In-depth Report: Cyber Security Fraud, Scams & Identity Theft Analysis
VerifiedAdded on 2023/06/12
|10
|2775
|272
Report
AI Summary
This report provides an in-depth analysis of cyber security fraud, scams, and identity theft, highlighting the increasing threats to data and information security. It discusses various cybercrime methods, such as spamming, online identity theft, and hacking, emphasizing the importance of identifying and addressing these illegal activities. The report includes statistical evidence from the FTC, revealing a significant rise in fraud and identity theft complaints, costing the global economy trillions of dollars. Furthermore, it outlines several proactive measures organizations and individuals can implement to protect themselves from cyber threats, including continuous device updates, anti-virus software, strong password habits, employee training, security plan creation, and careful handling of online interactions. The report underscores the necessity for ongoing vigilance and adaptation to evolving cyber threats to safeguard sensitive information and maintain economic stability. Desklib offers a wealth of resources, including solved assignments and past papers, to support students in understanding complex topics like cyber security.

RESEARCH REPORT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents.
INTRODUCTION...........................................................................................................................3
MAIN BODY...................................................................................................................................3
Cybercrime ..................................................................................................................................3
Statistical Evidence of Cyber Crime ...........................................................................................6
CONCLUSION................................................................................................................................9
REFERENCES................................................................................................................................9
INTRODUCTION...........................................................................................................................3
MAIN BODY...................................................................................................................................3
Cybercrime ..................................................................................................................................3
Statistical Evidence of Cyber Crime ...........................................................................................6
CONCLUSION................................................................................................................................9
REFERENCES................................................................................................................................9

INTRODUCTION
Cyber Security frauds are the threats to the data and information by the hackers who try
to steal the sensitive and confidential information of the organizations and its customers. Many
organizations adopt the ways to protect and secure the data through various technologies and
software to safeguard the information (Hasham, Joshi and Mikkelsen, 2019.). People to steal the
sensitive information try to spam the mail inboxes and the communicating tools. Spam mean the
bulk messages that the hackers and advertisers send because of zero operating costs. They use it
to spread malware and other viruses which reduce the capacity of the tools to work and leak the
information.
The other way to conduct cybercrimes is online identity theft, in which people steal the personal
information, account details and signature through their email accounts or online shopping sites
where they have entered the information. Through the information, they act as that person and
steal the money and necessary documents,
This report will discuss about “ Cyber Security Fraud, Scam and Identity Theft”. It will
specify the meaning and the actions that can be taken against cyber security fraud and identity
theft. The report will represent statistical data on the frauds and scams happening in the world
and the safety measures that organization take to protect their customer' s useful and confidential
data from the hackers.
MAIN BODY
Cybercrime
The cyber crime is renowned as the computer crime in which the individual person conduct the
crime by utilizing the the computer as well as internet. The cybercrime, fraud, scam is increasing
rapidly as large numbers of the people are depend on the technology. The utilization of the new
technology increasing the opportunity of conducting crime. In order to control the internet illegal
activity it is important to determine the the theft as well as fraud. The I theft can be done when
the individual person have enough information or the data related to particular person or the
organisation (Deora and Chudasama,2021. The identification of theft is to be done even after the
death of the victim. In the online fraud the individual person done the theft of personal
information in context to commit the the fraud. In fraudster can determine the detail for
conducting the detail such as open bank accounts, detail which is link to mobile numbers, credit
as well as debit card etc. in the current situation many if the citizens are compromised with the
Cyber Security frauds are the threats to the data and information by the hackers who try
to steal the sensitive and confidential information of the organizations and its customers. Many
organizations adopt the ways to protect and secure the data through various technologies and
software to safeguard the information (Hasham, Joshi and Mikkelsen, 2019.). People to steal the
sensitive information try to spam the mail inboxes and the communicating tools. Spam mean the
bulk messages that the hackers and advertisers send because of zero operating costs. They use it
to spread malware and other viruses which reduce the capacity of the tools to work and leak the
information.
