The Role of Blockchain Technology in Modern Cyber Security
VerifiedAdded on 2023/03/17
|15
|4158
|24
Report
AI Summary
This report provides an in-depth analysis of blockchain technology's role in cyber security. It begins with an introduction to blockchain, defining it as a distributed database and public ledger used for digital events. The report explores blockchain's application in various domains, focusing on its potential to shift the offense-defense balance in cyberspace. It discusses the features of cyberspace, the theory of offense and defense, and how blockchain technology can impact data integrity. The report explains the working mechanism of blockchain from the perspective of distributed ledger technology, covering key principles like private key cryptography, distributed networks, and incentive mechanisms. It examines the application of blockchain to data integrity, highlighting its role as a digital ledger for recording transactions and ensuring accuracy and reliability. The report references various sources to support its arguments, providing a comprehensive overview of blockchain's impact on cyber security.

Running head: CYBER SECURITY
CYBER SECURITY
Name of the Student
Name of the University
Author Note:
CYBER SECURITY
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY
Introduction
Blockchain Technology can be stated as a distributed database of records or public
ledger, which is completely based on various digital events. It is mainly needed for execution
and share of participants of parties. In this, each of transaction in public ledger is completely
verified by large number of participants of the system. As soon as the information is entered it
will be never being completely erased (Crosby et al. 2016). Blockchain technology aims to
maintain the record of each and every transaction that is made by the user. Blockchain to
decentralize peer-to-peer currency which is make use of blockchain technology. Digital
technology is very much controversial topic which has blockchain technology that has worked
flawlessly. It is mainly needed for wide range of application in both the terms that is financial
and non-financial domain (Zheng et al. 2017). Blockchain technology aims to create a proper
system by establishing a consensus in the whole digital world. It will be merely help the parties
for understanding certain number of digital events that is needed for recording public ledger
(Pilkington 2016). This particular technology aims to open up a door which is needed for
developing a democratic open and digital economy instead of centralized one. At present, there
are large number of benefits in the domain of disruptive technology and the whole revolution in
the space that has come into picture. Blockchain technology comes up with huge number of
application in both kind of sector that is financial and non-financial.
In the coming pages of the report, an idea has been provided concerning how blockchain
technology will shift the overall offence-defence balance in whole cyberspace. A proper debate
has been provided with cyberspace, which is dominating the whole offence-defence theory. A
proper description has been providing concerning the working mechanism of blockchain
technology from the perspective of distributed ledger technology to a government firm. The
Introduction
Blockchain Technology can be stated as a distributed database of records or public
ledger, which is completely based on various digital events. It is mainly needed for execution
and share of participants of parties. In this, each of transaction in public ledger is completely
verified by large number of participants of the system. As soon as the information is entered it
will be never being completely erased (Crosby et al. 2016). Blockchain technology aims to
maintain the record of each and every transaction that is made by the user. Blockchain to
decentralize peer-to-peer currency which is make use of blockchain technology. Digital
technology is very much controversial topic which has blockchain technology that has worked
flawlessly. It is mainly needed for wide range of application in both the terms that is financial
and non-financial domain (Zheng et al. 2017). Blockchain technology aims to create a proper
system by establishing a consensus in the whole digital world. It will be merely help the parties
for understanding certain number of digital events that is needed for recording public ledger
(Pilkington 2016). This particular technology aims to open up a door which is needed for
developing a democratic open and digital economy instead of centralized one. At present, there
are large number of benefits in the domain of disruptive technology and the whole revolution in
the space that has come into picture. Blockchain technology comes up with huge number of
application in both kind of sector that is financial and non-financial.
In the coming pages of the report, an idea has been provided concerning how blockchain
technology will shift the overall offence-defence balance in whole cyberspace. A proper debate
has been provided with cyberspace, which is dominating the whole offence-defence theory. A
proper description has been providing concerning the working mechanism of blockchain
technology from the perspective of distributed ledger technology to a government firm. The

2CYBER SECURITY
application of blockchain technology to data integrity has analysed both direction and
magnitude.
Discussion
Blockchain will shift offence-defence balance in Cyberspace
With time, government are becoming very much involved in its cyberspace for military.
It is considered to be a cyber-domain, which is known to be an important part of security
strategies (Biswas and Muthukkumarasamy 2016). Due to growth of reliance of cyber-assets
there is a need for much deeper investigation on the overall features of cyberspace along with
call for impact on state rivalry. In the coming pages of the report, offence-defence theory for
discussion of cyberspace that has become an incentive for making use of force. The theory of
offensive and defensive is considered to be very much expensive in comparison to offence.
There are mainly three important features for the advantage of over the defence for the place of
vulnerabilities (Wright and De Filippi 2015). There is large number of areas of overall
improvement for defence and offence technologies which is known to be a difficult attribute. In
the coming days, the areas of cyber-attack in the future will become very much common.
