Cyber Security Assignment 2022
VerifiedAdded on 2022/07/27
|13
|965
|14
Presentation
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Cyber Security
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

WHAT IS CYBER SECURITY
Ensures that the data of any organization is safe from the
hackers
Encompasses the body of the technologies, practices,
structures and processes
Protects the computers, programs, data and network from
any damage or unauthorized access (Craigen, Diakun-
Thibault & Purse, 2014)
Ensures the data confidentially, integrity and availability
Ensures that the data of any organization is safe from the
hackers
Encompasses the body of the technologies, practices,
structures and processes
Protects the computers, programs, data and network from
any damage or unauthorized access (Craigen, Diakun-
Thibault & Purse, 2014)
Ensures the data confidentially, integrity and availability

IMPORTANCE OF CYBER
SECURITY
To protect from the security breaches
Preventing the hackers from accessing to the system or
network (Tarter, 2017)
Protecting the information of organization as well as the
information of customers and employee.
Securing the network and system
SECURITY
To protect from the security breaches
Preventing the hackers from accessing to the system or
network (Tarter, 2017)
Protecting the information of organization as well as the
information of customers and employee.
Securing the network and system
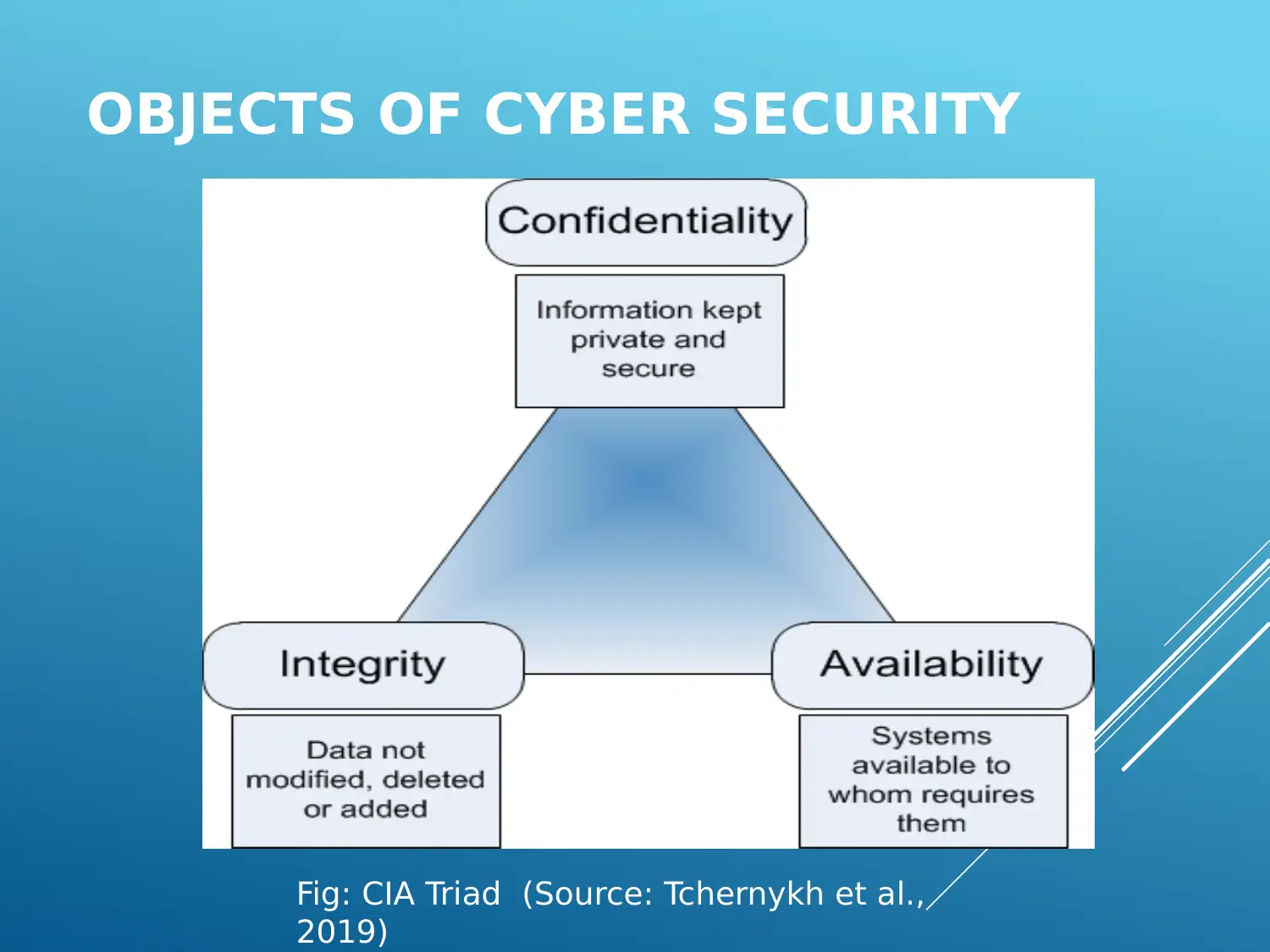
OBJECTS OF CYBER SECURITY
Fig: CIA Triad (Source: Tchernykh et al.,
2019)
Fig: CIA Triad (Source: Tchernykh et al.,
2019)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CYBER SECURITY IN
ORGANIZATION
Contains the set of security management tools with the
inclusive risks management strategies and wide security
awareness program (Kuypers, Maillart & Paté-Cornell,
2016)
Identifies the potential risks and will also pertain the cost
of those risks
Helps in preventing the risks before they occur
Helps in assessing the tactical plan in the organization
ORGANIZATION
Contains the set of security management tools with the
inclusive risks management strategies and wide security
awareness program (Kuypers, Maillart & Paté-Cornell,
2016)
Identifies the potential risks and will also pertain the cost
of those risks
Helps in preventing the risks before they occur
Helps in assessing the tactical plan in the organization

