CMP71001 Cybersecurity Report: BYOD, Authentication, and Anti-Spam
VerifiedAdded on 2022/08/19
|14
|3398
|36
Report
AI Summary
This cybersecurity report, prepared for Southern Cross University, addresses contemporary and emerging cyber threats, particularly those arising from the implementation of a Bring Your Own Device (BYOD) policy. The report begins with a BYOD risk assessment, evaluating potential vulnerabilities and security concerns associated with employees using personal devices for work. It then delves into certificate-based authentication as a more secure alternative to password-based systems, detailing the principles and implementation of this method. Finally, the report outlines anti-spam guidelines, crucial for mitigating email-related risks. The report provides a comprehensive overview of security measures and recommendations to enhance the university's overall cybersecurity posture. This assignment is a security consultation report and guideline for the course CMP71001.

Running head: CYBER SECURITY
CYBER SECURITY
Name of the Student
Name of the University
Author Note
CYBER SECURITY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY
Executive Summary
Security is one of the important aspects of a Company. The Company should always maintain
security. The report discusses about the Bring Your Device Policy that is very important in
the company so that the employees bring their devices and work in their familiar devices. The
risk assessment of the BYOD is performed in this report. The company should use
authentication that is based on certificate in place of authentication that is based on passwords
so that the company can protect the data properly and minimize the data breach. The report
focuses on the authentication that is based on certificate and the method of the certificate
based authentication. The report also focuses on the anti-spam guidelines that are very
important for the company in order to minimize the overflow of emails in the inbox on the
company or any of the employees. The company should take various steps in order to handle
the email spams.
Executive Summary
Security is one of the important aspects of a Company. The Company should always maintain
security. The report discusses about the Bring Your Device Policy that is very important in
the company so that the employees bring their devices and work in their familiar devices. The
risk assessment of the BYOD is performed in this report. The company should use
authentication that is based on certificate in place of authentication that is based on passwords
so that the company can protect the data properly and minimize the data breach. The report
focuses on the authentication that is based on certificate and the method of the certificate
based authentication. The report also focuses on the anti-spam guidelines that are very
important for the company in order to minimize the overflow of emails in the inbox on the
company or any of the employees. The company should take various steps in order to handle
the email spams.

2CYBER SECURITY
Table of Contents
Introduction:...............................................................................................................................3
Task 1: BOYD Risk Assessment...............................................................................................3
Task 2: Certificate-Based Authentication..................................................................................3
Task 3: Anti-Spam Guidelines...................................................................................................3
Conclusions................................................................................................................................3
References..................................................................................................................................4
Table of Contents
Introduction:...............................................................................................................................3
Task 1: BOYD Risk Assessment...............................................................................................3
Task 2: Certificate-Based Authentication..................................................................................3
Task 3: Anti-Spam Guidelines...................................................................................................3
Conclusions................................................................................................................................3
References..................................................................................................................................4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY
Introduction:
New devices’ advanced capabilities, as well as coming of internet with high speed,
has motivated the organizations in using the gadgets in workplace. Bring Your Own Device
(BYOD) is new occurrence where the employees connect the devices with the network of
enterprise in order to gain access to the corporate knowledge as well as carry out functions of
business those are regular. It permits the end users in engaging more in activities related to
work by using smartphones and endpoint devices in way, which is not dependent on
geographical position and time. Thus BYOD brought convenience to the business activities
like work flexibility and efficiency as well as significant advantages. Additionally, cost
efficiency is offe red by BYOD for the organizations, as this does not give devices for the
employees. Hence, number of the organizations taking advantage of productivity benefits for
computing devices is increasing on global scale. Organizations using BYOD in where the
employees who follow policies need to secure BYOD is quite low. The users use BYOD
where they make use of personal devices that are available for organization use.
This paper outlines the risks related with implementation of BYOD in Southern Cross
University. This paper also analyses working principle of mechanism of authentication that is
based on certificate. Spamming and its characteristics are also discussed in this paper as well.
