Cyber Defence For Business Analysis Report
VerifiedAdded on 2022/08/15
|11
|1814
|11
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CYBER DEFENCE
Cyber Defense in Web Based Attacks
Name of the Student
Name of the University
Author Note
Cyber Defense in Web Based Attacks
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1CYBER DEFENCE
Table of Contents
Introduction......................................................................................................................................2
Web Server Attack...........................................................................................................................2
Types of Web Server Attack........................................................................................................3
Security Practices.............................................................................................................................6
Recommended Solution...................................................................................................................7
Conclusion.......................................................................................................................................7
References........................................................................................................................................9
Table of Contents
Introduction......................................................................................................................................2
Web Server Attack...........................................................................................................................2
Types of Web Server Attack........................................................................................................3
Security Practices.............................................................................................................................6
Recommended Solution...................................................................................................................7
Conclusion.......................................................................................................................................7
References........................................................................................................................................9

2CYBER DEFENCE
Introduction
This paper aims to discuss the business security model of the IT firm that is based in
Saudi Arabia for expanding their business in the market of Middle East. This paper discusses the
various types of the web server attack and conduct a comparison between the best security
practices for keeping the personal data of the client safe in their server. This study also
recommends solution for the global expansion of the business by utilizing the methods for
identifying adequate model with the security goals.
Web Server Attack
On the web servers, websites are hosted. The servers are running the operating system,
they are connected to the database of back end and they are running multiple applications
(Tandon et al., 2019). Any risks or vulnerabilities in the operating system, network, running
application or database lead to the web server attack.
Web Server Vulnerability Stack (Source: Reddy, 2019)
Introduction
