Cyber Security Prevention and Detection: Risk Analysis and Mitigation
VerifiedAdded on 2020/04/15
|9
|1711
|42
Report
AI Summary
This report investigates cyber security prevention and detection, focusing on security risks, their management, and potential threats to an organization's information system. It examines physical and network security, emphasizing the importance of limiting access and considering external connections. The report details the process of managing risks, including establishing effective desktop management policies, defending the network perimeter, and securing the physical environment through access control, surveillance, and testing. It presents a chart illustrating potential risks from internal and external threats, hardware, and software vulnerabilities, and emphasizes the need for proper planning and policies to mitigate these risks. The report outlines various security risk levels and provides possible solutions, stressing the continuous need for updated products, well-defined outbreak-response plans, and mitigating strategies to create obstacles against threats and defend sensitive data.

Running head: CYBER SECURITY PREVENTION AND DETECTION
Cyber Security Prevention and Detection
Name of the student:
Name of the university:
Author Note
Cyber Security Prevention and Detection
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY PREVENTION AND DETECTION
Investigating the security risks, managing risks and potential risks to the
company’s information system
The potential for the destruction, damage and loss of the assets due to the threats exploiting
the vulnerability is regarded as the security risk. The security risk management is the particular
process, structure and culture direct towards maximizing the advantages of security to support the
business objectives.
The following study has investigated the security risks. It has considered the processes to
manage the risks. Lastly, a chart is illustrated to highlight all the potential risks to the information
system of the company.
Investigating the security risks:
The platform for the SQL server includes the networking systems and physical hardware.
The best practices of the physical security have been limiting the access to the physical server along
with the hardware components. Here the first consideration is consideration of the physical security
of the machines that have been running the SQL server (Stallings and Tahiliani 2014). However, the
layer is overlooked and is the subject of uncritical satisfaction. As per as the network security is
considered, though the servers could be inaccessible physically, they have been most likely
interconnected to the network of any type. It has been just the isolated LAN of the organization
devoid of any external connection. Further, it could be the direct connection to the Internet.
Whatever the situation has been, there have been few things that are needed to be taken into
consideration.
Investigating the security risks, managing risks and potential risks to the
company’s information system
The potential for the destruction, damage and loss of the assets due to the threats exploiting
the vulnerability is regarded as the security risk. The security risk management is the particular
process, structure and culture direct towards maximizing the advantages of security to support the
business objectives.
The following study has investigated the security risks. It has considered the processes to
manage the risks. Lastly, a chart is illustrated to highlight all the potential risks to the information
system of the company.
Investigating the security risks:
The platform for the SQL server includes the networking systems and physical hardware.
The best practices of the physical security have been limiting the access to the physical server along
with the hardware components. Here the first consideration is consideration of the physical security
of the machines that have been running the SQL server (Stallings and Tahiliani 2014). However, the
layer is overlooked and is the subject of uncritical satisfaction. As per as the network security is
considered, though the servers could be inaccessible physically, they have been most likely
interconnected to the network of any type. It has been just the isolated LAN of the organization
devoid of any external connection. Further, it could be the direct connection to the Internet.
Whatever the situation has been, there have been few things that are needed to be taken into
consideration.

2CYBER SECURITY PREVENTION AND DETECTION
Managing the risks:
The internal security threats could be explicitly forbidden by bypassing the security
checkpoints in the Acceptable Use Policy. Effective desktop management policies could be
established since they have been relating to the virus protections and the various workstation
lockdown levels.
The network perimeter could be defended by conducting the daily analysis of vulnerabilities
going beyond the assessments of perimeter technologies. Here the initial step is to create the
assurances regarding the weaknesses and strengths (Oppliger, Pernul and Katsikas 2017). A set of
minimum best practices of security is to purchased, maintained and developed. This is to implement
all the platforms including the firewalls, routers, servers and desktops.
The external network could be prevented by developing the baseline of the system patch
levels, active hosts and the areas of developments. Further, insights could be gained where the
systems have not achieved the security patches (Song 2014). Lastly, new externally facing hosts
could be discovered in the environment.