Government has become very much conscious about the overall capabilities that are more
specifically, the vulnerabilities in the whole cyberspace. In the coming years, it is expected that it
will ultimately the overall strategies. Offence Defence theory is completely concerned with the
issues in the international topics that have dilemma and escalation (Sikorski, Haughton and Kraft
2017). ODB theory aims to predict the systematic outcome and overall possibility of the wars
and tendency to increase the overall aims of the wars. In some cases, defence is considered to be
very much easier in comparison to offence where the states will have many incentives to
cooperate. It is all about binding huge number of strategies and engaging various policies.
application of blockchain technology to data integrity has analysed both direction and
magnitude.
Discussion
Blockchain will shift offence-defence balance in Cyberspace
With time, government are becoming very much involved in its cyberspace for military.
It is considered to be a cyber-domain, which is known to be an important part of security
strategies (Biswas and Muthukkumarasamy 2016). Due to growth of reliance of cyber-assets
there is a need for much deeper investigation on the overall features of cyberspace along with
call for impact on state rivalry. In the coming pages of the report, offence-defence theory for
discussion of cyberspace that has become an incentive for making use of force. The theory of
offensive and defensive is considered to be very much expensive in comparison to offence.
There are mainly three important features for the advantage of over the defence for the place of
vulnerabilities (Wright and De Filippi 2015). There is large number of areas of overall
improvement for defence and offence technologies which is known to be a difficult attribute. In
the coming days, the areas of cyber-attack in the future will become very much common.
Government has become very much conscious about the overall capabilities that are more
specifically, the vulnerabilities in the whole cyberspace. In the coming years, it is expected that it
will ultimately the overall strategies. Offence Defence theory is completely concerned with the
issues in the international topics that have dilemma and escalation (Sikorski, Haughton and Kraft
2017). ODB theory aims to predict the systematic outcome and overall possibility of the wars
and tendency to increase the overall aims of the wars. In some cases, defence is considered to be
very much easier in comparison to offence where the states will have many incentives to
cooperate. It is all about binding huge number of strategies and engaging various policies.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY
Cyberspace will affect the offence-defence dominant
Cyberspace can easily provide someone with the ability for attacking with the given
keystroke. It comes up with need of deployment of a physical force by which there can be easily
physical access to some of the important region. There is a need for deploying some physical
force can have physical access to region (Raval 2016). Cyber is not generally affected due to
environment concern or any kind of weather condition. For some given value, they can have
things undertaken relentlessly without a period. Cyberspace needs to be virtually constrained that
work by against most of the target. It does not require any kind of physical resource for working
with physical action (Zhang and Wen 2017). At present, there are wide variety of actors that
tends to operate in the whole cyberspace. The whole cyberspace comes up with three main areas
like physical network, logical network and cyberspace persona.
Physical Network: It mainly comprises of hardware like cables and system that exists in
various places of the world (Meng et al. 2018). It merely tends to exits in the state that has
sovereignty for its given components. They need to obey all the required law of the state in
which it tends to reside.
Logical Network: It can be stated as the software which tends to operate in the given
network along with manifestation of the given web pages. In this election aims to make the
logical bound of the network.
Cyber- Persona: It is completely made up list of people who are completely operating in
the given cyber-space (Treleaven, Brown and Yang 2017). Similar to physical network, it comes
up with states for required laws and policies.
There is mainly four main kinds of cyberspace that aims to space the cognition of cyber-
space that is CSR (Cyber Surveillance and Reconnaissance), OPE and lastly cyberspace attacks.
Cyberspace will affect the offence-defence dominant
Cyberspace can easily provide someone with the ability for attacking with the given
keystroke. It comes up with need of deployment of a physical force by which there can be easily
physical access to some of the important region. There is a need for deploying some physical
force can have physical access to region (Raval 2016). Cyber is not generally affected due to
environment concern or any kind of weather condition. For some given value, they can have
things undertaken relentlessly without a period. Cyberspace needs to be virtually constrained that
work by against most of the target. It does not require any kind of physical resource for working
with physical action (Zhang and Wen 2017). At present, there are wide variety of actors that
tends to operate in the whole cyberspace. The whole cyberspace comes up with three main areas
like physical network, logical network and cyberspace persona.
Physical Network: It mainly comprises of hardware like cables and system that exists in
various places of the world (Meng et al. 2018). It merely tends to exits in the state that has
sovereignty for its given components. They need to obey all the required law of the state in
which it tends to reside.
Logical Network: It can be stated as the software which tends to operate in the given
network along with manifestation of the given web pages. In this election aims to make the
logical bound of the network.
Cyber- Persona: It is completely made up list of people who are completely operating in
the given cyber-space (Treleaven, Brown and Yang 2017). Similar to physical network, it comes
up with states for required laws and policies.
There is mainly four main kinds of cyberspace that aims to space the cognition of cyber-
space that is CSR (Cyber Surveillance and Reconnaissance), OPE and lastly cyberspace attacks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBER SECURITY
It can be either of the following that is defensive or offensive. Operation of cyber-space tends to
have huge majority of military activities. Offensive cyber operation is considered to be rarer ones
(Atzori, 2015). In this, none of the given cyberspace needs reconnaissance and preparation. It is
completely shaping the whole information, which is completely ubiquitous in the present society.