This paper aims to discuss the business security model of the IT firm that is based in
Saudi Arabia for expanding their business in the market of Middle East. This paper discusses the
various types of the web server attack and conduct a comparison between the best security
practices for keeping the personal data of the client safe in their server. This study also
recommends solution for the global expansion of the business by utilizing the methods for
identifying adequate model with the security goals.
Web Server Attack
On the web servers, websites are hosted. The servers are running the operating system,
they are connected to the database of back end and they are running multiple applications
(Tandon et al., 2019). Any risks or vulnerabilities in the operating system, network, running
application or database lead to the web server attack.
Web Server Vulnerability Stack (Source: Reddy, 2019)

3CYBER DEFENCE
Types of Web Server Attack
There are multiple types of web server attacks, in which some of the attacks are:
DOS Attack
Any attacker can cause attack to the denial of service by sending multiple packets of
service request that overwhelm the capability of the service of the server (Zhang et al., 2015).
The attacker can also try to exploit the programming error in any running application that can
cause the attack in the DOS. Some of the examples of the DOS attack are SYN flooding, Ping of
death, buffer overflow attack and HTTP flood attack.
DOS attack (Source: Wang, Xu & Gu, 2015)
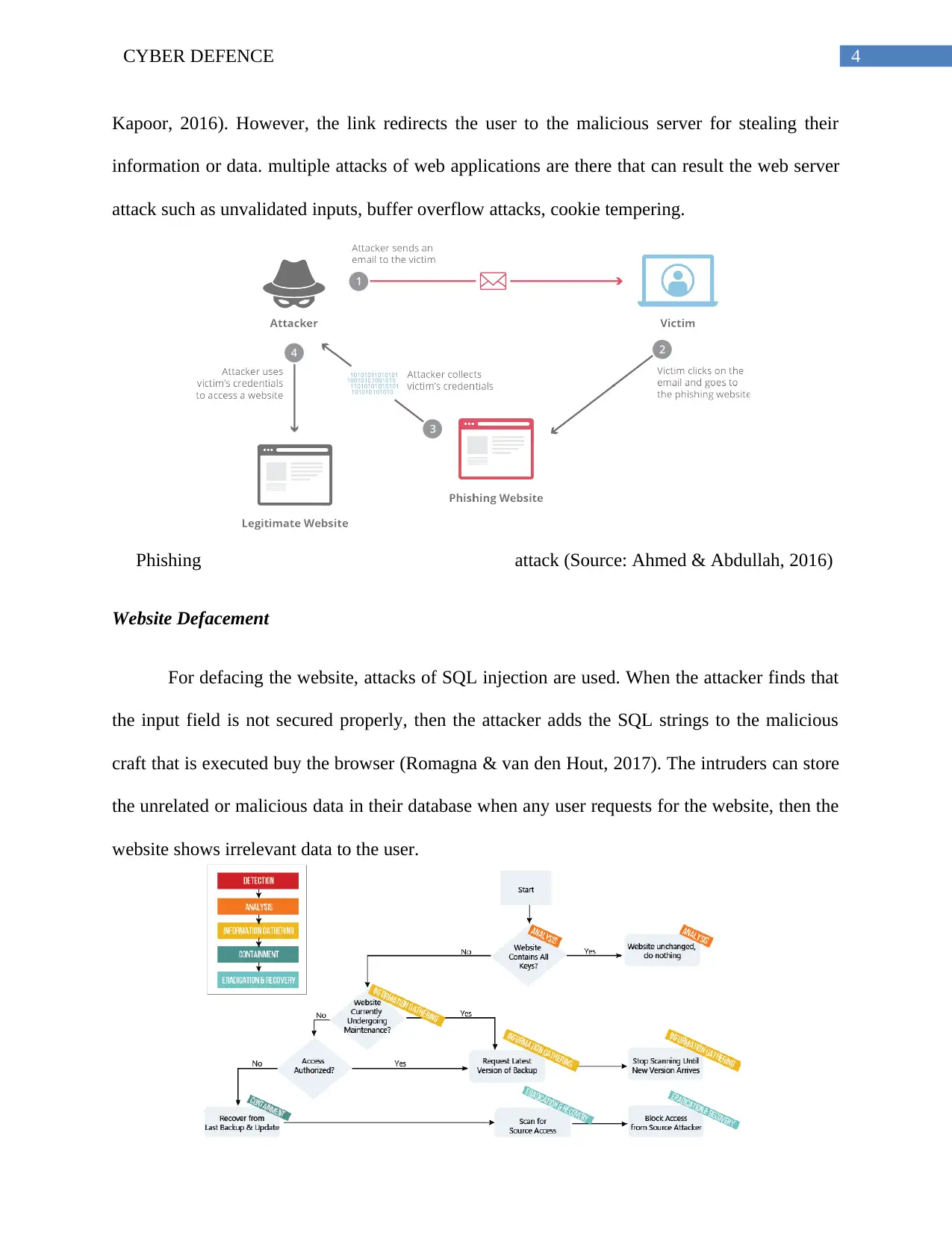
Phishing Attack
Any attacker can redirect the system of the victim to the malicious websites through
sending the user the malicious content or link via email that looks authentic (Gupta, Singhal &
Types of Web Server Attack
There are multiple types of web server attacks, in which some of the attacks are:
DOS Attack
Any attacker can cause attack to the denial of service by sending multiple packets of
service request that overwhelm the capability of the service of the server (Zhang et al., 2015).
The attacker can also try to exploit the programming error in any running application that can
cause the attack in the DOS. Some of the examples of the DOS attack are SYN flooding, Ping of
death, buffer overflow attack and HTTP flood attack.
DOS attack (Source: Wang, Xu & Gu, 2015)
Phishing Attack
Any attacker can redirect the system of the victim to the malicious websites through
sending the user the malicious content or link via email that looks authentic (Gupta, Singhal &
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4CYBER DEFENCE
Kapoor, 2016). However, the link redirects the user to the malicious server for stealing their
information or data. multiple attacks of web applications are there that can result the web server
attack such as unvalidated inputs, buffer overflow attacks, cookie tempering.
Phishing attack (Source: Ahmed & Abdullah, 2016)
Website Defacement
For defacing the website, attacks of SQL injection are used. When the attacker finds that
the input field is not secured properly, then the attacker adds the SQL strings to the malicious
craft that is executed buy the browser (Romagna & van den Hout, 2017). The intruders can store
the unrelated or malicious data in their database when any user requests for the website, then the
website shows irrelevant data to the user.
