Ask a question from expert
Evaluate the SQLite Database Issues | Project
20 Pages7712 Words261 Views
Added on 2019-10-12
Evaluate the SQLite Database Issues | Project
Added on 2019-10-12
BookmarkShareRelated Documents
Current issues with SQLite: WEB BASED DATABASE CHALLENGESAims of the ProjectThe goal is to evaluate the SQLite database issues on web based database challenges ObjectivesThis paper provides the details about the SQLite and the challenges using the SQLite in the web based database. Here we will investigate the risk associated with the SQLite. The requirement of web based database. AbstractToday’s dynamic and rapidly evolving nature of systems enforces the special requirements onthe technology, the approach to solve the system, architecture and design of the computational structure which include the database and Web application both. Now we have multiple solutions to suggest meeting the prospects and innovative functionality have been established to discourse the persisting problems of web based database challenges. It is beneficial for us to comprehend multiple technologies and multiple approaches. To habituate with the profit and loss of the existing technologies, the investigators can check its abilities. Here In this review we are going to discuss the current issues with the SQLite database in terms of web based database challenges (Ashenfelter, 1999).We will discuss about the SQLite (what is SQLite, How it work, and the architecture of SQLite) why it is not appropriate with the web based database, what is the difficulties we handle when we use SQLite as web based database. What are the challenges in web based database. The problem of using the server less architecture using in SQLite, the benefits of using the client server architecture, how the file licking system affects the performance of the SQLite database, Why it is suitable for the small application like mobile app, iPhone, and other android apps, What types of problem we faces while we use SQLite in a large volume website database, Why the SQLite failed in high volume concurrency data handling, why the file of database is failed in sync Describing the file over writing problem. But before discussing all first we need to understand what is SQLite, how it work, and what are the challenges of today’s web base database and how we can overcome from this type of challenges (Ungaro et al., 2017).1 | Page

