[PDF] Cybersecurity Law and Regulation
VerifiedAdded on 2021/02/20
|18
|5720
|63
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

CYBER SECURITY
LAW, REGULATION &
POLICY
LAW, REGULATION &
POLICY
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
EXECUTIVE SUMMARY.............................................................................................................3
BACKGROUND.............................................................................................................................3
CURRENT SITUATION.................................................................................................................3
GENERAL DEFINITIONS.............................................................................................................4
BENEFITS OF IT & OT:................................................................................................................5
types of ransomware attacks:................................................................................................10
DDOS.............................................................................................................................................10
Types of DDOS attacks........................................................................................................11
The Process of DDOS Attack...............................................................................................12
Vectors of Attack in IT/OT Combination......................................................................................12
IT/OT convergence's Various Challenges Relating to Security....................................................12
Lack of Clarity......................................................................................................................12
Less Control on the Policies Relating to Security ...............................................................13
Security Threat's Solution Relating to IT/OT Convergence..........................................................13
Network Visibility Should be Real-Time.............................................................................13
Segmentation of Networks...................................................................................................14
Monitoring Foundation of Networks....................................................................................14
Current Attacks in Combined Environment of IT/OT ..................................................................14
Legal Considerations.....................................................................................................................15
Cybercrime Act, 2001..........................................................................................................15
Surveillance Devices Act, 2007...........................................................................................15
Crime Act,1900....................................................................................................................15
CONCLUSION..............................................................................................................................16
Future............................................................................................................................................16
REFERENCES..............................................................................................................................17
EXECUTIVE SUMMARY.............................................................................................................3
BACKGROUND.............................................................................................................................3
CURRENT SITUATION.................................................................................................................3
GENERAL DEFINITIONS.............................................................................................................4
BENEFITS OF IT & OT:................................................................................................................5
types of ransomware attacks:................................................................................................10
DDOS.............................................................................................................................................10
Types of DDOS attacks........................................................................................................11
The Process of DDOS Attack...............................................................................................12
Vectors of Attack in IT/OT Combination......................................................................................12
IT/OT convergence's Various Challenges Relating to Security....................................................12
Lack of Clarity......................................................................................................................12
Less Control on the Policies Relating to Security ...............................................................13
Security Threat's Solution Relating to IT/OT Convergence..........................................................13
Network Visibility Should be Real-Time.............................................................................13
Segmentation of Networks...................................................................................................14
Monitoring Foundation of Networks....................................................................................14
Current Attacks in Combined Environment of IT/OT ..................................................................14
Legal Considerations.....................................................................................................................15
Cybercrime Act, 2001..........................................................................................................15
Surveillance Devices Act, 2007...........................................................................................15
Crime Act,1900....................................................................................................................15
CONCLUSION..............................................................................................................................16
Future............................................................................................................................................16
REFERENCES..............................................................................................................................17

EXECUTIVE SUMMARY
Operation technology creates various changes with the help of process like monitoring
and controlling by physical devices, sensors and software. On the other hand information
technology refers to the combination of all the technologies which is used for communication
and to operate the information and data in the working area. Theses both technologies are
different from each other because both the technology have different working style and follows
different standard, protocol, technology etc. Adoption of culture and technologies of information
technology like internet protocols, standard etc. by the operation technology helps the company
to reduces their operational cost, increased in profits. These technologies will help the industries
to minimizes the risk. By adopting the information technology operation technology became
more efficient and effective in the organization (Graham, Olson and Howard, 2016).
Organizational, strategic, technological operations are had to be efficient and effective and this
will only through the use of information technology.
(Graham, Olson and Howard, 2016)BACKGROUND
Automatic process is seemed to be difficult process for improvement and enhancement
of the industries which is used in the industries like manufacturing industries. The system of the
automation used for measuring the automatic process of the company is very common in every
organization. For sharing the storage of the data it gives permission to the different kinds of
technology. This will says that the use of automatic technology in the industries used in the
substantial changes and future as well. From the early 60s Information technology brings lots of
changes and it is the main source which brings changes. The process of automation is fully
depends on the information technology (Carr, 2016). With the information technology point of
view there is still the needs of changes in the operational technology.
CURRENT SITUATION
Information technology is expressed in different languages by everyone so it is broad
term to be defined. Information technology is used to convert the information and data by
hardware, software and applications of the software. Examples of information technology which
is used to convert to information are Enterprise Resource Plaining (ERP), Content management
system (CRM). It is that system in which all the inputs and outputs are said that data.
Operational technology includes the various process and physical devices of the company
which gives dynamic results on the operational system like networks of power distribution, plans
Operation technology creates various changes with the help of process like monitoring
and controlling by physical devices, sensors and software. On the other hand information
technology refers to the combination of all the technologies which is used for communication
and to operate the information and data in the working area. Theses both technologies are
different from each other because both the technology have different working style and follows
different standard, protocol, technology etc. Adoption of culture and technologies of information
technology like internet protocols, standard etc. by the operation technology helps the company
to reduces their operational cost, increased in profits. These technologies will help the industries
to minimizes the risk. By adopting the information technology operation technology became
more efficient and effective in the organization (Graham, Olson and Howard, 2016).
Organizational, strategic, technological operations are had to be efficient and effective and this
will only through the use of information technology.
(Graham, Olson and Howard, 2016)BACKGROUND
Automatic process is seemed to be difficult process for improvement and enhancement
of the industries which is used in the industries like manufacturing industries. The system of the
automation used for measuring the automatic process of the company is very common in every
organization. For sharing the storage of the data it gives permission to the different kinds of
technology. This will says that the use of automatic technology in the industries used in the
substantial changes and future as well. From the early 60s Information technology brings lots of
changes and it is the main source which brings changes. The process of automation is fully
depends on the information technology (Carr, 2016). With the information technology point of
view there is still the needs of changes in the operational technology.
CURRENT SITUATION
Information technology is expressed in different languages by everyone so it is broad
term to be defined. Information technology is used to convert the information and data by
hardware, software and applications of the software. Examples of information technology which
is used to convert to information are Enterprise Resource Plaining (ERP), Content management
system (CRM). It is that system in which all the inputs and outputs are said that data.
