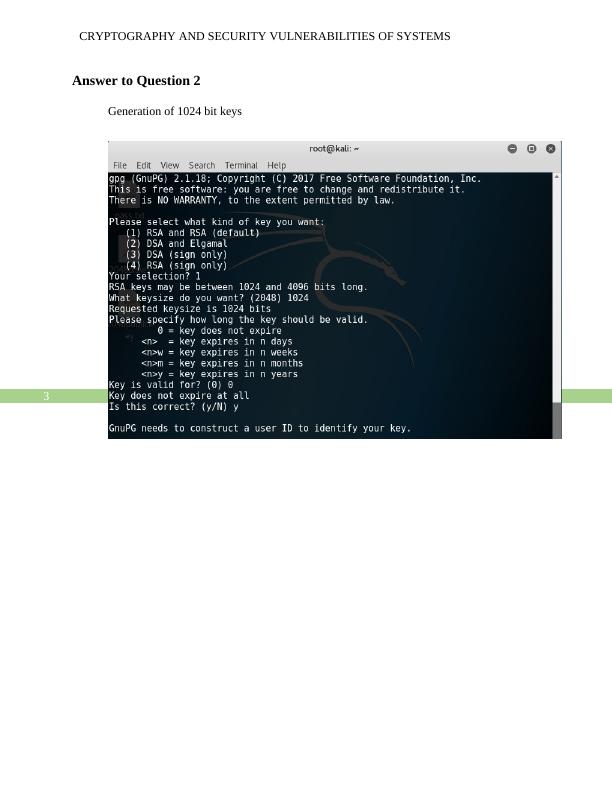
CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
Identify a recently announced security vulnerability and write a profile of the threat, including systems it attacks, how it performs its attack, mitigation strategies, scope of the threat, and concluding reflection on the adequacy of the mitigation strategies.
12 Pages794 Words21 Views
Added on 2022-08-27
CRYPTOGRAPHY AND SECURITY VULNERABILITIES OF SYSTEMS
Identify a recently announced security vulnerability and write a profile of the threat, including systems it attacks, how it performs its attack, mitigation strategies, scope of the threat, and concluding reflection on the adequacy of the mitigation strategies.
Added on 2022-08-27
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Microsoft Data Access Components Vulnerability Report
|5
|801
|430
Microsoft Data Access Components (MDAC) Vulnerability Report
|4
|1091
|417
Internet Security Threat
|4
|721
|361
Ethical Hacking: Research into OS vulnerabilities and Vulnerabilities Test Rational
|14
|2305
|257
EternalBlue: A Security Reference Code for MS17-010
|4
|977
|221
cyber Attack presentation 2022
|11
|796
|49