Kapoor, 2016). However, the link redirects the user to the malicious server for stealing their
information or data. multiple attacks of web applications are there that can result the web server
attack such as unvalidated inputs, buffer overflow attacks, cookie tempering.
Phishing attack (Source: Ahmed & Abdullah, 2016)
Website Defacement
For defacing the website, attacks of SQL injection are used. When the attacker finds that
the input field is not secured properly, then the attacker adds the SQL strings to the malicious
craft that is executed buy the browser (Romagna & van den Hout, 2017). The intruders can store
the unrelated or malicious data in their database when any user requests for the website, then the
website shows irrelevant data to the user.

5CYBER DEFENCE
Website Defacement (Source: Howell et al., 2019)
Misconfiguration attacks
If any unnecessary service is enabled or any default service is used, the errors in the data
are nit masked, then the intruders compromise with the server by multiple attacks such as
Command Injection, Error-based SQL injection and password cracking.
Misconfiguration attacks (Source: Chlosta et al., 2019)
Directory Traversal
Directory Traversal is the threat or vulnerability where the intruder is able in accessing
the directory of web root from any application. If the intruder is able to access the directory of
web root then the intruder can execute the commands of OS and can get the access to the
restricted directories or confidential information.
Website Defacement (Source: Howell et al., 2019)
Misconfiguration attacks
If any unnecessary service is enabled or any default service is used, the errors in the data
are nit masked, then the intruders compromise with the server by multiple attacks such as
Command Injection, Error-based SQL injection and password cracking.
Misconfiguration attacks (Source: Chlosta et al., 2019)
Directory Traversal
Directory Traversal is the threat or vulnerability where the intruder is able in accessing
the directory of web root from any application. If the intruder is able to access the directory of
web root then the intruder can execute the commands of OS and can get the access to the
restricted directories or confidential information.

6CYBER DEFENCE
Security Practices
Some of the best security practices, which the security manager of the organization can
employ for keeping the data of the customers safe such as:
Remote access
Though this is not practical but the administrators of the web server must login locally to
the server. If the remote access is required, the user can ensure that the connection of the remote
access is secured and protected by utilizing the encryption and tunneling protocols. Utilizing the
sign or security token or any equipment, this becomes a good security practice (Sheeba &
Rajkumar, 2016). The remote access must be restricted to the particular accounts and IP
addresses only. This is very essential not to login in any public network for accessing the
corporate server.
Server audit and monitor
The logs in the web server need to be stored in the separate area. The logs of network
service, database server logs, operating system logs and website access logs must be checked and
monitored properly. The strange log entries should be monitored. If anyone notices the strange
log activity then he or she must escalate that immediately so that the issue can be examined by
the server audit team.
Separate development or production environment
This is very faster and easier for the developer in developing the newer web application
version on the production server. The testing and the development of the application are done on
the server of the production itself. This can be the common occurrence on the server for finding
Security Practices
Some of the best security practices, which the security manager of the organization can
employ for keeping the data of the customers safe such as:
Remote access
Though this is not practical but the administrators of the web server must login locally to
the server. If the remote access is required, the user can ensure that the connection of the remote
access is secured and protected by utilizing the encryption and tunneling protocols. Utilizing the
sign or security token or any equipment, this becomes a good security practice (Sheeba &
Rajkumar, 2016). The remote access must be restricted to the particular accounts and IP
addresses only. This is very essential not to login in any public network for accessing the
corporate server.
Server audit and monitor
The logs in the web server need to be stored in the separate area. The logs of network
service, database server logs, operating system logs and website access logs must be checked and
monitored properly. The strange log entries should be monitored. If anyone notices the strange
log activity then he or she must escalate that immediately so that the issue can be examined by
the server audit team.
