CTEC5805 - Cyber Engineering: Communication Technologies for Buildings
VerifiedAdded on 2023/04/22
|10
|2472
|461
Report
AI Summary
This Cyber Engineering report analyzes communication technologies for large building environments, focusing on Bluetooth and RFID network models. The Bluetooth model, designed for an office setup, utilizes Bluetooth 5 or 4.x with a controller, network node, wireless antenna, server, and cloud computing backup. It details protocols for user access and emergency scenarios, including contingency planning with a proxy server. The RFID model, tailored for a campus setup, employs Radio Frequency Identification for identification, tracking, and localization. It outlines protocols for user access, collision avoidance, and system resilience, including a double-layered P2P system for efficient data management. The report includes diagrams and references to support the analysis and design of these communication technologies.
CYBER ENGINEERING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBER ENGINEERING
Table of Contents
Question 3..................................................................................................................................2
Bluetooth Networking Model.................................................................................................2
Protocol 1...................................................................................................................................3
Protocol 2...................................................................................................................................4
RFID Networking Model.......................................................................................................4
Protocol 1...................................................................................................................................5
Protocol 2...................................................................................................................................6
Reference list..............................................................................................................................7
Page 1 of 10
Table of Contents
Question 3..................................................................................................................................2
Bluetooth Networking Model.................................................................................................2
Protocol 1...................................................................................................................................3
Protocol 2...................................................................................................................................4
RFID Networking Model.......................................................................................................4
Protocol 1...................................................................................................................................5
Protocol 2...................................................................................................................................6
Reference list..............................................................................................................................7
Page 1 of 10
CYBER ENGINEERING
Question 3
Bluetooth Networking Model
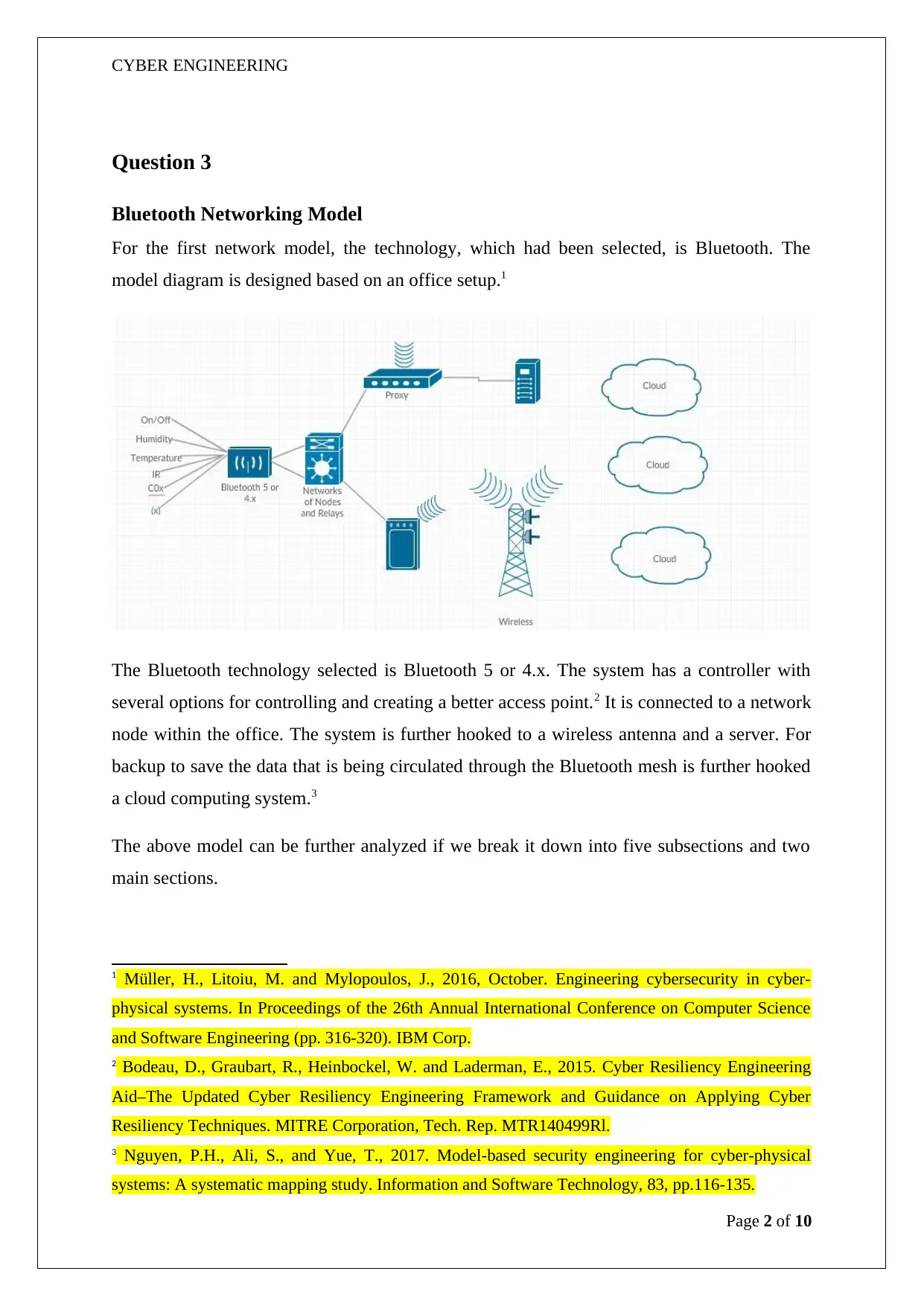
For the first network model, the technology, which had been selected, is Bluetooth. The
model diagram is designed based on an office setup.1
The Bluetooth technology selected is Bluetooth 5 or 4.x. The system has a controller with
several options for controlling and creating a better access point.2 It is connected to a network
node within the office. The system is further hooked to a wireless antenna and a server. For
backup to save the data that is being circulated through the Bluetooth mesh is further hooked
a cloud computing system.3
The above model can be further analyzed if we break it down into five subsections and two
main sections.