Task 1: BOYD Risk Assessment
Establishing security of BYOD starts with policy creation of BYOD. Strong policy of BYOD
accomplishes many objectives for Southern Cross University. Policy of BYOD must address
the basic considerations like goals of program of BYOD, which employees could bring own
devices, which devices would be supported as well as access levels which the employees are
provided permission while using their personal devices (Zhang, Mouritsen and Miller 2019).
Cloud communication’s rise has paved way for much more organizations in adopting policy
Introduction:
New devices’ advanced capabilities, as well as coming of internet with high speed,
has motivated the organizations in using the gadgets in workplace. Bring Your Own Device
(BYOD) is new occurrence where the employees connect the devices with the network of
enterprise in order to gain access to the corporate knowledge as well as carry out functions of
business those are regular. It permits the end users in engaging more in activities related to
work by using smartphones and endpoint devices in way, which is not dependent on
geographical position and time. Thus BYOD brought convenience to the business activities
like work flexibility and efficiency as well as significant advantages. Additionally, cost
efficiency is offe red by BYOD for the organizations, as this does not give devices for the
employees. Hence, number of the organizations taking advantage of productivity benefits for
computing devices is increasing on global scale. Organizations using BYOD in where the
employees who follow policies need to secure BYOD is quite low. The users use BYOD
where they make use of personal devices that are available for organization use.
This paper outlines the risks related with implementation of BYOD in Southern Cross
University. This paper also analyses working principle of mechanism of authentication that is
based on certificate. Spamming and its characteristics are also discussed in this paper as well.
Task 1: BOYD Risk Assessment
Establishing security of BYOD starts with policy creation of BYOD. Strong policy of BYOD
accomplishes many objectives for Southern Cross University. Policy of BYOD must address
the basic considerations like goals of program of BYOD, which employees could bring own
devices, which devices would be supported as well as access levels which the employees are
provided permission while using their personal devices (Zhang, Mouritsen and Miller 2019).
Cloud communication’s rise has paved way for much more organizations in adopting policy
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBER SECURITY
of BYOD. Wireless technology’s prevalence as well as cloud tools’ emergence keeps people
connected at every time make BYOD next step logically. For the users, ability in working
from personal device without need in shifting from a device to other device and ability for
working from virtually from anywhere is hard to pass on. For the employees, advantage to
not requiring to provide the mobile devices for the employees while having them still
connected to primary communication system drives down the cost (Giotopoulos et al 2019).
However, like other things, policies of BYOD come with own challenges. Line among
company owned and data those are personal would get skewed probably and quantity of the
non-IT gadgets that are controlled by staff are linked to the company is presenting few new
issues of security as well.
Advances in technology as well as perceived costs to provide the workforce with the
secured devices have made BYOD attractive proposition for the employers. Employers such
as that have only to keep record of single device as well as convenience to manage their work
and personal items at one place. Allowing the employees in bringing their devices of their
own has shown in improving the morale of the employers as well as the productivity. Risks
of BYOD become much more apparent while considering impact to have several separate
entry points to the systems of Southern Cross University. Policies of BYOD make this easy in
keeping contact of the employees of Southern Cross University (Tanimoto et al 2016).
However, there is always a risk of using unsecured network of Wi-Fi. This could have the
risk to expose sensitive information to the hackers who look to access to the crucial system of
Southern Cross University. Hackers would look for opportunities for stealing data and
BYOD’s practice could be great environment to them for doing so.
Employees of Southern Cross University use their own devices for downloading
every kind of information and might be careless about securing and separating valuable data
of Southern Cross University from everything. Employees of the university could download
of BYOD. Wireless technology’s prevalence as well as cloud tools’ emergence keeps people
connected at every time make BYOD next step logically. For the users, ability in working
from personal device without need in shifting from a device to other device and ability for
working from virtually from anywhere is hard to pass on. For the employees, advantage to
not requiring to provide the mobile devices for the employees while having them still
connected to primary communication system drives down the cost (Giotopoulos et al 2019).
