 and ‘I’ is number of word.
Then we will find out Nk = 4, And I = 5,6,7
7
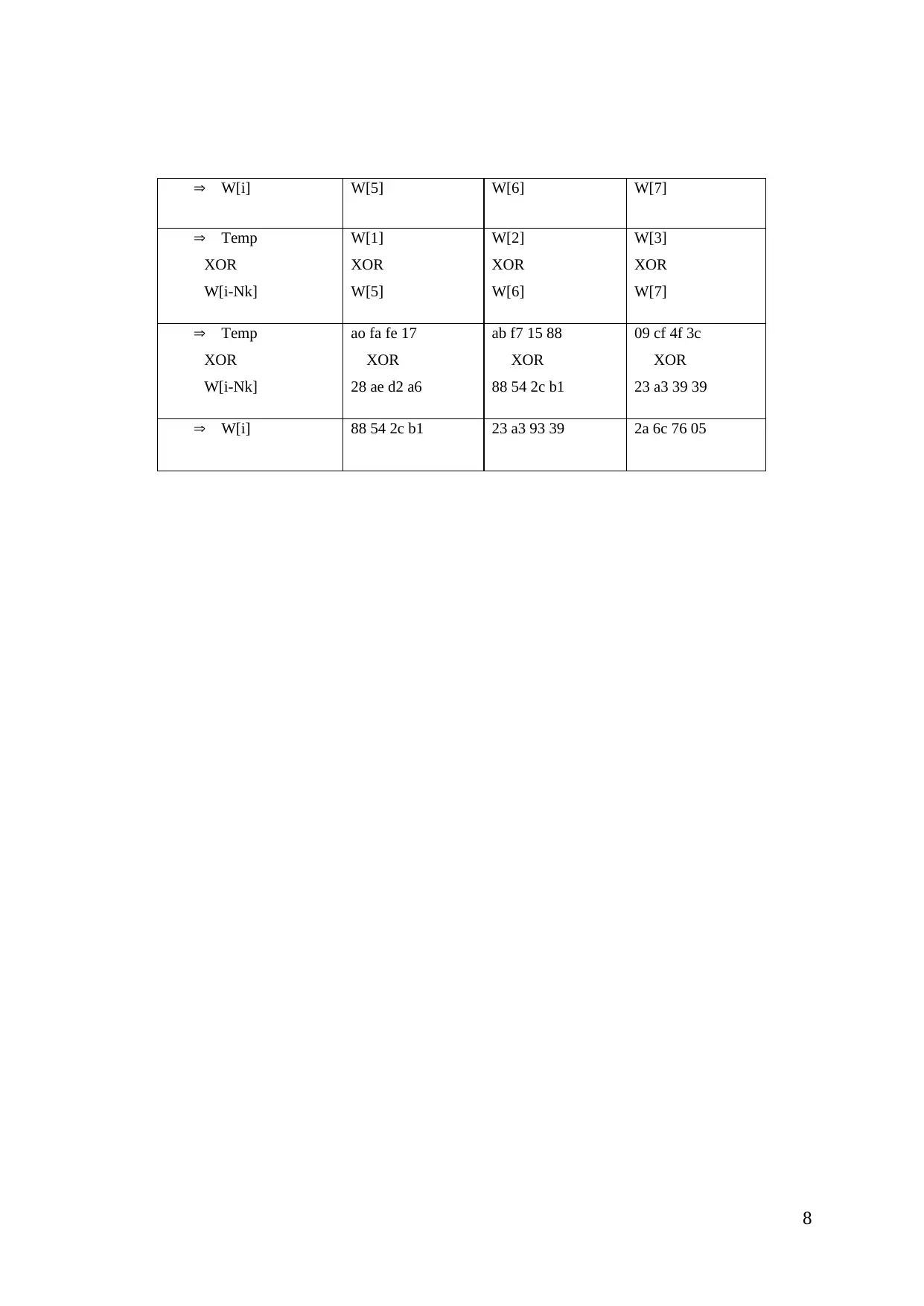
8
W[i] W[5] W[6] W[7]
Temp
XOR
W[i-Nk]
W[1]
XOR
W[5]
W[2]
XOR
W[6]
W[3]
XOR
W[7]
Temp
XOR
W[i-Nk]
ao fa fe 17
XOR
28 ae d2 a6
ab f7 15 88
XOR
88 54 2c b1
09 cf 4f 3c
XOR
23 a3 39 39
W[i] 88 54 2c b1 23 a3 93 39 2a 6c 76 05
W[i] W[5] W[6] W[7]
Temp
XOR
W[i-Nk]
W[1]
XOR
W[5]
W[2]
XOR
W[6]
W[3]
XOR
W[7]
Temp
XOR
W[i-Nk]
ao fa fe 17
XOR
28 ae d2 a6
ab f7 15 88
XOR
88 54 2c b1
09 cf 4f 3c
XOR
23 a3 39 39
W[i] 88 54 2c b1 23 a3 93 39 2a 6c 76 05

Task 5
Critical Reviewing DES and AES
The network communication has provided a lot of advantage over the traditional way of
communication for a lot of data. But the main problems come in the technology itself since
the network lines are open to everyone, so anyone can sniff or tap the lines and can steal the
crucial information. In order to deal with these types of situation, the cryptography
techniques are used to secure the communication between two systems.
In this, the communicating data are encrypted and decrypted using various algorithm. It
requires a lot of computing power to encrypt and decrypt the information. The DES and AES
are one of the algorithms which are used in the modern-day communication over the internet
as well as in the private network also. These two cryptography techniques usea different
technique to encrypt and decrypt the information.
The Data Encryption Standard (DES) which is developed by the US Department of defence
for the information encryption. It is developed in the year 1977 and it is still used in today’s
internet network. It is a symmetric key block cypher and it is based Feistel structure where