1 Müller, H., Litoiu, M. and Mylopoulos, J., 2016, October. Engineering cybersecurity in cyber-
physical systems. In Proceedings of the 26th Annual International Conference on Computer Science
and Software Engineering (pp. 316-320). IBM Corp.
2 Bodeau, D., Graubart, R., Heinbockel, W. and Laderman, E., 2015. Cyber Resiliency Engineering
Aid–The Updated Cyber Resiliency Engineering Framework and Guidance on Applying Cyber
Resiliency Techniques. MITRE Corporation, Tech. Rep. MTR140499Rl.
3 Nguyen, P.H., Ali, S., and Yue, T., 2017. Model-based security engineering for cyber-physical
systems: A systematic mapping study. Information and Software Technology, 83, pp.116-135.
Page 2 of 10
Question 3
Bluetooth Networking Model
For the first network model, the technology, which had been selected, is Bluetooth. The
model diagram is designed based on an office setup.1
The Bluetooth technology selected is Bluetooth 5 or 4.x. The system has a controller with
several options for controlling and creating a better access point.2 It is connected to a network
node within the office. The system is further hooked to a wireless antenna and a server. For
backup to save the data that is being circulated through the Bluetooth mesh is further hooked
a cloud computing system.3
The above model can be further analyzed if we break it down into five subsections and two
main sections.
1 Müller, H., Litoiu, M. and Mylopoulos, J., 2016, October. Engineering cybersecurity in cyber-
physical systems. In Proceedings of the 26th Annual International Conference on Computer Science
and Software Engineering (pp. 316-320). IBM Corp.
2 Bodeau, D., Graubart, R., Heinbockel, W. and Laderman, E., 2015. Cyber Resiliency Engineering
Aid–The Updated Cyber Resiliency Engineering Framework and Guidance on Applying Cyber
Resiliency Techniques. MITRE Corporation, Tech. Rep. MTR140499Rl.
3 Nguyen, P.H., Ali, S., and Yue, T., 2017. Model-based security engineering for cyber-physical
systems: A systematic mapping study. Information and Software Technology, 83, pp.116-135.
Page 2 of 10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
CYBER ENGINEERING
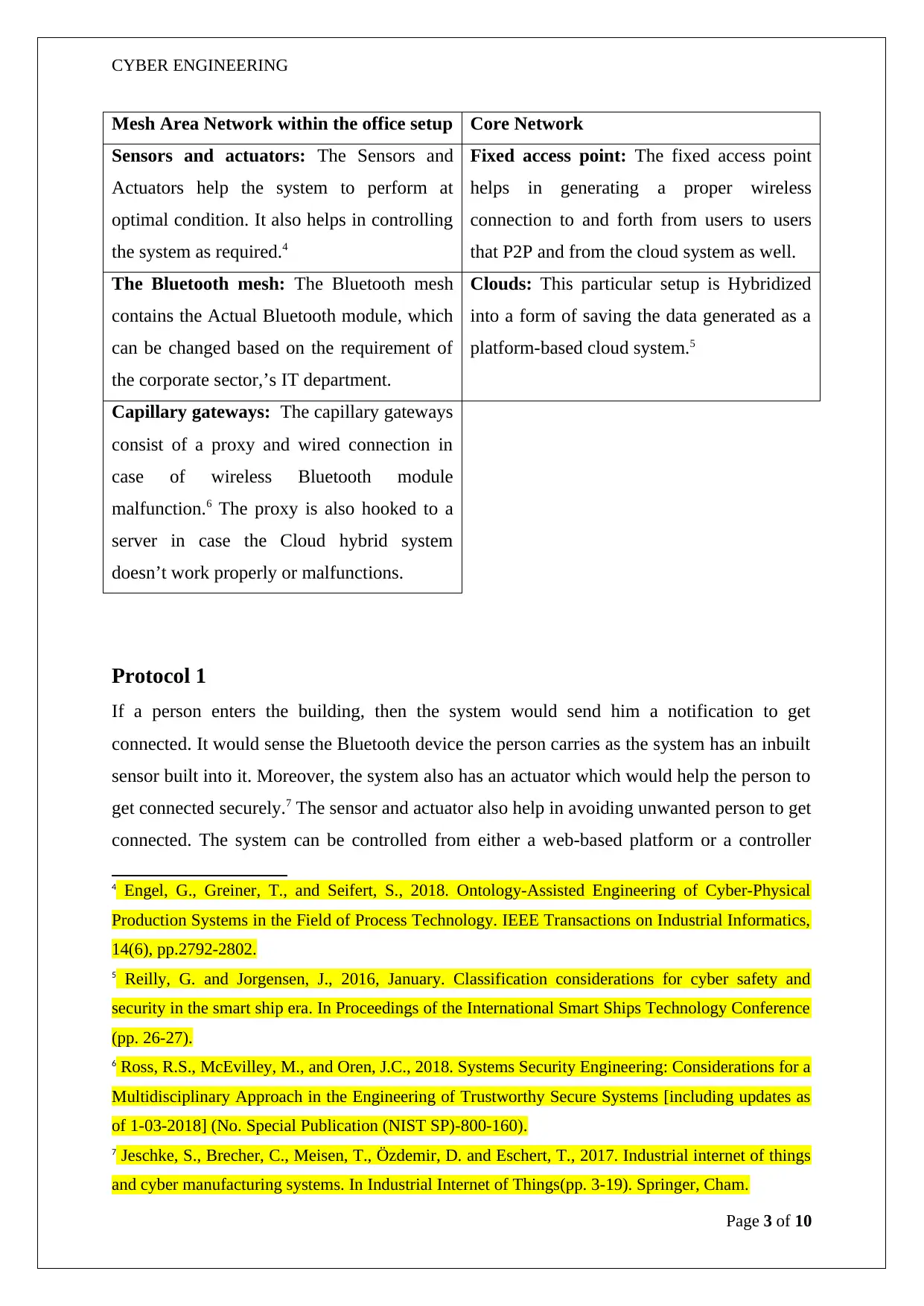
Mesh Area Network within the office setup Core Network
Sensors and actuators: The Sensors and
Actuators help the system to perform at
optimal condition. It also helps in controlling
the system as required.4
Fixed access point: The fixed access point
helps in generating a proper wireless
connection to and forth from users to users
that P2P and from the cloud system as well.
The Bluetooth mesh: The Bluetooth mesh
contains the Actual Bluetooth module, which
can be changed based on the requirement of