The physical security could be defended by considering three components. They are the
access control, surveillance and the testing. The challenges could be placed on the path of the
potential attackers (Feng, Wang and Li 2014). The physical sites must be hardened against the
environmental disasters, attacks and the accidents.
Managing the risks:
The internal security threats could be explicitly forbidden by bypassing the security
checkpoints in the Acceptable Use Policy. Effective desktop management policies could be
established since they have been relating to the virus protections and the various workstation
lockdown levels.
The network perimeter could be defended by conducting the daily analysis of vulnerabilities
going beyond the assessments of perimeter technologies. Here the initial step is to create the
assurances regarding the weaknesses and strengths (Oppliger, Pernul and Katsikas 2017). A set of
minimum best practices of security is to purchased, maintained and developed. This is to implement
all the platforms including the firewalls, routers, servers and desktops.
The external network could be prevented by developing the baseline of the system patch
levels, active hosts and the areas of developments. Further, insights could be gained where the
systems have not achieved the security patches (Song 2014). Lastly, new externally facing hosts
could be discovered in the environment.
The physical security could be defended by considering three components. They are the
access control, surveillance and the testing. The challenges could be placed on the path of the
potential attackers (Feng, Wang and Li 2014). The physical sites must be hardened against the
environmental disasters, attacks and the accidents.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3CYBER SECURITY PREVENTION AND DETECTION
Assets
Natural
disasters
Motives
and goals
Techniques
and methods
Techniques
and methods
Techniques
and methods Security Controls and policies
Vulnerabilities
Poor security policies No security policies
Security controls stopping attacks
Internal Threats
Hardware
External
threats
Software
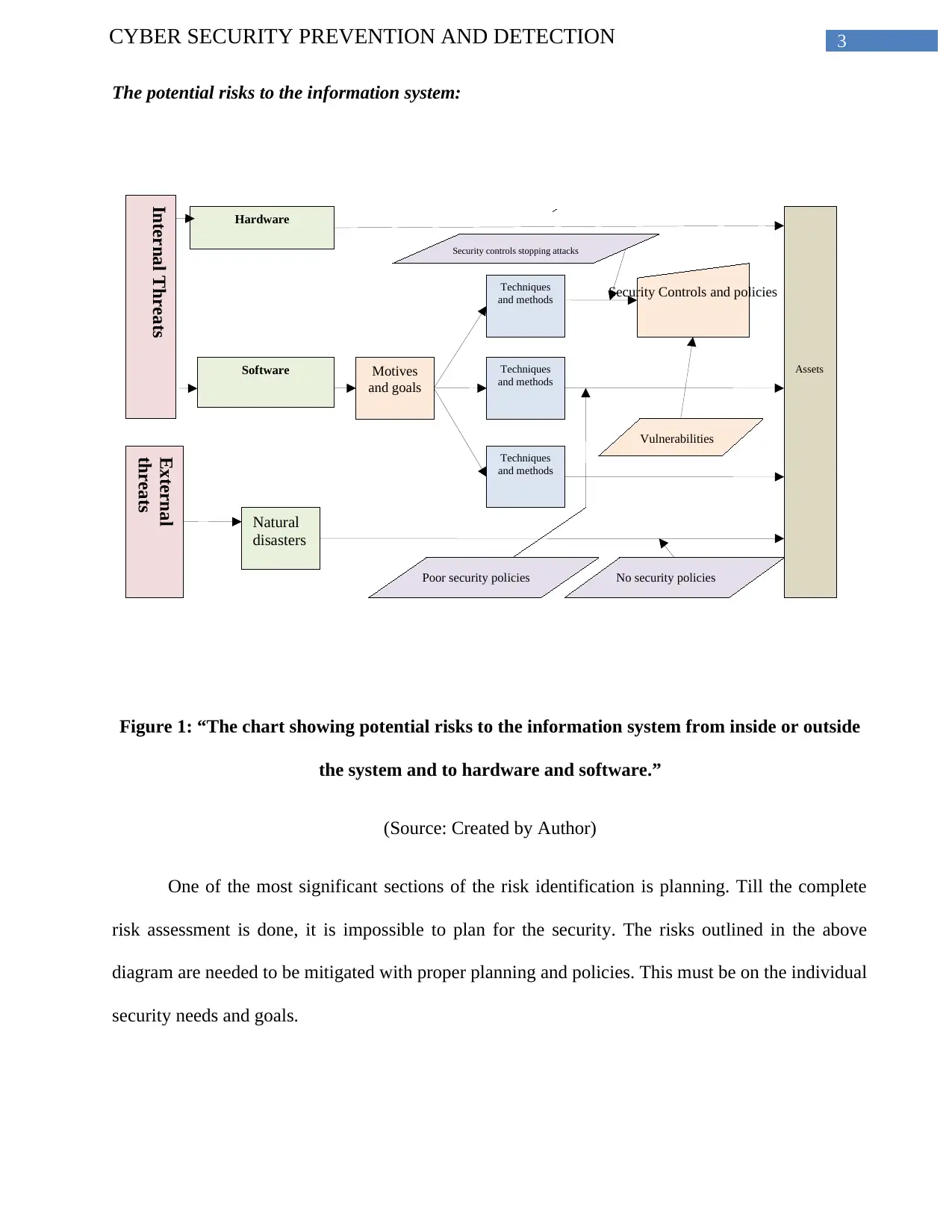
The potential risks to the information system:
Figure 1: “The chart showing potential risks to the information system from inside or outside
the system and to hardware and software.”
(Source: Created by Author)
One of the most significant sections of the risk identification is planning. Till the complete
risk assessment is done, it is impossible to plan for the security. The risks outlined in the above
diagram are needed to be mitigated with proper planning and policies. This must be on the individual
security needs and goals.
Assets
Natural
disasters
Motives
and goals
Techniques
and methods
Techniques
and methods