the plaintext will be divided into two halves parts. It takes 64-bit plain text and the 56-bit key
to produce 64-bit Cipher text (Engelfriet, 2018)
9
Critical Reviewing DES and AES
The network communication has provided a lot of advantage over the traditional way of
communication for a lot of data. But the main problems come in the technology itself since
the network lines are open to everyone, so anyone can sniff or tap the lines and can steal the
crucial information. In order to deal with these types of situation, the cryptography
techniques are used to secure the communication between two systems.
In this, the communicating data are encrypted and decrypted using various algorithm. It
requires a lot of computing power to encrypt and decrypt the information. The DES and AES
are one of the algorithms which are used in the modern-day communication over the internet
as well as in the private network also. These two cryptography techniques usea different
technique to encrypt and decrypt the information.
The Data Encryption Standard (DES) which is developed by the US Department of defence
for the information encryption. It is developed in the year 1977 and it is still used in today’s
internet network. It is a symmetric key block cypher and it is based Feistel structure where
the plaintext will be divided into two halves parts. It takes 64-bit plain text and the 56-bit key
to produce 64-bit Cipher text (Engelfriet, 2018)
9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
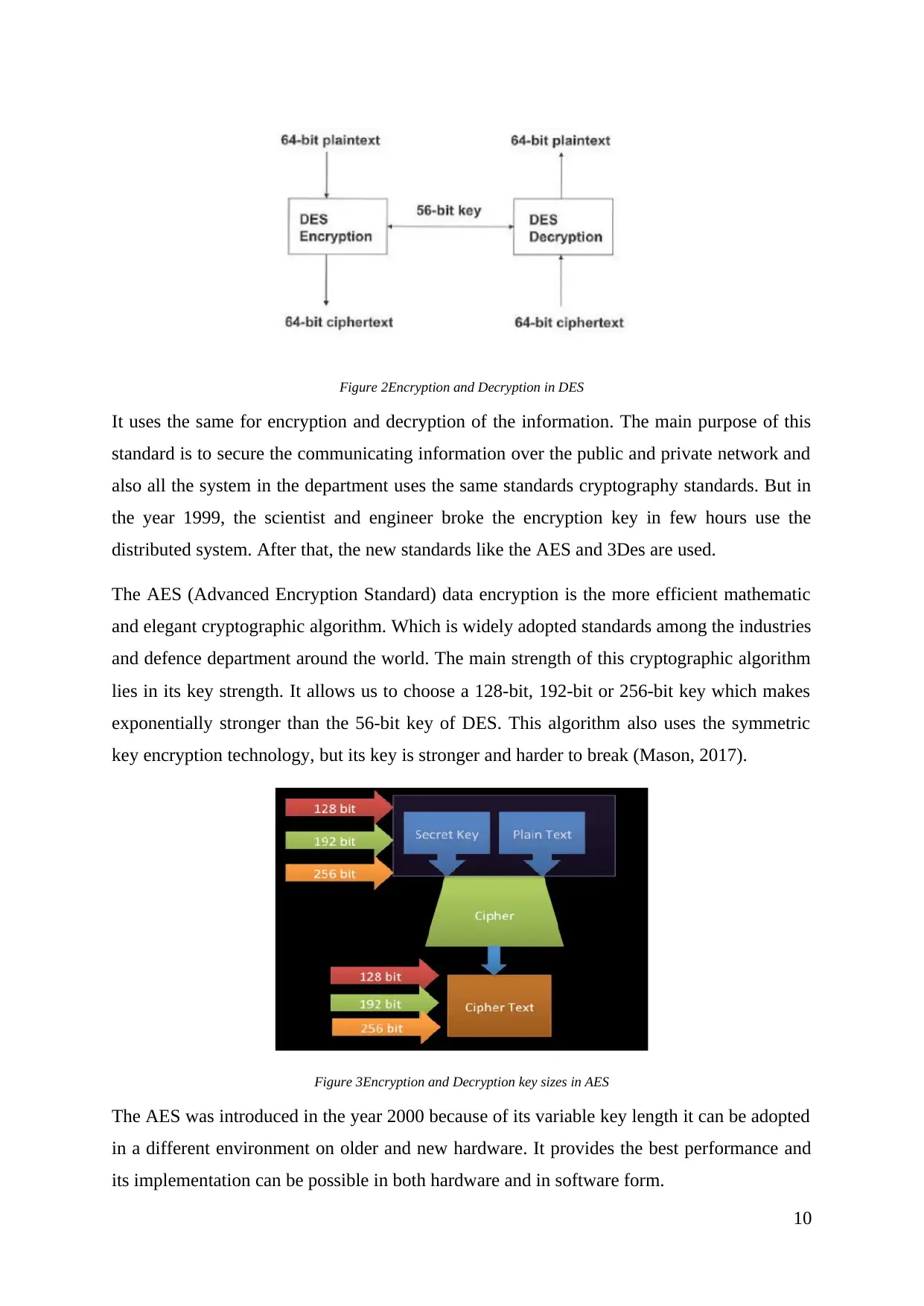
Figure 2Encryption and Decryption in DES
It uses the same for encryption and decryption of the information. The main purpose of this
standard is to secure the communicating information over the public and private network and
also all the system in the department uses the same standards cryptography standards. But in
the year 1999, the scientist and engineer broke the encryption key in few hours use the
distributed system. After that, the new standards like the AES and 3Des are used.
The AES (Advanced Encryption Standard) data encryption is the more efficient mathematic
and elegant cryptographic algorithm. Which is widely adopted standards among the industries
and defence department around the world. The main strength of this cryptographic algorithm
lies in its key strength. It allows us to choose a 128-bit, 192-bit or 256-bit key which makes
exponentially stronger than the 56-bit key of DES. This algorithm also uses the symmetric
key encryption technology, but its key is stronger and harder to break (Mason, 2017).
Figure 3Encryption and Decryption key sizes in AES
The AES was introduced in the year 2000 because of its variable key length it can be adopted
in a different environment on older and new hardware. It provides the best performance and
its implementation can be possible in both hardware and in software form.
10
It uses the same for encryption and decryption of the information. The main purpose of this
standard is to secure the communicating information over the public and private network and
also all the system in the department uses the same standards cryptography standards. But in
the year 1999, the scientist and engineer broke the encryption key in few hours use the
distributed system. After that, the new standards like the AES and 3Des are used.