There is huge number of components of performing the present shaping cognition in intelligence
operation.
Description of working of blockchain from the perspective of Distributive
Ledger Technology
Blockchain can be considered to be as one of the types of distributed ledger which comes
up with independent system. It is mainly needed for recording, sharing and proper
synchronization of electronic ledger. Blockchain aims to organize the given data into blocks
which is completely change in the append mode (Ølnes, Ubacht and Janssen 2017). DTL
blockchain is known to be building block for value of internet and helps in interaction and
transfer. It is expected that distributed ledger technology can easily make changes in the whole
financial sector, making it very much efficient and overall reliability. There are mainly three key
principles for creating a blockchain. The technologies are private key technologies like private
key cryptography, distributive network with shared ledger and lastly incentive for service of the
network transaction (Nofer et al. 2017). The main part of cryptographic key is all about
analysing every component of blockchain technology for creating security of digital identity. The
given identity is completely based on the possession, which is the combination of both public
and private cryptographic keys. Overall combination of the given keys can be used for creating
proper digital signature.
It can be either of the following that is defensive or offensive. Operation of cyber-space tends to
have huge majority of military activities. Offensive cyber operation is considered to be rarer ones
(Atzori, 2015). In this, none of the given cyberspace needs reconnaissance and preparation. It is
completely shaping the whole information, which is completely ubiquitous in the present society.
There is huge number of components of performing the present shaping cognition in intelligence
operation.
Description of working of blockchain from the perspective of Distributive
Ledger Technology
Blockchain can be considered to be as one of the types of distributed ledger which comes
up with independent system. It is mainly needed for recording, sharing and proper
synchronization of electronic ledger. Blockchain aims to organize the given data into blocks
which is completely change in the append mode (Ølnes, Ubacht and Janssen 2017). DTL
blockchain is known to be building block for value of internet and helps in interaction and
transfer. It is expected that distributed ledger technology can easily make changes in the whole
financial sector, making it very much efficient and overall reliability. There are mainly three key
principles for creating a blockchain. The technologies are private key technologies like private
key cryptography, distributive network with shared ledger and lastly incentive for service of the