Operational technology includes the various process and physical devices of the company
which gives dynamic results on the operational system like networks of power distribution, plans
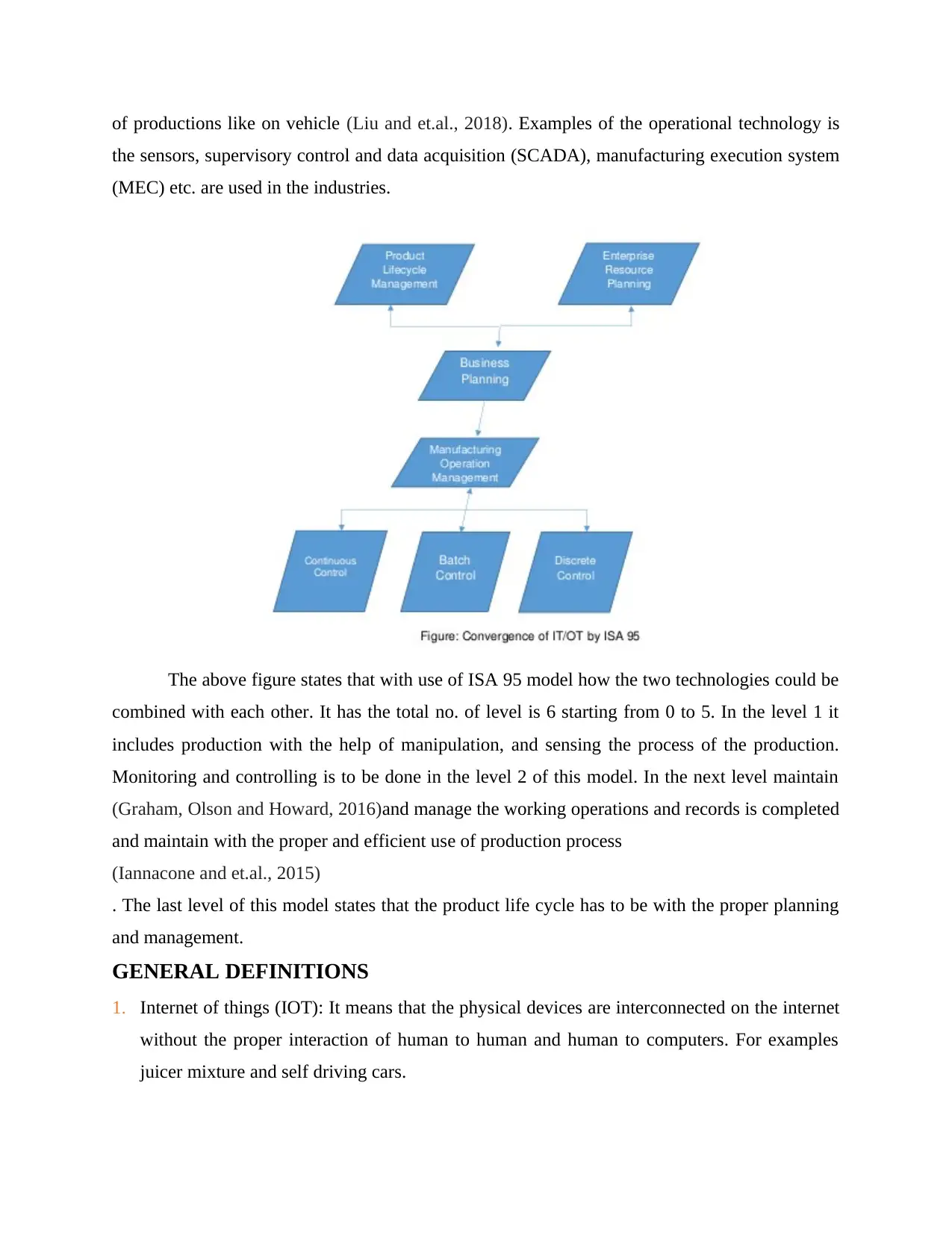
of productions like on vehicle (Liu and et.al., 2018). Examples of the operational technology is
the sensors, supervisory control and data acquisition (SCADA), manufacturing execution system
(MEC) etc. are used in the industries.
The above figure states that with use of ISA 95 model how the two technologies could be
combined with each other. It has the total no. of level is 6 starting from 0 to 5. In the level 1 it
includes production with the help of manipulation, and sensing the process of the production.
Monitoring and controlling is to be done in the level 2 of this model. In the next level maintain
(Graham, Olson and Howard, 2016)and manage the working operations and records is completed
and maintain with the proper and efficient use of production process
(Iannacone and et.al., 2015)
. The last level of this model states that the product life cycle has to be with the proper planning
and management.
GENERAL DEFINITIONS
1. Internet of things (IOT): It means that the physical devices are interconnected on the internet
without the proper interaction of human to human and human to computers. For examples
juicer mixture and self driving cars.
the sensors, supervisory control and data acquisition (SCADA), manufacturing execution system
(MEC) etc. are used in the industries.
The above figure states that with use of ISA 95 model how the two technologies could be
combined with each other. It has the total no. of level is 6 starting from 0 to 5. In the level 1 it
includes production with the help of manipulation, and sensing the process of the production.
Monitoring and controlling is to be done in the level 2 of this model. In the next level maintain
(Graham, Olson and Howard, 2016)and manage the working operations and records is completed
and maintain with the proper and efficient use of production process
(Iannacone and et.al., 2015)
. The last level of this model states that the product life cycle has to be with the proper planning
and management.
GENERAL DEFINITIONS
1. Internet of things (IOT): It means that the physical devices are interconnected on the internet
without the proper interaction of human to human and human to computers. For examples
juicer mixture and self driving cars.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

2. Information technology: It is that system in which both inputs and outputs are data but no t in
the physical world. Some common examples of information technology is enterprise resource
planning (ERP), content management system (CRM).
3. Operational technology: in the operational technology hardware and software gives dynamic
responds on the working operational system. Examples which responds dynamically are
distributed control system (DCS), Industrial control system (ICS), supervisory control and
data acquisition system (SCADA), automatic and control system.
4. Convergence of IT/OT: it means that the combination of information technology systems for
monitoring and controlling the process of physical devices in the industries. For proper
computing the system of operational technology.
BENEFITS OF IT & OT:
There are various advantages to each and every industry with the convergence of the IT
and OT. The advantages to the industries is different from each other like manufacturing
industry, telecommunication industry etc. from the convergence of IT and OT. The combination
of the technology gives greater benefits to the industries having large investments like
manufacturing, construction transportation etc (Chiang and Zhang, 2016). in the operational
technology. Advantages to these industries are as follows:
Reduction in the cost: when two technologies are merged than same principle, protocols,
standard are applied both the technologies. It means that there is the simple and easy
steps to convert the collaborations in various industries. But the focus of the industry is
not the reduction in the cost.
Performance improvement: Combination of both the technology will improve the
performance of the industry because it saves the time and cost of the company. Shifting
to the developed products from the earlier process it says that the smooth functioning of
the operations.
Increase in flexibility:Increase in flexibility: by reducing the cost of the company it will
increase the flexibility and become more transparent. Manufacturing could be efficiently
and effectively anywhere and from this the level of flexibility increases.
