Cyber Security and Traffic
VerifiedAdded on 2023/02/01
|18
|4523
|64
AI Summary
This study material covers the topics of Vignere cipher programming algorithm, policies for securing data, deletion and recovery, and the current state of encrypted emails. It provides expert insights and analysis on cyber security and traffic.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CYBER SECURITY AND TRAFFIC
Cyber Security and Traffic
Name of the Student
Name of the University
Author Note
Cyber Security and Traffic
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1CYBER SECURITY AND TRAFFIC
Question 1: Vignere cipher programming algorithm
The program written here summarizes the Vignere cypher algorithm. The Vignere cypher is a
polyalphabetic cypher which is used to encrypt messages and then decrypt it using a single
key. It is a type of symmetric algorithm as it uses the same key for both encryption and
decryption (Radwan, AbdElHaleem and Abd-El-Hafiz 2016). The program written is very
efficient as it uses the algebraic equivalent of the vignere cypher algorithm to both encrypt
and decrypt the data. The program written does not use any complex functions and is
relatively easy to understand. The program uses basic numerical calculations to implement
the algorithm. The Vignere cypher is quite a robust algorithm and has fewer weakness. The
algorithm due to its polyalphabetic substitution is quite difficult to break in and cannot be
hacked without knowing the secret key (Ardy et al. 2017). This cypher is especially suitable
for small text messages as theoretically it becomes impossible to break this encryption if the
message length and the key length is same. For example, in Vignere cypher due to the
polyalphabetic substitution and the interwoven Caesar cyphers, if a message of length 10
characters is encrypted using a randomly generated key of 10 characters it becomes
impossible to break this message without the key (Oktaviana and Siahaan 2016).
The functioning of the Vignere cypher is quite simple. The cypher uses a table to
encrypt and decrypt its data. The table is given below:
Question 1: Vignere cipher programming algorithm
The program written here summarizes the Vignere cypher algorithm. The Vignere cypher is a
polyalphabetic cypher which is used to encrypt messages and then decrypt it using a single
key. It is a type of symmetric algorithm as it uses the same key for both encryption and
decryption (Radwan, AbdElHaleem and Abd-El-Hafiz 2016). The program written is very
efficient as it uses the algebraic equivalent of the vignere cypher algorithm to both encrypt
and decrypt the data. The program written does not use any complex functions and is
relatively easy to understand. The program uses basic numerical calculations to implement
the algorithm. The Vignere cypher is quite a robust algorithm and has fewer weakness. The
algorithm due to its polyalphabetic substitution is quite difficult to break in and cannot be
hacked without knowing the secret key (Ardy et al. 2017). This cypher is especially suitable
for small text messages as theoretically it becomes impossible to break this encryption if the
message length and the key length is same. For example, in Vignere cypher due to the
polyalphabetic substitution and the interwoven Caesar cyphers, if a message of length 10
characters is encrypted using a randomly generated key of 10 characters it becomes
impossible to break this message without the key (Oktaviana and Siahaan 2016).
The functioning of the Vignere cypher is quite simple. The cypher uses a table to
encrypt and decrypt its data. The table is given below:

2CYBER SECURITY AND TRAFFIC
Figure 1: Vignere cipher polyalphabetic cipher
For example, let us assume the message as HELLO. Let the key be ASDAS. The algorithm
checks the first letter of the message with the first letter of the key and selects the letter than
coincides both rows in the table. This letter is H. So following this procedure if we encrypt
the data the message becomes: HWOLG. This is algebraically given in the program as Ei =
(Pi + Ki) mod 26, where P is plain text and K is key. The same process is repeated to decrypt
the message using the Pi = (Ei – Ki + 26) mod 26 expression, where E is the encrypted
message and K is the key. The program utilises both these expressions to implement the
algorithm.
This algorithm is best suitable to be used between two persons during communication
because between two people if the key is kept private and secure, it will be practically
impossible for an outsider to decode their messages without the secret key (Chou, Bloch and
Figure 1: Vignere cipher polyalphabetic cipher
For example, let us assume the message as HELLO. Let the key be ASDAS. The algorithm
checks the first letter of the message with the first letter of the key and selects the letter than
coincides both rows in the table. This letter is H. So following this procedure if we encrypt
the data the message becomes: HWOLG. This is algebraically given in the program as Ei =
(Pi + Ki) mod 26, where P is plain text and K is key. The same process is repeated to decrypt
the message using the Pi = (Ei – Ki + 26) mod 26 expression, where E is the encrypted
message and K is the key. The program utilises both these expressions to implement the
algorithm.
This algorithm is best suitable to be used between two persons during communication
because between two people if the key is kept private and secure, it will be practically
impossible for an outsider to decode their messages without the secret key (Chou, Bloch and

3CYBER SECURITY AND TRAFFIC
Abbe 2015). This helps in proper encrypting of the communication line and providing better
security.
Question 2: Policies for securing data, deletion and recovery
There exists various set of policies and procedures for securing, deleting and
recovering data. These policies vary as there are different types of operating systems
(Tanenbaum and Bos 2015). The security policies of operating systems outline processes of
ensuring the OS meets the required integrity and confidentiality levels as well as availability.
The OS security system provide protection from threats like virus, worm, malwares,
ransomware attacks as well as backdoor intrusions and others (Nourian and Madnick 2018).
Such protection is made possible through the security policies employed by operating
systems to cover preventive techniques and measures so as to safeguard a particular operating
system, the associated data that can be edited, stolen or destroyed as also the network that the
OS is connected to.
These security policies cover broad areas in securing OSes by protecting from attacks
and threats in several ways (Dautenhahn et al. 2015). These can be:
To ensure that systems are kept updated with the latest patches and hostfixes.
Installation of antivirus software and updating the definitions.
Installation of firewall applications and making sure that these are configured
appropriately for monitoring incoming as well as outgoing traffic.
Implementation of procedures for managing and securing accounts and
privileges of users.
For ascertaining that the right policies and procedures get defined one first requires to assess
the hardware, systems, assets and data that play a critical role for the business (Massa, Tucci
Abbe 2015). This helps in proper encrypting of the communication line and providing better
security.
