Cyber Security Awareness and Risk Management
VerifiedAdded on 2022/08/25
|9
|1583
|32
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: RESEARCH PROPOSAL
Research Proposal
Topic: How ICT Risk Management Issues are heightened with the awareness level of
employees of cyber security hygiene in an organization?
Name of the Student
Name of the University
Author Note
Research Proposal
Topic: How ICT Risk Management Issues are heightened with the awareness level of
employees of cyber security hygiene in an organization?
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1RESEARCH PROPOSAL
Table of Contents
Introduction................................................................................................................................2
Statement of the Problem.......................................................................................................2
Purpose/Objectives.................................................................................................................3
Hypotheses/Research questions.............................................................................................4
Significance of the study........................................................................................................4
Scope of the Study.................................................................................................................5
Literature Review...................................................................................................................5
Methods and Materials...........................................................................................................5
Financial Arrangements.........................................................................................................6
Duration..................................................................................................................................6
References..................................................................................................................................7
Table of Contents
Introduction................................................................................................................................2
Statement of the Problem.......................................................................................................2
Purpose/Objectives.................................................................................................................3
Hypotheses/Research questions.............................................................................................4
Significance of the study........................................................................................................4
Scope of the Study.................................................................................................................5
Literature Review...................................................................................................................5
Methods and Materials...........................................................................................................5
Financial Arrangements.........................................................................................................6
Duration..................................................................................................................................6
References..................................................................................................................................7

2RESEARCH PROPOSAL
Introduction
The concept of Cyber hygiene comes from a business which is performing their day to
day activities keeping up with the information technology and communication systems. For
any business that handles sensitive data with the help of the IT systems, functioning of the
data sensitivity is a matter of business success or failure. The handling of business with the
help of the functioning of all the activities for collection, processing, storage and
management of data cannot be practiced properly without initialising proper cyber hygiene
[1]. The scenario that the world is currently living in in and the business thriving with IT
infrastructure in them is at constant threat in the ever-changing business landscape. There
have been numerous reports about business failing to keep up with the proposed IT
infrastructure because of the lack of awareness about cyber hygiene resulting into several
issues leading to data breaches.
However, a proper utilisation of Cyber hygiene is extremely important because it
would help a business to prevent unauthorised malicious activities, intelligent Malware and
even advanced viruses from accessing or corrupting the devices used within the organisation.
Without a proper cyber hygiene, there is a possibility that the threat landscape would
increase.
Statement of the Problem
The problem with business organisations nowadays is the constant and Rapid
Changing of the business scenario. The more businesses are becoming technologically sound,
the unauthorised access of hackers is also becoming heightened in number. The technology
that the hackers are using to steal business data are becoming much more improved than it
has been a few years back [2]. However, on the other hand, the people who are currently
utilising IT Infrastructures in business, are often found to be implying the age-old procedures
Introduction
The concept of Cyber hygiene comes from a business which is performing their day to
day activities keeping up with the information technology and communication systems. For
any business that handles sensitive data with the help of the IT systems, functioning of the
data sensitivity is a matter of business success or failure. The handling of business with the
help of the functioning of all the activities for collection, processing, storage and
management of data cannot be practiced properly without initialising proper cyber hygiene
[1]. The scenario that the world is currently living in in and the business thriving with IT
infrastructure in them is at constant threat in the ever-changing business landscape. There
have been numerous reports about business failing to keep up with the proposed IT
infrastructure because of the lack of awareness about cyber hygiene resulting into several
issues leading to data breaches.
However, a proper utilisation of Cyber hygiene is extremely important because it
would help a business to prevent unauthorised malicious activities, intelligent Malware and
even advanced viruses from accessing or corrupting the devices used within the organisation.
Without a proper cyber hygiene, there is a possibility that the threat landscape would
increase.
Statement of the Problem
The problem with business organisations nowadays is the constant and Rapid
Changing of the business scenario. The more businesses are becoming technologically sound,
the unauthorised access of hackers is also becoming heightened in number. The technology
that the hackers are using to steal business data are becoming much more improved than it
has been a few years back [2]. However, on the other hand, the people who are currently
utilising IT Infrastructures in business, are often found to be implying the age-old procedures

3RESEARCH PROPOSAL
to maintain cyber hygiene. Sometimes few organisations are also found to be not implying
any cyber hygiene protocol at all within the organisation leading to possible vulnerability of
the organisation to threat.
