CSC8419 - Cryptography and Security: Debian ISO Verification & Key Gen
VerifiedAdded on 2024/05/29
|12
|1284
|406
Homework Assignment
AI Summary
This assignment solution for CSC8419 Cryptography and Security covers several key tasks, including the verification of a Debian DVD ISO image using GPG and checksums, and the generation of public/private keys along with shared secret keys using provided global public parameters. It details the steps involved in verifying the authenticity of the Debian DVD image, generating and extracting public keys, and creating shared secret keys. Additionally, the assignment includes an abstract and introduction to symmetric key block cipher algorithms, specifically DES (Data Encryption Standard) and AES (Advanced Encryption Standard), discussing their mechanisms, advantages, disadvantages, and future aspects. The report concludes with a recommendation for AES due to its enhanced security and simpler structure, providing a comprehensive overview of cryptographic techniques and their practical applications.

CSC8419
Assignment 2
Cryptography and Security
Student Name:
Student Number:
Assignment 2
Cryptography and Security
Student Name:
Student Number:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1..........................................................................................................................................................2
Task 2..........................................................................................................................................................5
Task 3..........................................................................................................................................................9
Task 4........................................................................................................................................................10
Reference..................................................................................................................................................12
1
Task 1..........................................................................................................................................................2
Task 2..........................................................................................................................................................5
Task 3..........................................................................................................................................................9
Task 4........................................................................................................................................................10
Reference..................................................................................................................................................12
1

Task 1
Verification of Debian DVD ISO image
Download all the files from thelink: https://goo.gl/8CNeyc . For completeness, MD5is done having ISO
image long with its signature.
Firstly, all the filesgets listed in the directory so that every data is placed is placed at the
appropriate place
Secondly, using the GNU Privacy Guard (GPG) check for the correct signature in MD5
On the system, there is no public key possibly during the first time running of this command.
From this command, the ID got is = ’6294BE9B’ and after this public key can easily be retrieved
as shown in further steps.
Thirdly, download the public using the ID ‘6294BE9B’ and the debian key server:
2
Verification of Debian DVD ISO image
Download all the files from thelink: https://goo.gl/8CNeyc . For completeness, MD5is done having ISO
image long with its signature.
Firstly, all the filesgets listed in the directory so that every data is placed is placed at the
appropriate place
Secondly, using the GNU Privacy Guard (GPG) check for the correct signature in MD5
On the system, there is no public key possibly during the first time running of this command.
From this command, the ID got is = ’6294BE9B’ and after this public key can easily be retrieved
as shown in further steps.
Thirdly, download the public using the ID ‘6294BE9B’ and the debian key server:
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Fourthly, verify the signature available for both the checksum files
The statement occur after running command is “Good signature from "Debian CD signing key
<debian-cd@lists.debian.org>” and this appears to provide the confirmation of the authenticity
of the Debian DVD image. After this, the fingerprint key which is generated having value is‘DF9B
9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B’ can be used to compare with the listed
value in https://www.debian.org/CD/verify . From the comparison with the fingerprint key, the
following result appears.
