Cybersecurity Report: Password Cracking Tool Analysis and Testing
VerifiedAdded on 2022/12/29
|10
|1318
|36
Report
AI Summary
This cybersecurity report provides an analysis of password cracking tools, focusing on John the Ripper and RainbowCrack. The report outlines the functionalities of these tools, including their methods for cracking passwords using techniques like brute force and rainbow tables. It also covers penetration testing, specifically FTP installation, anonymous login vulnerabilities, and methods to secure FTP services through SSL certificates and fail2ban. The report demonstrates practical aspects of password cracking and penetration testing, offering insights into securing systems against brute force attacks and other security threats. The conclusion summarizes the different attack modes and the importance of password security. It also includes a bibliography of relevant sources. This report is an example of the type of content available on Desklib, which provides students with past papers and solved assignments.

Running head: Cyber security and analysis
Cyber security and analysis
Name of the student
Name of the university
Author notes
Cyber security and analysis
Name of the student
Name of the university
Author notes
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
2Cyber security and analysis
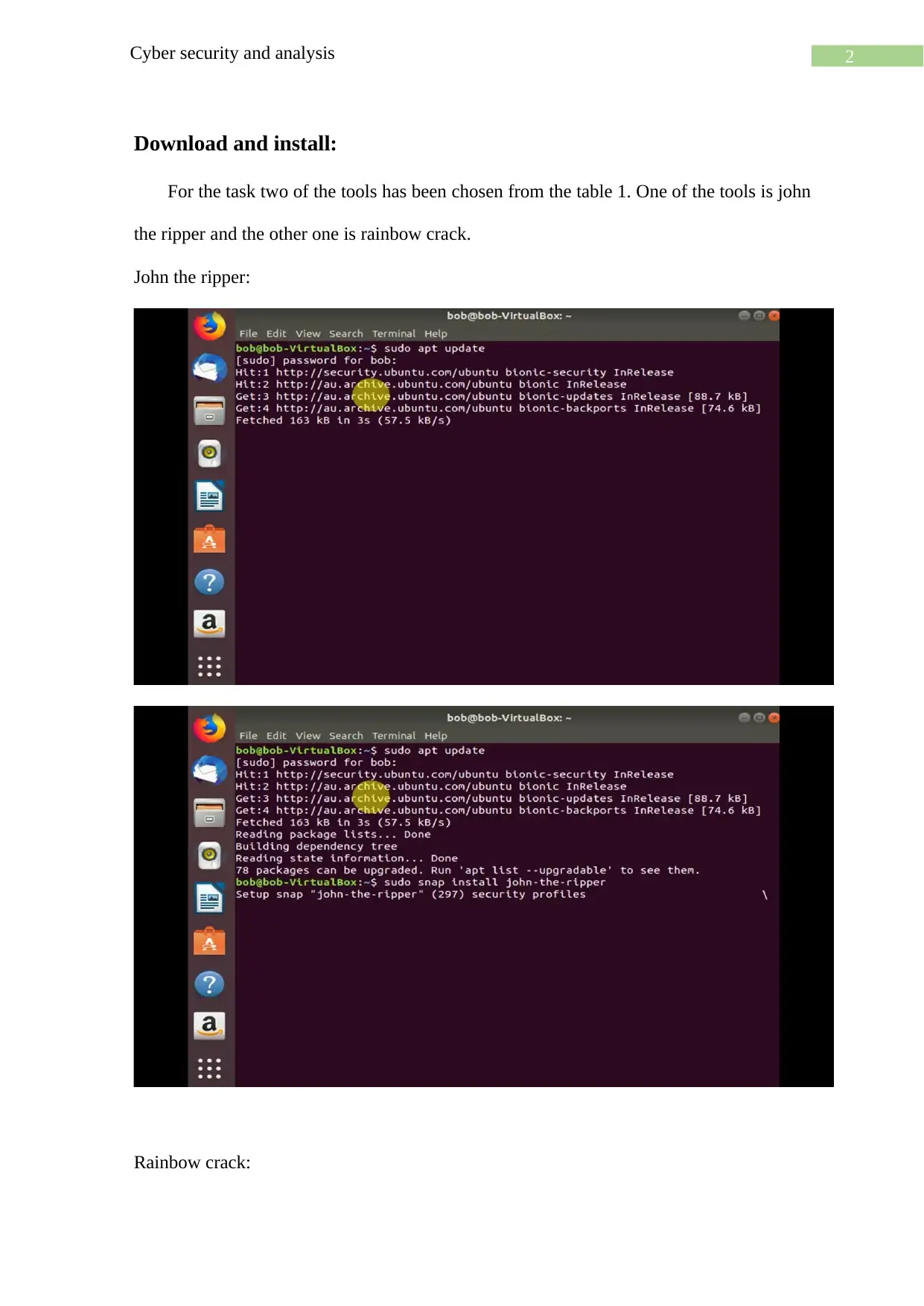
Download and install:
For the task two of the tools has been chosen from the table 1. One of the tools is john
the ripper and the other one is rainbow crack.