However, like other things, policies of BYOD come with own challenges. Line among
company owned and data those are personal would get skewed probably and quantity of the
non-IT gadgets that are controlled by staff are linked to the company is presenting few new
issues of security as well.
Advances in technology as well as perceived costs to provide the workforce with the
secured devices have made BYOD attractive proposition for the employers. Employers such
as that have only to keep record of single device as well as convenience to manage their work
and personal items at one place. Allowing the employees in bringing their devices of their
own has shown in improving the morale of the employers as well as the productivity. Risks
of BYOD become much more apparent while considering impact to have several separate
entry points to the systems of Southern Cross University. Policies of BYOD make this easy in
keeping contact of the employees of Southern Cross University (Tanimoto et al 2016).
However, there is always a risk of using unsecured network of Wi-Fi. This could have the
risk to expose sensitive information to the hackers who look to access to the crucial system of
Southern Cross University. Hackers would look for opportunities for stealing data and
BYOD’s practice could be great environment to them for doing so.
Employees of Southern Cross University use their own devices for downloading
every kind of information and might be careless about securing and separating valuable data
of Southern Cross University from everything. Employees of the university could download

5CYBER SECURITY
contents which might have hidden viruses or malware. They might end up passing this into
the network of the university (Keyes 2016). Reputation of Southern Cross University could
be damaged severely if security breach by device of an employee leads to leakage of critical
information of the university, which means dealing with the litigation of the different parties.
Southern Cross University would need in laying out capital attempting to defend
against the legal challenges. Employee of the university having his device stolen or losing his
device could go from big inconvenience into disaster for the university if they did not follow
recommended security protocols by the university. Even if employees of the university did
everything right, hackers have access now to much more sophisticated technology (Ganiyu
and Jimoh 2018). Anyone having enough skill and determination could crack the secure
network of the university. Several security breaches take place as result of the mistakes made
by the employees. They might not totally understand the requirements of the system when it
is about securing the devices. The employees of Southern Cross University should be
provided proper training which would help them in understanding the requirements of the
systems of the university.
Components Of IT Components of Risk
Management
Assets
Hardware Hardwares of the university Laptops, desktops
smartphones
Software Softwares those are used in
the university
Operating systems and the
other application softwares
People The people of the university Staffs, teachers and students
Network The network components WAN, LAN and the other
networks
Table 1: WFA Table
contents which might have hidden viruses or malware. They might end up passing this into
the network of the university (Keyes 2016). Reputation of Southern Cross University could
be damaged severely if security breach by device of an employee leads to leakage of critical
information of the university, which means dealing with the litigation of the different parties.
Southern Cross University would need in laying out capital attempting to defend
against the legal challenges. Employee of the university having his device stolen or losing his
device could go from big inconvenience into disaster for the university if they did not follow
recommended security protocols by the university. Even if employees of the university did
everything right, hackers have access now to much more sophisticated technology (Ganiyu
and Jimoh 2018). Anyone having enough skill and determination could crack the secure
network of the university. Several security breaches take place as result of the mistakes made
by the employees. They might not totally understand the requirements of the system when it
is about securing the devices. The employees of Southern Cross University should be
provided proper training which would help them in understanding the requirements of the
systems of the university.
