Cryptography and Security - Assignment 2: Verification, Validation, and Encryption Algorithms
VerifiedAdded on 2024/05/29
|11
|1366
|462
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

CSC8419
Cryptography and Security
Assignment 2
Cryptography and Security
Assignment 2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TASK 1
In this Task, verification and validation would be done on Debian DVD (Digital video disc) ISO
image. All the necessary files are downloaded from link https://goo.gl/8CNeyc and ISO
(International organization for standard) image along with the signature files of MD5 are ready
for the purpose of completeness.
Firstly there is a listing of each and every file present in the directory to ensure that
everything is present in its designated place.
Secondly, proper checking is done for the precise and accurate signature with the help of free
GNU privacy guard (gpg) which is done for MD5. Therefore,
While the command is run for the very first time then the public key might not be present in
the system which we got from ‘6294BE9B’ ID. This command from which public keys can
be retrieved are as follows:
Thirdly the public key is been downloaded with the help of ID ‘6294BE9B’the Debian server
keyring:
In this Task, verification and validation would be done on Debian DVD (Digital video disc) ISO
image. All the necessary files are downloaded from link https://goo.gl/8CNeyc and ISO
(International organization for standard) image along with the signature files of MD5 are ready
for the purpose of completeness.
Firstly there is a listing of each and every file present in the directory to ensure that
everything is present in its designated place.
Secondly, proper checking is done for the precise and accurate signature with the help of free
GNU privacy guard (gpg) which is done for MD5. Therefore,