Question 2: Policies for securing data, deletion and recovery
There exists various set of policies and procedures for securing, deleting and
recovering data. These policies vary as there are different types of operating systems
(Tanenbaum and Bos 2015). The security policies of operating systems outline processes of
ensuring the OS meets the required integrity and confidentiality levels as well as availability.
The OS security system provide protection from threats like virus, worm, malwares,
ransomware attacks as well as backdoor intrusions and others (Nourian and Madnick 2018).
Such protection is made possible through the security policies employed by operating
systems to cover preventive techniques and measures so as to safeguard a particular operating
system, the associated data that can be edited, stolen or destroyed as also the network that the
OS is connected to.
These security policies cover broad areas in securing OSes by protecting from attacks
and threats in several ways (Dautenhahn et al. 2015). These can be:
To ensure that systems are kept updated with the latest patches and hostfixes.
Installation of antivirus software and updating the definitions.
Installation of firewall applications and making sure that these are configured
appropriately for monitoring incoming as well as outgoing traffic.
Implementation of procedures for managing and securing accounts and
privileges of users.
For ascertaining that the right policies and procedures get defined one first requires to assess
the hardware, systems, assets and data that play a critical role for the business (Massa, Tucci
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4CYBER SECURITY AND TRAFFIC
and Afuah 2017). Having done that, policies can now be built around the items for securing
and safeguarding them.
These procedures and policies for securing operating systems are:
1. Acceptable Use Policy or AUP
2. Access Control Policy or ACP
3. Change Management Policy
4. Information Security Policy
5. Incident Response or IR
AUP: AUP (Acceptable Use Policy) refers to the standard document meant for onboarding
that must be signed by the employees before the digital resources of the organization are
made available to them (Caldwell and Caldwell 2016). Such policies lay down the acceptable
practises and outlines restrictions and practises that employees need to follow to access
network organizations. The contents of AUP vary based on business to business (Rooney and
Foley 2018). Irrespective of the document contents, it needs to get reviewed by security, IT,
cyber, HR and legal departments to implement necessary changes.
ACP: ACP (Access Control Policy) is the policy document that mentions access limitations
of the employees in businesses (Rezaeibagha and Mu 2016). These can be based on access
control standards, password complexity rules, password change policies, network access
control for users, monitoring of network access by users, standard of security in workplaces,
standard for removing equipment of organizations.
Change Management Policy: Outlining of proper procedures to make changes to the network,
IT equipment, operational procedures, security and software is given in this policy (Braun
2015). The intention of change management policy is about making sure that organizations
get the ability to effectively track how changes to infrastructure occur and that the least
and Afuah 2017). Having done that, policies can now be built around the items for securing
and safeguarding them.
These procedures and policies for securing operating systems are:
1. Acceptable Use Policy or AUP
2. Access Control Policy or ACP
3. Change Management Policy
4. Information Security Policy
5. Incident Response or IR
AUP: AUP (Acceptable Use Policy) refers to the standard document meant for onboarding
that must be signed by the employees before the digital resources of the organization are
made available to them (Caldwell and Caldwell 2016). Such policies lay down the acceptable
practises and outlines restrictions and practises that employees need to follow to access
network organizations. The contents of AUP vary based on business to business (Rooney and
Foley 2018). Irrespective of the document contents, it needs to get reviewed by security, IT,
cyber, HR and legal departments to implement necessary changes.
ACP: ACP (Access Control Policy) is the policy document that mentions access limitations
of the employees in businesses (Rezaeibagha and Mu 2016). These can be based on access
control standards, password complexity rules, password change policies, network access
control for users, monitoring of network access by users, standard of security in workplaces,
standard for removing equipment of organizations.
Change Management Policy: Outlining of proper procedures to make changes to the network,
IT equipment, operational procedures, security and software is given in this policy (Braun
2015). The intention of change management policy is about making sure that organizations
get the ability to effectively track how changes to infrastructure occur and that the least

5CYBER SECURITY AND TRAFFIC
amount of disruptions take place in applying the changes more so if they directly affect the
clients and customers (Gomber et al. 2018). A big role is played by the management in
executing changes based on this policy. The management are the ones making the final call
on if changes need to be implemented or not. They need to be more aware and able to
understand the request for changes within the business.
Information Security Policy: The key importance of this policy is about informing users
about guidelines on how to handle confidential information and on how employees can be
held accountable for breaching adherence of the policy (Safa, Von Solms and Furnell 2016).
Policies like this can be broken into subcategories for covering including how employees use
IT, network and Internet resources of the business.
Incident Response Policy: IR (Incident Response) policy presents the response procedures for
tackling respective incidents (Raithel et al. 2017). These response procedures include steps
required for recovering from incidents like network and power outages, loss of data,
disruption in regular business operations and client or employee specific issues. This way,
recovery time about incidents can be reduced with lower cost of impact.
Deletion of files
It is the process by which files are removed from the file system of computers (Yuan
et al. 2016). The usual intentions behind deleting files can be making more disk space
available, removal of redundant and obsolete information for avoiding confusions, sensitive
information that is to be made unavailable from other users.
Every operating system offers commands usable for deleting files. These can be – rm
for UNIX, era in CP/M as well as DR-DOS, del/erase in MS-DOS, PC DOS, DR-DOS,
Microsoft Windows, among others (Silberschatz, Gagne and Galvin 2018). File managers
provide easier ways to delete files like in the GUI (Graphic User Interface) of Windows
amount of disruptions take place in applying the changes more so if they directly affect the
clients and customers (Gomber et al. 2018). A big role is played by the management in
executing changes based on this policy. The management are the ones making the final call
on if changes need to be implemented or not. They need to be more aware and able to
understand the request for changes within the business.
Information Security Policy: The key importance of this policy is about informing users
about guidelines on how to handle confidential information and on how employees can be
held accountable for breaching adherence of the policy (Safa, Von Solms and Furnell 2016).
Policies like this can be broken into subcategories for covering including how employees use
IT, network and Internet resources of the business.
Incident Response Policy: IR (Incident Response) policy presents the response procedures for
tackling respective incidents (Raithel et al. 2017). These response procedures include steps
required for recovering from incidents like network and power outages, loss of data,
disruption in regular business operations and client or employee specific issues. This way,
recovery time about incidents can be reduced with lower cost of impact.