The other way to conduct cybercrimes is online identity theft, in which people steal the personal
information, account details and signature through their email accounts or online shopping sites
where they have entered the information. Through the information, they act as that person and
steal the money and necessary documents,
This report will discuss about “ Cyber Security Fraud, Scam and Identity Theft”. It will
specify the meaning and the actions that can be taken against cyber security fraud and identity
theft. The report will represent statistical data on the frauds and scams happening in the world
and the safety measures that organization take to protect their customer' s useful and confidential
data from the hackers.
MAIN BODY
Cybercrime
The cyber crime is renowned as the computer crime in which the individual person conduct the
crime by utilizing the the computer as well as internet. The cybercrime, fraud, scam is increasing
rapidly as large numbers of the people are depend on the technology. The utilization of the new
technology increasing the opportunity of conducting crime. In order to control the internet illegal
activity it is important to determine the the theft as well as fraud. The I theft can be done when
the individual person have enough information or the data related to particular person or the
organisation (Deora and Chudasama,2021. The identification of theft is to be done even after the
death of the victim. In the online fraud the individual person done the theft of personal
information in context to commit the the fraud. In fraudster can determine the detail for
conducting the detail such as open bank accounts, detail which is link to mobile numbers, credit
as well as debit card etc. in the current situation many if the citizens are compromised with the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

issues. Basically the cyber crime is to be done by hacking the personal as well as professional
accounts.
In the current period the online auction fraud is the most common fraud and most of the report
are register on the name of online fraud. In the online fraud the victim asked for the password as
well as account numbers which the financial institute never asked for Fontanilla,2020) . So it is
important to register the complaint and take action against the activity. Therefore the criminals
encourage people to make unnecessary transaction in order to access the information for the
robbery . in general the cybercrime includes the telephone communication or conversation and
due to various innovative programme it is hard to detect but not impossible to punish the
criminal. For conducting the crime the criminals offers various offered, bonus, rewards etc,. for
instance the people get notification like congratulation you have won the prices of lakhs rupees
clinch the link below to enjoy the experience and rewards.
The theft is to be done through the purchase of online shopping when the individual person
deliver the sensitive data to the other by sharing the contact detail, bank detail, credit or debit
card information and email. through the over utilization of the social media or online sites put the
consumer or the buyers at the risk. The malicious fake activity threaten the public and affect the
economic condition badly. In the situation of the covid 19 the fraud cases are increasing rapidly
because in order to deliver the protection the fake people call the citizen and asked for the
personal information for imitating the crimes. For the protection of the people it is important to
deliver to safety measure to the people as well as organisation. Along with the stooling of the
money the criminals or the fraud peoples harass and cyberbullying the citizen of the nation. As
per the records the higher authority detected 1.7 million fraud report are being registered due to
that the economy of the country is suffered the loss of $1.9 billion(Goutam, 2015.) . Moreover,
As per the lab observation the country is 375 malware threats per minute. Some measures should
be taken in order to protect the scams, frauds, cybercrime etc in the following manner.
Continuous updating of the device: it is considered as the important trick that the consumer or[
the business unit can used for protecting the data from any kind of illegal activity. The
cybercrime is mainly access the data due to operating software’s and the function used on the
computer as well as mobile phones. Through the continuous update the individual person can
determine the viruses and problems in effective manners. The updates allow the user to provide
security shield to the collection of the information. In order to update the features and software
accounts.
In the current period the online auction fraud is the most common fraud and most of the report
are register on the name of online fraud. In the online fraud the victim asked for the password as
well as account numbers which the financial institute never asked for Fontanilla,2020) . So it is
important to register the complaint and take action against the activity. Therefore the criminals
encourage people to make unnecessary transaction in order to access the information for the
robbery . in general the cybercrime includes the telephone communication or conversation and
due to various innovative programme it is hard to detect but not impossible to punish the
criminal. For conducting the crime the criminals offers various offered, bonus, rewards etc,. for
instance the people get notification like congratulation you have won the prices of lakhs rupees
clinch the link below to enjoy the experience and rewards.
