Southern Cross University CMP71001: Cyber Security Report on BYOD
VerifiedAdded on 2023/04/20
|11
|1923
|183
Report
AI Summary
This cybersecurity report, prepared for Southern Cross University's CMP71001 unit, assesses the risks associated with a Bring Your Own Device (BYOD) policy. The report identifies critical information assets and analyzes threats posed by BYOD, including vulnerabilities in computer devices, licenses, cloud storage, the university website, servers, and the network monitoring system. It includes a risk assessment, evaluating the likelihood and impact of potential threats. The report then explores certificate-based and password-based authentication methods, comparing their advantages and disadvantages in securing the university's systems. Finally, the report addresses spam and phishing, outlining characteristics of spam emails and providing strategies to avoid them, emphasizing the importance of vigilance and security measures to protect the university's network and information systems.
Running Head: CYBER SECURITY 0
Cyber Security
Report
Student name
Cyber Security
Report
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CYBER SECURITY 1
Table of Contents
Task -1.............................................................................................................................................2
Risk Assessment:.........................................................................................................................4
Task -2.............................................................................................................................................5
Certificate-based Authentication..................................................................................................5
Password-based authentication:...................................................................................................5
Task -3.............................................................................................................................................7
References........................................................................................................................................8
Table of Contents
Task -1.............................................................................................................................................2
Risk Assessment:.........................................................................................................................4
Task -2.............................................................................................................................................5
Certificate-based Authentication..................................................................................................5
Password-based authentication:...................................................................................................5
Task -3.............................................................................................................................................7
References........................................................................................................................................8

CYBER SECURITY 2
Task -1
University is having different information assets for their business processes. Therefore, they
must know about those assets, which are critical. Critical information assets are required to fulfill
basic needs of university. University is having their Intellectual Property (IP) in their system
(Andrijcic & Horowitz, 2016). However, all those assets should have proper security. Follows
are critical information assets of university:
Compatible devices
License
Cloud storage
Website of university
University Servers
Network monitoring system
Bring Your Own Device (BYOD) system is currently implemented in our university. It means
anyone can take their own device in university premises for different type of works. BYOD
system is providing facility to connect with university internal network for business purposes of
university as well as other works (Arlitsch & Edelman, 2014). It has many advantages as well as
few disadvantages.
These are the advantages of the BYOD system:
Lower cost
Flexibility to bring devices to home
Technological familiarity
It has some disadvantages, which are costs of employees, security and device disparity. It is
depend on the network of the organization. Therefore, it is useful for low-level organization’s
business. Many organizations are having two different types of network that are intranet and
extranet (Barkly, 2018). Local people or devices are connected with the university intranet for
different works. In the extranet, outside people are using that network that has high level of
security. All those critical information assets are connected through internal network. Therefore,
Task -1
University is having different information assets for their business processes. Therefore, they
must know about those assets, which are critical. Critical information assets are required to fulfill
basic needs of university. University is having their Intellectual Property (IP) in their system
(Andrijcic & Horowitz, 2016). However, all those assets should have proper security. Follows
are critical information assets of university:
Compatible devices
License
Cloud storage
Website of university
University Servers
Network monitoring system
Bring Your Own Device (BYOD) system is currently implemented in our university. It means
anyone can take their own device in university premises for different type of works. BYOD
system is providing facility to connect with university internal network for business purposes of
university as well as other works (Arlitsch & Edelman, 2014). It has many advantages as well as
few disadvantages.
These are the advantages of the BYOD system:
Lower cost
Flexibility to bring devices to home
Technological familiarity
It has some disadvantages, which are costs of employees, security and device disparity. It is
depend on the network of the organization. Therefore, it is useful for low-level organization’s
business. Many organizations are having two different types of network that are intranet and
extranet (Barkly, 2018). Local people or devices are connected with the university intranet for
different works. In the extranet, outside people are using that network that has high level of
security. All those critical information assets are connected through internal network. Therefore,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBER SECURITY 3
they can be threatened by this policy, as they are having connectivity with the external computer
system and portable devices (Fruhlinger, 2018). In next section, threats of BYOD system to the
critical assets of university will describe.
Threat of BYOD concept to the critical information assets:
1. Computer devices:
Computer systems are connected with the network for different works of university.
Therefore, they should compatible with the present system and technology. If they are
not compatible then they can be affected by the malwares and it will affect whole
system.