Deletion of files
It is the process by which files are removed from the file system of computers (Yuan
et al. 2016). The usual intentions behind deleting files can be making more disk space
available, removal of redundant and obsolete information for avoiding confusions, sensitive
information that is to be made unavailable from other users.
Every operating system offers commands usable for deleting files. These can be – rm
for UNIX, era in CP/M as well as DR-DOS, del/erase in MS-DOS, PC DOS, DR-DOS,
Microsoft Windows, among others (Silberschatz, Gagne and Galvin 2018). File managers
provide easier ways to delete files like in the GUI (Graphic User Interface) of Windows

6CYBER SECURITY AND TRAFFIC
based operating systems such operations are grossly different (Friese 2016). After selecting
files with mouse clicks, once the file gets selected, it can be deleted using the delete button
from the keyboard. However, this only transfers the file to the recycle bin from where the file
can be deleted again to remove it permanently or rather removing all links to the data
(Gutmann and Warner 2019). Alternately users can skip sending files to recycle bin before
permanent removal by using shift + delete.
The major concern regarding removal of sensitive data is that the removal process is
not always an easy task. In most cases, the file systems only eliminates the links to the
instead of removing the actual data, thus making the confidential information recoverable by
other interested parties. Even processes like formatting will not guarantee these sensitive
information to be completely unrecoverable (Teing et al. 2017). Specialized applications
already exists that can overwrite data, some modern drives include secure erase commands in
their firmware.
When files are deleted from mechanical drives, the disk area occupied by the files are
marked by the OS as free but data is left untouched unless overwritten by a new file.
Recovery applications thus tap in to these files that still exists but marked free and are yet to
get overwritten. In SSDs (Solid State Drives) when a file is deleted, the OS instructs the
TRIM command which tells the SSD that the files are no more required following which the
SSD places the data on special cells to be purged afterwards. Thus, these data can be
recovered by specialized software by accessing the purged cells. EaseUS Data Recovery
Wizard and Recuva are two software applications that are widely used in recovering files by
both rgular users as well as businesses.
based operating systems such operations are grossly different (Friese 2016). After selecting
files with mouse clicks, once the file gets selected, it can be deleted using the delete button
from the keyboard. However, this only transfers the file to the recycle bin from where the file
can be deleted again to remove it permanently or rather removing all links to the data
(Gutmann and Warner 2019). Alternately users can skip sending files to recycle bin before
permanent removal by using shift + delete.
The major concern regarding removal of sensitive data is that the removal process is
not always an easy task. In most cases, the file systems only eliminates the links to the
instead of removing the actual data, thus making the confidential information recoverable by
other interested parties. Even processes like formatting will not guarantee these sensitive
information to be completely unrecoverable (Teing et al. 2017). Specialized applications
already exists that can overwrite data, some modern drives include secure erase commands in
their firmware.
When files are deleted from mechanical drives, the disk area occupied by the files are
marked by the OS as free but data is left untouched unless overwritten by a new file.
Recovery applications thus tap in to these files that still exists but marked free and are yet to
get overwritten. In SSDs (Solid State Drives) when a file is deleted, the OS instructs the
TRIM command which tells the SSD that the files are no more required following which the
SSD places the data on special cells to be purged afterwards. Thus, these data can be
recovered by specialized software by accessing the purged cells. EaseUS Data Recovery
Wizard and Recuva are two software applications that are widely used in recovering files by
both rgular users as well as businesses.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY AND TRAFFIC
Question 3: Current state of encrypted e-mails
E-mails or electronic mails are encrypted so that the contents can be kept hidden from
internet service providers, cybercriminals as well as intelligence systems that are willing to
access this data through hacked routers, email servers as well as recording messages during
transmission. Ever since the whistleblowing made by Edward Snowden coupled with the rise
in email servers getting hacked over the recent years, email contents getting stolen from
compromised networks are appearing to be a realistic threat and can potentially have wide
scale implications for the concerned clients an businesses as well as the average end user.
This is because the data theft can involve stealing of passwords, licenses, banking codes, and
user id among others. These are sensitive user data which if gets stolen, can perform
malicious activity like completing transactions without the consent of the user and thus
resulting to loss of money.
The most common way of claiming victims in such attacks is by luring users to open
unsolicited and infected emails which is why it is essential no to open emails from untrusted
sources.
When network traffic gets intercepted, information can definitely get extracted from
emails. One prime example for this can be from the recent network interception Dell where
the company noticed unauthorized activity in their network and it was identified that hackers
tried cracking hashed passwords to gain access to customer data (Englehardt, Han and
Narayanan 2018). Although Dell could not say for sure the success rate of these attacks, the
very possibility of such a large enterprise with comprehensive multi-layered security getting
targeted, makes it an increasingly alarming concern for the everyday users. The attack
involved attempts to access customer records that ranged from customer names, email
addresses and hashed passwords. The customer updates did not mention of anything getting
compromised and Dell later clarified that despite some records possibly got removed from
Question 3: Current state of encrypted e-mails
E-mails or electronic mails are encrypted so that the contents can be kept hidden from
internet service providers, cybercriminals as well as intelligence systems that are willing to
access this data through hacked routers, email servers as well as recording messages during
transmission. Ever since the whistleblowing made by Edward Snowden coupled with the rise
in email servers getting hacked over the recent years, email contents getting stolen from
compromised networks are appearing to be a realistic threat and can potentially have wide
scale implications for the concerned clients an businesses as well as the average end user.
This is because the data theft can involve stealing of passwords, licenses, banking codes, and
user id among others. These are sensitive user data which if gets stolen, can perform
malicious activity like completing transactions without the consent of the user and thus
resulting to loss of money.
The most common way of claiming victims in such attacks is by luring users to open
unsolicited and infected emails which is why it is essential no to open emails from untrusted
sources.