CYBER SECURITY
GOVERNANCE
Helps in controlling and directing the IT security
Pertains who is the right and authorized person for
making the decision (De Bruin & Von Solms, 2016)
Provides the oversight and specifies the accountability
Ensures that the security strategies are properly aligned
with the objectives of the business
GOVERNANCE
Helps in controlling and directing the IT security
Pertains who is the right and authorized person for
making the decision (De Bruin & Von Solms, 2016)
Provides the oversight and specifies the accountability
Ensures that the security strategies are properly aligned
with the objectives of the business

LEGAL IMPLICATIONS OF
CYBERSECURITY ON
BUSINESS
Legal policies include the wide range of the legal
measures and consideration
Combating and preventing the cybercrime in the
organizations
Required areas including the jurisdiction, criminalization,
internet service, International Corporation and procedural
powers (Rothrock, Kaplan & Van Der Oord, 2018)
Legal factors and laws of the cyber crimes are the
frequent concern of the criminalization
CYBERSECURITY ON
BUSINESS
Legal policies include the wide range of the legal
measures and consideration
Combating and preventing the cybercrime in the
organizations
Required areas including the jurisdiction, criminalization,
internet service, International Corporation and procedural
powers (Rothrock, Kaplan & Van Der Oord, 2018)
Legal factors and laws of the cyber crimes are the
frequent concern of the criminalization
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

POLITICAL IMPLICATIONS OF
CYBERSECURITY ON
BUSINESS
Prioritizing the cyber security as the national issue
Strengthening the international collaboration
Furnace the public-private partnerships (Cavelty, 2014)
Evolution of Inclusive National Cybersecurity Ingenuity
Developments to the better information sharing
Working to the passage of main cyber security bill
CYBERSECURITY ON
BUSINESS
Prioritizing the cyber security as the national issue
Strengthening the international collaboration
Furnace the public-private partnerships (Cavelty, 2014)
Evolution of Inclusive National Cybersecurity Ingenuity
Developments to the better information sharing
Working to the passage of main cyber security bill

CYBERSECURITY POLICIES
Spyware and Virus Protection policy
Intrusion Prevention policy
Device and Application Control (Alotaibi, Furnell & Clarke,
2016)
Firewall Policy
Host Integrity policy
Exceptions policy
Live Update policy
Spyware and Virus Protection policy
Intrusion Prevention policy
Device and Application Control (Alotaibi, Furnell & Clarke,
2016)
Firewall Policy
Host Integrity policy
Exceptions policy
Live Update policy

CYBERSECURITY STANDARDS
Published materials and attempt for protecting the cyber
environment of the organization
Includes the users, software, networks, data, devices,
processes, applications, services and data storage
Main objectives is to mitigate the risks by mitigating and
preventing the cyber attacks
Regulations and standards are the generic set of the
prescription for the ideal execution of the proper
measures (Collier et al., 2014)
Published materials and attempt for protecting the cyber
environment of the organization
Includes the users, software, networks, data, devices,
processes, applications, services and data storage
Main objectives is to mitigate the risks by mitigating and
preventing the cyber attacks
Regulations and standards are the generic set of the
prescription for the ideal execution of the proper
measures (Collier et al., 2014)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CONCLUSION
Most of the large organizations with the significant
resources and top talent devoted.
More highly skilled employees in the cyber security roles
can help the nation or the organization for responding
more robustly.
This will help the organization to prevent the cyber
security by applying proper regulation and policies.
Most of the large organizations with the significant
resources and top talent devoted.
More highly skilled employees in the cyber security roles
can help the nation or the organization for responding
more robustly.
This will help the organization to prevent the cyber
security by applying proper regulation and policies.