Purpose/Objectives
The ever changing world of business has seen changes and enhancements in the threat
landscapes as well. With time, organisations must adapt to Cyber hygiene routine. It is much
important today to maintain a proper cyber hygiene routine within the organisation and
letting the employees within the organisation understand the importance of Cyber hygiene so
that hackers can be prevented, intelligent Malware and advanced by the service can be
stopped from accessing and corrupting the data gathered within the organisation every day
[3]. This is why it is important that the awareness of ICT organisations and its employees
about the cyber hygiene is researched thoroughly so that an idea can be gathered about the
vulnerability probability of these organisations from the malicious and intelligent hackers.
This would lead to provide solutions to the issues faced by organisations due to lack of
awareness in cyber hygiene. The impact of the malicious hackers can be detected in this way
due to the organisations not adapting to cyber hygiene regulations.
The objectives of the research can be described as follows:
To find out the possible cyber security procedure that ideally an ICT
organisation maintains.
To find out how these cyber security procedures lead to you are not authorised
access of malicious hackers.
To find out what basic cyber hygiene issues are occurring within an ICT
organisation that the devices are often found to be vulnerable to attacks by the
malicious hackers.
to maintain cyber hygiene. Sometimes few organisations are also found to be not implying
any cyber hygiene protocol at all within the organisation leading to possible vulnerability of
the organisation to threat.
Purpose/Objectives
The ever changing world of business has seen changes and enhancements in the threat
landscapes as well. With time, organisations must adapt to Cyber hygiene routine. It is much
important today to maintain a proper cyber hygiene routine within the organisation and
letting the employees within the organisation understand the importance of Cyber hygiene so
that hackers can be prevented, intelligent Malware and advanced by the service can be
stopped from accessing and corrupting the data gathered within the organisation every day
[3]. This is why it is important that the awareness of ICT organisations and its employees
about the cyber hygiene is researched thoroughly so that an idea can be gathered about the
vulnerability probability of these organisations from the malicious and intelligent hackers.
This would lead to provide solutions to the issues faced by organisations due to lack of
awareness in cyber hygiene. The impact of the malicious hackers can be detected in this way
due to the organisations not adapting to cyber hygiene regulations.
The objectives of the research can be described as follows:
To find out the possible cyber security procedure that ideally an ICT
organisation maintains.
To find out how these cyber security procedures lead to you are not authorised
access of malicious hackers.
To find out what basic cyber hygiene issues are occurring within an ICT
organisation that the devices are often found to be vulnerable to attacks by the
malicious hackers.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4RESEARCH PROPOSAL
To find out the solutions of how the cyber hygiene procedures can be
implemented in an IT organisation so that such ICT risk does not occur for the
computers and other devices in the organisation can be free of vulnerability to
the attackers by applying basic cyber hygiene.
From the above short term objectives that is to be defined as per the aims and
objective, the main objective of the research is to how the cyber hygiene procedures can be
implemented in an IT organisation to attain wholesome cyber security.
Hypotheses/Research questions
The hypothesis in this particular research can be phased in two ways:
H0: The ICT risk within an organisation is impacted due to lack of awareness in cyber
hygiene.
H1: The ICT risk within an organisation is not impacted due to the lack of awareness
in cyber hygiene.
The research questions for this research can be formed as below:
What are the basic cyber hygiene practices that ICT organisations are usually
found to be implying within the organisation?
What is the cyber security risk that occur due to the lack of awareness in cyber
hygiene within an organisation?
How do cyber hygiene reduce the risk of data vulnerability?
How can it be ensured that cyber hygiene and its maintenance would prevent
malicious attacks and malware threats to an organisation related to
Information and Communication Technology?
How the lack of awareness in cyber hygiene has been impacting the ICT
organisations on becoming vulnerable to data attacks and threats?
To find out the solutions of how the cyber hygiene procedures can be
implemented in an IT organisation so that such ICT risk does not occur for the
computers and other devices in the organisation can be free of vulnerability to
the attackers by applying basic cyber hygiene.