The theft is to be done through the purchase of online shopping when the individual person
deliver the sensitive data to the other by sharing the contact detail, bank detail, credit or debit
card information and email. through the over utilization of the social media or online sites put the
consumer or the buyers at the risk. The malicious fake activity threaten the public and affect the
economic condition badly. In the situation of the covid 19 the fraud cases are increasing rapidly
because in order to deliver the protection the fake people call the citizen and asked for the
personal information for imitating the crimes. For the protection of the people it is important to
deliver to safety measure to the people as well as organisation. Along with the stooling of the
money the criminals or the fraud peoples harass and cyberbullying the citizen of the nation. As
per the records the higher authority detected 1.7 million fraud report are being registered due to
that the economy of the country is suffered the loss of $1.9 billion(Goutam, 2015.) . Moreover,
As per the lab observation the country is 375 malware threats per minute. Some measures should
be taken in order to protect the scams, frauds, cybercrime etc in the following manner.
Continuous updating of the device: it is considered as the important trick that the consumer or[
the business unit can used for protecting the data from any kind of illegal activity. The
cybercrime is mainly access the data due to operating software’s and the function used on the
computer as well as mobile phones. Through the continuous update the individual person can
determine the viruses and problems in effective manners. The updates allow the user to provide
security shield to the collection of the information. In order to update the features and software
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

regally the individual person can use the features of auto updating and manging the data. During
the updating of the computer or mobile if any illegal or unwanted activity is detected then it is
important to file a complaint against the unwanted activity ( Miedema,2018).
Employees anti-virus and anti-malware software: the fraud people or the
cybercriminals use some tools and techniques in order to initiate illegal activity. In the
cybercrime the victim directly attract the accounts of the person or the origination with
the utilization of viruses, botnets, malware, keyloggers as well ass spyware in order to
control and monitor the machines in appropriate manner. in context to that the
organisation supposed to buy the new machines which includes the anti-virus software
that are already installed in the computers, mobile or any sort of electronic devices that
collect the information. It is essential to make sure that the machine or the software is
delivering proper protection to the data. Along with that the detected virus should be
removed every week or on regular basis. So it’s better to take the subscription from
internet services providers in order to deliver security to the customers as well as
employees of the organisation. The cyber crime rise the issue of loyalty and the customer
got affect as well as not able to trust the brand easily.
passwords habits: in order to provide the security to the data it is good to utilized unique
password that the individual person can not access easily. Along with that the individual person
or the organisation suppose to use unique password for different websites and required to change
on the regular bases. In order to avoid the scam or fraud it is vital to create the strong and long
password in effective as well as efficient manner. in order to create strong password the
individual person can utilized the symbols, numbers or long spellings. The combination of the
symbols, numbers and alphabets do not allow the password to excess easily. The utilization of
the password vault allow the origination to keep the password safe at one secure place that help
the organisation for the long period of time (Whitty,2019).
Employees training: in order to avoid the scans or any crime that affect the value and
image of the company in domestic as well as international market can be improved by
providing the training to the employees of the organisation. Training to the workers
means acknowledging them with the pros and cons of the utilization of the internet and
saved themselves from the virus or theft of the data relate to company in appropriate
manner. in the training programme the origination provide the information related to
the updating of the computer or mobile if any illegal or unwanted activity is detected then it is
important to file a complaint against the unwanted activity ( Miedema,2018).
Employees anti-virus and anti-malware software: the fraud people or the
cybercriminals use some tools and techniques in order to initiate illegal activity. In the
cybercrime the victim directly attract the accounts of the person or the origination with
the utilization of viruses, botnets, malware, keyloggers as well ass spyware in order to
control and monitor the machines in appropriate manner. in context to that the
organisation supposed to buy the new machines which includes the anti-virus software
that are already installed in the computers, mobile or any sort of electronic devices that
collect the information. It is essential to make sure that the machine or the software is
delivering proper protection to the data. Along with that the detected virus should be
removed every week or on regular basis. So it’s better to take the subscription from
internet services providers in order to deliver security to the customers as well as
employees of the organisation. The cyber crime rise the issue of loyalty and the customer
got affect as well as not able to trust the brand easily.