network transaction (Nofer et al. 2017). The main part of cryptographic key is all about
analysing every component of blockchain technology for creating security of digital identity. The
given identity is completely based on the possession, which is the combination of both public
and private cryptographic keys. Overall combination of the given keys can be used for creating
proper digital signature.
5CYBER SECURITY
Identity: It needs to have strong control of the overall ownership of secure digital
relationship (Ouaddah, Elkalam and Ouahman 2017). At the time of authentication that needs to
be solved, which is a combination of certain number of means which required transition and
permission.
Distributed Network: There is large number of benefits and need of distributed network
that can be easily understood by the help of experiment. Major of the bitcoin blockchain tends to
work for some of the large network where validators come into play (Apte and Petrovsky 2016).
The point can be concluded that overall size of the network is known to be an important aspect
for securing network.
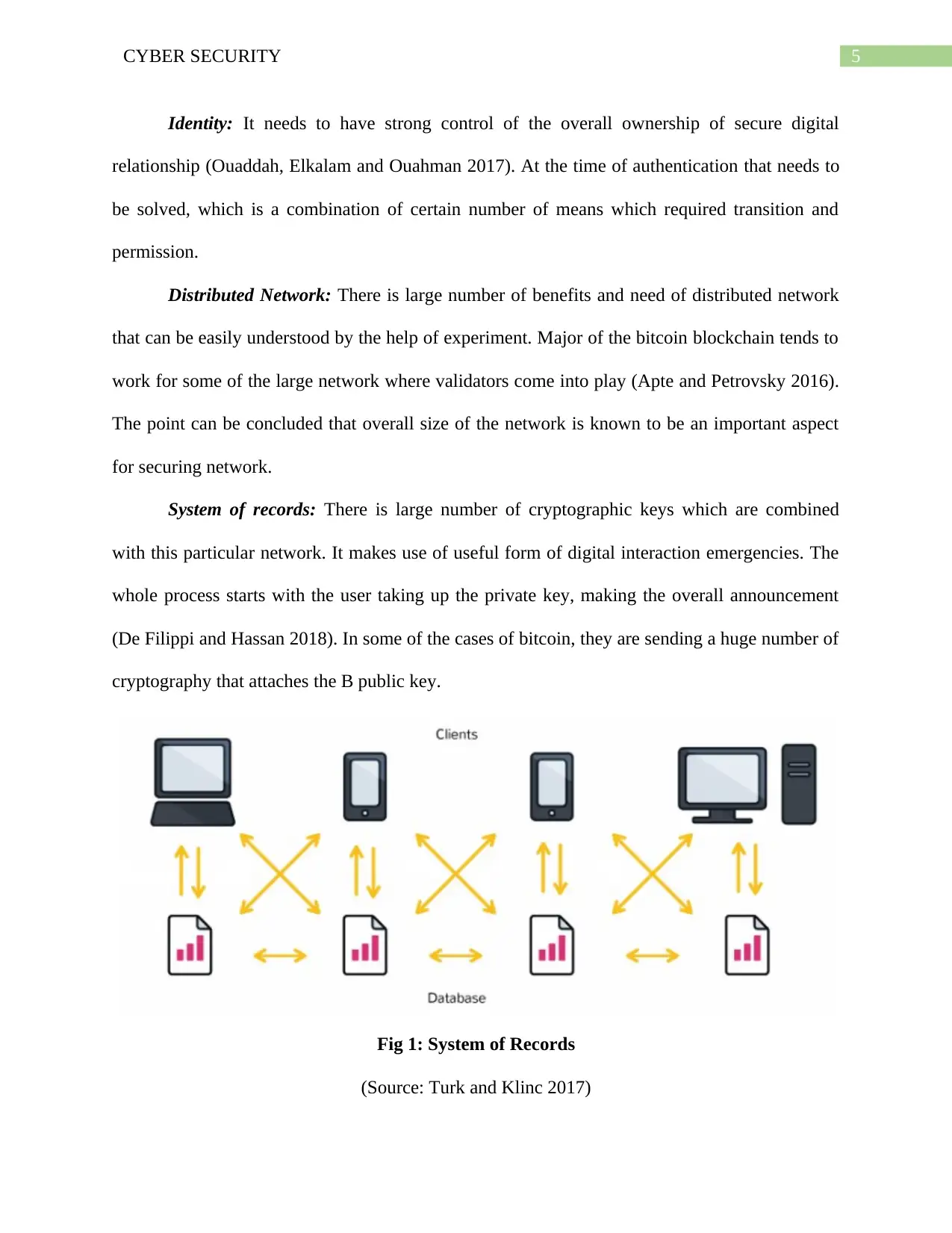
System of records: There is large number of cryptographic keys which are combined
with this particular network. It makes use of useful form of digital interaction emergencies. The
whole process starts with the user taking up the private key, making the overall announcement
(De Filippi and Hassan 2018). In some of the cases of bitcoin, they are sending a huge number of
cryptography that attaches the B public key.
Fig 1: System of Records
(Source: Turk and Klinc 2017)
Identity: It needs to have strong control of the overall ownership of secure digital
relationship (Ouaddah, Elkalam and Ouahman 2017). At the time of authentication that needs to
be solved, which is a combination of certain number of means which required transition and
permission.
Distributed Network: There is large number of benefits and need of distributed network
that can be easily understood by the help of experiment. Major of the bitcoin blockchain tends to
work for some of the large network where validators come into play (Apte and Petrovsky 2016).
The point can be concluded that overall size of the network is known to be an important aspect
for securing network.
System of records: There is large number of cryptographic keys which are combined
with this particular network. It makes use of useful form of digital interaction emergencies. The
whole process starts with the user taking up the private key, making the overall announcement
(De Filippi and Hassan 2018). In some of the cases of bitcoin, they are sending a huge number of
cryptography that attaches the B public key.
Fig 1: System of Records
(Source: Turk and Klinc 2017)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6CYBER SECURITY
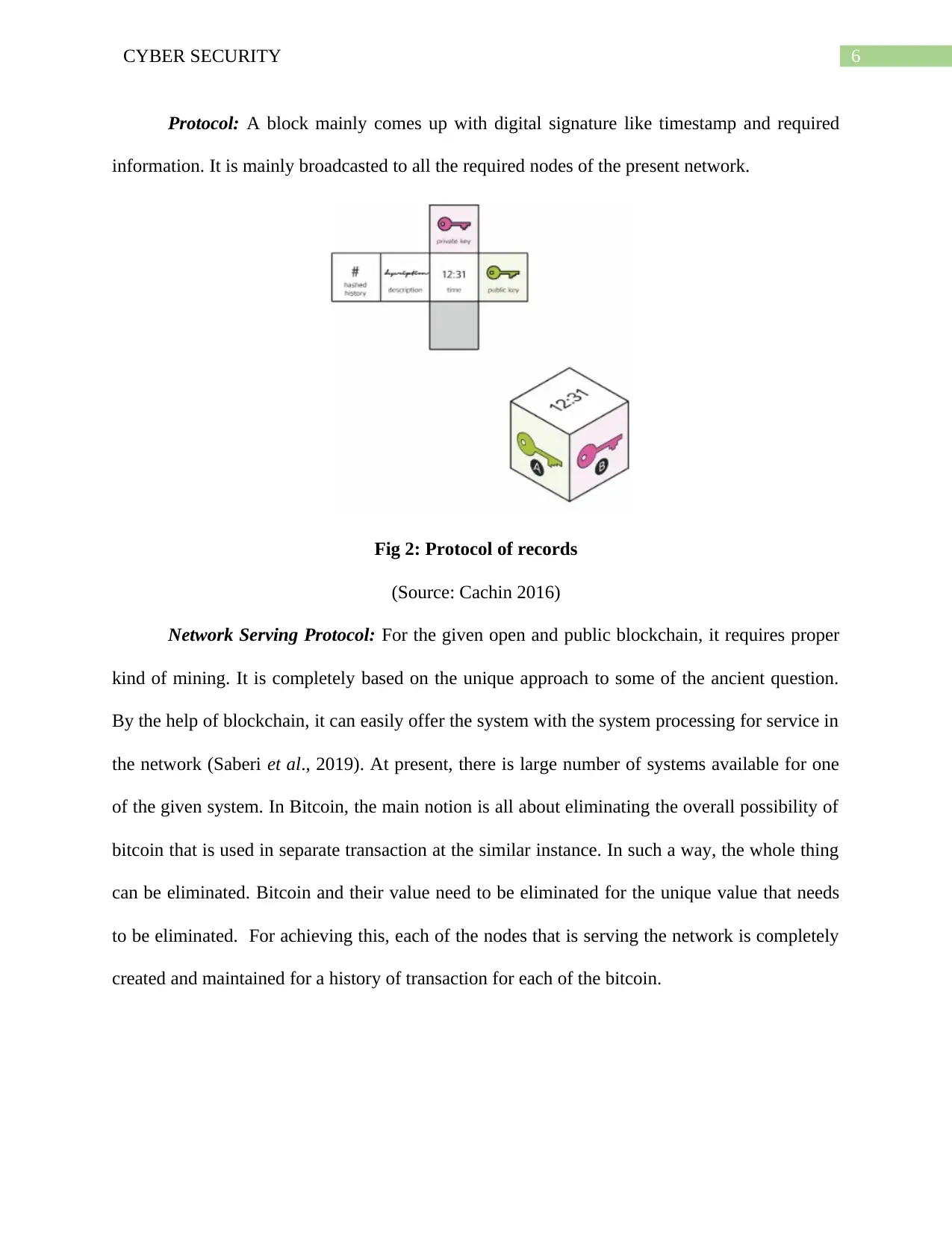