While the command is run for the very first time then the public key might not be present in
the system which we got from ‘6294BE9B’ ID. This command from which public keys can
be retrieved are as follows:
Thirdly the public key is been downloaded with the help of ID ‘6294BE9B’the Debian server
keyring:

Here the signature of together checksum files is been verified.
The line- “Good signature from "Debian CD signing key <debian–cd@lists.debian.org”
authorizes the validation of Debian DVD image. The generated key fingerprint which is
DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B can be used and then compare
it to the one’s listed in this link- https://www.debian.org/CD/verify. This comparison presents
with the key fingerprint matches.
The line- “Good signature from "Debian CD signing key <debian–cd@lists.debian.org”
authorizes the validation of Debian DVD image. The generated key fingerprint which is
DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B can be used and then compare
it to the one’s listed in this link- https://www.debian.org/CD/verify. This comparison presents
with the key fingerprint matches.
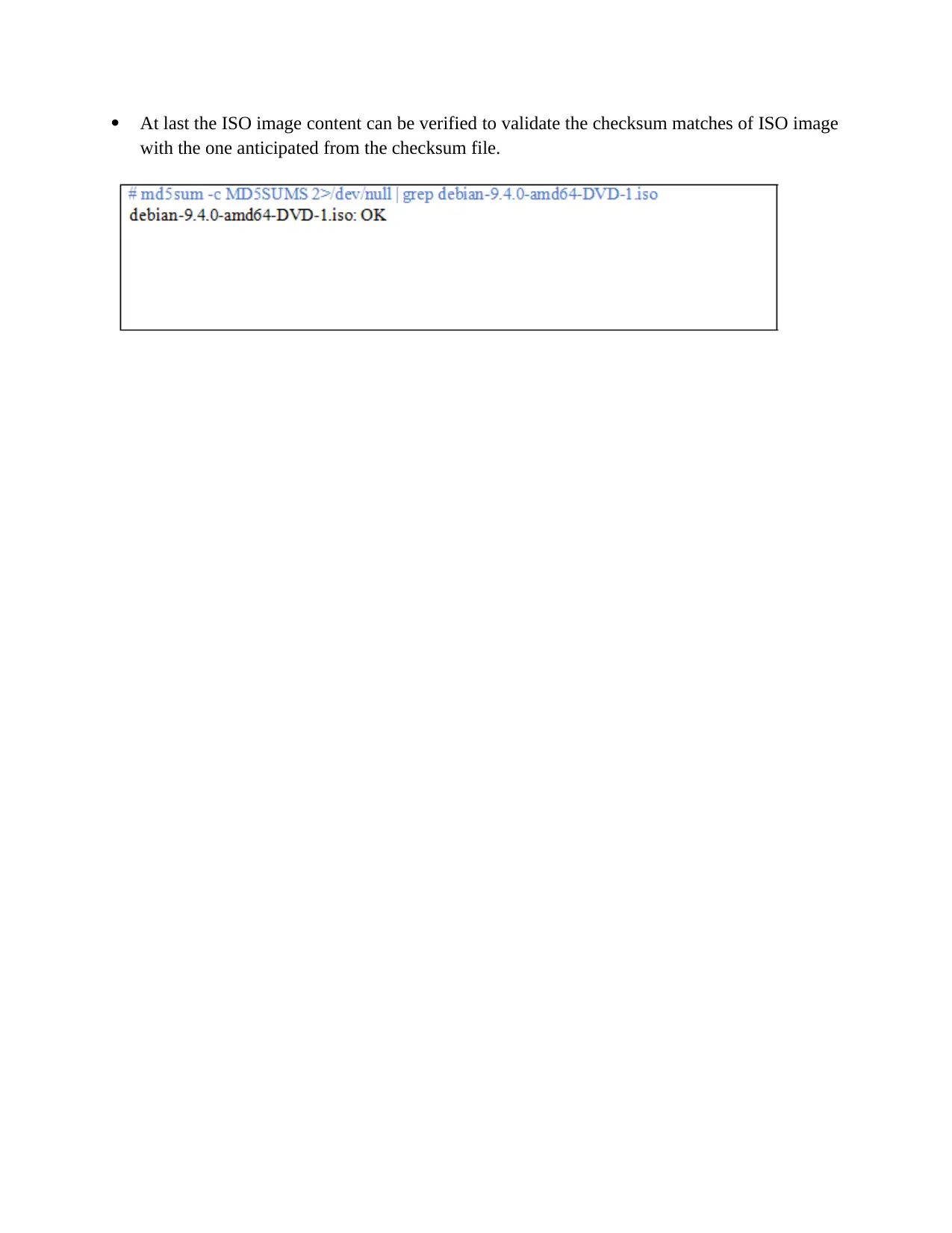
At last the ISO image content can be verified to validate the checksum matches of ISO image
with the one anticipated from the checksum file.
with the one anticipated from the checksum file.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
TASK 2
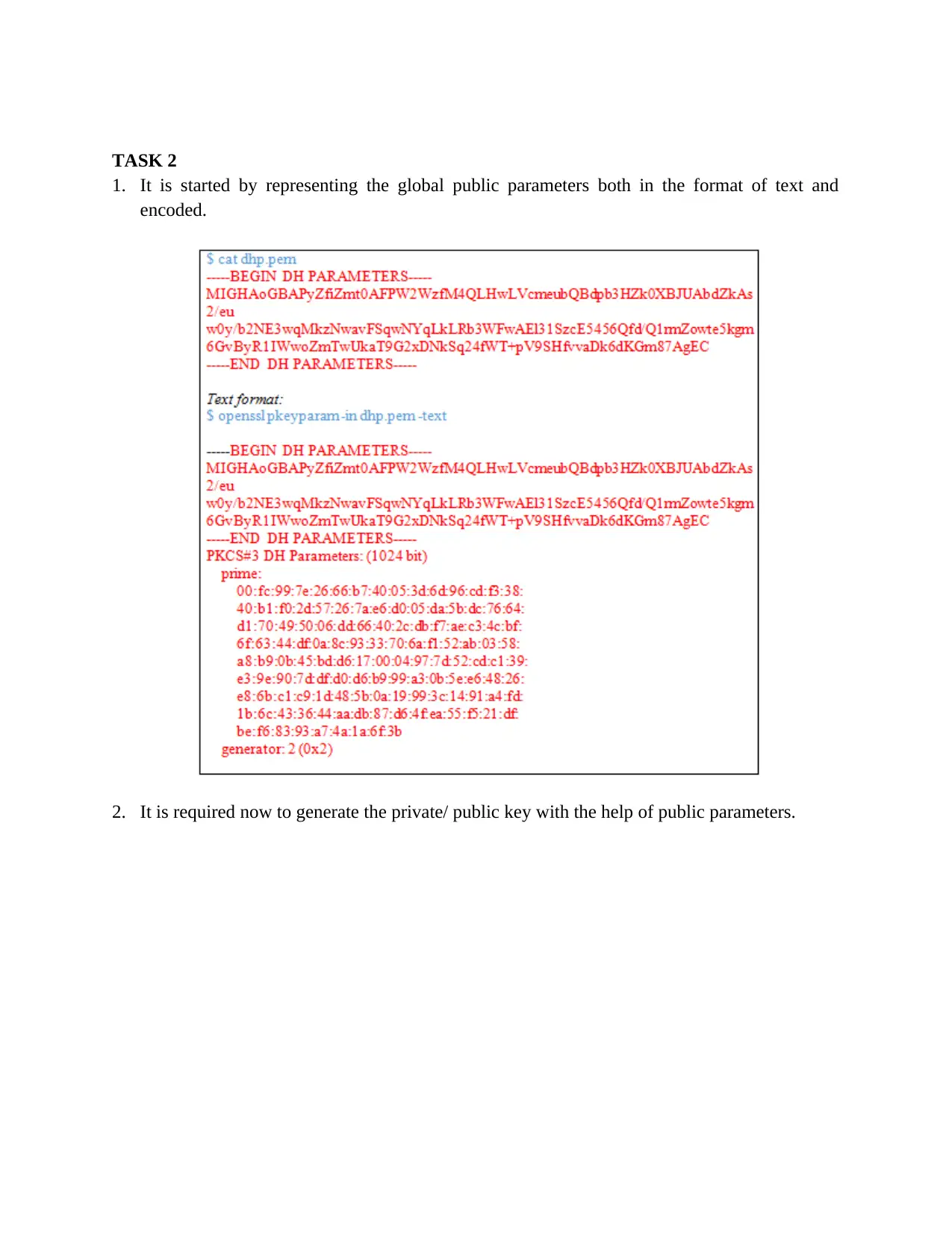
1. It is started by representing the global public parameters both in the format of text and
encoded.
2. It is required now to generate the private/ public key with the help of public parameters.
1. It is started by representing the global public parameters both in the format of text and
encoded.
2. It is required now to generate the private/ public key with the help of public parameters.
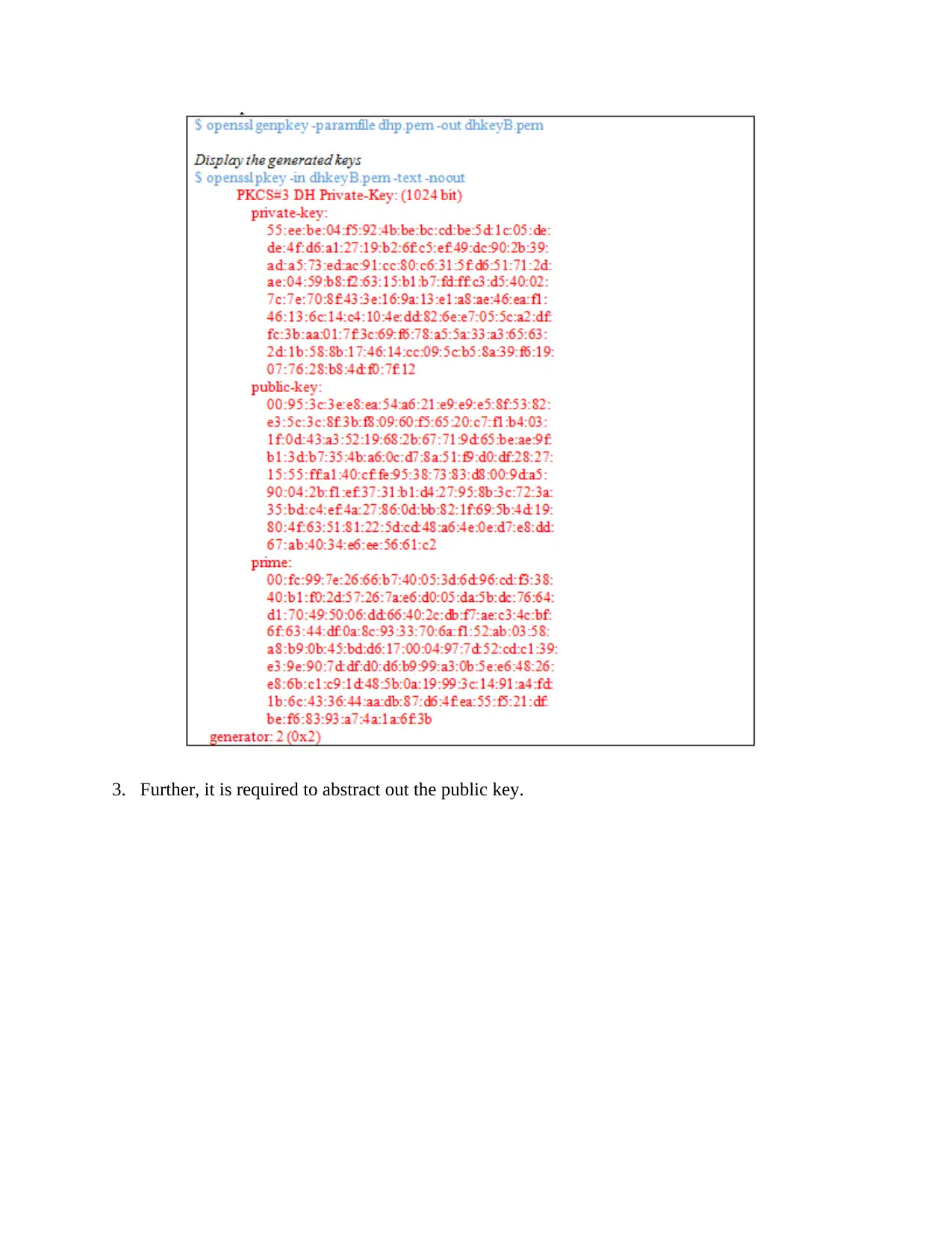