Minimum risk: it will help to reduce the risk of the company by giving security and
protection from the outside of the industry and to provide the focal security within the
industry.
the physical world. Some common examples of information technology is enterprise resource
planning (ERP), content management system (CRM).
3. Operational technology: in the operational technology hardware and software gives dynamic
responds on the working operational system. Examples which responds dynamically are
distributed control system (DCS), Industrial control system (ICS), supervisory control and
data acquisition system (SCADA), automatic and control system.
4. Convergence of IT/OT: it means that the combination of information technology systems for
monitoring and controlling the process of physical devices in the industries. For proper
computing the system of operational technology.
BENEFITS OF IT & OT:
There are various advantages to each and every industry with the convergence of the IT
and OT. The advantages to the industries is different from each other like manufacturing
industry, telecommunication industry etc. from the convergence of IT and OT. The combination
of the technology gives greater benefits to the industries having large investments like
manufacturing, construction transportation etc (Chiang and Zhang, 2016). in the operational
technology. Advantages to these industries are as follows:
Reduction in the cost: when two technologies are merged than same principle, protocols,
standard are applied both the technologies. It means that there is the simple and easy
steps to convert the collaborations in various industries. But the focus of the industry is
not the reduction in the cost.
Performance improvement: Combination of both the technology will improve the
performance of the industry because it saves the time and cost of the company. Shifting
to the developed products from the earlier process it says that the smooth functioning of
the operations.
Increase in flexibility:Increase in flexibility: by reducing the cost of the company it will
increase the flexibility and become more transparent. Manufacturing could be efficiently
and effectively anywhere and from this the level of flexibility increases.
Minimum risk: it will help to reduce the risk of the company by giving security and
protection from the outside of the industry and to provide the focal security within the
industry.

Challenges in the convergence of IT and OT:
The challenges are faced with the convergence of IT and OT are as follows:
Organizational: in the present times organization assumes that both the IT and OT are two
different areas with different structure, process and standard (Khan and et.al., 2018). Challenges
of the organization can be beat by the following :
development is necessary for the alignment of both the technologies, joint bodies, and the
structure of the government.
Their is need to manage and execute the projects of cross technology together.
Process like duplicate and overlapped are harmonized.
Their is need to develop inter disciplinary skills to identify the importance of the IT and
OT.
Their is also needed to mange and maintain the physical infrastructure.
Elimination of the security concerns because that is different from both the needs.
Strategical: for the integration of both IT and OT there is need to combine the strategy of CIO
strategy (for IT) with the COO (for OT). Various conditions are necessary for to makes the
comp[any success fulfil has many company restricted and zero integration.
Technological: integration is needed in enterprise resource planning (ERP) and manufacturing
execution system by considering the level 1 as defined under the ISA 95 MODEL. The
combination of PLM and MES is in the second action when the product is at the stage of
production.
Strategies of IT and OT convergence:
Accomplishment of the combination IT and OT is based on the factors like conquering
internal factors and separating the structure which have developed years ago. Alignment and
harmonization of the process and strategies of the company by the skilled and trained staff leads
to the success and growth of the IT and OT convergence (Hassanalieragh and et.al., 2015). These
are explained below:
HARMONISATION: as IT and OT are two different aspects so their processes, strategies
and standard which is followed by the industries are also different from each other. The
main aim is to harmonize them. The development of the standard governance model that
could bring harmonization in the practices, standard, strategies, techniques, solutions that
The challenges are faced with the convergence of IT and OT are as follows:
Organizational: in the present times organization assumes that both the IT and OT are two
different areas with different structure, process and standard (Khan and et.al., 2018). Challenges
of the organization can be beat by the following :
development is necessary for the alignment of both the technologies, joint bodies, and the
structure of the government.
Their is need to manage and execute the projects of cross technology together.
Process like duplicate and overlapped are harmonized.
Their is need to develop inter disciplinary skills to identify the importance of the IT and
OT.
Their is also needed to mange and maintain the physical infrastructure.
Elimination of the security concerns because that is different from both the needs.
Strategical: for the integration of both IT and OT there is need to combine the strategy of CIO
strategy (for IT) with the COO (for OT). Various conditions are necessary for to makes the
comp[any success fulfil has many company restricted and zero integration.
Technological: integration is needed in enterprise resource planning (ERP) and manufacturing
execution system by considering the level 1 as defined under the ISA 95 MODEL. The
combination of PLM and MES is in the second action when the product is at the stage of
production.
Strategies of IT and OT convergence:
Accomplishment of the combination IT and OT is based on the factors like conquering
internal factors and separating the structure which have developed years ago. Alignment and
harmonization of the process and strategies of the company by the skilled and trained staff leads
to the success and growth of the IT and OT convergence (Hassanalieragh and et.al., 2015). These
are explained below:
HARMONISATION: as IT and OT are two different aspects so their processes, strategies
and standard which is followed by the industries are also different from each other. The
main aim is to harmonize them. The development of the standard governance model that
could bring harmonization in the practices, standard, strategies, techniques, solutions that

both the IT and OT follows the discipline. joint bodies should be developed which unites
the IT/OT experts which shows the rule, procedure, policies etc. rather than for separate
responsibilities. So the IT and OT changed to the one organisation from separate
organisation. By following the same and common standards it will create the whole
organisation. For the support and alignment of the software configuration common
method is to be followed (Marjani and et.al., 2017). There is need of the standard
procurement policies for joining the software and hardware. Monitoring and tracking
should be done carefully when these two are implemented in the company.
SECURITY: when operational technology system are exposing in the open market then
there is need of proper security. When it should be properly followed then it wills brings
threats.
STAFF TRAINING: information technology refers to all the advanced technology which
used by the company. Information technology is the important in the future for
management of this coverage atmosphere. When the structure is set up by the team of IT
than there are needs of the OT features. From this they will increase the skills for
complete incomplete system of the OT. The proper intelligence and knowledge is
required for the success and growth of the IT/OT coverage world.
COMMUNICATION: the communication must be effective and efficient so that
everyone could understand the concept and power of the IT and OT in the company's
environment. All the information of IT and OT projects like tracking, informing and
gathering the information is important to delivered to all the stakeholders. Developed
applications of the intranet helped the stakeholders to gives the feedback to the team of
the implementation. Information must be up to date on the application of intranet.
Interview should be faced to face that could help in identifying and measuring the
efficiency and effectiveness of the process.