Techniques
and methods Security Controls and policies
Vulnerabilities
Poor security policies No security policies
Security controls stopping attacks
Internal Threats
Hardware
External
threats
Software
The potential risks to the information system:
Figure 1: “The chart showing potential risks to the information system from inside or outside
the system and to hardware and software.”
(Source: Created by Author)
One of the most significant sections of the risk identification is planning. Till the complete
risk assessment is done, it is impossible to plan for the security. The risks outlined in the above
diagram are needed to be mitigated with proper planning and policies. This must be on the individual
security needs and goals.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBER SECURITY PREVENTION AND DETECTION
As the assets get identifies, it is vital to find out every risk affecting the assets. One of the
methods to do so is to determine every different way by which the asset could be destroyed, stolen,
altered and damaged. For instance, in the current scenario, the asset is the financial information that
is kept stored in the database. Here the risks are the software flaws and bugs, penetration by hackers
accessing the machines, unauthorized modification or deletion and unauthorized disclosure of
information. This also includes the worms, Trojan horses and viruses and the misuse of hardware
and software.
The threats shown in the above diagram are the incident or actions that have the potential to
harm the organization in various ways. This includes the destruction, modification and disclosure of
information. This also consists of the denial of the critical success. The security threats are divided
into internal and external threats as illustrated in the above diagram.
Let the case of no policy for the hardware and software changes or additions is considered.
Whether getting motivated by the rise in recreation and productivity, the upgrade or addition to the
hardware or software could introduce the security vulnerabilities that are unexpected. Incorporating
the unauthorized points of access to the network could throw and open the virtual door of the garage
to the company resources and networks. In the same manner, the unauthorized screensaver could
also be harvesting the userIDs, passwords and the additional information for anyone else.
As per as the hardware equipment is considered around the security pillars, first the products
generate defense against the malware. Here the protection is given against the external threats. Next,
they just access the control for protecting against the internal risks instead of any impeding
productivity. The protections are needed to be created that must be active as any device gets stolen.