John the ripper:
Rainbow crack:
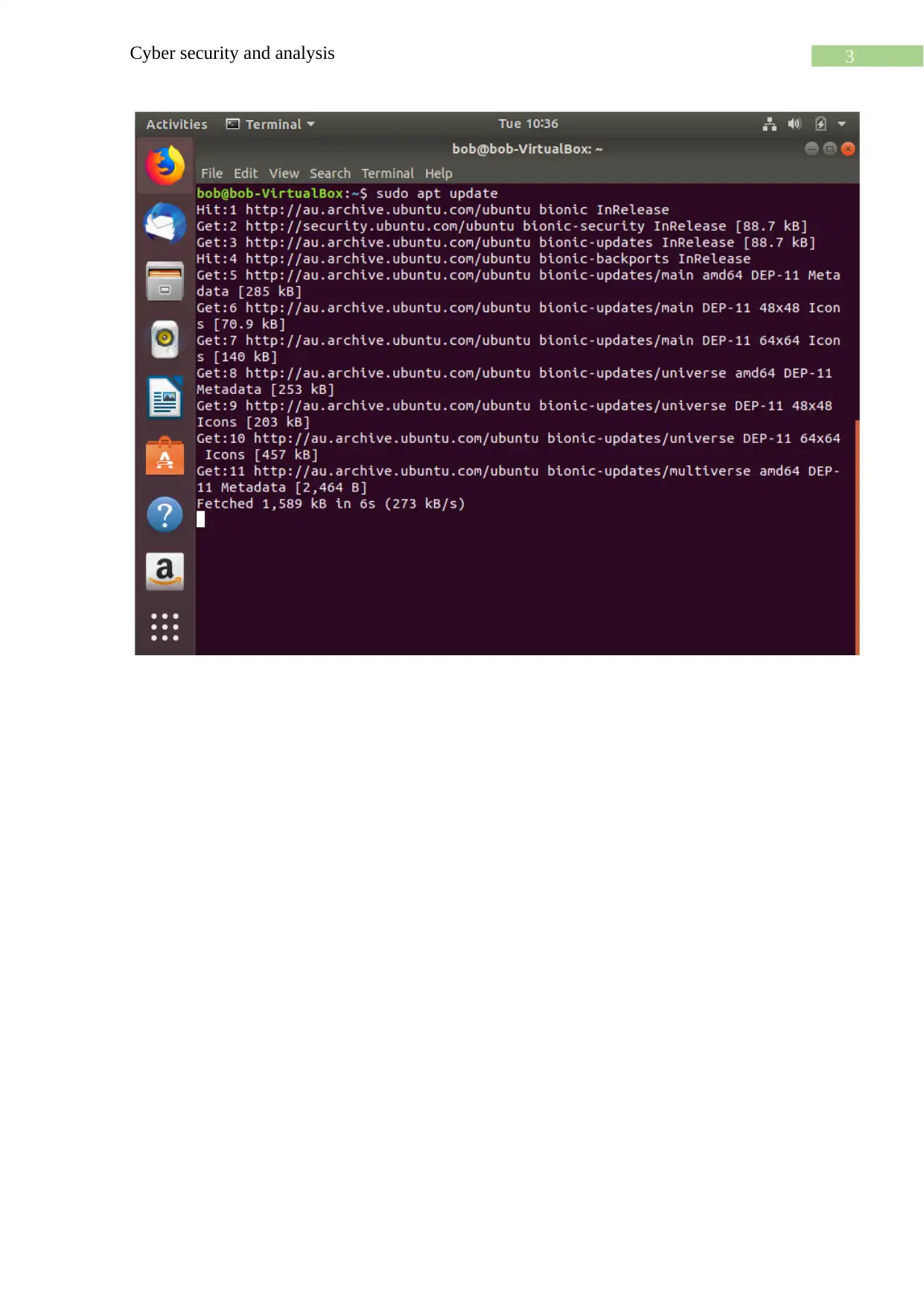
Download and install:
For the task two of the tools has been chosen from the table 1. One of the tools is john
the ripper and the other one is rainbow crack.