Protocol: A block mainly comes up with digital signature like timestamp and required
information. It is mainly broadcasted to all the required nodes of the present network.
Fig 2: Protocol of records
(Source: Cachin 2016)
Network Serving Protocol: For the given open and public blockchain, it requires proper
kind of mining. It is completely based on the unique approach to some of the ancient question.
By the help of blockchain, it can easily offer the system with the system processing for service in
the network (Saberi et al., 2019). At present, there is large number of systems available for one
of the given system. In Bitcoin, the main notion is all about eliminating the overall possibility of
bitcoin that is used in separate transaction at the similar instance. In such a way, the whole thing
can be eliminated. Bitcoin and their value need to be eliminated for the unique value that needs
to be eliminated. For achieving this, each of the nodes that is serving the network is completely
created and maintained for a history of transaction for each of the bitcoin.
Protocol: A block mainly comes up with digital signature like timestamp and required
information. It is mainly broadcasted to all the required nodes of the present network.
Fig 2: Protocol of records
(Source: Cachin 2016)
Network Serving Protocol: For the given open and public blockchain, it requires proper
kind of mining. It is completely based on the unique approach to some of the ancient question.
By the help of blockchain, it can easily offer the system with the system processing for service in
the network (Saberi et al., 2019). At present, there is large number of systems available for one
of the given system. In Bitcoin, the main notion is all about eliminating the overall possibility of
bitcoin that is used in separate transaction at the similar instance. In such a way, the whole thing
can be eliminated. Bitcoin and their value need to be eliminated for the unique value that needs
to be eliminated. For achieving this, each of the nodes that is serving the network is completely
created and maintained for a history of transaction for each of the bitcoin.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CYBER SECURITY
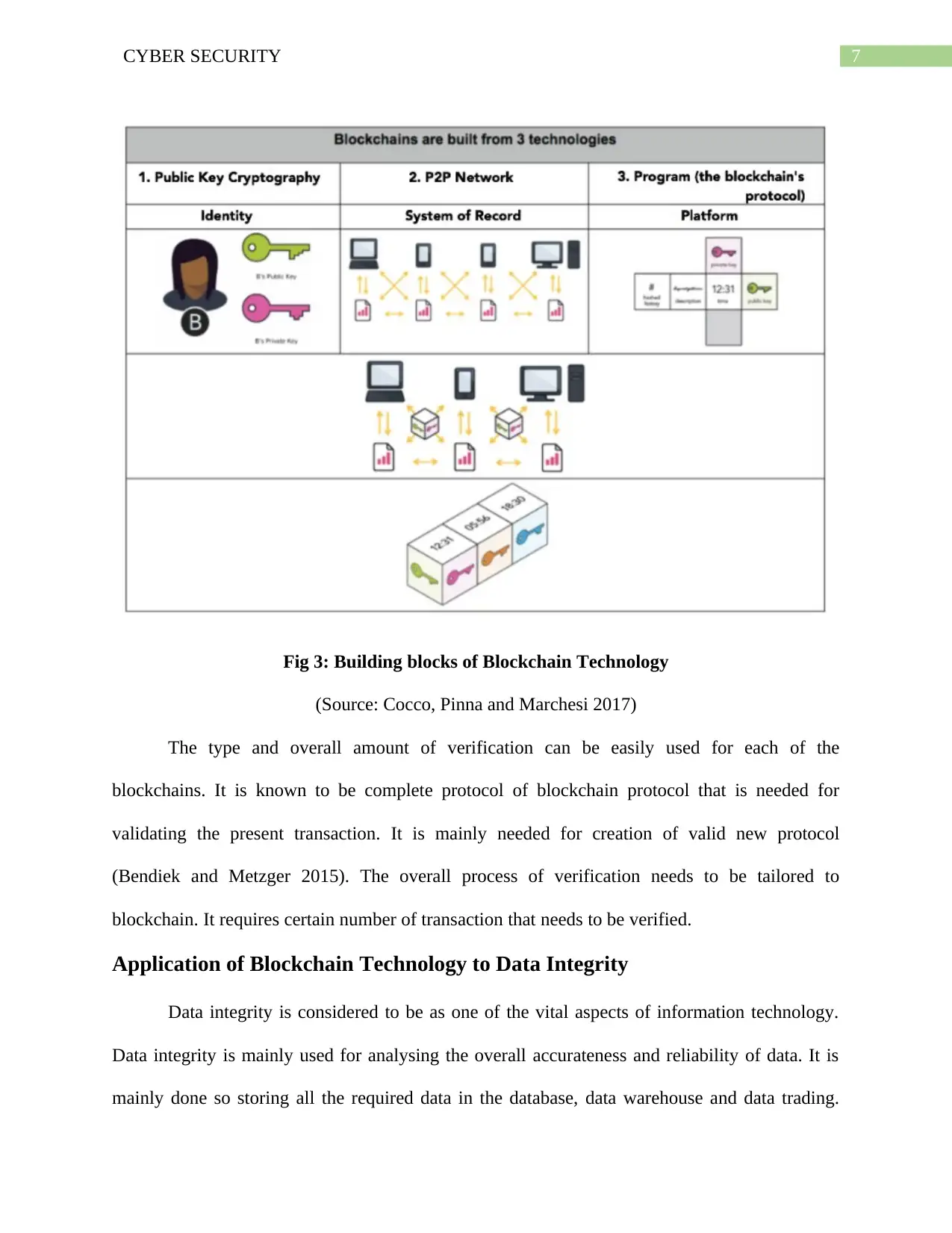
Fig 3: Building blocks of Blockchain Technology
(Source: Cocco, Pinna and Marchesi 2017)
The type and overall amount of verification can be easily used for each of the
blockchains. It is known to be complete protocol of blockchain protocol that is needed for
validating the present transaction. It is mainly needed for creation of valid new protocol
(Bendiek and Metzger 2015). The overall process of verification needs to be tailored to
blockchain. It requires certain number of transaction that needs to be verified.
Application of Blockchain Technology to Data Integrity