passwords habits: in order to provide the security to the data it is good to utilized unique
password that the individual person can not access easily. Along with that the individual person
or the organisation suppose to use unique password for different websites and required to change
on the regular bases. In order to avoid the scam or fraud it is vital to create the strong and long
password in effective as well as efficient manner. in order to create strong password the
individual person can utilized the symbols, numbers or long spellings. The combination of the
symbols, numbers and alphabets do not allow the password to excess easily. The utilization of
the password vault allow the origination to keep the password safe at one secure place that help
the organisation for the long period of time (Whitty,2019).
Employees training: in order to avoid the scans or any crime that affect the value and
image of the company in domestic as well as international market can be improved by
providing the training to the employees of the organisation. Training to the workers
means acknowledging them with the pros and cons of the utilization of the internet and
saved themselves from the virus or theft of the data relate to company in appropriate
manner. in the training programme the origination provide the information related to

information technology and deliver the knowledge and skills related to the security
practices in order to get safe operations and obtain success in the marketplace
( Pahrudin,2020.). it give assistance in boulting the trust between the members of the
company. with the assistance of that the workers are able to deliver the warning sign to
the origination in context to proceed the company from forthcoming threats and scams.
Training and development programme men’s providing education to the working people
delivering services within the organisation. The training suppose to provide on the
regular basis as the technology acquiring continues innovation in the modern world.
Creation of security plan: a system of security plan includes the practices of the
security and secure the collection of the information. These features identify the limited
access to authorized customers and make sure that the workers are responding to the
security branch or not. The security system includes hardware, security measure, software
along with the training method.
Online stalking case: in the any members of the origination detect any kind of online
stalking from tiny unwanted or reorganized person then it is important to focused on the
data protection. In the case of online staking it is mentored to avoid online conversation
with the chatbots or the robots as they consume the information of the individual person
as well as organisation. The particular person need to ignore the spam messages or mail
received from the unrecognised websites. In context to that the person suppose to block
on the social media or on emails in effective as well as efficient manner(Shah and
Chudasama 2021).
Control over the information: in context to avoid the illegal activity the individual
person should make sure that the information is not accessible by the peoples. Along with
that the organisation and the employees need to control the sharing of the information
with the other members. The information should be protected and share with the
trustworthy employees and with the limited people that contributed in increasing the sales
of the company and willing to increase the growth scale of the company.
Statistical Evidence of Cyber Crime
From the data , collected from the records of FTC (Federal Trade Commission), that
maintained the data regarding the consumer frauds and identity thefts complaints it is found that
an average of 4.5 million complaints received in the year 2020 by the FTC which is more than
practices in order to get safe operations and obtain success in the marketplace
( Pahrudin,2020.). it give assistance in boulting the trust between the members of the
company. with the assistance of that the workers are able to deliver the warning sign to
the origination in context to proceed the company from forthcoming threats and scams.
Training and development programme men’s providing education to the working people
delivering services within the organisation. The training suppose to provide on the
regular basis as the technology acquiring continues innovation in the modern world.
Creation of security plan: a system of security plan includes the practices of the
security and secure the collection of the information. These features identify the limited
access to authorized customers and make sure that the workers are responding to the
security branch or not. The security system includes hardware, security measure, software
along with the training method.
Online stalking case: in the any members of the origination detect any kind of online
stalking from tiny unwanted or reorganized person then it is important to focused on the
data protection. In the case of online staking it is mentored to avoid online conversation
with the chatbots or the robots as they consume the information of the individual person
as well as organisation. The particular person need to ignore the spam messages or mail
received from the unrecognised websites. In context to that the person suppose to block
on the social media or on emails in effective as well as efficient manner(Shah and
Chudasama 2021).
Control over the information: in context to avoid the illegal activity the individual
person should make sure that the information is not accessible by the peoples. Along with
that the organisation and the employees need to control the sharing of the information
with the other members. The information should be protected and share with the
trustworthy employees and with the limited people that contributed in increasing the sales
of the company and willing to increase the growth scale of the company.