3
The statement occur after running command is “Good signature from "Debian CD signing key
<debian-cd@lists.debian.org>” and this appears to provide the confirmation of the authenticity
of the Debian DVD image. After this, the fingerprint key which is generated having value is‘DF9B
9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B’ can be used to compare with the listed
value in https://www.debian.org/CD/verify . From the comparison with the fingerprint key, the
following result appears.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
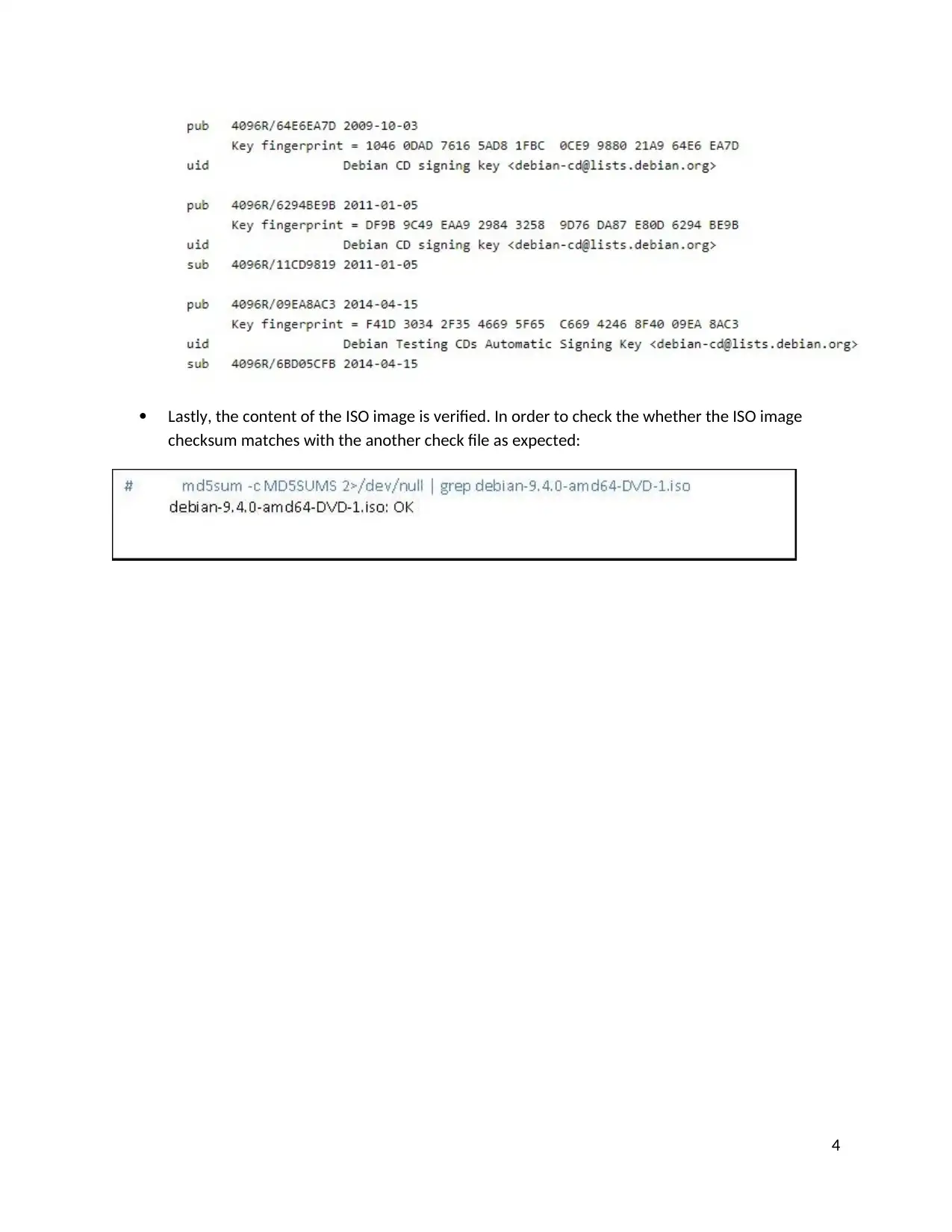