John the ripper:
Rainbow crack:
3Cyber security and analysis
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4Cyber security and analysis
Outline:
John the Ripper:
Password cracking:
Password cracking is a complicated process. There is a tool for cracking password which
is John the Ripper (JtR). JtR is an open source and free to use tool which is distributed by
a form of source that can be compiled. Incremental is a type of brute force attack and in
this case, it is very complicated. The passwords that are under 5 characters for the brute
force attack is a trivial process. But with the increase of the length of the password the
complexity also increases.
Rainbow Crack:
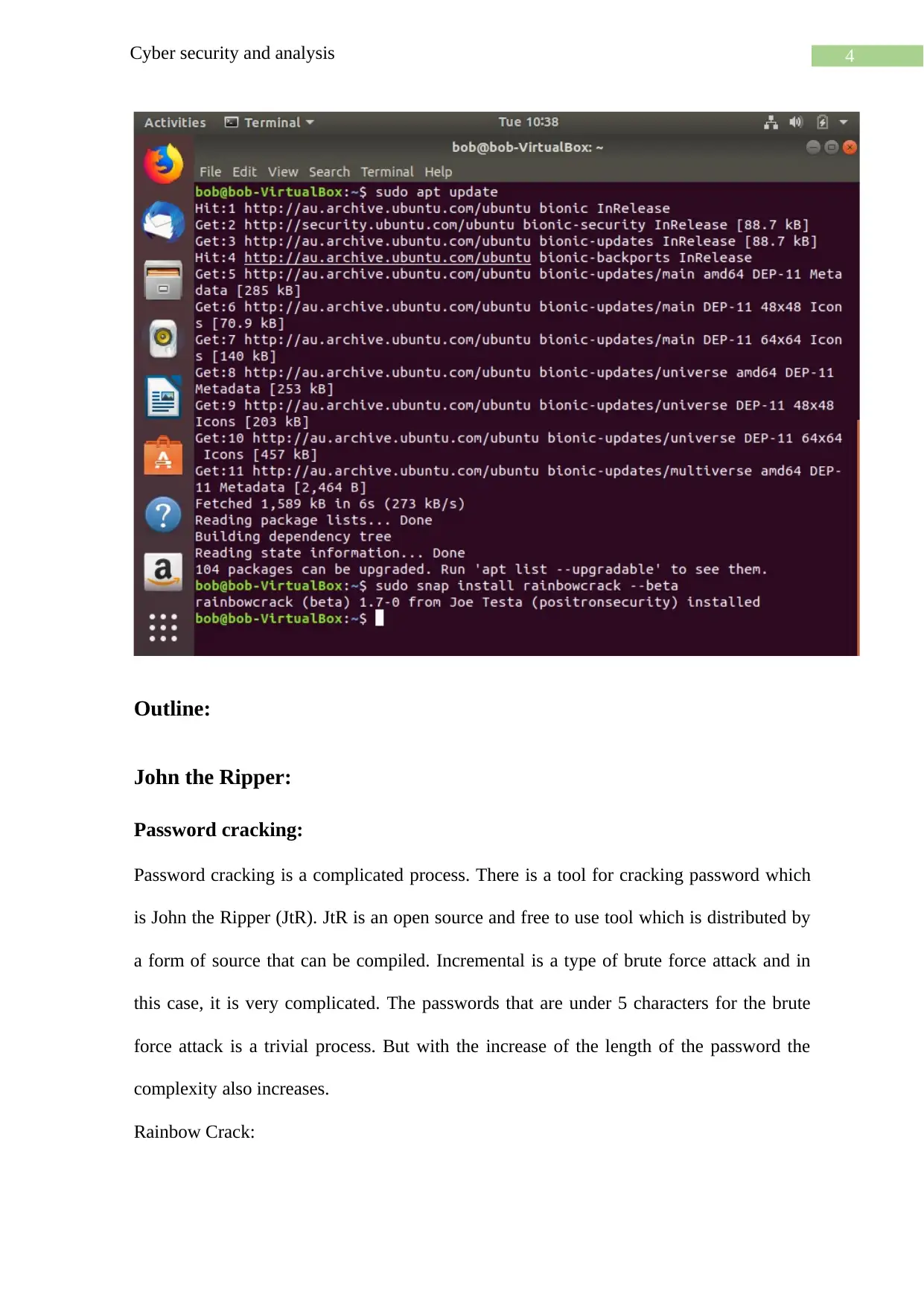
Outline:
John the Ripper:
Password cracking:
Password cracking is a complicated process. There is a tool for cracking password which
is John the Ripper (JtR). JtR is an open source and free to use tool which is distributed by
a form of source that can be compiled. Incremental is a type of brute force attack and in
this case, it is very complicated. The passwords that are under 5 characters for the brute
force attack is a trivial process. But with the increase of the length of the password the
complexity also increases.
Rainbow Crack:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5Cyber security and analysis
Rainbow crack is considered to be the computer program which creates the rainbow table
that uses the password cracking. Rainbow crack is different from the brute force which use
computed tables which is also called the rainbow tables. The rainbow tables are used to
reduce the length for the time that is needed in cracking the password. The trade-off
algorithm that is used by RainbowCrack is known as time memory. The crack of the brute
force also helps in generating of the plaintexts and to compute the hashes. A pre
computation stage is required for the hash cracket. This is a process that takes huge