Components Of IT Components of Risk
Management
Assets
Hardware Hardwares of the university Laptops, desktops
smartphones
Software Softwares those are used in
the university
Operating systems and the
other application softwares
People The people of the university Staffs, teachers and students
Network The network components WAN, LAN and the other
networks
Table 1: WFA Table
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
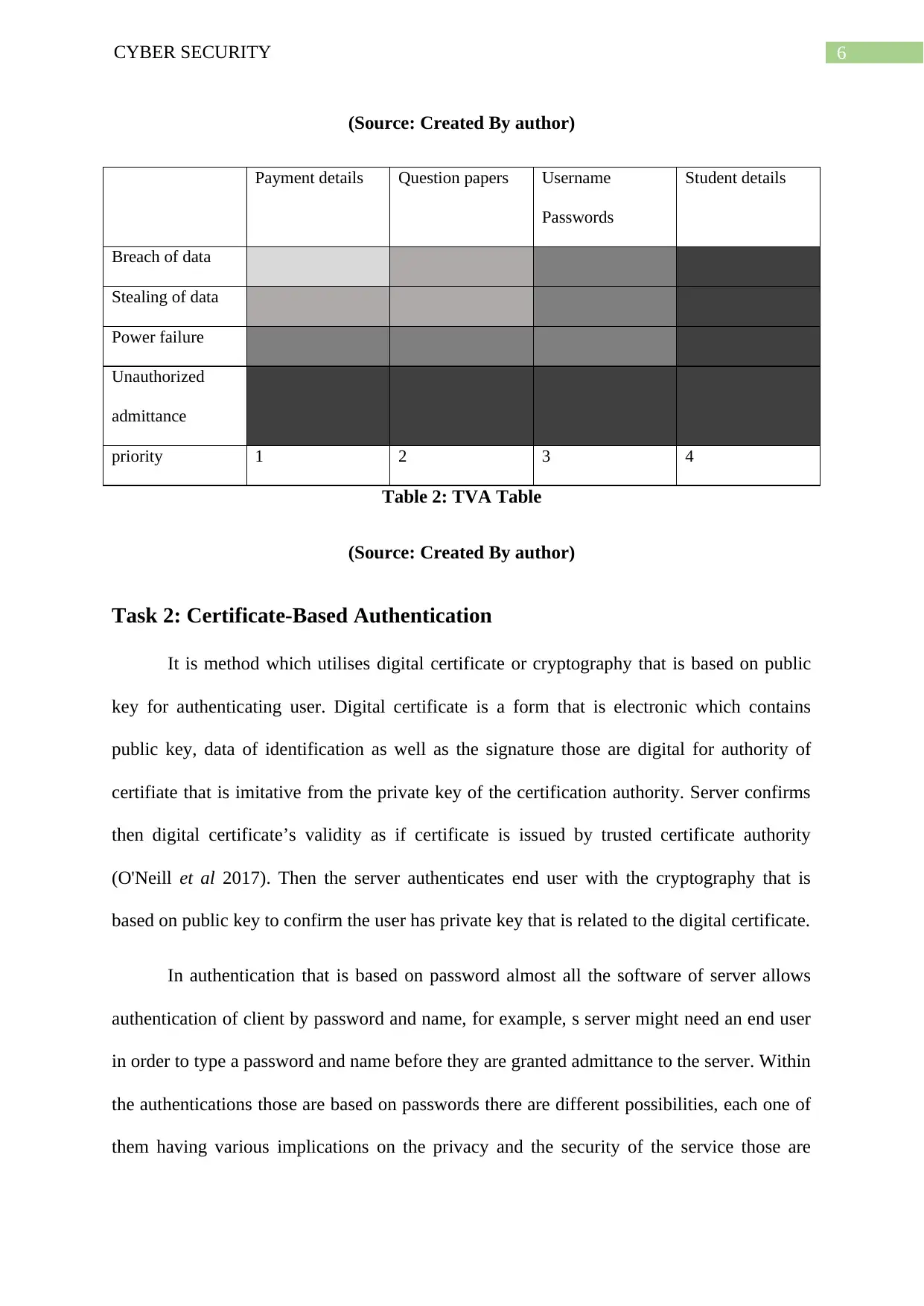
6CYBER SECURITY
(Source: Created By author)
Payment details Question papers Username
Passwords
Student details
Breach of data
Stealing of data
Power failure
Unauthorized
admittance
priority 1 2 3 4
Table 2: TVA Table
(Source: Created By author)
Task 2: Certificate-Based Authentication
It is method which utilises digital certificate or cryptography that is based on public
key for authenticating user. Digital certificate is a form that is electronic which contains
public key, data of identification as well as the signature those are digital for authority of
certifiate that is imitative from the private key of the certification authority. Server confirms
then digital certificate’s validity as if certificate is issued by trusted certificate authority
(O'Neill et al 2017). Then the server authenticates end user with the cryptography that is
based on public key to confirm the user has private key that is related to the digital certificate.