Data integrity is considered to be as one of the vital aspects of information technology.
Data integrity is mainly used for analysing the overall accurateness and reliability of data. It is
mainly done so storing all the required data in the database, data warehouse and data trading.
Fig 3: Building blocks of Blockchain Technology
(Source: Cocco, Pinna and Marchesi 2017)
The type and overall amount of verification can be easily used for each of the
blockchains. It is known to be complete protocol of blockchain protocol that is needed for
validating the present transaction. It is mainly needed for creation of valid new protocol
(Bendiek and Metzger 2015). The overall process of verification needs to be tailored to
blockchain. It requires certain number of transaction that needs to be verified.
Application of Blockchain Technology to Data Integrity
Data integrity is considered to be as one of the vital aspects of information technology.
Data integrity is mainly used for analysing the overall accurateness and reliability of data. It is
mainly done so storing all the required data in the database, data warehouse and data trading.

8CYBER SECURITY
Blockchain is known to be digital ledger (Howard 2018). It is mainly used for keeping a record
of various transaction on the given system. In the last few years, blockchain technology has
received huge amount of success. This particular technology is known to be leading in various
application like banking and areas of finance along with various sector. This particular
application is mainly used in some of the fields for making internet connection without any
control of trustworthy of the third party.
Open blockchain technology comes up with huge number of characteristics like its global
range and its working environment. Blockchain technology comes up with required documents
which are needed for handling record and management of digital ID for various governmental
bodies (Valeriano and Maness 2018). Every transaction come up with secure and record of
blockchain. It can be either economic transaction and business transaction that requires
governmental procedures. Blockchain aims to provide huge number of security for managing the
documents that becomes very much easier for open that is simple and transparent. Blockchain
comes up with verified records for every record for given transaction (Pilkington 2016).
Concerning blockchain technology, every transaction is completely into required blocks that are
completely connected. If any kind of change takes place in the node, then it will favour the
transaction.
Blockchain can be stated as the digitized, decentralized public ledger for various kind of
cryptocurrency based transaction. This particular technique will ultimately allow the market to
keep track of digital transaction without any kind of central record-keeping (Zheng et al. 2017).