The AES (Advanced Encryption Standard) data encryption is the more efficient mathematic
and elegant cryptographic algorithm. Which is widely adopted standards among the industries
and defence department around the world. The main strength of this cryptographic algorithm
lies in its key strength. It allows us to choose a 128-bit, 192-bit or 256-bit key which makes
exponentially stronger than the 56-bit key of DES. This algorithm also uses the symmetric
key encryption technology, but its key is stronger and harder to break (Mason, 2017).
Figure 3Encryption and Decryption key sizes in AES
The AES was introduced in the year 2000 because of its variable key length it can be adopted
in a different environment on older and new hardware. It provides the best performance and
its implementation can be possible in both hardware and in software form.
10
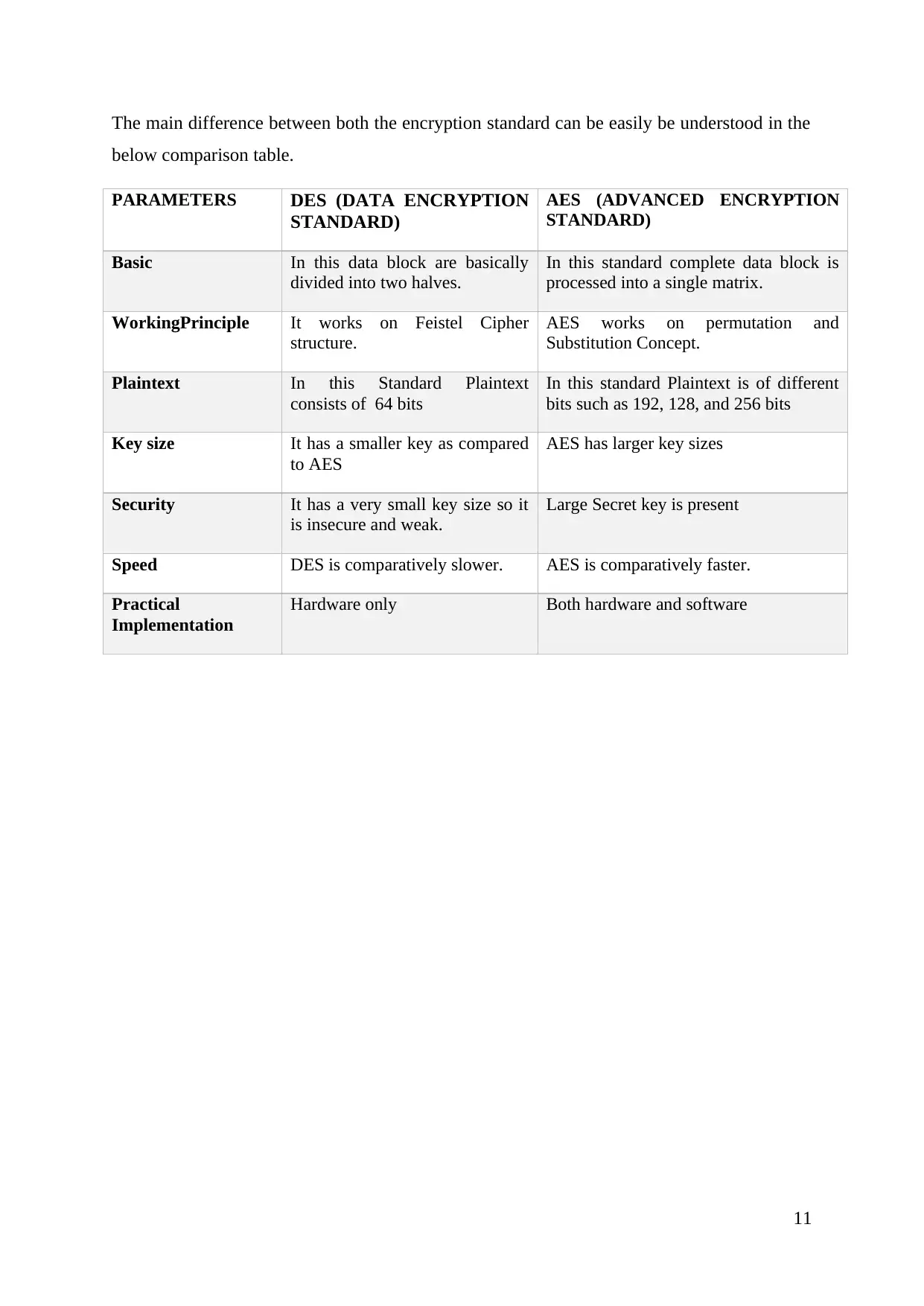
The main difference between both the encryption standard can be easily be understood in the
below comparison table.