When network traffic gets intercepted, information can definitely get extracted from
emails. One prime example for this can be from the recent network interception Dell where
the company noticed unauthorized activity in their network and it was identified that hackers
tried cracking hashed passwords to gain access to customer data (Englehardt, Han and
Narayanan 2018). Although Dell could not say for sure the success rate of these attacks, the
very possibility of such a large enterprise with comprehensive multi-layered security getting
targeted, makes it an increasingly alarming concern for the everyday users. The attack
involved attempts to access customer records that ranged from customer names, email
addresses and hashed passwords. The customer updates did not mention of anything getting
compromised and Dell later clarified that despite some records possibly got removed from

8CYBER SECURITY AND TRAFFIC
the network of Dell, there was no conclusive proof which suggested that any information got
extracted from the these stolen emails. After the incident Dell insists that hashed passwords
limit potential exposure to attackers. To prevent similar attacks from taking place in future,
the company conducted a forced reset of all passwords by hiring digital forensics teams and
advising customers not to use similar passwords.
As noticeable from the above situation it is clear that hashed passwords help prevent
sensitive email data from becoming visible to the hackers and intruders. Hashed emails refer
to the encryption mechanism based on which contents of emails are hidden. Hashing encrypts
parts of data like email addresses into hexadecimal strings, each of which stay constant
irrespective of where the email address gets used. It is not possible to trace the email address
back from the code although the behaviour associated with the email addresses do get
recorded. That is to say, such hashed emails can be used to acquire data regarding the
interests and activities of a particular individual over the digital space by marketers without
knowing the email addresses. The security attack of Dell’s network is a real life practical
example that assures the effectiveness of hashed emails.
Though the concept might appear similar to cookies because of being able to track
abilities customers, hashing and cookies do have their differences. One such difference can
be of cookies not being able to work with multiple systems. Thus, since in today’s world
where average users work with 3 systems daily throughout the week, hashed emails can be
more useful to marketers than cookies. Also cookies can easily be blocked by the users and
are not always trusted. Cookies do not connect to app based mobile activities. In contrast
emails are much more reliable and offer cross platform support.
The other email encryption scheme broadly used for securing emails is OpenPGP.
Email applications are supported by OpenPGP either directly or through other software
the network of Dell, there was no conclusive proof which suggested that any information got
extracted from the these stolen emails. After the incident Dell insists that hashed passwords
limit potential exposure to attackers. To prevent similar attacks from taking place in future,
the company conducted a forced reset of all passwords by hiring digital forensics teams and
advising customers not to use similar passwords.
As noticeable from the above situation it is clear that hashed passwords help prevent
sensitive email data from becoming visible to the hackers and intruders. Hashed emails refer
to the encryption mechanism based on which contents of emails are hidden. Hashing encrypts
parts of data like email addresses into hexadecimal strings, each of which stay constant
irrespective of where the email address gets used. It is not possible to trace the email address
back from the code although the behaviour associated with the email addresses do get
recorded. That is to say, such hashed emails can be used to acquire data regarding the
interests and activities of a particular individual over the digital space by marketers without
knowing the email addresses. The security attack of Dell’s network is a real life practical
example that assures the effectiveness of hashed emails.
Though the concept might appear similar to cookies because of being able to track
abilities customers, hashing and cookies do have their differences. One such difference can
be of cookies not being able to work with multiple systems. Thus, since in today’s world
where average users work with 3 systems daily throughout the week, hashed emails can be
more useful to marketers than cookies. Also cookies can easily be blocked by the users and
are not always trusted. Cookies do not connect to app based mobile activities. In contrast
emails are much more reliable and offer cross platform support.
The other email encryption scheme broadly used for securing emails is OpenPGP.
Email applications are supported by OpenPGP either directly or through other software

9CYBER SECURITY AND TRAFFIC
applications. The PGP in OpenPGP stands for pretty good privacy (Ruoti et al. 2015).
OpenPGP is the most extensively used email encryption standard that got defined by the
OpenPGP Working Group of Internet Engineering Task Force or IETF as the standard
proposed in RFC 4880 (Kreutz et al. 2018). It is an open source solution that is derived from
the PGP software that got created by Phil Zimmermann. This program provided encrypting
and decrypting of texts, emails, files, directories and in increasing security of email
communications. Instead of just doing hashing, PGP employs a range of encryption
mechanisms like data compression, authentication, symmetric key cryptography and public
key cryptography. Here, each set of the public key get assigned to a specific usernames and
email address. Initially it got called web of trust for in sharp contrast to X.509 system which
uses hierarchical approach on the basis of the certifying
authority that later gets added to PGP.
Recent PGP versions involve encryption through automated keys as well as management
servers. Among the PGP mechanisms are:
PGP fingerprint: Refers to public key fingerprints that are shorter than public keys. The
correct corresponding public key can be obtained from the fingerprint which an example of
which can be C3A6 77DF 5E46 7B54 3C4C 9790 B3CA 4D22 FF66 5B32 and can be
printable on business cards.
Compatibility: With the evolution of PGP, versions supporting newer algorithms and features
can enable encryption of messages that cannot be decrypted using older versions even if they
possess a valid private key. Thus, it becomes extremely necessary for understanding each
other’s capabilities and to agree upon PGP configuration.
applications. The PGP in OpenPGP stands for pretty good privacy (Ruoti et al. 2015).
OpenPGP is the most extensively used email encryption standard that got defined by the
OpenPGP Working Group of Internet Engineering Task Force or IETF as the standard
proposed in RFC 4880 (Kreutz et al. 2018). It is an open source solution that is derived from
the PGP software that got created by Phil Zimmermann. This program provided encrypting
and decrypting of texts, emails, files, directories and in increasing security of email
communications. Instead of just doing hashing, PGP employs a range of encryption
mechanisms like data compression, authentication, symmetric key cryptography and public
key cryptography. Here, each set of the public key get assigned to a specific usernames and
email address. Initially it got called web of trust for in sharp contrast to X.509 system which
uses hierarchical approach on the basis of the certifying
authority that later gets added to PGP.
Recent PGP versions involve encryption through automated keys as well as management
servers. Among the PGP mechanisms are:
PGP fingerprint: Refers to public key fingerprints that are shorter than public keys. The
correct corresponding public key can be obtained from the fingerprint which an example of
which can be C3A6 77DF 5E46 7B54 3C4C 9790 B3CA 4D22 FF66 5B32 and can be
printable on business cards.