the corporate sector,’s IT department.
Clouds: This particular setup is Hybridized
into a form of saving the data generated as a
platform-based cloud system.5
Capillary gateways: The capillary gateways
consist of a proxy and wired connection in
case of wireless Bluetooth module
malfunction.6 The proxy is also hooked to a
server in case the Cloud hybrid system
doesn’t work properly or malfunctions.
Protocol 1
If a person enters the building, then the system would send him a notification to get
connected. It would sense the Bluetooth device the person carries as the system has an inbuilt
sensor built into it. Moreover, the system also has an actuator which would help the person to
get connected securely.7 The sensor and actuator also help in avoiding unwanted person to get
connected. The system can be controlled from either a web-based platform or a controller
4 Engel, G., Greiner, T., and Seifert, S., 2018. Ontology-Assisted Engineering of Cyber-Physical
Production Systems in the Field of Process Technology. IEEE Transactions on Industrial Informatics,
14(6), pp.2792-2802.
5 Reilly, G. and Jorgensen, J., 2016, January. Classification considerations for cyber safety and
security in the smart ship era. In Proceedings of the International Smart Ships Technology Conference
(pp. 26-27).
6 Ross, R.S., McEvilley, M., and Oren, J.C., 2018. Systems Security Engineering: Considerations for a
Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems [including updates as
of 1-03-2018] (No. Special Publication (NIST SP)-800-160).
7 Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017. Industrial internet of things
and cyber manufacturing systems. In Industrial Internet of Things(pp. 3-19). Springer, Cham.
Page 3 of 10
Mesh Area Network within the office setup Core Network
Sensors and actuators: The Sensors and
Actuators help the system to perform at
optimal condition. It also helps in controlling
the system as required.4
Fixed access point: The fixed access point
helps in generating a proper wireless
connection to and forth from users to users
that P2P and from the cloud system as well.
The Bluetooth mesh: The Bluetooth mesh
contains the Actual Bluetooth module, which
can be changed based on the requirement of
the corporate sector,’s IT department.
Clouds: This particular setup is Hybridized
into a form of saving the data generated as a
platform-based cloud system.5
Capillary gateways: The capillary gateways
consist of a proxy and wired connection in
case of wireless Bluetooth module
malfunction.6 The proxy is also hooked to a
server in case the Cloud hybrid system
doesn’t work properly or malfunctions.