In authentication that is based on password almost all the software of server allows
authentication of client by password and name, for example, s server might need an end user
in order to type a password and name before they are granted admittance to the server. Within
the authentications those are based on passwords there are different possibilities, each one of
them having various implications on the privacy and the security of the service those are
(Source: Created By author)
Payment details Question papers Username
Passwords
Student details
Breach of data
Stealing of data
Power failure
Unauthorized
admittance
priority 1 2 3 4
Table 2: TVA Table
(Source: Created By author)
Task 2: Certificate-Based Authentication
It is method which utilises digital certificate or cryptography that is based on public
key for authenticating user. Digital certificate is a form that is electronic which contains
public key, data of identification as well as the signature those are digital for authority of
certifiate that is imitative from the private key of the certification authority. Server confirms
then digital certificate’s validity as if certificate is issued by trusted certificate authority
(O'Neill et al 2017). Then the server authenticates end user with the cryptography that is
based on public key to confirm the user has private key that is related to the digital certificate.
In authentication that is based on password almost all the software of server allows
authentication of client by password and name, for example, s server might need an end user
in order to type a password and name before they are granted admittance to the server. Within
the authentications those are based on passwords there are different possibilities, each one of
them having various implications on the privacy and the security of the service those are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY
offered to the user (Ruoti, Andersen and Seamons 2016). In the mechanism that is simple,
both the client and the server know the password initially. In this type of protocol, the client
sends the password and then server responds whether the authentication is successful or not.
An easy variation of this scheme is where the hash of the password is sent or the encrypted
version of the password is sent instead of the password.
The authentication that is based on certificate is utilization of a certification those are
digital to recognise a machine, an user or a gadget before giving them admittance to asset,
application of network and many more. In case of authentication based on user, it is often
implemented in co-ordination with traditional techniques such a passwords and username.
The authentication that is based on certificate is flexible and it can be utilised in many ways
(Farooq et al 2018). It permits access only to the machines and the users those are approved
or authorized and it prevent the users and the machines those are unauthorized.
Authentication of User
Accessing intranets, emails and the internal networks.
Accessing the services those are based on cloud that includes Google Apps
Logon of Windows
The steps of authentication that is based on certificate are as follows:
The client software preserves a database of the keys those are private that corresponds to
any of the key those are public and those are published in any of the certificates those are
provided for the client The client then asks for the password to this database when the
client requires to get into it during a session. After the password has been entered, the
user do not have to enter the password again for the session even when they access the
servers those are enabled by SSL.
offered to the user (Ruoti, Andersen and Seamons 2016). In the mechanism that is simple,
both the client and the server know the password initially. In this type of protocol, the client
sends the password and then server responds whether the authentication is successful or not.
An easy variation of this scheme is where the hash of the password is sent or the encrypted
version of the password is sent instead of the password.
The authentication that is based on certificate is utilization of a certification those are
digital to recognise a machine, an user or a gadget before giving them admittance to asset,
application of network and many more. In case of authentication based on user, it is often
implemented in co-ordination with traditional techniques such a passwords and username.
The authentication that is based on certificate is flexible and it can be utilised in many ways
(Farooq et al 2018). It permits access only to the machines and the users those are approved
or authorized and it prevent the users and the machines those are unauthorized.
Authentication of User
Accessing intranets, emails and the internal networks.