Relationship with the IT and OT convergence with IOT:
IOT is key for merging these two technologies in the organisation. Burt there is the thing how
both the technologies gives facilities to the IOT with maintaining their own working and
responsibilities. IOT is the automatic process with the use of devices and data which have ability
to send, collect and receive the information and knowledge and intelligence to connect into the
devices and manage the process and applications which unlocks the new aspects.
the IT/OT experts which shows the rule, procedure, policies etc. rather than for separate
responsibilities. So the IT and OT changed to the one organisation from separate
organisation. By following the same and common standards it will create the whole
organisation. For the support and alignment of the software configuration common
method is to be followed (Marjani and et.al., 2017). There is need of the standard
procurement policies for joining the software and hardware. Monitoring and tracking
should be done carefully when these two are implemented in the company.
SECURITY: when operational technology system are exposing in the open market then
there is need of proper security. When it should be properly followed then it wills brings
threats.
STAFF TRAINING: information technology refers to all the advanced technology which
used by the company. Information technology is the important in the future for
management of this coverage atmosphere. When the structure is set up by the team of IT
than there are needs of the OT features. From this they will increase the skills for
complete incomplete system of the OT. The proper intelligence and knowledge is
required for the success and growth of the IT/OT coverage world.
COMMUNICATION: the communication must be effective and efficient so that
everyone could understand the concept and power of the IT and OT in the company's
environment. All the information of IT and OT projects like tracking, informing and
gathering the information is important to delivered to all the stakeholders. Developed
applications of the intranet helped the stakeholders to gives the feedback to the team of
the implementation. Information must be up to date on the application of intranet.
Interview should be faced to face that could help in identifying and measuring the
efficiency and effectiveness of the process.
Relationship with the IT and OT convergence with IOT:
IOT is key for merging these two technologies in the organisation. Burt there is the thing how
both the technologies gives facilities to the IOT with maintaining their own working and
responsibilities. IOT is the automatic process with the use of devices and data which have ability
to send, collect and receive the information and knowledge and intelligence to connect into the
devices and manage the process and applications which unlocks the new aspects.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Drivers for convergence of IT and OT:
There are different types of drivers which helps that to dries these two technologies.
From the point of the technology transfer of the legacy system like Public switched telephone
networks (PSTN) to the internet protocol. Building automatic system (BAS) used by the other
drivers for building smart concept and these helps to provide the automatic facilities like
ventilation, heating, cooling, lighting, safety features etc. it also includes other benefits like
decrease in sizes of the offices, efficient use of the energy (Yan and et.al., 2015). Personal
advantages of the employees are also included under these systems. In the industry's information
of the control system are sent through the internet such as system of alarm, video surveillance.
Difference between IT and OT with respect to security:
Convergence of these two technology are not the issue but the focus is there is need
secure because there is difference their priorities and practices. Some common differences are
explained below:
Information technology Operational technology
Management of the information Management of the physical process
Its focus is on the data Its focus is on the physical devices control
Physical environment should be controlled
under this
Distribution of physical device should be done
geographically
Computing is the main importance Higher importance is given to the production
and lower importance is given to the software
up-gradation.
Enterprise resource planning is the example of
the IT
ICS, SCADA are some examples of the OT
It includes IOT internet of things
For examples: phones, laptops, tablets
It includes IIOT industrial internet of things
For examples: sensors, scanners etc.
C++, C#, API web services are some systems
of the IT
Ethernet, TCP/IP are some systems of the OT
There are different types of drivers which helps that to dries these two technologies.
From the point of the technology transfer of the legacy system like Public switched telephone
networks (PSTN) to the internet protocol. Building automatic system (BAS) used by the other
drivers for building smart concept and these helps to provide the automatic facilities like
ventilation, heating, cooling, lighting, safety features etc. it also includes other benefits like
decrease in sizes of the offices, efficient use of the energy (Yan and et.al., 2015). Personal
advantages of the employees are also included under these systems. In the industry's information
of the control system are sent through the internet such as system of alarm, video surveillance.
Difference between IT and OT with respect to security:
Convergence of these two technology are not the issue but the focus is there is need
secure because there is difference their priorities and practices. Some common differences are
explained below:
Information technology Operational technology
Management of the information Management of the physical process
Its focus is on the data Its focus is on the physical devices control
Physical environment should be controlled
under this
Distribution of physical device should be done
geographically
Computing is the main importance Higher importance is given to the production
and lower importance is given to the software
up-gradation.
Enterprise resource planning is the example of
the IT
ICS, SCADA are some examples of the OT
It includes IOT internet of things
For examples: phones, laptops, tablets
It includes IIOT industrial internet of things
For examples: sensors, scanners etc.
C++, C#, API web services are some systems
of the IT
Ethernet, TCP/IP are some systems of the OT

From the above security order it states that the IT and OT are different from each other
and makes the task more challenging. The basic terms of the security such as confidentiality,
availability and integrity which IT gives more importance to that.
On the other hand manner of security are shows that the control system of the OT gives
focus to the safety and risks.
Security threats in IT/OT convergence:
In the beginning the researchers recommend that the cyber and security areas are same
security areas. The convergence of IT and OT is challenging because both are different working
environment. The main concern of any industry is protection and security of their assets. In this
changing technologies researchers still find the better way to protect and secure the data and
assets of the company (Wang, B and et.al., 2015). Because of the hacking of the system
ransomware are increasing faster in the environment and with the help of IOT.
Customer is the fully responsible for operating their data and how to distribute them
according to the general data protection regulations. These regulations are the key for the
company to move from traditional system to the new and up to date system which brings success
and growth of working operations of the company. These up to date security will support the
and makes the task more challenging. The basic terms of the security such as confidentiality,
availability and integrity which IT gives more importance to that.
On the other hand manner of security are shows that the control system of the OT gives
focus to the safety and risks.
Security threats in IT/OT convergence:
In the beginning the researchers recommend that the cyber and security areas are same
security areas. The convergence of IT and OT is challenging because both are different working
environment. The main concern of any industry is protection and security of their assets. In this
changing technologies researchers still find the better way to protect and secure the data and
assets of the company (Wang, B and et.al., 2015). Because of the hacking of the system
ransomware are increasing faster in the environment and with the help of IOT.
Customer is the fully responsible for operating their data and how to distribute them
according to the general data protection regulations. These regulations are the key for the
company to move from traditional system to the new and up to date system which brings success
and growth of working operations of the company. These up to date security will support the

teams of security which easily monitor the in stores, ware houses where the company data is
recorded but if it is not accurately maintained then attackers should attack easily.
Industries are adopting convergence of IT and OT for being focused, competitive and for
improving the business increase in growth of the company. There have many security threats in
convergence of IT and OT which are explained below:
RANSOMWARE
:it is a kind of system in which malware locks the system and user is enabled to operate the
before paying the ransom. Laptops, computers system can be of any type. The main target of the
attackers is the business rather to individual users. The attackers make the business more ransom.