From the above short term objectives that is to be defined as per the aims and
objective, the main objective of the research is to how the cyber hygiene procedures can be
implemented in an IT organisation to attain wholesome cyber security.
Hypotheses/Research questions
The hypothesis in this particular research can be phased in two ways:
H0: The ICT risk within an organisation is impacted due to lack of awareness in cyber
hygiene.
H1: The ICT risk within an organisation is not impacted due to the lack of awareness
in cyber hygiene.
The research questions for this research can be formed as below:
What are the basic cyber hygiene practices that ICT organisations are usually
found to be implying within the organisation?
What is the cyber security risk that occur due to the lack of awareness in cyber
hygiene within an organisation?
How do cyber hygiene reduce the risk of data vulnerability?
How can it be ensured that cyber hygiene and its maintenance would prevent
malicious attacks and malware threats to an organisation related to
Information and Communication Technology?
How the lack of awareness in cyber hygiene has been impacting the ICT
organisations on becoming vulnerable to data attacks and threats?

5RESEARCH PROPOSAL
Significance of the study
The significance of the study can be given by understanding of a proper cyber security
hygiene rules and regulations that an organisation can imply [6]. By finding out the issues
that these organisations usually face with the lack of awareness in cyber hygiene, they can
bring about solution to the problem with this research.
Scope of the Study
Literature Review
As per the author Corradini and Nardelli (2019), it has been described that there are
several ICT organisations that do not understand how the organisation would probably
implement basic cyber security rules and regulations within an organisation that would
maintain the cyber hygiene. The author also points out that due to not maintaining the cyber
hygiene, there has been several problems in ICT organisation that has led to several
ransomware attacks and data vulnerability threats [5]. Organizations could not understand
why even after cyber security rules and regulations malicious hackers could pass by the
organisation data set. With further investigation it was found that it was simpler basic cyber
hygiene policies that the organisation could not follow.
Not understanding the basic cyber hygiene rules and regulations within an
organisation has often led to such problematic situations that confidential data has been
compromised and also there are several organisations that has lost customer base and
reputation as they have lost their monetary asset.
Methods and Materials
The methodology that would be used in this purpose would be the mixed method.
This will collect both primary and secondary data where the secondary data would be
Significance of the study
The significance of the study can be given by understanding of a proper cyber security
hygiene rules and regulations that an organisation can imply [6]. By finding out the issues
that these organisations usually face with the lack of awareness in cyber hygiene, they can
bring about solution to the problem with this research.
Scope of the Study
Literature Review
As per the author Corradini and Nardelli (2019), it has been described that there are
several ICT organisations that do not understand how the organisation would probably
implement basic cyber security rules and regulations within an organisation that would
maintain the cyber hygiene. The author also points out that due to not maintaining the cyber
hygiene, there has been several problems in ICT organisation that has led to several
ransomware attacks and data vulnerability threats [5]. Organizations could not understand
why even after cyber security rules and regulations malicious hackers could pass by the
organisation data set. With further investigation it was found that it was simpler basic cyber
hygiene policies that the organisation could not follow.
Not understanding the basic cyber hygiene rules and regulations within an
organisation has often led to such problematic situations that confidential data has been
compromised and also there are several organisations that has lost customer base and
reputation as they have lost their monetary asset.
Methods and Materials
The methodology that would be used in this purpose would be the mixed method.
This will collect both primary and secondary data where the secondary data would be
6RESEARCH PROPOSAL
collected from different authors and their writing and researches done on this subject. This
will found the base of a survey questionnaire that would include people from the ICT
organizations who provide that inputs on the question as provided for the analysis of the
collected primary data.
