Cyber Security in Medium Enterprise Organizations
VerifiedAdded on 2023/05/30
|8
|1375
|165
AI Summary
This report gives a clear overview about the organizational security standards and strategies. The security of the organizational networks is of utmost priority in order to eliminate the risks of data breach as well as misuse of data by the hackers. This report shows the network security procedures for medium scale enterprise organizations using the HIPAA compliance standards.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CYBER SECURITY IN MEDIUM ENTERPRISE ORGANIZATIONS
CYBER SECURITY IN MEDIUM ENTERPRISE ORGANIZATIONS
Name of the student:
Name of the university:
Author note:
CYBER SECURITY IN MEDIUM ENTERPRISE ORGANIZATIONS
Name of the student:
Name of the university:
Author note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1CYBER SECURITY IN MEDIUM ENTERPRISE ORGANIZATIONS
Table of Contents
Overview of the report:....................................................................................................................2
Description of the system:...............................................................................................................2
Framework governing the enterprise:..............................................................................................3
Major gaps in the system:................................................................................................................4
Recommendations:..........................................................................................................................5
- Auditing and mapping can be performed:............................................................................5
- Mac address filtering can be done in the network:...............................................................5
- Using 802.1X for the purpose of authentication:..................................................................5
High Level Diagram representing the current state of the system...................................................5
Equal Diagram representing the Proper End State..........................................................................6
References:......................................................................................................................................7
Table of Contents
Overview of the report:....................................................................................................................2
Description of the system:...............................................................................................................2
Framework governing the enterprise:..............................................................................................3
Major gaps in the system:................................................................................................................4
Recommendations:..........................................................................................................................5
- Auditing and mapping can be performed:............................................................................5
- Mac address filtering can be done in the network:...............................................................5
- Using 802.1X for the purpose of authentication:..................................................................5
High Level Diagram representing the current state of the system...................................................5
Equal Diagram representing the Proper End State..........................................................................6
References:......................................................................................................................................7

2CYBER SECURITY IN MEDIUM ENTERPRISE ORGANIZATIONS
Overview of the report:
This report gives a clear overview about the organizational security standards and
strategies. The security of the organizational networks is of utmost priority in order to eliminate
the risks of data breach as well as misuse of data by the hackers. This report shows the network
security procedures for medium scale enterprise organizations using the HIPAA compliance
standards. No security standards can give assurance of complete data protection for the
organizations. However if the HIPAA compliances are properly implemented in the healthcare
industries the security of the organizational data stored in the networks can be optimized. This
report highlights the description of such a security system for the organizations including the risk
assessment and mitigation techniques and recommendations for data security. The report also
clearly gives recommendations for a proper disaster recovery mechanism within the companies
including the action plans and milestones that the company aims to achieve in terms of data
security. This report explains the components of a security standard for the healthcare industry.
The different kinds of electronic transactions within the healthcare organizations such as cancer
institute’s and hospitals should be well protected. This will not only help the medical
practitioners, nurses, doctors and other medical experts in securing the patient medical data,
prescriptions and health insurance data but also ensure to secure such sensitive data from the
hackers and the outside world. These aspects have been clearly explained in the report.
Description of the system:
The present network solutions makes use of the different network servers and workstation
which are commonly connected in the same network. The internal hosts such as the systems can
communicate with the external servers through a firewall in order to prevent any kind of eternal
Overview of the report:
This report gives a clear overview about the organizational security standards and
strategies. The security of the organizational networks is of utmost priority in order to eliminate
the risks of data breach as well as misuse of data by the hackers. This report shows the network
security procedures for medium scale enterprise organizations using the HIPAA compliance
standards. No security standards can give assurance of complete data protection for the
organizations. However if the HIPAA compliances are properly implemented in the healthcare
industries the security of the organizational data stored in the networks can be optimized. This
report highlights the description of such a security system for the organizations including the risk
assessment and mitigation techniques and recommendations for data security. The report also
clearly gives recommendations for a proper disaster recovery mechanism within the companies
including the action plans and milestones that the company aims to achieve in terms of data
security. This report explains the components of a security standard for the healthcare industry.