Protocol 1
If a person enters the building, then the system would send him a notification to get
connected. It would sense the Bluetooth device the person carries as the system has an inbuilt
sensor built into it. Moreover, the system also has an actuator which would help the person to
get connected securely.7 The sensor and actuator also help in avoiding unwanted person to get
connected. The system can be controlled from either a web-based platform or a controller
4 Engel, G., Greiner, T., and Seifert, S., 2018. Ontology-Assisted Engineering of Cyber-Physical
Production Systems in the Field of Process Technology. IEEE Transactions on Industrial Informatics,
14(6), pp.2792-2802.
5 Reilly, G. and Jorgensen, J., 2016, January. Classification considerations for cyber safety and
security in the smart ship era. In Proceedings of the International Smart Ships Technology Conference
(pp. 26-27).
6 Ross, R.S., McEvilley, M., and Oren, J.C., 2018. Systems Security Engineering: Considerations for a
Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems [including updates as
of 1-03-2018] (No. Special Publication (NIST SP)-800-160).
7 Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017. Industrial internet of things
and cyber manufacturing systems. In Industrial Internet of Things(pp. 3-19). Springer, Cham.
Page 3 of 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CYBER ENGINEERING
function. Thus, it would help the administrator to blacklist any user. Moreover, if the person
entering the building wants to get the connection password changed for any purpose, then the
system can generate a new password and also assign those data that are required by the
person. This can be done as the system has been hooked to a cloud system that uses Platform
as a service and Software as a service. The systems are hybridized to provide a better search
and storage capacity.
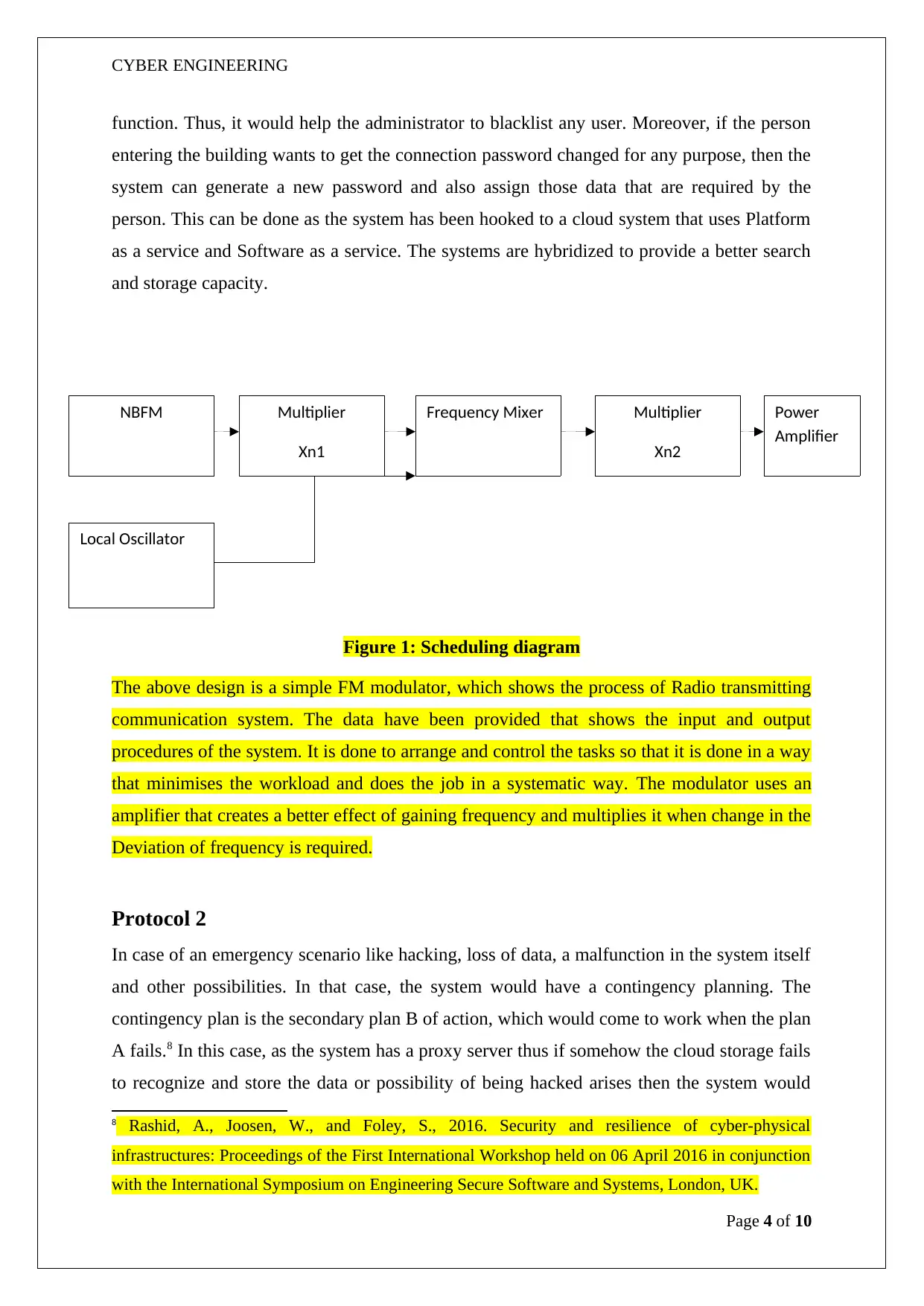
Figure 1: Scheduling diagram
The above design is a simple FM modulator, which shows the process of Radio transmitting
communication system. The data have been provided that shows the input and output
procedures of the system. It is done to arrange and control the tasks so that it is done in a way
that minimises the workload and does the job in a systematic way. The modulator uses an
amplifier that creates a better effect of gaining frequency and multiplies it when change in the
Deviation of frequency is required.