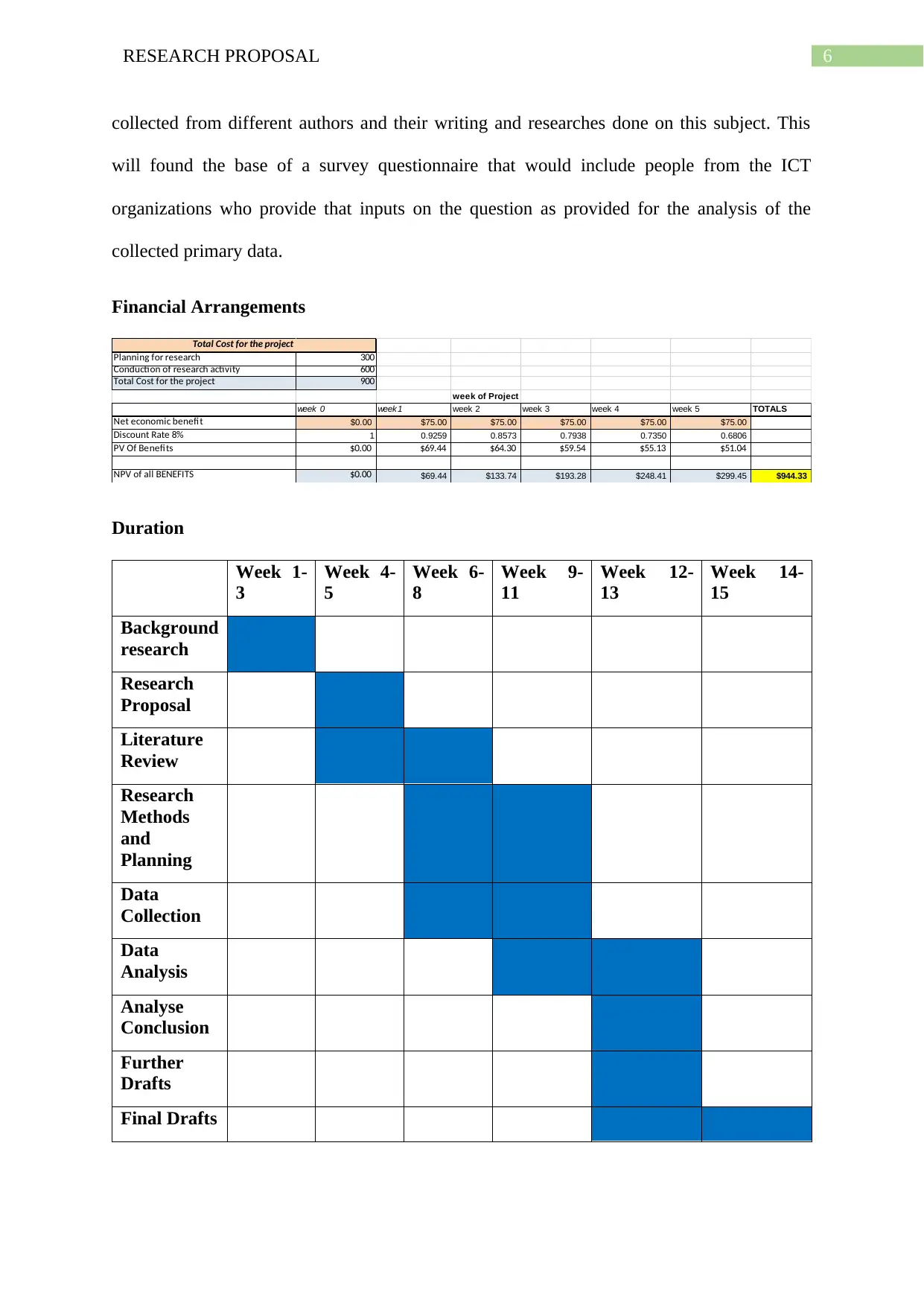
Financial Arrangements
Planning for research 300
Conduction of research activity 600
Total Cost for the project 900
week of Project
week 0 week 1 week 2 week 3 week 4 week 5 TOTALS
Net economic benefit $0.00 $75.00 $75.00 $75.00 $75.00 $75.00
Discount Rate 8% 1 0.9259 0.8573 0.7938 0.7350 0.6806
PV Of Benefits $0.00 $69.44 $64.30 $59.54 $55.13 $51.04
NPV of all BENEFITS $0.00 $69.44 $133.74 $193.28 $248.41 $299.45 $944.33
Total Cost for the project
Duration
Week 1-
3
Week 4-
5
Week 6-
8
Week 9-
11
Week 12-
13
Week 14-
15
Background
research
Research
Proposal
Literature
Review
Research
Methods
and
Planning
Data
Collection
Data
Analysis
Analyse
Conclusion
Further
Drafts
Final Drafts
collected from different authors and their writing and researches done on this subject. This
will found the base of a survey questionnaire that would include people from the ICT
organizations who provide that inputs on the question as provided for the analysis of the
collected primary data.