The different kinds of electronic transactions within the healthcare organizations such as cancer
institute’s and hospitals should be well protected. This will not only help the medical
practitioners, nurses, doctors and other medical experts in securing the patient medical data,
prescriptions and health insurance data but also ensure to secure such sensitive data from the
hackers and the outside world. These aspects have been clearly explained in the report.
Description of the system:
The present network solutions makes use of the different network servers and workstation
which are commonly connected in the same network. The internal hosts such as the systems can
communicate with the external servers through a firewall in order to prevent any kind of eternal

3CYBER SECURITY IN MEDIUM ENTERPRISE ORGANIZATIONS
virus attacks and other data security related issues entering the internal organizational network.
The network firewall system is installed within a DMZ zone. Separate network switches a swell
as VLAN technology is used to interconnect the different departments within the organization
and the network is further divided into smaller parts to reduce the issues such as collision as well
as congestion of data traffic. Layered data routing is used within the network for load
management whereas layer three switching is used for server configuration. Layer two switching
is used for implementation as the clients.
Third party processers are used within the organization therefore the different open
source frameworks are also used for the implementation of the network security solution in order
to ensure optimization of the network security. The different workstation and hosts connected
over the network can access the common resources such as printer, scanner and other devices
shared over the network. The transmission of data packets from the internal devices as well as
the request of incoming traffic for the external network have to happen across the network
firewall that has been installed in the DMZ zone within the network to ensure optimum data and
information security.
Framework governing the enterprise:
The HIPAA framework is used in the proposed security solution which will help in the
proper measurement of the security parameters. All the important data such as the transaction
details form the patients including the other important data such as medical records,
prescriptions, personal details of the patients as well as their health insurance data should be
stored securely over the network which is possible using the HIPAA framework. The useful data
of the internal operations of the hospitals as well as the clinics can be stored and transmitted
securely across the different department so the organizations. The electronic transactions of the
virus attacks and other data security related issues entering the internal organizational network.
The network firewall system is installed within a DMZ zone. Separate network switches a swell
as VLAN technology is used to interconnect the different departments within the organization
and the network is further divided into smaller parts to reduce the issues such as collision as well
as congestion of data traffic. Layered data routing is used within the network for load
management whereas layer three switching is used for server configuration. Layer two switching
is used for implementation as the clients.
Third party processers are used within the organization therefore the different open
source frameworks are also used for the implementation of the network security solution in order
to ensure optimization of the network security. The different workstation and hosts connected
over the network can access the common resources such as printer, scanner and other devices
shared over the network. The transmission of data packets from the internal devices as well as
the request of incoming traffic for the external network have to happen across the network
firewall that has been installed in the DMZ zone within the network to ensure optimum data and
information security.
Framework governing the enterprise:
The HIPAA framework is used in the proposed security solution which will help in the
proper measurement of the security parameters. All the important data such as the transaction
details form the patients including the other important data such as medical records,
prescriptions, personal details of the patients as well as their health insurance data should be
stored securely over the network which is possible using the HIPAA framework. The useful data
of the internal operations of the hospitals as well as the clinics can be stored and transmitted
securely across the different department so the organizations. The electronic transactions of the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4CYBER SECURITY IN MEDIUM ENTERPRISE ORGANIZATIONS
healthcare should be protected to include the data of the hospitals, individual health practitioners,
and the clinics.
However, the proposed network solution for the company can also be integrated with the
open source PCI framework so that there are provisions of future integration of the PCI
standards. The network solution is so designed since the information on credit and debit card
should be stored on a secured environment of card holder data. Additionally, third party
processors form other companies can also be incorporated in the network solution using the PCI
framework to optimize the network security (Helm & Georgatos, 2014). The network solution
can also be incorporated with the NIST framework in order to achieve a better competitive
advantage and flexibility in security solutions in the future.