amount of time but after the completion of the pre computation the hash is stored in a table
which can be cracked with higher performance to that of a brute trade.
Demonstration:
Rainbow Crack
There are certain features of Rainbow Crack that are discussed below:
Suite the tools of full time-memory which also includes the generation of the rainbow
table, rainbow sort, lookup and the conversion.
It also supports the rainbow table for a particular hash algorithm.
It also supports the rainbow table for a particular charset.
The raw format of a file and the compact format of a file is also supported by rainbow
table [6].
It also supports the computation for a multi-core processor.
It supports the acceleration of GPU with the help of NVDIA GPU.
It also accelerates the GPU for GPU’s of AMD [8].
Runs on various type of operating systems.
Runs on Windows XP.
Runs on Windows 8.
Rainbow crack is considered to be the computer program which creates the rainbow table
that uses the password cracking. Rainbow crack is different from the brute force which use
computed tables which is also called the rainbow tables. The rainbow tables are used to
reduce the length for the time that is needed in cracking the password. The trade-off
algorithm that is used by RainbowCrack is known as time memory. The crack of the brute
force also helps in generating of the plaintexts and to compute the hashes. A pre
computation stage is required for the hash cracket. This is a process that takes huge
amount of time but after the completion of the pre computation the hash is stored in a table
which can be cracked with higher performance to that of a brute trade.
Demonstration:
Rainbow Crack
There are certain features of Rainbow Crack that are discussed below:
Suite the tools of full time-memory which also includes the generation of the rainbow
table, rainbow sort, lookup and the conversion.