In this, each of the nodes can have a copy of the required blockchain that is completely
downloaded automatically. All the required information is completely transferred by making use
of blockchain that can be automatically downloaded. All the required kind of information is
Blockchain is known to be digital ledger (Howard 2018). It is mainly used for keeping a record
of various transaction on the given system. In the last few years, blockchain technology has
received huge amount of success. This particular technology is known to be leading in various
application like banking and areas of finance along with various sector. This particular
application is mainly used in some of the fields for making internet connection without any
control of trustworthy of the third party.
Open blockchain technology comes up with huge number of characteristics like its global
range and its working environment. Blockchain technology comes up with required documents
which are needed for handling record and management of digital ID for various governmental
bodies (Valeriano and Maness 2018). Every transaction come up with secure and record of
blockchain. It can be either economic transaction and business transaction that requires
governmental procedures. Blockchain aims to provide huge number of security for managing the
documents that becomes very much easier for open that is simple and transparent. Blockchain
comes up with verified records for every record for given transaction (Pilkington 2016).
Concerning blockchain technology, every transaction is completely into required blocks that are
completely connected. If any kind of change takes place in the node, then it will favour the
transaction.
Blockchain can be stated as the digitized, decentralized public ledger for various kind of
cryptocurrency based transaction. This particular technique will ultimately allow the market to
keep track of digital transaction without any kind of central record-keeping (Zheng et al. 2017).
In this, each of the nodes can have a copy of the required blockchain that is completely
downloaded automatically. All the required information is completely transferred by making use
of blockchain that can be automatically downloaded. All the required kind of information is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER SECURITY
completely transformed by making use of blockchain technology, which is evidence. In this
domain, it is also known to be a ledger in the whole cryptography world (Biswas and
Muthukkumarasamy 2016). Each and every time the required information is exchanged it can be
stated like a transaction.
With the increase in the overall use of cloud services and security threats is all also
improving at a rapid rate. There is large number of policies for dealing with security incidents in
the whole cloud environment (Wright and De Filippi 2015). At present, there is large number of
solution that focuses on various research of incident of digital forensic which response to the
overall security. It becomes very difficult for proving the overall integrity of the collection and
overall storage in cloud environment (Sikorski, Haughton and Kraft 2017). Blockchain
technology aims to provide technologies that are needed for overall efficiency and security-based
practices in various domains like public and government.
Effect on both direction and magnitude which will shift offence-defence
balance
With time, blockchain technology is getting huge attention from the industry. It is being
used in various field for its various use (Raval 2016). Depending on the nature of the blockchain
security analysis has been done concerning areas of problem in blockchain. It is mainly needed
for dealing with various issues of data integrity and overall transparency of text documents. In
the last section, the paper aims to highlight the overview of some of the technology components
that makes consultation with the blockchain (Zhang and Wen 2017). It is all about overall
relevance optimization that is needed for data authentication and protecting issues. User of cloud
computing user can easily assume that if the given data is completely encrypted before it is
completely outsourcing to cloud which is very much secure in nature.
completely transformed by making use of blockchain technology, which is evidence. In this
domain, it is also known to be a ledger in the whole cryptography world (Biswas and
Muthukkumarasamy 2016). Each and every time the required information is exchanged it can be
stated like a transaction.
With the increase in the overall use of cloud services and security threats is all also
improving at a rapid rate. There is large number of policies for dealing with security incidents in
the whole cloud environment (Wright and De Filippi 2015). At present, there is large number of
solution that focuses on various research of incident of digital forensic which response to the
overall security. It becomes very difficult for proving the overall integrity of the collection and
overall storage in cloud environment (Sikorski, Haughton and Kraft 2017). Blockchain
technology aims to provide technologies that are needed for overall efficiency and security-based
practices in various domains like public and government.
Effect on both direction and magnitude which will shift offence-defence
balance
With time, blockchain technology is getting huge attention from the industry. It is being
used in various field for its various use (Raval 2016). Depending on the nature of the blockchain
security analysis has been done concerning areas of problem in blockchain. It is mainly needed
for dealing with various issues of data integrity and overall transparency of text documents. In
the last section, the paper aims to highlight the overview of some of the technology components
that makes consultation with the blockchain (Zhang and Wen 2017). It is all about overall
relevance optimization that is needed for data authentication and protecting issues. User of cloud
computing user can easily assume that if the given data is completely encrypted before it is
completely outsourcing to cloud which is very much secure in nature.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER SECURITY
Encryption is mainly provided so that they improve the overall confidentiality against any
kind of internal attacks (Meng et al. 2018). It does not only protect data from any kind of
corruption that is caused by error of configuration and bugs in software. There is large number of
ways available for proving integrity of the outsourced data in some of the remote server. All the
required checking of integrity of data is mainly by client or third party (Treleaven, Brown and
Yang 2017). The first one is all about downloading of file followed by checking the hash value.
Offence-defence theory for international stability
Offence- Defence theory is defined as the optimistic view which is needed for having a
proper view of international politics. It is completely based on the argument that war can be
easily prevented if and only if defence can gain proper advantage over the offence (Atzori 2015).
It is mainly needed for arguing that proper arm control can reduce the overall risk of race and
wars. This particular theory is considered to be very much useful in understanding foreign policy
analysis. In the domain of international relations, the overall scholarship is needed for explaining
both theoretical and overall policy issues that resulted in World War I.