Lastly, the systems have been designed for updates and upgrades for keeping up with the developing
security necessities.
As the assets get identifies, it is vital to find out every risk affecting the assets. One of the
methods to do so is to determine every different way by which the asset could be destroyed, stolen,
altered and damaged. For instance, in the current scenario, the asset is the financial information that
is kept stored in the database. Here the risks are the software flaws and bugs, penetration by hackers
accessing the machines, unauthorized modification or deletion and unauthorized disclosure of
information. This also includes the worms, Trojan horses and viruses and the misuse of hardware
and software.
The threats shown in the above diagram are the incident or actions that have the potential to
harm the organization in various ways. This includes the destruction, modification and disclosure of
information. This also consists of the denial of the critical success. The security threats are divided
into internal and external threats as illustrated in the above diagram.
Let the case of no policy for the hardware and software changes or additions is considered.
Whether getting motivated by the rise in recreation and productivity, the upgrade or addition to the
hardware or software could introduce the security vulnerabilities that are unexpected. Incorporating
the unauthorized points of access to the network could throw and open the virtual door of the garage
to the company resources and networks. In the same manner, the unauthorized screensaver could
also be harvesting the userIDs, passwords and the additional information for anyone else.
As per as the hardware equipment is considered around the security pillars, first the products
generate defense against the malware. Here the protection is given against the external threats. Next,
they just access the control for protecting against the internal risks instead of any impeding
productivity. The protections are needed to be created that must be active as any device gets stolen.
Lastly, the systems have been designed for updates and upgrades for keeping up with the developing
security necessities.

5CYBER SECURITY PREVENTION AND DETECTION
Level 1 (Low):
Here no imminent threats are present in the network or
the system.
Level 2 (Medium):
Here the system security gets compromised and vulnerable to
the attacks.
Level 3 (High):
Here the random systems are damaged and the security
attacks get reported.
Level 4 (Critical):
The latest threats in the security are found being infested via Internet. Various
systems gets damaged and the present measures of security gets ineffective.
The possible threats are needed to be continued monitored and detected. Thus a secure environment is needed to
The latest patches are to be downloaded and the Anti-virus is to be installed.
The system is to be scanned for the security risks for mitigating the possible threats generated by the worms
The engine is to be upgraded. The harmful worms and viruses are to e scanned. The latest patches are to be downloaded. The Windows m
The level of risks The possible solutions
As per as the software vulnerabilities are concerned the software is not updated consistently
by everyone with the patches. It has been posing high risks from any attack from the hackers.
Further, there has been the constant stream of fixes that are issued in the vendor security patches and
the upgrades. These are needed to be installed for the optimal securities.
Figure 2: “The various security risk levels”
(Source: Created by Author)
Irrespective of the type of the organization, the risk is needed to be run regarding the issue of
network security. The internal dangers are present, and all kinds of business have connections
external to the vendors introducing the network to the unknown. As shown in the above diagram,
Level 1 (Low):
Here no imminent threats are present in the network or
the system.
Level 2 (Medium):
Here the system security gets compromised and vulnerable to
the attacks.
Level 3 (High):
Here the random systems are damaged and the security
attacks get reported.
Level 4 (Critical):
The latest threats in the security are found being infested via Internet. Various
systems gets damaged and the present measures of security gets ineffective.
The possible threats are needed to be continued monitored and detected. Thus a secure environment is needed to
The latest patches are to be downloaded and the Anti-virus is to be installed.
The system is to be scanned for the security risks for mitigating the possible threats generated by the worms
The engine is to be upgraded. The harmful worms and viruses are to e scanned. The latest patches are to be downloaded. The Windows m
The level of risks The possible solutions
As per as the software vulnerabilities are concerned the software is not updated consistently
by everyone with the patches. It has been posing high risks from any attack from the hackers.
Further, there has been the constant stream of fixes that are issued in the vendor security patches and
the upgrades. These are needed to be installed for the optimal securities.