REFERENCES
Alotaibi, M., Furnell, S., & Clarke, N. (2016, December). Information security policies: a
review of challenges and influencing factors. In 2016 11th International Conference for
Internet Technology and Secured Transactions (ICITST) (pp. 352-358). IEEE.
Cavelty, M. D. (2014). Breaking the cyber-security dilemma: Aligning security needs and
removing vulnerabilities. Science and engineering ethics, 20(3), 701-715.
Collier, Z. A., DiMase, D., Walters, S., Tehranipoor, M. M., Lambert, J. H., & Linkov, I.
(2014). Cybersecurity standards: Managing risk and creating resilience. Computer, 47(9),
70-76.
Craigen, D., Diakun-Thibault, N., & Purse, R. (2014). Defining cybersecurity. Technology
Innovation Management Review, 4(10).
De Bruin, R., & Von Solms, S. H. (2016, May). Cybersecurity Governance: How can we
measure it?. In 2016 IST-Africa Week Conference (pp. 1-9). IEEE.
Kuypers, M. A., Maillart, T., & Paté-Cornell, E. (2016). An empirical analysis of cyber
security incidents at a large organization. Department of Management Science and
Engineering, Stanford University, School of Information, UC Berkeley, http://fsi. stanford.
edu/sites/default/files/kuypersweis_v7. pdf, accessed July, 30.
Alotaibi, M., Furnell, S., & Clarke, N. (2016, December). Information security policies: a
review of challenges and influencing factors. In 2016 11th International Conference for
Internet Technology and Secured Transactions (ICITST) (pp. 352-358). IEEE.
Cavelty, M. D. (2014). Breaking the cyber-security dilemma: Aligning security needs and
removing vulnerabilities. Science and engineering ethics, 20(3), 701-715.
Collier, Z. A., DiMase, D., Walters, S., Tehranipoor, M. M., Lambert, J. H., & Linkov, I.
(2014). Cybersecurity standards: Managing risk and creating resilience. Computer, 47(9),
70-76.
Craigen, D., Diakun-Thibault, N., & Purse, R. (2014). Defining cybersecurity. Technology
Innovation Management Review, 4(10).
De Bruin, R., & Von Solms, S. H. (2016, May). Cybersecurity Governance: How can we
measure it?. In 2016 IST-Africa Week Conference (pp. 1-9). IEEE.
Kuypers, M. A., Maillart, T., & Paté-Cornell, E. (2016). An empirical analysis of cyber
security incidents at a large organization. Department of Management Science and
Engineering, Stanford University, School of Information, UC Berkeley, http://fsi. stanford.
edu/sites/default/files/kuypersweis_v7. pdf, accessed July, 30.

REFERENCES
Lanz, J. (2014). Cybersecurity governance: The role of the audit
committee and the CPA. The CPA Journal, 84(11), 6.
Rothrock, R. A., Kaplan, J., & Van Der Oord, F. (2018). The board's role in
managing cybersecurity risks. MIT Sloan Management Review, 59(2), 12-
15.
Tarter, A. (2017). Importance of cyber security. In Community Policing-A
European Perspective (pp. 213-230). Springer, Cham.
Tchernykh, A., Schwiegelsohn, U., Talbi, E. G., & Babenko, M. (2019).
Towards understanding uncertainty in cloud computing with risks of
confidentiality, integrity, and availability. Journal of Computational
Science, 36, 100581.
Weber, R. H., & Studer, E. (2016). Cybersecurity in the Internet of Things:
Legal aspects. Computer Law & Security Review, 32(5), 715-728.
Lanz, J. (2014). Cybersecurity governance: The role of the audit
committee and the CPA. The CPA Journal, 84(11), 6.
Rothrock, R. A., Kaplan, J., & Van Der Oord, F. (2018). The board's role in
managing cybersecurity risks. MIT Sloan Management Review, 59(2), 12-
15.
Tarter, A. (2017). Importance of cyber security. In Community Policing-A
European Perspective (pp. 213-230). Springer, Cham.
Tchernykh, A., Schwiegelsohn, U., Talbi, E. G., & Babenko, M. (2019).
Towards understanding uncertainty in cloud computing with risks of
confidentiality, integrity, and availability. Journal of Computational
Science, 36, 100581.
Weber, R. H., & Studer, E. (2016). Cybersecurity in the Internet of Things:
Legal aspects. Computer Law & Security Review, 32(5), 715-728.
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