Compatibility: With the evolution of PGP, versions supporting newer algorithms and features
can enable encryption of messages that cannot be decrypted using older versions even if they
possess a valid private key. Thus, it becomes extremely necessary for understanding each
other’s capabilities and to agree upon PGP configuration.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
10CYBER SECURITY AND TRAFFIC
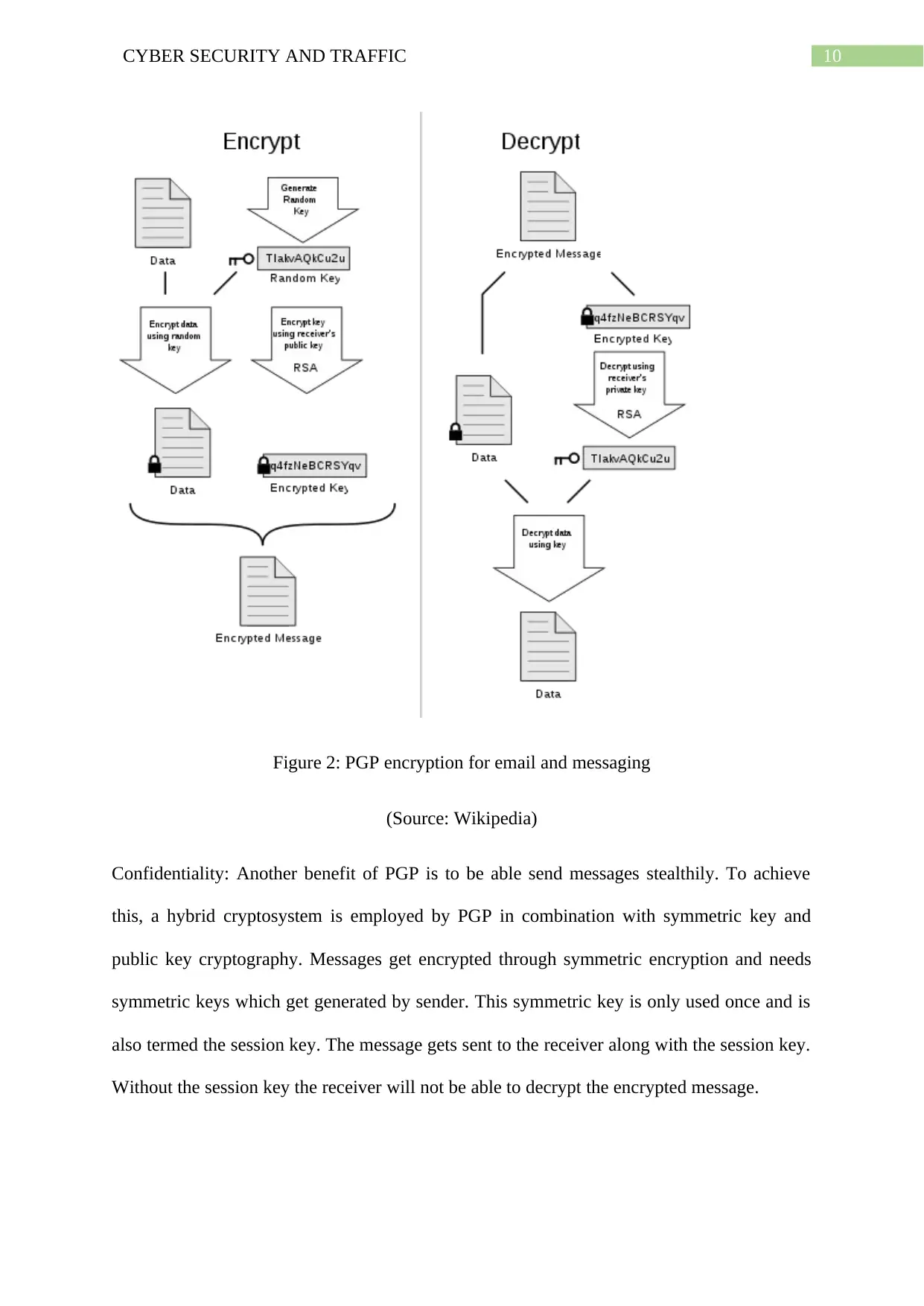
Figure 2: PGP encryption for email and messaging
(Source: Wikipedia)
Confidentiality: Another benefit of PGP is to be able send messages stealthily. To achieve
this, a hybrid cryptosystem is employed by PGP in combination with symmetric key and
public key cryptography. Messages get encrypted through symmetric encryption and needs
symmetric keys which get generated by sender. This symmetric key is only used once and is
also termed the session key. The message gets sent to the receiver along with the session key.
Without the session key the receiver will not be able to decrypt the encrypted message.
Figure 2: PGP encryption for email and messaging
(Source: Wikipedia)
Confidentiality: Another benefit of PGP is to be able send messages stealthily. To achieve
this, a hybrid cryptosystem is employed by PGP in combination with symmetric key and
public key cryptography. Messages get encrypted through symmetric encryption and needs
symmetric keys which get generated by sender. This symmetric key is only used once and is
also termed the session key. The message gets sent to the receiver along with the session key.
Without the session key the receiver will not be able to decrypt the encrypted message.

11CYBER SECURITY AND TRAFFIC
Digital Signatures: Integrity checks and authentication of messages are also supported by
PGP with the former checking if any alterations are made to the message or the message
integrity was maintained. Authentication ensures the message is sent by the right person
(sender having digital signature). As the messages get encrypted any changes will make it
unable to open with the provided key. PGP is used by the sender for creating digital
signatures with DSA or RSSA algorithms.
Compared to hashing PGP is vastly different. PGP refers to an entire software
solution for tackling cyber security threats in emails, messages and other formal
communication modes whereas hashing is only a particular feature that can be used to
encrypt emails. As a result, if the firm is looking to implement an extremely lightweight fix
for adding security to the email exchange processes within the business with minimal
investment then hashing is the right choice and can be implemented through the in-house IT
and development department of businesses. PGP being a complete application will require
more extensive work for the company to acquire and implement with the mailing clients in
use by the company.
Digital Signatures: Integrity checks and authentication of messages are also supported by
PGP with the former checking if any alterations are made to the message or the message
integrity was maintained. Authentication ensures the message is sent by the right person
(sender having digital signature). As the messages get encrypted any changes will make it
unable to open with the provided key. PGP is used by the sender for creating digital
signatures with DSA or RSSA algorithms.