Accessing the services those are based on cloud that includes Google Apps
Logon of Windows
The steps of authentication that is based on certificate are as follows:
The client software preserves a database of the keys those are private that corresponds to
any of the key those are public and those are published in any of the certificates those are
provided for the client The client then asks for the password to this database when the
client requires to get into it during a session. After the password has been entered, the
user do not have to enter the password again for the session even when they access the
servers those are enabled by SSL.

8CYBER SECURITY
The user then opens the database of private key, recover the private key for the certificate
of the user and then utilise the private key in order to sign the data those are generated
randomly from the input both the server and the client (Verma, Kumar and Sinha 2016).
The digital signature and the data are proof of authority of private key. The signature
those are digital can be generated only with the private key that is used and it can be
validated with the public key against the data those are signed and that is distinctive in the
session of SSL.
The client sends both the certificate of the user and the data those are produced randomly
across the network.
The server uses the certificate and the data that is signed to validate the individuality of
the end user.
The server may execute other activities of validation that is inspecting that the digital
certificate that is given by the user is then kept in the entry of the user in the directory of
LDAP. The server than examines if the user those are recognised is permitted in order to
access the requested assets. This examination procedure an employ large diversity of
authorization methods those are standard, utilising the information in the directory of
LDAP (Patil et al 2018). If the output of the examination is positive, the server permits
the clients in order to access the resources those are requested.
The comparison between authentication that is based on password and that is based on
certificate are as follows:
Certificate based authentication
Certificates need management and installation. The authentication that is based on
certificate are more complex than authentication that is based on password (Zink and
The user then opens the database of private key, recover the private key for the certificate
of the user and then utilise the private key in order to sign the data those are generated
randomly from the input both the server and the client (Verma, Kumar and Sinha 2016).
The digital signature and the data are proof of authority of private key. The signature
those are digital can be generated only with the private key that is used and it can be
validated with the public key against the data those are signed and that is distinctive in the
session of SSL.
The client sends both the certificate of the user and the data those are produced randomly
across the network.
The server uses the certificate and the data that is signed to validate the individuality of
the end user.
The server may execute other activities of validation that is inspecting that the digital
certificate that is given by the user is then kept in the entry of the user in the directory of
LDAP. The server than examines if the user those are recognised is permitted in order to
access the requested assets. This examination procedure an employ large diversity of
authorization methods those are standard, utilising the information in the directory of
LDAP (Patil et al 2018). If the output of the examination is positive, the server permits
the clients in order to access the resources those are requested.
The comparison between authentication that is based on password and that is based on
certificate are as follows:
Certificate based authentication
Certificates need management and installation. The authentication that is based on
certificate are more complex than authentication that is based on password (Zink and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER SECURITY
Waldvogel 2017). Any individual in control of the private key of the certificate is granted
admittance to the server. The certificates should be distributed with proper care.
Password based authentication
The authentication that is based on password are less complex than certificate based
authentication. In this authentication, passwords are used in order to authenticate a server.
The basic mechanism behind the authentication that is based on password is an unauthorized
user can keep and then remember a secret (Mandal and Deepti 2017). And the secret is
utilised validate the individuality of the user those are authorized for admittance to specific
system.
Task 3: Anti-Spam Guidelines
A message that is electronic is called a spam if the individual characteristics of
receiver and the context are not relevant as the message is valid to various receivers those are
potential and the recipient has not given explicit, intentional and revocable consent for the
message that is to be sent (Bhuiyan et al 2018).
The characteristics of spam are:
Maximum of the spam messages are sent using Gmail. Any real organization would use
their own email address when they send a mail (Jiang, Guo and Guo 2017).
The grammar of the spam mails are generally very bad and the email must be read first
before giving a reply as the grammar will be worse and kinky.
The email spams do not belong to any of the company and no organization is related with
their signature of email.
Waldvogel 2017). Any individual in control of the private key of the certificate is granted
admittance to the server. The certificates should be distributed with proper care.
Password based authentication
The authentication that is based on password are less complex than certificate based
authentication. In this authentication, passwords are used in order to authenticate a server.