Statistical Evidence of Cyber Crime
From the data , collected from the records of FTC (Federal Trade Commission), that
maintained the data regarding the consumer frauds and identity thefts complaints it is found that
an average of 4.5 million complaints received in the year 2020 by the FTC which is more than
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
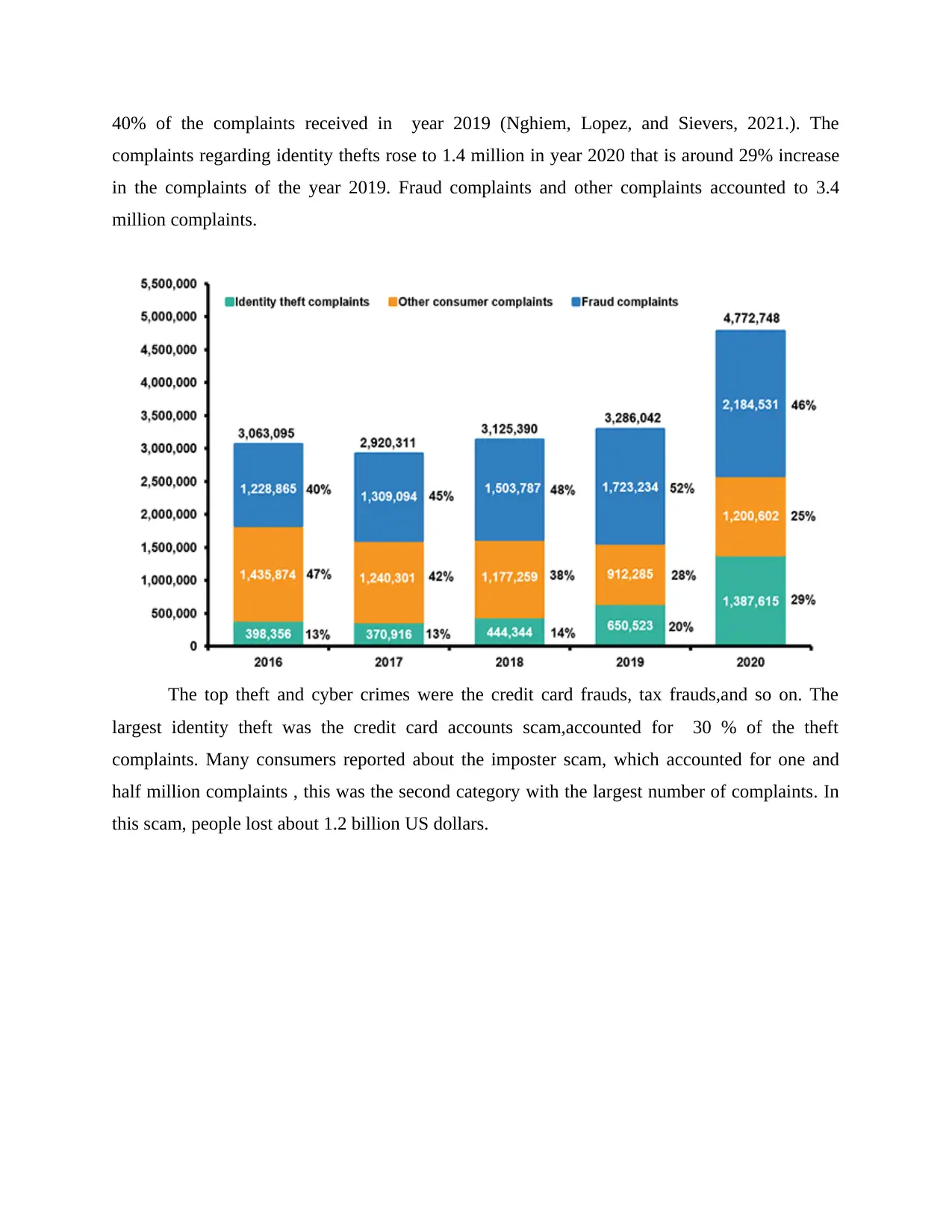
40% of the complaints received in year 2019 (Nghiem, Lopez, and Sievers, 2021.). The
complaints regarding identity thefts rose to 1.4 million in year 2020 that is around 29% increase
in the complaints of the year 2019. Fraud complaints and other complaints accounted to 3.4
million complaints.
