MN623 Cybersecurity and Analytics: Penetration Testing Report
VerifiedAdded on 2023/01/19
|15
|2543
|26
Report
AI Summary
This report details a cybersecurity penetration test conducted on an e-commerce website. The report begins with an executive summary highlighting key vulnerabilities, including SQL injections and cross-site scripting, and recommending solutions such as input validation and web server updates. The introduction outlines the report's structure, which includes sections on potential threats, penetration tools and technologies (Acunetix, Aircrack-ng, Cain & Abel, Ettercap, and Metasploit), expected outcomes, practical demonstrations of tool usage, business benefits of penetration testing, and a conclusion summarizing findings. The report identifies risks like denial-of-service attacks and service degradation, along with vulnerabilities such as insufficient authentication and weak passwords. The practical demonstration section illustrates the use of the various penetration testing tools. The report concludes by emphasizing the benefits of penetration testing, such as meeting regulatory requirements, enhancing customer loyalty, and reducing downtime costs. The report recommends addressing insufficient authentication, invalid input filtering, and SQL injections to mitigate potential cyber threats.

Running head: Cyber Security and Analytics 1
Cyber Security and Analytics
[Author Name(s), First M. Last, Omit Titles and Degrees]
[Institutional Affiliation(s)]
Author Note
[Include any grant/funding information and a complete correspondence address.]
Cyber Security and Analytics
[Author Name(s), First M. Last, Omit Titles and Degrees]
[Institutional Affiliation(s)]
Author Note
[Include any grant/funding information and a complete correspondence address.]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Cyber Security and Analytics 2
1 TABLE OF CONTENTS
Executive Summary.....................................................................................................................................2
2 Introduction.........................................................................................................................................3
3 Report layout.......................................................................................................................................3
4 Potential threats and risks...................................................................................................................4
5 Penetration tools and technologies.....................................................................................................4
5.1 Acunetix.......................................................................................................................................5
5.2 Aircrack-ng...................................................................................................................................5
5.3 Cain & Abel..................................................................................................................................5
5.4 Ettercap.......................................................................................................................................5
5.5 Metasploit...................................................................................................................................6
6 Expected outcomes.............................................................................................................................6
Acunetix...................................................................................................................................................7
Aircrack-ng...............................................................................................................................................7
Cain & Abel..............................................................................................................................................7
Ettercap...................................................................................................................................................7
Metasploit...............................................................................................................................................7
7 Practical demonstration......................................................................................................................7
7.1 Acunetix.......................................................................................................................................7
7.2 Cain and Abel.............................................................................................................................10
7.3 Ettercap.....................................................................................................................................11
7.4 Metasploit.................................................................................................................................12
8 Business benefits...............................................................................................................................12
9 Conclusion and remarks....................................................................................................................13
1 TABLE OF CONTENTS
Executive Summary.....................................................................................................................................2
2 Introduction.........................................................................................................................................3
3 Report layout.......................................................................................................................................3
4 Potential threats and risks...................................................................................................................4
5 Penetration tools and technologies.....................................................................................................4
5.1 Acunetix.......................................................................................................................................5
5.2 Aircrack-ng...................................................................................................................................5
5.3 Cain & Abel..................................................................................................................................5
5.4 Ettercap.......................................................................................................................................5
5.5 Metasploit...................................................................................................................................6
6 Expected outcomes.............................................................................................................................6
Acunetix...................................................................................................................................................7
Aircrack-ng...............................................................................................................................................7
Cain & Abel..............................................................................................................................................7
Ettercap...................................................................................................................................................7
Metasploit...............................................................................................................................................7
7 Practical demonstration......................................................................................................................7
7.1 Acunetix.......................................................................................................................................7
7.2 Cain and Abel.............................................................................................................................10
7.3 Ettercap.....................................................................................................................................11
7.4 Metasploit.................................................................................................................................12
8 Business benefits...............................................................................................................................12
9 Conclusion and remarks....................................................................................................................13

Running head: Cyber Security and Analytics 3
EXECUTIVE SUMMARY
This security plan was intended for Mr. Daniel Gromer web service which hosts the e-commerce
application that isutilized to process transactions of the business. From the preliminary case study,
the following key vulnerabilities are associated with the business.
There are high vulnerabilities associated with SQL injections due to improper database setting. We
recommended a complete overhaul of the application layer of the e-commerce site
Some user validation is not done hence some cabbage finds their way into the database. It is,
therefore, recommended the site developer s have input validation at both presentation and
application layers.