Lastly, the content of the ISO image is verified. In order to check the whether the ISO image
checksum matches with the another check file as expected:
4
checksum matches with the another check file as expected:
4
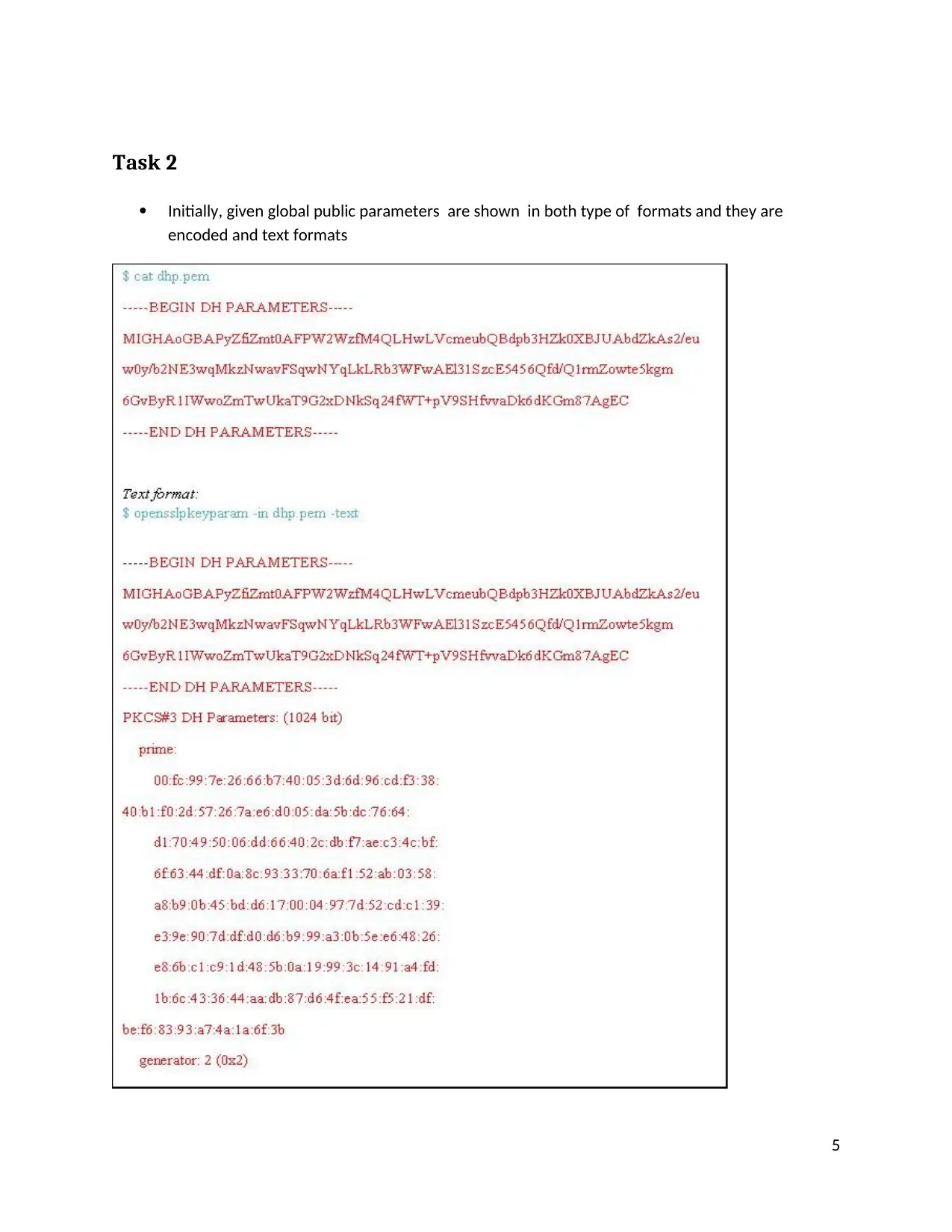
Task 2
Initially, given global public parameters are shown in both type of formats and they are
encoded and text formats
5
Initially, given global public parameters are shown in both type of formats and they are
encoded and text formats
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

From the given public parameters, generate the public/private key to use further
Now after, generating the key, extract the public key