Major gaps in the system:
In the proposed business solution there is no redundant links available for the successful
data flow from the host to the desired destination. For instance if there is a failure of a particular
link between a particular workstation and a server in the external environment, the data cannot be
transmitted and the packet will be returned to the source system. There are no alternative routes
available for the successful transmission of the data packet. Also in the present system there is no
specific routing protocol defined for the efficient transmission of the data. There are different
kinds of routing protocols available such as routing information protocol, interior gateway
protocol, open shortest path first etc. This again is a major gap in the system since the proper
definition of a routing protocol determines the priority levels of the transmission of different data
packets while ensuring the proper transmission of data.
healthcare should be protected to include the data of the hospitals, individual health practitioners,
and the clinics.
However, the proposed network solution for the company can also be integrated with the
open source PCI framework so that there are provisions of future integration of the PCI
standards. The network solution is so designed since the information on credit and debit card
should be stored on a secured environment of card holder data. Additionally, third party
processors form other companies can also be incorporated in the network solution using the PCI
framework to optimize the network security (Helm & Georgatos, 2014). The network solution
can also be incorporated with the NIST framework in order to achieve a better competitive
advantage and flexibility in security solutions in the future.
Major gaps in the system:
In the proposed business solution there is no redundant links available for the successful
data flow from the host to the desired destination. For instance if there is a failure of a particular
link between a particular workstation and a server in the external environment, the data cannot be
transmitted and the packet will be returned to the source system. There are no alternative routes
available for the successful transmission of the data packet. Also in the present system there is no