Cross-site scripting is another serious vulnerability caused by weaknesses in the Apache web server
vulnerabilities. We recommended updating the web server core libraries.
EXECUTIVE SUMMARY
This security plan was intended for Mr. Daniel Gromer web service which hosts the e-commerce
application that isutilized to process transactions of the business. From the preliminary case study,
the following key vulnerabilities are associated with the business.
There are high vulnerabilities associated with SQL injections due to improper database setting. We
recommended a complete overhaul of the application layer of the e-commerce site
Some user validation is not done hence some cabbage finds their way into the database. It is,
therefore, recommended the site developer s have input validation at both presentation and
application layers.
Cross-site scripting is another serious vulnerability caused by weaknesses in the Apache web server
vulnerabilities. We recommended updating the web server core libraries.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Cyber Security and Analytics 4
2 INTRODUCTION
This report provides the plan of action that will be used to conduct a full cyber security penetration
testing for Mr. Daniel Gromer who runs a series of e-commerce stores that expands the cities of Sydney
and Melbourne [1]. This business has a lot of competition hence requires a unique approach to ensure
the customer finds the site not only convenient but also secure to shop in. The plan is organized in a
different section with each section focusing on a given area. The following section discusses the layout
of the report [2].
3 REPORT LAYOUT
The report is divided into sections with each section focusing on a given subset of the penetration
testing subset. First sections discuss the potential risks that the e-commerce faces in relation to the
cybersecurity threats and vulnerabilities within the e-commerce realm. This will give the pentest
activities more focus on trying to find the risks identified [3]. The second section discusses the various
points tools and procedure that will be used methodologically to conduct the cybersecurity pentest to
ensure the risks and vulnerabilities are identified. The third section enumerates the expected outcomes
from the pentest conducted on the e-commerce site. This will aid in gauging the success of the pentest.
The resources required to conduct the pentest will also be enumerated in this section to list all the tools
and methodologies that will be used to conduct the pentest [4]. The next section will provide a practical
demonstration of the various pentest tools to ensure the effectiveness of the results obtained. This will
enable the store owner to appreciate the pentest procedure. Lastly, the business benefits and
conclusion will be given to provide a summary of the various vulnerabilities identified. The writing style
for the report shall be IEEE.
4 POTENTIAL THREATS AND RISKS
Conducting penetration testing comes with its inherent risks that must be identified and mitigated. The
following section identifies some of the risks and potential remedies. First, denial of service poses a
2 INTRODUCTION
This report provides the plan of action that will be used to conduct a full cyber security penetration
testing for Mr. Daniel Gromer who runs a series of e-commerce stores that expands the cities of Sydney
and Melbourne [1]. This business has a lot of competition hence requires a unique approach to ensure
the customer finds the site not only convenient but also secure to shop in. The plan is organized in a
different section with each section focusing on a given area. The following section discusses the layout
of the report [2].
3 REPORT LAYOUT
The report is divided into sections with each section focusing on a given subset of the penetration
testing subset. First sections discuss the potential risks that the e-commerce faces in relation to the
cybersecurity threats and vulnerabilities within the e-commerce realm. This will give the pentest
activities more focus on trying to find the risks identified [3]. The second section discusses the various
points tools and procedure that will be used methodologically to conduct the cybersecurity pentest to
ensure the risks and vulnerabilities are identified. The third section enumerates the expected outcomes
from the pentest conducted on the e-commerce site. This will aid in gauging the success of the pentest.
The resources required to conduct the pentest will also be enumerated in this section to list all the tools
and methodologies that will be used to conduct the pentest [4]. The next section will provide a practical
demonstration of the various pentest tools to ensure the effectiveness of the results obtained. This will
enable the store owner to appreciate the pentest procedure. Lastly, the business benefits and
conclusion will be given to provide a summary of the various vulnerabilities identified. The writing style
for the report shall be IEEE.
4 POTENTIAL THREATS AND RISKS
Conducting penetration testing comes with its inherent risks that must be identified and mitigated. The
following section identifies some of the risks and potential remedies. First, denial of service poses a
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Running head: Cyber Security and Analytics 5
serious threat to the success of the pentest as such attacks would deny even the pentest tools ability to
scan the system and applications to identify some of the vulnerabilities [5]. It is therefore vital for the
servers to be configured with redundancies to ensure the system won’t be affected by a potential denial
of service threats [6].