6
Now after, generating the key, extract the public key
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
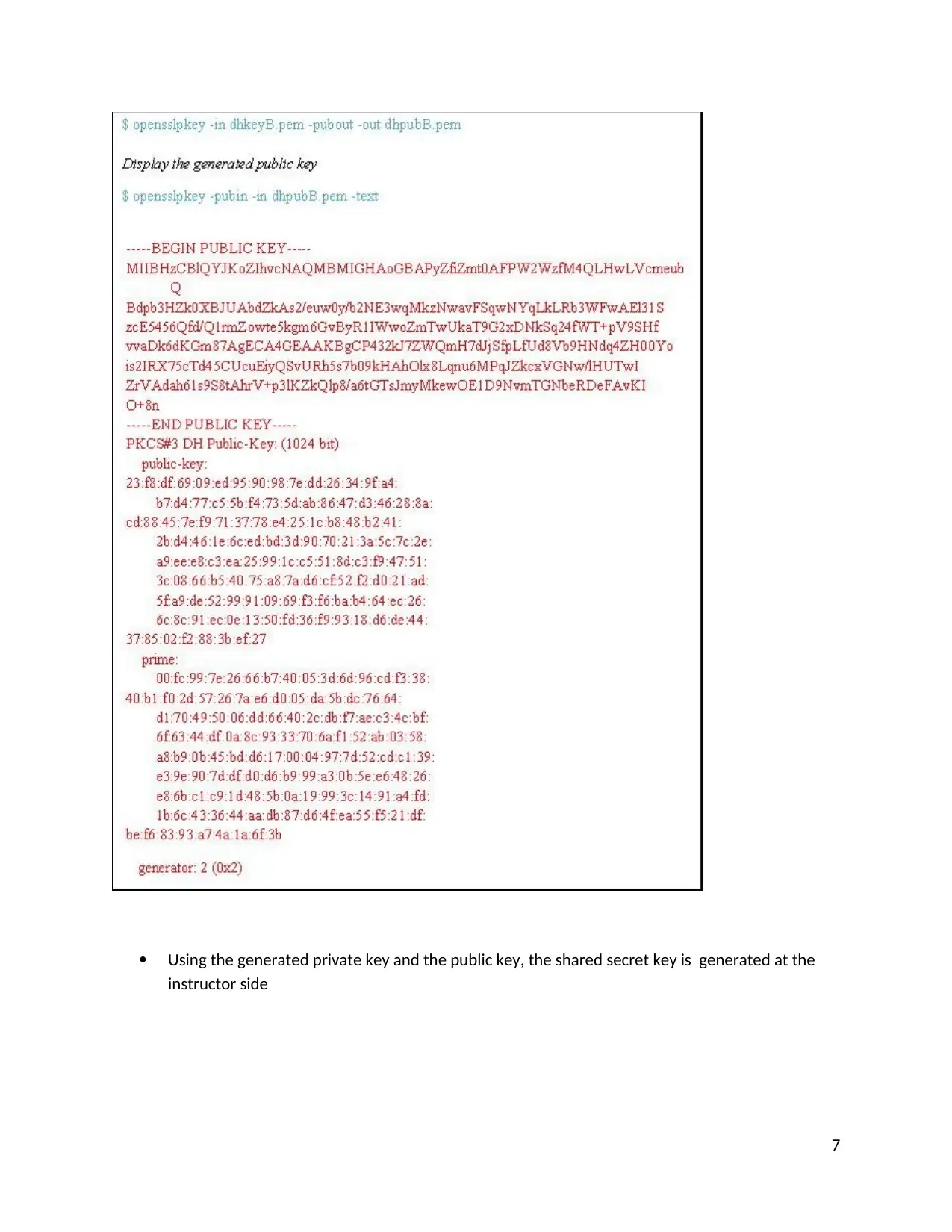
Using the generated private key and the public key, the shared secret key is generated at the
instructor side
7
instructor side
7
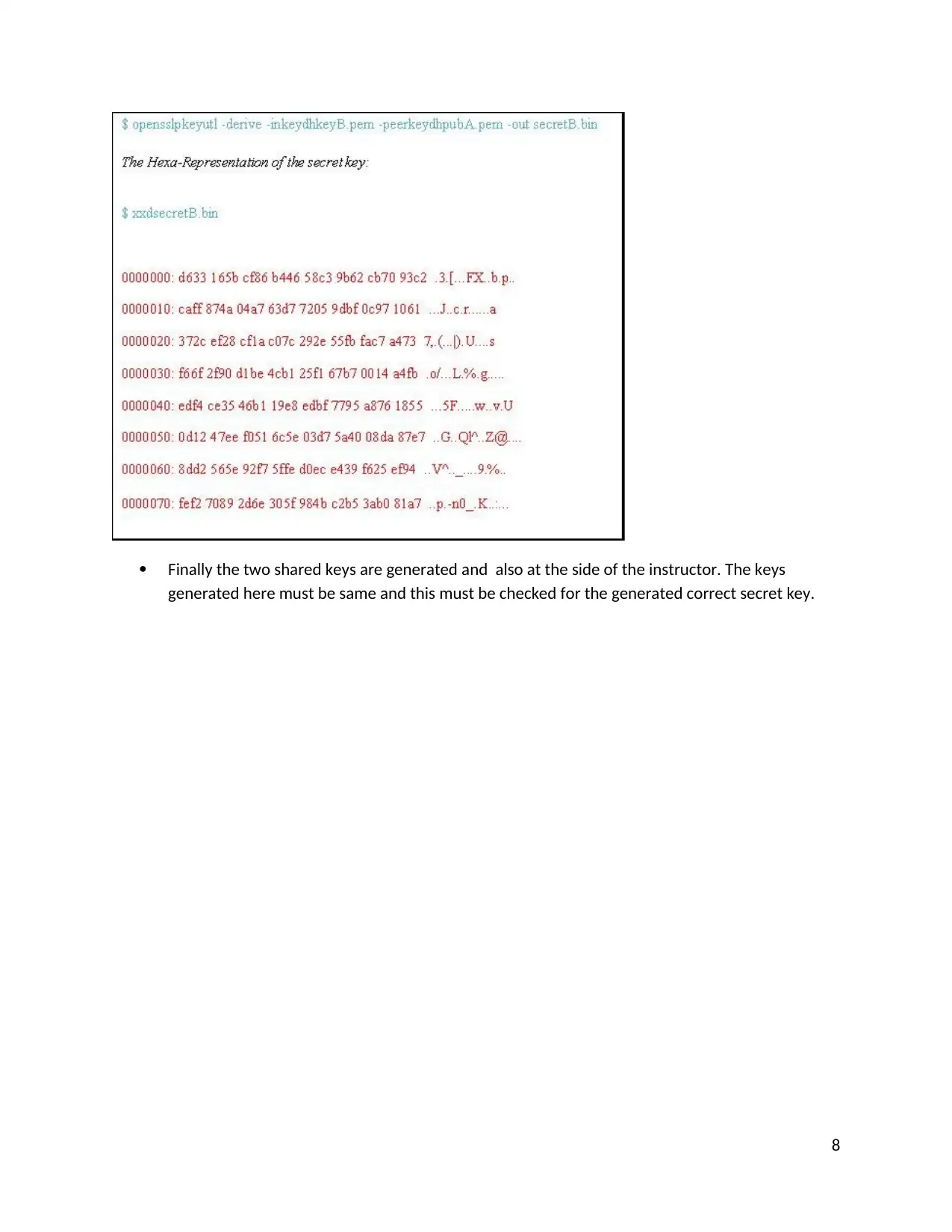
Finally the two shared keys are generated and also at the side of the instructor. The keys
generated here must be same and this must be checked for the generated correct secret key.
8
generated here must be same and this must be checked for the generated correct secret key.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Task 4
Abstract
In the information technology, security system requires different key aspects of transmitting confidential
data and this data is shared over non-secured network such as internet. There are different security
mechanisms that will help in securing the data in their transfer. In such techniques, there is a
mechanism called cryptography which protect the data from the unwanted individuals by converting the
data into some another form. Some of the examples of cryptography which includessymmetric key block
cipher algorithmsareDES, AES, blow fish, RC2 and so on (S, Rasmi and Varghese, 2014).
