Cyber Engineering: Bluetooth and RFID Networking Models
Added on 2023-04-22
10 Pages2472 Words461 Views
CYBER ENGINEERING
CYBER ENGINEERING
Table of Contents
Question 3..................................................................................................................................2
Bluetooth Networking Model.................................................................................................2
Protocol 1...................................................................................................................................3
Protocol 2...................................................................................................................................4
RFID Networking Model.......................................................................................................4
Protocol 1...................................................................................................................................5
Protocol 2...................................................................................................................................6
Reference list..............................................................................................................................7
Page 1 of 10
Table of Contents
Question 3..................................................................................................................................2
Bluetooth Networking Model.................................................................................................2
Protocol 1...................................................................................................................................3
Protocol 2...................................................................................................................................4
RFID Networking Model.......................................................................................................4
Protocol 1...................................................................................................................................5
Protocol 2...................................................................................................................................6
Reference list..............................................................................................................................7
Page 1 of 10

CYBER ENGINEERING
Question 3
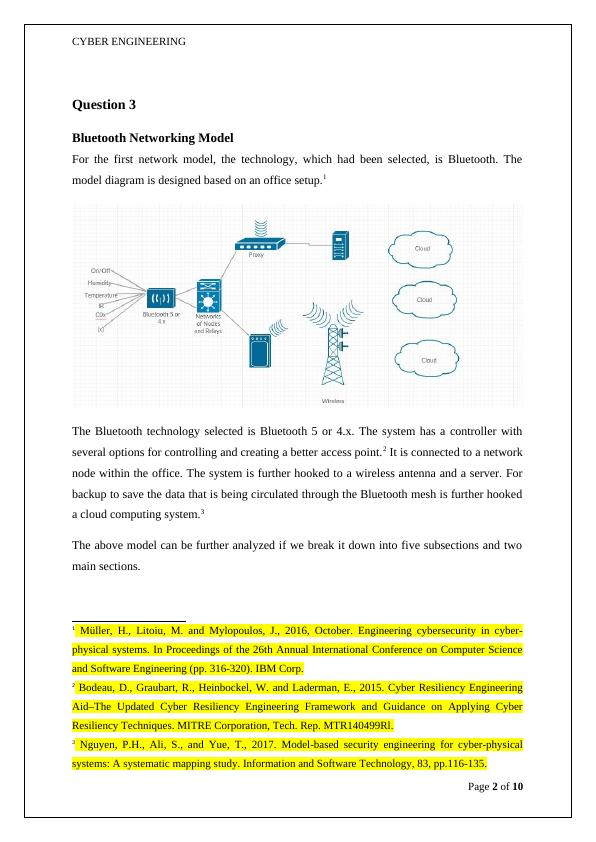
Bluetooth Networking Model
For the first network model, the technology, which had been selected, is Bluetooth. The
model diagram is designed based on an office setup.1
The Bluetooth technology selected is Bluetooth 5 or 4.x. The system has a controller with
several options for controlling and creating a better access point.2 It is connected to a network
node within the office. The system is further hooked to a wireless antenna and a server. For
backup to save the data that is being circulated through the Bluetooth mesh is further hooked
a cloud computing system.3
The above model can be further analyzed if we break it down into five subsections and two
main sections.
1 Müller, H., Litoiu, M. and Mylopoulos, J., 2016, October. Engineering cybersecurity in cyber-
physical systems. In Proceedings of the 26th Annual International Conference on Computer Science
and Software Engineering (pp. 316-320). IBM Corp.
2 Bodeau, D., Graubart, R., Heinbockel, W. and Laderman, E., 2015. Cyber Resiliency Engineering
Aid–The Updated Cyber Resiliency Engineering Framework and Guidance on Applying Cyber
Resiliency Techniques. MITRE Corporation, Tech. Rep. MTR140499Rl.
3 Nguyen, P.H., Ali, S., and Yue, T., 2017. Model-based security engineering for cyber-physical
systems: A systematic mapping study. Information and Software Technology, 83, pp.116-135.
Page 2 of 10
Question 3
Bluetooth Networking Model
For the first network model, the technology, which had been selected, is Bluetooth. The
model diagram is designed based on an office setup.1
The Bluetooth technology selected is Bluetooth 5 or 4.x. The system has a controller with
several options for controlling and creating a better access point.2 It is connected to a network
node within the office. The system is further hooked to a wireless antenna and a server. For
backup to save the data that is being circulated through the Bluetooth mesh is further hooked
a cloud computing system.3
The above model can be further analyzed if we break it down into five subsections and two
main sections.
1 Müller, H., Litoiu, M. and Mylopoulos, J., 2016, October. Engineering cybersecurity in cyber-
physical systems. In Proceedings of the 26th Annual International Conference on Computer Science
and Software Engineering (pp. 316-320). IBM Corp.
2 Bodeau, D., Graubart, R., Heinbockel, W. and Laderman, E., 2015. Cyber Resiliency Engineering
Aid–The Updated Cyber Resiliency Engineering Framework and Guidance on Applying Cyber
Resiliency Techniques. MITRE Corporation, Tech. Rep. MTR140499Rl.
3 Nguyen, P.H., Ali, S., and Yue, T., 2017. Model-based security engineering for cyber-physical
systems: A systematic mapping study. Information and Software Technology, 83, pp.116-135.
Page 2 of 10
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
IoT devices. Connection between diff erent device s. Inlg...
|17
|350
|256
Network Design: Case Study of LUCMAT LTDlg...
|32
|6131
|456
IT Infrastructure Management - Deskliblg...
|7
|1577
|102
Internet of Things: Privacy Issues and Contentslg...
|9
|1402
|116