Second, the business risk having a general degradation of service during the pentest and most of the
penetration testing and vulnerabilities scanners are system intensive in terms of resource utilization. The
amount of bandwidth estimated to be used is quite high hence will affect the performance of other
business operations [7]. The remedy for this is to perform testing on business-critical applications during
the offpeak hours to ensure no degradation of service to customers. Testing can again be conducted in
phases by first doing the UAT and then focusing on the production environment [8].
The following table list the vulnerabilities the business currently face.
Risk Severity
Insufficient Authentication High
Improper Input Filtration High
Cross-site scripting High
SSL weak ciphers Medium
Deprecated protocols Medium
Weak password High
SQL injections High
5 PENETRATION TOOLS AND TECHNOLOGIES
This section describes the various tools that will be used to conduct the pentest procedures The
rationale for choosing the tool is also explained in these sections.
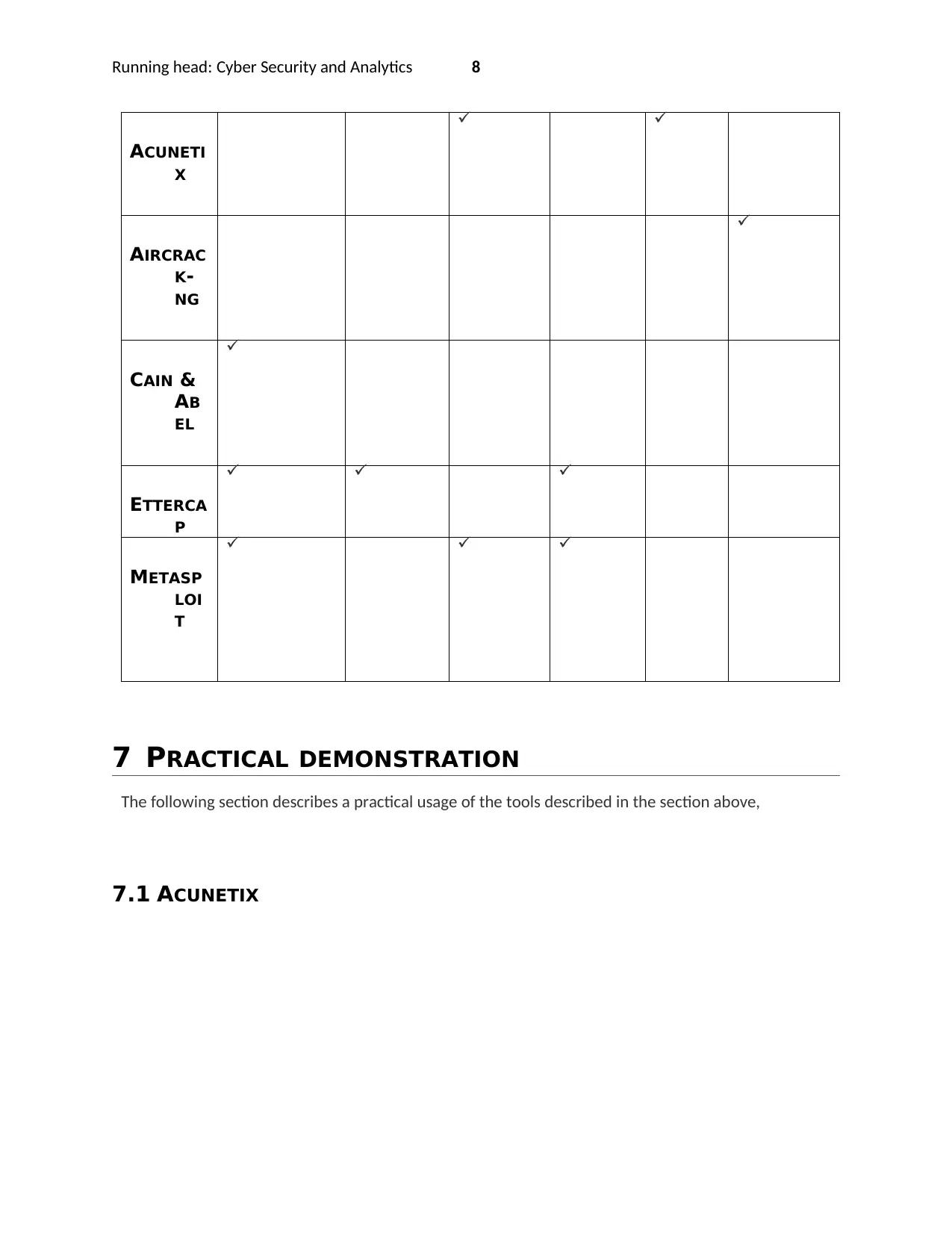
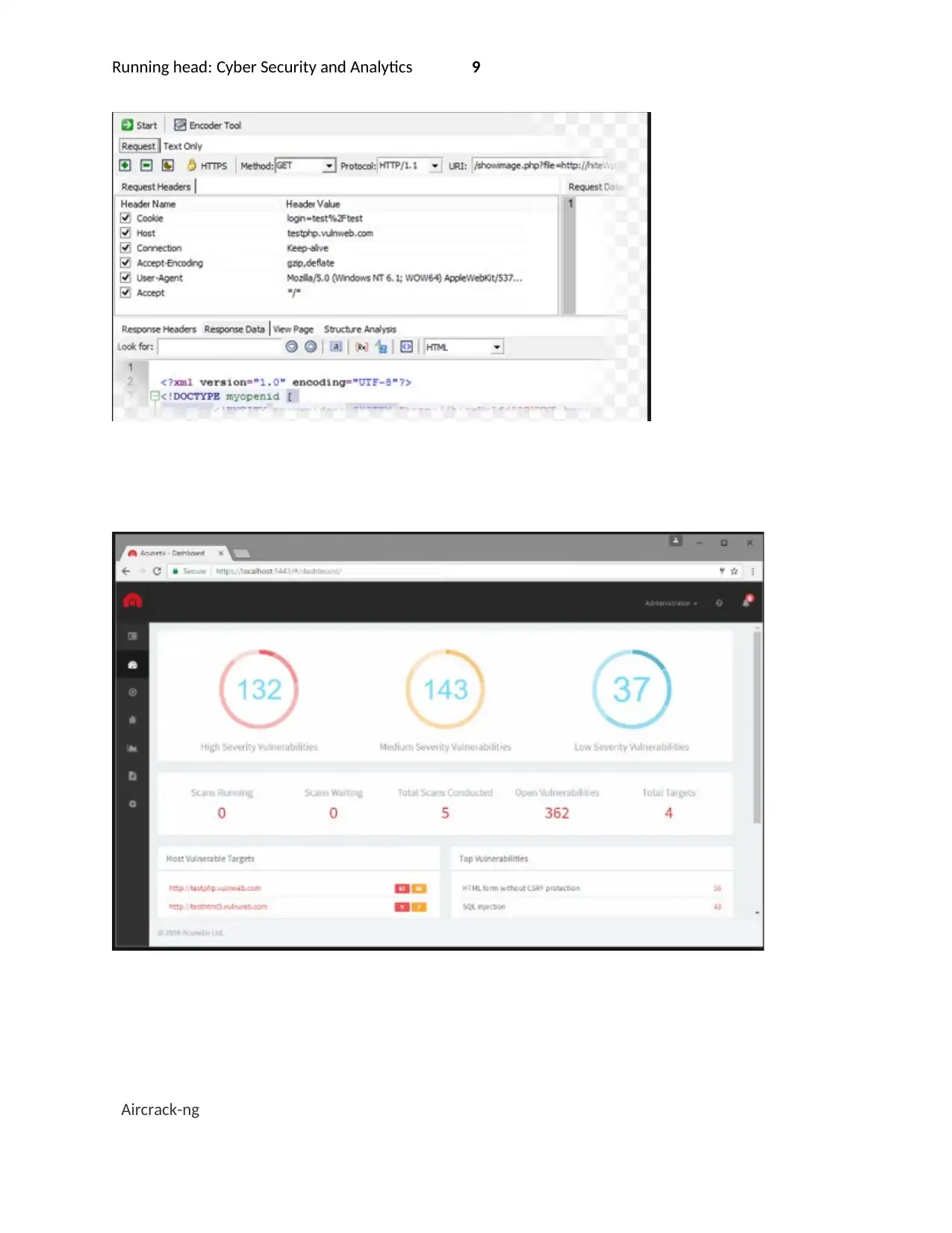
5.1 ACUNETIX
This is a web security tool that will allow the pentest procedures to find various attack vectors that are
associated with the web applications including the XSS and SQL injections. The tools are chosen due to
its versatility and ability to run only on demand and can be scheduled to run on many web applications
serious threat to the success of the pentest as such attacks would deny even the pentest tools ability to
scan the system and applications to identify some of the vulnerabilities [5]. It is therefore vital for the
servers to be configured with redundancies to ensure the system won’t be affected by a potential denial
of service threats [6].