2. License
University is allowing their colleagues to download software and other things though
thier network. Therefore, university is responsible for any fault and it is vulnerability
for the university.
3. Cloud storage
University is storing their confidential information at their cloud storage. Therefore, it
is accessible everywhere with proper authorization. However, hackers can get access
through other person’s credentials in the cloud network and storage. Therefore, it is
also vulnerability for the university (Bhagat, 2012).
4. Website of University
Website of university is providing access to different portals that are required high
security, such as fee collection, examination, finance, and many others. If anyone
accesses the website and portals without proper security updates then it is a way for
hackers to data breaches and many things.
5. University Servers
Colleagues and students are accessing different things from university server.
Therefore, it is restricted for the unknown devices to access servers of university for
security purposes.
6. Network Monitoring system
Network infrastructure of university is critical information asset, as it is the most
suitable way to communicate inside the university as well as outside for business
they can be threatened by this policy, as they are having connectivity with the external computer
system and portable devices (Fruhlinger, 2018). In next section, threats of BYOD system to the
critical assets of university will describe.
Threat of BYOD concept to the critical information assets:
1. Computer devices:
Computer systems are connected with the network for different works of university.
Therefore, they should compatible with the present system and technology. If they are
not compatible then they can be affected by the malwares and it will affect whole
system.
2. License
University is allowing their colleagues to download software and other things though
thier network. Therefore, university is responsible for any fault and it is vulnerability
for the university.
3. Cloud storage
University is storing their confidential information at their cloud storage. Therefore, it
is accessible everywhere with proper authorization. However, hackers can get access
through other person’s credentials in the cloud network and storage. Therefore, it is
also vulnerability for the university (Bhagat, 2012).
4. Website of University
Website of university is providing access to different portals that are required high
security, such as fee collection, examination, finance, and many others. If anyone
accesses the website and portals without proper security updates then it is a way for
hackers to data breaches and many things.
5. University Servers
Colleagues and students are accessing different things from university server.
Therefore, it is restricted for the unknown devices to access servers of university for
security purposes.
6. Network Monitoring system
Network infrastructure of university is critical information asset, as it is the most
suitable way to communicate inside the university as well as outside for business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CYBER SECURITY 4