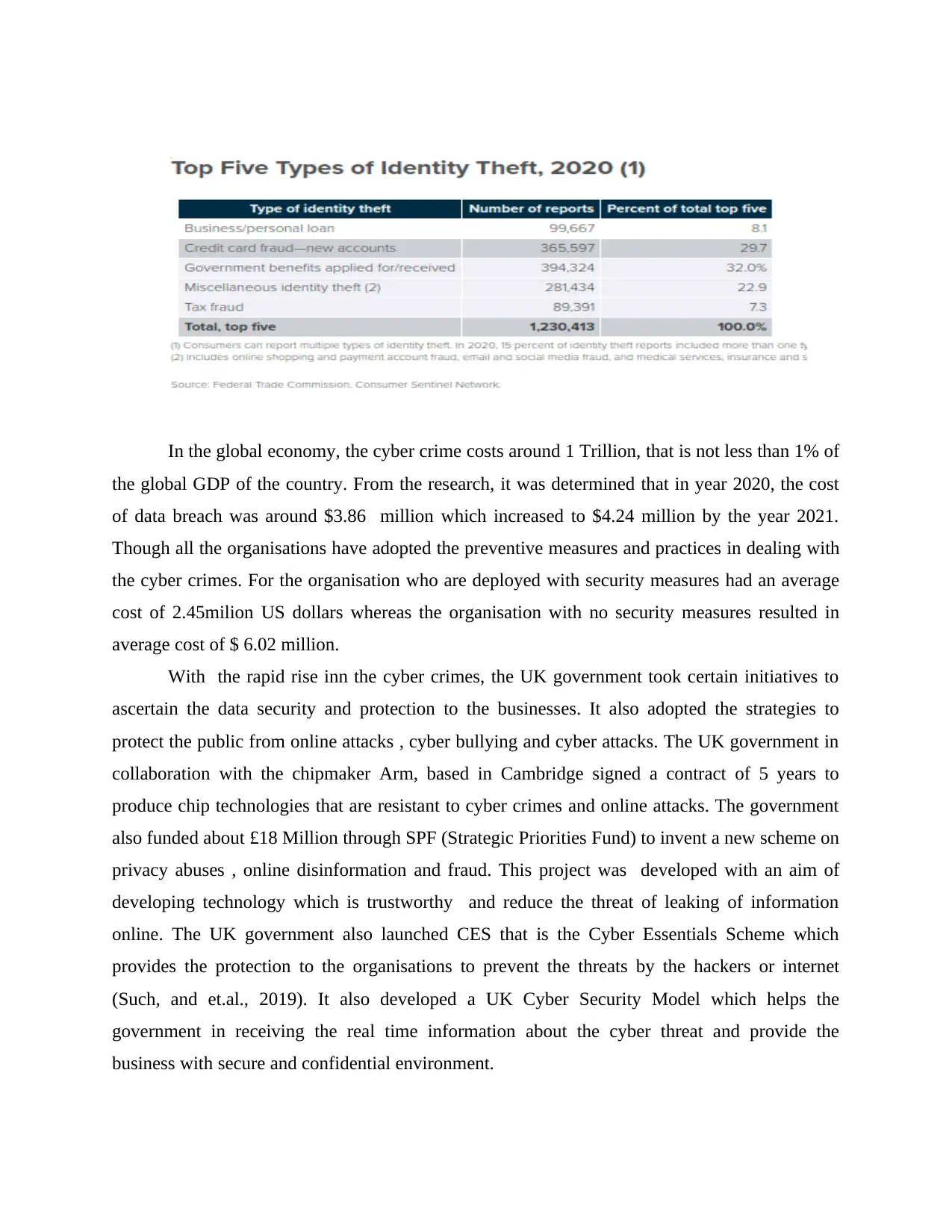
The top theft and cyber crimes were the credit card frauds, tax frauds,and so on. The
largest identity theft was the credit card accounts scam,accounted for 30 % of the theft
complaints. Many consumers reported about the imposter scam, which accounted for one and
half million complaints , this was the second category with the largest number of complaints. In
this scam, people lost about 1.2 billion US dollars.