Development of the IOT gives another stress to the ransomware that affect the automatic system,
control system of the companies (Bawany, Shamsi and Salah, 2017). Hackers will hacks the
vehicles, public system hotels etc.
Examples of the ransomware are given below:
smart home: when the person is far away from the home and the hacker will hack the therostat
and it gives you the notification that your is hacked and you have to pay the ransom under this
situation you have to pay the ransom otherwise your house will be fired and you have to pay the
huge electricity bills
connected vehicles: hacker will follow your car hack your car when you are at the places like
desert and you have to pay the ransom at that point
hotels: hackers lock the guest in the room and you have pay the ransom at that point
types of ransomware attacks:
Crypto ransomware: in this attack there is impossible to cover the data which is
hacked by the hacker user is had to pay the bit cons for this attack
Locker ransomware: in this ransomware attacker lock the systems like computers,
laptops and user will not operate the system before paying.
DDOS
It stands for Distributed denial services of attacks and it has become a very similar word
since cyber threats came in to picture. In this attacker can attack the system by sending various
number of requests which are unwanted to user and then authentic user is not able to make
access to it system due to huge traffic. In internet of things, attacker gain the access to a device
recorded but if it is not accurately maintained then attackers should attack easily.
Industries are adopting convergence of IT and OT for being focused, competitive and for
improving the business increase in growth of the company. There have many security threats in
convergence of IT and OT which are explained below:
RANSOMWARE
:it is a kind of system in which malware locks the system and user is enabled to operate the
before paying the ransom. Laptops, computers system can be of any type. The main target of the
attackers is the business rather to individual users. The attackers make the business more ransom.
Development of the IOT gives another stress to the ransomware that affect the automatic system,
control system of the companies (Bawany, Shamsi and Salah, 2017). Hackers will hacks the
vehicles, public system hotels etc.
Examples of the ransomware are given below:
smart home: when the person is far away from the home and the hacker will hack the therostat
and it gives you the notification that your is hacked and you have to pay the ransom under this
situation you have to pay the ransom otherwise your house will be fired and you have to pay the
huge electricity bills
connected vehicles: hacker will follow your car hack your car when you are at the places like
desert and you have to pay the ransom at that point
hotels: hackers lock the guest in the room and you have pay the ransom at that point
types of ransomware attacks:
Crypto ransomware: in this attack there is impossible to cover the data which is
hacked by the hacker user is had to pay the bit cons for this attack
Locker ransomware: in this ransomware attacker lock the systems like computers,
laptops and user will not operate the system before paying.
DDOS
It stands for Distributed denial services of attacks and it has become a very similar word
since cyber threats came in to picture. In this attacker can attack the system by sending various
number of requests which are unwanted to user and then authentic user is not able to make
access to it system due to huge traffic. In internet of things, attacker gain the access to a device
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

for example video surveillance camera and after gaining the access to one device attacker can
gain access to various other connected devices.
Due to rise in adoption IOT, the scale of DDOS attacks have raised, these small devices
which are in IOT are mounted all across the world like video surveillance camera which is
secured at all. The reason behind it is that attacker can install virus as well as can program it then
can use in the future. Attacker can also enlist the malware within the robots and that too with
small investment.
The attacks on DDOS are increasing rapidly at present especially within IOT and the
most attacked layer are applications and network. Also, the security measures that are being used
in order to overcome the attacks on DDOS are called firewalls. In line on premises appliances,
cloud scrubbing and almost all the safety measures which are effective for line on premises
appliances are considered as the best for mitigating the anomalous traffic. This is also highly
recommended by the corporate personnels that it should be deployed in front of firewalls as well
as time of emergency if DDOS is on attack. Also, addition to it cloud scrubbing services can help
in dealing with volumetric attacks in order to reduce the malevolent networking trafficking
before it enters in the firm. These are also referred as effective than firewall as it can help in
dealing with MIRAI BOTNET.
Types of DDOS attacks
1. Fragmentation attacks: There are such attacks which degrades the performance of a system,
fragments can not reassembled by the server of a particular victim and this is also known as UDP
or TCP fragments.
2. Volumetric Attacks: Such attacks are responsible for maximum DDOS incidents, it is also
referred as floods. According to AKAMAI 99 percent of attacks are volumetric attacks.
3. Application attacks: These are the attacks in which a specific application packets are affected
and whole system is not targeted and it also results in disabling of OSI model.
4. TCP Connection attacks: Web servers, firewalls as well as load balancers mainly focus on
such types of attacks and this results in interruptions of the connections by putting out the
available connections attached to a device.
5. Zero day attacks: These are the attacks in which external opponents exploits previous fault.
gain access to various other connected devices.
Due to rise in adoption IOT, the scale of DDOS attacks have raised, these small devices
which are in IOT are mounted all across the world like video surveillance camera which is
secured at all. The reason behind it is that attacker can install virus as well as can program it then
can use in the future. Attacker can also enlist the malware within the robots and that too with
small investment.
The attacks on DDOS are increasing rapidly at present especially within IOT and the
most attacked layer are applications and network. Also, the security measures that are being used
in order to overcome the attacks on DDOS are called firewalls. In line on premises appliances,
cloud scrubbing and almost all the safety measures which are effective for line on premises
appliances are considered as the best for mitigating the anomalous traffic. This is also highly
recommended by the corporate personnels that it should be deployed in front of firewalls as well
as time of emergency if DDOS is on attack. Also, addition to it cloud scrubbing services can help
in dealing with volumetric attacks in order to reduce the malevolent networking trafficking
before it enters in the firm. These are also referred as effective than firewall as it can help in
dealing with MIRAI BOTNET.
Types of DDOS attacks
1. Fragmentation attacks: There are such attacks which degrades the performance of a system,
fragments can not reassembled by the server of a particular victim and this is also known as UDP
or TCP fragments.
2. Volumetric Attacks: Such attacks are responsible for maximum DDOS incidents, it is also
referred as floods. According to AKAMAI 99 percent of attacks are volumetric attacks.
3. Application attacks: These are the attacks in which a specific application packets are affected
and whole system is not targeted and it also results in disabling of OSI model.
4. TCP Connection attacks: Web servers, firewalls as well as load balancers mainly focus on
such types of attacks and this results in interruptions of the connections by putting out the
available connections attached to a device.
5. Zero day attacks: These are the attacks in which external opponents exploits previous fault.

The Process of DDOS Attack
DDOS procedures for attacks has six stages, among which the three stages consists of the
Botnet and its formation, which are as follows:
First and foremost step done is about scanning of the systems on internet that are infirm
and weak in nature.
The very first part of the system is contaminated along with the hacking and corruption of
the systems which are weak in nature(Cavelty, 2015).
The DDOS agents tends to be fixed into which accustoms the Botnet.