processes. If personal devices are accessing the network without updated softwares or
operating system then it will be affect from the malicious softwares. This is a huge
issue for university and it is vulnerability for this asset (Von Solms & Van Niekerk,
2013).
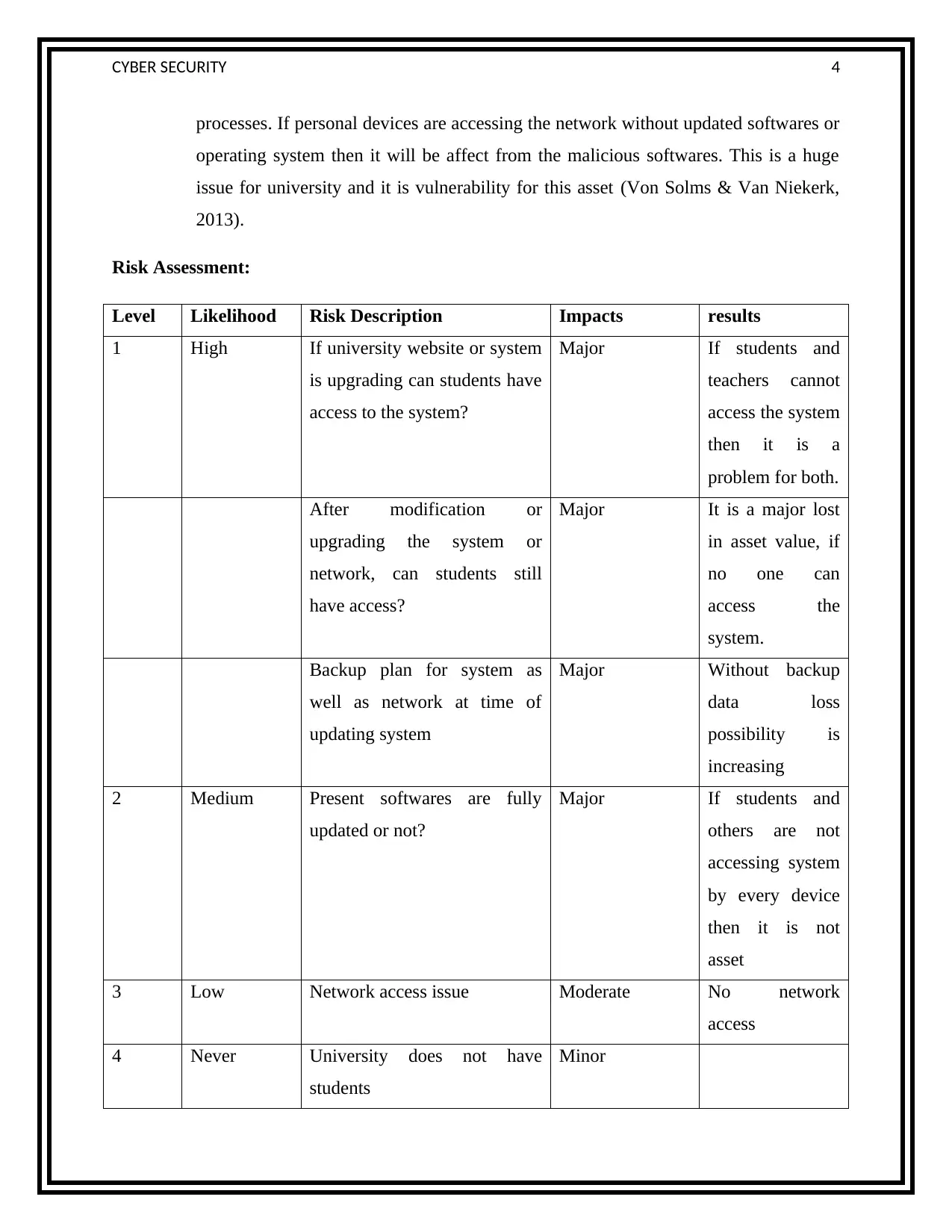
Risk Assessment:
Level Likelihood Risk Description Impacts results
1 High If university website or system
is upgrading can students have
access to the system?
Major If students and
teachers cannot
access the system
then it is a
problem for both.
After modification or
upgrading the system or
network, can students still
have access?
Major It is a major lost
in asset value, if
no one can
access the
system.
Backup plan for system as
well as network at time of
updating system
Major Without backup
data loss
possibility is
increasing
2 Medium Present softwares are fully
updated or not?
Major If students and
others are not
accessing system
by every device
then it is not
asset
3 Low Network access issue Moderate No network
access
4 Never University does not have
students
Minor
processes. If personal devices are accessing the network without updated softwares or
operating system then it will be affect from the malicious softwares. This is a huge
issue for university and it is vulnerability for this asset (Von Solms & Van Niekerk,
2013).
Risk Assessment:
Level Likelihood Risk Description Impacts results
1 High If university website or system
is upgrading can students have
access to the system?
Major If students and
teachers cannot
access the system
then it is a
problem for both.
After modification or
upgrading the system or
network, can students still
have access?
Major It is a major lost
in asset value, if
no one can
access the
system.
Backup plan for system as
well as network at time of
updating system
Major Without backup
data loss
possibility is
increasing
2 Medium Present softwares are fully
updated or not?
Major If students and
others are not
accessing system
by every device
then it is not
asset
3 Low Network access issue Moderate No network
access
4 Never University does not have
students
Minor
CYBER SECURITY 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
CYBER SECURITY 6
Task -2
Certificate-based Authentication
Digital signature can be used for verifying users in certificate-based authentication (REDHAT,
2018). Server always verify user before providing any facility or accessibility of university
system and network. It is a fast way of authentication as well. Code of ethics must be followed
by each user of the system (ACSC, 2017).
Advantages Disadvantages
Secret private key is used for verification of
users
It requires PKI that is cost effective for
university
It is not require any authentication agents Cost effective
Digital certificate can use for login as well as
servers, emails, and web access
It is not require distribute public key at the
time of update (SSH, 2018)
It is highly scalable
Certificate-based authentication is providing a message, emails or voice call after sending
password (GlobalSign, 2016). It is like digital certificate for accessing the network and
university system.