Second, the business risk having a general degradation of service during the pentest and most of the
penetration testing and vulnerabilities scanners are system intensive in terms of resource utilization. The
amount of bandwidth estimated to be used is quite high hence will affect the performance of other
business operations [7]. The remedy for this is to perform testing on business-critical applications during
the offpeak hours to ensure no degradation of service to customers. Testing can again be conducted in
phases by first doing the UAT and then focusing on the production environment [8].
The following table list the vulnerabilities the business currently face.
Risk Severity
Insufficient Authentication High
Improper Input Filtration High
Cross-site scripting High
SSL weak ciphers Medium
Deprecated protocols Medium
Weak password High
SQL injections High
5 PENETRATION TOOLS AND TECHNOLOGIES
This section describes the various tools that will be used to conduct the pentest procedures The
rationale for choosing the tool is also explained in these sections.
5.1 ACUNETIX
This is a web security tool that will allow the pentest procedures to find various attack vectors that are
associated with the web applications including the XSS and SQL injections. The tools are chosen due to
its versatility and ability to run only on demand and can be scheduled to run on many web applications

Running head: Cyber Security and Analytics 6
efficiently at a reasonable cost. The reporting engine of the tool is also intuitive hence will be key in
providing the feedback requires [9]
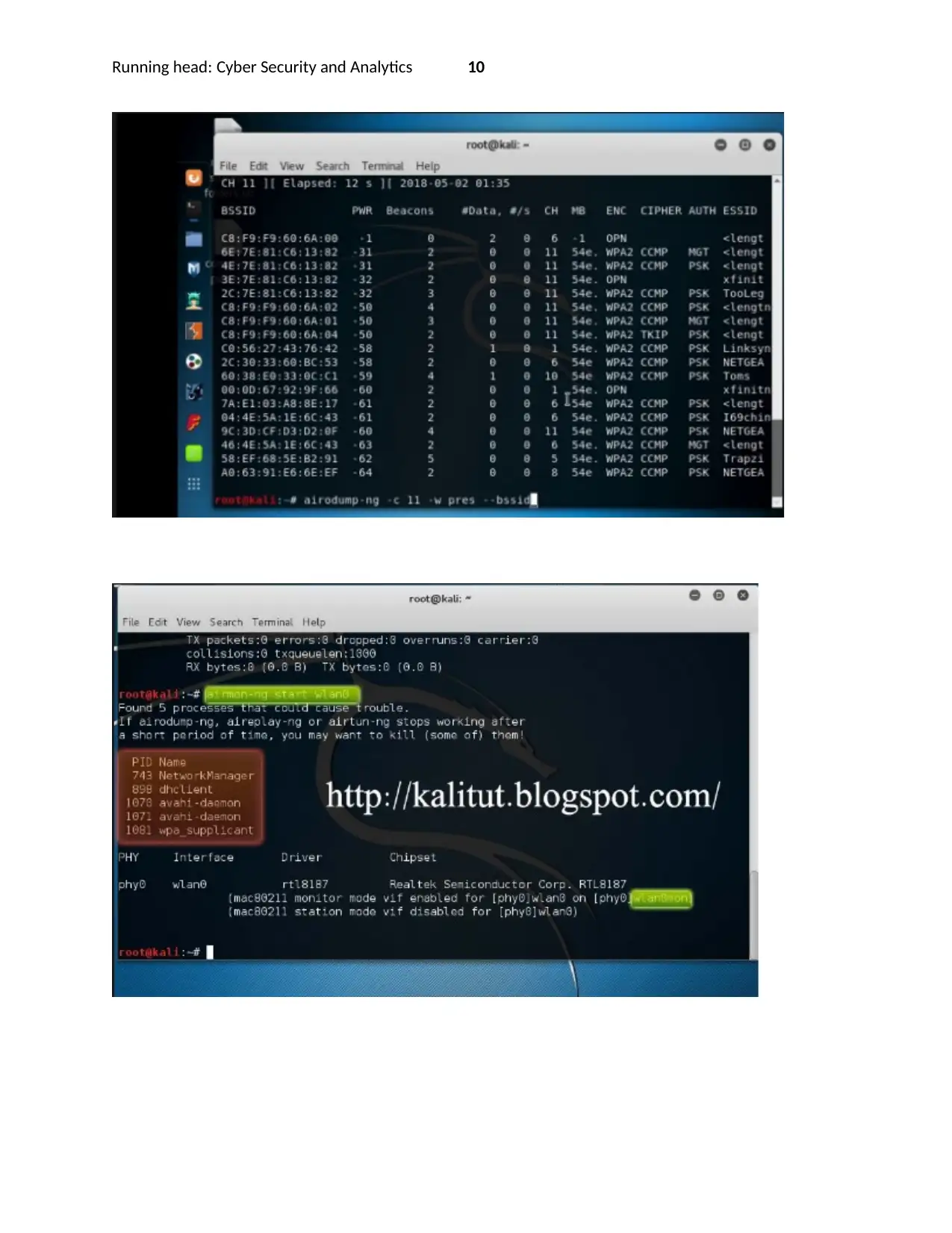
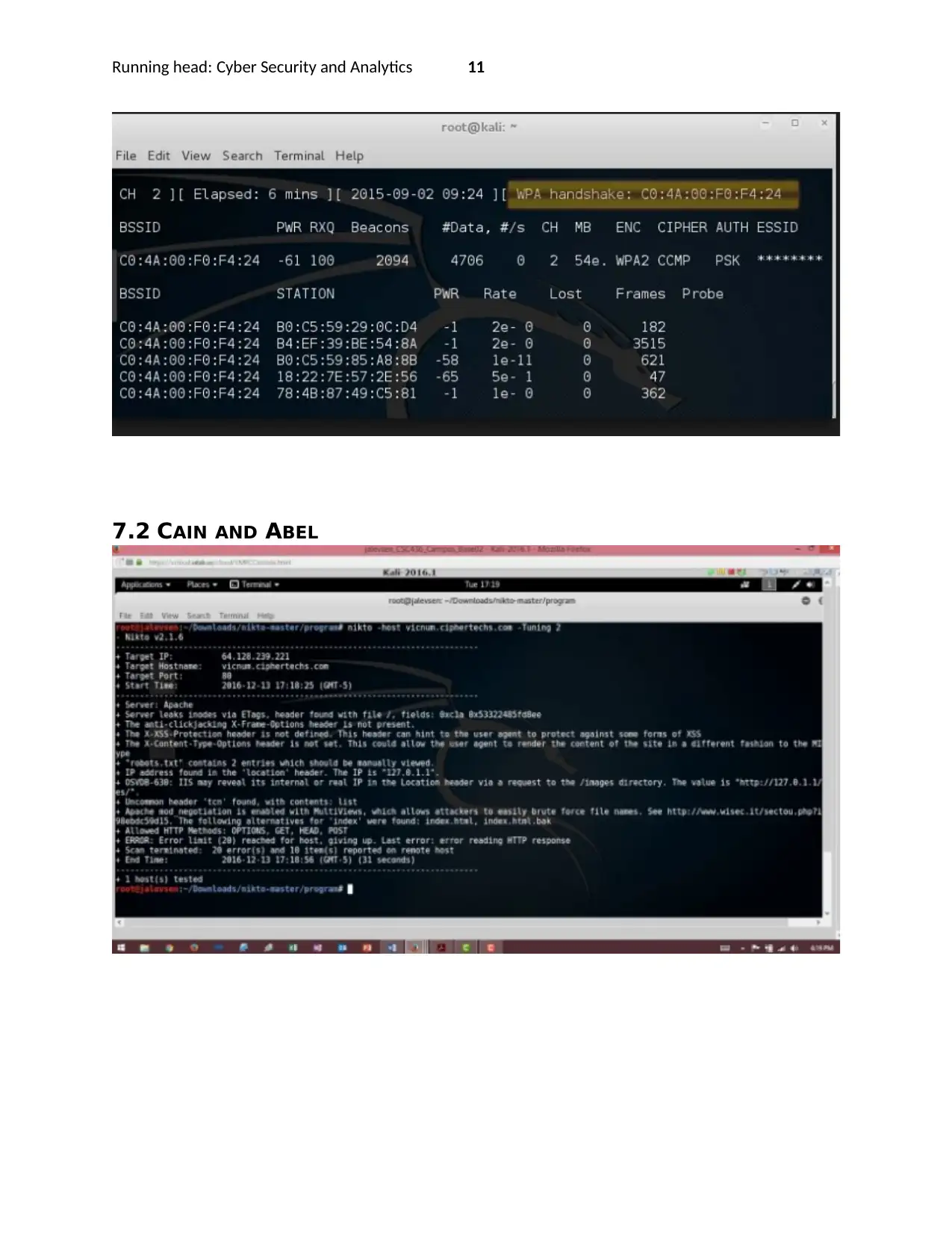
5.2 AIRCRACK-NG
This tool is critical for scanning the vulnerabilities within the wifi networks that the company uses to
enable access to the internet by the employees and other guests. It will be used to test the crackability
of the various wifi passwords, checking the wifi network interface vulnerabilities against know
vulnerabilities. In particular, Aircrack-ng is just a suite for an array of software used for vulnerabilities
testing. Key among them includes the Airodump-ng, Airplay-ng, Aircrack-ng, Airedecap-ng [10].
