Cyber Security Risk Assessment Report for CMP71001 Unit
VerifiedAdded on 2023/05/27
|10
|1693
|388
Report
AI Summary
This report addresses a cyber security risk assessment assignment, simulating an interview for a cybersecurity consultant position. It begins by emphasizing the importance of risk assessment in managing cyber security, identifying limitations of current methods. Task 2 focuses on developing five key questions to identify critical information assets and creating a weighted factor analysis (WFA) template for asset ranking. The report then details various cyber threats, including malware, hardware failures, and human errors, along with related statistics. Finally, it explains the CIA triad (Confidentiality, Integrity, Availability) and includes a risk matrix prioritizing different threats, hazards, and vulnerabilities. The assignment highlights the significance of protecting information assets and implementing robust cyber security measures.
Running Head: CYBER SECURITY 0 | P a g e
Cyber Security
Individual task
Student name
Cyber Security
Individual task
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security 1 | P a g e
Contents
TASK – 1.........................................................................................................................................1
TASK - 2..........................................................................................................................................1
TASK - 3..........................................................................................................................................2
TASK - 4..........................................................................................................................................2
References........................................................................................................................................3
Contents
TASK – 1.........................................................................................................................................1
TASK - 2..........................................................................................................................................1
TASK - 3..........................................................................................................................................2
TASK - 4..........................................................................................................................................2
References........................................................................................................................................3

Cyber Security 2 | P a g e
TASK – 1
Risk assessment is a process in which find the assets of an organization, which are affected from
the outside attacks. In case of cyber security, the identification of assets, which are affected from
the cyber-attacks, such as Privacy, data security, softwares, hardware. Based on these assets
could find the risks for the organization (ACSC, 2017).
Identification of risks in an organization is a tough process on the bases of their assets. There are
so many types of failures and faults in the system because of the virus, worms, and threats. There
are so many malwares, which affects the system from different sources. They may be harm
hardware or softwares of the organization (Rouse, 2013). On the bases of risk assessment, every
organization can characterize the system working; it can be change the processes, functions of
the systems according to the risk assessments.
According to my opinion, it is also beneficial for the identification of the threats for the system
of organization. Based on risk assessment, system can determine inherent risk and impacts of
different risks. Risk assessment is helpful for customization of control environment. There are
different controls according to risks in the system to the assets of an organization. There are few
different types of rating provided to the risks and based on them, administrator can take actions
for that threats. It is divided into three categories basically, which are high, medium, and low.
Basic risks of an organization from cyber-attacks are unauthorized access in to system, misuse of
information, data leakage, process failure, Loss of data, and service disruption. They all are
affected productivity of a system (Arlitsch & Edelman, 2014).
TASK – 1
Risk assessment is a process in which find the assets of an organization, which are affected from
the outside attacks. In case of cyber security, the identification of assets, which are affected from
the cyber-attacks, such as Privacy, data security, softwares, hardware. Based on these assets
could find the risks for the organization (ACSC, 2017).
Identification of risks in an organization is a tough process on the bases of their assets. There are
so many types of failures and faults in the system because of the virus, worms, and threats. There
are so many malwares, which affects the system from different sources. They may be harm
hardware or softwares of the organization (Rouse, 2013). On the bases of risk assessment, every
organization can characterize the system working; it can be change the processes, functions of
the systems according to the risk assessments.
According to my opinion, it is also beneficial for the identification of the threats for the system
of organization. Based on risk assessment, system can determine inherent risk and impacts of
different risks. Risk assessment is helpful for customization of control environment. There are
different controls according to risks in the system to the assets of an organization. There are few
different types of rating provided to the risks and based on them, administrator can take actions
for that threats. It is divided into three categories basically, which are high, medium, and low.
Basic risks of an organization from cyber-attacks are unauthorized access in to system, misuse of
information, data leakage, process failure, Loss of data, and service disruption. They all are
affected productivity of a system (Arlitsch & Edelman, 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cyber Security 3 | P a g e
TASK - 2
There are basic five questions about the identification of the critical information assets:
What is Information Assets of an organization?
What is identification of assets of an organization?
What is the value of assets of an organization?
What is Critical information assets management?
What are the types of informational assets of an organization?
A single entity, which is having body of knowledge in managed and organized manner, is known
as information assets. They are having financial value for an organization. They are also public
record with in few criteria. In case of information architecture, organization devices, data, and
the processes are accepted as assets. Information assets are may be URL’s, and Meta data of the
organization (qgcio.qld.gov.au, 2018). Critical information assets management is a task for
protection and controlling the information assets of an organization. There are an information life
cycles of a system. It is having rights for allowing changes over time in the system processes
(Barkly, 2018).
Every organization is dividing their informational assets in three groups, which are following:
Public
Internal
Restricted
All are separate according to the priority bases. These are depending on the risk assessment
report of the organization (BWISE, 2018).