complaints regarding identity thefts rose to 1.4 million in year 2020 that is around 29% increase
in the complaints of the year 2019. Fraud complaints and other complaints accounted to 3.4
million complaints.
The top theft and cyber crimes were the credit card frauds, tax frauds,and so on. The
largest identity theft was the credit card accounts scam,accounted for 30 % of the theft
complaints. Many consumers reported about the imposter scam, which accounted for one and
half million complaints , this was the second category with the largest number of complaints. In
this scam, people lost about 1.2 billion US dollars.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
In the global economy, the cyber crime costs around 1 Trillion, that is not less than 1% of
the global GDP of the country. From the research, it was determined that in year 2020, the cost
of data breach was around $3.86 million which increased to $4.24 million by the year 2021.
Though all the organisations have adopted the preventive measures and practices in dealing with
the cyber crimes. For the organisation who are deployed with security measures had an average
cost of 2.45milion US dollars whereas the organisation with no security measures resulted in
average cost of $ 6.02 million.
With the rapid rise inn the cyber crimes, the UK government took certain initiatives to
ascertain the data security and protection to the businesses. It also adopted the strategies to
protect the public from online attacks , cyber bullying and cyber attacks. The UK government in
collaboration with the chipmaker Arm, based in Cambridge signed a contract of 5 years to
produce chip technologies that are resistant to cyber crimes and online attacks. The government
also funded about £18 Million through SPF (Strategic Priorities Fund) to invent a new scheme on
privacy abuses , online disinformation and fraud. This project was developed with an aim of
developing technology which is trustworthy and reduce the threat of leaking of information
online. The UK government also launched CES that is the Cyber Essentials Scheme which
provides the protection to the organisations to prevent the threats by the hackers or internet
(Such, and et.al., 2019). It also developed a UK Cyber Security Model which helps the
government in receiving the real time information about the cyber threat and provide the
business with secure and confidential environment.
the global GDP of the country. From the research, it was determined that in year 2020, the cost
of data breach was around $3.86 million which increased to $4.24 million by the year 2021.
Though all the organisations have adopted the preventive measures and practices in dealing with
the cyber crimes. For the organisation who are deployed with security measures had an average
cost of 2.45milion US dollars whereas the organisation with no security measures resulted in
average cost of $ 6.02 million.
With the rapid rise inn the cyber crimes, the UK government took certain initiatives to
ascertain the data security and protection to the businesses. It also adopted the strategies to
protect the public from online attacks , cyber bullying and cyber attacks. The UK government in
collaboration with the chipmaker Arm, based in Cambridge signed a contract of 5 years to
produce chip technologies that are resistant to cyber crimes and online attacks. The government
also funded about £18 Million through SPF (Strategic Priorities Fund) to invent a new scheme on
privacy abuses , online disinformation and fraud. This project was developed with an aim of
developing technology which is trustworthy and reduce the threat of leaking of information
online. The UK government also launched CES that is the Cyber Essentials Scheme which
provides the protection to the organisations to prevent the threats by the hackers or internet
(Such, and et.al., 2019). It also developed a UK Cyber Security Model which helps the
government in receiving the real time information about the cyber threat and provide the
business with secure and confidential environment.

CONCLUSION
From the report it is concluded that nowadays cyber attacks and frauds are practised in the
businesses and general environment to leak and steal the confidential and private information on
the public. This involves the business secrets, account details and many more information. The
hackers and cyber criminals also practice identity thefts to take advantage of someone's position
and details. The report discussed the various measures which can be adopted by business and
people to avoid the leak of information such as strong passwords, updating their systems
regularly to avoid attacking through viruses and malware and so on. The government also take
preventive measures to safeguard the important information of the organisation and public and
for that they launched various programmes and schemes. The report also specified the data
regarding the cyber crimes prevailing in the world.