Compared to hashing PGP is vastly different. PGP refers to an entire software
solution for tackling cyber security threats in emails, messages and other formal
communication modes whereas hashing is only a particular feature that can be used to
encrypt emails. As a result, if the firm is looking to implement an extremely lightweight fix
for adding security to the email exchange processes within the business with minimal
investment then hashing is the right choice and can be implemented through the in-house IT
and development department of businesses. PGP being a complete application will require
more extensive work for the company to acquire and implement with the mailing clients in
use by the company.
12CYBER SECURITY AND TRAFFIC
Question 4: Traffic Analysis
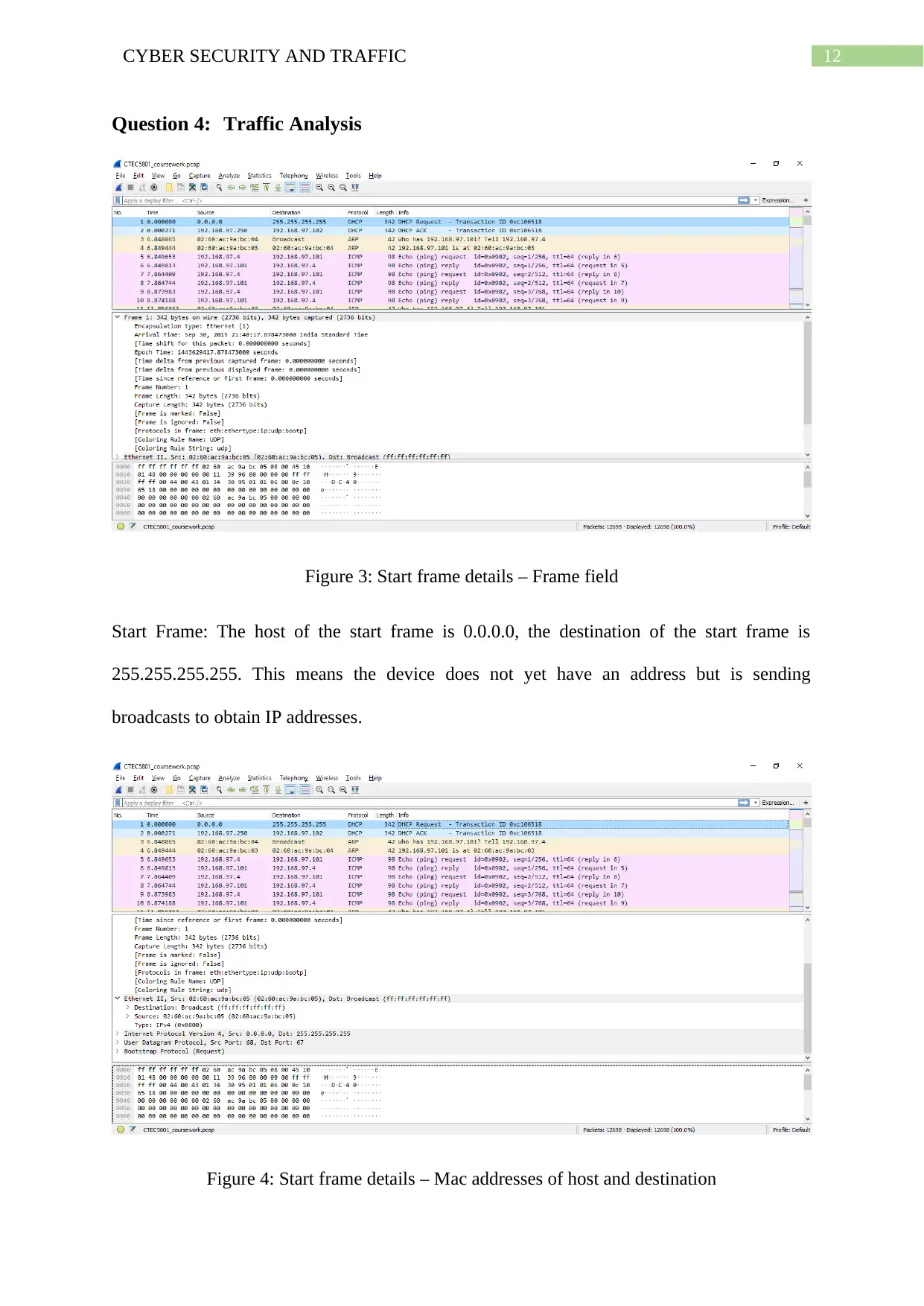
Figure 3: Start frame details – Frame field
Start Frame: The host of the start frame is 0.0.0.0, the destination of the start frame is
255.255.255.255. This means the device does not yet have an address but is sending
broadcasts to obtain IP addresses.
Figure 4: Start frame details – Mac addresses of host and destination
Question 4: Traffic Analysis
Figure 3: Start frame details – Frame field
Start Frame: The host of the start frame is 0.0.0.0, the destination of the start frame is
255.255.255.255. This means the device does not yet have an address but is sending
broadcasts to obtain IP addresses.
Figure 4: Start frame details – Mac addresses of host and destination
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13CYBER SECURITY AND TRAFFIC
Mac address of host initiating connection: The start frame denotes that connection is being
initiated. Therefore Mac address noted from the Ethernet field is 02:60:ac:9a:bc:05.
Mac address of destination host: From the Ethernet field the destination Mac address can also
be obtained which is ff:ff:ff:ff:ff:ff.
IP address of host initiating the connection: The IP address of the host initiating the
connection reads 0.0.0.0 as no IP has been assigned yet, only broadcasts are being sent for
initiating connections.
IP address of destination host is 255.255.255.255. This IP has a special meaning that is it
means this network. This lets frames send broadcast packets to the network the device is
connected to without even caring about the IP address of the device in that frame.
The source and destination ports used by the frame are 68 and 67 respectively.
The start frame, frame 1 is a DHCP request asking for IP address, the following frame, frame
2, refers to the DHCP acknowledge that assigns the IP address 192.168.97.250
The following frame, frame 3 sends broadcast to know the MAC address of 192.168.97.101
and wants the information to be sent to 192.168.97.4. The following frame, frame 4 obtains
the required Mac address information. This process is ensured by using the Address
Resolution Protocol or ARP.