Then for receiving and getting the final instructions, a connection has to be established
between the Bots and the C&C architecture.
Then those guidelines and set instructions are being followed up by the Botnets
ultimately for, where to do the attack.
By addition of various new features, attributes to the Botnet, there conservation and
preservation is done accordingly.
Vectors of Attack in IT/OT Combination
Systems which are out-dated.
Experience and refinement of attackers
Various Risks related to efficiency and capacity for yielding.
Liability of IT/OT.
IT/OT convergence's Various Challenges Relating to Security
Most of the teams of IT focus their attention on the security issues, and are being worried
about the same. The issues relating to the protection and shielding of various factors and
resources of environment and also its assets, which are being degrading and deploying, and steps
has to been taken to protect the same. The various challenges in regard to security includes:
Lack of Clarity
It mainly emphasis on the forecasting by the teams engaged in security department of
various issues which may arise, such as IT/OT's network connections and their
discontinuance(Savage, Coogan and Lau, 2015). As the era is of advanced and new technology
through which the development of various process and their monitoring and controlling
according to the desired results are done and managed accordingly. In this situation, the teas
found it difficulty in collecting the dynamic data and work on it.
DDOS procedures for attacks has six stages, among which the three stages consists of the
Botnet and its formation, which are as follows:
First and foremost step done is about scanning of the systems on internet that are infirm
and weak in nature.
The very first part of the system is contaminated along with the hacking and corruption of
the systems which are weak in nature(Cavelty, 2015).
The DDOS agents tends to be fixed into which accustoms the Botnet.
Then for receiving and getting the final instructions, a connection has to be established
between the Bots and the C&C architecture.
Then those guidelines and set instructions are being followed up by the Botnets
ultimately for, where to do the attack.
By addition of various new features, attributes to the Botnet, there conservation and
preservation is done accordingly.
Vectors of Attack in IT/OT Combination
Systems which are out-dated.
Experience and refinement of attackers
Various Risks related to efficiency and capacity for yielding.
Liability of IT/OT.
IT/OT convergence's Various Challenges Relating to Security
Most of the teams of IT focus their attention on the security issues, and are being worried
about the same. The issues relating to the protection and shielding of various factors and
resources of environment and also its assets, which are being degrading and deploying, and steps
has to been taken to protect the same. The various challenges in regard to security includes:
Lack of Clarity
It mainly emphasis on the forecasting by the teams engaged in security department of
various issues which may arise, such as IT/OT's network connections and their
discontinuance(Savage, Coogan and Lau, 2015). As the era is of advanced and new technology
through which the development of various process and their monitoring and controlling
according to the desired results are done and managed accordingly. In this situation, the teas
found it difficulty in collecting the dynamic data and work on it.

Most of the times, even the IT employees are not aware of the changing technology and
the network information, which is a major drawback and the company are lagging at this
stage, which can lead to hacking, malware attacks, etc. This is taken as an opportunity by
the attacker, which is a risk for the company.
Less Control on the Policies Relating to Security
The teams established for the security purposes in the organizations are grappling with
the confusion and turmoil relating to the out-dated, obsolete, tedious, out of agreement of
the set of rules and standards, etc. And all this mismanagement regarding the policies set
for security purposes has become a custom for them(Boylan, 2017). Hence, the policies
implemented for the security purposes and managing the contingent risks, is full of gaps
and weaknesses.
Security Threat's Solution Relating to IT/OT Convergence
Business promoter and organizer should be the main motive behind Security an its services and
not for being in the queue in the area of industry.
Network Visibility Should be Real-Time
In the fast growing world, IT always update itself whenever there is new emergence of
reinforcement of any security in the market. But, on the other hand, the OT is not as effective as
IT and it lags, as it is still relying on the traditional concepts. Therefore, a challenges arises here
to protect the devices and equipment's which are older than a decade, as they do not consists of
any sort of security feature in-built in it. For, integration of OT with the IT, it needs to first focus
on the security and safety purposes of its devices(Kotut and Wahsheh, 2016). For installing the
software of security in the decade old system is so unrealistic as the appropriate capacity is being
required for computation of security software, which is missing. For finding appropriate solution
to this problem, firstly threats relating to the security are to be found out and ceased so that it
could not reach to the main points of OT Terminal. For this more focus has to be done on the
approaches which are realistic in nature, which can be done by following the below given steps
for security pose by the team established for IT:
Network's Incidents
Network's Asset and Equipment
Duty of each device
the network information, which is a major drawback and the company are lagging at this
stage, which can lead to hacking, malware attacks, etc. This is taken as an opportunity by
the attacker, which is a risk for the company.
Less Control on the Policies Relating to Security
The teams established for the security purposes in the organizations are grappling with
the confusion and turmoil relating to the out-dated, obsolete, tedious, out of agreement of
the set of rules and standards, etc. And all this mismanagement regarding the policies set
for security purposes has become a custom for them(Boylan, 2017). Hence, the policies
implemented for the security purposes and managing the contingent risks, is full of gaps
and weaknesses.
Security Threat's Solution Relating to IT/OT Convergence
Business promoter and organizer should be the main motive behind Security an its services and
not for being in the queue in the area of industry.
Network Visibility Should be Real-Time
In the fast growing world, IT always update itself whenever there is new emergence of
reinforcement of any security in the market. But, on the other hand, the OT is not as effective as
IT and it lags, as it is still relying on the traditional concepts. Therefore, a challenges arises here
to protect the devices and equipment's which are older than a decade, as they do not consists of
any sort of security feature in-built in it. For, integration of OT with the IT, it needs to first focus
on the security and safety purposes of its devices(Kotut and Wahsheh, 2016). For installing the
software of security in the decade old system is so unrealistic as the appropriate capacity is being
required for computation of security software, which is missing. For finding appropriate solution
to this problem, firstly threats relating to the security are to be found out and ceased so that it
could not reach to the main points of OT Terminal. For this more focus has to be done on the
approaches which are realistic in nature, which can be done by following the below given steps
for security pose by the team established for IT:
Network's Incidents
Network's Asset and Equipment
Duty of each device
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Trafficking Pattern
Lagging Points which may cause attacks.
All these things can be known easily and the real-time scene of the same can be captured
by recognition of the equipment and devices by the proper usage of the technology by the
IT Teams. This will help them in learning the Art of Management of Policies, application
of rules and regulations correctly and also each asset and device's configuration on the
network by ensuring that all the things are according to the policy pattern in the network.
Segmentation of Networks
It generally refers to distribution or breaking down of the entire network in small and distinct
division. It can be partitioned on the basis of type, purpose, causes and also the rights relating to
the network's access(Zetter, 2015). Its advantage is that, if any attacker or user which is not
authorized, tends to attack by entering into the network without access. The attack can only be
done on the particular segment or division and not on the whole or the closest of the network's
division.