Protocol 2
In case of an emergency scenario like hacking, loss of data, a malfunction in the system itself
and other possibilities. In that case, the system would have a contingency planning. The
contingency plan is the secondary plan B of action, which would come to work when the plan
A fails.8 In this case, as the system has a proxy server thus if somehow the cloud storage fails
to recognize and store the data or possibility of being hacked arises then the system would
8 Rashid, A., Joosen, W., and Foley, S., 2016. Security and resilience of cyber-physical
infrastructures: Proceedings of the First International Workshop held on 06 April 2016 in conjunction
with the International Symposium on Engineering Secure Software and Systems, London, UK.
Page 4 of 10
NBFM Multiplier
Xn1
Frequency Mixer Multiplier
Xn2
Power
Amplifier
Local Oscillator
function. Thus, it would help the administrator to blacklist any user. Moreover, if the person
entering the building wants to get the connection password changed for any purpose, then the
system can generate a new password and also assign those data that are required by the
person. This can be done as the system has been hooked to a cloud system that uses Platform
as a service and Software as a service. The systems are hybridized to provide a better search
and storage capacity.
Figure 1: Scheduling diagram
The above design is a simple FM modulator, which shows the process of Radio transmitting
communication system. The data have been provided that shows the input and output
procedures of the system. It is done to arrange and control the tasks so that it is done in a way
that minimises the workload and does the job in a systematic way. The modulator uses an
amplifier that creates a better effect of gaining frequency and multiplies it when change in the
Deviation of frequency is required.
Protocol 2
In case of an emergency scenario like hacking, loss of data, a malfunction in the system itself
and other possibilities. In that case, the system would have a contingency planning. The
contingency plan is the secondary plan B of action, which would come to work when the plan
A fails.8 In this case, as the system has a proxy server thus if somehow the cloud storage fails
to recognize and store the data or possibility of being hacked arises then the system would
8 Rashid, A., Joosen, W., and Foley, S., 2016. Security and resilience of cyber-physical
infrastructures: Proceedings of the First International Workshop held on 06 April 2016 in conjunction
with the International Symposium on Engineering Secure Software and Systems, London, UK.
Page 4 of 10
NBFM Multiplier
Xn1
Frequency Mixer Multiplier
Xn2
Power
Amplifier
Local Oscillator
CYBER ENGINEERING
use the server to store the data for a temporary period. In case the system is getting hacked
then the sensor can eliminate or notify the administrator with a command prompt notification
system.
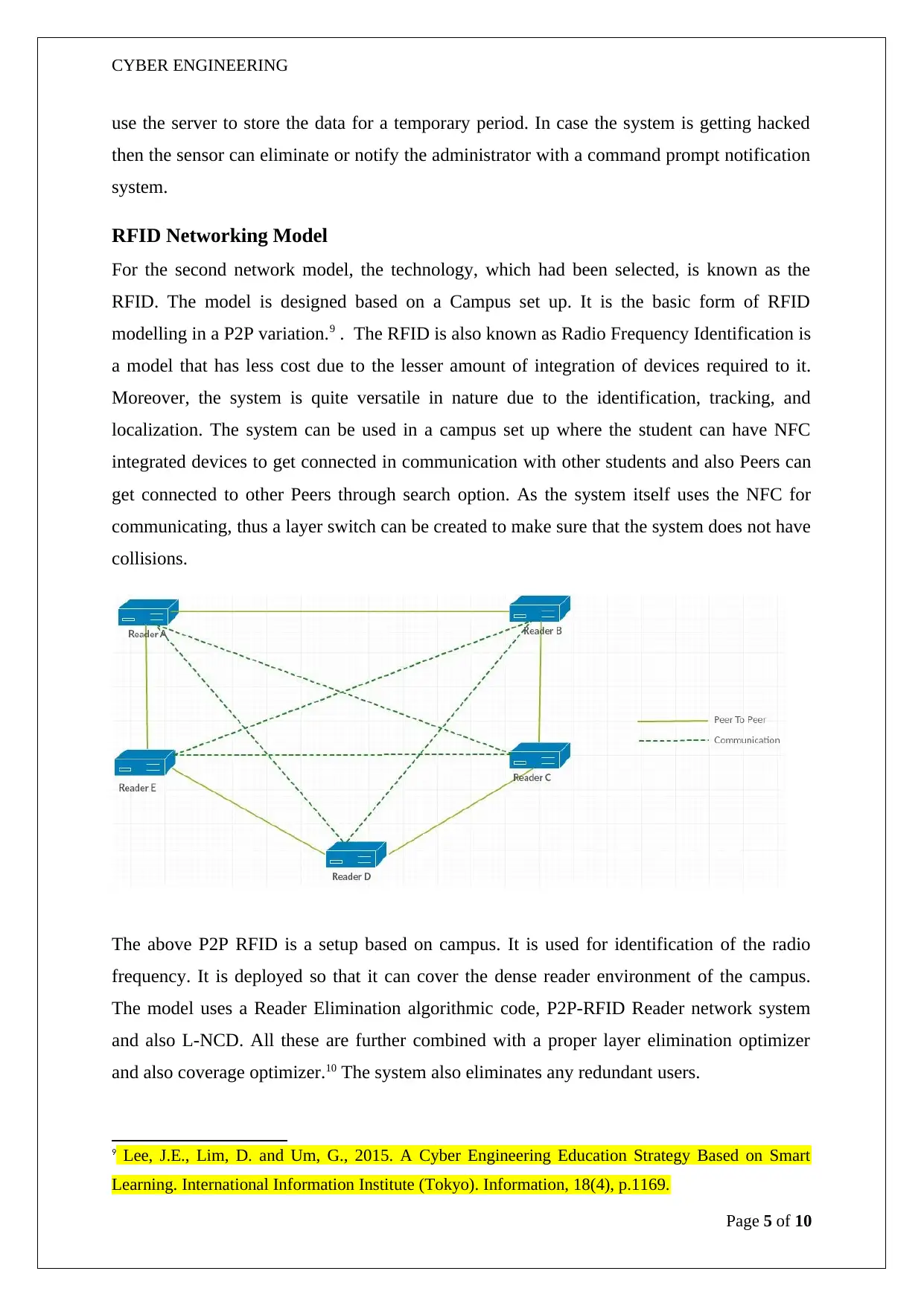
RFID Networking Model
For the second network model, the technology, which had been selected, is known as the
RFID. The model is designed based on a Campus set up. It is the basic form of RFID
modelling in a P2P variation.9 . The RFID is also known as Radio Frequency Identification is
a model that has less cost due to the lesser amount of integration of devices required to it.
Moreover, the system is quite versatile in nature due to the identification, tracking, and
localization. The system can be used in a campus set up where the student can have NFC
integrated devices to get connected in communication with other students and also Peers can