Figure 2: “The various security risk levels”
(Source: Created by Author)
Irrespective of the type of the organization, the risk is needed to be run regarding the issue of
network security. The internal dangers are present, and all kinds of business have connections
external to the vendors introducing the network to the unknown. As shown in the above diagram,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBER SECURITY PREVENTION AND DETECTION
any beginning level with the link to the anonymous generates the potential risks. Thus the business
must proceed. The necessary steps are to be learnt for every level for limiting the risk of those
problems. This must also protect the data and the network from the hackers that have been lurking
outside the security perimeter.
The above study shows that without any effective disaster-recovery practices the business is
at continuous risk. The various defenses identified needs the constant upgraded products like client
security or Anti-virus and the well-defined plans of outbreak-responses. This is to deal and
determine the ever-expanding challenges. The mitigating strategies help in creating obstacles against
the threats and security risks, facilitate the removal and identification and defend the private and the
sensitive data. Instead of this protection, the company could face administrative nightmares along
with expensive and time-consuming complete system reloads for recovering the lost data.
any beginning level with the link to the anonymous generates the potential risks. Thus the business
must proceed. The necessary steps are to be learnt for every level for limiting the risk of those
problems. This must also protect the data and the network from the hackers that have been lurking
outside the security perimeter.
The above study shows that without any effective disaster-recovery practices the business is
at continuous risk. The various defenses identified needs the constant upgraded products like client
security or Anti-virus and the well-defined plans of outbreak-responses. This is to deal and
determine the ever-expanding challenges. The mitigating strategies help in creating obstacles against
the threats and security risks, facilitate the removal and identification and defend the private and the
sensitive data. Instead of this protection, the company could face administrative nightmares along
with expensive and time-consuming complete system reloads for recovering the lost data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY PREVENTION AND DETECTION
References:
Feng, N., Wang, H.J. and Li, M., 2014. A security risk analysis model for information systems:
Causal relationships of risk factors and vulnerability propagation analysis. Information
sciences, 256, pp.57-73.
Lirn.net. (2017). Library and Information Resources Network, Inc.. [online] Available at:
http://www.lirn.net/ [Accessed 15 Nov. 2017].
Lynda.com - from LinkedIn. (2017). Internal network. [online] Available at:
https://www.lynda.com/Security-tutorials/Internal-network/184142/189049-4.html [Accessed 15
Nov. 2017].
Oppliger, R., Pernul, G. and Katsikas, S., 2017. New Frontiers: Assessing and Managing Security
Risks. Computer, 50(4), pp.48-51.
Song, M.H., 2014. On Computer Network Security Risks and Emergency Response Technology.
In Applied Mechanics and Materials (Vol. 484, pp. 833-836). Trans Tech Publications.
Stallings, W. and Tahiliani, M.P., 2014. Cryptography and network security: principles and
practice (Vol. 6). London: Pearson.
References:
Feng, N., Wang, H.J. and Li, M., 2014. A security risk analysis model for information systems:
Causal relationships of risk factors and vulnerability propagation analysis. Information
sciences, 256, pp.57-73.
Lirn.net. (2017). Library and Information Resources Network, Inc.. [online] Available at:
http://www.lirn.net/ [Accessed 15 Nov. 2017].
Lynda.com - from LinkedIn. (2017). Internal network. [online] Available at:
https://www.lynda.com/Security-tutorials/Internal-network/184142/189049-4.html [Accessed 15
Nov. 2017].
Oppliger, R., Pernul, G. and Katsikas, S., 2017. New Frontiers: Assessing and Managing Security
Risks. Computer, 50(4), pp.48-51.
Song, M.H., 2014. On Computer Network Security Risks and Emergency Response Technology.
In Applied Mechanics and Materials (Vol. 484, pp. 833-836). Trans Tech Publications.
Stallings, W. and Tahiliani, M.P., 2014. Cryptography and network security: principles and
practice (Vol. 6). London: Pearson.

8CYBER SECURITY PREVENTION AND DETECTION
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