Financial Arrangements
Planning for research 300
Conduction of research activity 600
Total Cost for the project 900
week of Project
week 0 week 1 week 2 week 3 week 4 week 5 TOTALS
Net economic benefit $0.00 $75.00 $75.00 $75.00 $75.00 $75.00
Discount Rate 8% 1 0.9259 0.8573 0.7938 0.7350 0.6806
PV Of Benefits $0.00 $69.44 $64.30 $59.54 $55.13 $51.04
NPV of all BENEFITS $0.00 $69.44 $133.74 $193.28 $248.41 $299.45 $944.33
Total Cost for the project
Duration
Week 1-
3
Week 4-
5
Week 6-
8
Week 9-
11
Week 12-
13
Week 14-
15
Background
research
Research
Proposal
Literature
Review
Research
Methods
and
Planning
Data
Collection
Data
Analysis
Analyse
Conclusion
Further
Drafts
Final Drafts
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RESEARCH PROPOSAL

8RESEARCH PROPOSAL
References
[1] Maennel, K., Mäses, S. and Maennel, O., 2018, November. Cyber Hygiene: The Big
Picture. In Nordic Conference on Secure IT Systems (pp. 291-305). Springer, Cham.
[2] Vishwanath, A., Neo, L.S., Goh, P., Lee, S., Khader, M., Ong, G. and Chin, J., 2020.
Cyber hygiene: The concept, its measure, and its initial tests. Decision Support
Systems, 128, p.113160.
[3] Such, J.M., Ciholas, P., Rashid, A., Vidler, J. and Seabrook, T., 2019. Basic Cyber
Hygiene: Does It Work?. Computer, 52(4), pp.21-31.
[4] Ifinedo, P., Mengesha, N. and Longe, O., 2019, May. Factors that Influence Workers’
Participation in Unhygienic Cyber Practices: A Pilot Study from Nigeria. In International
Conference on Social Implications of Computers in Developing Countries (pp. 303-315).
Springer, Cham.
[5] Zwilling, M., Klien, G., Lesjak, D., Wiechetek, Ł., Cetin, F. and Basim, H.N., 2020.
Cyber Security Awareness, Knowledge and Behavior: A Comparative Study. Journal of
Computer Information Systems, pp.1-16.
[6] Corradini, I. and Nardelli, E., 2019, July. Social Engineering and the Value of Data: The
Need of Specific Awareness Programs. In International Conference on Applied Human
Factors and Ergonomics (pp. 59-65). Springer, Cham.
References
[1] Maennel, K., Mäses, S. and Maennel, O., 2018, November. Cyber Hygiene: The Big
Picture. In Nordic Conference on Secure IT Systems (pp. 291-305). Springer, Cham.
[2] Vishwanath, A., Neo, L.S., Goh, P., Lee, S., Khader, M., Ong, G. and Chin, J., 2020.
Cyber hygiene: The concept, its measure, and its initial tests. Decision Support
Systems, 128, p.113160.
[3] Such, J.M., Ciholas, P., Rashid, A., Vidler, J. and Seabrook, T., 2019. Basic Cyber
Hygiene: Does It Work?. Computer, 52(4), pp.21-31.
[4] Ifinedo, P., Mengesha, N. and Longe, O., 2019, May. Factors that Influence Workers’
Participation in Unhygienic Cyber Practices: A Pilot Study from Nigeria. In International
Conference on Social Implications of Computers in Developing Countries (pp. 303-315).
Springer, Cham.
[5] Zwilling, M., Klien, G., Lesjak, D., Wiechetek, Ł., Cetin, F. and Basim, H.N., 2020.
Cyber Security Awareness, Knowledge and Behavior: A Comparative Study. Journal of
Computer Information Systems, pp.1-16.
[6] Corradini, I. and Nardelli, E., 2019, July. Social Engineering and the Value of Data: The
Need of Specific Awareness Programs. In International Conference on Applied Human
Factors and Ergonomics (pp. 59-65). Springer, Cham.
1 out of 9
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.