Separate development or production environment
This is very faster and easier for the developer in developing the newer web application
version on the production server. The testing and the development of the application are done on
the server of the production itself. This can be the common occurrence on the server for finding
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER DEFENCE
the new version of the particular website must not be available to public. As these types of
websites are in the early stage of development, they can have lack input validation, multiple
vulnerabilities and they are not able to manage the expectation properly (Sheeba & Rajkumar,
2016). These types of application can be discovered easily and exploited by any intruder by
using the free available tools.
Recommended Solution
From this study, the best solution for the IT-based organization that will be best suited for
the global expansion by securing the data of the customer is Separate Development. for easing
the development and the testing off the web application, the developers may develop the
particular internal applications, which will provide the users privileged access to the website,
web servers and database. This will be normal for the anonymous uses not to have. These types
of application never have the restriction as they the test applications access, which needs to be
access from the developers only (Răduca et al., 2015). If the separate development and the
testing are done on the production server, then the application will discover the malicious users
or intruders easily that can help the organization to comprise and gain access on production
server. This separate development strategy for the organization can help to build a sustainable
model in the market by securing the confidential information.
Conclusion
Not only protecting the web applications and web server is vital but also protecting the
business environment is also essential. Now days the businesses are utilizing the internet as the
resources and as the database for storing their data in cloud safely. However, there are also many
the new version of the particular website must not be available to public. As these types of
websites are in the early stage of development, they can have lack input validation, multiple
vulnerabilities and they are not able to manage the expectation properly (Sheeba & Rajkumar,
2016). These types of application can be discovered easily and exploited by any intruder by
using the free available tools.
Recommended Solution
From this study, the best solution for the IT-based organization that will be best suited for
the global expansion by securing the data of the customer is Separate Development. for easing
the development and the testing off the web application, the developers may develop the
particular internal applications, which will provide the users privileged access to the website,
web servers and database. This will be normal for the anonymous uses not to have. These types
of application never have the restriction as they the test applications access, which needs to be
access from the developers only (Răduca et al., 2015). If the separate development and the
testing are done on the production server, then the application will discover the malicious users
or intruders easily that can help the organization to comprise and gain access on production
server. This separate development strategy for the organization can help to build a sustainable
model in the market by securing the confidential information.
Conclusion
Not only protecting the web applications and web server is vital but also protecting the
business environment is also essential. Now days the businesses are utilizing the internet as the
resources and as the database for storing their data in cloud safely. However, there are also many

8CYBER DEFENCE
intruders, who are trying the hack that information and trying to attack against the web
application and web server, which has become the pervasive issues. For reducing the attacks, the
organization can conduct the analysis on these issues and then they can implement the security
practices for securing the confidential fata of their customer and a protected and secure
environment can help the organization to expand globally in the market effectively.
intruders, who are trying the hack that information and trying to attack against the web
application and web server, which has become the pervasive issues. For reducing the attacks, the
organization can conduct the analysis on these issues and then they can implement the security
practices for securing the confidential fata of their customer and a protected and secure
environment can help the organization to expand globally in the market effectively.

9CYBER DEFENCE
References
Ahmed, A. A., & Abdullah, N. A. (2016, October). Real time detection of phishing websites.
In 2016 IEEE 7th Annual Information Technology, Electronics and Mobile
Communication Conference (IEMCON) (pp. 1-6). IEEE.
Chlosta, M., Rupprecht, D., Holz, T., & Pöpper, C. (2019, May). LTE security disabled:
misconfiguration in commercial networks. In Proceedings of the 12th Conference on
Security and Privacy in Wireless and Mobile Networks (pp. 261-266).
Gupta, S., Singhal, A., & Kapoor, A. (2016, April). A literature survey on social engineering
attacks: Phishing attack. In 2016 international conference on computing, communication
and automation (ICCCA) (pp. 537-540). IEEE.
Howell, C. J., Burruss, G. W., Maimon, D., & Sahani, S. (2019). Website defacement and
routine activities: considering the importance of hackers’ valuations of potential
targets. Journal of Crime and Justice, 42(5), 536-550.
Răduca, E., Nistor, L., Hatiegan, C., Răduca, M., Pădureanu, I., & Drăghici, S. (2015, May).