3. Further, it is required to abstract out the public key.
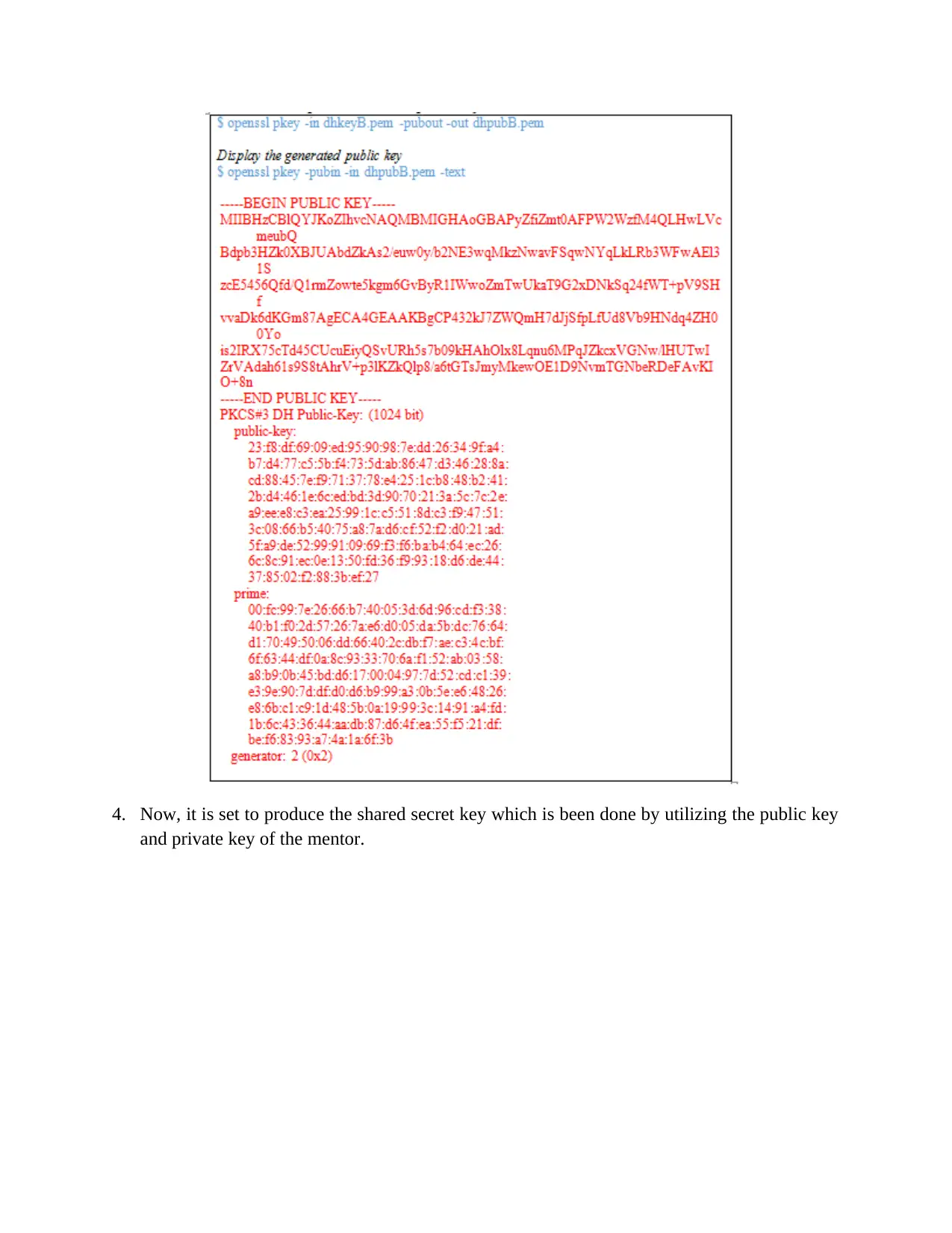
4. Now, it is set to produce the shared secret key which is been done by utilizing the public key
and private key of the mentor.
and private key of the mentor.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
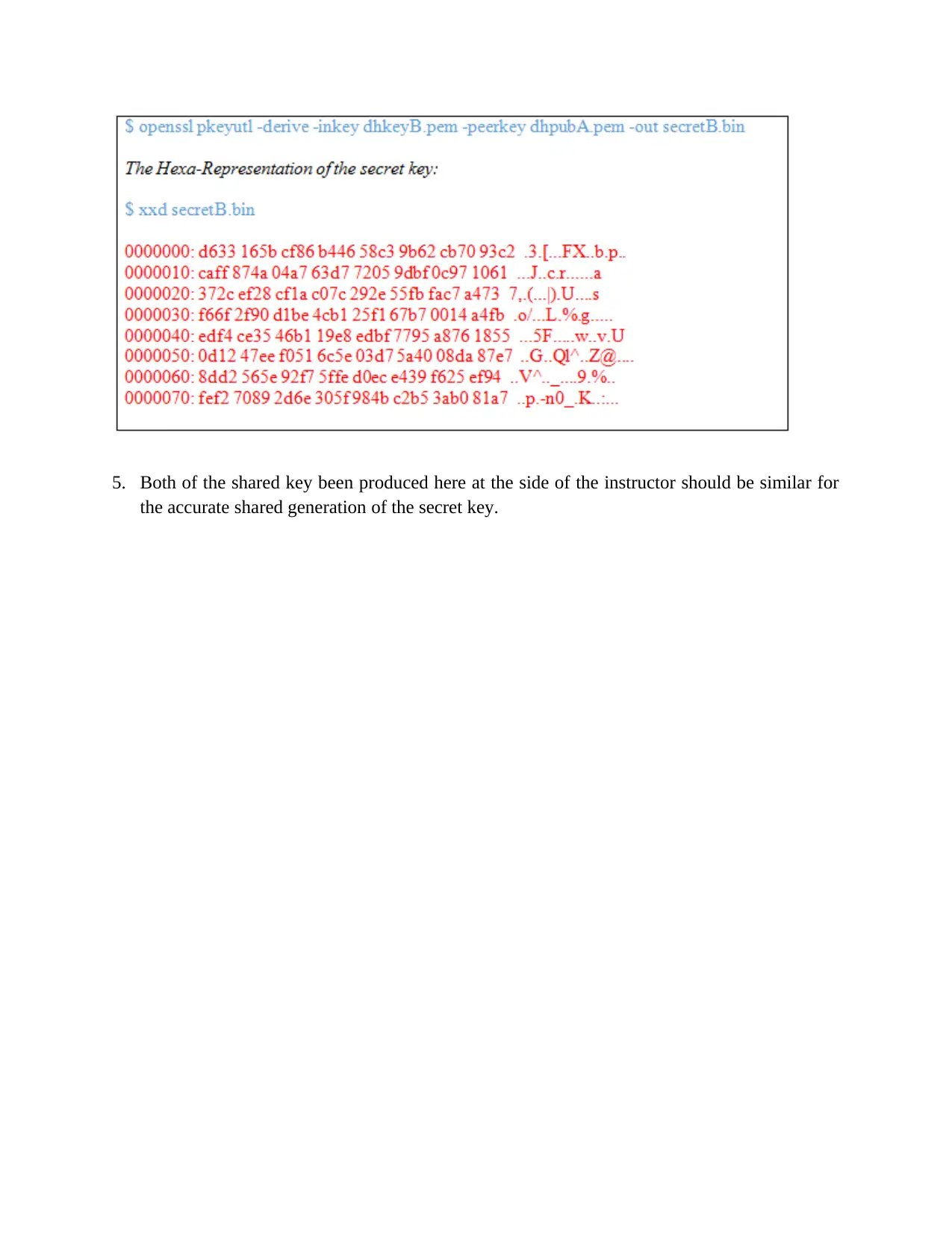
5. Both of the shared key been produced here at the side of the instructor should be similar for
the accurate shared generation of the secret key.
the accurate shared generation of the secret key.

TASK 4
AES (Advanced Encryption Standard) and DES (Data Encryption Standard)
Abstract
Both DES and AES are known as a symmetric block cipher and in this AES was announced to
overcome with all the drawbacks of DES. Since DES has a smaller key size which allows less
security to overcome such introduced triple DES but rather it turned to be slower. Later,
Advanced encryption standard was been introduced and the basic difference among AES and
DES is that in AES the complete block is processed to attain the ciphertext whereas in DES the
plaintext block is segregated to two halves prior to the starting of the main algorithm.
Introduction
Here, proper explanation will be done of DES and AES along with each one of its advantages
and disadvantages. The main problem lies in choosing whether network data needs to be
encrypted with DES encryption algorithm or AES encryption algorithm because it is now a
major security matter.
DES
DES is known as (shared secret key) symmetric block cipher having a 56 bits key-length.
Originally the federal government developed DES encryption in order to proffer government
communications with cryptographic security. To present the inadequacy of DES and also it
should not be utilized in importance system; many challenges were funded to watch how much
time it would be taking the message to decrypt.