PARAMETERS DES (DATA ENCRYPTION
STANDARD)
AES (ADVANCED ENCRYPTION
STANDARD)
Basic In this data block are basically
divided into two halves.
In this standard complete data block is
processed into a single matrix.
WorkingPrinciple It works on Feistel Cipher
structure.
AES works on permutation and
Substitution Concept.
Plaintext In this Standard Plaintext
consists of 64 bits
In this standard Plaintext is of different
bits such as 192, 128, and 256 bits
Key size It has a smaller key as compared
to AES
AES has larger key sizes
Security It has a very small key size so it
is insecure and weak.
Large Secret key is present
Speed DES is comparatively slower. AES is comparatively faster.
Practical
Implementation
Hardware only Both hardware and software
11
below comparison table.
PARAMETERS DES (DATA ENCRYPTION
STANDARD)
AES (ADVANCED ENCRYPTION
STANDARD)
Basic In this data block are basically
divided into two halves.
In this standard complete data block is
processed into a single matrix.
WorkingPrinciple It works on Feistel Cipher
structure.
AES works on permutation and
Substitution Concept.
Plaintext In this Standard Plaintext
consists of 64 bits
In this standard Plaintext is of different
bits such as 192, 128, and 256 bits
Key size It has a smaller key as compared
to AES
AES has larger key sizes
Security It has a very small key size so it
is insecure and weak.
Large Secret key is present
Speed DES is comparatively slower. AES is comparatively faster.
Practical
Implementation
Hardware only Both hardware and software
11

References
Henderson, A 2015, The CIA Triad: Confidentiality, Integrity, Availability - Panmore
Institute, viewed 23 March 2018,<http://panmore.com/the-cia-triad-confidentiality-integrity-
availability>
Chia, T2012, Confidentiality, Integrity, Availability: The three components of the CIA Triad,
viewed 23 March 2018,<https://security.blogoverflow.com/2012/08/confidentiality-integrity-
availability-the-three-components-of-the-cia-triad/>
Engelfriet, A 2018, The DES encryption algorithm (in Technology > Encryption @
iusmentis.com), viewed 25 March 2018,
<http://www.iusmentis.com/technology/encryption/des/>
Mason, J2017, What is Advanced Encryption Standard (AES): Beginner's Guide, viewed 25
March 2018, <https://thebestvpn.com/advanced-encryption-standard-aes/>
12
Henderson, A 2015, The CIA Triad: Confidentiality, Integrity, Availability - Panmore
Institute, viewed 23 March 2018,<http://panmore.com/the-cia-triad-confidentiality-integrity-
availability>
Chia, T2012, Confidentiality, Integrity, Availability: The three components of the CIA Triad,
viewed 23 March 2018,<https://security.blogoverflow.com/2012/08/confidentiality-integrity-
availability-the-three-components-of-the-cia-triad/>
Engelfriet, A 2018, The DES encryption algorithm (in Technology > Encryption @
iusmentis.com), viewed 25 March 2018,
<http://www.iusmentis.com/technology/encryption/des/>
Mason, J2017, What is Advanced Encryption Standard (AES): Beginner's Guide, viewed 25
March 2018, <https://thebestvpn.com/advanced-encryption-standard-aes/>
12
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