Monitoring Foundation of Networks
It monitors the changes and up-gradation regarding the network division and its
deviations which are dynamic in nature. Through which the attacker can enter into the
network and can infringe various rights relating to communication and security, which in
result can cause risks and dangers ultimately. Therefore, through monitoring and up to
date information, the IT teams can keep a check on the unauthorized users and can easily
react to the disruptions.
Current Attacks in Combined Environment of IT/OT
After concerning on the power grid hacks which occurred in Ukraine in 2016, tow of the
firms which were dealing in security services proclaimed that they constituted the malignant
program, named as 'Industroyer', which can be used for attacking the Kiev Power Grid. And the
main purpose behind this was to accordingly bolt the power stations, and this was considered as
a pacifying reminder to the internet Industry(Richardson and North, 2017). As a result of which,
a large number of industries, organizations unit, families would suffer few hours darkness.
Lagging Points which may cause attacks.
All these things can be known easily and the real-time scene of the same can be captured
by recognition of the equipment and devices by the proper usage of the technology by the
IT Teams. This will help them in learning the Art of Management of Policies, application
of rules and regulations correctly and also each asset and device's configuration on the
network by ensuring that all the things are according to the policy pattern in the network.
Segmentation of Networks
It generally refers to distribution or breaking down of the entire network in small and distinct
division. It can be partitioned on the basis of type, purpose, causes and also the rights relating to
the network's access(Zetter, 2015). Its advantage is that, if any attacker or user which is not
authorized, tends to attack by entering into the network without access. The attack can only be
done on the particular segment or division and not on the whole or the closest of the network's
division.
Monitoring Foundation of Networks
It monitors the changes and up-gradation regarding the network division and its
deviations which are dynamic in nature. Through which the attacker can enter into the
network and can infringe various rights relating to communication and security, which in
result can cause risks and dangers ultimately. Therefore, through monitoring and up to
date information, the IT teams can keep a check on the unauthorized users and can easily
react to the disruptions.
Current Attacks in Combined Environment of IT/OT
After concerning on the power grid hacks which occurred in Ukraine in 2016, tow of the
firms which were dealing in security services proclaimed that they constituted the malignant
program, named as 'Industroyer', which can be used for attacking the Kiev Power Grid. And the
main purpose behind this was to accordingly bolt the power stations, and this was considered as
a pacifying reminder to the internet Industry(Richardson and North, 2017). As a result of which,
a large number of industries, organizations unit, families would suffer few hours darkness.

Legal Considerations
Cybercrime Act, 2001
The act basically emphasis on the attacks which can be of dissent for the services,
Ransom ware, Denial of service, diffusion relating to the hacking , viruses, etc. of the
computer system.
Also it includes intentionally ownership and controlling the data for committing crime.
Intentionally accessing, using and Modification of data in an Unofficial manner which
causes damage and which is being regarded as crime.
Unofficial damage of electronic communication and access or alteration of the data which
is specifically restricted.
The data which is being stored safely in a hard disk or a pen-drive. Changing or harming
them, by unauthorized usage. Moreover, having unofficial approach over the passwords
and user-names.
And, also, it take cares of the creation, moving, recuperation, etc. of the facts and figures
for the purpose of attack.
Surveillance Devices Act, 2007
It basically establishes the procedure for the officers, so that they can gain warranty,
emergency and authorization for tracking devices for the purpose of installation for
investigation accordingly(Murray, Johnstone and Valli, 2017).
And it eventually gives dissent on devices and other gadgets use, their process of
installation and other supports such as listening.
Crime Act,1900
It is applicable in the cases where, any sort of entry or access to the protected data by the
user which is unauthorized, and altering the same with the motive of committing serious
crime and causing damage.
It also emphasis on the problems caused in the process of communication by making
changes in the electronic devices by the unofficial user.
Also, it takes care of the unauthorized access over the secured data, infringing the
passwords and user-names and causing damage and harm to it intentionally.
Cybercrime Act, 2001
The act basically emphasis on the attacks which can be of dissent for the services,
Ransom ware, Denial of service, diffusion relating to the hacking , viruses, etc. of the
computer system.
Also it includes intentionally ownership and controlling the data for committing crime.
Intentionally accessing, using and Modification of data in an Unofficial manner which
causes damage and which is being regarded as crime.
Unofficial damage of electronic communication and access or alteration of the data which
is specifically restricted.
The data which is being stored safely in a hard disk or a pen-drive. Changing or harming
them, by unauthorized usage. Moreover, having unofficial approach over the passwords
and user-names.
And, also, it take cares of the creation, moving, recuperation, etc. of the facts and figures
for the purpose of attack.
Surveillance Devices Act, 2007
It basically establishes the procedure for the officers, so that they can gain warranty,
emergency and authorization for tracking devices for the purpose of installation for
investigation accordingly(Murray, Johnstone and Valli, 2017).
And it eventually gives dissent on devices and other gadgets use, their process of
installation and other supports such as listening.
Crime Act,1900
It is applicable in the cases where, any sort of entry or access to the protected data by the
user which is unauthorized, and altering the same with the motive of committing serious
crime and causing damage.
It also emphasis on the problems caused in the process of communication by making
changes in the electronic devices by the unofficial user.
Also, it takes care of the unauthorized access over the secured data, infringing the
passwords and user-names and causing damage and harm to it intentionally.

CONCLUSION
The convergence of IT/OT has lots of beneficial attributes and features, though the
movement toward it is quiet slow but highly advantageous. It will be useful to the organizations
and result in reduction in the costs, with very less risk, and also upgrade their performance. Also
the conditions has to be explored by the company for getting progress through IOT and gain
competitive \edge by reducing the risks. This security will then ultimately result as a enable for
operations of organizations rather than gridlock.
Future
As it is not a concept which is new for the organizations, and being growing steadily
from years. Developed countries are accelerating its growth for advancement, and also the
numbers of country are also increasing which are basically engaged in the merger of the IT and
OT, as every sector needs information for carrying smooth operations. The successful integration
of IT and OT will require high level skills and efforts and also working on it will provide a
strong base and lead in the market.
The convergence of IT/OT has lots of beneficial attributes and features, though the
movement toward it is quiet slow but highly advantageous. It will be useful to the organizations
and result in reduction in the costs, with very less risk, and also upgrade their performance. Also
the conditions has to be explored by the company for getting progress through IOT and gain
competitive \edge by reducing the risks. This security will then ultimately result as a enable for
operations of organizations rather than gridlock.