Password-based authentication:
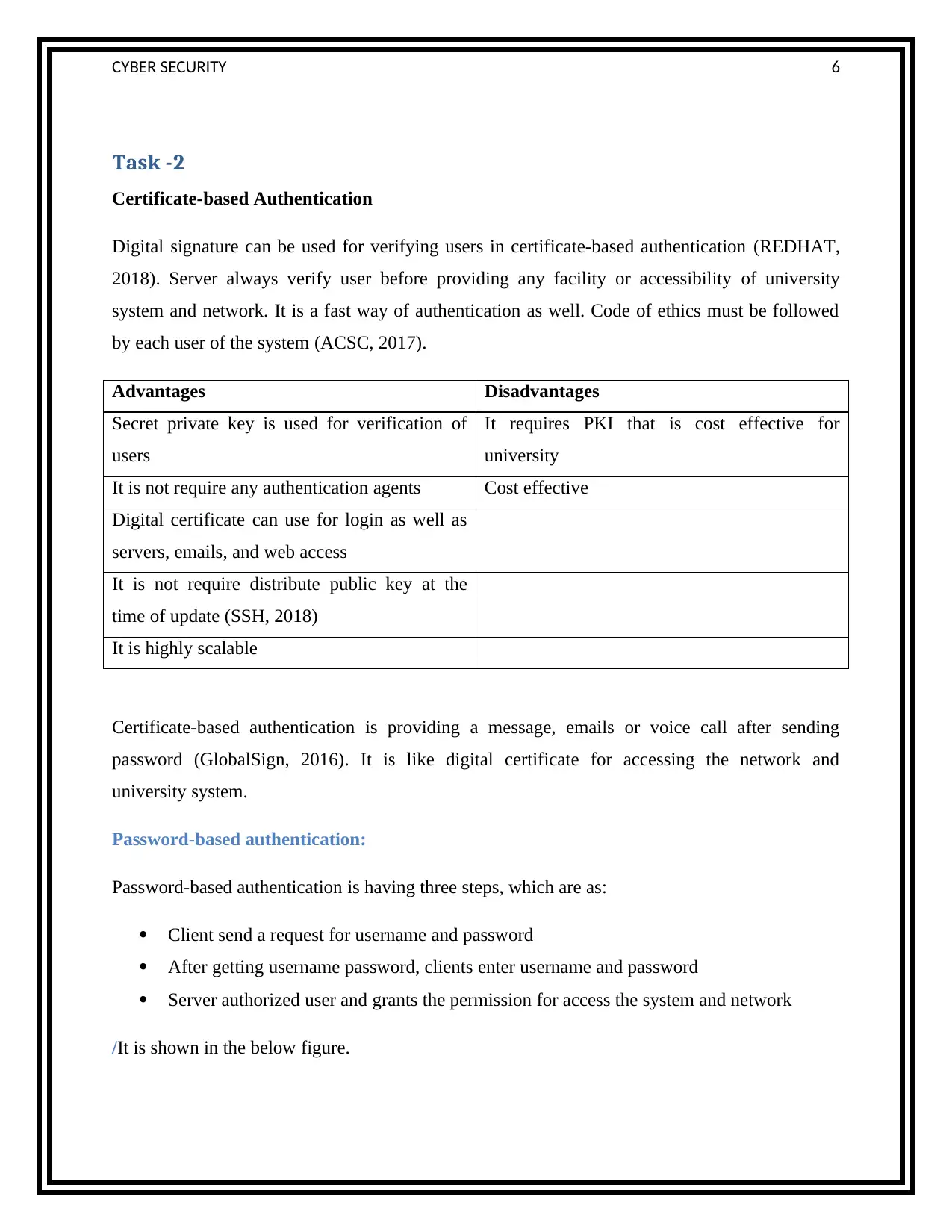
Password-based authentication is having three steps, which are as:
Client send a request for username and password
After getting username password, clients enter username and password
Server authorized user and grants the permission for access the system and network
/It is shown in the below figure.
Task -2
Certificate-based Authentication
Digital signature can be used for verifying users in certificate-based authentication (REDHAT,
2018). Server always verify user before providing any facility or accessibility of university
system and network. It is a fast way of authentication as well. Code of ethics must be followed
by each user of the system (ACSC, 2017).
Advantages Disadvantages
Secret private key is used for verification of
users
It requires PKI that is cost effective for
university
It is not require any authentication agents Cost effective
Digital certificate can use for login as well as
servers, emails, and web access
It is not require distribute public key at the
time of update (SSH, 2018)
It is highly scalable
Certificate-based authentication is providing a message, emails or voice call after sending
password (GlobalSign, 2016). It is like digital certificate for accessing the network and
university system.
