Cyber Safety Awareness Among School Children
VerifiedAdded on 2023/04/21
|64
|15843
|335
AI Summary
This research explores the importance of cyber safety awareness among school children and the need for suitable programs to educate them about cyber threats and safe internet practices. It discusses the current cyber-security issues faced by children, the challenges in creating awareness, and the potential programs that could be used to educate children about cyber safety. The research aims to provide insights and recommendations for developing effective cyber safety awareness programs for young learners.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
HRCOS82
2018
Assignment 02
Assignment unique code 612672
Student number: 46112340
Last name & Initials Uzamukunda MT
HRCOS82
2018
Assignment 02
Assignment unique code 612672
Student number: 46112340
Last name & Initials Uzamukunda MT
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
By
Marie Therese Uzamukunda
UNIVERSITY OF SOUTH AFRICA
by
A Research Dissertation submitted to the Faculty of Please enterSchool of
……..,University of South Africa, in partial fulfilment of the requirements for the
degree of …Bsc Honours Please enter …..in ……Computer Science
Johannesburg, 2019
CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
By
Marie Therese Uzamukunda
UNIVERSITY OF SOUTH AFRICA
by
A Research Dissertation submitted to the Faculty of Please enterSchool of
……..,University of South Africa, in partial fulfilment of the requirements for the
degree of …Bsc Honours Please enter …..in ……Computer Science
Johannesburg, 2019

2CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Abstract
Internet plays a key role in daily lives of the children as it is one of the most important
medium of learning and communication. Among the children, internet is invaluable sources
to provide knowledge, skills along with encourage creativity among them. The growing
public concern regarding security of data, along with t dramatic increase in security attacks, is
creating a global debate on cyber security. Threats to cyber security remain unlimited. While
security solutions from security software to data protection are improving, attacks are
becoming more sophisticated; attackers are more sophisticated and more capable of attacking.
We hear about cyber-attacks, online frauds, phishing and ransomware in media every day. In
this world of digital information, it is vital for each of us to have a certain understanding of
cyber security and to know how to protect against online security threats. Regrettably, cyber
risks are encountered when using internet. The cyber risks can range from inappropriate
content, chat room “friends”, cyber bullying to sexting, online scams or identity theft.
Children may not have the required expertise or ability to handle those risks. How to make
sure children enjoy safer online involvement and how to protect them from online risks?
The cyber safety awareness program is implemented for the children so that it helps to aware
them of cyber threats. This program helps in teaching children how to use computer safely.
Keywords:Children, cyber risks, cyber awareness, cyber education
Abstract
Internet plays a key role in daily lives of the children as it is one of the most important
medium of learning and communication. Among the children, internet is invaluable sources
to provide knowledge, skills along with encourage creativity among them. The growing
public concern regarding security of data, along with t dramatic increase in security attacks, is
creating a global debate on cyber security. Threats to cyber security remain unlimited. While
security solutions from security software to data protection are improving, attacks are
becoming more sophisticated; attackers are more sophisticated and more capable of attacking.
We hear about cyber-attacks, online frauds, phishing and ransomware in media every day. In
this world of digital information, it is vital for each of us to have a certain understanding of
cyber security and to know how to protect against online security threats. Regrettably, cyber
risks are encountered when using internet. The cyber risks can range from inappropriate
content, chat room “friends”, cyber bullying to sexting, online scams or identity theft.
Children may not have the required expertise or ability to handle those risks. How to make
sure children enjoy safer online involvement and how to protect them from online risks?
The cyber safety awareness program is implemented for the children so that it helps to aware
them of cyber threats. This program helps in teaching children how to use computer safely.
Keywords:Children, cyber risks, cyber awareness, cyber education

3CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Acknowledgement
I want to acknowledge the assistance of all the people who helped me complete this research
successfully. I would wish to show my gratitude towards my supervisor who has helped me
extensively in this study and without whose support I would not have been able to finish this
research. I would also like thank all the participants of the survey and the managers of Miss
Millie’s Fried Chicken, who have sportingly participated and cooperated with me in my
investigation. Without their support and response, this study would not have been possible.
Lastly, I would also express my gratitude to my friends and classmates who have assisted me
during my research.
Thanking you all.
Acknowledgement
I want to acknowledge the assistance of all the people who helped me complete this research
successfully. I would wish to show my gratitude towards my supervisor who has helped me
extensively in this study and without whose support I would not have been able to finish this
research. I would also like thank all the participants of the survey and the managers of Miss
Millie’s Fried Chicken, who have sportingly participated and cooperated with me in my
investigation. Without their support and response, this study would not have been possible.
Lastly, I would also express my gratitude to my friends and classmates who have assisted me
during my research.
Thanking you all.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Table of Contents
Chapter 1: Introduction..............................................................................................................7
1.1 Introduction and background.......................................................................................7
1.2 Problem statement.......................................................................................................8
1.3 Main research question................................................................................................8
1.3.1 Sub research questions..............................................................................................8
1.4 The current cyber-security issues identified among school children...............................9
1.5 Identified community.......................................................................................................9
1.6 What is community engagement?....................................................................................9
1.7 Improvement of cyber awareness for children...............................................................10
1.8 Programs to be used for cyber safety awareness............................................................10
1.9 Structure of dissertation.................................................................................................11
1.10 Conclusion....................................................................................................................12
Chapter 2: Literature Review...................................................................................................13
2.1 Introduction....................................................................................................................13
2.2 Understanding Cyber Security.......................................................................................13
2.2.1 Disadvantages of cyber security..............................................................................13
2.3 Risks for Children using internet...................................................................................14
2.3.1 Content Risks..........................................................................................................15
2.3.2 Contact Risks..........................................................................................................15
2.3.3 Conduct Risks.........................................................................................................16
2.3.4 Security risks...........................................................................................................17
2.4 Information Security Awareness....................................................................................21
2.5 Security Awareness among school Children..................................................................21
2.5.1 Cyber Countermeasures..........................................................................................22
2.6 Literature gap.................................................................................................................23
Chapter 3: Research Methodology...........................................................................................24
Table of Contents
Chapter 1: Introduction..............................................................................................................7
1.1 Introduction and background.......................................................................................7
1.2 Problem statement.......................................................................................................8
1.3 Main research question................................................................................................8
1.3.1 Sub research questions..............................................................................................8
1.4 The current cyber-security issues identified among school children...............................9
1.5 Identified community.......................................................................................................9
1.6 What is community engagement?....................................................................................9
1.7 Improvement of cyber awareness for children...............................................................10
1.8 Programs to be used for cyber safety awareness............................................................10
1.9 Structure of dissertation.................................................................................................11
1.10 Conclusion....................................................................................................................12
Chapter 2: Literature Review...................................................................................................13
2.1 Introduction....................................................................................................................13
2.2 Understanding Cyber Security.......................................................................................13
2.2.1 Disadvantages of cyber security..............................................................................13
2.3 Risks for Children using internet...................................................................................14
2.3.1 Content Risks..........................................................................................................15
2.3.2 Contact Risks..........................................................................................................15
2.3.3 Conduct Risks.........................................................................................................16
2.3.4 Security risks...........................................................................................................17
2.4 Information Security Awareness....................................................................................21
2.5 Security Awareness among school Children..................................................................21
2.5.1 Cyber Countermeasures..........................................................................................22
2.6 Literature gap.................................................................................................................23
Chapter 3: Research Methodology...........................................................................................24

5CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
3.1 Introduction....................................................................................................................24
3.2 Research outline.............................................................................................................24
3.3 Research Paradigm.........................................................................................................24
3.3.1 Research Philosophy...............................................................................................24
3.3.2 Research approach..................................................................................................25
3.3.3 Research Design......................................................................................................25
3.4 Sampling method...........................................................................................................26
3.5 Research Strategy...........................................................................................................26
3.5.1 Justification for selection of research strategy (Survey).........................................27
3.6 Data collection methods.................................................................................................27
3.6.1 Quantitative Data Collection Method.....................................................................27
3.7 Accessibility issues........................................................................................................27
3.8 Ethical consideration......................................................................................................28
3.9 Data analysis..................................................................................................................28
3.10 Time table.....................................................................................................................28
3.11 Summary......................................................................................................................29
Chapter 4: Data analysis and findings......................................................................................30
4.0 Introduction....................................................................................................................30
4.1 Quantitative Data Representation and Interpretations.................................................30
4.1.1 Conducting survey questionnaires for the responses of 25 school children.........31
4.2 Summary........................................................................................................................47
Chapter 5: Conclusion and Recommendations........................................................................48
5.1 Conclusion......................................................................................................................48
5.2 Linking Objectives with Findings..................................................................................48
5.3 Recommendations..........................................................................................................50
5.4 Limitations of the research.............................................................................................51
5.5 Future Scope of research................................................................................................52
3.1 Introduction....................................................................................................................24
3.2 Research outline.............................................................................................................24
3.3 Research Paradigm.........................................................................................................24
3.3.1 Research Philosophy...............................................................................................24
3.3.2 Research approach..................................................................................................25
3.3.3 Research Design......................................................................................................25
3.4 Sampling method...........................................................................................................26
3.5 Research Strategy...........................................................................................................26
3.5.1 Justification for selection of research strategy (Survey).........................................27
3.6 Data collection methods.................................................................................................27
3.6.1 Quantitative Data Collection Method.....................................................................27
3.7 Accessibility issues........................................................................................................27
3.8 Ethical consideration......................................................................................................28
3.9 Data analysis..................................................................................................................28
3.10 Time table.....................................................................................................................28
3.11 Summary......................................................................................................................29
Chapter 4: Data analysis and findings......................................................................................30
4.0 Introduction....................................................................................................................30
4.1 Quantitative Data Representation and Interpretations.................................................30
4.1.1 Conducting survey questionnaires for the responses of 25 school children.........31
4.2 Summary........................................................................................................................47
Chapter 5: Conclusion and Recommendations........................................................................48
5.1 Conclusion......................................................................................................................48
5.2 Linking Objectives with Findings..................................................................................48
5.3 Recommendations..........................................................................................................50
5.4 Limitations of the research.............................................................................................51
5.5 Future Scope of research................................................................................................52

6CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
References................................................................................................................................53
Appendix 1: Survey questionnaires.........................................................................................57
References................................................................................................................................53
Appendix 1: Survey questionnaires.........................................................................................57
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Chapter 1: Introduction
1.1 Introduction and background
Kokkinoset al.(2016) stated that there is time of advanced Information Communication
Technology (ICT), where every aspect of our daily life is associated with learning. In current
era, internet is used for creation of useful resources by which people can get required
information at our fingerprints. The development of technology has led to many amazing
discoveries, better devices and better luxury products, while radically altering our daily lives.
Various highly developed Internet-connected gadgets have altered the way people interact,
learn, effort, shop, and play besides perform (Bele et al. 2014). At the same time, the
development of technology, its interactivity and increasing communication opportunities
represent risk for all its users, especially children.
The internet is used by young children and parents and it is critical to involve the role
players in ICT as well as cyber safety awareness, mainly in the schools those provided access
to the ICT devices. ICT is used in the schools with increasing number of learners. ICT
devices are exposed to schools which are consisted of cell phones, tablets to the computer
laboratory.Higher skills levels mean that children have more and more confidence in the use
of the Internet, although they are not mature and have no broader awareness to be safe on
the internet (Chandarman and Van Niekerk, 2018). Due to lack of awareness of internet
usage, the children and teenagers are possibly in danger and are often unsure what to do
about unsuitable materials on the internet. Parents know that they have short of information,
abilities in addition to considerate of this innovative technology that is needed to converse
children how to continue harmless on the Internet. This shows that children have more skills
in using technology than their parents. Many parents experience discomfort with position
setback as well as have fears related to Internet use by children. The parents are feared of that
if their children are using the internet for any unethical purposes or they are sharing of any
confidential data in any website (Sharples et al. 2009).
Internet use exposes children to many different online threats such as cyber bullying,
sharing of private information, phishing, scams, downloading of malware and cyber
predators. There is lack of skills among children to manage the cyber threats. In order to
overcome with the cyber threats, there is controlling over access of children so that the hacker
cannot access to any confidential data (Creswell, 2009). Hence, to allow children to use
Chapter 1: Introduction
1.1 Introduction and background
Kokkinoset al.(2016) stated that there is time of advanced Information Communication
Technology (ICT), where every aspect of our daily life is associated with learning. In current
era, internet is used for creation of useful resources by which people can get required
information at our fingerprints. The development of technology has led to many amazing
discoveries, better devices and better luxury products, while radically altering our daily lives.
Various highly developed Internet-connected gadgets have altered the way people interact,
learn, effort, shop, and play besides perform (Bele et al. 2014). At the same time, the
development of technology, its interactivity and increasing communication opportunities
represent risk for all its users, especially children.
The internet is used by young children and parents and it is critical to involve the role
players in ICT as well as cyber safety awareness, mainly in the schools those provided access
to the ICT devices. ICT is used in the schools with increasing number of learners. ICT
devices are exposed to schools which are consisted of cell phones, tablets to the computer
laboratory.Higher skills levels mean that children have more and more confidence in the use
of the Internet, although they are not mature and have no broader awareness to be safe on
the internet (Chandarman and Van Niekerk, 2018). Due to lack of awareness of internet
usage, the children and teenagers are possibly in danger and are often unsure what to do
about unsuitable materials on the internet. Parents know that they have short of information,
abilities in addition to considerate of this innovative technology that is needed to converse
children how to continue harmless on the Internet. This shows that children have more skills
in using technology than their parents. Many parents experience discomfort with position
setback as well as have fears related to Internet use by children. The parents are feared of that
if their children are using the internet for any unethical purposes or they are sharing of any
confidential data in any website (Sharples et al. 2009).
Internet use exposes children to many different online threats such as cyber bullying,
sharing of private information, phishing, scams, downloading of malware and cyber
predators. There is lack of skills among children to manage the cyber threats. In order to
overcome with the cyber threats, there is controlling over access of children so that the hacker
cannot access to any confidential data (Creswell, 2009). Hence, to allow children to use

8CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
opportunities offered by Internet and to protect them from cyber threats, it is necessary to
provide them with the knowledge and skills to stay safe on the Internet. Therefore, it is
required to aware the young school children about the security issues and their impact on
their daily lives. Therefore, it can be said that adequate learning and consciousness programs
will be more successful in raising awareness of cybersecurity for protection of children on
Internet. Therefore, it is important that suitable educational programs are introduced in
schools to allow children to develop harmless, smarter and more accountable Internet users.
1.2 Problem statement
In this present era of modern technology and trend, uses of online
tools and technology are increasing among school children. This is the most
vulnerable group of children that get targeted in socio-pathological incidents. As explained
by Livingstone et al. (2018, p.82), children in South Africa are gradually becoming
victimized of threats of social networks. Educational values and awareness are important in
this aspect. Therefore, the problem at present is to identify the role of awareness creation in
cyber safety among school children.
1.3 Main research question
The main research question for this research is:
What are the most suitable approaches and programs that could bring awareness among
school children about cyber safety in order to follow better practices related to internet, smart
phones and other cyber technologies?
1.3.1 Sub research questions
What is the current cyber safety awareness situation for children
at school in South Africa?
Which programs could be used to educate cyber safety for children
at school and home?
What are the methods used to create cyber safety awareness programs for young
children and parents?
What are the challenges in creating cyber safety awareness among
young learners?
opportunities offered by Internet and to protect them from cyber threats, it is necessary to
provide them with the knowledge and skills to stay safe on the Internet. Therefore, it is
required to aware the young school children about the security issues and their impact on
their daily lives. Therefore, it can be said that adequate learning and consciousness programs
will be more successful in raising awareness of cybersecurity for protection of children on
Internet. Therefore, it is important that suitable educational programs are introduced in
schools to allow children to develop harmless, smarter and more accountable Internet users.
1.2 Problem statement
In this present era of modern technology and trend, uses of online
tools and technology are increasing among school children. This is the most
vulnerable group of children that get targeted in socio-pathological incidents. As explained
by Livingstone et al. (2018, p.82), children in South Africa are gradually becoming
victimized of threats of social networks. Educational values and awareness are important in
this aspect. Therefore, the problem at present is to identify the role of awareness creation in
cyber safety among school children.
1.3 Main research question
The main research question for this research is:
What are the most suitable approaches and programs that could bring awareness among
school children about cyber safety in order to follow better practices related to internet, smart
phones and other cyber technologies?
1.3.1 Sub research questions
What is the current cyber safety awareness situation for children
at school in South Africa?
Which programs could be used to educate cyber safety for children
at school and home?
What are the methods used to create cyber safety awareness programs for young
children and parents?
What are the challenges in creating cyber safety awareness among
young learners?

9CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
1.4 The current cyber-security issues identified among school children
Use of ICT tools is integral part of new education system which has created a
vulnerable situation for school children in South Africa. As commented by Livingstone,
Mascheroni and Staksrud (2018, p.1103), mobile penetration in South Africa is 65.8% and
97.9% of young learners possess cell phones or have access to internet. It has been seen that
41.2% users spend more than 3 hours a day on internet and 60.1% of them have emerged in
cell phones (Khurana, Bleakley, Jordan and Romer, 2015, p.1039). In addition, 79% of
school children tell about monitored internet and cell phone usage. However, Livingstone et
al. (2017, p.85) argued that 63% of children are devoid of any parental guidance in issues
such as cybercrime and safety against this. However, school intervention programs have been
implemented to provide awareness of cyber safety processes. This research intends to help in
identifying probable challenges and developing awareness program schedules for
enlightenment of young children on this current issue. The issues can be tackled with the
support of reading promotions, seminars, posters, and brochure. These programs should
include practical guidelines for raising awareness in cyber security measures related to
mobile phone hacking, computer terrorism, and information warfare. The researcher had
identified some of cyber security issues in the research and obtained from different sitessuch
as keep the personal information safe, cyber bullying, hacking of password, online privacy,
social network, digital footprint, free downloads, phishing scams and cookies.Those cyber
threats are required to be considered before planning for the cyber safety programs.
1.5 Identified community
The identified community is the young learners of school going age of South Africa. As
explained by Naplavovaet al. (2014, p.3546), South Africa has 32.5% of students who are
victims of cyberbullying, 65% of students among them are targeted through Facebook. On
the other hand, 37% of students are victims at personal level and 42% are victimized by
anonymous individual. In this research program, the targeted community is the school
children who lack cyber awareness and fall victims.
1.6 What is community engagement?
Community engagement is referred to as the process of collaborative work and
decision-making. As explained by Kokkinos, Antoniadou, Asdre and Voulgaridou (2016,
p.439), community engagement can occur with geographical proximity with similar
1.4 The current cyber-security issues identified among school children
Use of ICT tools is integral part of new education system which has created a
vulnerable situation for school children in South Africa. As commented by Livingstone,
Mascheroni and Staksrud (2018, p.1103), mobile penetration in South Africa is 65.8% and
97.9% of young learners possess cell phones or have access to internet. It has been seen that
41.2% users spend more than 3 hours a day on internet and 60.1% of them have emerged in
cell phones (Khurana, Bleakley, Jordan and Romer, 2015, p.1039). In addition, 79% of
school children tell about monitored internet and cell phone usage. However, Livingstone et
al. (2017, p.85) argued that 63% of children are devoid of any parental guidance in issues
such as cybercrime and safety against this. However, school intervention programs have been
implemented to provide awareness of cyber safety processes. This research intends to help in
identifying probable challenges and developing awareness program schedules for
enlightenment of young children on this current issue. The issues can be tackled with the
support of reading promotions, seminars, posters, and brochure. These programs should
include practical guidelines for raising awareness in cyber security measures related to
mobile phone hacking, computer terrorism, and information warfare. The researcher had
identified some of cyber security issues in the research and obtained from different sitessuch
as keep the personal information safe, cyber bullying, hacking of password, online privacy,
social network, digital footprint, free downloads, phishing scams and cookies.Those cyber
threats are required to be considered before planning for the cyber safety programs.
1.5 Identified community
The identified community is the young learners of school going age of South Africa. As
explained by Naplavovaet al. (2014, p.3546), South Africa has 32.5% of students who are
victims of cyberbullying, 65% of students among them are targeted through Facebook. On
the other hand, 37% of students are victims at personal level and 42% are victimized by
anonymous individual. In this research program, the targeted community is the school
children who lack cyber awareness and fall victims.
1.6 What is community engagement?
Community engagement is referred to as the process of collaborative work and
decision-making. As explained by Kokkinos, Antoniadou, Asdre and Voulgaridou (2016,
p.439), community engagement can occur with geographical proximity with similar
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
situational interests. This helps in providing social activities that effective problem solving
and wellbeing. Community engages in present issue can help in creating awareness programs
for school goers. Opportunities for bringing change and development can be achieved
through the cooperation of community.
Proper ICT application and general awareness creation can be achieved through the
integration of community into research project. According to Maxwell (2008, p.246), cyber
community awareness community engagement helps in creating awareness and educating
young school students about risks involved in unguided use of cyber technology. Community
engagement helps in facilitating encouragement and educational programs to make them
aware of the use of computer skills and promote good security practices. This might help in
developing countermeasures to deal with this issue.
1.7 Improvement of cyber awareness for children
The proposed cyber security awareness program aims to educate young school goers
on basic computer security and safe and secure online usage (Kokkinos et al. 2016, p.441).
Furthermore, the proposed cyber security awareness program also aims to prepare children on
use of internet applications and new applications for cyberspace. The goal is to raise
awareness and understanding of the Internet's dangers in providing the knowledge needed to
make the right decisions in Internet-related situations. According to Hymelet al. (2015, p.16),
the proposed cyber security awareness program is not a PC literacy program but can be
enhanced and clear as a way of self-defence for users of Internet. Target audiences are
children that are computer users who have computing skills. The security awareness theory is
used by the researchers to understand expected outcomes related to selected research topic
(Stephanou, 2009).
1.8 Programs to be used for cyber safety awareness
Cyber safety awareness programs can be arranged in such a way that school students
get interested and motivated through the program. As stated by von Solms and von Solms
(2014, p.185), fun activities through the use of ICT can help in creating awareness in a
motivating way, such as security crossword puzzles, workshop in security awareness and
showing a movie to depict pros and cons of using cyber technology.
situational interests. This helps in providing social activities that effective problem solving
and wellbeing. Community engages in present issue can help in creating awareness programs
for school goers. Opportunities for bringing change and development can be achieved
through the cooperation of community.
Proper ICT application and general awareness creation can be achieved through the
integration of community into research project. According to Maxwell (2008, p.246), cyber
community awareness community engagement helps in creating awareness and educating
young school students about risks involved in unguided use of cyber technology. Community
engagement helps in facilitating encouragement and educational programs to make them
aware of the use of computer skills and promote good security practices. This might help in
developing countermeasures to deal with this issue.
1.7 Improvement of cyber awareness for children
The proposed cyber security awareness program aims to educate young school goers
on basic computer security and safe and secure online usage (Kokkinos et al. 2016, p.441).
Furthermore, the proposed cyber security awareness program also aims to prepare children on
use of internet applications and new applications for cyberspace. The goal is to raise
awareness and understanding of the Internet's dangers in providing the knowledge needed to
make the right decisions in Internet-related situations. According to Hymelet al. (2015, p.16),
the proposed cyber security awareness program is not a PC literacy program but can be
enhanced and clear as a way of self-defence for users of Internet. Target audiences are
children that are computer users who have computing skills. The security awareness theory is
used by the researchers to understand expected outcomes related to selected research topic
(Stephanou, 2009).
1.8 Programs to be used for cyber safety awareness
Cyber safety awareness programs can be arranged in such a way that school students
get interested and motivated through the program. As stated by von Solms and von Solms
(2014, p.185), fun activities through the use of ICT can help in creating awareness in a
motivating way, such as security crossword puzzles, workshop in security awareness and
showing a movie to depict pros and cons of using cyber technology.

11CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Security Crossword Puzzles: It is a security practice used where a clue with question
mark is provided. It means particular clue demands for second look. The clue is a play
of words used for the security purposes.
Security Awareness Day (workshop): A workshop is conducted to poses regarding
protection of physical and informational assets of the organization.
Promote reading: The parents and young children should read articles on
cybersecurity awareness.
Seminars: Seminars are conducted on weekly basis to aware people of the cyber
threats and their possible solutions.
Posters, banners and brochure: Those are used to design images in HD regarding the
cybersecurity.
These programs need to be planned previously with the collaboration of community and
practical guidance from experts in the field of cybercrime and security measures.
1.9 Structure of dissertation
Following are the structure of the dissertation which is consisted of chapters such as:
Chapter 1: Introduction of topic, research aim, questions and objectives: This
chapter provides a brief summary of the background related to selected research topic. It also
discusses about the aim of the study and questions based on which the entire research work is
carried out.
Chapter 2: Literature review: The literature study discusses about the cybersecurity
threats among the young children due to using of ICT devices in schools. The methods are
also discussed use to prevent from the cyber threats.
Chapter 3: Research methodology: The methods and procedures are discussed help
to collect information related to selected research topic. Primary data collection method is
used by use of survey method where questionnaire is selected to analyze the topic.
Chapter 4: Research findings and analysis: This part analyzes the data which are
collected from the responses of research participants. Each of the data is analyzed by
providing answers to each of survey questions.
Chapter 5: Conclusion and recommendations: The research outcome is provided in
this chapter with linking the research questions with the outcomes.
Security Crossword Puzzles: It is a security practice used where a clue with question
mark is provided. It means particular clue demands for second look. The clue is a play
of words used for the security purposes.
Security Awareness Day (workshop): A workshop is conducted to poses regarding
protection of physical and informational assets of the organization.
Promote reading: The parents and young children should read articles on
cybersecurity awareness.
Seminars: Seminars are conducted on weekly basis to aware people of the cyber
threats and their possible solutions.
Posters, banners and brochure: Those are used to design images in HD regarding the
cybersecurity.
These programs need to be planned previously with the collaboration of community and
practical guidance from experts in the field of cybercrime and security measures.
1.9 Structure of dissertation
Following are the structure of the dissertation which is consisted of chapters such as:
Chapter 1: Introduction of topic, research aim, questions and objectives: This
chapter provides a brief summary of the background related to selected research topic. It also
discusses about the aim of the study and questions based on which the entire research work is
carried out.
Chapter 2: Literature review: The literature study discusses about the cybersecurity
threats among the young children due to using of ICT devices in schools. The methods are
also discussed use to prevent from the cyber threats.
Chapter 3: Research methodology: The methods and procedures are discussed help
to collect information related to selected research topic. Primary data collection method is
used by use of survey method where questionnaire is selected to analyze the topic.
Chapter 4: Research findings and analysis: This part analyzes the data which are
collected from the responses of research participants. Each of the data is analyzed by
providing answers to each of survey questions.
Chapter 5: Conclusion and recommendations: The research outcome is provided in
this chapter with linking the research questions with the outcomes.

12CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
1.10 Conclusion
From the entire study on chapter one, it is concluded that the main aim is to analyse
the cyber threats among the children due to use of internet for daily activities. The young
children are used of internet for learning purposes. From the research objectives, it is
discussed that the possible methods are also summarized so that children can prevent from
the threats.
1.10 Conclusion
From the entire study on chapter one, it is concluded that the main aim is to analyse
the cyber threats among the children due to use of internet for daily activities. The young
children are used of internet for learning purposes. From the research objectives, it is
discussed that the possible methods are also summarized so that children can prevent from
the threats.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Chapter 2: Literature Review
2.1 Introduction
This particular chapter analyzes a literature study on the cyber security issues and
threats that the children are facing on the internet. Section 2.2 of this chapter classifies the
risks based on their types related to cyber issues. Section 2.3 analyzes the habits of children
and online interests by use of internet. Section 2.4 analyzes the risk management approaches
for identification of solutions of cyber threats so that the children and their parents can able to
deal with all of them.
2.2 Understanding Cyber Security
As with any technological advancement in history, whenever new opportunities arise,
there will always be those who will use them for their own benefit. Despite the threat of
viruses and malware since the dawn of computers, knowledge of security and integrity of
data in computer systems has not picked up speed until the rapid growth of the Internet.
According to ACS (Acs.org.au, 2016), cybercrime refers to destruction of websites, stealing
data or to committing fraudulent activities. Cyber security is an act to protect information
along with information system like network, data centres, computers, applications as well as
databases (Kushzhanov and Aliyev, 2018, p.98). The technological solutions such as
firewalls and antivirus software are used to secure data as well as computer networks. As the
nation is rapidly building of cyber infrastructure, therefore it is required to educate people to
keep the infrastructure safe.Cyber security and cyber security issues need to be included in
the educational procedure that begins at an early age. Safeguards help ensure the
confidentiality, accessibility, and truthfulness of computer systems by avoiding or limiting
property losses from cyber-attacks (Hassan et al. 2018).
2.2.1 Disadvantages of cyber security
The various disadvantages of cyber security depend on the pattern of its use and its
implication in daily life. Cyber security is important to eliminate adverse effects of cyber-
crimes. According to Wishart (2018, p.82), certain disadvantages of this system are
described below:
Chapter 2: Literature Review
2.1 Introduction
This particular chapter analyzes a literature study on the cyber security issues and
threats that the children are facing on the internet. Section 2.2 of this chapter classifies the
risks based on their types related to cyber issues. Section 2.3 analyzes the habits of children
and online interests by use of internet. Section 2.4 analyzes the risk management approaches
for identification of solutions of cyber threats so that the children and their parents can able to
deal with all of them.
2.2 Understanding Cyber Security
As with any technological advancement in history, whenever new opportunities arise,
there will always be those who will use them for their own benefit. Despite the threat of
viruses and malware since the dawn of computers, knowledge of security and integrity of
data in computer systems has not picked up speed until the rapid growth of the Internet.
According to ACS (Acs.org.au, 2016), cybercrime refers to destruction of websites, stealing
data or to committing fraudulent activities. Cyber security is an act to protect information
along with information system like network, data centres, computers, applications as well as
databases (Kushzhanov and Aliyev, 2018, p.98). The technological solutions such as
firewalls and antivirus software are used to secure data as well as computer networks. As the
nation is rapidly building of cyber infrastructure, therefore it is required to educate people to
keep the infrastructure safe.Cyber security and cyber security issues need to be included in
the educational procedure that begins at an early age. Safeguards help ensure the
confidentiality, accessibility, and truthfulness of computer systems by avoiding or limiting
property losses from cyber-attacks (Hassan et al. 2018).
2.2.1 Disadvantages of cyber security
The various disadvantages of cyber security depend on the pattern of its use and its
implication in daily life. Cyber security is important to eliminate adverse effects of cyber-
crimes. According to Wishart (2018, p.82), certain disadvantages of this system are
described below:

14CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Difficulty in configuration: In some cases the configuration of firewalls is difficult. It
is important to configure the firewalls correctly; otherwise, it will affect the security
system by providing loopholes (Gcazaet al. 2018).
Blocked user performance: incorrect firewalls configurations might block the
activities and performances of users. Inappropriate configuration of firewalls blocks
online activities.
Slower system: Using different firewalls make total system slower.
Excessive use of data: firewalls are needed to keep updated that uses a lot of internet
data. It is a slow process and requires periodic updates (Gámez-Guadix, Borrajo and
Almendros, 2016, p.100).
Costly: Different firewalls available in market are costly.
It is clear that using cyber security is important in protecting personal information
privacy; however, the processes can be quite disadvantageous for the user.
2.3 Risks for Children using internet
The Internet offers young people many positive educational and social benefits, but
unfortunately, there is a risk. According to Kortjan and Von Solms (2014, p.29), children and
adolescents are exposed to dangers and consciously or unconsciously take risks when using
the Internet and other digital technologies. In fact, some young people may be involved in
inappropriate or possibly illegal activities. There is a sum of online threats for children due to
the unidentified and abundant scenery Internet and the point of contact it provides (Goutam,
2015).
EU Kids Online Network, Livingstone and Haddon (2011, p.387) classify online risks to
children into three categories – content, contact and conduct.
Content risk is a threat which can exploit vulnerabilities of asset and group of assets
that can harm to the organization.
Content risks are such risks which are happened when children are engaged in the
process of communication.
This risk occurred when children may become initiator as well as actor of content.
Therefore, it is important to implement cyber security software and creating awareness to
safeguard young learners from the trap of cybercrimes.
Difficulty in configuration: In some cases the configuration of firewalls is difficult. It
is important to configure the firewalls correctly; otherwise, it will affect the security
system by providing loopholes (Gcazaet al. 2018).
Blocked user performance: incorrect firewalls configurations might block the
activities and performances of users. Inappropriate configuration of firewalls blocks
online activities.
Slower system: Using different firewalls make total system slower.
Excessive use of data: firewalls are needed to keep updated that uses a lot of internet
data. It is a slow process and requires periodic updates (Gámez-Guadix, Borrajo and
Almendros, 2016, p.100).
Costly: Different firewalls available in market are costly.
It is clear that using cyber security is important in protecting personal information
privacy; however, the processes can be quite disadvantageous for the user.
2.3 Risks for Children using internet
The Internet offers young people many positive educational and social benefits, but
unfortunately, there is a risk. According to Kortjan and Von Solms (2014, p.29), children and
adolescents are exposed to dangers and consciously or unconsciously take risks when using
the Internet and other digital technologies. In fact, some young people may be involved in
inappropriate or possibly illegal activities. There is a sum of online threats for children due to
the unidentified and abundant scenery Internet and the point of contact it provides (Goutam,
2015).
EU Kids Online Network, Livingstone and Haddon (2011, p.387) classify online risks to
children into three categories – content, contact and conduct.
Content risk is a threat which can exploit vulnerabilities of asset and group of assets
that can harm to the organization.
Content risks are such risks which are happened when children are engaged in the
process of communication.
This risk occurred when children may become initiator as well as actor of content.
Therefore, it is important to implement cyber security software and creating awareness to
safeguard young learners from the trap of cybercrimes.

15CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
2.3.1 Content Risks
As per the report of Equifax, 27% of personal data are subjected to massive hacking
(Accaglobal.com, 2018). On the other hand, 54% of school goers all over the world are
subjected to cyber bullying and crimes that result in severe depression and anxiety.Following
are two categorizes of the content risks such as age inappropriate content and incorrect
content which are discussed as:
Age inappropriate content: Content on the Internet is not divided among children of
below 18ages. Without supervision and guidance, a small child can also unintentionally or
deliberately find content that is disturbing, unambiguous or inappropriate (Symon, Cassell
and Johnson, 2018. Unacceptable age-related content includes unlawful content, such as
children pornographic or racist content.
Incorrect content: Users can now upload their personal content to the Internet. This
content can be sent to blogs, wikis, and social networks furthermore chat rooms. This allows
children to get incorrect content when browsing network. Young, new Internet clients are
sensitive to this because they do not contain internet abilities to successfully supervise these
dangers in addition to download safe data.
Therefore, it is important to consider content risk during cyber safety of children.
Assessing this domain may help in creating protecting services for cyber safety.
2.3.2 Contact Risks
Contact risk is related to the interaction of hackers and fraud individuals with school
children through online media. This is related to release of personal information in online
platform that is misused for criminal activities (Kortjan and Von Solms, 2014,
p.195).Following are two categorizes of the contact risks such as undesired contract and
disclosing of personal information which are discussed as:
Undesired contact: With growth in the use of social networking sites plus instant
messaging, children are more likely to receive unwanted and inappropriate contacts from
strangers and cyber-bullies.
“Cyberbullying is when technology, such as email, mobile phones, chat rooms and
social networking sites, are used to verbally or socially bully another person. Bullying is an
ongoing abuse of power to threaten or harm another person” (Bada and Sasse, 2014, p.129).
2.3.1 Content Risks
As per the report of Equifax, 27% of personal data are subjected to massive hacking
(Accaglobal.com, 2018). On the other hand, 54% of school goers all over the world are
subjected to cyber bullying and crimes that result in severe depression and anxiety.Following
are two categorizes of the content risks such as age inappropriate content and incorrect
content which are discussed as:
Age inappropriate content: Content on the Internet is not divided among children of
below 18ages. Without supervision and guidance, a small child can also unintentionally or
deliberately find content that is disturbing, unambiguous or inappropriate (Symon, Cassell
and Johnson, 2018. Unacceptable age-related content includes unlawful content, such as
children pornographic or racist content.
Incorrect content: Users can now upload their personal content to the Internet. This
content can be sent to blogs, wikis, and social networks furthermore chat rooms. This allows
children to get incorrect content when browsing network. Young, new Internet clients are
sensitive to this because they do not contain internet abilities to successfully supervise these
dangers in addition to download safe data.
Therefore, it is important to consider content risk during cyber safety of children.
Assessing this domain may help in creating protecting services for cyber safety.
2.3.2 Contact Risks
Contact risk is related to the interaction of hackers and fraud individuals with school
children through online media. This is related to release of personal information in online
platform that is misused for criminal activities (Kortjan and Von Solms, 2014,
p.195).Following are two categorizes of the contact risks such as undesired contract and
disclosing of personal information which are discussed as:
Undesired contact: With growth in the use of social networking sites plus instant
messaging, children are more likely to receive unwanted and inappropriate contacts from
strangers and cyber-bullies.
“Cyberbullying is when technology, such as email, mobile phones, chat rooms and
social networking sites, are used to verbally or socially bully another person. Bullying is an
ongoing abuse of power to threaten or harm another person” (Bada and Sasse, 2014, p.129).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Disclose of personal information: Many of the threats posed by the Internet can be
mitigated if young people are more active in protecting their privacy on the Internet. This
means that they need to be more conscious of the significances of disclosing credentials and
strategies to determine when it is suitable. Unluckily, many young people do not identify
simply situations in which the disclosure of information may endanger them (Farrukh,
Sadwickand Villasenor 2014). Being unconscious of this threat can lead to many different
risks, from phishing attacks to being the receivers of unsuitable publicity or advertising, and
therefore raising their vulnerability to unwanted interaction.
Therefore, it can be stated that while online, it is needed to secure personal data before
it came to contact risk.
2.3.3 Conduct Risks
Conduct risk refers to the risks that lead to detrimental effects of individuals in contact
due to improper use of cyber technology (Livingstone, Mascheroni and Staksrud, 2018).
Following are two categorizes of the conduct risks such as illegal downloads, bullying or
harassing children and create/upload incorrect or harmful materials which are discussed as:
Illegal downloads: There is obtaining of files which do not have right to use from the
internet.
Bullying or harassing other children: There is physical or verbal bullying of children
in the schools which leads to aggressive antisocial behavior.
Creating/uploading incorrect or harmful material: Unknowingly, there is creating and
uploading of harmful materials in the internet which can include of personal and
confidential information.
It is important to give significant importance to cyber security to manage conduct risks.
Disclose of personal information: Many of the threats posed by the Internet can be
mitigated if young people are more active in protecting their privacy on the Internet. This
means that they need to be more conscious of the significances of disclosing credentials and
strategies to determine when it is suitable. Unluckily, many young people do not identify
simply situations in which the disclosure of information may endanger them (Farrukh,
Sadwickand Villasenor 2014). Being unconscious of this threat can lead to many different
risks, from phishing attacks to being the receivers of unsuitable publicity or advertising, and
therefore raising their vulnerability to unwanted interaction.
Therefore, it can be stated that while online, it is needed to secure personal data before
it came to contact risk.
2.3.3 Conduct Risks
Conduct risk refers to the risks that lead to detrimental effects of individuals in contact
due to improper use of cyber technology (Livingstone, Mascheroni and Staksrud, 2018).
Following are two categorizes of the conduct risks such as illegal downloads, bullying or
harassing children and create/upload incorrect or harmful materials which are discussed as:
Illegal downloads: There is obtaining of files which do not have right to use from the
internet.
Bullying or harassing other children: There is physical or verbal bullying of children
in the schools which leads to aggressive antisocial behavior.
Creating/uploading incorrect or harmful material: Unknowingly, there is creating and
uploading of harmful materials in the internet which can include of personal and
confidential information.
It is important to give significant importance to cyber security to manage conduct risks.

17CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
2.3.4 Security risks
Security risks need to be assessed to ensure controls of cyber security appropriately.
2.3.4.1 Worms, Trojan Horses, Virus
The computer virus is spread throughout any medium and in other words, the
computer virus becomes effective when it is connects to malicious programs and executable
files. When there is running or executing of support files, the virus leaves infections. In area
of the computer science, it is identified that generation of viruses is not considered as natural
situation. It is required of human efforts for development of proper security in computer
networks. When the computer is connected with executable file or it runs a program, then
only the virus can harm the system. It is seen that the worm is not required to support
attached files when there is demand for viruses. It does not require any human activity. The
Trojan seems useful software at first glance, but it damages the computer and its software
during installation. Some Trojans make a backdoor for malicious users; remotely control the
computer, permitting privacy and personal data breach.
2.3.4.2 Spyware
Two significant things to know concerning spyware: the programs are such that they can
be downloaded to the computer without consent during visit to dangerous website and obtain
managing of the computer. Keep the computer up to date in particular for action system, web
browsers in addition to antivirus / antispyware security (King et al. 2018, p.240).
2.3.4.3 Phishing
Phishing is used email addresses or malicious sites to obtain private or monetary data. It
can take the method of e-mail, apparently from a trustworthy credit card business or
monetary institute that requests account information. When users react to the requested
information, crook scan employ it to contact the accounts. Do not open messages or
attachments from unidentified sources. Use spam filters to avoid unsolicited and unsafe
emails (Tucker and Director, 2015).
2.3.4.4 Sexting
There is a large database of present literature dealing with sexual harassment or
surplus sexual contact solicitation of minors by adults besides other young people.
Behaviours that constitute sexual harassment include requests for sexual contact, sexual
conversations, sending or searching for sexual images or disclosure of unwanted sexual
2.3.4 Security risks
Security risks need to be assessed to ensure controls of cyber security appropriately.
2.3.4.1 Worms, Trojan Horses, Virus
The computer virus is spread throughout any medium and in other words, the
computer virus becomes effective when it is connects to malicious programs and executable
files. When there is running or executing of support files, the virus leaves infections. In area
of the computer science, it is identified that generation of viruses is not considered as natural
situation. It is required of human efforts for development of proper security in computer
networks. When the computer is connected with executable file or it runs a program, then
only the virus can harm the system. It is seen that the worm is not required to support
attached files when there is demand for viruses. It does not require any human activity. The
Trojan seems useful software at first glance, but it damages the computer and its software
during installation. Some Trojans make a backdoor for malicious users; remotely control the
computer, permitting privacy and personal data breach.
2.3.4.2 Spyware
Two significant things to know concerning spyware: the programs are such that they can
be downloaded to the computer without consent during visit to dangerous website and obtain
managing of the computer. Keep the computer up to date in particular for action system, web
browsers in addition to antivirus / antispyware security (King et al. 2018, p.240).
2.3.4.3 Phishing
Phishing is used email addresses or malicious sites to obtain private or monetary data. It
can take the method of e-mail, apparently from a trustworthy credit card business or
monetary institute that requests account information. When users react to the requested
information, crook scan employ it to contact the accounts. Do not open messages or
attachments from unidentified sources. Use spam filters to avoid unsolicited and unsafe
emails (Tucker and Director, 2015).
2.3.4.4 Sexting
There is a large database of present literature dealing with sexual harassment or
surplus sexual contact solicitation of minors by adults besides other young people.
Behaviours that constitute sexual harassment include requests for sexual contact, sexual
conversations, sending or searching for sexual images or disclosure of unwanted sexual

18CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
content information. "Aggressive Sexual Solicitation" may also include the acquisition of
data performed by phone, offline and mail(Mitchell, Wolak, and Finkelhor, 2007)
Adverse or accidental contact to sexual content refers to all the circumstances in which
young people meet evocative content or erotic images / videos at the time of searching of
sexual content in the Internet. It is occurred at the time of Internet searches, unwanted
advertisements, email scams and when people are opening email and messages with knowing
the victim (Mitchell, Wolak and Finkelhor, 2007).
2.3.4.5 Cyberbullying
Some examples of cyberbullying are easily identifiable, taking into account language
along with tactics used to annoy and / or threaten the victim on the Internet. It is difficult to
identify which actions are serious and criminal offense until it provides an effect on young
children (Sabella, Patchin, and Hinduja, 2013, p.2709).Nevertheless, researchers generally
call cyberbullying activities by means of technological means to threaten or transmit intention
to harm. Communication often includes recurrence of activities and inequity between the
victim and the perpetrator.
In the case of cyber-harassment, you can conceptualize a lack of balance of powers in
different ways. For example, a bully may have more knowledge with the Internet than the
victim. The physical strength is not needed to maintain power, because cyberbullying is able
to protect the identity of the victim for a long time (Slonje, Smith and Frisen, 2013). It has
ability to hide ability which leads to cyberbullying by people. Content in cyberspace is not
possible to suppress can add to feelings of victim of humiliation, that someway prevent them
for asking for help from side of adults. There are some similarities among traditional bullying
along with cyberbullying. Some scientists are pointed to occurrence in the internet of the
cyber threats that young children are facing. Some Scientists point to the presence on the
Internet of many similar threats facing young people. For example, there is "often a link
between school bullying and cyberbullying” (Farrukh, Sadwickand Villasenor 2014, p. 15).
Strong overlap between traditional themes, personal persecution and cyberbullying - seeking
revenge and power - led many researchers to recommend the implementation of school and
general social strategies to cope with environment and basic cause’s harassment of peers
(Livingstone, Mascheroni and Staksrud, 2018). The strategies are included of security
awareness program in the school so that they are aware of cybersecurity threats due to use of
internet and ICT devices. There is also implementation of secured cyber infrastructure for
sharing of confidential information to others so that no third party can access to the
content information. "Aggressive Sexual Solicitation" may also include the acquisition of
data performed by phone, offline and mail(Mitchell, Wolak, and Finkelhor, 2007)
Adverse or accidental contact to sexual content refers to all the circumstances in which
young people meet evocative content or erotic images / videos at the time of searching of
sexual content in the Internet. It is occurred at the time of Internet searches, unwanted
advertisements, email scams and when people are opening email and messages with knowing
the victim (Mitchell, Wolak and Finkelhor, 2007).
2.3.4.5 Cyberbullying
Some examples of cyberbullying are easily identifiable, taking into account language
along with tactics used to annoy and / or threaten the victim on the Internet. It is difficult to
identify which actions are serious and criminal offense until it provides an effect on young
children (Sabella, Patchin, and Hinduja, 2013, p.2709).Nevertheless, researchers generally
call cyberbullying activities by means of technological means to threaten or transmit intention
to harm. Communication often includes recurrence of activities and inequity between the
victim and the perpetrator.
In the case of cyber-harassment, you can conceptualize a lack of balance of powers in
different ways. For example, a bully may have more knowledge with the Internet than the
victim. The physical strength is not needed to maintain power, because cyberbullying is able
to protect the identity of the victim for a long time (Slonje, Smith and Frisen, 2013). It has
ability to hide ability which leads to cyberbullying by people. Content in cyberspace is not
possible to suppress can add to feelings of victim of humiliation, that someway prevent them
for asking for help from side of adults. There are some similarities among traditional bullying
along with cyberbullying. Some scientists are pointed to occurrence in the internet of the
cyber threats that young children are facing. Some Scientists point to the presence on the
Internet of many similar threats facing young people. For example, there is "often a link
between school bullying and cyberbullying” (Farrukh, Sadwickand Villasenor 2014, p. 15).
Strong overlap between traditional themes, personal persecution and cyberbullying - seeking
revenge and power - led many researchers to recommend the implementation of school and
general social strategies to cope with environment and basic cause’s harassment of peers
(Livingstone, Mascheroni and Staksrud, 2018). The strategies are included of security
awareness program in the school so that they are aware of cybersecurity threats due to use of
internet and ICT devices. There is also implementation of secured cyber infrastructure for
sharing of confidential information to others so that no third party can access to the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
19CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
information. Cyberbullying can occur both online plus offline and vice versa, and in some
cases in offline mode, the victims have no identification with each other. Schools are taking
initiatives to modify relations furthermore attitudes that young people have towards one
another are seen as potentially effective prevention resources, although further research is
still needed on the most effective programs and strategies(Farrukh, Sadwickand Villasenor
2014).
2.3.4.6Passwords
The internet users are advised selecting strong passwords to children so that the hacker
cannot easily guess the password. The strong password should always contain an alphabet of
small letter, capital letter, numerical numbers and punctuation. On weekly basis, the
password should be changed unless it will be hacked or stolen by others (Tucker and
Director, 2015).
2.3.4.7 Social Media
The social media becomes a medium of interaction, while it may also create the
opportunity to disclose information, and even expose personal identity and security. The
internet users are advised to be smart with identification on social networks. That information
should not be published in social media which consists of individual’s identity. Other cyber
risks recognized in the search and were gained from a number of diverse websites include of
digital reputation, theft of information, online predators, copyright, plagiarism, posting
online, incident reporting and others.
Following table shows the comparison of risks, activities and nature of internet usage
that children are exposed due to online activities using internet.
RISKS CHILDREN MAY BE EXPOSED TO DUE TO ONLINE ACTIVITY
Activities Content Risks Contact Risks Conduct Risks
Playing
games
Age inappropriate content
- Pornography, racist
content, harmful
content
Commercial content
- Advertising,
marketing, spam,
sponsorship
Disclosure of personal
information
- Identity theft,
Undesirable contact
- Unfamiliar
person,
cyberbullying,
online groomers
Disclosure of personal
information
- Identity theft,
phishing, spam
Bullying
Uploading of harmful
material
information. Cyberbullying can occur both online plus offline and vice versa, and in some
cases in offline mode, the victims have no identification with each other. Schools are taking
initiatives to modify relations furthermore attitudes that young people have towards one
another are seen as potentially effective prevention resources, although further research is
still needed on the most effective programs and strategies(Farrukh, Sadwickand Villasenor
2014).
2.3.4.6Passwords
The internet users are advised selecting strong passwords to children so that the hacker
cannot easily guess the password. The strong password should always contain an alphabet of
small letter, capital letter, numerical numbers and punctuation. On weekly basis, the
password should be changed unless it will be hacked or stolen by others (Tucker and
Director, 2015).
2.3.4.7 Social Media
The social media becomes a medium of interaction, while it may also create the
opportunity to disclose information, and even expose personal identity and security. The
internet users are advised to be smart with identification on social networks. That information
should not be published in social media which consists of individual’s identity. Other cyber
risks recognized in the search and were gained from a number of diverse websites include of
digital reputation, theft of information, online predators, copyright, plagiarism, posting
online, incident reporting and others.
Following table shows the comparison of risks, activities and nature of internet usage
that children are exposed due to online activities using internet.
RISKS CHILDREN MAY BE EXPOSED TO DUE TO ONLINE ACTIVITY
Activities Content Risks Contact Risks Conduct Risks
Playing
games
Age inappropriate content
- Pornography, racist
content, harmful
content
Commercial content
- Advertising,
marketing, spam,
sponsorship
Disclosure of personal
information
- Identity theft,
Undesirable contact
- Unfamiliar
person,
cyberbullying,
online groomers
Disclosure of personal
information
- Identity theft,
phishing, spam
Bullying
Uploading of harmful
material
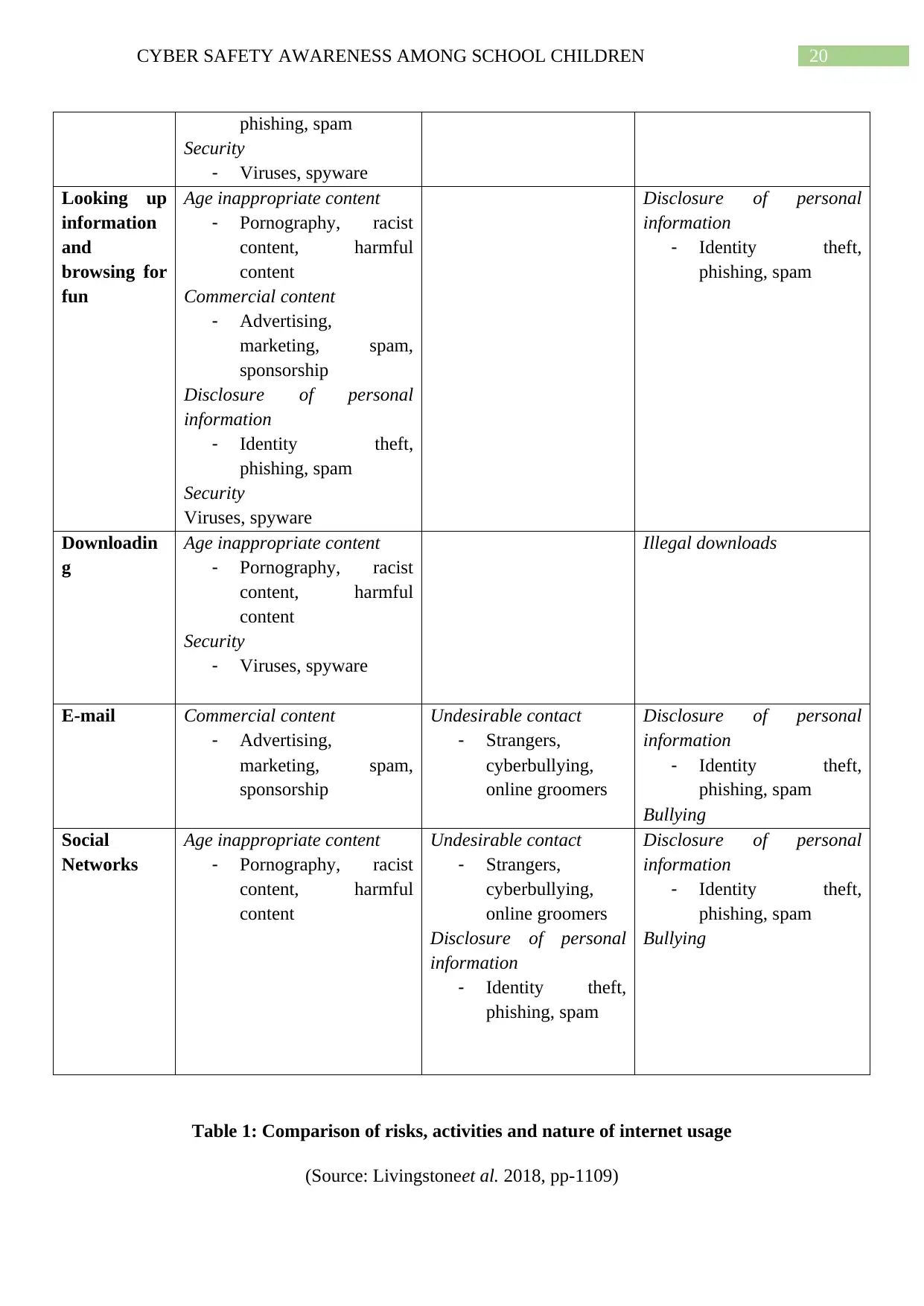
20CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
phishing, spam
Security
- Viruses, spyware
Looking up
information
and
browsing for
fun
Age inappropriate content
- Pornography, racist
content, harmful
content
Commercial content
- Advertising,
marketing, spam,
sponsorship
Disclosure of personal
information
- Identity theft,
phishing, spam
Security
Viruses, spyware
Disclosure of personal
information
- Identity theft,
phishing, spam
Downloadin
g
Age inappropriate content
- Pornography, racist
content, harmful
content
Security
- Viruses, spyware
Illegal downloads
E-mail Commercial content
- Advertising,
marketing, spam,
sponsorship
Undesirable contact
- Strangers,
cyberbullying,
online groomers
Disclosure of personal
information
- Identity theft,
phishing, spam
Bullying
Social
Networks
Age inappropriate content
- Pornography, racist
content, harmful
content
Undesirable contact
- Strangers,
cyberbullying,
online groomers
Disclosure of personal
information
- Identity theft,
phishing, spam
Disclosure of personal
information
- Identity theft,
phishing, spam
Bullying
Table 1: Comparison of risks, activities and nature of internet usage
(Source: Livingstoneet al. 2018, pp-1109)
phishing, spam
Security
- Viruses, spyware
Looking up
information
and
browsing for
fun
Age inappropriate content
- Pornography, racist
content, harmful
content
Commercial content
- Advertising,
marketing, spam,
sponsorship
Disclosure of personal
information
- Identity theft,
phishing, spam
Security
Viruses, spyware
Disclosure of personal
information
- Identity theft,
phishing, spam
Downloadin
g
Age inappropriate content
- Pornography, racist
content, harmful
content
Security
- Viruses, spyware
Illegal downloads
E-mail Commercial content
- Advertising,
marketing, spam,
sponsorship
Undesirable contact
- Strangers,
cyberbullying,
online groomers
Disclosure of personal
information
- Identity theft,
phishing, spam
Bullying
Social
Networks
Age inappropriate content
- Pornography, racist
content, harmful
content
Undesirable contact
- Strangers,
cyberbullying,
online groomers
Disclosure of personal
information
- Identity theft,
phishing, spam
Disclosure of personal
information
- Identity theft,
phishing, spam
Bullying
Table 1: Comparison of risks, activities and nature of internet usage
(Source: Livingstoneet al. 2018, pp-1109)

21CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
2.4 Information Security Awareness
Hänsch and Benenson (2014) discussed three dissimilar meanings of information security
awareness according to the way most scientists have seen them. Researchers contain
attempted to describe information security awareness as a thought and have come to the
assumption of these three meanings:
Security awareness as perception
Security awareness as protection
Security awareness as behaviour
Security awareness as perception contains the opinions of researchers that accomplish the
information security consciousness means that users should distinguish that threats, besides
risks occur (Norman, 2014). This statement defines the significance of security awareness as
perception. End users react independently to a variety of security threats, and the answer
depends on what type of person’s perception is the cyber threat. Security awareness as insight
also narrates to the level an end user thinks somewhat is protected or not (Huang, Rau and
Salvendy, 2010).
Security awareness as protection contains advice from academics who require users to
know that threats, risks, in addition to dangers exists, and the users also need to know what
measures they can use to protect themselves (Norman, 2014). The importance of safety
awareness concerns users' attention to security and their ability to recognize problems and
problems related to IT security and how they should reply.
Security awareness as behavior contains advice from researchers who state that the main
reasons for information security awareness are the effective mitigation of security threats.
This is possible when users distinguish what types of security measures they can practise to
defend them and to organise and continue applications. This importance of security
awareness focuses on how users behave in addition to believe about the security of
information, and the unit of transmission of knowledge about different factors in the field of
information security can influence the user behaviour (Norman, 2014).
2.5 Security Awareness among school Children
With the increase in Internet use by children and adolescents, the cyber threat is also
increasing. Providing a safe environment needs a thorough considerate of the types and the
spread of online threats faced by young Internet users, as well as most actual in mitigating
2.4 Information Security Awareness
Hänsch and Benenson (2014) discussed three dissimilar meanings of information security
awareness according to the way most scientists have seen them. Researchers contain
attempted to describe information security awareness as a thought and have come to the
assumption of these three meanings:
Security awareness as perception
Security awareness as protection
Security awareness as behaviour
Security awareness as perception contains the opinions of researchers that accomplish the
information security consciousness means that users should distinguish that threats, besides
risks occur (Norman, 2014). This statement defines the significance of security awareness as
perception. End users react independently to a variety of security threats, and the answer
depends on what type of person’s perception is the cyber threat. Security awareness as insight
also narrates to the level an end user thinks somewhat is protected or not (Huang, Rau and
Salvendy, 2010).
Security awareness as protection contains advice from academics who require users to
know that threats, risks, in addition to dangers exists, and the users also need to know what
measures they can use to protect themselves (Norman, 2014). The importance of safety
awareness concerns users' attention to security and their ability to recognize problems and
problems related to IT security and how they should reply.
Security awareness as behavior contains advice from researchers who state that the main
reasons for information security awareness are the effective mitigation of security threats.
This is possible when users distinguish what types of security measures they can practise to
defend them and to organise and continue applications. This importance of security
awareness focuses on how users behave in addition to believe about the security of
information, and the unit of transmission of knowledge about different factors in the field of
information security can influence the user behaviour (Norman, 2014).
2.5 Security Awareness among school Children
With the increase in Internet use by children and adolescents, the cyber threat is also
increasing. Providing a safe environment needs a thorough considerate of the types and the
spread of online threats faced by young Internet users, as well as most actual in mitigating
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
this risk(Farrukh, Sadwickand Villasenor 2014). There are several educators playing a role in
the cyber education of children. These includes of:
Government: Government should develop structures to adequately support
cybersecurity, implementation and promotion of a culture of cybersecurity through
support and funding research and education of cybersecurity initiatives and to
encourage compliance with cybersecurity standards(Kritzinger et al.2015)
Law enforcement: Legislation on cybercrime against children is crucial to protect
them from cyberbullying, cyber-persecution, and harassment on the Internet and so
on
Parents/guardians: Parents or guardians have the most direct impact on children and
play an important role in cybersecurity education and awareness, which includes
education on safe and responsible use, principles and assistance whenusing the
Internet
Schools: Cyber safety strategies should be establish and carry out in schools
Teachers: Teachers should have knowledge in the field of cybersecurity, act as
counselors for children, provide cybersecurity messages and act as observers notice
changes in the child's behavior
Peers: Peer mentoring is a very effective way to encourage children to stay secure
online. Encouragement, support and knowledge sharing give children more
confidence in practicing safe online behavior
2.5.1 Cyber Countermeasures
2.5.1.1 Preventive Cyber bullying
Cyber bullying is the result of using internet and cell phones for 80.5% of time a day by
young children. According to Kinget al. (2018, p.233), 46% of children face online bullying,
and 70% of children have witnessed this type of activities. In addition, it was reported that
92.5% of online bullying incidents occurred through commenting and chatting on social
media. However, cyber securities are there to provide preventive measures against cyber
bullying which are described as follows.
Interacting with psychologists and parents help in providing solutions to issues like
cyber bullying. In addition, it helps in generating awareness among young children.
Role models are used to support cyber bullying victims and to provide a way to
eliminate this practice.
this risk(Farrukh, Sadwickand Villasenor 2014). There are several educators playing a role in
the cyber education of children. These includes of:
Government: Government should develop structures to adequately support
cybersecurity, implementation and promotion of a culture of cybersecurity through
support and funding research and education of cybersecurity initiatives and to
encourage compliance with cybersecurity standards(Kritzinger et al.2015)
Law enforcement: Legislation on cybercrime against children is crucial to protect
them from cyberbullying, cyber-persecution, and harassment on the Internet and so
on
Parents/guardians: Parents or guardians have the most direct impact on children and
play an important role in cybersecurity education and awareness, which includes
education on safe and responsible use, principles and assistance whenusing the
Internet
Schools: Cyber safety strategies should be establish and carry out in schools
Teachers: Teachers should have knowledge in the field of cybersecurity, act as
counselors for children, provide cybersecurity messages and act as observers notice
changes in the child's behavior
Peers: Peer mentoring is a very effective way to encourage children to stay secure
online. Encouragement, support and knowledge sharing give children more
confidence in practicing safe online behavior
2.5.1 Cyber Countermeasures
2.5.1.1 Preventive Cyber bullying
Cyber bullying is the result of using internet and cell phones for 80.5% of time a day by
young children. According to Kinget al. (2018, p.233), 46% of children face online bullying,
and 70% of children have witnessed this type of activities. In addition, it was reported that
92.5% of online bullying incidents occurred through commenting and chatting on social
media. However, cyber securities are there to provide preventive measures against cyber
bullying which are described as follows.
Interacting with psychologists and parents help in providing solutions to issues like
cyber bullying. In addition, it helps in generating awareness among young children.
Role models are used to support cyber bullying victims and to provide a way to
eliminate this practice.

23CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Online activities are to be monitored and performed under elder’s guidance.
Community activities are needed to be arranged that would involve parents and youth
in creating policies against cyber-crime (Hassanet al. 2018, p.93).
Positive climate and voluntary activities of community will help in reducing
cybercrimes and facilitates cyber safety.
2.6 Literature gap
The research study will fill literature gap in current approach to deal with the
cybercrime by creating innovative research. It will directly involve stakeholders as well as
public to map the cyber threats and offer tailored advices for various community groups.
There is also big gap between recognition of cyber threats and manifestation of desired
behavior at daily intervals. There is also a review of evidences require further research to
develop an understanding of cyberbullying among young school going children. There is also
gap in parent’s abilities, knowledge plus skills to prevent from the cyber threats. There is
little research on the cyber threats cases in real life. Gaps among capability, knowledge and
skills of young children are also an evidence in online safety.
Online activities are to be monitored and performed under elder’s guidance.
Community activities are needed to be arranged that would involve parents and youth
in creating policies against cyber-crime (Hassanet al. 2018, p.93).
Positive climate and voluntary activities of community will help in reducing
cybercrimes and facilitates cyber safety.
2.6 Literature gap
The research study will fill literature gap in current approach to deal with the
cybercrime by creating innovative research. It will directly involve stakeholders as well as
public to map the cyber threats and offer tailored advices for various community groups.
There is also big gap between recognition of cyber threats and manifestation of desired
behavior at daily intervals. There is also a review of evidences require further research to
develop an understanding of cyberbullying among young school going children. There is also
gap in parent’s abilities, knowledge plus skills to prevent from the cyber threats. There is
little research on the cyber threats cases in real life. Gaps among capability, knowledge and
skills of young children are also an evidence in online safety.

24CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Chapter 3: Research Methodology
3.1 Introduction
In this chapter, the researcher framed a suitable research methodology for carrying out
research effectively. The vital key to research work is research as well as analysis of the steps
which are required to implement. The researcher should test the research questions and
facilitate access of entire research design like collection furthermore investigation of data.
The data collection methods included of primary and secondary sources of data. In order to
collect primary data, questionnaire is used and secondary data using websites, books and
journal articles. Both sets of data collection methods are utilized to create valuable
information of research.
3.2 Research outline
The research outline provides the primary structure based on which the research
methodology can be formed. In this context, positivism research philosophy, deductive
research approach, and descriptive research design. Data collection has been conducted in
primary quantitative as well as qualitative method to analyse the effects of cyber safety
among school going children. The children and parents are surveyed based on the questions
prepared based on selected research topic. The research ethics, validity, and reliability have
been taken into consideration during survey.
3.3 Research Paradigm
3.3.1 Research Philosophy
Research philosophy used in this research is positivism. Fletcher (2018, p.181)
commented that positivism deals with real and available facts of life. There are other research
philosophies that help in deciding the research methodology. Interpretivism helps in dealing
with perception of people based on particular situation (Guestet al.2018, p.693). This
research philosophy helps in emphasizing on observation of target group to examine research
problem. Positivism theory of research philosophy helps in making useful logical analysis of
collected data. In addition, research problems are evaluated to support actual facts and pieces
of evidence available.
Chapter 3: Research Methodology
3.1 Introduction
In this chapter, the researcher framed a suitable research methodology for carrying out
research effectively. The vital key to research work is research as well as analysis of the steps
which are required to implement. The researcher should test the research questions and
facilitate access of entire research design like collection furthermore investigation of data.
The data collection methods included of primary and secondary sources of data. In order to
collect primary data, questionnaire is used and secondary data using websites, books and
journal articles. Both sets of data collection methods are utilized to create valuable
information of research.
3.2 Research outline
The research outline provides the primary structure based on which the research
methodology can be formed. In this context, positivism research philosophy, deductive
research approach, and descriptive research design. Data collection has been conducted in
primary quantitative as well as qualitative method to analyse the effects of cyber safety
among school going children. The children and parents are surveyed based on the questions
prepared based on selected research topic. The research ethics, validity, and reliability have
been taken into consideration during survey.
3.3 Research Paradigm
3.3.1 Research Philosophy
Research philosophy used in this research is positivism. Fletcher (2018, p.181)
commented that positivism deals with real and available facts of life. There are other research
philosophies that help in deciding the research methodology. Interpretivism helps in dealing
with perception of people based on particular situation (Guestet al.2018, p.693). This
research philosophy helps in emphasizing on observation of target group to examine research
problem. Positivism theory of research philosophy helps in making useful logical analysis of
collected data. In addition, research problems are evaluated to support actual facts and pieces
of evidence available.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

25CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
3.3.1.1 Justification of choosing positivism research philosophy
After making fact-based analysis of the research philosophies, positivism philosophy is
opted for furthering the research project because this philosophy is capable of making logical
and critical analysis of research investigation. As opined by Welch and Piekkari (2018,
p.714), positivism helps in generating research results with the support from real facts.
Therefore, in this case, study, the effects of cyber safety processes can be determined through
analysis of facts and data obtained from the sample group.
3.3.2 Research approach
There are two major kinds of research approaches, namely inductive and deductive
approach. Symon, Cassell and Johnson (2018, p.134) commented that deductive approach is
useful in obtaining authentic knowledge by the top-down and bottom-up approach by creating
a hypothesis. On the other hand, the inductive approach facilitates in analysing new theories
significant to a research topic.
3.3.2.1 Justification of choosing deductive research approach
With a thorough analysis of both kinds of research approaches, this research topic
provides emphasis on obtaining fact-based knowledge. Therefore, it is important to
implement a deductive approach to research. This approach helps in reducing information
based on present information and existing theories, concepts and models on cyber security
and cyber safety. There is modest scope to develop new theories on this topic. Thus,
inductive approach would not be appropriate for this investigation.
3.3.3 Research Design
Three types of research designs (explanatory, exploratory and descriptive) are used for
conducting research processes. Research design is selected based on research objectives and
aims to plan for research conduction. Zukauskas, Vveinhardt and Andriukaitiene (2018, p.7)
stated that exploratory research design is used to take a psychological aspect of research. In
case of exploratory research design, research data is explained with both positive and
negative outcomes. These two research designs are used when formal objective or question
set is not formulated. On the other hand, Panhwar, Ansari and Shah (2018, p.253) commented
that descriptive design is useful for research where a set of objectives in addition to questions
are selected. In this method, positive as well as negative viewpoints of the research results are
considered to come to a definite conclusion.
3.3.1.1 Justification of choosing positivism research philosophy
After making fact-based analysis of the research philosophies, positivism philosophy is
opted for furthering the research project because this philosophy is capable of making logical
and critical analysis of research investigation. As opined by Welch and Piekkari (2018,
p.714), positivism helps in generating research results with the support from real facts.
Therefore, in this case, study, the effects of cyber safety processes can be determined through
analysis of facts and data obtained from the sample group.
3.3.2 Research approach
There are two major kinds of research approaches, namely inductive and deductive
approach. Symon, Cassell and Johnson (2018, p.134) commented that deductive approach is
useful in obtaining authentic knowledge by the top-down and bottom-up approach by creating
a hypothesis. On the other hand, the inductive approach facilitates in analysing new theories
significant to a research topic.
3.3.2.1 Justification of choosing deductive research approach
With a thorough analysis of both kinds of research approaches, this research topic
provides emphasis on obtaining fact-based knowledge. Therefore, it is important to
implement a deductive approach to research. This approach helps in reducing information
based on present information and existing theories, concepts and models on cyber security
and cyber safety. There is modest scope to develop new theories on this topic. Thus,
inductive approach would not be appropriate for this investigation.
3.3.3 Research Design
Three types of research designs (explanatory, exploratory and descriptive) are used for
conducting research processes. Research design is selected based on research objectives and
aims to plan for research conduction. Zukauskas, Vveinhardt and Andriukaitiene (2018, p.7)
stated that exploratory research design is used to take a psychological aspect of research. In
case of exploratory research design, research data is explained with both positive and
negative outcomes. These two research designs are used when formal objective or question
set is not formulated. On the other hand, Panhwar, Ansari and Shah (2018, p.253) commented
that descriptive design is useful for research where a set of objectives in addition to questions
are selected. In this method, positive as well as negative viewpoints of the research results are
considered to come to a definite conclusion.

26CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
3.3.3.1 Justification for choosing descriptive research design
In this research, there are specific objectives and aims that are to be achieved.
Descriptive design helped in providing suitable structure to continue with formal research
methodology. This has helped in providing scope for proceeding with enriched analysis in
order to collect relevant information for fulfilling the purpose of the study. In addition,
descriptive research design supported the limitations faced by the researcher in form of time
constraints. The cross-sectional survey was supported by this research design to develop
productive results by in-depth analysis of sample population.
3.4 Sampling method
There are two sampling methods namely, probability and non-probability sampling
method to help in conducting research survey. Wright (2015, p.2) explained that a probability
sampling method helps the researcher in selecting respondents randomly. However, this
sampling method needs to consider the sample as a unit. The purposeful selection of sample
is needed to be considered in case of the non-probability method of sampling.
In this research, probability sampling methods are conducted to gather primary data.
The survey has been conducted on a sample size of 25 school children of South Africa.
Probability sampling emphasized unbiased management of the population and it is cost and
time effective. Each of the research participants have equal chance to be selected. The sample
population was selected from International School of South Africa and the population was
school children. The survey questionnaires were distributed among the school children and
the participants those were interested in the research provide their responses. As per the
researcher, the selected sample size is 50, but only 25 students were interested to provide
their responses. The researchers approached the respondents of a sample according to the
convenience of the respondents to collect enriched and refined data. The fixed sample size
helped in developing authenticated research data for analysis of the research topic.
3.5 Research Strategy
Based on the research aims, research strategies are selected to better achievement of
those aims and objectives. As commented by Fletcher (2018, p.185), research strategies are
related to surveys, interviews, experiments and case studies. Surveys help in collecting data
from a large population in a rate and instance effective manner. On the other hand, interviews
help in collecting data which are enriched with knowledge of selected people. In case of case
3.3.3.1 Justification for choosing descriptive research design
In this research, there are specific objectives and aims that are to be achieved.
Descriptive design helped in providing suitable structure to continue with formal research
methodology. This has helped in providing scope for proceeding with enriched analysis in
order to collect relevant information for fulfilling the purpose of the study. In addition,
descriptive research design supported the limitations faced by the researcher in form of time
constraints. The cross-sectional survey was supported by this research design to develop
productive results by in-depth analysis of sample population.
3.4 Sampling method
There are two sampling methods namely, probability and non-probability sampling
method to help in conducting research survey. Wright (2015, p.2) explained that a probability
sampling method helps the researcher in selecting respondents randomly. However, this
sampling method needs to consider the sample as a unit. The purposeful selection of sample
is needed to be considered in case of the non-probability method of sampling.
In this research, probability sampling methods are conducted to gather primary data.
The survey has been conducted on a sample size of 25 school children of South Africa.
Probability sampling emphasized unbiased management of the population and it is cost and
time effective. Each of the research participants have equal chance to be selected. The sample
population was selected from International School of South Africa and the population was
school children. The survey questionnaires were distributed among the school children and
the participants those were interested in the research provide their responses. As per the
researcher, the selected sample size is 50, but only 25 students were interested to provide
their responses. The researchers approached the respondents of a sample according to the
convenience of the respondents to collect enriched and refined data. The fixed sample size
helped in developing authenticated research data for analysis of the research topic.
3.5 Research Strategy
Based on the research aims, research strategies are selected to better achievement of
those aims and objectives. As commented by Fletcher (2018, p.185), research strategies are
related to surveys, interviews, experiments and case studies. Surveys help in collecting data
from a large population in a rate and instance effective manner. On the other hand, interviews
help in collecting data which are enriched with knowledge of selected people. In case of case

27CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
studies, they help in collecting secondary data and providing secondary knowledge.
Experiments are useful in obtaining new theories and models in relation to research topic.
These research strategies help in providing viable and reliable data for further researches.
3.5.1 Justification for selection of research strategy (Survey)
After in view of diverse research strategies, the researcher opted for surveys to conduct
the study and come to conclusion to answer research questions. With the help of survey
conducted on 25 school children, extensive and original data were obtained. The survey
conducted on school children is most suitable because it provided research results in a cost
and time effective manner. A vast population can be addressed through this research strategy.
Therefore, it is justified to use this research strategy in this investigation process.
3.6 Data collection methods
Primary research method is selected for collecting data in this research investigation.
Questionnaire method is most important approach throughout which primary data was
collected for this research study. The primary sources of data collection method were
conducted through questionnaire on basis of school children experiences of cyber awareness.
3.6.1 Quantitative Data Collection Method
Quantitative data collection method benefits in collecting numerical data that can be
signified in the form of table, charts, and graphs. This is a cost-effective manner for data
collection. Guest et al. (2018, p.692) stated that this method of data collection helps in
collecting authentic results that can be subjected to testing. This type of data collection is
conducted through survey. A list of questions was prepared based on demographic profile of
the participants and questions related to cyber awareness among young children. After
distributing the survey questions in offline mode, the interested participants provide their
responses. The questions on the survey were related to awareness of cyber threats among
children and possible methods to prevent from the threats. After collecting the data, the
researcher analyzed all data in form of statistical form. The responses of participants are
analyzed in percentage of responses.
3.7 Accessibility issues
Accessibility issues are faced during the conduction of research strategies. In this case,
the researcher faced certain accessibility issues due to the unavailability of students to share
experiences. Students due to lack of maturity were closed up to answering questions
studies, they help in collecting secondary data and providing secondary knowledge.
Experiments are useful in obtaining new theories and models in relation to research topic.
These research strategies help in providing viable and reliable data for further researches.
3.5.1 Justification for selection of research strategy (Survey)
After in view of diverse research strategies, the researcher opted for surveys to conduct
the study and come to conclusion to answer research questions. With the help of survey
conducted on 25 school children, extensive and original data were obtained. The survey
conducted on school children is most suitable because it provided research results in a cost
and time effective manner. A vast population can be addressed through this research strategy.
Therefore, it is justified to use this research strategy in this investigation process.
3.6 Data collection methods
Primary research method is selected for collecting data in this research investigation.
Questionnaire method is most important approach throughout which primary data was
collected for this research study. The primary sources of data collection method were
conducted through questionnaire on basis of school children experiences of cyber awareness.
3.6.1 Quantitative Data Collection Method
Quantitative data collection method benefits in collecting numerical data that can be
signified in the form of table, charts, and graphs. This is a cost-effective manner for data
collection. Guest et al. (2018, p.692) stated that this method of data collection helps in
collecting authentic results that can be subjected to testing. This type of data collection is
conducted through survey. A list of questions was prepared based on demographic profile of
the participants and questions related to cyber awareness among young children. After
distributing the survey questions in offline mode, the interested participants provide their
responses. The questions on the survey were related to awareness of cyber threats among
children and possible methods to prevent from the threats. After collecting the data, the
researcher analyzed all data in form of statistical form. The responses of participants are
analyzed in percentage of responses.
3.7 Accessibility issues
Accessibility issues are faced during the conduction of research strategies. In this case,
the researcher faced certain accessibility issues due to the unavailability of students to share
experiences. Students due to lack of maturity were closed up to answering questions
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
28CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
truthfully. However, the researcher arranged offline surveys in International School of South
Africa to get individualized answers from sample population.
3.8 Ethical consideration
During the conduction of research, it is mandatory to maintain ethical considerations.
In Accordance to Data Protection Act 1998, the researcher made sure not to pressurize
respondents. They were given liberty to express their individualized opinions. Nevertheless,
the collected data was made confidential and used only for academic purposes.
3.9 Data analysis
All the collected data are evaluated in quantitative manner by representing them into
percentage form for better understanding and easy visualization of the collected data. In
addition, numeric data collected from the survey are represented through graphs, tables, and
charts for better convenience. This provided an in-depth study of the results obtained from
the questionnaire conducted on 25 school children.
3.10 Time table
Figure 3.1: Time table of research methodology
(Source: Created by author)
truthfully. However, the researcher arranged offline surveys in International School of South
Africa to get individualized answers from sample population.
3.8 Ethical consideration
During the conduction of research, it is mandatory to maintain ethical considerations.
In Accordance to Data Protection Act 1998, the researcher made sure not to pressurize
respondents. They were given liberty to express their individualized opinions. Nevertheless,
the collected data was made confidential and used only for academic purposes.
3.9 Data analysis
All the collected data are evaluated in quantitative manner by representing them into
percentage form for better understanding and easy visualization of the collected data. In
addition, numeric data collected from the survey are represented through graphs, tables, and
charts for better convenience. This provided an in-depth study of the results obtained from
the questionnaire conducted on 25 school children.
3.10 Time table
Figure 3.1: Time table of research methodology
(Source: Created by author)

29CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
3.11 Summary
It is summarized that a small group of population is selected for the research study. It
works with an objective to get proper as well as reliable information related to selected
research topic. The questions are prepared by the researcher where school children is selected
to gather the data. Based on the responses of school children, the data are analyzed by using
statistical graphs and charts.
3.11 Summary
It is summarized that a small group of population is selected for the research study. It
works with an objective to get proper as well as reliable information related to selected
research topic. The questions are prepared by the researcher where school children is selected
to gather the data. Based on the responses of school children, the data are analyzed by using
statistical graphs and charts.

30CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Chapter 4: Data analysis and findings
4.0 Introduction
This chapter explains the different age group of students that have awareness about
cyber safety. This chapter discusses the different materials that will be preferred by school
students for cyber safety training such as workshop and online awareness material. This
chapter also explains the purpose of a cell phone being used by school children such as for
accessing the internet and social network engagement. This chapter also discusses how
school students rate their knowledge of cyber safety awareness.
This chapter explains that whether school students have admission to the Internet and
the point of using the internet. Moreover, this chapter explains the different danger and
threats related to cell phones such as health risks such as cancer and tumour and security risk
such as sharing of personal information. This chapter explains school children having access
to internet and how cyber safety awareness help children such as helping them in developing
critical thinking skills and protecting them from harmful content. This chapter also explains
the benefits of cyber safety for school children.
4.1 Quantitative Data Representation and Interpretations
The researcher conducted a quantitative research study to analyse the collected data. At
first, demographic profile of the school students are analyzed to determine the age group,
gender of the participants. The researcher tried to show data analysis of cyber safety
awareness among the school children. With help of this data analysis method, the researcher
tried to increase quality of collected data and make better analysis of data along with
conclusion on selected research topic. With this data analysis method, the researcher
implemented theoretical knowledge in practical application. In this present section, the school
children of International School of South Africa were considered for quantitative analysis
such that the researcher can understand the importance of cybersecurity awareness among
young school children. The total number of respondents involved in data analysis are 25 as
others were not interested to fill the questionnaire and therefore they were discarded from
sample of this research study.
Chapter 4: Data analysis and findings
4.0 Introduction
This chapter explains the different age group of students that have awareness about
cyber safety. This chapter discusses the different materials that will be preferred by school
students for cyber safety training such as workshop and online awareness material. This
chapter also explains the purpose of a cell phone being used by school children such as for
accessing the internet and social network engagement. This chapter also discusses how
school students rate their knowledge of cyber safety awareness.
This chapter explains that whether school students have admission to the Internet and
the point of using the internet. Moreover, this chapter explains the different danger and
threats related to cell phones such as health risks such as cancer and tumour and security risk
such as sharing of personal information. This chapter explains school children having access
to internet and how cyber safety awareness help children such as helping them in developing
critical thinking skills and protecting them from harmful content. This chapter also explains
the benefits of cyber safety for school children.
4.1 Quantitative Data Representation and Interpretations
The researcher conducted a quantitative research study to analyse the collected data. At
first, demographic profile of the school students are analyzed to determine the age group,
gender of the participants. The researcher tried to show data analysis of cyber safety
awareness among the school children. With help of this data analysis method, the researcher
tried to increase quality of collected data and make better analysis of data along with
conclusion on selected research topic. With this data analysis method, the researcher
implemented theoretical knowledge in practical application. In this present section, the school
children of International School of South Africa were considered for quantitative analysis
such that the researcher can understand the importance of cybersecurity awareness among
young school children. The total number of respondents involved in data analysis are 25 as
others were not interested to fill the questionnaire and therefore they were discarded from
sample of this research study.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

31CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
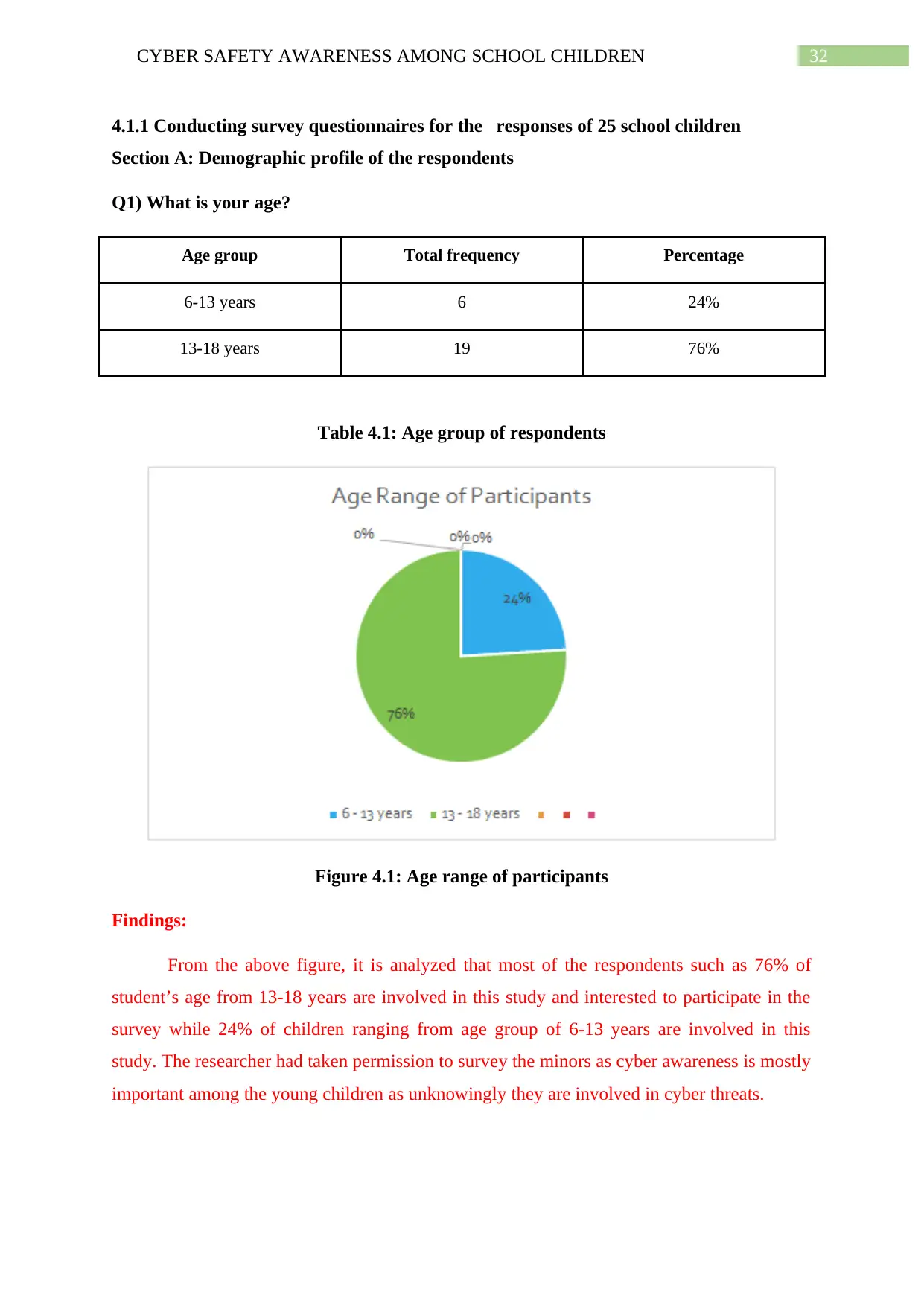
32CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
4.1.1 Conducting survey questionnaires for the responses of 25 school children
Section A: Demographic profile of the respondents
Q1) What is your age?
Age group Total frequency Percentage
6-13 years 6 24%
13-18 years 19 76%
Table 4.1: Age group of respondents
Figure 4.1: Age range of participants
Findings:
From the above figure, it is analyzed that most of the respondents such as 76% of
student’s age from 13-18 years are involved in this study and interested to participate in the
survey while 24% of children ranging from age group of 6-13 years are involved in this
study. The researcher had taken permission to survey the minors as cyber awareness is mostly
important among the young children as unknowingly they are involved in cyber threats.
4.1.1 Conducting survey questionnaires for the responses of 25 school children
Section A: Demographic profile of the respondents
Q1) What is your age?
Age group Total frequency Percentage
6-13 years 6 24%
13-18 years 19 76%
Table 4.1: Age group of respondents
Figure 4.1: Age range of participants
Findings:
From the above figure, it is analyzed that most of the respondents such as 76% of
student’s age from 13-18 years are involved in this study and interested to participate in the
survey while 24% of children ranging from age group of 6-13 years are involved in this
study. The researcher had taken permission to survey the minors as cyber awareness is mostly
important among the young children as unknowingly they are involved in cyber threats.
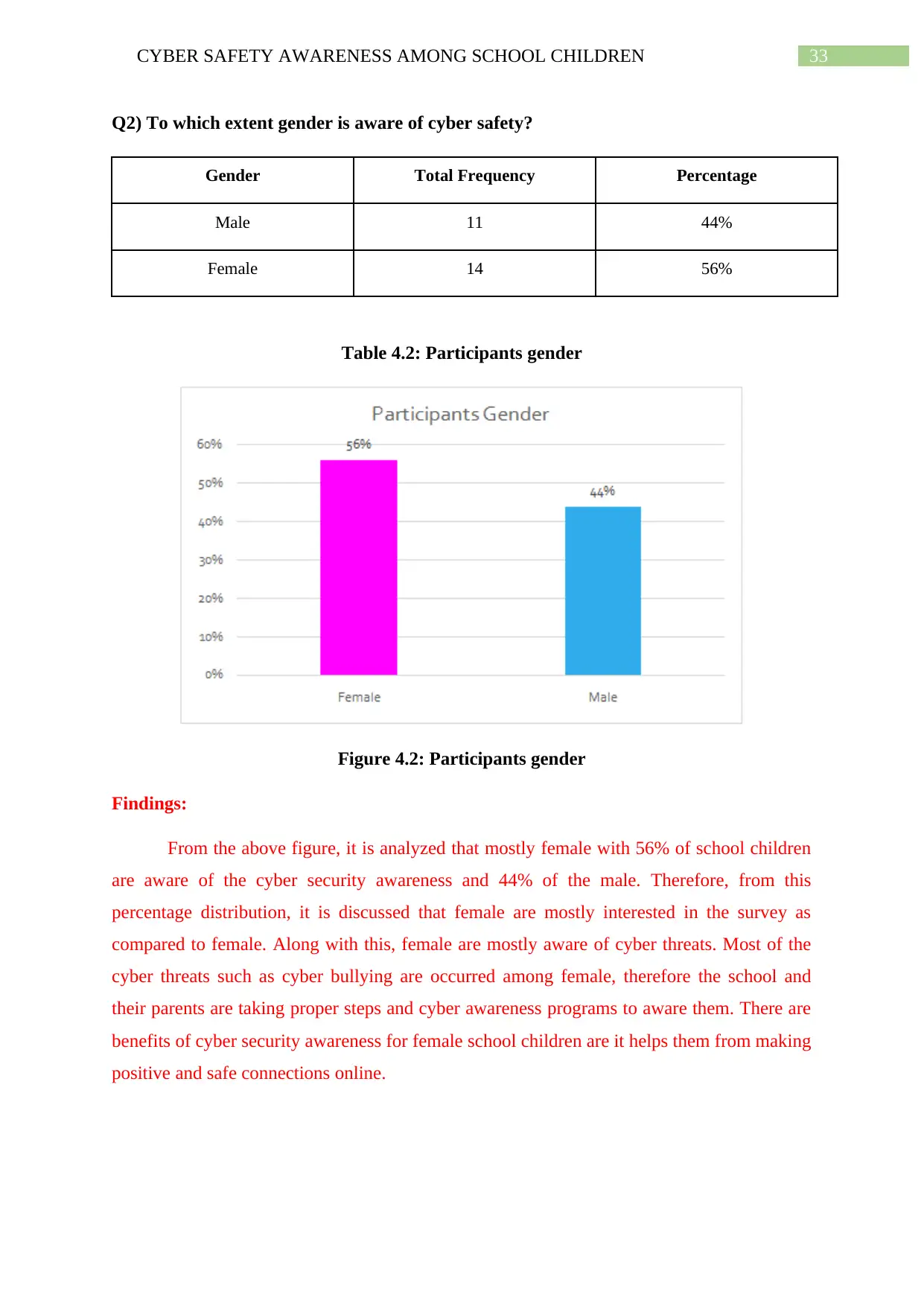
33CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Q2) To which extent gender is aware of cyber safety?
Gender Total Frequency Percentage
Male 11 44%
Female 14 56%
Table 4.2: Participants gender
Figure 4.2: Participants gender
Findings:
From the above figure, it is analyzed that mostly female with 56% of school children
are aware of the cyber security awareness and 44% of the male. Therefore, from this
percentage distribution, it is discussed that female are mostly interested in the survey as
compared to female. Along with this, female are mostly aware of cyber threats. Most of the
cyber threats such as cyber bullying are occurred among female, therefore the school and
their parents are taking proper steps and cyber awareness programs to aware them. There are
benefits of cyber security awareness for female school children are it helps them from making
positive and safe connections online.
Q2) To which extent gender is aware of cyber safety?
Gender Total Frequency Percentage
Male 11 44%
Female 14 56%
Table 4.2: Participants gender
Figure 4.2: Participants gender
Findings:
From the above figure, it is analyzed that mostly female with 56% of school children
are aware of the cyber security awareness and 44% of the male. Therefore, from this
percentage distribution, it is discussed that female are mostly interested in the survey as
compared to female. Along with this, female are mostly aware of cyber threats. Most of the
cyber threats such as cyber bullying are occurred among female, therefore the school and
their parents are taking proper steps and cyber awareness programs to aware them. There are
benefits of cyber security awareness for female school children are it helps them from making
positive and safe connections online.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
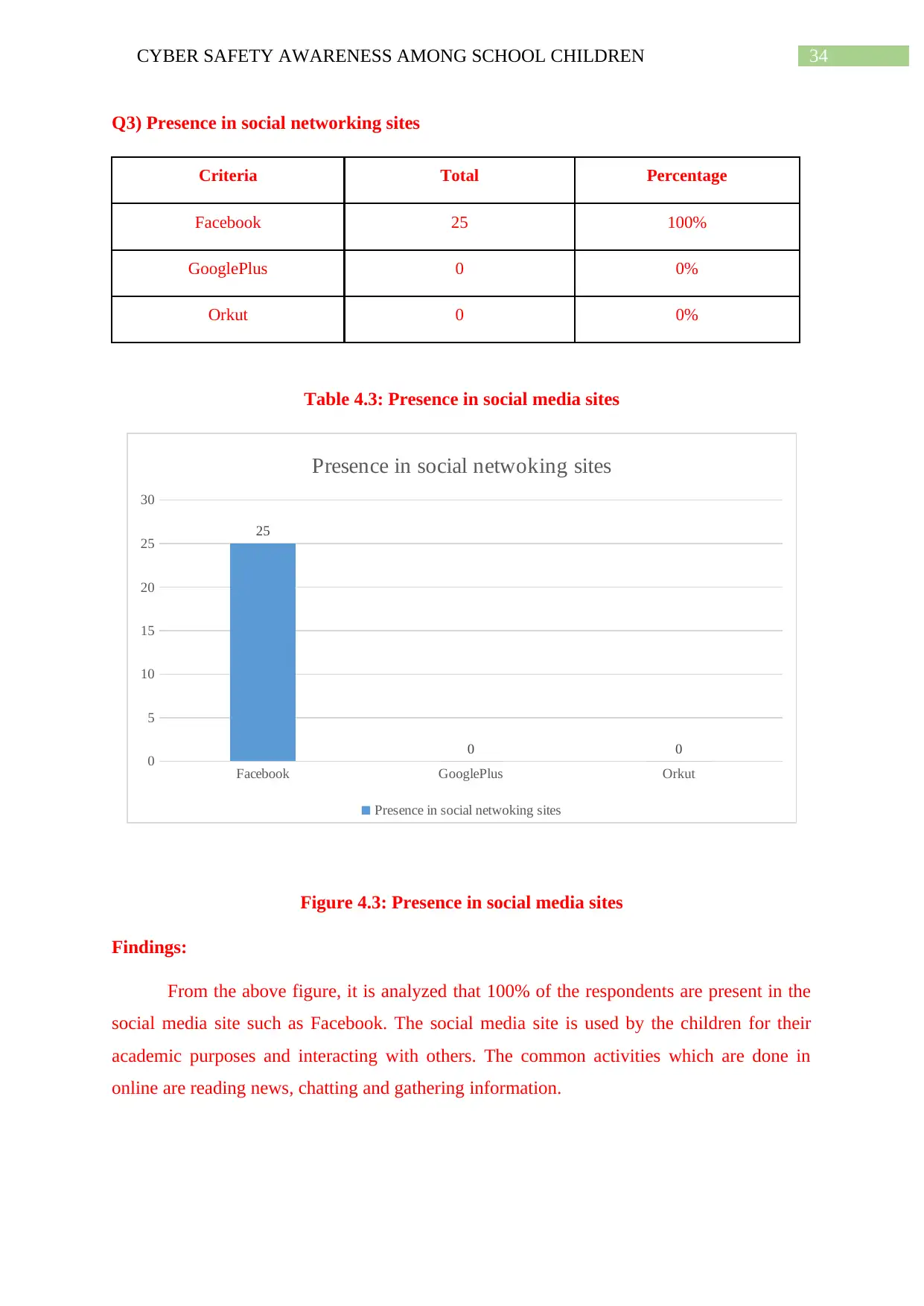
34CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Q3) Presence in social networking sites
Criteria Total Percentage
Facebook 25 100%
GooglePlus 0 0%
Orkut 0 0%
Table 4.3: Presence in social media sites
Facebook GooglePlus Orkut
0
5
10
15
20
25
30
25
0 0
Presence in social netwoking sites
Presence in social netwoking sites
Figure 4.3: Presence in social media sites
Findings:
From the above figure, it is analyzed that 100% of the respondents are present in the
social media site such as Facebook. The social media site is used by the children for their
academic purposes and interacting with others. The common activities which are done in
online are reading news, chatting and gathering information.
Q3) Presence in social networking sites
Criteria Total Percentage
Facebook 25 100%
GooglePlus 0 0%
Orkut 0 0%
Table 4.3: Presence in social media sites
Facebook GooglePlus Orkut
0
5
10
15
20
25
30
25
0 0
Presence in social netwoking sites
Presence in social netwoking sites
Figure 4.3: Presence in social media sites
Findings:
From the above figure, it is analyzed that 100% of the respondents are present in the
social media site such as Facebook. The social media site is used by the children for their
academic purposes and interacting with others. The common activities which are done in
online are reading news, chatting and gathering information.
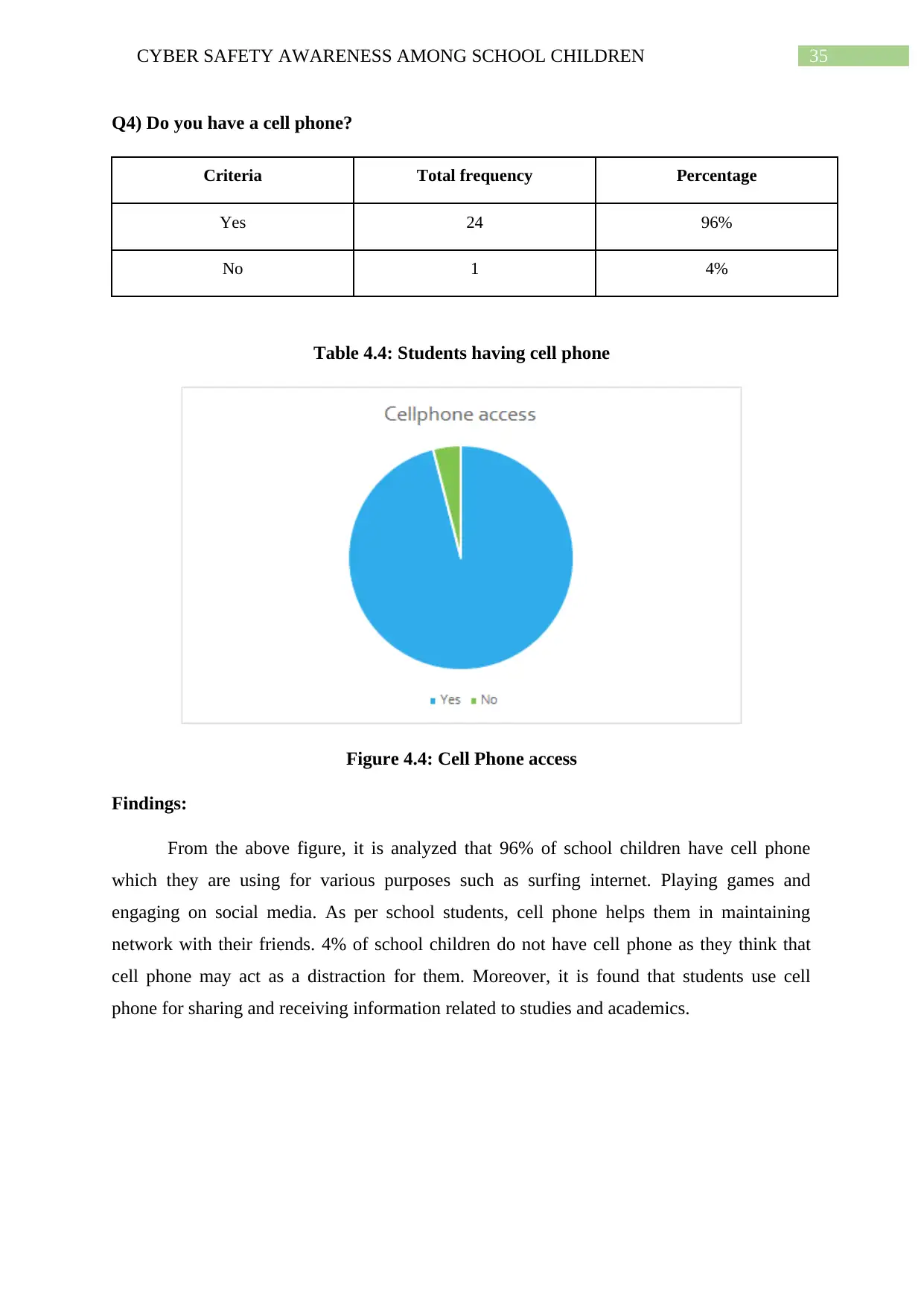
35CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Q4) Do you have a cell phone?
Criteria Total frequency Percentage
Yes 24 96%
No 1 4%
Table 4.4: Students having cell phone
Figure 4.4: Cell Phone access
Findings:
From the above figure, it is analyzed that 96% of school children have cell phone
which they are using for various purposes such as surfing internet. Playing games and
engaging on social media. As per school students, cell phone helps them in maintaining
network with their friends. 4% of school children do not have cell phone as they think that
cell phone may act as a distraction for them. Moreover, it is found that students use cell
phone for sharing and receiving information related to studies and academics.
Q4) Do you have a cell phone?
Criteria Total frequency Percentage
Yes 24 96%
No 1 4%
Table 4.4: Students having cell phone
Figure 4.4: Cell Phone access
Findings:
From the above figure, it is analyzed that 96% of school children have cell phone
which they are using for various purposes such as surfing internet. Playing games and
engaging on social media. As per school students, cell phone helps them in maintaining
network with their friends. 4% of school children do not have cell phone as they think that
cell phone may act as a distraction for them. Moreover, it is found that students use cell
phone for sharing and receiving information related to studies and academics.
36CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Q5) What is the purpose of using a cell phone?
Criteria Yes No Unsure Total frequency Percentage
Send and make
calls
20 4 0 24 80%
Sending and
receiving SMS
19 5 0 24 76%
Playing games 16 7 1 24 64%
Accessing the
internet
23 1 0 24 92%
Social network
engaging
22 1 1 24 88%
Surfing the
internet
21 1 2 24 84%
using facebook
or MXit
7 15 1 24 28%
Visiting chat
rooms
8 13 2 23 32%
Taking
pictures
23 1 0 24 92%
Other Purposes 13 6 5 24 52%
Table 4.5: Purpose of using cell phone
Q5) What is the purpose of using a cell phone?
Criteria Yes No Unsure Total frequency Percentage
Send and make
calls
20 4 0 24 80%
Sending and
receiving SMS
19 5 0 24 76%
Playing games 16 7 1 24 64%
Accessing the
internet
23 1 0 24 92%
Social network
engaging
22 1 1 24 88%
Surfing the
internet
21 1 2 24 84%
using facebook
or MXit
7 15 1 24 28%
Visiting chat
rooms
8 13 2 23 32%
Taking
pictures
23 1 0 24 92%
Other Purposes 13 6 5 24 52%
Table 4.5: Purpose of using cell phone
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
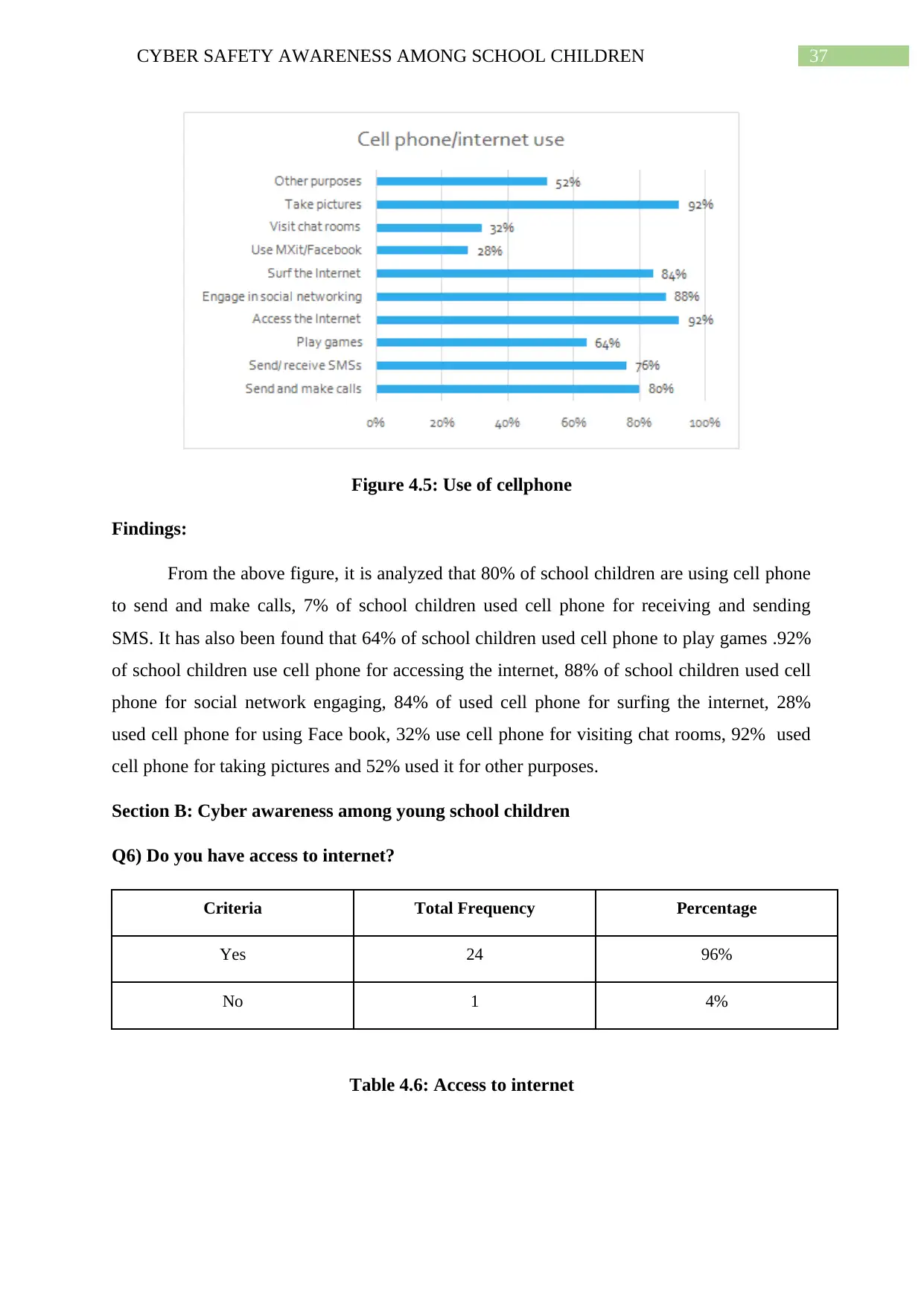
37CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Figure 4.5: Use of cellphone
Findings:
From the above figure, it is analyzed that 80% of school children are using cell phone
to send and make calls, 7% of school children used cell phone for receiving and sending
SMS. It has also been found that 64% of school children used cell phone to play games .92%
of school children use cell phone for accessing the internet, 88% of school children used cell
phone for social network engaging, 84% of used cell phone for surfing the internet, 28%
used cell phone for using Face book, 32% use cell phone for visiting chat rooms, 92% used
cell phone for taking pictures and 52% used it for other purposes.
Section B: Cyber awareness among young school children
Q6) Do you have access to internet?
Criteria Total Frequency Percentage
Yes 24 96%
No 1 4%
Table 4.6: Access to internet
Figure 4.5: Use of cellphone
Findings:
From the above figure, it is analyzed that 80% of school children are using cell phone
to send and make calls, 7% of school children used cell phone for receiving and sending
SMS. It has also been found that 64% of school children used cell phone to play games .92%
of school children use cell phone for accessing the internet, 88% of school children used cell
phone for social network engaging, 84% of used cell phone for surfing the internet, 28%
used cell phone for using Face book, 32% use cell phone for visiting chat rooms, 92% used
cell phone for taking pictures and 52% used it for other purposes.
Section B: Cyber awareness among young school children
Q6) Do you have access to internet?
Criteria Total Frequency Percentage
Yes 24 96%
No 1 4%
Table 4.6: Access to internet
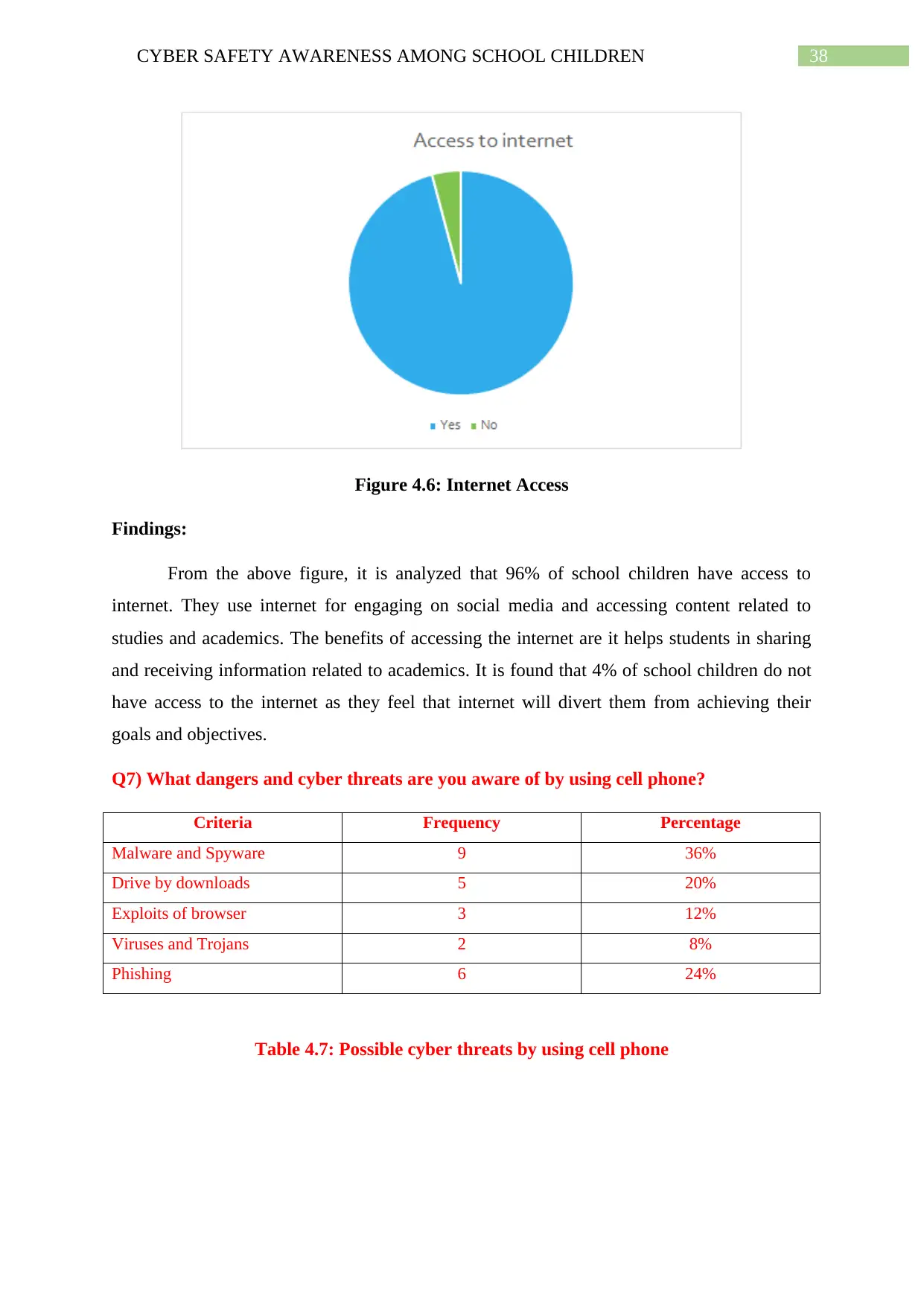
38CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Figure 4.6: Internet Access
Findings:
From the above figure, it is analyzed that 96% of school children have access to
internet. They use internet for engaging on social media and accessing content related to
studies and academics. The benefits of accessing the internet are it helps students in sharing
and receiving information related to academics. It is found that 4% of school children do not
have access to the internet as they feel that internet will divert them from achieving their
goals and objectives.
Q7) What dangers and cyber threats are you aware of by using cell phone?
Criteria Frequency Percentage
Malware and Spyware 9 36%
Drive by downloads 5 20%
Exploits of browser 3 12%
Viruses and Trojans 2 8%
Phishing 6 24%
Table 4.7: Possible cyber threats by using cell phone
Figure 4.6: Internet Access
Findings:
From the above figure, it is analyzed that 96% of school children have access to
internet. They use internet for engaging on social media and accessing content related to
studies and academics. The benefits of accessing the internet are it helps students in sharing
and receiving information related to academics. It is found that 4% of school children do not
have access to the internet as they feel that internet will divert them from achieving their
goals and objectives.
Q7) What dangers and cyber threats are you aware of by using cell phone?
Criteria Frequency Percentage
Malware and Spyware 9 36%
Drive by downloads 5 20%
Exploits of browser 3 12%
Viruses and Trojans 2 8%
Phishing 6 24%
Table 4.7: Possible cyber threats by using cell phone
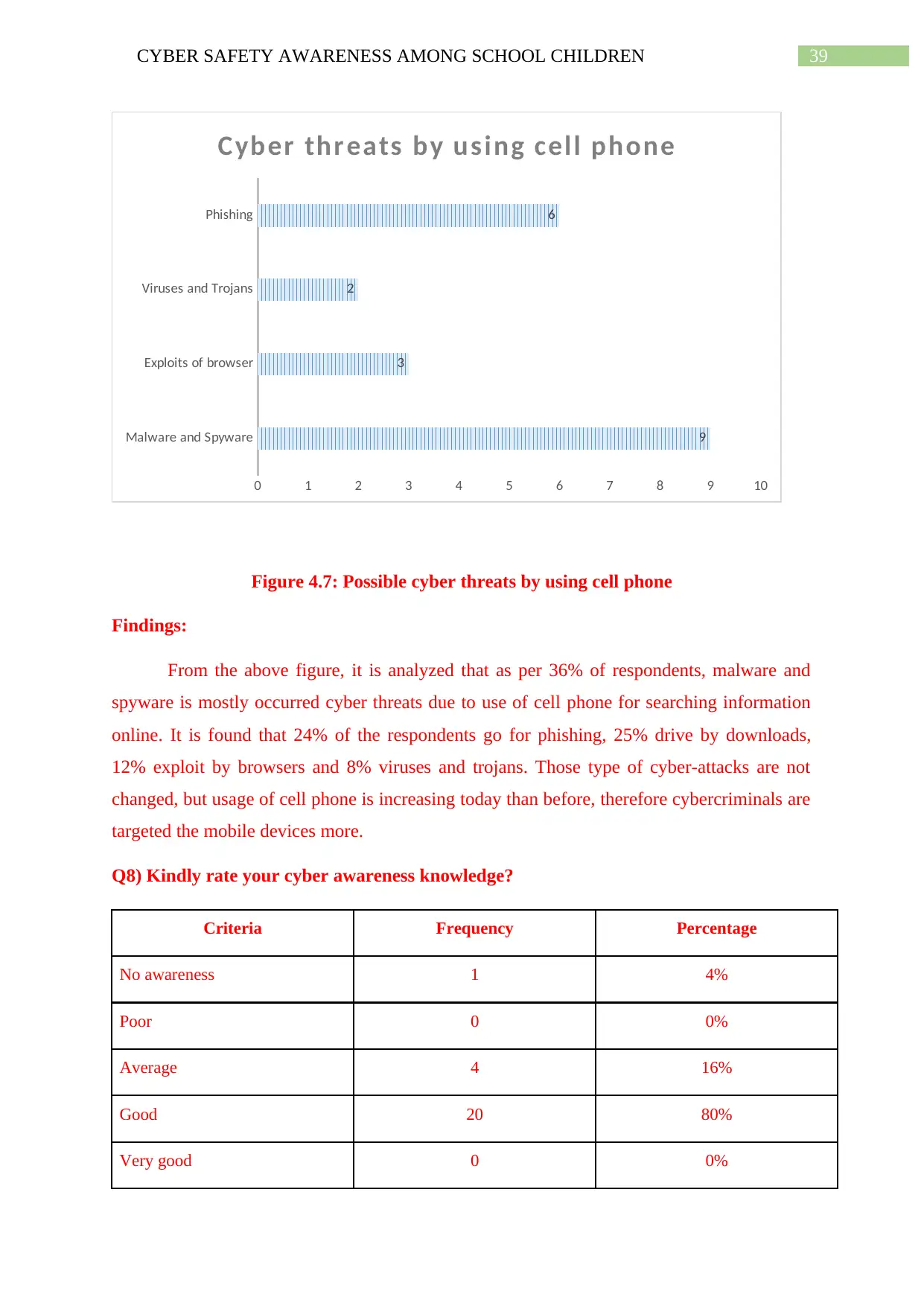
39CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Malware and Spyware
Exploits of browser
Viruses and Trojans
Phishing
0 1 2 3 4 5 6 7 8 9 10
9
3
2
6
Cyber threats by using cell phone
Figure 4.7: Possible cyber threats by using cell phone
Findings:
From the above figure, it is analyzed that as per 36% of respondents, malware and
spyware is mostly occurred cyber threats due to use of cell phone for searching information
online. It is found that 24% of the respondents go for phishing, 25% drive by downloads,
12% exploit by browsers and 8% viruses and trojans. Those type of cyber-attacks are not
changed, but usage of cell phone is increasing today than before, therefore cybercriminals are
targeted the mobile devices more.
Q8) Kindly rate your cyber awareness knowledge?
Criteria Frequency Percentage
No awareness 1 4%
Poor 0 0%
Average 4 16%
Good 20 80%
Very good 0 0%
Malware and Spyware
Exploits of browser
Viruses and Trojans
Phishing
0 1 2 3 4 5 6 7 8 9 10
9
3
2
6
Cyber threats by using cell phone
Figure 4.7: Possible cyber threats by using cell phone
Findings:
From the above figure, it is analyzed that as per 36% of respondents, malware and
spyware is mostly occurred cyber threats due to use of cell phone for searching information
online. It is found that 24% of the respondents go for phishing, 25% drive by downloads,
12% exploit by browsers and 8% viruses and trojans. Those type of cyber-attacks are not
changed, but usage of cell phone is increasing today than before, therefore cybercriminals are
targeted the mobile devices more.
Q8) Kindly rate your cyber awareness knowledge?
Criteria Frequency Percentage
No awareness 1 4%
Poor 0 0%
Average 4 16%
Good 20 80%
Very good 0 0%
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
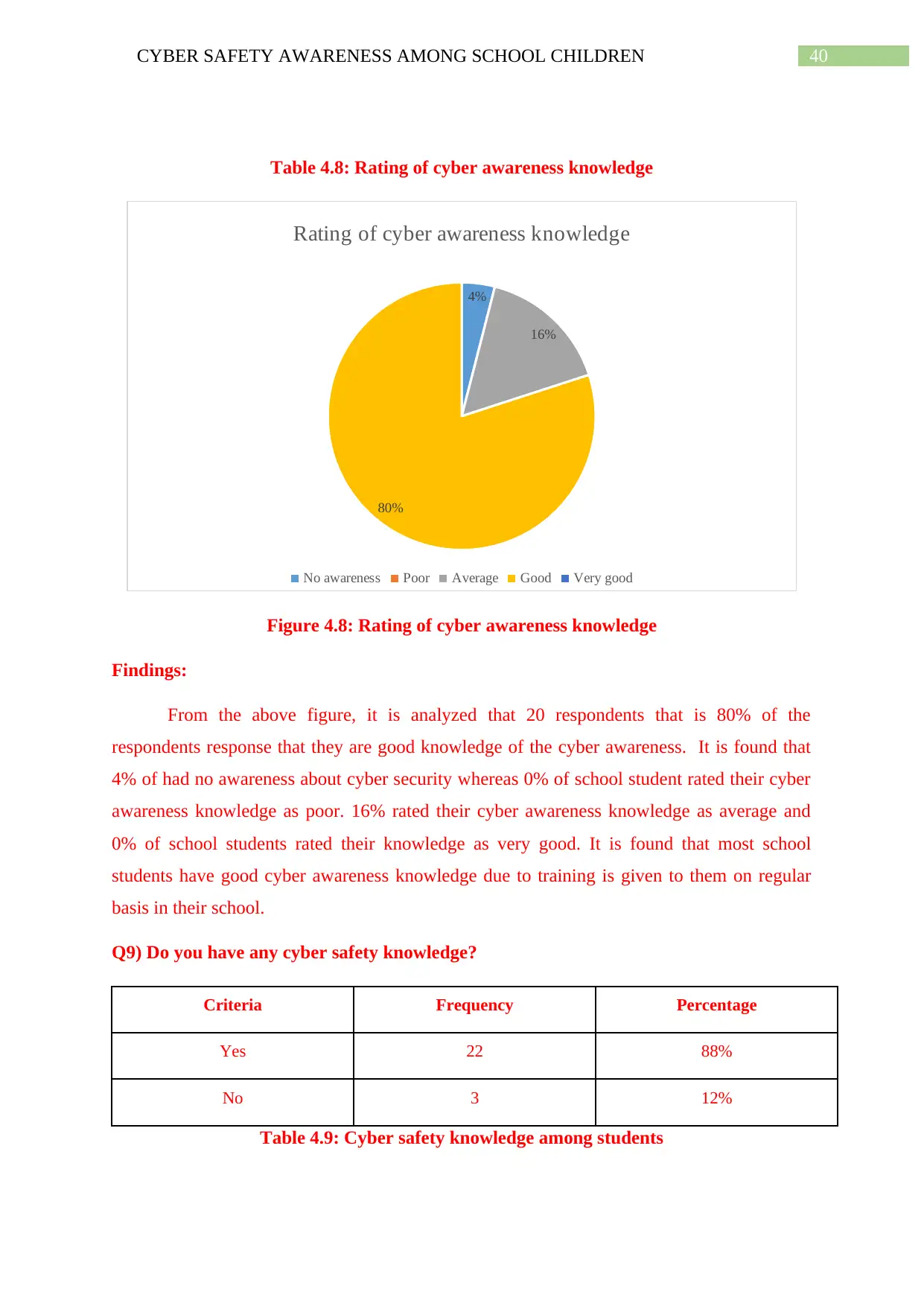
40CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Table 4.8: Rating of cyber awareness knowledge
4%
16%
80%
Rating of cyber awareness knowledge
No awareness Poor Average Good Very good
Figure 4.8: Rating of cyber awareness knowledge
Findings:
From the above figure, it is analyzed that 20 respondents that is 80% of the
respondents response that they are good knowledge of the cyber awareness. It is found that
4% of had no awareness about cyber security whereas 0% of school student rated their cyber
awareness knowledge as poor. 16% rated their cyber awareness knowledge as average and
0% of school students rated their knowledge as very good. It is found that most school
students have good cyber awareness knowledge due to training is given to them on regular
basis in their school.
Q9) Do you have any cyber safety knowledge?
Criteria Frequency Percentage
Yes 22 88%
No 3 12%
Table 4.9: Cyber safety knowledge among students
Table 4.8: Rating of cyber awareness knowledge
4%
16%
80%
Rating of cyber awareness knowledge
No awareness Poor Average Good Very good
Figure 4.8: Rating of cyber awareness knowledge
Findings:
From the above figure, it is analyzed that 20 respondents that is 80% of the
respondents response that they are good knowledge of the cyber awareness. It is found that
4% of had no awareness about cyber security whereas 0% of school student rated their cyber
awareness knowledge as poor. 16% rated their cyber awareness knowledge as average and
0% of school students rated their knowledge as very good. It is found that most school
students have good cyber awareness knowledge due to training is given to them on regular
basis in their school.
Q9) Do you have any cyber safety knowledge?
Criteria Frequency Percentage
Yes 22 88%
No 3 12%
Table 4.9: Cyber safety knowledge among students
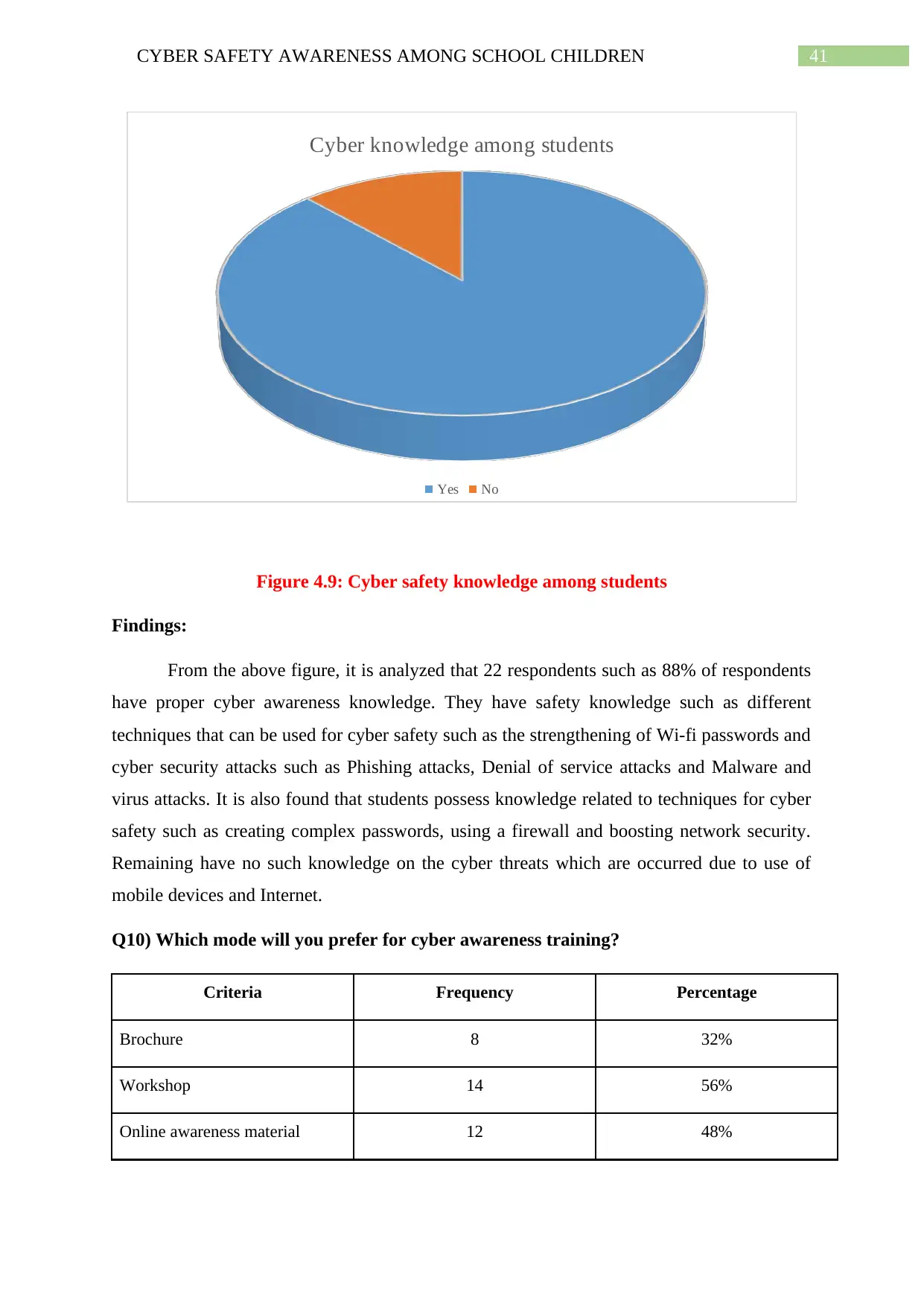
41CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Cyber knowledge among students
Yes No
Figure 4.9: Cyber safety knowledge among students
Findings:
From the above figure, it is analyzed that 22 respondents such as 88% of respondents
have proper cyber awareness knowledge. They have safety knowledge such as different
techniques that can be used for cyber safety such as the strengthening of Wi-fi passwords and
cyber security attacks such as Phishing attacks, Denial of service attacks and Malware and
virus attacks. It is also found that students possess knowledge related to techniques for cyber
safety such as creating complex passwords, using a firewall and boosting network security.
Remaining have no such knowledge on the cyber threats which are occurred due to use of
mobile devices and Internet.
Q10) Which mode will you prefer for cyber awareness training?
Criteria Frequency Percentage
Brochure 8 32%
Workshop 14 56%
Online awareness material 12 48%
Cyber knowledge among students
Yes No
Figure 4.9: Cyber safety knowledge among students
Findings:
From the above figure, it is analyzed that 22 respondents such as 88% of respondents
have proper cyber awareness knowledge. They have safety knowledge such as different
techniques that can be used for cyber safety such as the strengthening of Wi-fi passwords and
cyber security attacks such as Phishing attacks, Denial of service attacks and Malware and
virus attacks. It is also found that students possess knowledge related to techniques for cyber
safety such as creating complex passwords, using a firewall and boosting network security.
Remaining have no such knowledge on the cyber threats which are occurred due to use of
mobile devices and Internet.
Q10) Which mode will you prefer for cyber awareness training?
Criteria Frequency Percentage
Brochure 8 32%
Workshop 14 56%
Online awareness material 12 48%
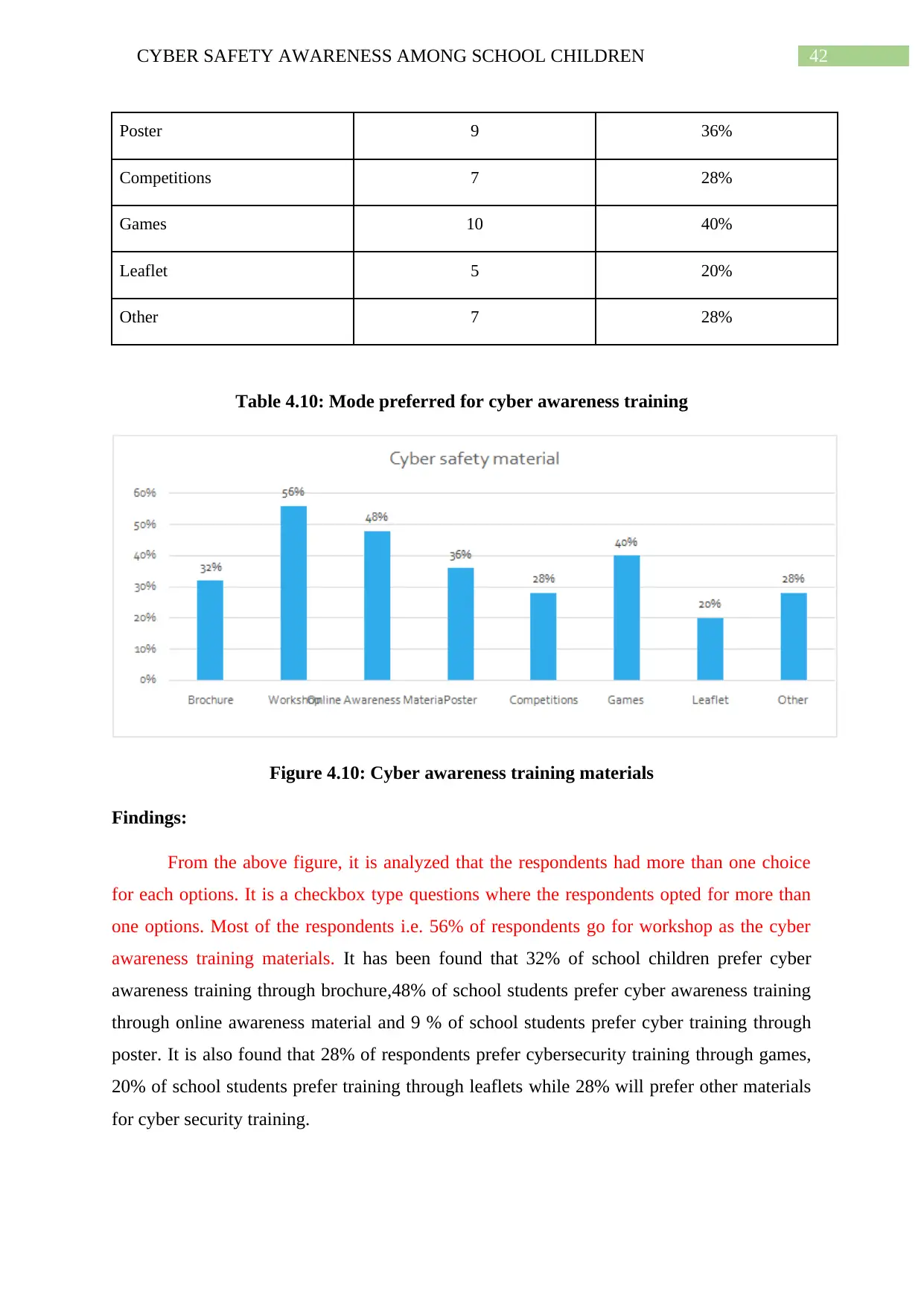
42CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Poster 9 36%
Competitions 7 28%
Games 10 40%
Leaflet 5 20%
Other 7 28%
Table 4.10: Mode preferred for cyber awareness training
Figure 4.10: Cyber awareness training materials
Findings:
From the above figure, it is analyzed that the respondents had more than one choice
for each options. It is a checkbox type questions where the respondents opted for more than
one options. Most of the respondents i.e. 56% of respondents go for workshop as the cyber
awareness training materials. It has been found that 32% of school children prefer cyber
awareness training through brochure,48% of school students prefer cyber awareness training
through online awareness material and 9 % of school students prefer cyber training through
poster. It is also found that 28% of respondents prefer cybersecurity training through games,
20% of school students prefer training through leaflets while 28% will prefer other materials
for cyber security training.
Poster 9 36%
Competitions 7 28%
Games 10 40%
Leaflet 5 20%
Other 7 28%
Table 4.10: Mode preferred for cyber awareness training
Figure 4.10: Cyber awareness training materials
Findings:
From the above figure, it is analyzed that the respondents had more than one choice
for each options. It is a checkbox type questions where the respondents opted for more than
one options. Most of the respondents i.e. 56% of respondents go for workshop as the cyber
awareness training materials. It has been found that 32% of school children prefer cyber
awareness training through brochure,48% of school students prefer cyber awareness training
through online awareness material and 9 % of school students prefer cyber training through
poster. It is also found that 28% of respondents prefer cybersecurity training through games,
20% of school students prefer training through leaflets while 28% will prefer other materials
for cyber security training.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
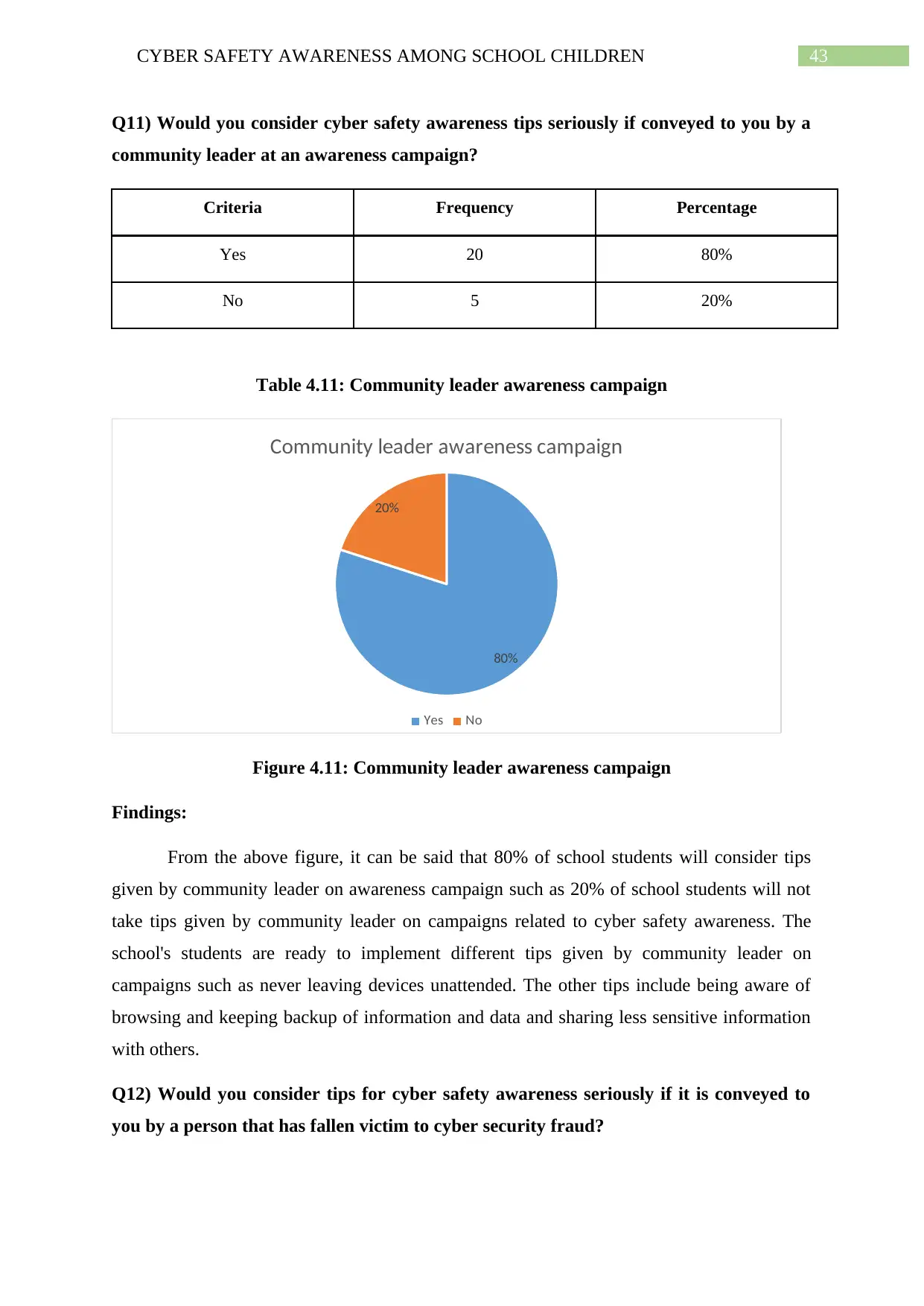
43CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Q11) Would you consider cyber safety awareness tips seriously if conveyed to you by a
community leader at an awareness campaign?
Criteria Frequency Percentage
Yes 20 80%
No 5 20%
Table 4.11: Community leader awareness campaign
80%
20%
Community leader awareness campaign
Yes No
Figure 4.11: Community leader awareness campaign
Findings:
From the above figure, it can be said that 80% of school students will consider tips
given by community leader on awareness campaign such as 20% of school students will not
take tips given by community leader on campaigns related to cyber safety awareness. The
school's students are ready to implement different tips given by community leader on
campaigns such as never leaving devices unattended. The other tips include being aware of
browsing and keeping backup of information and data and sharing less sensitive information
with others.
Q12) Would you consider tips for cyber safety awareness seriously if it is conveyed to
you by a person that has fallen victim to cyber security fraud?
Q11) Would you consider cyber safety awareness tips seriously if conveyed to you by a
community leader at an awareness campaign?
Criteria Frequency Percentage
Yes 20 80%
No 5 20%
Table 4.11: Community leader awareness campaign
80%
20%
Community leader awareness campaign
Yes No
Figure 4.11: Community leader awareness campaign
Findings:
From the above figure, it can be said that 80% of school students will consider tips
given by community leader on awareness campaign such as 20% of school students will not
take tips given by community leader on campaigns related to cyber safety awareness. The
school's students are ready to implement different tips given by community leader on
campaigns such as never leaving devices unattended. The other tips include being aware of
browsing and keeping backup of information and data and sharing less sensitive information
with others.
Q12) Would you consider tips for cyber safety awareness seriously if it is conveyed to
you by a person that has fallen victim to cyber security fraud?
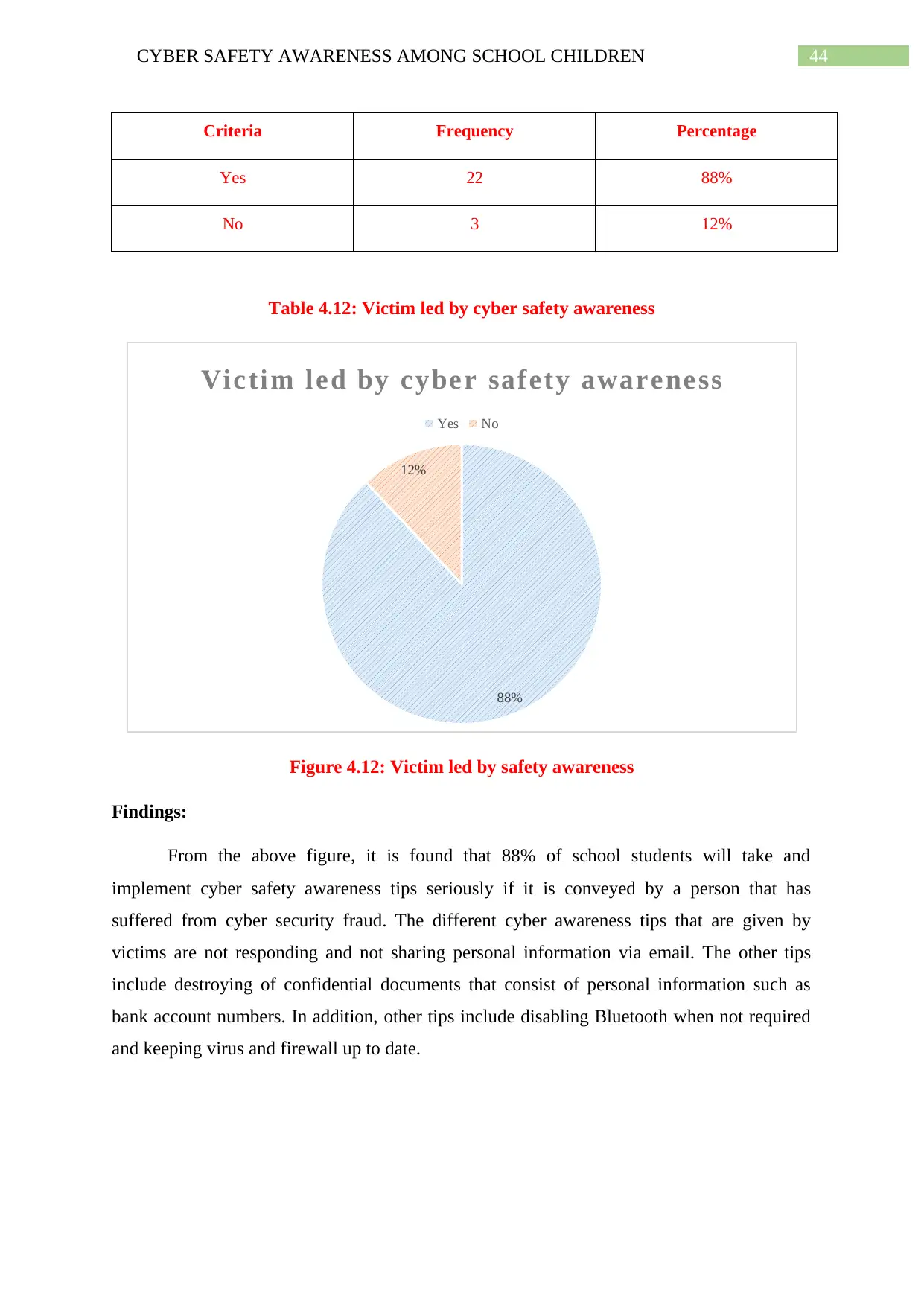
44CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Criteria Frequency Percentage
Yes 22 88%
No 3 12%
Table 4.12: Victim led by cyber safety awareness
88%
12%
Victim led by cyber safety awareness
Yes No
Figure 4.12: Victim led by safety awareness
Findings:
From the above figure, it is found that 88% of school students will take and
implement cyber safety awareness tips seriously if it is conveyed by a person that has
suffered from cyber security fraud. The different cyber awareness tips that are given by
victims are not responding and not sharing personal information via email. The other tips
include destroying of confidential documents that consist of personal information such as
bank account numbers. In addition, other tips include disabling Bluetooth when not required
and keeping virus and firewall up to date.
Criteria Frequency Percentage
Yes 22 88%
No 3 12%
Table 4.12: Victim led by cyber safety awareness
88%
12%
Victim led by cyber safety awareness
Yes No
Figure 4.12: Victim led by safety awareness
Findings:
From the above figure, it is found that 88% of school students will take and
implement cyber safety awareness tips seriously if it is conveyed by a person that has
suffered from cyber security fraud. The different cyber awareness tips that are given by
victims are not responding and not sharing personal information via email. The other tips
include destroying of confidential documents that consist of personal information such as
bank account numbers. In addition, other tips include disabling Bluetooth when not required
and keeping virus and firewall up to date.
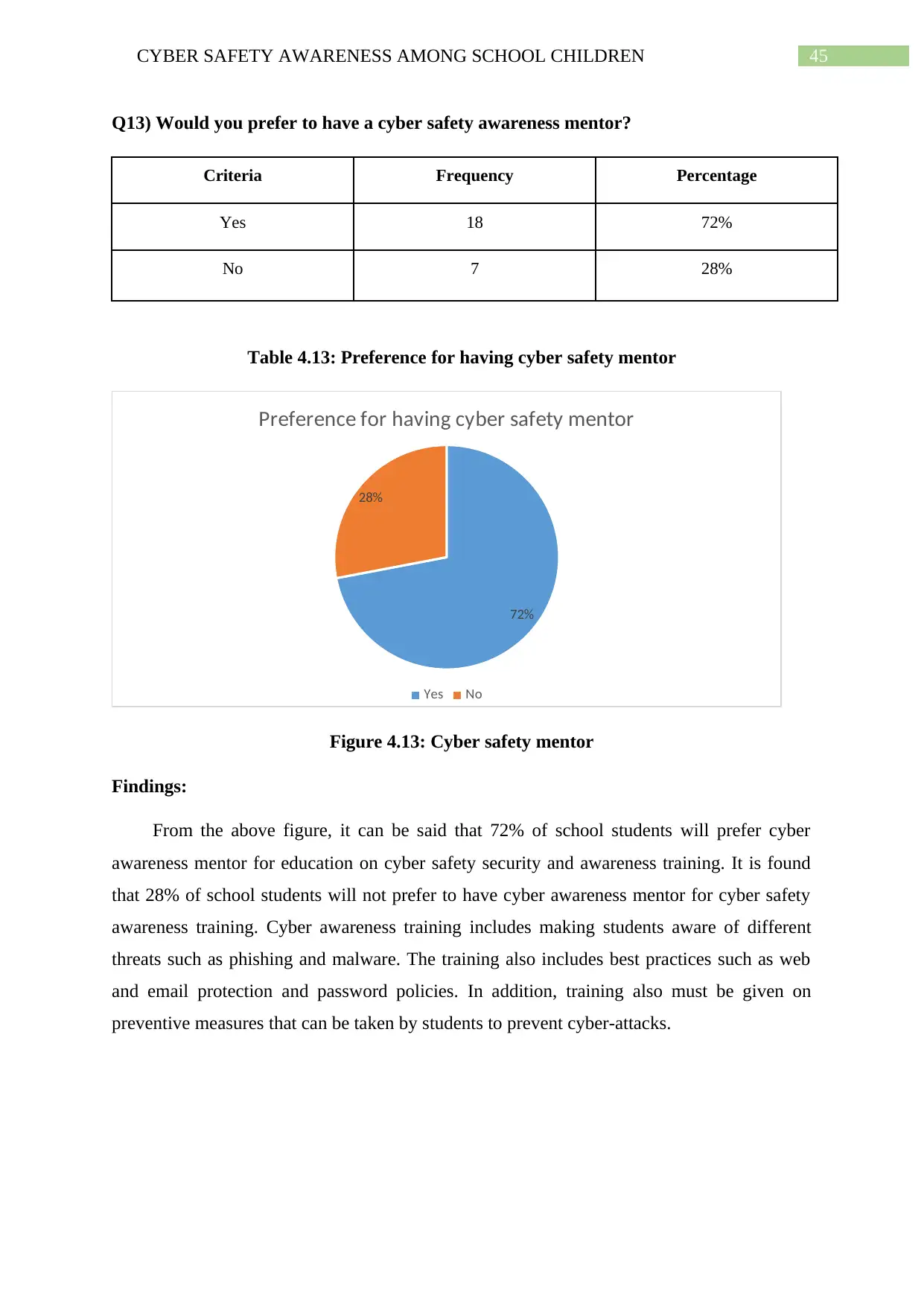
45CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Q13) Would you prefer to have a cyber safety awareness mentor?
Criteria Frequency Percentage
Yes 18 72%
No 7 28%
Table 4.13: Preference for having cyber safety mentor
72%
28%
Preference for having cyber safety mentor
Yes No
Figure 4.13: Cyber safety mentor
Findings:
From the above figure, it can be said that 72% of school students will prefer cyber
awareness mentor for education on cyber safety security and awareness training. It is found
that 28% of school students will not prefer to have cyber awareness mentor for cyber safety
awareness training. Cyber awareness training includes making students aware of different
threats such as phishing and malware. The training also includes best practices such as web
and email protection and password policies. In addition, training also must be given on
preventive measures that can be taken by students to prevent cyber-attacks.
Q13) Would you prefer to have a cyber safety awareness mentor?
Criteria Frequency Percentage
Yes 18 72%
No 7 28%
Table 4.13: Preference for having cyber safety mentor
72%
28%
Preference for having cyber safety mentor
Yes No
Figure 4.13: Cyber safety mentor
Findings:
From the above figure, it can be said that 72% of school students will prefer cyber
awareness mentor for education on cyber safety security and awareness training. It is found
that 28% of school students will not prefer to have cyber awareness mentor for cyber safety
awareness training. Cyber awareness training includes making students aware of different
threats such as phishing and malware. The training also includes best practices such as web
and email protection and password policies. In addition, training also must be given on
preventive measures that can be taken by students to prevent cyber-attacks.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
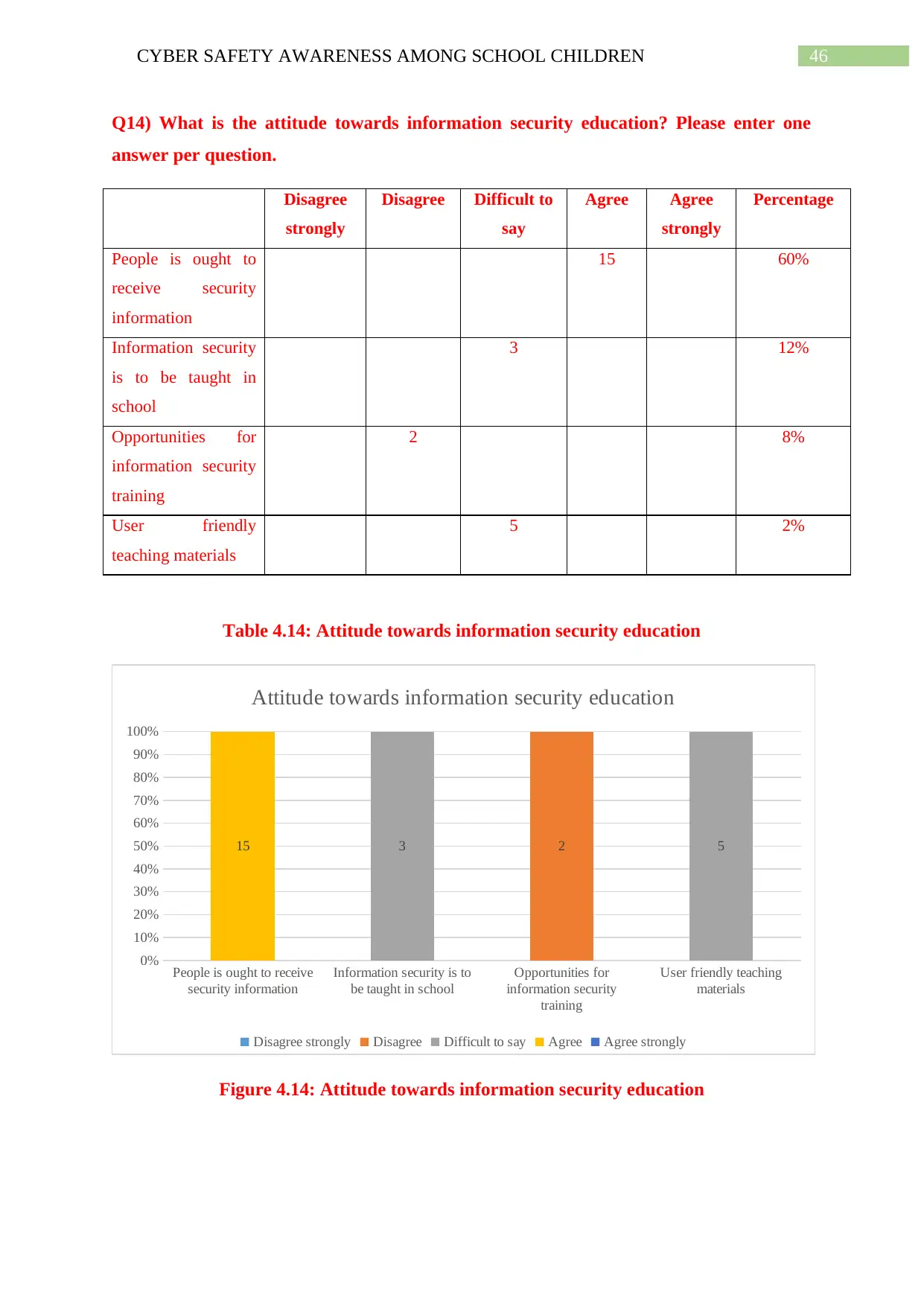
46CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Q14) What is the attitude towards information security education? Please enter one
answer per question.
Disagree
strongly
Disagree Difficult to
say
Agree Agree
strongly
Percentage
People is ought to
receive security
information
15 60%
Information security
is to be taught in
school
3 12%
Opportunities for
information security
training
2 8%
User friendly
teaching materials
5 2%
Table 4.14: Attitude towards information security education
People is ought to receive
security information
Information security is to
be taught in school
Opportunities for
information security
training
User friendly teaching
materials
0%
10%
20%
30%
40%
50%
60%
70%
80%
90%
100%
15 3 52
Attitude towards information security education
Disagree strongly Disagree Difficult to say Agree Agree strongly
Figure 4.14: Attitude towards information security education
Q14) What is the attitude towards information security education? Please enter one
answer per question.
Disagree
strongly
Disagree Difficult to
say
Agree Agree
strongly
Percentage
People is ought to
receive security
information
15 60%
Information security
is to be taught in
school
3 12%
Opportunities for
information security
training
2 8%
User friendly
teaching materials
5 2%
Table 4.14: Attitude towards information security education
People is ought to receive
security information
Information security is to
be taught in school
Opportunities for
information security
training
User friendly teaching
materials
0%
10%
20%
30%
40%
50%
60%
70%
80%
90%
100%
15 3 52
Attitude towards information security education
Disagree strongly Disagree Difficult to say Agree Agree strongly
Figure 4.14: Attitude towards information security education
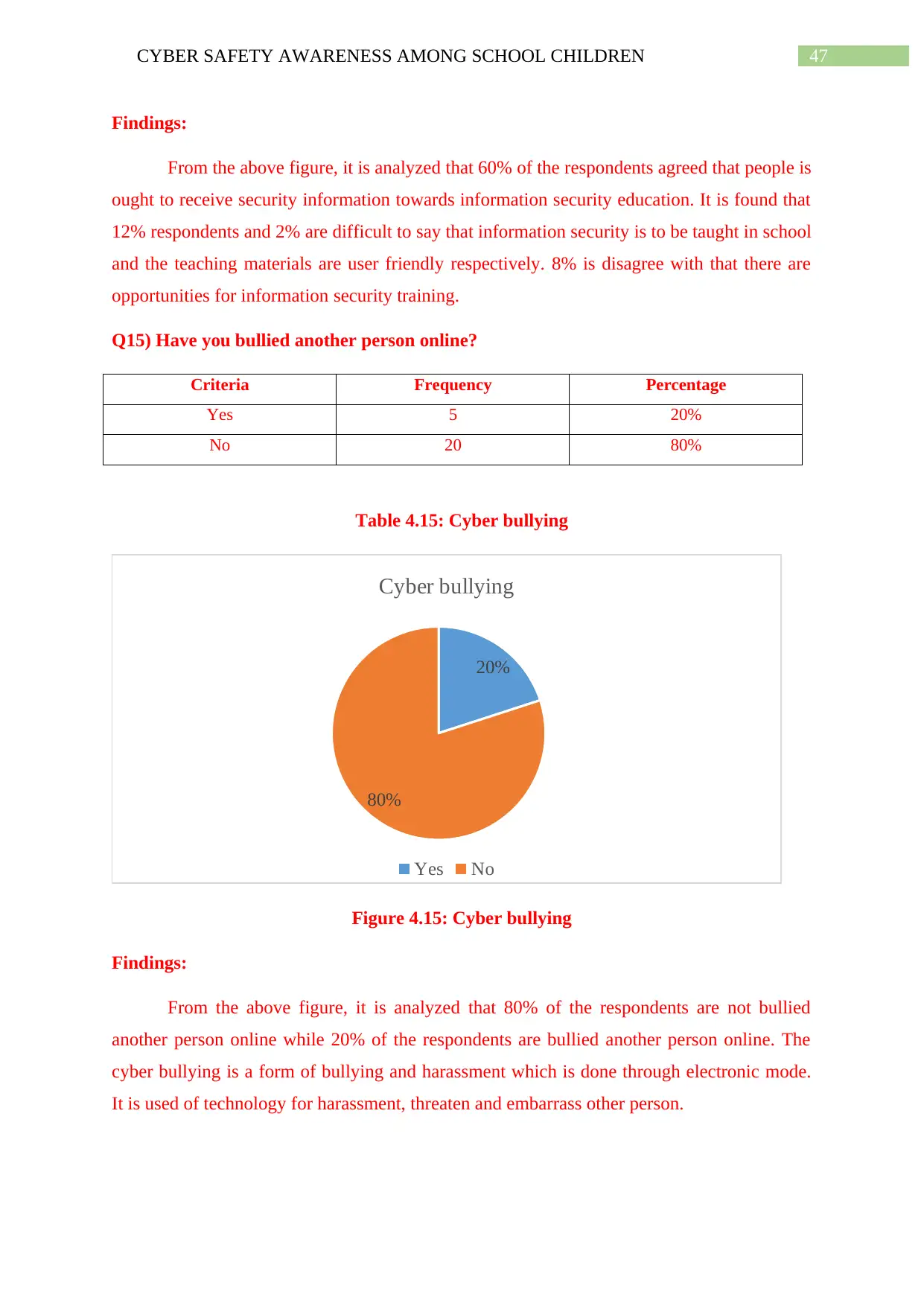
47CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Findings:
From the above figure, it is analyzed that 60% of the respondents agreed that people is
ought to receive security information towards information security education. It is found that
12% respondents and 2% are difficult to say that information security is to be taught in school
and the teaching materials are user friendly respectively. 8% is disagree with that there are
opportunities for information security training.
Q15) Have you bullied another person online?
Criteria Frequency Percentage
Yes 5 20%
No 20 80%
Table 4.15: Cyber bullying
20%
80%
Cyber bullying
Yes No
Figure 4.15: Cyber bullying
Findings:
From the above figure, it is analyzed that 80% of the respondents are not bullied
another person online while 20% of the respondents are bullied another person online. The
cyber bullying is a form of bullying and harassment which is done through electronic mode.
It is used of technology for harassment, threaten and embarrass other person.
Findings:
From the above figure, it is analyzed that 60% of the respondents agreed that people is
ought to receive security information towards information security education. It is found that
12% respondents and 2% are difficult to say that information security is to be taught in school
and the teaching materials are user friendly respectively. 8% is disagree with that there are
opportunities for information security training.
Q15) Have you bullied another person online?
Criteria Frequency Percentage
Yes 5 20%
No 20 80%
Table 4.15: Cyber bullying
20%
80%
Cyber bullying
Yes No
Figure 4.15: Cyber bullying
Findings:
From the above figure, it is analyzed that 80% of the respondents are not bullied
another person online while 20% of the respondents are bullied another person online. The
cyber bullying is a form of bullying and harassment which is done through electronic mode.
It is used of technology for harassment, threaten and embarrass other person.

48CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
4.2 Summary
It can be said from this chapter is that the age group ranging from 13-18 years possess
more knowledge about cyber awareness as compared to 3-12 years of old children. It can also
be said that male students have more knowledge about cyber safety awareness than females.
Moreover, it can be said that all students have completed grade 12 and majority of school
students have cell phone and use for its purposes such as for taking pictures, accessing and
surfing the internet and playing games.
In addition, this chapter explains the majority of students possess knowledge related
to cyber awareness. The different materials that are preferred by school students for cyber
security training are online websites and workshops. It can also be concluded that majority of
school students require mentor for ensuring that all cyber security awareness tips are
implemented by school students. It can also be said that majority of school students will
prefer education related to cyber safety awareness such as a preventive measures to be taken
to prevent cyber-attacks and the different techniques that can be used for maintaining cyber
safety. It can be said that school students are aware of cyber security awareness.. Moreover,
this chapter also explains that training required on cyber safety awareness such as techniques
required for cyber training and preventive measures taken by cyber security training in
requirement. It can also be said the different modes that have been preferred by school
students are a brochure, workshop, games and competition. In addition, it can also be said
that majority of school students need education and training on cyber security awareness and
benefits of such training are it protect from data being shared and privacy is maintained.
4.2 Summary
It can be said from this chapter is that the age group ranging from 13-18 years possess
more knowledge about cyber awareness as compared to 3-12 years of old children. It can also
be said that male students have more knowledge about cyber safety awareness than females.
Moreover, it can be said that all students have completed grade 12 and majority of school
students have cell phone and use for its purposes such as for taking pictures, accessing and
surfing the internet and playing games.
In addition, this chapter explains the majority of students possess knowledge related
to cyber awareness. The different materials that are preferred by school students for cyber
security training are online websites and workshops. It can also be concluded that majority of
school students require mentor for ensuring that all cyber security awareness tips are
implemented by school students. It can also be said that majority of school students will
prefer education related to cyber safety awareness such as a preventive measures to be taken
to prevent cyber-attacks and the different techniques that can be used for maintaining cyber
safety. It can be said that school students are aware of cyber security awareness.. Moreover,
this chapter also explains that training required on cyber safety awareness such as techniques
required for cyber training and preventive measures taken by cyber security training in
requirement. It can also be said the different modes that have been preferred by school
students are a brochure, workshop, games and competition. In addition, it can also be said
that majority of school students need education and training on cyber security awareness and
benefits of such training are it protect from data being shared and privacy is maintained.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

49CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Chapter 5: Conclusion and Recommendations
5.1 Conclusion
From the above study, it is concluded that cyber-attack is a burning problem among the
children of South Africa which can impact the personal safety of the children. Nowadays
children are highly attracted to smart phones, tablets and other electronic gadgets. They are
using social media websites like Facebook, twitter, and Instagram to fit in the changing
culture throughout the world. For this reason, they are often sharing their personal
information like address, age, and contact number to unknown persons. They are facing
different types of unwanted accidents by intruders or cyber hackers. Many of the children are
getting involved with illegal activities. In order to avoid this, parents must keep an eye on the
browsing history of their children. Along with it, parents need to protect devices with strong
passwords which children cannot break easily. School authority needs to conduct awareness
programs to enhance the knowledge o0f children about cyber security. Lastly, children must
share their problems with their parents while facing any cyber-related problem.
5.2 Linking Objectives with Findings
● To analyse the current cyber safety awareness situation for children at school
The first objective can be explained with the help of point 2.1 in the Literature review
and the survey questionnaire. It helps in understanding the current cyber safety awareness
situation for children at schools. The respondents are aware of different techniques that can
be used to prevent cyber-attacks such as creating complex passwords for Wi-Fi and not
sharing sensitive information on online websites and online portals. Hence, the objective is
met as it helps in understanding different situations related to cyber awareness.
● To identify different programs that could be used to educate cyber safety for
children at school and home
The next objective is explained with the help of point 2.5 in Literature review. It can
be stated as different programs that can be used to educate cyber safety for children at school.
The different programs that are being used to educate cyber safety are conducting educational
programs for children. Moreover, as per findings, the educational material the school children
prefer for the education of cyber safety awareness is 56% of students prefer workshop for
Chapter 5: Conclusion and Recommendations
5.1 Conclusion
From the above study, it is concluded that cyber-attack is a burning problem among the
children of South Africa which can impact the personal safety of the children. Nowadays
children are highly attracted to smart phones, tablets and other electronic gadgets. They are
using social media websites like Facebook, twitter, and Instagram to fit in the changing
culture throughout the world. For this reason, they are often sharing their personal
information like address, age, and contact number to unknown persons. They are facing
different types of unwanted accidents by intruders or cyber hackers. Many of the children are
getting involved with illegal activities. In order to avoid this, parents must keep an eye on the
browsing history of their children. Along with it, parents need to protect devices with strong
passwords which children cannot break easily. School authority needs to conduct awareness
programs to enhance the knowledge o0f children about cyber security. Lastly, children must
share their problems with their parents while facing any cyber-related problem.
5.2 Linking Objectives with Findings
● To analyse the current cyber safety awareness situation for children at school
The first objective can be explained with the help of point 2.1 in the Literature review
and the survey questionnaire. It helps in understanding the current cyber safety awareness
situation for children at schools. The respondents are aware of different techniques that can
be used to prevent cyber-attacks such as creating complex passwords for Wi-Fi and not
sharing sensitive information on online websites and online portals. Hence, the objective is
met as it helps in understanding different situations related to cyber awareness.
● To identify different programs that could be used to educate cyber safety for
children at school and home
The next objective is explained with the help of point 2.5 in Literature review. It can
be stated as different programs that can be used to educate cyber safety for children at school.
The different programs that are being used to educate cyber safety are conducting educational
programs for children. Moreover, as per findings, the educational material the school children
prefer for the education of cyber safety awareness is 56% of students prefer workshop for

50CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
education, whereas 48% prefer online awareness websites and 40% prefer games. Hence, the
objective is met by identifying different
● To recognize the methods used to create cyber safety awareness programs for young
children and parents
The third objective can be explained with the help of point 2.5.1.1 is understanding
probable methods for creating cyber safety awareness programs that can be improved by
using awareness materials at schools and home. The findings include 56% of students prefer
workshops, 32% of school students prefer brochure and 48% of students prefer online
awareness material. Moreover, the other findings include 36% of school students prefer
poster, 28% of school students prefer competitions, 40% of school students prefer games for
gaining knowledge related to cyber safety. In addition, 20% of school students prefer leaflets
and 28% of school students prefer other materials. Moreover, the probable methods that can
be used for creating security awareness such as 100% of students prefer mentor for creating
awareness among security among students. The other method that is used for creating cyber
security awareness among students is campaigns. Moreover, students prefer campaign leaders
for gaining knowledge related to cyber security awareness. Hence, the objective is met.
● To identify different challenges faced in creating cyber safety awareness among
young learners
The last objective can be explained with help of point 2. 3 and the survey
questionnaires. It explains recognizing the challenges in creating cyber safety awareness
among young learners. As per the findings, the biggest challenge being faced in creating
security awareness are potential threats and danger faced in using cell phones. The finding
includes 64% of school students face various challenges such as health risk like students are
prone to cancer and tumour, security risks such as sharing of personal and sensitive
information breaching of personal data and conduct and contact risks such as non-compliance
of procedures and policies. Moreover, the other challenges being faced by school students are
loss of studies and sharing of incorrect data and information. The cyber-attacks such as
malware attacks, virus attacks and phishing of information is also a major challenge faced by
school students in cyber security awareness. Hence, the objective is met.
education, whereas 48% prefer online awareness websites and 40% prefer games. Hence, the
objective is met by identifying different
● To recognize the methods used to create cyber safety awareness programs for young
children and parents
The third objective can be explained with the help of point 2.5.1.1 is understanding
probable methods for creating cyber safety awareness programs that can be improved by
using awareness materials at schools and home. The findings include 56% of students prefer
workshops, 32% of school students prefer brochure and 48% of students prefer online
awareness material. Moreover, the other findings include 36% of school students prefer
poster, 28% of school students prefer competitions, 40% of school students prefer games for
gaining knowledge related to cyber safety. In addition, 20% of school students prefer leaflets
and 28% of school students prefer other materials. Moreover, the probable methods that can
be used for creating security awareness such as 100% of students prefer mentor for creating
awareness among security among students. The other method that is used for creating cyber
security awareness among students is campaigns. Moreover, students prefer campaign leaders
for gaining knowledge related to cyber security awareness. Hence, the objective is met.
● To identify different challenges faced in creating cyber safety awareness among
young learners
The last objective can be explained with help of point 2. 3 and the survey
questionnaires. It explains recognizing the challenges in creating cyber safety awareness
among young learners. As per the findings, the biggest challenge being faced in creating
security awareness are potential threats and danger faced in using cell phones. The finding
includes 64% of school students face various challenges such as health risk like students are
prone to cancer and tumour, security risks such as sharing of personal and sensitive
information breaching of personal data and conduct and contact risks such as non-compliance
of procedures and policies. Moreover, the other challenges being faced by school students are
loss of studies and sharing of incorrect data and information. The cyber-attacks such as
malware attacks, virus attacks and phishing of information is also a major challenge faced by
school students in cyber security awareness. Hence, the objective is met.

51CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
The main objective of this research study is:To identify suitable approaches and
programs that could bring awareness among school children about cyber safety in order to
follow better practices related to internet, smart phones and other cyber technologies
Among all the cybersecurity programs, educational programs among young children
brings awareness among the school children about the cyber safety to follow better practices
related to internet, smart phones and cyber technologies. The young children is sharp with
technology as well as internet, therefore there are various cyber threats which are occurred.
As they are not mostly aware of cyber threats, therefore the school should implement of cyber
educational programs that should provide them education. The best way to fight with
cybercriminals is throughout education which can start at any age group. Educational
awareness is powerful as it can change social perceptions rather than to create panic among
young children to use of technology and internet. Cyber bullying is a spotlight into the
classroom, and the students should teach about psychological along with legal ramifications.
The students should be educated how they can use technology to get better lifestyle.
5.3 Recommendations
Innovative security ideas by parents: It is recommended that parents should keep an
eye upon the technological devices of their children. Parents need to lock their gadgets with
strong passwords made coming special characters, letters, and numbers. It would be difficult
for unlocking these strong passwords by children. In affiliation to it, a parent must use
alphanumeric passwords for protection tablets, laptops, and smart phones of their children.
Teaching children the ways to be cautious and respectful online: it is
recommended that parents should teach their children the right usage of using the internet and
social media as well. In addition to it, parents also keep track of browsing history of their
children in order to get notified about any intrusion.
Providing security guidance by teachers as well as schools: It needs to be
recommended that teachers and school authority must because it’s while giving their student
opportunity of internet browsing. School authority should conduct an awareness program
where several teachers can guide their student about tips of cyber security. In addition to it,
school authority may introduce the existing students who have faced cyber bullying before.
Their experiences can teach children about the massive impact of cyber insurance.
The main objective of this research study is:To identify suitable approaches and
programs that could bring awareness among school children about cyber safety in order to
follow better practices related to internet, smart phones and other cyber technologies
Among all the cybersecurity programs, educational programs among young children
brings awareness among the school children about the cyber safety to follow better practices
related to internet, smart phones and cyber technologies. The young children is sharp with
technology as well as internet, therefore there are various cyber threats which are occurred.
As they are not mostly aware of cyber threats, therefore the school should implement of cyber
educational programs that should provide them education. The best way to fight with
cybercriminals is throughout education which can start at any age group. Educational
awareness is powerful as it can change social perceptions rather than to create panic among
young children to use of technology and internet. Cyber bullying is a spotlight into the
classroom, and the students should teach about psychological along with legal ramifications.
The students should be educated how they can use technology to get better lifestyle.
5.3 Recommendations
Innovative security ideas by parents: It is recommended that parents should keep an
eye upon the technological devices of their children. Parents need to lock their gadgets with
strong passwords made coming special characters, letters, and numbers. It would be difficult
for unlocking these strong passwords by children. In affiliation to it, a parent must use
alphanumeric passwords for protection tablets, laptops, and smart phones of their children.
Teaching children the ways to be cautious and respectful online: it is
recommended that parents should teach their children the right usage of using the internet and
social media as well. In addition to it, parents also keep track of browsing history of their
children in order to get notified about any intrusion.
Providing security guidance by teachers as well as schools: It needs to be
recommended that teachers and school authority must because it’s while giving their student
opportunity of internet browsing. School authority should conduct an awareness program
where several teachers can guide their student about tips of cyber security. In addition to it,
school authority may introduce the existing students who have faced cyber bullying before.
Their experiences can teach children about the massive impact of cyber insurance.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

52CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Proper communication: parents, as well as teachers, must communicate with their
children about internet safety. They should act very friendly with their children in order to
know their browsing history. In addition to it, school teachers also need to communicate with
their student about internet security.
Enhancing awareness among children: it is to be recommended that, school
children also need to be cautious themselves in order to avoid any unwanted intruders
activity. They should be cautious while talking with an unknown person in social media.
They should not give their address or contact number to an unknown person. In addition to it,
children also should read internet awareness books before using any smart phones or tablets.
Sharing problems with parents: Children should share their problems with their
parents without any doubt. They should know that their parents can save them in case of any
security-related problems.
Taking advantages of parental controls: parents should take the advantages to
control privacy issues of children smart phones as well as tablets. In addition to it, parents
must install matured content filtering applications in their devices in order to protect their
children from seeing matured web contents.
Using Cyber security software: children and their parents should install cyber
security software’s to avoid any types of information hacking, they may use Avast antivirus,
Kaspersky software which has a strong firewall to oppose any type of cyber-attacks.
Installing updates timely: children of South Africa have to clean their machine
regularly to avoid any type of junk file. All the cache files should be removed at regular basis
which is the major cause of cyber-attack. In addition to it, all of the software applications
need to be upgraded timely which ensures a better-protected device.
Parental controls: parents should not use online shopping site in front of their
children. They should keep their smart phones far away from small children and to needs to
engage them with more paperwork activities.
5.4 Limitations of the research
While executing above investigation of research, researcher has empowered certain
amount of limitations. The researcher was dealing with several types of space as well as time
restraints. That research had obstructions about finance, that made whole execution little
Proper communication: parents, as well as teachers, must communicate with their
children about internet safety. They should act very friendly with their children in order to
know their browsing history. In addition to it, school teachers also need to communicate with
their student about internet security.
Enhancing awareness among children: it is to be recommended that, school
children also need to be cautious themselves in order to avoid any unwanted intruders
activity. They should be cautious while talking with an unknown person in social media.
They should not give their address or contact number to an unknown person. In addition to it,
children also should read internet awareness books before using any smart phones or tablets.
Sharing problems with parents: Children should share their problems with their
parents without any doubt. They should know that their parents can save them in case of any
security-related problems.
Taking advantages of parental controls: parents should take the advantages to
control privacy issues of children smart phones as well as tablets. In addition to it, parents
must install matured content filtering applications in their devices in order to protect their
children from seeing matured web contents.
Using Cyber security software: children and their parents should install cyber
security software’s to avoid any types of information hacking, they may use Avast antivirus,
Kaspersky software which has a strong firewall to oppose any type of cyber-attacks.
Installing updates timely: children of South Africa have to clean their machine
regularly to avoid any type of junk file. All the cache files should be removed at regular basis
which is the major cause of cyber-attack. In addition to it, all of the software applications
need to be upgraded timely which ensures a better-protected device.
Parental controls: parents should not use online shopping site in front of their
children. They should keep their smart phones far away from small children and to needs to
engage them with more paperwork activities.
5.4 Limitations of the research
While executing above investigation of research, researcher has empowered certain
amount of limitations. The researcher was dealing with several types of space as well as time
restraints. That research had obstructions about finance, that made whole execution little

53CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
difficult. Researcher has come to a research survey on 25 students about the cyber security. In
this survey, a researcher had faced several difficulties. Some of the students got nervous
while giving opinion about their experiences on cyber security. Due to small number of
sample size, it is difficult to test the identified research questions and validity and reliability
of collected data.
5.5 Future Scope of research
This research investigation might not produce a diversified and descriptive result due
to lack of money, time and other resources. There is also future scope to select a large
number of sample or population for the primary data collection method. The researcher
should also search for other cyber security programs in the classroom so that they can opt of
any of the programs so that the cyber threats are prevented in the classroom.
difficult. Researcher has come to a research survey on 25 students about the cyber security. In
this survey, a researcher had faced several difficulties. Some of the students got nervous
while giving opinion about their experiences on cyber security. Due to small number of
sample size, it is difficult to test the identified research questions and validity and reliability
of collected data.
5.5 Future Scope of research
This research investigation might not produce a diversified and descriptive result due
to lack of money, time and other resources. There is also future scope to select a large
number of sample or population for the primary data collection method. The researcher
should also search for other cyber security programs in the classroom so that they can opt of
any of the programs so that the cyber threats are prevented in the classroom.

54CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
References
Accaglobal.com (2018). Threats of Cyber Attacks. Available on: 10 November 2018.
Available from: https://www.accaglobal.com/hk/en/member/member/accounting-business/
2018/04/in-focus/cyber-attack.html
Acs.org.au (2016). Cybersecurity - Threats Challenges Opportunities. [online] Acs.org.au.
Available at:
https://www.acs.org.au/content/dam/acs/acs-publications/ACS_Cybersecurity_Guide.pdf
[Accessed 9 Jan. 2019].
Bada, M. and Sasse, A., (2014). Cyber security awareness campaigns: Why do they fail to
change behaviour?.
Bele, J.L., Dimc, M., Rozman, D. and Jemec, A.S., (2014). Raising Awareness of
Cybercrime--The Use of Education as a Means of Prevention and Protection. International
Association for Development of the Information Society.
Byron, T., (2008). Safer children in a digital world: The report of the Byron Review: Be safe,
be aware, have fun.
Chandarman, R. and Van Niekerk, B., (2018). Students’ cybersecurity awareness at a private
tertiary educational institution. The African Journal of Information and
Communication, (2018)(20), pp.133-155.
Creswell, J. (2009) ‘Research Design’, Journal of Chemical Information and Modeling,
53(9), pp. 1689–1699.
Farrukh, A., Sadwick, R. and Villasenor, J., (2014). Youth internet safety: Risks, responses,
and research recommendations. Center for Technology Innovation at Brookings. Retrieved
from http://www. brookings. edu/~/media/research/files/papers/(2014)/10/21-youth-
internetsafety-farrukh-sadwick-villasenor/youth-internet-safety_v07. pdf.
Fletcher, A.J., (2018). Applying critical realism in qualitative research: methodology meets
method. International Journal of Social Research Methodology, 20(2), pp.181-194.
Gámez-Guadix, M., Borrajo, E. and Almendros, C., (2016). Risky online behaviors among
adolescents: Longitudinal relations among problematic Internet use, cyberbullying
References
Accaglobal.com (2018). Threats of Cyber Attacks. Available on: 10 November 2018.
Available from: https://www.accaglobal.com/hk/en/member/member/accounting-business/
2018/04/in-focus/cyber-attack.html
Acs.org.au (2016). Cybersecurity - Threats Challenges Opportunities. [online] Acs.org.au.
Available at:
https://www.acs.org.au/content/dam/acs/acs-publications/ACS_Cybersecurity_Guide.pdf
[Accessed 9 Jan. 2019].
Bada, M. and Sasse, A., (2014). Cyber security awareness campaigns: Why do they fail to
change behaviour?.
Bele, J.L., Dimc, M., Rozman, D. and Jemec, A.S., (2014). Raising Awareness of
Cybercrime--The Use of Education as a Means of Prevention and Protection. International
Association for Development of the Information Society.
Byron, T., (2008). Safer children in a digital world: The report of the Byron Review: Be safe,
be aware, have fun.
Chandarman, R. and Van Niekerk, B., (2018). Students’ cybersecurity awareness at a private
tertiary educational institution. The African Journal of Information and
Communication, (2018)(20), pp.133-155.
Creswell, J. (2009) ‘Research Design’, Journal of Chemical Information and Modeling,
53(9), pp. 1689–1699.
Farrukh, A., Sadwick, R. and Villasenor, J., (2014). Youth internet safety: Risks, responses,
and research recommendations. Center for Technology Innovation at Brookings. Retrieved
from http://www. brookings. edu/~/media/research/files/papers/(2014)/10/21-youth-
internetsafety-farrukh-sadwick-villasenor/youth-internet-safety_v07. pdf.
Fletcher, A.J., (2018). Applying critical realism in qualitative research: methodology meets
method. International Journal of Social Research Methodology, 20(2), pp.181-194.
Gámez-Guadix, M., Borrajo, E. and Almendros, C., (2016). Risky online behaviors among
adolescents: Longitudinal relations among problematic Internet use, cyberbullying
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

55CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
perpetration, and meeting strangers online. Journal of Behavioral Addictions, 5(1), pp.100-
107.
Gcaza, N., von Solms, R., Grobler, M.M. and van Vuuren, J.J., (2018). A general
morphological analysis: delineating a cyber-security culture. Information & Computer
Security, 25(3), pp.259-278.
Goutam, R.K., (2015). Importance of Cyber Security. International Journal of Computer
Applications, 111(7).
Guest, G., Namey, E., Taylor, J., Eley, N. and McKenna, K., (2018). Comparing focus groups
and individual interviews: findings from a randomized study. International Journal of Social
Research Methodology, 20(6), pp.693-708.
Hänsch, N. and Benenson, Z., (2014), September. Specifying IT security awareness.
In Database and Expert Systems Applications (DEXA), (2014) 25th International Workshop
on(pp. 326-330). IEEE.
Hassan, N.R., Swartz, L., Kagee, A., De Wet, A., Lesch, A., Kafaar, Z. and Newman, P.A.,
(2018). “There is not a safe space where they can find themselves to be free”:(Un) safe
spaces and the promotion of queer visibilities among township males who have sex with
males (MSM) in Cape Town, South Africa. Health & place, 49, pp.93-100.
Huang, D.L., Rau, P.L.P. and Salvendy, G., (2010). Perception of information
security. Behaviour & Information Technology, 29(3), pp.221-232.
Hymel, S., McClure, R., Miller, M., Shumka, E. and Trach, J., (2015). Addressing school
bullying: Insights from theories of group processes. Journal of Applied Developmental
Psychology, 37, pp.16-24.
Khurana, A., Bleakley, A., Jordan, A.B. and Romer, D., (2015). The protective effects of
parental monitoring and internet restriction on adolescents’ risk of online harassment. Journal
of youth and Adolescence, 44(5), pp.1039-1047.
King, D.L., Delfabbro, P.H., Doh, Y.Y., Wu, A.M., Kuss, D.J., Pallesen, S., Mentzoni, R.,
Carragher, N. and Sakuma, H., (2018). Policy and prevention approaches for disordered and
hazardous gaming and Internet use: An international perspective. Prevention Science, 19(2),
pp.233-249.
perpetration, and meeting strangers online. Journal of Behavioral Addictions, 5(1), pp.100-
107.
Gcaza, N., von Solms, R., Grobler, M.M. and van Vuuren, J.J., (2018). A general
morphological analysis: delineating a cyber-security culture. Information & Computer
Security, 25(3), pp.259-278.
Goutam, R.K., (2015). Importance of Cyber Security. International Journal of Computer
Applications, 111(7).
Guest, G., Namey, E., Taylor, J., Eley, N. and McKenna, K., (2018). Comparing focus groups
and individual interviews: findings from a randomized study. International Journal of Social
Research Methodology, 20(6), pp.693-708.
Hänsch, N. and Benenson, Z., (2014), September. Specifying IT security awareness.
In Database and Expert Systems Applications (DEXA), (2014) 25th International Workshop
on(pp. 326-330). IEEE.
Hassan, N.R., Swartz, L., Kagee, A., De Wet, A., Lesch, A., Kafaar, Z. and Newman, P.A.,
(2018). “There is not a safe space where they can find themselves to be free”:(Un) safe
spaces and the promotion of queer visibilities among township males who have sex with
males (MSM) in Cape Town, South Africa. Health & place, 49, pp.93-100.
Huang, D.L., Rau, P.L.P. and Salvendy, G., (2010). Perception of information
security. Behaviour & Information Technology, 29(3), pp.221-232.
Hymel, S., McClure, R., Miller, M., Shumka, E. and Trach, J., (2015). Addressing school
bullying: Insights from theories of group processes. Journal of Applied Developmental
Psychology, 37, pp.16-24.
Khurana, A., Bleakley, A., Jordan, A.B. and Romer, D., (2015). The protective effects of
parental monitoring and internet restriction on adolescents’ risk of online harassment. Journal
of youth and Adolescence, 44(5), pp.1039-1047.
King, D.L., Delfabbro, P.H., Doh, Y.Y., Wu, A.M., Kuss, D.J., Pallesen, S., Mentzoni, R.,
Carragher, N. and Sakuma, H., (2018). Policy and prevention approaches for disordered and
hazardous gaming and Internet use: An international perspective. Prevention Science, 19(2),
pp.233-249.

56CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Kokkinos, C.M., Antoniadou, N., Asdre, A. and Voulgaridou, K., (2016). Parenting and
Internet behavior predictors of cyber-bullying and cyber-victimization among
preadolescents. Deviant Behavior, 37(4), pp.439-455.
Kortjan, N. and Von Solms, R., (2014). A conceptual framework for cyber-security
awareness and education in SA. South African Computer Journal, 52(1), pp.29-41.
Kritzinger, E., (2015), July. Enhancing cyber safety awareness among school children in
South Africa through gaming. In Science and Information Conference (SAI), (2015) (pp.
1243-1248). IEEE.
Kushzhanov, N.V. and Aliyev, U.Z., (2018). DIGITAL SPACE: CHANGES IN SOCIETY
AND SECURITY AWARENESS. BULLETIN OF THE NATIONAL ACADEMY OF
SCIENCES OF THE REPUBLIC OF KAZAKHSTAN, (1), pp.94-101.
Livingstone, S. and Haddon, L., (2011). Management report EU Kids Online II: enhancing
knowledge regarding European children’s use, risk and safety online.
Livingstone, S., Mascheroni, G. and Staksrud, E., (2018). European research on children’s
internet use: Assessing the past and anticipating the future. New Media & Society, 20(3),
pp.1103-1122.
Livingstone, S., Ólafsson, K., Helsper, E.J., Lupiáñez-Villanueva, F., Veltri, G.A. and
Folkvord, F., (2018). Maximizing opportunities and minimizing risks for children online: The
role of digital skills in emerging strategies of parental mediation. Journal of
Communication, 67(1), pp.82-105.
Maxwell, J.A., (2008). Designing a qualitative study. The SAGE handbook of applied social
research methods, 2, pp.214-253.
Mitchell, K.J., Wolak, J. and Finkelhor, D., (2007). Trends in youth reports of sexual
solicitations, harassment and unwanted exposure to pornography on the Internet. Journal of
adolescent health, 40(2), pp.116-126.
Naplavova, M., Ludik, T., Hruza, P. and Bozek, F., (2014). General Awareness of Teenagers
in Information Security. World Academy of Science, Engineering and Technology,
International Journal of Social, Behavioral, Educational, Economic, Business and Industrial
Engineering, 8(11), pp.3544-3547.
Kokkinos, C.M., Antoniadou, N., Asdre, A. and Voulgaridou, K., (2016). Parenting and
Internet behavior predictors of cyber-bullying and cyber-victimization among
preadolescents. Deviant Behavior, 37(4), pp.439-455.
Kortjan, N. and Von Solms, R., (2014). A conceptual framework for cyber-security
awareness and education in SA. South African Computer Journal, 52(1), pp.29-41.
Kritzinger, E., (2015), July. Enhancing cyber safety awareness among school children in
South Africa through gaming. In Science and Information Conference (SAI), (2015) (pp.
1243-1248). IEEE.
Kushzhanov, N.V. and Aliyev, U.Z., (2018). DIGITAL SPACE: CHANGES IN SOCIETY
AND SECURITY AWARENESS. BULLETIN OF THE NATIONAL ACADEMY OF
SCIENCES OF THE REPUBLIC OF KAZAKHSTAN, (1), pp.94-101.
Livingstone, S. and Haddon, L., (2011). Management report EU Kids Online II: enhancing
knowledge regarding European children’s use, risk and safety online.
Livingstone, S., Mascheroni, G. and Staksrud, E., (2018). European research on children’s
internet use: Assessing the past and anticipating the future. New Media & Society, 20(3),
pp.1103-1122.
Livingstone, S., Ólafsson, K., Helsper, E.J., Lupiáñez-Villanueva, F., Veltri, G.A. and
Folkvord, F., (2018). Maximizing opportunities and minimizing risks for children online: The
role of digital skills in emerging strategies of parental mediation. Journal of
Communication, 67(1), pp.82-105.
Maxwell, J.A., (2008). Designing a qualitative study. The SAGE handbook of applied social
research methods, 2, pp.214-253.
Mitchell, K.J., Wolak, J. and Finkelhor, D., (2007). Trends in youth reports of sexual
solicitations, harassment and unwanted exposure to pornography on the Internet. Journal of
adolescent health, 40(2), pp.116-126.
Naplavova, M., Ludik, T., Hruza, P. and Bozek, F., (2014). General Awareness of Teenagers
in Information Security. World Academy of Science, Engineering and Technology,
International Journal of Social, Behavioral, Educational, Economic, Business and Industrial
Engineering, 8(11), pp.3544-3547.

57CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Panhwar, A.H., Ansari, S. and Shah, A.A., (2018). Post-positivism: an effective paradigm for
social and educational research. International Research Journal of Arts & Humanities
(IRJAH), 45(45).
Sabella, R.A., Patchin, J.W. and Hinduja, S., (2013). Cyberbullying myths and
realities. Computers in Human behavior, 29(6), pp.2703-2711.
Sharples, M., Graber, R., Harrison, C. and Logan, K., (2009). E‐safety and Web 2.0 for
children aged 11–16. Journal of Computer Assisted Learning, 25(1), pp.70-84.
Slonje, R., Smith, P.K. and FriséN, A., (2013). The nature of cyberbullying, and strategies for
prevention. Computers in human behavior, 29(1), pp.26-32.
Stephanou, A., (2009). The impact of information security awareness training on information
security behaviour(Doctoral dissertation).
Symon, G., Cassell, C. and Johnson, P., (2018). Evaluative practices in qualitative
management research: A critical review. International Journal of Management
Reviews, 20(1), pp.134-154.
Tucker, K. and Director, C.C.O., (2015). Cybersecurity.
von Solms, S. and von Solms, R., (2014). Towards Cyber Safety Education in Primary
Schools in Africa. In HAISA (pp. 185-197).
Welch, C. and Piekkari, R., (2018). How should we (not) judge the ‘quality’of qualitative
research? A re-assessment of current evaluative criteria in International Business. Journal of
World Business, 52(5), pp.714-725.
Wishart, J., (2018). Ethical considerations in the incorporation of mobile and ubiquitous
technologies into teaching and learning in educational contexts. In Mobile and Ubiquitous
Learning(pp. 81-93). Springer, Singapore.
Wright, M.F., (2015). Cyber victimization and adjustment difficulties: The mediation of
Chinese and American adolescents’ digital technology usage. Cyberpsychology: Journal of
Psychosocial Research on Cyberspace, 9(1).
Panhwar, A.H., Ansari, S. and Shah, A.A., (2018). Post-positivism: an effective paradigm for
social and educational research. International Research Journal of Arts & Humanities
(IRJAH), 45(45).
Sabella, R.A., Patchin, J.W. and Hinduja, S., (2013). Cyberbullying myths and
realities. Computers in Human behavior, 29(6), pp.2703-2711.
Sharples, M., Graber, R., Harrison, C. and Logan, K., (2009). E‐safety and Web 2.0 for
children aged 11–16. Journal of Computer Assisted Learning, 25(1), pp.70-84.
Slonje, R., Smith, P.K. and FriséN, A., (2013). The nature of cyberbullying, and strategies for
prevention. Computers in human behavior, 29(1), pp.26-32.
Stephanou, A., (2009). The impact of information security awareness training on information
security behaviour(Doctoral dissertation).
Symon, G., Cassell, C. and Johnson, P., (2018). Evaluative practices in qualitative
management research: A critical review. International Journal of Management
Reviews, 20(1), pp.134-154.
Tucker, K. and Director, C.C.O., (2015). Cybersecurity.
von Solms, S. and von Solms, R., (2014). Towards Cyber Safety Education in Primary
Schools in Africa. In HAISA (pp. 185-197).
Welch, C. and Piekkari, R., (2018). How should we (not) judge the ‘quality’of qualitative
research? A re-assessment of current evaluative criteria in International Business. Journal of
World Business, 52(5), pp.714-725.
Wishart, J., (2018). Ethical considerations in the incorporation of mobile and ubiquitous
technologies into teaching and learning in educational contexts. In Mobile and Ubiquitous
Learning(pp. 81-93). Springer, Singapore.
Wright, M.F., (2015). Cyber victimization and adjustment difficulties: The mediation of
Chinese and American adolescents’ digital technology usage. Cyberpsychology: Journal of
Psychosocial Research on Cyberspace, 9(1).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

58CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Appendix 1: Survey questionnaires
Q1) What is your age?
Age group Total frequency Percentage
6-13 years
13-18 years
Q2) To which extent which gender is aware of cyber safety?
Gender Total Frequency Percentage
Male
Female
Q3) Presence in social networking sites
Criteria Total Percentage
Facebook
GooglePlus
Orkut
Q4) Do you have a cell phone?
Criteria Total frequency Percentage
Yes
No
Appendix 1: Survey questionnaires
Q1) What is your age?
Age group Total frequency Percentage
6-13 years
13-18 years
Q2) To which extent which gender is aware of cyber safety?
Gender Total Frequency Percentage
Male
Female
Q3) Presence in social networking sites
Criteria Total Percentage
GooglePlus
Orkut
Q4) Do you have a cell phone?
Criteria Total frequency Percentage
Yes
No
59CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Q5) What is the purpose of using a cell phone?
Criteria Yes No Unsure Total
frequency
Percentage
Send and make
calls
Sending and
receiving SMS
Playing games
Accessing the
internet
Social network
engaging
Surfing the
internet
using facebook
or MXit
Visiting chat
rooms
Taking
pictures
Other Purposes
Q6) Do you have access to internet?
Criteria Total Frequency Percentage
Yes
No
Q5) What is the purpose of using a cell phone?
Criteria Yes No Unsure Total
frequency
Percentage
Send and make
calls
Sending and
receiving SMS
Playing games
Accessing the
internet
Social network
engaging
Surfing the
internet
using facebook
or MXit
Visiting chat
rooms
Taking
pictures
Other Purposes
Q6) Do you have access to internet?
Criteria Total Frequency Percentage
Yes
No
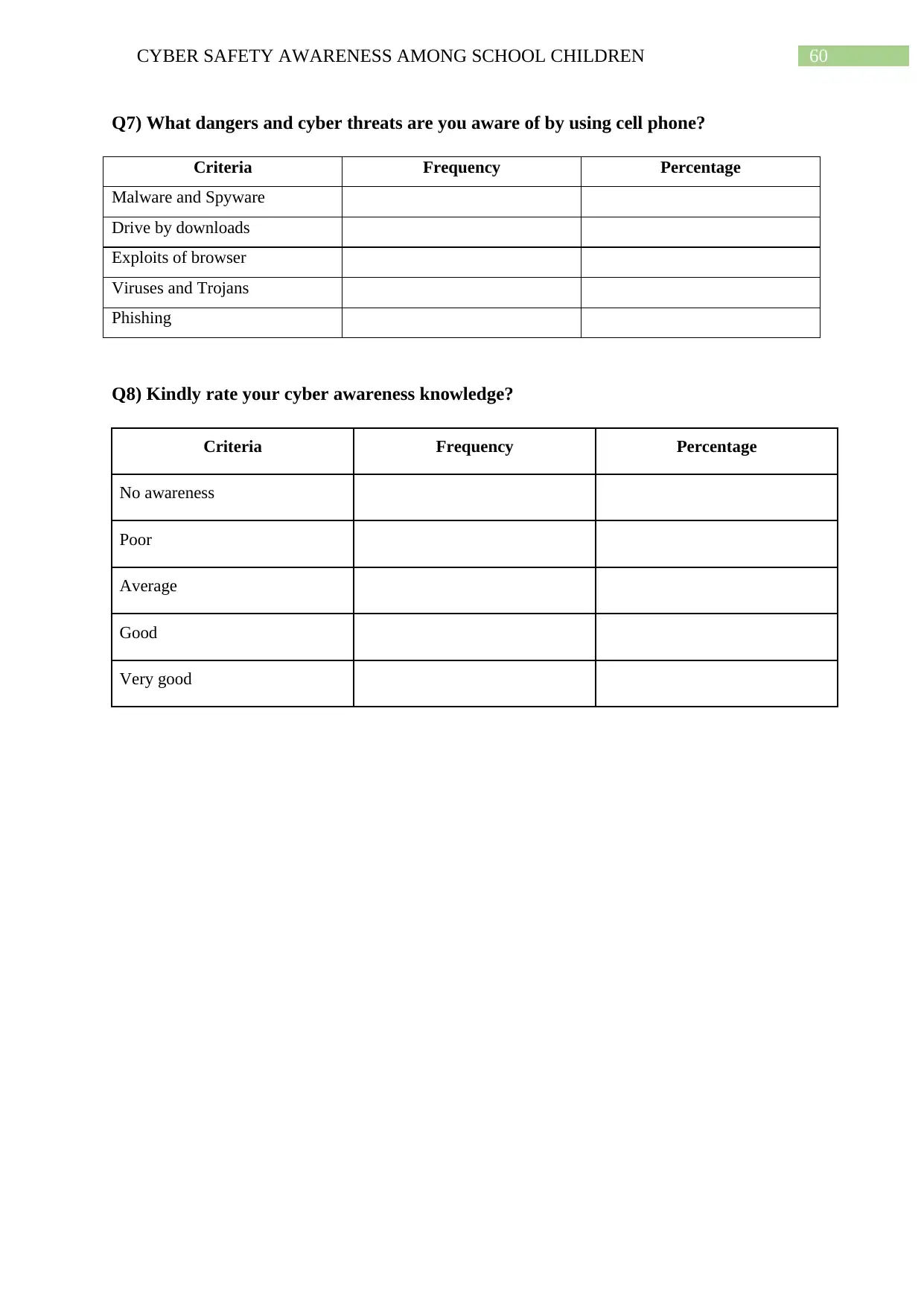
60CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Q7) What dangers and cyber threats are you aware of by using cell phone?
Criteria Frequency Percentage
Malware and Spyware
Drive by downloads
Exploits of browser
Viruses and Trojans
Phishing
Q8) Kindly rate your cyber awareness knowledge?
Criteria Frequency Percentage
No awareness
Poor
Average
Good
Very good
Q7) What dangers and cyber threats are you aware of by using cell phone?
Criteria Frequency Percentage
Malware and Spyware
Drive by downloads
Exploits of browser
Viruses and Trojans
Phishing
Q8) Kindly rate your cyber awareness knowledge?
Criteria Frequency Percentage
No awareness
Poor
Average
Good
Very good
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
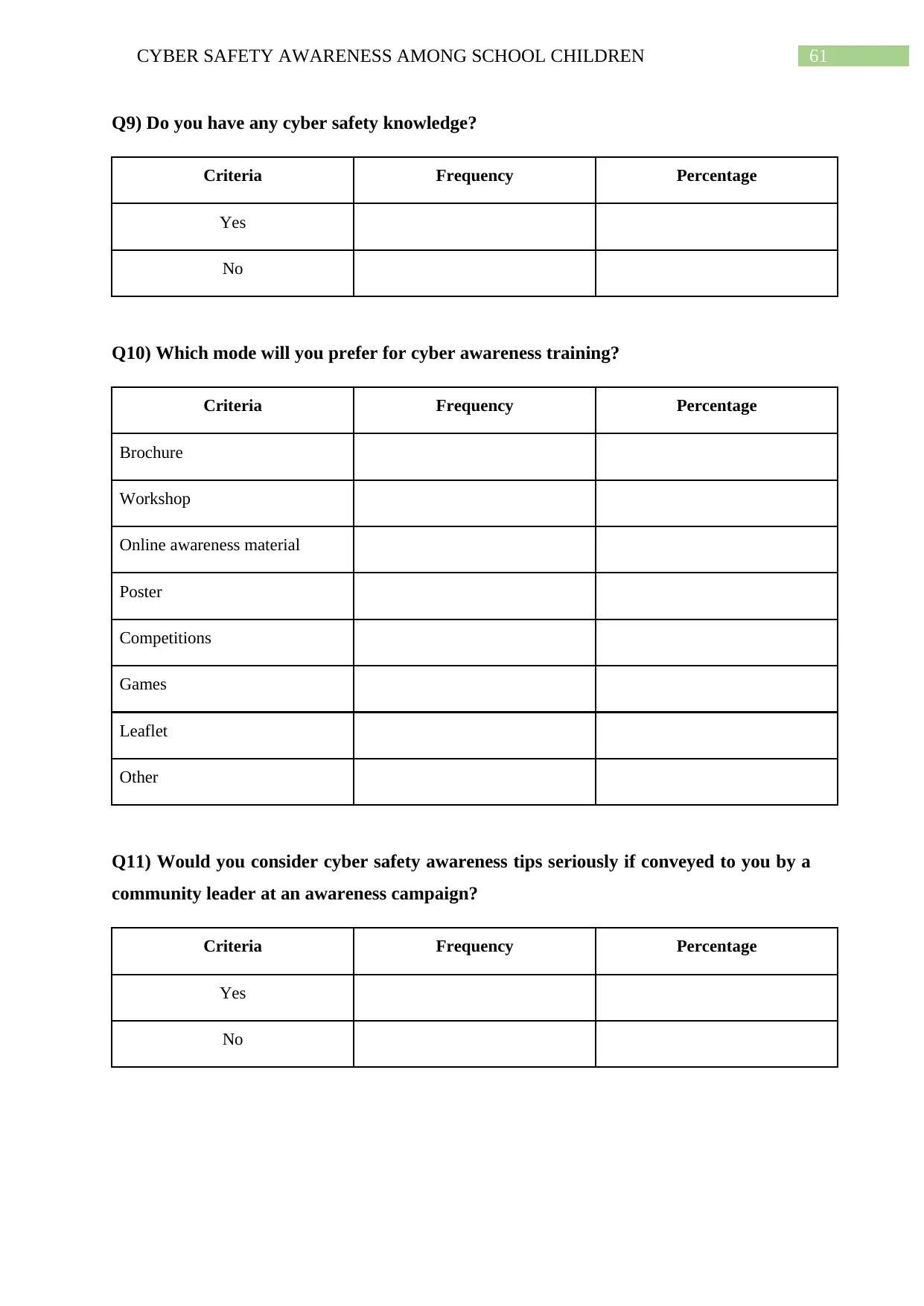
61CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Q9) Do you have any cyber safety knowledge?
Criteria Frequency Percentage
Yes
No
Q10) Which mode will you prefer for cyber awareness training?
Criteria Frequency Percentage
Brochure
Workshop
Online awareness material
Poster
Competitions
Games
Leaflet
Other
Q11) Would you consider cyber safety awareness tips seriously if conveyed to you by a
community leader at an awareness campaign?
Criteria Frequency Percentage
Yes
No
Q9) Do you have any cyber safety knowledge?
Criteria Frequency Percentage
Yes
No
Q10) Which mode will you prefer for cyber awareness training?
Criteria Frequency Percentage
Brochure
Workshop
Online awareness material
Poster
Competitions
Games
Leaflet
Other
Q11) Would you consider cyber safety awareness tips seriously if conveyed to you by a
community leader at an awareness campaign?
Criteria Frequency Percentage
Yes
No
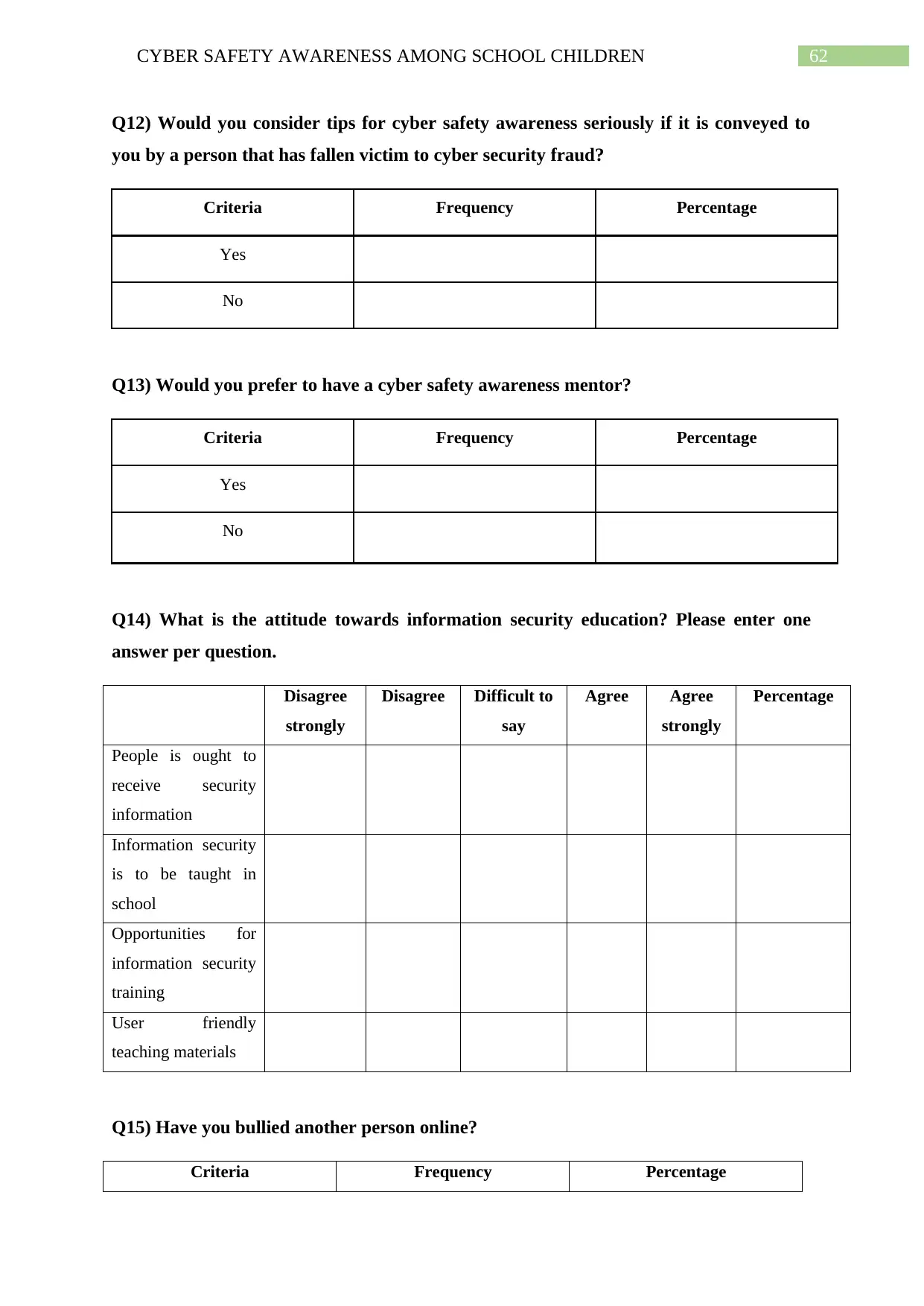
62CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Q12) Would you consider tips for cyber safety awareness seriously if it is conveyed to
you by a person that has fallen victim to cyber security fraud?
Criteria Frequency Percentage
Yes
No
Q13) Would you prefer to have a cyber safety awareness mentor?
Criteria Frequency Percentage
Yes
No
Q14) What is the attitude towards information security education? Please enter one
answer per question.
Disagree
strongly
Disagree Difficult to
say
Agree Agree
strongly
Percentage
People is ought to
receive security
information
Information security
is to be taught in
school
Opportunities for
information security
training
User friendly
teaching materials
Q15) Have you bullied another person online?
Criteria Frequency Percentage
Q12) Would you consider tips for cyber safety awareness seriously if it is conveyed to
you by a person that has fallen victim to cyber security fraud?
Criteria Frequency Percentage
Yes
No
Q13) Would you prefer to have a cyber safety awareness mentor?
Criteria Frequency Percentage
Yes
No
Q14) What is the attitude towards information security education? Please enter one
answer per question.
Disagree
strongly
Disagree Difficult to
say
Agree Agree
strongly
Percentage
People is ought to
receive security
information
Information security
is to be taught in
school
Opportunities for
information security
training
User friendly
teaching materials
Q15) Have you bullied another person online?
Criteria Frequency Percentage

63CYBER SAFETY AWARENESS AMONG SCHOOL CHILDREN
Yes
No
.
Yes
No
.
1 out of 64
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