The principle of DES work is Feistel cipher structure and plaintext has 64 bits. In comparison to
AES, DES has comparatively smaller key size. It is comparatively slower and contains a smaller
key which tends to be less secure (Simmons, 2016).
Advantages of DES
It is encountered while interfacing with the legacy services and commercial products.
It is the predecessor which encrypts using 56-bit key having 64-bit blocks.
It can extend its key length by applying 3 DES operations which goes with 0 key encryption,
key 1 decryption and key 2 encryption (Qin, Deng, Liu & Ma, 2015).
Disadvantages of DES
Each block is been encrypted to the isolation which is creating a security vulnerability.
The three keys may be related.
Its key length is 56 bits only.
AES (Advanced Encryption Standard) and DES (Data Encryption Standard)
Abstract
Both DES and AES are known as a symmetric block cipher and in this AES was announced to
overcome with all the drawbacks of DES. Since DES has a smaller key size which allows less
security to overcome such introduced triple DES but rather it turned to be slower. Later,
Advanced encryption standard was been introduced and the basic difference among AES and
DES is that in AES the complete block is processed to attain the ciphertext whereas in DES the
plaintext block is segregated to two halves prior to the starting of the main algorithm.
Introduction
Here, proper explanation will be done of DES and AES along with each one of its advantages
and disadvantages. The main problem lies in choosing whether network data needs to be
encrypted with DES encryption algorithm or AES encryption algorithm because it is now a
major security matter.
DES
DES is known as (shared secret key) symmetric block cipher having a 56 bits key-length.
Originally the federal government developed DES encryption in order to proffer government
communications with cryptographic security. To present the inadequacy of DES and also it
should not be utilized in importance system; many challenges were funded to watch how much
time it would be taking the message to decrypt.
The principle of DES work is Feistel cipher structure and plaintext has 64 bits. In comparison to
AES, DES has comparatively smaller key size. It is comparatively slower and contains a smaller
key which tends to be less secure (Simmons, 2016).
Advantages of DES
It is encountered while interfacing with the legacy services and commercial products.
It is the predecessor which encrypts using 56-bit key having 64-bit blocks.
It can extend its key length by applying 3 DES operations which goes with 0 key encryption,
key 1 decryption and key 2 encryption (Qin, Deng, Liu & Ma, 2015).
Disadvantages of DES
Each block is been encrypted to the isolation which is creating a security vulnerability.
The three keys may be related.
Its key length is 56 bits only.

Block size is 64 bits (Li, Zhang, Chen & Xiang, 2018).
AES
AES is also known as symmetric key block cipher which was published in 2001 by the National
Institute of standards and technology. Further, it was been introduced in order to replace DES to
a use-up algorithm which was quite slower and very small cipher key.
It has 128-bit secret key and 128-bit plaintext to form together a 128-bit block depicted as 4*4
square matrix which undergoes an initial transformation (Kumar & Farik, 2017).
Advantages of AES
It is more mathematically elegant and efficient cryptographic algorithm.
It allows users to choose among 256-bit key, 192-bit or 128-bit key.
It is secure
It is considered with modern standard and successor.
Decryption and encryption are done from the particular key in AES (Wadi & Zainal,
2013).
Disadvantages of AES
It uses very simple algebraic structure.
It is tough to execute with software.
Each block is been encrypted in the similar way (Li & Liu, 2013).
Recommendation
AES is the replacement of DES since standard symmetric algorithm encryption for the US
federal organization. AES uses 128-bit blocks and accepts any of 256, 192 or 128 bits and also is
effective in both of the hardware and software. Also, it was been chosen via an open competition
including many cryptographers. Basically, AES is the best amongst both.
Conclusion
DES is known as the older algorithm and also AES is called as the advanced algorithm. Thus, it
tends to be faster and secure compared to DES. AES is unbreakable and uses substitution-
permutation whereas DES is breakable and uses balanced Feistel structure. In all, AES gets to be
the better among two.