get connected to other Peers through search option. As the system itself uses the NFC for
communicating, thus a layer switch can be created to make sure that the system does not have
collisions.
The above P2P RFID is a setup based on campus. It is used for identification of the radio
frequency. It is deployed so that it can cover the dense reader environment of the campus.
The model uses a Reader Elimination algorithmic code, P2P-RFID Reader network system
and also L-NCD. All these are further combined with a proper layer elimination optimizer
and also coverage optimizer.10 The system also eliminates any redundant users.
9 Lee, J.E., Lim, D. and Um, G., 2015. A Cyber Engineering Education Strategy Based on Smart
Learning. International Information Institute (Tokyo). Information, 18(4), p.1169.
Page 5 of 10
use the server to store the data for a temporary period. In case the system is getting hacked
then the sensor can eliminate or notify the administrator with a command prompt notification
system.
RFID Networking Model
For the second network model, the technology, which had been selected, is known as the
RFID. The model is designed based on a Campus set up. It is the basic form of RFID
modelling in a P2P variation.9 . The RFID is also known as Radio Frequency Identification is
a model that has less cost due to the lesser amount of integration of devices required to it.
Moreover, the system is quite versatile in nature due to the identification, tracking, and
localization. The system can be used in a campus set up where the student can have NFC
integrated devices to get connected in communication with other students and also Peers can
get connected to other Peers through search option. As the system itself uses the NFC for
communicating, thus a layer switch can be created to make sure that the system does not have
collisions.
The above P2P RFID is a setup based on campus. It is used for identification of the radio
frequency. It is deployed so that it can cover the dense reader environment of the campus.
The model uses a Reader Elimination algorithmic code, P2P-RFID Reader network system
and also L-NCD. All these are further combined with a proper layer elimination optimizer
and also coverage optimizer.10 The system also eliminates any redundant users.
9 Lee, J.E., Lim, D. and Um, G., 2015. A Cyber Engineering Education Strategy Based on Smart
Learning. International Information Institute (Tokyo). Information, 18(4), p.1169.
Page 5 of 10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBER ENGINEERING
Protocol 1
In case of a person enters the building or the campus, in this case, the L-NCD would either
mark the person as a student or else a redundant user.11 The user would then only gain access
to the network coverage. Once the user gains access to the network coverage then only they
can read the data, which would be circulated through the system. However, in case, the
person who had entered the campus has an NFC enabled device then there can be a collision
with the Radiofrequency wave as every RFID reader has a pair of NFC into it. To avoid the
collision the anti-collision protocol can be designed as well. Thus, in this case, if the channel
detects any collision then the NFC initiator device within the readers would change its
operating mode to the card emulation mode of the system. As the card initiator mode is
compatible with the current RFID standards, thus the reader would understand the presence
of the NFC and based on that it will allocate a P2P communication mode.