It also supports the rainbow table for a particular hash algorithm.
It also supports the rainbow table for a particular charset.
The raw format of a file and the compact format of a file is also supported by rainbow
table [6].
It also supports the computation for a multi-core processor.
It supports the acceleration of GPU with the help of NVDIA GPU.
It also accelerates the GPU for GPU’s of AMD [8].
Runs on various type of operating systems.
Runs on Windows XP.
Runs on Windows 8.

6Cyber security and analysis
John the ripper:
There are certain features of this open source tool that are discussed below:
Cross platform, can be build and run on various platforms of desktop.
This is based on a software of password cracking which is very powerful and robust.
It supports jumbo flavours and John core.
It exposes the attack mode of JtR that is very useful.
It simplifies the JtR mode of attack and this is an interface that is very useful.
New attacks can be defined very easily and the session management for multiple
attack can also be defined.
Guess functions help to guess the password manually.
Various type of files that are protected by passwords are imported the function of
2john.
This also translatable completely.
The supported formats are listed below:
Crypt:
“$ cat hashes.txt
SDbsugeBiC58A
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".
$ john --format=crypt hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".
$ john --format=crypt hashes.txt
John the ripper:
There are certain features of this open source tool that are discussed below:
Cross platform, can be build and run on various platforms of desktop.
This is based on a software of password cracking which is very powerful and robust.
It supports jumbo flavours and John core.
It exposes the attack mode of JtR that is very useful.
It simplifies the JtR mode of attack and this is an interface that is very useful.
New attacks can be defined very easily and the session management for multiple
attack can also be defined.
Guess functions help to guess the password manually.
Various type of files that are protected by passwords are imported the function of
2john.
This also translatable completely.
The supported formats are listed below:
Crypt:
“$ cat hashes.txt
SDbsugeBiC58A
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".
$ john --format=crypt hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".
$ john --format=crypt hashes.txt
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7Cyber security and analysis
$ cat hashes.txt
username: SDbsugeBiC58A:
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".
$ john --format=crypt hashes.txt”
Des:
$ cat hashes.txt
SDbsugeBiC58A
$ john hashes.txt
$ john --format=des hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A
$ john hashes.txt
$ john --format=des hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A:
$ john hashes.txt
$ john --format=des hashes.txt”
Password cracking and ease of access:
The tool john the ripper has taken less time than the other tools as this tool is having
some of the advanced features.
$ cat hashes.txt
username: SDbsugeBiC58A:
$ john hashes.txt # Doesn't work. JTR detects hash as "Traditional DES".
$ john --format=crypt hashes.txt”
Des:
$ cat hashes.txt
SDbsugeBiC58A
$ john hashes.txt
$ john --format=des hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A
$ john hashes.txt
$ john --format=des hashes.txt
$ cat hashes.txt
username: SDbsugeBiC58A:
$ john hashes.txt
$ john --format=des hashes.txt”
Password cracking and ease of access:
The tool john the ripper has taken less time than the other tools as this tool is having
some of the advanced features.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8Cyber security and analysis
Penetration testing:
FTP installation process
FTP is installed by typing the apt install vstpd command on the Ubuntu terminal.
After the installation of the FTP type nmap -p21 192.168.1.102.
Anonymous Log in
FTP users can authenticate themselves by clear text sign in protocol mechanism. If the
server allow the user to connect anonymously then the user can connect to the server
easily. Open the vsftpd.conf using the text editor and then change the no option to yes.
Disable the FTP_banner
Type nmap –sV 192.168.1.102. This will scan the ftp from the nmap. Delete the #
symbol from the ftpd_banner statement.
Switch Port for the FTP service
User can switch to any port address by typing the following command
listen_port=portnumber. User should save the file and should restart service of the ftp .
Sniffing process
Type ftp 192.168.1.102 5000 command and then input the user name anfd the
password. Use the Wireshark to capture the traffic. TCP stream is followed to clearly
visible all the credentials of the users.