The basic mechanism behind the authentication that is based on password is an unauthorized
user can keep and then remember a secret (Mandal and Deepti 2017). And the secret is
utilised validate the individuality of the user those are authorized for admittance to specific
system.
Task 3: Anti-Spam Guidelines
A message that is electronic is called a spam if the individual characteristics of
receiver and the context are not relevant as the message is valid to various receivers those are
potential and the recipient has not given explicit, intentional and revocable consent for the
message that is to be sent (Bhuiyan et al 2018).
The characteristics of spam are:
Maximum of the spam messages are sent using Gmail. Any real organization would use
their own email address when they send a mail (Jiang, Guo and Guo 2017).
The grammar of the spam mails are generally very bad and the email must be read first
before giving a reply as the grammar will be worse and kinky.
The email spams do not belong to any of the company and no organization is related with
their signature of email.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER SECURITY
Unless the user utilise the filters judiciously, there is a high chance that the inbox of
the user is full of spam (Atanasova, Parusheva and Kostadinova 2016). The examples of
spam include:
The messages of email that the user did not ask for are from the senders that the user does
not know.
The commercial emails those are unsolicited are sent is bulk, often to a purchased list of
mailing that includes the user’s email address.
The messages those are misleading from the people that the user know whose accounts of
email are hacked.
The techniques of anti-spam can be grouped into several categories but only some these
techniques are in use. There are two points of view to the spam response. The most common
issue associates to the ability to distinguish between legitimate email and spam. For bulk
percentage of email, the decision is very easy (Seneviratne et al 207). The user can easily
recognise more than half of the emails. It is rest of the emails those are more complex to
handle. The various ways to handle the email by the users include:
Whitelists and blacklists
Heuristic engines
Rule based ranking
Authenticated email
Reverse DNS Lookup.
Conclusions
The report discusses about the security aspects of a company that they should follow
so that they can manage the data and reduce the data breach in the company. The security
aspects include Bring Your Own Device, authentication that is based on certificate and
Unless the user utilise the filters judiciously, there is a high chance that the inbox of
the user is full of spam (Atanasova, Parusheva and Kostadinova 2016). The examples of
spam include:
The messages of email that the user did not ask for are from the senders that the user does
not know.
The commercial emails those are unsolicited are sent is bulk, often to a purchased list of
mailing that includes the user’s email address.
The messages those are misleading from the people that the user know whose accounts of
email are hacked.
The techniques of anti-spam can be grouped into several categories but only some these
techniques are in use. There are two points of view to the spam response. The most common
issue associates to the ability to distinguish between legitimate email and spam. For bulk
percentage of email, the decision is very easy (Seneviratne et al 207). The user can easily
recognise more than half of the emails. It is rest of the emails those are more complex to
handle. The various ways to handle the email by the users include:
Whitelists and blacklists
Heuristic engines
Rule based ranking
Authenticated email
Reverse DNS Lookup.
Conclusions
The report discusses about the security aspects of a company that they should follow
so that they can manage the data and reduce the data breach in the company. The security
aspects include Bring Your Own Device, authentication that is based on certificate and

11CYBER SECURITY
guidelines of anti spam that the company should follow so that the data can be managed
properly. The employees in the company should follow the policy of Bring Your Own
Device. The company should follow authentication that is based on certificate so that the data
of the company can be properly secured and the advantage of authentication that is based on
certificates is that it uses digital certificates. The report also focuses on the anti spam
guidelines that should be followed by the employees of the company in order to save the
emails from being over flowed with emails.
guidelines of anti spam that the company should follow so that the data can be managed
properly. The employees in the company should follow the policy of Bring Your Own
Device. The company should follow authentication that is based on certificate so that the data
of the company can be properly secured and the advantage of authentication that is based on
certificates is that it uses digital certificates. The report also focuses on the anti spam
guidelines that should be followed by the employees of the company in order to save the
emails from being over flowed with emails.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