Future
As it is not a concept which is new for the organizations, and being growing steadily
from years. Developed countries are accelerating its growth for advancement, and also the
numbers of country are also increasing which are basically engaged in the merger of the IT and
OT, as every sector needs information for carrying smooth operations. The successful integration
of IT and OT will require high level skills and efforts and also working on it will provide a
strong base and lead in the market.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

REFERENCES
Books & Journals
Alter, K. J. 2018. The Future of International Law. The New Global Agenda, Lahnham: Rowman
& Littlefield. pp.25-42.
Bawany, N. Z., Shamsi, J. A. and Salah, K., 2017. DDoS attack detection and mitigation using
SDN: methods, practices, and solutions. Arabian Journal for Science and Engineering.
42(2). pp.425-441.
Boylan, E. 2017. Applying the Law of Proportionality to Cyber Conflict: Suggestions for
Practitioners. Vand. J. Transnat'l L.,50. p.217.
Carr, M., 2016. Public–private partnerships in national cyber-security strategies. International
Affairs. 92(1). pp.43-62.
Cavelty, M.D. 2015. Cyber-security and private actors.Routledge handbook of private security
studies. pp.89-99.
Chiang, M. and Zhang, T., 2016. Fog and IoT: An overview of research opportunities. IEEE
Internet of Things Journal. 3(6). pp.854-864.
Graham, J., Olson, R. and Howard, R., 2016. Cyber security essentials. Auerbach Publications.
Hassanalieragh, M and et.al., 2015, June. Health monitoring and management using Internet-of-
Things (IoT) sensing with cloud-based processing: Opportunities and challenges.
In 2015 IEEE International Conference on Services Computing. (pp. 285-292). IEEE.
Iannacone, M. D and et.al., 2015. Developing an Ontology for Cyber Security Knowledge
Graphs. CISR, 15. p.12.
Khan, M and et.al., 2018, October. A Model-Driven Approach for Access Control in Internet of
Things (IoT) Applications–An Introduction to UMLOA. In International Conference on
Information and Software Technologies. (pp. 198-209). Springer, Cham.
Kotut, L. and Wahsheh, L. A. 2016. April. Survey of cyber security challenges and solutions in
smart grids. In 2016 Cybersecurity Symposium (CYBERSEC). (pp. 32-37). IEEE.
Liu, X and et.al., 2018. Trace malicious source to guarantee cyber security for mass monitor
critical infrastructure. Journal of Computer and System Sciences. 98. pp.1-26.
Marjani, M and et.al., 2017. Big IoT data analytics: architecture, opportunities, and open
research challenges. IEEE Access, 5, pp.5247-5261.
Murray, G., Johnstone, M. N. and Valli, C. 2017. The convergence of IT and OT in critical
infrastructure.
Richardson, R. and North, M. M. 2017. Ransomware: Evolution, mitigation and
prevention. International Management Review. 13(1). p.10.
Savage, K., Coogan, P. and Lau, H. 2015. The evolution of ransomware. Symantec, Mountain
View.
Wang, B and et.al., 2015. DDoS attack protection in the era of cloud computing and software-
defined networking. Computer Networks. 81. pp.308-319.
Yan, Q and et.al, 2015. Software-defined networking (SDN) and distributed denial of service
(DDoS) attacks in cloud computing environments: A survey, some research issues, and
challenges. IEEE Communications Surveys & Tutorials. 18(1). pp.602-622.
Zetter, K. 2015. Hacker lexicon: A guide to Ransomware, the scary hack that’s on the
rise. Retrieved from Security, https://www. wired. com/2015/09/hacker-
lexiconguideransomware-scary-hack-thats-rise.
Books & Journals
Alter, K. J. 2018. The Future of International Law. The New Global Agenda, Lahnham: Rowman
& Littlefield. pp.25-42.
Bawany, N. Z., Shamsi, J. A. and Salah, K., 2017. DDoS attack detection and mitigation using
SDN: methods, practices, and solutions. Arabian Journal for Science and Engineering.
42(2). pp.425-441.
Boylan, E. 2017. Applying the Law of Proportionality to Cyber Conflict: Suggestions for
Practitioners. Vand. J. Transnat'l L.,50. p.217.
Carr, M., 2016. Public–private partnerships in national cyber-security strategies. International
Affairs. 92(1). pp.43-62.
Cavelty, M.D. 2015. Cyber-security and private actors.Routledge handbook of private security
studies. pp.89-99.
Chiang, M. and Zhang, T., 2016. Fog and IoT: An overview of research opportunities. IEEE
Internet of Things Journal. 3(6). pp.854-864.
Graham, J., Olson, R. and Howard, R., 2016. Cyber security essentials. Auerbach Publications.
Hassanalieragh, M and et.al., 2015, June. Health monitoring and management using Internet-of-
Things (IoT) sensing with cloud-based processing: Opportunities and challenges.
In 2015 IEEE International Conference on Services Computing. (pp. 285-292). IEEE.
Iannacone, M. D and et.al., 2015. Developing an Ontology for Cyber Security Knowledge
Graphs. CISR, 15. p.12.
Khan, M and et.al., 2018, October. A Model-Driven Approach for Access Control in Internet of
Things (IoT) Applications–An Introduction to UMLOA. In International Conference on
Information and Software Technologies. (pp. 198-209). Springer, Cham.
Kotut, L. and Wahsheh, L. A. 2016. April. Survey of cyber security challenges and solutions in
smart grids. In 2016 Cybersecurity Symposium (CYBERSEC). (pp. 32-37). IEEE.
Liu, X and et.al., 2018. Trace malicious source to guarantee cyber security for mass monitor
critical infrastructure. Journal of Computer and System Sciences. 98. pp.1-26.
Marjani, M and et.al., 2017. Big IoT data analytics: architecture, opportunities, and open
research challenges. IEEE Access, 5, pp.5247-5261.
Murray, G., Johnstone, M. N. and Valli, C. 2017. The convergence of IT and OT in critical
infrastructure.
Richardson, R. and North, M. M. 2017. Ransomware: Evolution, mitigation and
prevention. International Management Review. 13(1). p.10.
Savage, K., Coogan, P. and Lau, H. 2015. The evolution of ransomware. Symantec, Mountain
View.
Wang, B and et.al., 2015. DDoS attack protection in the era of cloud computing and software-
defined networking. Computer Networks. 81. pp.308-319.
Yan, Q and et.al, 2015. Software-defined networking (SDN) and distributed denial of service
(DDoS) attacks in cloud computing environments: A survey, some research issues, and
challenges. IEEE Communications Surveys & Tutorials. 18(1). pp.602-622.
Zetter, K. 2015. Hacker lexicon: A guide to Ransomware, the scary hack that’s on the
rise. Retrieved from Security, https://www. wired. com/2015/09/hacker-
lexiconguideransomware-scary-hack-thats-rise.

1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