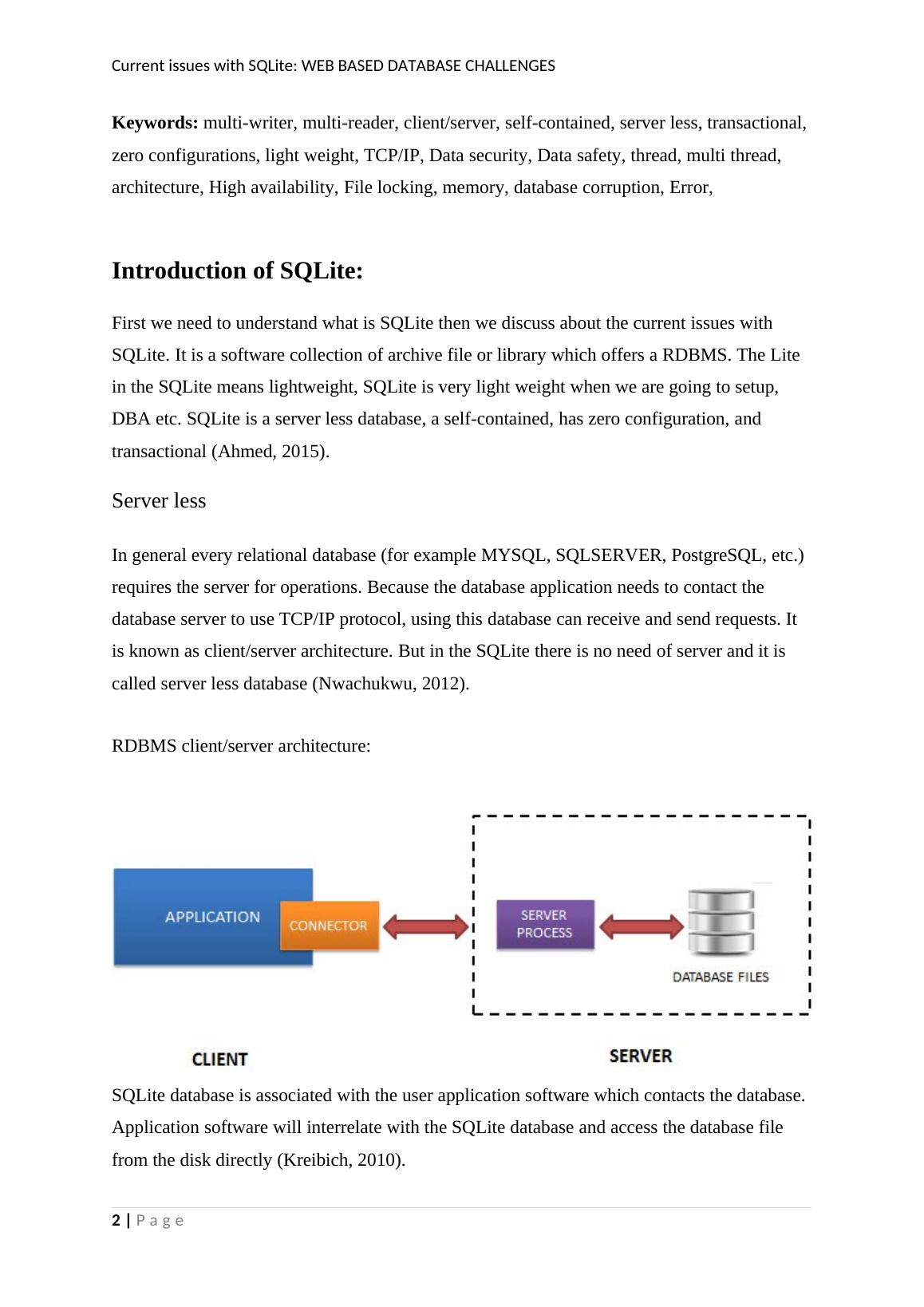
Current issues with SQLite: WEB BASED DATABASE CHALLENGESKeywords:multi-writer, multi-reader, client/server, self-contained, server less, transactional, zero configurations, light weight, TCP/IP, Data security, Data safety, thread, multi thread, architecture, High availability, File locking, memory, database corruption, Error,Introduction of SQLite:First we need to understand what is SQLite then we discuss about the current issues with SQLite. It is a software collection of archive file or library which offers a RDBMS. The Lite in the SQLite means lightweight, SQLite is very light weight when we are going to setup, DBA etc. SQLite is a server less database, a self-contained, has zero configuration, and transactional (Ahmed, 2015).Server lessIn general every relational database (for example MYSQL, SQLSERVER, PostgreSQL, etc.) requires the server for operations. Because the database application needs to contact the database server to use TCP/IP protocol, using this database can receive and send requests. It is known as client/server architecture. But in the SQLite there is no need of server and it is called server less database (Nwachukwu, 2012).RDBMS client/server architecture:SQLite database is associated with the user application software which contacts the database. Application software will interrelate with the SQLite database and access the database file from the disk directly (Kreibich, 2010).2 | Page
Current issues with SQLite: WEB BASED DATABASE CHALLENGESSQLite server-less architecture:Self-ContainedSelf-contained like independent, SQLite is self-contained, it require marginal or minimum maintenance from the external library or the operating system. That’s why it’s useful for the embedded devices like iPhones, android phones, and handheld media players etc (Alvaro, 2016).Zero-configurationSQLite has no server it is server less architecture so it does not requires server, and also no need to be configured, started, and stopped (Pereira, 2009).TransactionalSQLite is totally ACID compliant, the requests (query) and variations are Atomic, Consistent,Isolated, and Durable (Min,Kang, Kim, Lee, & Eom, 2015).Overview of web based database challenges:Today we have a number of databases available, all database have own advantage and drawbacks, The perfect technique to decide the correct database for our desired requirement is to decide our self ,the challenges we have, and what we need in our database to meet?(Mitrovic, Suraweera, Martin, & Weerasinghe, 2004).Followings are some common database challenges and the solution to overcome this type of problem:3 | Page

Current issues with SQLite: WEB BASED DATABASE CHALLENGES1. Data securityIn the recent years we have multiple examples of website or system hacked due to the database is totally unprotected on the internet (publically).The irony is that the databases weren’t stranded due to the safety issues. Now the databases come with the security which is informal to set up, fast to inform the users if anything is going incorrect (Stallings, Brow, Bauer, & Bhattacharjee, 2012). 2. PerformanceIn terms of performance we can see in the recent year the database continuously challenged tough working standards. The quantity of data we are taking in may be increasing, but to gratify our customer or user we require its processing faster, without creating them to hurdle over hoops to get there. A good database designed be made for good concert, irrespective of the hardware. If it will perform well on machines, it has good “native” performance (Florescu, & Kossmann, 2009).3. Data safetyAn information is always require to be treated in a technique that guarantees zero loss. Even in a non-relational database, they must have ACID assurances both the database and cluster. The main test for any database is in the working criteria. A noble database is always gives us the good performance as well as the transactional guarantees (Cheung, Cheung, & Suen, 2004).4. Resource utilizationIn terms of web based challenges we always assumed that database run on a best available hardware and behave accordingly. To preserve the performance in the restricted calculating capacity and they will tackle vast quantities of composite data, a database needed 100 percentout of the capitals it is occupied on for each nanosecond it is running (Kavadas et al., 2013).5. High availability4 | Page

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Distributed Systems: TCP, Mutex Algorithm, Digital Signature, Web Server and Web Servicelg...
|7
|1442
|109
Client/Server Application Componentslg...
|23
|5991
|87
Security in Cloud Computing and Preventive Methods Assignmentlg...
|14
|3523
|58