5.3 CAIN & ABEL
This tool has a set of pentest tools that will aid the penetration to be conducted. It will be used to
attempt to test the security of the transport layer security, password guessing, and the MAC address
spoofing. This will be a key tool for the team [11].
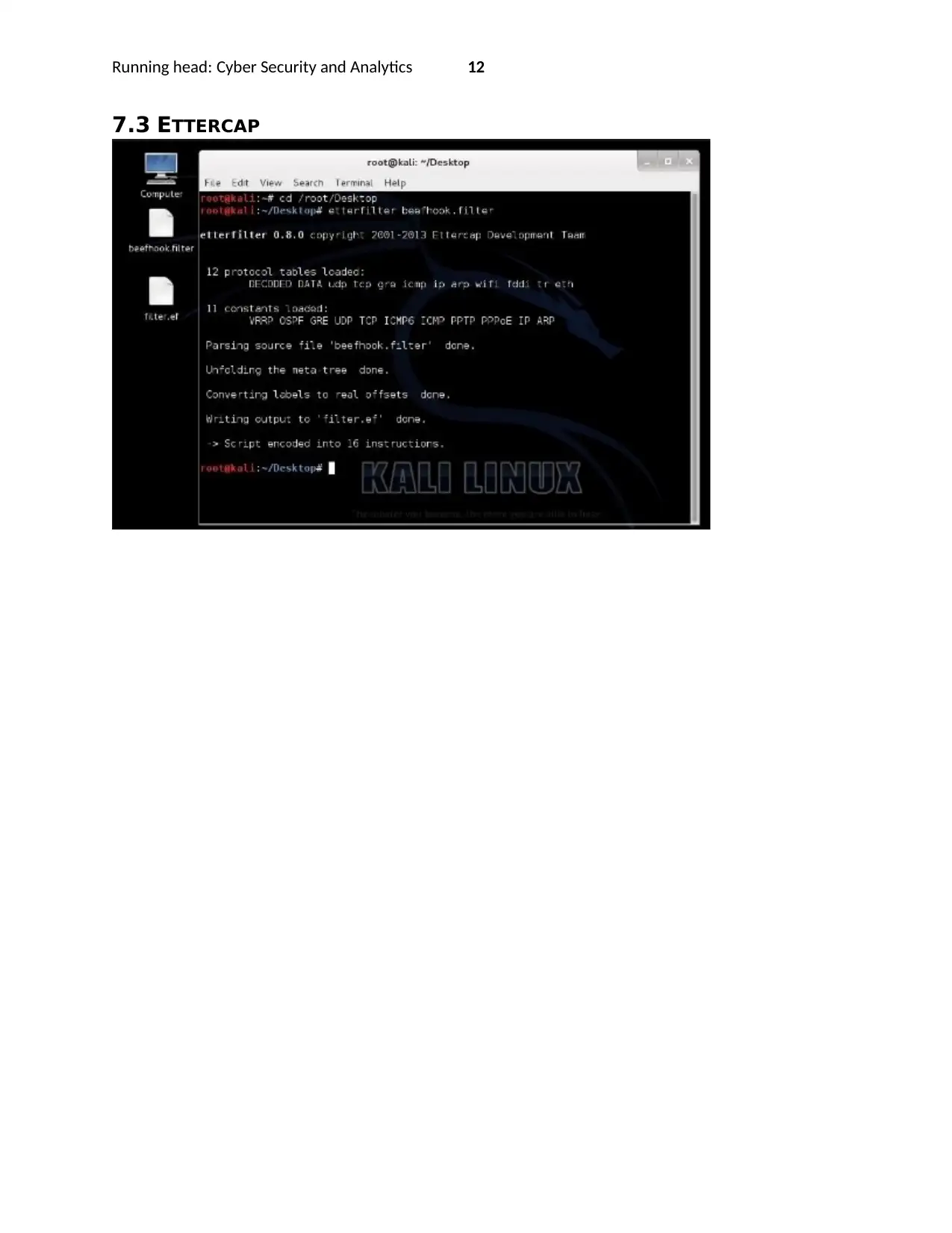
5.4 ETTERCAP
Ettercap is a tool used to simulate Man in the middle attacks as it will be used to catch live packets and
attempts to get the data on transit [12]. This is particularly important because most of the adversaries of
an e-commerce site are mainly Man in the middle attacks who sniff packets to gain access to critical
information such as credit card details of the customers [13].