The next six messages are ICMP echo packets concerning ping requests and reply messages
between 192.168.97.101 and 192.168.97.4.
The following communications continue to involve the above type of communications.
Frames 25 to 34 involve the 3 way TCP handshaking protocol with packets responsible for
synchronize, acknowledge, requests (SYN, SYN-ACK, ACK) as well as few HTTP requests
like GET.
Mac address of host initiating connection: The start frame denotes that connection is being
initiated. Therefore Mac address noted from the Ethernet field is 02:60:ac:9a:bc:05.
Mac address of destination host: From the Ethernet field the destination Mac address can also
be obtained which is ff:ff:ff:ff:ff:ff.
IP address of host initiating the connection: The IP address of the host initiating the
connection reads 0.0.0.0 as no IP has been assigned yet, only broadcasts are being sent for
initiating connections.
IP address of destination host is 255.255.255.255. This IP has a special meaning that is it
means this network. This lets frames send broadcast packets to the network the device is
connected to without even caring about the IP address of the device in that frame.
The source and destination ports used by the frame are 68 and 67 respectively.
The start frame, frame 1 is a DHCP request asking for IP address, the following frame, frame
2, refers to the DHCP acknowledge that assigns the IP address 192.168.97.250
The following frame, frame 3 sends broadcast to know the MAC address of 192.168.97.101
and wants the information to be sent to 192.168.97.4. The following frame, frame 4 obtains
the required Mac address information. This process is ensured by using the Address
Resolution Protocol or ARP.
The next six messages are ICMP echo packets concerning ping requests and reply messages
between 192.168.97.101 and 192.168.97.4.
The following communications continue to involve the above type of communications.
Frames 25 to 34 involve the 3 way TCP handshaking protocol with packets responsible for
synchronize, acknowledge, requests (SYN, SYN-ACK, ACK) as well as few HTTP requests
like GET.
14CYBER SECURITY AND TRAFFIC
Frames 44 and 46 involve SSHv2 packets with client server communications.
Frame 698 involves a TCP packet with RST or reset request.
These are all the type of communications that occur in the traffic that can be noted from the
Wireshark packet capture file.
Frames 44 and 46 involve SSHv2 packets with client server communications.
Frame 698 involves a TCP packet with RST or reset request.
These are all the type of communications that occur in the traffic that can be noted from the
Wireshark packet capture file.

15CYBER SECURITY AND TRAFFIC
References
Ardy, R.D., Indriani, O.R., Sari, C.A. and Rachmawanto, E.H., 2017, November. Digital
image signature using triple protection cryptosystem (RSA, Vigenere, and MD5). In 2017
International Conference on Smart Cities, Automation & Intelligent Computing Systems
(ICON-SONICS) (pp. 87-92). IEEE.
Braun, B., 2015. Preparedness, crisis management and policy change: The euro area at the
critical juncture of 2008–2013. The British Journal of Politics and International Relations,
17(3), pp.419-441.
Caldwell, B.G. and Caldwell, C., 2016. Ten classic onboarding errors: violations of the
HRM–employee relationship. Business and Management Research, 5(4), pp.47-55.
Chou, R.A., Bloch, M.R. and Abbe, E., 2015. Polar coding for secret-key generation. IEEE
Transactions on Information Theory, 61(11), pp.6213-6237.
Dautenhahn, N., Kasampalis, T., Dietz, W., Criswell, J. and Adve, V., 2015, March. Nested
kernel: An operating system architecture for intra-kernel privilege separation. In ACM
SIGPLAN Notices (Vol. 50, No. 4, pp. 191-206). ACM.
Englehardt, S., Han, J. and Narayanan, A., 2018. I never signed up for this! Privacy
implications of email tracking. Proceedings on Privacy Enhancing Technologies, 2018(1),
pp.109-126.
Friese, S., 2016. ATLAS. ti 8 Windows Quick Tour. ATLAS. ti Scientific Software
Development, 54(20161222), pp.1-86.
Gomber, P., Kauffman, R.J., Parker, C. and Weber, B.W., 2018. On the fintech revolution:
interpreting the forces of innovation, disruption, and transformation in financial services.
Journal of Management Information Systems, 35(1), pp.220-265.
References
Ardy, R.D., Indriani, O.R., Sari, C.A. and Rachmawanto, E.H., 2017, November. Digital
image signature using triple protection cryptosystem (RSA, Vigenere, and MD5). In 2017
International Conference on Smart Cities, Automation & Intelligent Computing Systems
(ICON-SONICS) (pp. 87-92). IEEE.
Braun, B., 2015. Preparedness, crisis management and policy change: The euro area at the
critical juncture of 2008–2013. The British Journal of Politics and International Relations,
17(3), pp.419-441.
Caldwell, B.G. and Caldwell, C., 2016. Ten classic onboarding errors: violations of the
HRM–employee relationship. Business and Management Research, 5(4), pp.47-55.
Chou, R.A., Bloch, M.R. and Abbe, E., 2015. Polar coding for secret-key generation. IEEE
Transactions on Information Theory, 61(11), pp.6213-6237.
Dautenhahn, N., Kasampalis, T., Dietz, W., Criswell, J. and Adve, V., 2015, March. Nested
kernel: An operating system architecture for intra-kernel privilege separation. In ACM
SIGPLAN Notices (Vol. 50, No. 4, pp. 191-206). ACM.
Englehardt, S., Han, J. and Narayanan, A., 2018. I never signed up for this! Privacy
implications of email tracking. Proceedings on Privacy Enhancing Technologies, 2018(1),
pp.109-126.
Friese, S., 2016. ATLAS. ti 8 Windows Quick Tour. ATLAS. ti Scientific Software
Development, 54(20161222), pp.1-86.
Gomber, P., Kauffman, R.J., Parker, C. and Weber, B.W., 2018. On the fintech revolution:
interpreting the forces of innovation, disruption, and transformation in financial services.
Journal of Management Information Systems, 35(1), pp.220-265.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16CYBER SECURITY AND TRAFFIC
Gutmann, A. and Warner, M., 2019, June. Fight to be Forgotten: Exploring the Efficacy of
Data Erasure in Popular Operating Systems. In Annual Privacy Forum (Vol. 19). Springer.