Web server for command, control and monitoring of industrial equipment. In 2015 9th
International Symposium on Advanced Topics in Electrical Engineering (ATEE) (pp. 61-
66). IEEE.
Reddy, N. (2019). Web Attack Forensics. In Practical Cyber Forensics (pp. 317-344). Apress,
Berkeley, CA.
References
Ahmed, A. A., & Abdullah, N. A. (2016, October). Real time detection of phishing websites.
In 2016 IEEE 7th Annual Information Technology, Electronics and Mobile
Communication Conference (IEMCON) (pp. 1-6). IEEE.
Chlosta, M., Rupprecht, D., Holz, T., & Pöpper, C. (2019, May). LTE security disabled:
misconfiguration in commercial networks. In Proceedings of the 12th Conference on
Security and Privacy in Wireless and Mobile Networks (pp. 261-266).
Gupta, S., Singhal, A., & Kapoor, A. (2016, April). A literature survey on social engineering
attacks: Phishing attack. In 2016 international conference on computing, communication
and automation (ICCCA) (pp. 537-540). IEEE.
Howell, C. J., Burruss, G. W., Maimon, D., & Sahani, S. (2019). Website defacement and
routine activities: considering the importance of hackers’ valuations of potential
targets. Journal of Crime and Justice, 42(5), 536-550.
Răduca, E., Nistor, L., Hatiegan, C., Răduca, M., Pădureanu, I., & Drăghici, S. (2015, May).
Web server for command, control and monitoring of industrial equipment. In 2015 9th
International Symposium on Advanced Topics in Electrical Engineering (ATEE) (pp. 61-
66). IEEE.
Reddy, N. (2019). Web Attack Forensics. In Practical Cyber Forensics (pp. 317-344). Apress,
Berkeley, CA.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10CYBER DEFENCE
Romagna, M., & van den Hout, N. J. (2017, October). Hacktivism and website defacement:
motivations, capabilities and potential threats. In 27th Virus Bulletin International
Conference (Vol. 1).
Sheeba, R., & Rajkumar, K. (2016). Enhancing Security by Preventing DoS and DDoS Attack
using Hybrid Approach. Indian Journal of Science and Technology, 9, 48.
Tandon, R., Palia, A., Ramani, J., Paulsen, B., Bartlett, G., & Mirkovic, J. (2019, October).
Defending Web Servers Against Flash Crowd Attacks. In 2019 IEEE 27th International
Conference on Network Protocols (ICNP) (pp. 1-2). IEEE.
Wang, H., Xu, L., & Gu, G. (2015, June). Floodguard: A dos attack prevention extension in
software-defined networks. In 2015 45th Annual IEEE/IFIP International Conference on
Dependable Systems and Networks (pp. 239-250). IEEE.
Zhang, H., Cheng, P., Shi, L., & Chen, J. (2015). Optimal DoS attack scheduling in wireless
networked control system. IEEE Transactions on Control Systems Technology, 24(3),
843-852.
Romagna, M., & van den Hout, N. J. (2017, October). Hacktivism and website defacement:
motivations, capabilities and potential threats. In 27th Virus Bulletin International
Conference (Vol. 1).
Sheeba, R., & Rajkumar, K. (2016). Enhancing Security by Preventing DoS and DDoS Attack
using Hybrid Approach. Indian Journal of Science and Technology, 9, 48.
Tandon, R., Palia, A., Ramani, J., Paulsen, B., Bartlett, G., & Mirkovic, J. (2019, October).
Defending Web Servers Against Flash Crowd Attacks. In 2019 IEEE 27th International
Conference on Network Protocols (ICNP) (pp. 1-2). IEEE.
Wang, H., Xu, L., & Gu, G. (2015, June). Floodguard: A dos attack prevention extension in
software-defined networks. In 2015 45th Annual IEEE/IFIP International Conference on
Dependable Systems and Networks (pp. 239-250). IEEE.
Zhang, H., Cheng, P., Shi, L., & Chen, J. (2015). Optimal DoS attack scheduling in wireless
networked control system. IEEE Transactions on Control Systems Technology, 24(3),
843-852.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