Protocol 2
In case of any emergency like hacking or malfunctioning of the system, the system can adjust
itself with the algorithmic code and the process of eliminating unwanted users would also
help the system to stay intact.12 It would also make the system to function properly without
any kind of issue, as it’s a closed system with controllable coverage as well. In the ever-
increasing process of adding peers, the system may stop functioning due to the decrease in
energy. Thus, the above diagram shows a double-layered P2P system. In this case, a set of
readers or peers are known as Super readers that is A and B whereas C, D, and E are known
as the sub peers. In such design, the generation of data would be less. This is because the
10 Schoitsch, E., Schmittner, C., Ma, Z. and Gruber, T., 2016. The need for safety and cyber-security
co-engineering and standardization for highly automated automotive vehicles. In Advanced
Microsystems for Automotive Applications 2015 (pp. 251-261). Springer, Cham.
11 Fitzgerald, J., Gamble, C., Payne, R., Larsen, P.G., Basagiannis, S. and Mady, A.E.D., 2016, July.
Collaborative Model-based Systems Engineering for Cyber-Physical Systems–a Case Study in
Building Automation. In Proceedings of INCOSE International Symposium on Systems Engineering,
Edinburgh, Scotland.
12 Harrison, R., Vera, D. and Ahmad, B., 2016. Engineering methods and tools for cyber-physical
automation systems. Proceedings of the IEEE, 104(5), pp.973-985.
Page 6 of 10
Protocol 1
In case of a person enters the building or the campus, in this case, the L-NCD would either
mark the person as a student or else a redundant user.11 The user would then only gain access
to the network coverage. Once the user gains access to the network coverage then only they
can read the data, which would be circulated through the system. However, in case, the
person who had entered the campus has an NFC enabled device then there can be a collision
with the Radiofrequency wave as every RFID reader has a pair of NFC into it. To avoid the
collision the anti-collision protocol can be designed as well. Thus, in this case, if the channel
detects any collision then the NFC initiator device within the readers would change its
operating mode to the card emulation mode of the system. As the card initiator mode is
compatible with the current RFID standards, thus the reader would understand the presence
of the NFC and based on that it will allocate a P2P communication mode.
Protocol 2
In case of any emergency like hacking or malfunctioning of the system, the system can adjust
itself with the algorithmic code and the process of eliminating unwanted users would also
help the system to stay intact.12 It would also make the system to function properly without
any kind of issue, as it’s a closed system with controllable coverage as well. In the ever-
increasing process of adding peers, the system may stop functioning due to the decrease in
energy. Thus, the above diagram shows a double-layered P2P system. In this case, a set of
readers or peers are known as Super readers that is A and B whereas C, D, and E are known
as the sub peers. In such design, the generation of data would be less. This is because the
10 Schoitsch, E., Schmittner, C., Ma, Z. and Gruber, T., 2016. The need for safety and cyber-security
co-engineering and standardization for highly automated automotive vehicles. In Advanced
Microsystems for Automotive Applications 2015 (pp. 251-261). Springer, Cham.
11 Fitzgerald, J., Gamble, C., Payne, R., Larsen, P.G., Basagiannis, S. and Mady, A.E.D., 2016, July.
Collaborative Model-based Systems Engineering for Cyber-Physical Systems–a Case Study in
Building Automation. In Proceedings of INCOSE International Symposium on Systems Engineering,
Edinburgh, Scotland.
12 Harrison, R., Vera, D. and Ahmad, B., 2016. Engineering methods and tools for cyber-physical
automation systems. Proceedings of the IEEE, 104(5), pp.973-985.
Page 6 of 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBER ENGINEERING
supper peers can see all the readers can take the file search option and communication apart.
This would help in dismissing the flooding within the system.
Page 7 of 10
supper peers can see all the readers can take the file search option and communication apart.
This would help in dismissing the flooding within the system.
Page 7 of 10

CYBER ENGINEERING
Reference list
Bodeau, D., Graubart, R., Heinbockel, W. and Laderman, E., 2015. Cyber Resiliency
Engineering Aid–The Updated Cyber Resiliency Engineering Framework and Guidance on
Applying Cyber Resiliency Techniques. MITRE Corporation, Tech. Rep. MTR140499Rl.
Engel, G., Greiner, T., and Seifert, S., 2018. Ontology-Assisted Engineering of Cyber-
Physical Production Systems in the Field of Process Technology. IEEE Transactions on
Industrial Informatics, 14(6), pp.2792-2802.
Fitzgerald, J., Gamble, C., Payne, R., Larsen, P.G., Basagiannis, S. and Mady, A.E.D., 2016,
July. Collaborative Model-based Systems Engineering for Cyber-Physical Systems–a Case
Study in Building Automation. In Proceedings of INCOSE International Symposium on
Systems Engineering, Edinburgh, Scotland.
