Cyber-Crime Report: Understanding Ethical Implications of Petya Attack
VerifiedAdded on 2023/01/16
|5
|828
|74
Report
AI Summary
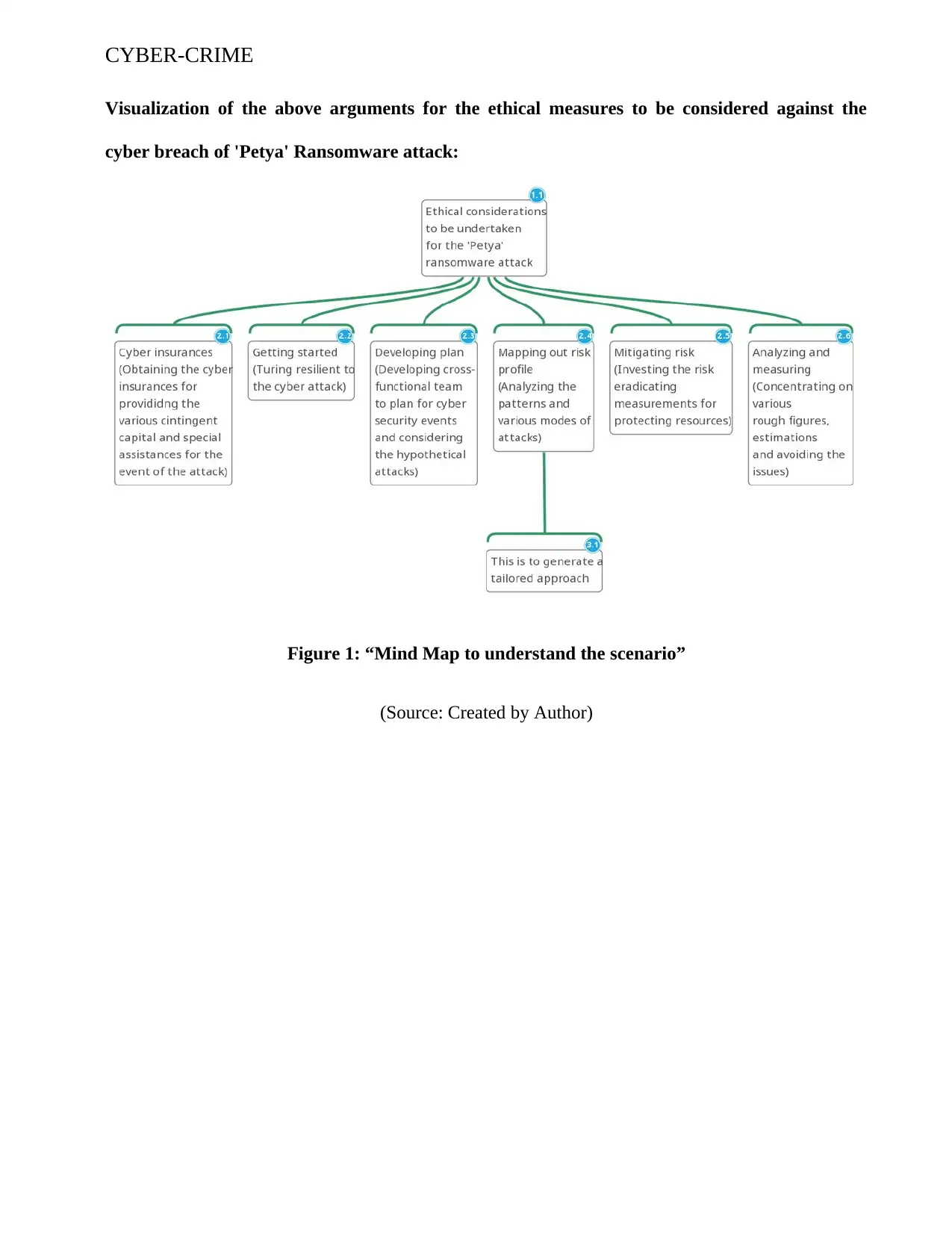
This report delves into the ethical dimensions of the Petya ransomware cyber attack, examining it through the lens of various classical ethical theories. The study begins by establishing the importance of ethics in cybersecurity, particularly in light of the actions of black-hat hackers. It then analyzes the Petya attack, a 2016 ransomware incident targeting Microsoft Windows systems, through the frameworks of utilitarianism, deontology, and social contract theory. The report discusses how each theory provides a unique perspective on the ethical implications of the attack, considering factors such as the maximization of pleasure, the fulfillment of duties and rights, and the violation of social contracts. Additionally, it explores the application of virtue ethics in fostering effective mentoring relationships within cybersecurity. The report concludes by emphasizing the need for businesses to consider ethical considerations in their incident responses and overall cybersecurity strategies, highlighting the interconnectedness of breach handling and ethical practices. References and a mind map visualization are included to support the analysis.
1 out of 5











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)