Kreutz, D., Yu, J., Esteves-Veríssimo, P., Magalhães, C. and Ramos, F.M., 2018. The KISS
principle in Software-Defined Networking: a framework for secure communications. IEEE
Security & Privacy, 16(5), pp.60-70.
Massa, L., Tucci, C.L. and Afuah, A., 2017. A critical assessment of business model
research. Academy of Management Annals, 11(1), pp.73-104.
Nourian, A. and Madnick, S., 2018. A systems theoretic approach to the security threats in
cyber physical systems applied to stuxnet. IEEE Transactions on Dependable and Secure
Computing, 15(1), pp.2-13.
Oktaviana, B. and Siahaan, A.P.U., 2016. Three-Pass Protocol Implementation in Caesar
Cipher Classic Cryptography. IOSR Journal of Computer Engineering, 18(4), pp.26-29.
Radwan, A.G., AbdElHaleem, S.H. and Abd-El-Hafiz, S.K., 2016. Symmetric encryption
algorithms using chaotic and non-chaotic generators: a review. Journal of Advanced
Research, 7(2), pp.193-208.
Raithel, J.D., Reynolds‐Hogland, M.J., Koons, D.N., Carr, P.C. and Aubry, L.M., 2017.
Recreational harvest and incident‐response management reduce human–carnivore conflicts in
an anthropogenic landscape. Journal of Applied Ecology, 54(5), pp.1552-1562.
Rezaeibagha, F. and Mu, Y., 2016. Distributed clinical data sharing via dynamic access-
control policy transformation. International journal of medical informatics, 89, pp.25-31.
Rooney, V.M. and Foley, S.N., 2018, August. An Online Consent Maturity Model: Moving
from Acceptable Use towards Ethical Practice. In Proceedings of the New Security
Paradigms Workshop (pp. 64-79). ACM.
Gutmann, A. and Warner, M., 2019, June. Fight to be Forgotten: Exploring the Efficacy of
Data Erasure in Popular Operating Systems. In Annual Privacy Forum (Vol. 19). Springer.
Kreutz, D., Yu, J., Esteves-Veríssimo, P., Magalhães, C. and Ramos, F.M., 2018. The KISS
principle in Software-Defined Networking: a framework for secure communications. IEEE
Security & Privacy, 16(5), pp.60-70.
Massa, L., Tucci, C.L. and Afuah, A., 2017. A critical assessment of business model
research. Academy of Management Annals, 11(1), pp.73-104.
Nourian, A. and Madnick, S., 2018. A systems theoretic approach to the security threats in
cyber physical systems applied to stuxnet. IEEE Transactions on Dependable and Secure
Computing, 15(1), pp.2-13.
Oktaviana, B. and Siahaan, A.P.U., 2016. Three-Pass Protocol Implementation in Caesar
Cipher Classic Cryptography. IOSR Journal of Computer Engineering, 18(4), pp.26-29.
Radwan, A.G., AbdElHaleem, S.H. and Abd-El-Hafiz, S.K., 2016. Symmetric encryption
algorithms using chaotic and non-chaotic generators: a review. Journal of Advanced
Research, 7(2), pp.193-208.
Raithel, J.D., Reynolds‐Hogland, M.J., Koons, D.N., Carr, P.C. and Aubry, L.M., 2017.
Recreational harvest and incident‐response management reduce human–carnivore conflicts in
an anthropogenic landscape. Journal of Applied Ecology, 54(5), pp.1552-1562.
Rezaeibagha, F. and Mu, Y., 2016. Distributed clinical data sharing via dynamic access-
control policy transformation. International journal of medical informatics, 89, pp.25-31.
Rooney, V.M. and Foley, S.N., 2018, August. An Online Consent Maturity Model: Moving
from Acceptable Use towards Ethical Practice. In Proceedings of the New Security
Paradigms Workshop (pp. 64-79). ACM.

17CYBER SECURITY AND TRAFFIC
Ruoti, S., Andersen, J., Zappala, D. and Seamons, K., 2015. Why Johnny still, still can't
encrypt: Evaluating the usability of a modern PGP client. arXiv preprint arXiv:1510.08555.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. Computers & Security, 56, pp.70-82.
Silberschatz, A., Gagne, G. and Galvin, P.B., 2018. Operating system concepts. Wiley.
Tanenbaum, A.S. and Bos, H., 2015. Modern operating systems. Pearson.
Teing, Y.Y., Dehghantanha, A., Choo, K.K.R. and Yang, L.T., 2017. Forensic investigation
of P2P cloud storage services and backbone for IoT networks: BitTorrent Sync as a case
study. Computers & Electrical Engineering, 58, pp.350-363.
Yuan, J., Zhan, Y., Jannen, W., Pandey, P., Akshintala, A., Chandnani, K., Deo, P., Kasheff,
Z., Walsh, L., Bender, M. and Farach-Colton, M., 2016. Optimizing every operation in a
write-optimized file system. In 14th {USENIX} Conference on File and Storage Technologies
({FAST} 16) (pp. 1-14).
Ruoti, S., Andersen, J., Zappala, D. and Seamons, K., 2015. Why Johnny still, still can't
encrypt: Evaluating the usability of a modern PGP client. arXiv preprint arXiv:1510.08555.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance
model in organizations. Computers & Security, 56, pp.70-82.
Silberschatz, A., Gagne, G. and Galvin, P.B., 2018. Operating system concepts. Wiley.
Tanenbaum, A.S. and Bos, H., 2015. Modern operating systems. Pearson.
Teing, Y.Y., Dehghantanha, A., Choo, K.K.R. and Yang, L.T., 2017. Forensic investigation
of P2P cloud storage services and backbone for IoT networks: BitTorrent Sync as a case
study. Computers & Electrical Engineering, 58, pp.350-363.
Yuan, J., Zhan, Y., Jannen, W., Pandey, P., Akshintala, A., Chandnani, K., Deo, P., Kasheff,
Z., Walsh, L., Bender, M. and Farach-Colton, M., 2016. Optimizing every operation in a
write-optimized file system. In 14th {USENIX} Conference on File and Storage Technologies
({FAST} 16) (pp. 1-14).
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