REFERENCES
Books and journals
Deora, R.S. and Chudasama, D., 2021. Brief study of cybercrime on an internet. Journal of
Communication Engineering & Systems, 11(1), pp.1-6.
Fontanilla, M.V., 2020. Cybercrime pandemic. Eubios Journal of Asian and International
Bioethics, 30(4), pp.161-165.
Goutam, R.K., 2015. Importance of cyber security. International Journal of Computer
Applications, 111(7).
Miedema, T.E., 2018. Consumer protection in cyber space and the ethics of stewardship. Journal
of consumer policy, 41(1), pp.55-75.
Pahrudin, P., 2020. Cybercrime in the Context of Cellular Telephone Scams. Jurnal Penelitian
Pos dan Informatika, 10(1), pp.73-85.
Shah, A. and Chudasama, D., 2021. Investigating Various Approaches and Ways to Detect
Cybercrime. Journal of Network Security, 9(2), pp.12-20p.
Whitty, M.T., 2019. Predicting susceptibility to cyber-fraud victimhood. Journal of Financial
Crime.
Hasham, S., Joshi, S. and Mikkelsen, D., 2019. Financial crime and fraud in the age of
cybersecurity. McKinsey & Company, pp.1-11.
Such, J. M., and et.al., 2019. Basic cyber hygiene: does it work?. Computer. 52(4). pp.21-31.
From the report it is concluded that nowadays cyber attacks and frauds are practised in the
businesses and general environment to leak and steal the confidential and private information on
the public. This involves the business secrets, account details and many more information. The
hackers and cyber criminals also practice identity thefts to take advantage of someone's position
and details. The report discussed the various measures which can be adopted by business and
people to avoid the leak of information such as strong passwords, updating their systems
regularly to avoid attacking through viruses and malware and so on. The government also take
preventive measures to safeguard the important information of the organisation and public and
for that they launched various programmes and schemes. The report also specified the data
regarding the cyber crimes prevailing in the world.
REFERENCES
Books and journals
Deora, R.S. and Chudasama, D., 2021. Brief study of cybercrime on an internet. Journal of
Communication Engineering & Systems, 11(1), pp.1-6.
Fontanilla, M.V., 2020. Cybercrime pandemic. Eubios Journal of Asian and International
Bioethics, 30(4), pp.161-165.
Goutam, R.K., 2015. Importance of cyber security. International Journal of Computer
Applications, 111(7).
Miedema, T.E., 2018. Consumer protection in cyber space and the ethics of stewardship. Journal
of consumer policy, 41(1), pp.55-75.
Pahrudin, P., 2020. Cybercrime in the Context of Cellular Telephone Scams. Jurnal Penelitian
Pos dan Informatika, 10(1), pp.73-85.
Shah, A. and Chudasama, D., 2021. Investigating Various Approaches and Ways to Detect
Cybercrime. Journal of Network Security, 9(2), pp.12-20p.
Whitty, M.T., 2019. Predicting susceptibility to cyber-fraud victimhood. Journal of Financial
Crime.
Hasham, S., Joshi, S. and Mikkelsen, D., 2019. Financial crime and fraud in the age of
cybersecurity. McKinsey & Company, pp.1-11.
Such, J. M., and et.al., 2019. Basic cyber hygiene: does it work?. Computer. 52(4). pp.21-31.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Nghiem, C., Lopez, D. and Sievers, A., 2021. FEDERAL TRADE COMMISSION V.
FACEBOOK: A Case Study of the Effects of Antitrust Laws on Consumers’ Data
Privacy Protection. The Maastricht Journal of Liberal Arts. 13.
FACEBOOK: A Case Study of the Effects of Antitrust Laws on Consumers’ Data
Privacy Protection. The Maastricht Journal of Liberal Arts. 13.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