Password-based authentication:
Password-based authentication is having three steps, which are as:
Client send a request for username and password
After getting username password, clients enter username and password
Server authorized user and grants the permission for access the system and network
/It is shown in the below figure.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CYBER SECURITY 7
Source: (REDHAT, 2018)
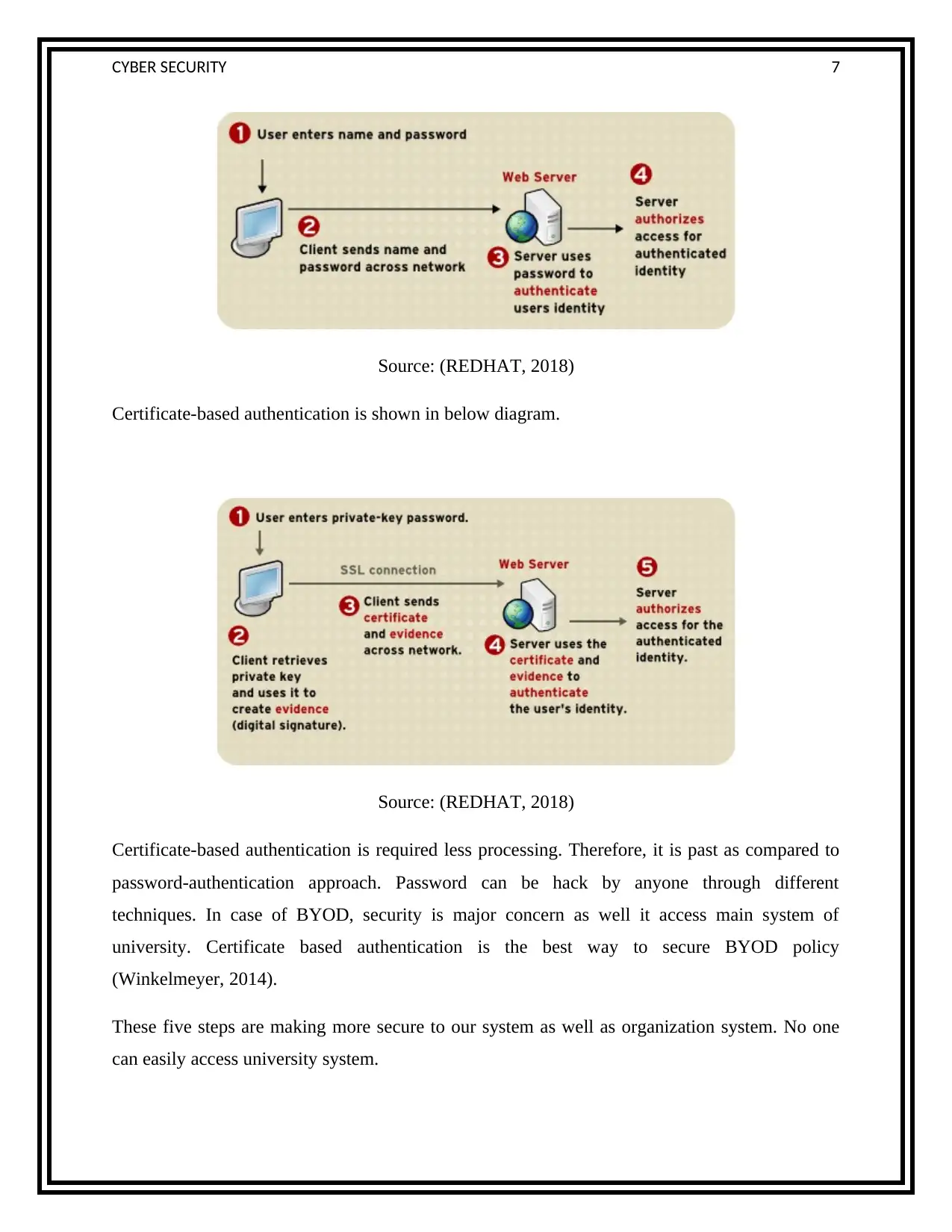
Certificate-based authentication is shown in below diagram.
Source: (REDHAT, 2018)
Certificate-based authentication is required less processing. Therefore, it is past as compared to
password-authentication approach. Password can be hack by anyone through different
techniques. In case of BYOD, security is major concern as well it access main system of
university. Certificate based authentication is the best way to secure BYOD policy
(Winkelmeyer, 2014).
These five steps are making more secure to our system as well as organization system. No one
can easily access university system.