specific routing protocol defined for the efficient transmission of the data. There are different
kinds of routing protocols available such as routing information protocol, interior gateway
protocol, open shortest path first etc. This again is a major gap in the system since the proper
definition of a routing protocol determines the priority levels of the transmission of different data
packets while ensuring the proper transmission of data.
5CYBER SECURITY IN MEDIUM ENTERPRISE ORGANIZATIONS
Recommendations:
- Auditing and mapping can be performed:
The different components of the network such as the routers, switches, servers as well as
the hosts should be properly mapped with each other including the wireless connections
in the network (Yuan & Yu 2013). This will help in establishing a proper connectivity
path between the different network components with the organization.
- Mac address filtering can be done in the network:
Mac address can help the employees in the organization to plug and play the required and
accepted devices within the organization.
- Using 802.1X for the purpose of authentication:
This ensures enterpriser-level WPA2 security with AES information encryption in order
to ensure improved network security within the organization.
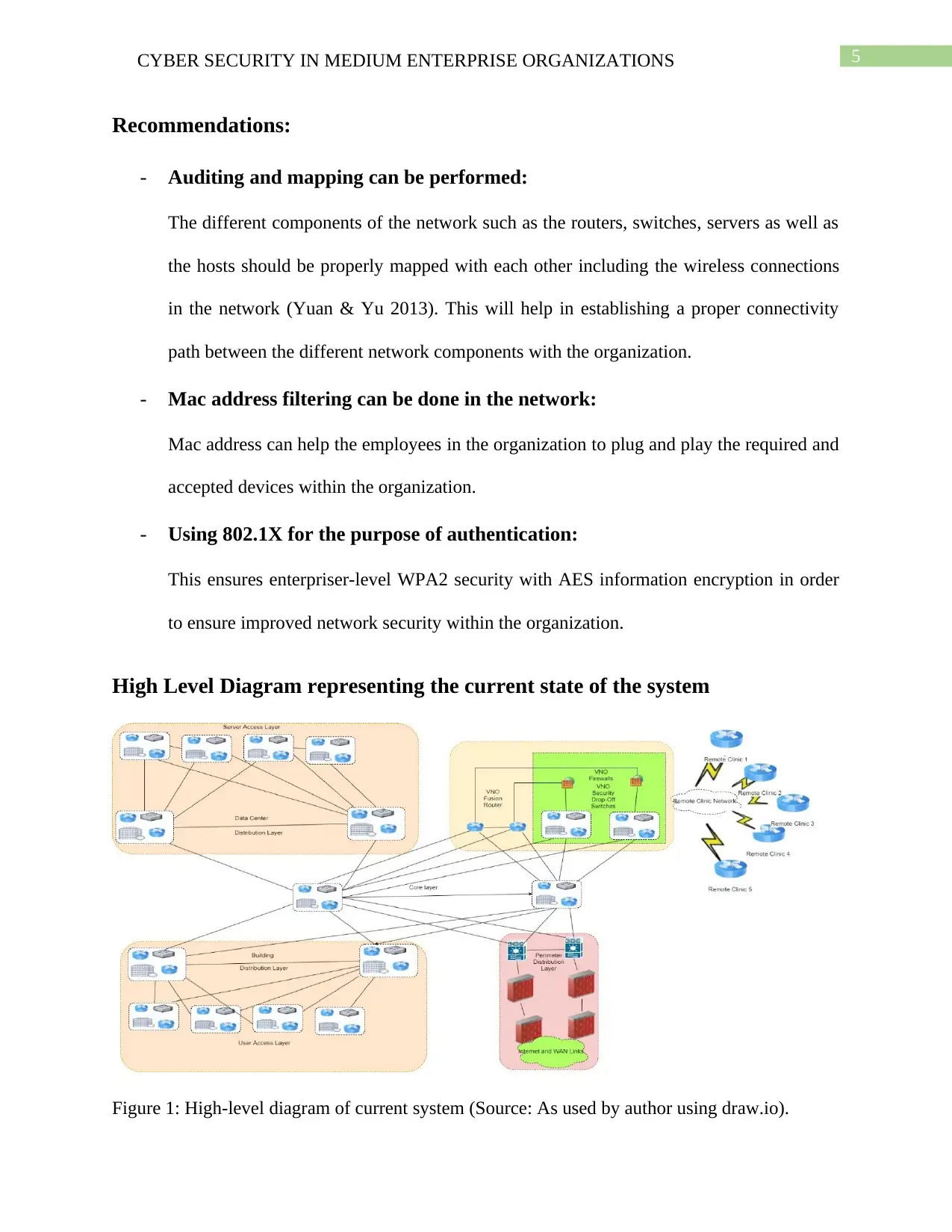
High Level Diagram representing the current state of the system
Figure 1: High-level diagram of current system (Source: As used by author using draw.io).
Recommendations:
- Auditing and mapping can be performed:
The different components of the network such as the routers, switches, servers as well as
the hosts should be properly mapped with each other including the wireless connections
in the network (Yuan & Yu 2013). This will help in establishing a proper connectivity
path between the different network components with the organization.
- Mac address filtering can be done in the network:
Mac address can help the employees in the organization to plug and play the required and
accepted devices within the organization.
- Using 802.1X for the purpose of authentication:
This ensures enterpriser-level WPA2 security with AES information encryption in order
to ensure improved network security within the organization.
High Level Diagram representing the current state of the system
Figure 1: High-level diagram of current system (Source: As used by author using draw.io).