Introduction
This report is developed in context to provide information regarding symmetric key block cipher
algorithms. Here the discussion is on the two most important algorithms of cryptography and they are
DES (Data Encryption Standard) and AES (Advanced Encryption Standard).
DES (Data Encryption Standard)
This standard is block encryption which encrypts data in the form of blocks of 64 bits and these blocks is
taken considering a 56 bit key. This size is used for same encryption and decryption (Simmons, 2016).
Mechanism working
In working, a 16 cycle Feistel System is used for data encryption and decryption where it uses the 56 bit
key permuted into 16 sub keys for 48 bits. In this, one permuted bit key is used in each cycle and this
similar process is done in decryption but with reverse order.
Advantages
Simple method for 64 bit encryption
Hard to attack
Uses cipher key which can be expanded
Dis- Advantages
Low scalability
Limited security(Oukili and Bri, 2017).
Future aspects
This can be used in more advanced transactions in support of bank. It can be used for more complex
routers and remote access servers. For future, this standard can be used in several applications to
secure data.
9
Abstract
In the information technology, security system requires different key aspects of transmitting confidential
data and this data is shared over non-secured network such as internet. There are different security
mechanisms that will help in securing the data in their transfer. In such techniques, there is a
mechanism called cryptography which protect the data from the unwanted individuals by converting the
data into some another form. Some of the examples of cryptography which includessymmetric key block
cipher algorithmsareDES, AES, blow fish, RC2 and so on (S, Rasmi and Varghese, 2014).
Introduction
This report is developed in context to provide information regarding symmetric key block cipher
algorithms. Here the discussion is on the two most important algorithms of cryptography and they are
DES (Data Encryption Standard) and AES (Advanced Encryption Standard).
DES (Data Encryption Standard)
This standard is block encryption which encrypts data in the form of blocks of 64 bits and these blocks is
taken considering a 56 bit key. This size is used for same encryption and decryption (Simmons, 2016).
Mechanism working
In working, a 16 cycle Feistel System is used for data encryption and decryption where it uses the 56 bit
key permuted into 16 sub keys for 48 bits. In this, one permuted bit key is used in each cycle and this
similar process is done in decryption but with reverse order.
Advantages
Simple method for 64 bit encryption
Hard to attack
Uses cipher key which can be expanded
Dis- Advantages
Low scalability
Limited security(Oukili and Bri, 2017).
Future aspects
This can be used in more advanced transactions in support of bank. It can be used for more complex
routers and remote access servers. For future, this standard can be used in several applications to
secure data.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

AES(Advanced Encryption Standard)
This standard form of encryption uses the block encryption which encrypts data in the form of blocks of
128, 192 or 256 bits. The rounds and cycle used for the permuted sub keys are according to the used
blocks of bits (Kumar and Farik, 2017).
Mechanism working
In one round, there are four operations:
Substitute byte transformation
Shift-Rows Transformation
Mix-Column transformation
Add round key transformation
Advantages
Robust security
High length of bits used
Useful for wider range of applications
Less probability of hacking
Dis- Advantages
Structure is too simpler
Every block uses the same encryption method
Software implementation is difficult(Sharifian and Soltani, 2015)
Future aspects
AES technique is used widely in the different sector to protect the sensitive information. According to
the researchers, this technique is going to be best solution in future (Arai and Okazaki, 2013).
Recommendations
After analysing both the symmetric key block cipher algorithms, it was found that Advanced Encryption
Standard is better solution. This is so because this algorithm provides better security and simpler
structure to understand. In addition, this technique has less possibility of being hacked (Bhat, Ali and
Gupta, 2015).
Conclusion
This report will provide the details of the two major algorithms of symmetric key block cipher algorithms
and they are AES (Advanced Encryption Standard) and DES (Data Encryption Standard). It also includes
their advantages and disadvantages in addition to their future possibilities and recommendations.