Usage of the SSL certificate
A certificate is produced by typing the command openssl req -x509 -nodes -days 365 -
newkey rs. Then user should open the vsftpd.conf to alter the default settings.
Resist the Brute_Force attack using Fail2ban
Penetration testing:
FTP installation process
FTP is installed by typing the apt install vstpd command on the Ubuntu terminal.
After the installation of the FTP type nmap -p21 192.168.1.102.
Anonymous Log in
FTP users can authenticate themselves by clear text sign in protocol mechanism. If the
server allow the user to connect anonymously then the user can connect to the server
easily. Open the vsftpd.conf using the text editor and then change the no option to yes.
Disable the FTP_banner
Type nmap –sV 192.168.1.102. This will scan the ftp from the nmap. Delete the #
symbol from the ftpd_banner statement.
Switch Port for the FTP service
User can switch to any port address by typing the following command
listen_port=portnumber. User should save the file and should restart service of the ftp .
Sniffing process
Type ftp 192.168.1.102 5000 command and then input the user name anfd the
password. Use the Wireshark to capture the traffic. TCP stream is followed to clearly
visible all the credentials of the users.
Usage of the SSL certificate
A certificate is produced by typing the command openssl req -x509 -nodes -days 365 -
newkey rs. Then user should open the vsftpd.conf to alter the default settings.
Resist the Brute_Force attack using Fail2ban

9Cyber security and analysis
Execute the brute force by typing the command hydra -L user -P pass 192.168.1.102
ftp. When the user limits the brute force attack by the fail2ban then the user can utilize the
hydra command again but now he or she will get negative result.
Restrict the IP to connect the FTP
Open the hosts. Allow file from the /etc such that it can allow the valid user to
connect with the server.
Conclusion:
Thus, it can be concluded from the report that there are three particular modes by which
the attack can be done including single, incremental and wordlist. In case of Wordlist and in
case of Single attacks the hashes are computed to supply the list of passwords and the hashes
are checked form the file of password.
Execute the brute force by typing the command hydra -L user -P pass 192.168.1.102
ftp. When the user limits the brute force attack by the fail2ban then the user can utilize the
hydra command again but now he or she will get negative result.
Restrict the IP to connect the FTP
Open the hosts. Allow file from the /etc such that it can allow the valid user to
connect with the server.
Conclusion:
Thus, it can be concluded from the report that there are three particular modes by which
the attack can be done including single, incremental and wordlist. In case of Wordlist and in
case of Single attacks the hashes are computed to supply the list of passwords and the hashes
are checked form the file of password.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10Cyber security and analysis
Bibliography:
[1] B. Rodrigues, J. Paiva, V. Gomes, C. Morris and W. Calixto. Passfault: an open
source tool for measuring password complexity and strength. Orlando, Florida, Mar,
2017.
[2] E. Ates, O. Tuncer, A. Turk, V.J. Leung, J. Brandt, M. Egele and A.K Coskun.
Taxonomist: Application Detection through Rich Monitoring Data. In European
Conference on Parallel Processing (pp. 92-105). Springer, Cham.
[3] G. Avoine, X. Carpent, B. Kordy and F. Tardif. How to Handle Rainbow Tables with
External Memory. In Australasian Conference on Information Security and Privacy (pp.
306-323). Springer, Cham, 2017, July.
Bibliography:
[1] B. Rodrigues, J. Paiva, V. Gomes, C. Morris and W. Calixto. Passfault: an open
source tool for measuring password complexity and strength. Orlando, Florida, Mar,
2017.
[2] E. Ates, O. Tuncer, A. Turk, V.J. Leung, J. Brandt, M. Egele and A.K Coskun.
Taxonomist: Application Detection through Rich Monitoring Data. In European
Conference on Parallel Processing (pp. 92-105). Springer, Cham.
[3] G. Avoine, X. Carpent, B. Kordy and F. Tardif. How to Handle Rainbow Tables with
External Memory. In Australasian Conference on Information Security and Privacy (pp.
306-323). Springer, Cham, 2017, July.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