Source: (REDHAT, 2018)
Certificate-based authentication is shown in below diagram.
Source: (REDHAT, 2018)
Certificate-based authentication is required less processing. Therefore, it is past as compared to
password-authentication approach. Password can be hack by anyone through different
techniques. In case of BYOD, security is major concern as well it access main system of
university. Certificate based authentication is the best way to secure BYOD policy
(Winkelmeyer, 2014).
These five steps are making more secure to our system as well as organization system. No one
can easily access university system.

CYBER SECURITY 8
Task -3
Sending of unnecessary electronic messages to anyone is known as spam. It is used different
links for sending messages (runbox.com, 2018). Any message must follow these conditions
otherwise; it is treated as a spam.
Emails that have spontaneous business purposes must not be sent
Individual or association must approved the sending of the message for business emails
Business emails must have unsubscribe option
User cannot use address-harvesting softwares for emails sending
Furthermore, spams are also containing malwares that are not good for computer peripherals as
well as university information system. Therefore, these characteristics of spams are as follows:
To: field is missing
No message id
To: field is having invalid email address
Suspect message ID
Cc: field is having more than 15 recipients
From: field is having same details as To: field
These messages can send without any consent of receivers according to act.
Government bodies, such as local government, federal government
Registered charity organization’s messages
Registered political parties messages
Messages of educational institutions
These are things that we can do to avoid spams:
Always check the recipients and sender address fields of suspicious electronic message
Both network and computer system must have firewall (Spykerman , 2016).
Read headers of emails carefully
Always take serious auto replies
Do not provide email address for free subscription of different fake sites
Do not use same credentials for many domains.
Task -3
Sending of unnecessary electronic messages to anyone is known as spam. It is used different
links for sending messages (runbox.com, 2018). Any message must follow these conditions
otherwise; it is treated as a spam.
Emails that have spontaneous business purposes must not be sent
Individual or association must approved the sending of the message for business emails
Business emails must have unsubscribe option
User cannot use address-harvesting softwares for emails sending
Furthermore, spams are also containing malwares that are not good for computer peripherals as
well as university information system. Therefore, these characteristics of spams are as follows:
To: field is missing
No message id
To: field is having invalid email address
Suspect message ID
Cc: field is having more than 15 recipients
From: field is having same details as To: field
These messages can send without any consent of receivers according to act.
Government bodies, such as local government, federal government
Registered charity organization’s messages
Registered political parties messages
Messages of educational institutions
These are things that we can do to avoid spams:
Always check the recipients and sender address fields of suspicious electronic message
Both network and computer system must have firewall (Spykerman , 2016).
Read headers of emails carefully
Always take serious auto replies
Do not provide email address for free subscription of different fake sites
Do not use same credentials for many domains.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CYBER SECURITY 9
All these things make secure our email accounts from the spams as well as other malicious
activities. Therefore, always treat an email as unsecure messages.
Phishing is simply unwanted messages flooding in an email account. They mail can have
malwares that creates a problem for intranet as well as internal servers.
References
ACSC, 2017. Australian Cyber Security Centre. [Online]
Available at: https://www.acsc.gov.au/publications/ACSC_Threat_Report_2017.pdf
[Accessed 12 December 2018].
Andrijcic, E. & Horowitz, B., 2016. A Macro‐Economic Framework for Evaluation of Cyber
Security Risks Related to Protection of Intellectual Property. Risk analysis, 26(4), pp. 907-923.
Arlitsch, K. & Edelman, A., 2014. Staying safe: Cyber security for people and organizations.
Journal of Library Administration, 54(1), pp. 46-56.
Barkly, 2018. 5 Cybersecurity Statistics Every Small Business Should Know in 2018. [Online]
Available at: https://blog.barkly.com/small-business-cybersecurity-statistics-2018
Bhagat, . B. C., 2012. Cloud computing governance, cyber security, risk, and compliance
business rules system and method. U. S., Patent No. 13/016,999.
Fruhlinger, J., 2018. Top cybersecurity facts, figures and statistics for 2018. [Online]
Available at: https://www.csoonline.com/article/3153707/security/top-cybersecurity-facts-
figures-and-statistics.html
[Accessed 11 december 2018].
GlobalSign, 2016. What Is Certificate-Based Authentication and Why Should I Use It?. [Online]
Available at: https://www.globalsign.com/en/blog/what-is-certificate-based-authentication/
[Accessed 8 February 2019].