10
This standard form of encryption uses the block encryption which encrypts data in the form of blocks of
128, 192 or 256 bits. The rounds and cycle used for the permuted sub keys are according to the used
blocks of bits (Kumar and Farik, 2017).
Mechanism working
In one round, there are four operations:
Substitute byte transformation
Shift-Rows Transformation
Mix-Column transformation
Add round key transformation
Advantages
Robust security
High length of bits used
Useful for wider range of applications
Less probability of hacking
Dis- Advantages
Structure is too simpler
Every block uses the same encryption method
Software implementation is difficult(Sharifian and Soltani, 2015)
Future aspects
AES technique is used widely in the different sector to protect the sensitive information. According to
the researchers, this technique is going to be best solution in future (Arai and Okazaki, 2013).
Recommendations
After analysing both the symmetric key block cipher algorithms, it was found that Advanced Encryption
Standard is better solution. This is so because this algorithm provides better security and simpler
structure to understand. In addition, this technique has less possibility of being hacked (Bhat, Ali and
Gupta, 2015).
Conclusion
This report will provide the details of the two major algorithms of symmetric key block cipher algorithms
and they are AES (Advanced Encryption Standard) and DES (Data Encryption Standard). It also includes
their advantages and disadvantages in addition to their future possibilities and recommendations.
10

Reference
Arai, K. & Okazaki, H. 2013, "Formalization of the Advanced Encryption Standard. Part I", Formalized
Mathematics, vol. 21, no. 3, pp. 171-184.
Bhat, B., Ali, A.W. & Gupta, A. 2015, "DES and AES performance evaluation", IEEE, , pp. 887.
Kumar, J. &Farik, M. 2017, "Cracking Advanced Encryption Standard-A Review", International Journal
of Scientific & Technology Research, vol. 6, no. 7, pp. 101-105.
Oukili, S. &Bri, S. 2017, "High throughput FPGA implementation of Advanced Encryption Standard
algorithm", TELKOMNIKA, vol. 15, no. 1, pp. 494
S,Rasmi,P. & Varghese, P. 2014, "An efficient mixed mode and paired cipher text cryptographic
algorithm for effective key distribution", International Journal of Communication Systems, vol. 27,
no. 11, pp. 2593-2603
Simmons, G.J. 2016, Data Encryption Standard (DES), Encyclopædia Britannica Inc.
Soltani, A. &Sharifian, S. 2015, "An ultra-high throughput and fully pipelined implementation of AES
algorithm on FPGA", Microprocessors and Microsystems, vol. 39, no. 7, pp. 480-493
11
Arai, K. & Okazaki, H. 2013, "Formalization of the Advanced Encryption Standard. Part I", Formalized
Mathematics, vol. 21, no. 3, pp. 171-184.
Bhat, B., Ali, A.W. & Gupta, A. 2015, "DES and AES performance evaluation", IEEE, , pp. 887.
Kumar, J. &Farik, M. 2017, "Cracking Advanced Encryption Standard-A Review", International Journal
of Scientific & Technology Research, vol. 6, no. 7, pp. 101-105.
Oukili, S. &Bri, S. 2017, "High throughput FPGA implementation of Advanced Encryption Standard
algorithm", TELKOMNIKA, vol. 15, no. 1, pp. 494
S,Rasmi,P. & Varghese, P. 2014, "An efficient mixed mode and paired cipher text cryptographic
algorithm for effective key distribution", International Journal of Communication Systems, vol. 27,
no. 11, pp. 2593-2603
Simmons, G.J. 2016, Data Encryption Standard (DES), Encyclopædia Britannica Inc.
Soltani, A. &Sharifian, S. 2015, "An ultra-high throughput and fully pipelined implementation of AES
algorithm on FPGA", Microprocessors and Microsystems, vol. 39, no. 7, pp. 480-493
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12