6CYBER SECURITY IN MEDIUM ENTERPRISE ORGANIZATIONS
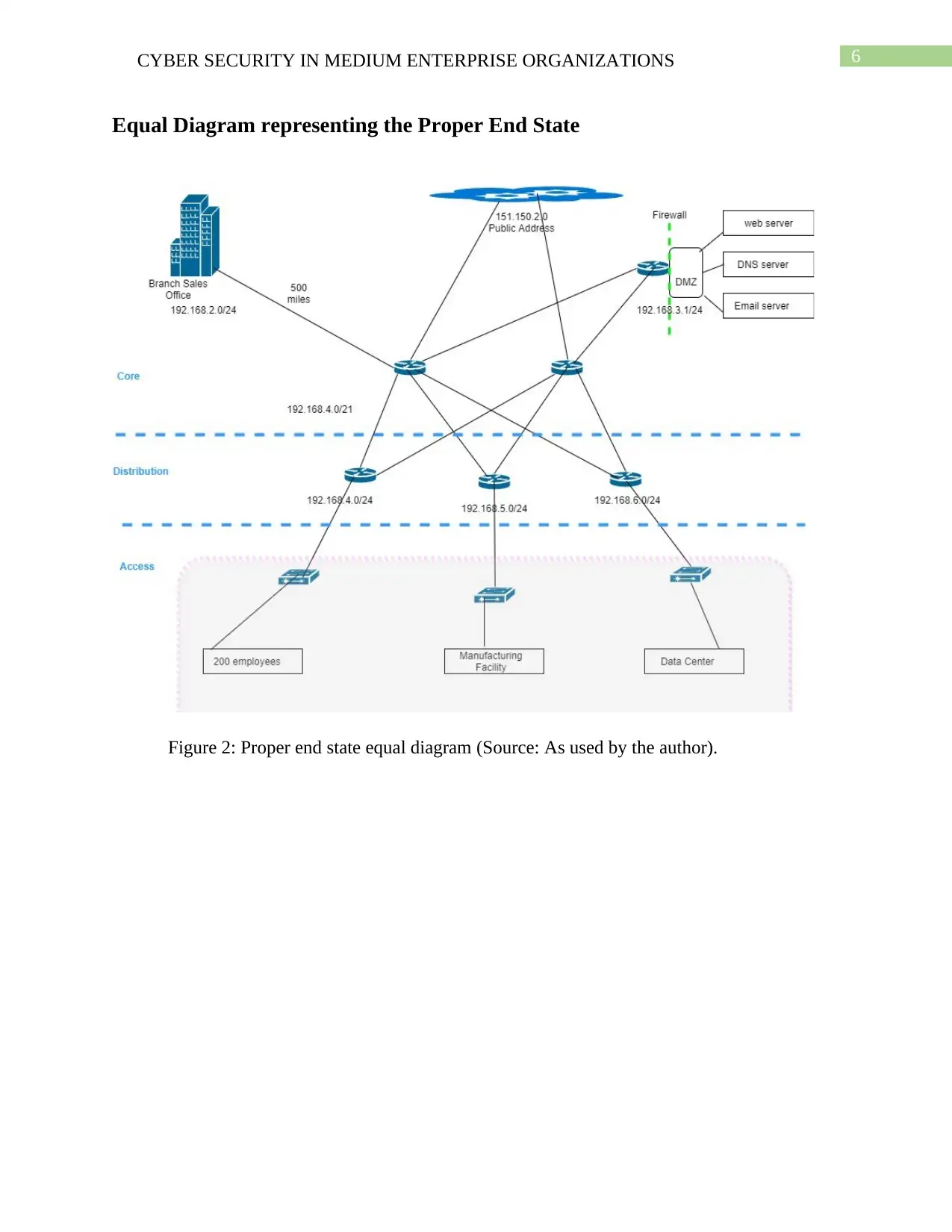
Equal Diagram representing the Proper End State
Figure 2: Proper end state equal diagram (Source: As used by the author).
Equal Diagram representing the Proper End State
Figure 2: Proper end state equal diagram (Source: As used by the author).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY IN MEDIUM ENTERPRISE ORGANIZATIONS
References:
Helm, A. M., & Georgatos, D. (2014). Privacy and mHealth: How mobile health apps fit into a
privacy framework not limited to HIPAA. Syracuse L. Rev., 64, 131.
Yuan, J., & Yu, S. (2013, October). Secure and constant cost public cloud storage auditing with
deduplication. In Communications and Network Security (CNS), 2013 IEEE Conference
on (pp. 145-153). IEEE.
References:
Helm, A. M., & Georgatos, D. (2014). Privacy and mHealth: How mobile health apps fit into a
privacy framework not limited to HIPAA. Syracuse L. Rev., 64, 131.
Yuan, J., & Yu, S. (2013, October). Secure and constant cost public cloud storage auditing with
deduplication. In Communications and Network Security (CNS), 2013 IEEE Conference
on (pp. 145-153). IEEE.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