Harrison, R., Vera, D. and Ahmad, B., 2016. Engineering methods and tools for cyber-
physical automation systems. Proceedings of the IEEE, 104(5), pp.973-985.
Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017. Industrial internet of
things and cyber manufacturing systems. In Industrial Internet of Things(pp. 3-19). Springer,
Cham.
Lee, J.E., Lim, D. and Um, G., 2015. A Cyber Engineering Education Strategy Based on
Smart Learning. International Information Institute (Tokyo). Information, 18(4), p.1169.
Müller, H., Litoiu, M. and Mylopoulos, J., 2016, October. Engineering cybersecurity in
cyber-physical systems. In Proceedings of the 26th Annual International Conference on
Computer Science and Software Engineering (pp. 316-320). IBM Corp.
Nguyen, P.H., Ali, S., and Yue, T., 2017. Model-based security engineering for cyber-
physical systems: A systematic mapping study. Information and Software Technology, 83,
pp.116-135.
Rashid, A., Joosen, W., and Foley, S., 2016. Security and resilience of cyber-physical
infrastructures: Proceedings of the First International Workshop held on 06 April 2016 in
Page 8 of 10
Reference list
Bodeau, D., Graubart, R., Heinbockel, W. and Laderman, E., 2015. Cyber Resiliency
Engineering Aid–The Updated Cyber Resiliency Engineering Framework and Guidance on
Applying Cyber Resiliency Techniques. MITRE Corporation, Tech. Rep. MTR140499Rl.
Engel, G., Greiner, T., and Seifert, S., 2018. Ontology-Assisted Engineering of Cyber-
Physical Production Systems in the Field of Process Technology. IEEE Transactions on
Industrial Informatics, 14(6), pp.2792-2802.
Fitzgerald, J., Gamble, C., Payne, R., Larsen, P.G., Basagiannis, S. and Mady, A.E.D., 2016,
July. Collaborative Model-based Systems Engineering for Cyber-Physical Systems–a Case
Study in Building Automation. In Proceedings of INCOSE International Symposium on
Systems Engineering, Edinburgh, Scotland.
Harrison, R., Vera, D. and Ahmad, B., 2016. Engineering methods and tools for cyber-
physical automation systems. Proceedings of the IEEE, 104(5), pp.973-985.
Jeschke, S., Brecher, C., Meisen, T., Özdemir, D. and Eschert, T., 2017. Industrial internet of
things and cyber manufacturing systems. In Industrial Internet of Things(pp. 3-19). Springer,
Cham.
Lee, J.E., Lim, D. and Um, G., 2015. A Cyber Engineering Education Strategy Based on
Smart Learning. International Information Institute (Tokyo). Information, 18(4), p.1169.
Müller, H., Litoiu, M. and Mylopoulos, J., 2016, October. Engineering cybersecurity in
cyber-physical systems. In Proceedings of the 26th Annual International Conference on
Computer Science and Software Engineering (pp. 316-320). IBM Corp.
Nguyen, P.H., Ali, S., and Yue, T., 2017. Model-based security engineering for cyber-
physical systems: A systematic mapping study. Information and Software Technology, 83,
pp.116-135.
Rashid, A., Joosen, W., and Foley, S., 2016. Security and resilience of cyber-physical
infrastructures: Proceedings of the First International Workshop held on 06 April 2016 in
Page 8 of 10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBER ENGINEERING
conjunction with the International Symposium on Engineering Secure Software and Systems,
London, UK.
Reilly, G. and Jorgensen, J., 2016, January. Classification considerations for cyber safety and
security in the smart ship era. In Proceedings of the International Smart Ships Technology
Conference (pp. 26-27).
Ross, R.S., McEvilley, M., and Oren, J.C., 2018. Systems Security Engineering:
Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure
Systems [including updates as of 1-03-2018] (No. Special Publication (NIST SP)-800-160).
Schoitsch, E., Schmittner, C., Ma, Z. and Gruber, T., 2016. The need for safety and cyber-
security co-engineering and standardization for highly automated automotive vehicles.
In Advanced Microsystems for Automotive Applications 2015 (pp. 251-261). Springer, Cham.
Page 9 of 10
conjunction with the International Symposium on Engineering Secure Software and Systems,
London, UK.
Reilly, G. and Jorgensen, J., 2016, January. Classification considerations for cyber safety and
security in the smart ship era. In Proceedings of the International Smart Ships Technology
Conference (pp. 26-27).
Ross, R.S., McEvilley, M., and Oren, J.C., 2018. Systems Security Engineering:
Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure
Systems [including updates as of 1-03-2018] (No. Special Publication (NIST SP)-800-160).
Schoitsch, E., Schmittner, C., Ma, Z. and Gruber, T., 2016. The need for safety and cyber-
security co-engineering and standardization for highly automated automotive vehicles.
In Advanced Microsystems for Automotive Applications 2015 (pp. 251-261). Springer, Cham.
Page 9 of 10
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