AES
AES is also known as symmetric key block cipher which was published in 2001 by the National
Institute of standards and technology. Further, it was been introduced in order to replace DES to
a use-up algorithm which was quite slower and very small cipher key.
It has 128-bit secret key and 128-bit plaintext to form together a 128-bit block depicted as 4*4
square matrix which undergoes an initial transformation (Kumar & Farik, 2017).
Advantages of AES
It is more mathematically elegant and efficient cryptographic algorithm.
It allows users to choose among 256-bit key, 192-bit or 128-bit key.
It is secure
It is considered with modern standard and successor.
Decryption and encryption are done from the particular key in AES (Wadi & Zainal,
2013).
Disadvantages of AES
It uses very simple algebraic structure.
It is tough to execute with software.
Each block is been encrypted in the similar way (Li & Liu, 2013).
Recommendation
AES is the replacement of DES since standard symmetric algorithm encryption for the US
federal organization. AES uses 128-bit blocks and accepts any of 256, 192 or 128 bits and also is
effective in both of the hardware and software. Also, it was been chosen via an open competition
including many cryptographers. Basically, AES is the best amongst both.
Conclusion
DES is known as the older algorithm and also AES is called as the advanced algorithm. Thus, it
tends to be faster and secure compared to DES. AES is unbreakable and uses substitution-
permutation whereas DES is breakable and uses balanced Feistel structure. In all, AES gets to be
the better among two.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

References
Kumar, J. & Farik, M. 2017, "Cracking Advanced Encryption Standard-A Review",
International Journal of Scientific & Technology Research, vol. 6, no. 7, pp. 101-105.
Li, J. & Liu, H. 2013, "Colour image encryption based on advanced encryption standard
algorithm with two-dimensional chaotic map", IET Information Security, vol. 7, no. 4, pp.
265-270.
Li, J., Zhang, Y., Chen, X. & Xiang, Y. 2018, "Secure attribute-based data sharing for
resource-limited users in cloud computing", Computers & Security, vol. 72, pp. 1.
Qin, B., Deng, R.H., Liu, S. & Ma, S. 2015, "Attribute-Based Encryption With Efficient
Verifiable Outsourced Decryption", IEEE Transactions on Information Forensics and
Security, vol. 10, no. 7, pp. 1384-1393.
Simmons, G.J. 2016, Data Encryption Standard (DES), Encyclopædia Britannica Inc.
WADI, S.M. & ZAINAL, N. 2013, "A LOW COST IMPLEMENTATION OF MODIFIED
ADVANCED ENCRYPTION STANDARD ALGORITHM USING 8085A
MICROPROCESSOR", Journal of Engineering Science and Technology, vol. 8, no. 4, pp.
406-415.
Kumar, J. & Farik, M. 2017, "Cracking Advanced Encryption Standard-A Review",
International Journal of Scientific & Technology Research, vol. 6, no. 7, pp. 101-105.
Li, J. & Liu, H. 2013, "Colour image encryption based on advanced encryption standard
algorithm with two-dimensional chaotic map", IET Information Security, vol. 7, no. 4, pp.
265-270.
Li, J., Zhang, Y., Chen, X. & Xiang, Y. 2018, "Secure attribute-based data sharing for
resource-limited users in cloud computing", Computers & Security, vol. 72, pp. 1.
Qin, B., Deng, R.H., Liu, S. & Ma, S. 2015, "Attribute-Based Encryption With Efficient
Verifiable Outsourced Decryption", IEEE Transactions on Information Forensics and
Security, vol. 10, no. 7, pp. 1384-1393.
Simmons, G.J. 2016, Data Encryption Standard (DES), Encyclopædia Britannica Inc.
WADI, S.M. & ZAINAL, N. 2013, "A LOW COST IMPLEMENTATION OF MODIFIED
ADVANCED ENCRYPTION STANDARD ALGORITHM USING 8085A
MICROPROCESSOR", Journal of Engineering Science and Technology, vol. 8, no. 4, pp.
406-415.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