5.5 METASPLOIT
The Metasploit framework which comes inbuilt into the Kali Linux security OS shall be key in conducting
a vulnerability assessment of the web server hosting the e-commerce application, conduct the
vulnerabilities of intrusion detection systems [14].
efficiently at a reasonable cost. The reporting engine of the tool is also intuitive hence will be key in
providing the feedback requires [9]
5.2 AIRCRACK-NG
This tool is critical for scanning the vulnerabilities within the wifi networks that the company uses to
enable access to the internet by the employees and other guests. It will be used to test the crackability
of the various wifi passwords, checking the wifi network interface vulnerabilities against know
vulnerabilities. In particular, Aircrack-ng is just a suite for an array of software used for vulnerabilities
testing. Key among them includes the Airodump-ng, Airplay-ng, Aircrack-ng, Airedecap-ng [10].
5.3 CAIN & ABEL
This tool has a set of pentest tools that will aid the penetration to be conducted. It will be used to
attempt to test the security of the transport layer security, password guessing, and the MAC address
spoofing. This will be a key tool for the team [11].
5.4 ETTERCAP
Ettercap is a tool used to simulate Man in the middle attacks as it will be used to catch live packets and
attempts to get the data on transit [12]. This is particularly important because most of the adversaries of
an e-commerce site are mainly Man in the middle attacks who sniff packets to gain access to critical
information such as credit card details of the customers [13].
5.5 METASPLOIT
The Metasploit framework which comes inbuilt into the Kali Linux security OS shall be key in conducting
a vulnerability assessment of the web server hosting the e-commerce application, conduct the
vulnerabilities of intrusion detection systems [14].
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Running head: Cyber Security and Analytics 7
6 EXPECTED OUTCOMES
The goals for conducting this pentest includes
I. To secure the client’s data
II. To identify and document security vulnerabilities in the client’s e-commerce applications
III. To identify loopholes in the current system
IV. To guide the client in implementing an effective cybersecurity strategy for the company.
The expected outcomes for the test include;
I. Identification of Key system and application risks
II. Security vulnerabilities in the current e-commerce site
III. Identify the potential threats the company faces due to its current systems
Resources required
The following are key resources that shall be used by the team.
I. Laptop with 8GB RAM
II. Kali Linux 64bit ISO image
III. VLAN for pentest
IV. Word processor for report
For each of the tool, the following vulnerabilities shall be tested
Insufficient
Authentication
Improper
Input
Filtration
Cross-site
scripting
SSL weak
ciphers
SQL
injection
Deprecated
protocols
6 EXPECTED OUTCOMES
The goals for conducting this pentest includes
I. To secure the client’s data
II. To identify and document security vulnerabilities in the client’s e-commerce applications
III. To identify loopholes in the current system
IV. To guide the client in implementing an effective cybersecurity strategy for the company.
The expected outcomes for the test include;
I. Identification of Key system and application risks
II. Security vulnerabilities in the current e-commerce site
III. Identify the potential threats the company faces due to its current systems
Resources required
The following are key resources that shall be used by the team.
I. Laptop with 8GB RAM
II. Kali Linux 64bit ISO image
III. VLAN for pentest
IV. Word processor for report
For each of the tool, the following vulnerabilities shall be tested
Insufficient
Authentication
Improper
Input
Filtration
Cross-site
scripting
SSL weak
ciphers
SQL
injection
Deprecated
protocols
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head: Cyber Security and Analytics 8
ACUNETI
X
AIRCRAC
K-
NG
CAIN &
AB
EL
ETTERCA
P
METASP
LOI
T
7 PRACTICAL DEMONSTRATION
The following section describes a practical usage of the tools described in the section above,
7.1 ACUNETIX
ACUNETI
X
AIRCRAC
K-
NG
CAIN &
AB
EL
ETTERCA
P
METASP
LOI
T
7 PRACTICAL DEMONSTRATION
The following section describes a practical usage of the tools described in the section above,
7.1 ACUNETIX
Running head: Cyber Security and Analytics 9
Aircrack-ng
Aircrack-ng
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Running head: Cyber Security and Analytics 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Running head: Cyber Security and Analytics 11
7.2 CAIN AND ABEL
7.2 CAIN AND ABEL
Running head: Cyber Security and Analytics 12
7.3 ETTERCAP
7.3 ETTERCAP
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.