All these things make secure our email accounts from the spams as well as other malicious
activities. Therefore, always treat an email as unsecure messages.
Phishing is simply unwanted messages flooding in an email account. They mail can have
malwares that creates a problem for intranet as well as internal servers.
References
ACSC, 2017. Australian Cyber Security Centre. [Online]
Available at: https://www.acsc.gov.au/publications/ACSC_Threat_Report_2017.pdf
[Accessed 12 December 2018].
Andrijcic, E. & Horowitz, B., 2016. A Macro‐Economic Framework for Evaluation of Cyber
Security Risks Related to Protection of Intellectual Property. Risk analysis, 26(4), pp. 907-923.
Arlitsch, K. & Edelman, A., 2014. Staying safe: Cyber security for people and organizations.
Journal of Library Administration, 54(1), pp. 46-56.
Barkly, 2018. 5 Cybersecurity Statistics Every Small Business Should Know in 2018. [Online]
Available at: https://blog.barkly.com/small-business-cybersecurity-statistics-2018
Bhagat, . B. C., 2012. Cloud computing governance, cyber security, risk, and compliance
business rules system and method. U. S., Patent No. 13/016,999.
Fruhlinger, J., 2018. Top cybersecurity facts, figures and statistics for 2018. [Online]
Available at: https://www.csoonline.com/article/3153707/security/top-cybersecurity-facts-
figures-and-statistics.html
[Accessed 11 december 2018].
GlobalSign, 2016. What Is Certificate-Based Authentication and Why Should I Use It?. [Online]
Available at: https://www.globalsign.com/en/blog/what-is-certificate-based-authentication/
[Accessed 8 February 2019].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CYBER SECURITY 10
REDHAT, 2018. 1.3. Certificates and Authentication. [Online]
Available at: https://access.redhat.com/documentation/en-US/Red_Hat_Certificate_System/8.0/
html/Deployment_Guide/Introduction_to_Public_Key_Cryptography-
Certificates_and_Authentication.html
[Accessed 10 February 2019].
runbox.com, 2018. What is spam, and how to avoid it. [Online]
Available at: https://runbox.com/email-school/what-is-spam-and-how-to-avoid-it/
[Accessed 8 February 2019].
Spykerman , M., 2016. Typical spam characteristics. [Online]
Available at: https://www.spamhelp.org/articles/Spam-filter-article.pdf
[Accessed 8 February 2019].
SSH, 2018. ADVANTAGES AND DISADVANTAGES OF CERTIFICATE AUTHENTICATION.
[Online]
Available at: https://www.ssh.com/manuals/server-zos-product/55/ch06s03s05.html
[Accessed 8 February 2019].
Von Solms, R. & Van Niekerk, J., 2013. From information security to cyber security. computers
& security, Volume 38, pp. 97-102.
Winkelmeyer, R., 2014. Explaining Certificate Authentication – 101 style. [Online]
Available at: https://blog.winkelmeyer.com/2014/07/explaining-certificate-authentication-101-
style/
[Accessed 8 February 2019].
REDHAT, 2018. 1.3. Certificates and Authentication. [Online]
Available at: https://access.redhat.com/documentation/en-US/Red_Hat_Certificate_System/8.0/
html/Deployment_Guide/Introduction_to_Public_Key_Cryptography-
Certificates_and_Authentication.html
[Accessed 10 February 2019].
runbox.com, 2018. What is spam, and how to avoid it. [Online]
Available at: https://runbox.com/email-school/what-is-spam-and-how-to-avoid-it/
[Accessed 8 February 2019].
Spykerman , M., 2016. Typical spam characteristics. [Online]
Available at: https://www.spamhelp.org/articles/Spam-filter-article.pdf
[Accessed 8 February 2019].
SSH, 2018. ADVANTAGES AND DISADVANTAGES OF CERTIFICATE AUTHENTICATION.
[Online]
Available at: https://www.ssh.com/manuals/server-zos-product/55/ch06s03s05.html
[Accessed 8 February 2019].
Von Solms, R. & Van Niekerk, J., 2013. From information security to cyber security. computers
& security, Volume 38, pp. 97-102.
Winkelmeyer, R., 2014. Explaining Certificate Authentication – 101 style. [Online]
Available at: https://blog.winkelmeyer.com/2014/07/explaining-certificate-authentication-101-
style/
[Accessed 8 February 2019].
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