Offence defence theory can be considered to be optimistic theory which is needed for
international politics. It mainly makes argument when the defence makes an advantage over
offence in most of cases where war can be avoided (Ølnes, Ubacht and Janssen 2017). Overall
the likelihood for arms race and war can easily be reduced by the help of careful design and
control. In the last few years, this particular theory is increasing at a rapid in both international
relations and proper analysis of the foreign policy.
This particular theory comes up with proper growth status where critics are known to be
as one of biggest question. The biggest foundation of the theory is that it is completely
underdeveloped (Nofer et al. 2017). The offence-defence theory has ultimately resulted in proper
Encryption is mainly provided so that they improve the overall confidentiality against any
kind of internal attacks (Meng et al. 2018). It does not only protect data from any kind of
corruption that is caused by error of configuration and bugs in software. There is large number of
ways available for proving integrity of the outsourced data in some of the remote server. All the
required checking of integrity of data is mainly by client or third party (Treleaven, Brown and
Yang 2017). The first one is all about downloading of file followed by checking the hash value.
Offence-defence theory for international stability
Offence- Defence theory is defined as the optimistic view which is needed for having a
proper view of international politics. It is completely based on the argument that war can be
easily prevented if and only if defence can gain proper advantage over the offence (Atzori 2015).
It is mainly needed for arguing that proper arm control can reduce the overall risk of race and
wars. This particular theory is considered to be very much useful in understanding foreign policy
analysis. In the domain of international relations, the overall scholarship is needed for explaining
both theoretical and overall policy issues that resulted in World War I.
Offence defence theory can be considered to be optimistic theory which is needed for
international politics. It mainly makes argument when the defence makes an advantage over
offence in most of cases where war can be avoided (Ølnes, Ubacht and Janssen 2017). Overall
the likelihood for arms race and war can easily be reduced by the help of careful design and
control. In the last few years, this particular theory is increasing at a rapid in both international
relations and proper analysis of the foreign policy.
This particular theory comes up with proper growth status where critics are known to be
as one of biggest question. The biggest foundation of the theory is that it is completely
underdeveloped (Nofer et al. 2017). The offence-defence theory has ultimately resulted in proper

11CYBER SECURITY
application and testing of the theory. The biggest issue that needs to be considered is complete
application and testing of the theory.
Conclusion
The above pages of the report help us in concluding the fact that this report is all about
blockchain technology. Blockchain technology can be defined as the distributed record of
database on public ledger on which various kind of transaction or digital events are completely
executed and shared. Bitcoin is the most suitable example of technology which is intrinsically
tied to this blockchain technology. At present, it is known to be most controversial topic as it
helps the multibillion-dollar global market for making transaction without any kind of
government control. At present, there is large number of regulatory issues that requires
involvement of some national and financial institutes. In the last few years, blockchain
technology is being applied to be being applied flawlessly to both kinds of domain like financial
and non-financial world of application. The software of bitcoin technology is being applied to
whole digital currency for its proper functioning, which needs to be considered like an
intervention like a steam of combustion engine. It comes up with the function which needs to be
considered to be an intervention like steam or combustion engine that can transform the world of
finance. At present, digital economy is completely based on dependency on certain number of
theory. Most of the given transaction is completely based on narrating the truth which can be
either trusting someone with the truth that can be either email service provider. Blockchain
technology has completely revolutionized the whole world of digital technology by creating a
distribution of consensus for every online transaction. In the above pages, an overview has been
provided concerning shift of offence and defence theory in the whole cyberspace. The debate is
completely done in the domain of offence-defence. The complete working mechanism of
application and testing of the theory. The biggest issue that needs to be considered is complete
application and testing of the theory.
Conclusion
The above pages of the report help us in concluding the fact that this report is all about
blockchain technology. Blockchain technology can be defined as the distributed record of
database on public ledger on which various kind of transaction or digital events are completely
executed and shared. Bitcoin is the most suitable example of technology which is intrinsically
tied to this blockchain technology. At present, it is known to be most controversial topic as it
helps the multibillion-dollar global market for making transaction without any kind of
government control. At present, there is large number of regulatory issues that requires
involvement of some national and financial institutes. In the last few years, blockchain
technology is being applied to be being applied flawlessly to both kinds of domain like financial
and non-financial world of application. The software of bitcoin technology is being applied to
whole digital currency for its proper functioning, which needs to be considered like an
intervention like a steam of combustion engine. It comes up with the function which needs to be
considered to be an intervention like steam or combustion engine that can transform the world of
finance. At present, digital economy is completely based on dependency on certain number of
theory. Most of the given transaction is completely based on narrating the truth which can be
either trusting someone with the truth that can be either email service provider. Blockchain
technology has completely revolutionized the whole world of digital technology by creating a
distribution of consensus for every online transaction. In the above pages, an overview has been
provided concerning shift of offence and defence theory in the whole cyberspace. The debate is
completely done in the domain of offence-defence. The complete working mechanism of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