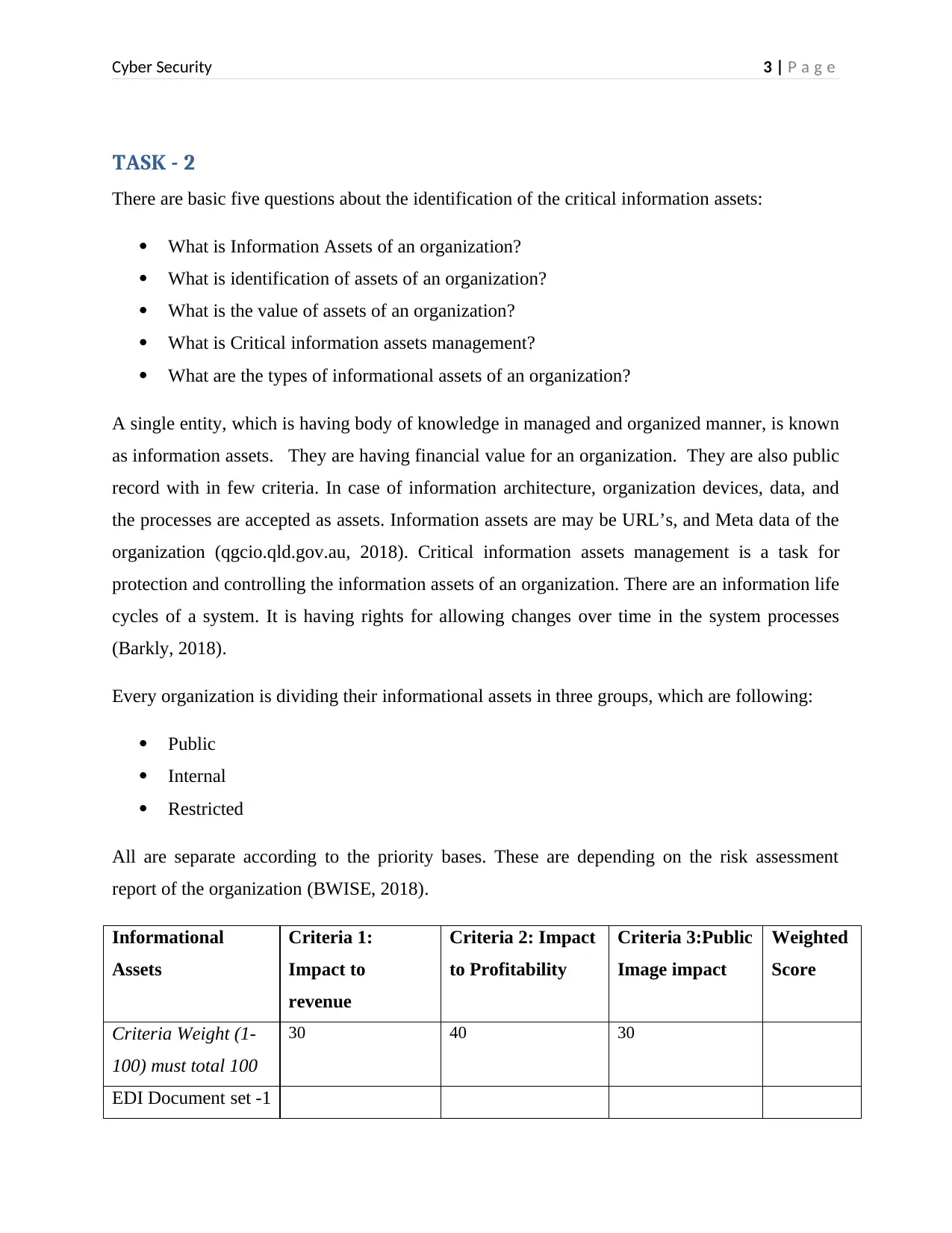
Informational
Assets
Criteria 1:
Impact to
revenue
Criteria 2: Impact
to Profitability
Criteria 3:Public
Image impact
Weighted
Score
Criteria Weight (1-
100) must total 100
30 40 30
EDI Document set -1
TASK - 2
There are basic five questions about the identification of the critical information assets:
What is Information Assets of an organization?
What is identification of assets of an organization?
What is the value of assets of an organization?
What is Critical information assets management?
What are the types of informational assets of an organization?
A single entity, which is having body of knowledge in managed and organized manner, is known
as information assets. They are having financial value for an organization. They are also public
record with in few criteria. In case of information architecture, organization devices, data, and
the processes are accepted as assets. Information assets are may be URL’s, and Meta data of the
organization (qgcio.qld.gov.au, 2018). Critical information assets management is a task for
protection and controlling the information assets of an organization. There are an information life
cycles of a system. It is having rights for allowing changes over time in the system processes
(Barkly, 2018).
Every organization is dividing their informational assets in three groups, which are following:
Public
Internal
Restricted
All are separate according to the priority bases. These are depending on the risk assessment
report of the organization (BWISE, 2018).
Informational
Assets
Criteria 1:
Impact to
revenue
Criteria 2: Impact
to Profitability
Criteria 3:Public
Image impact
Weighted
Score
Criteria Weight (1-
100) must total 100
30 40 30
EDI Document set -1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cyber Security 4 | P a g e
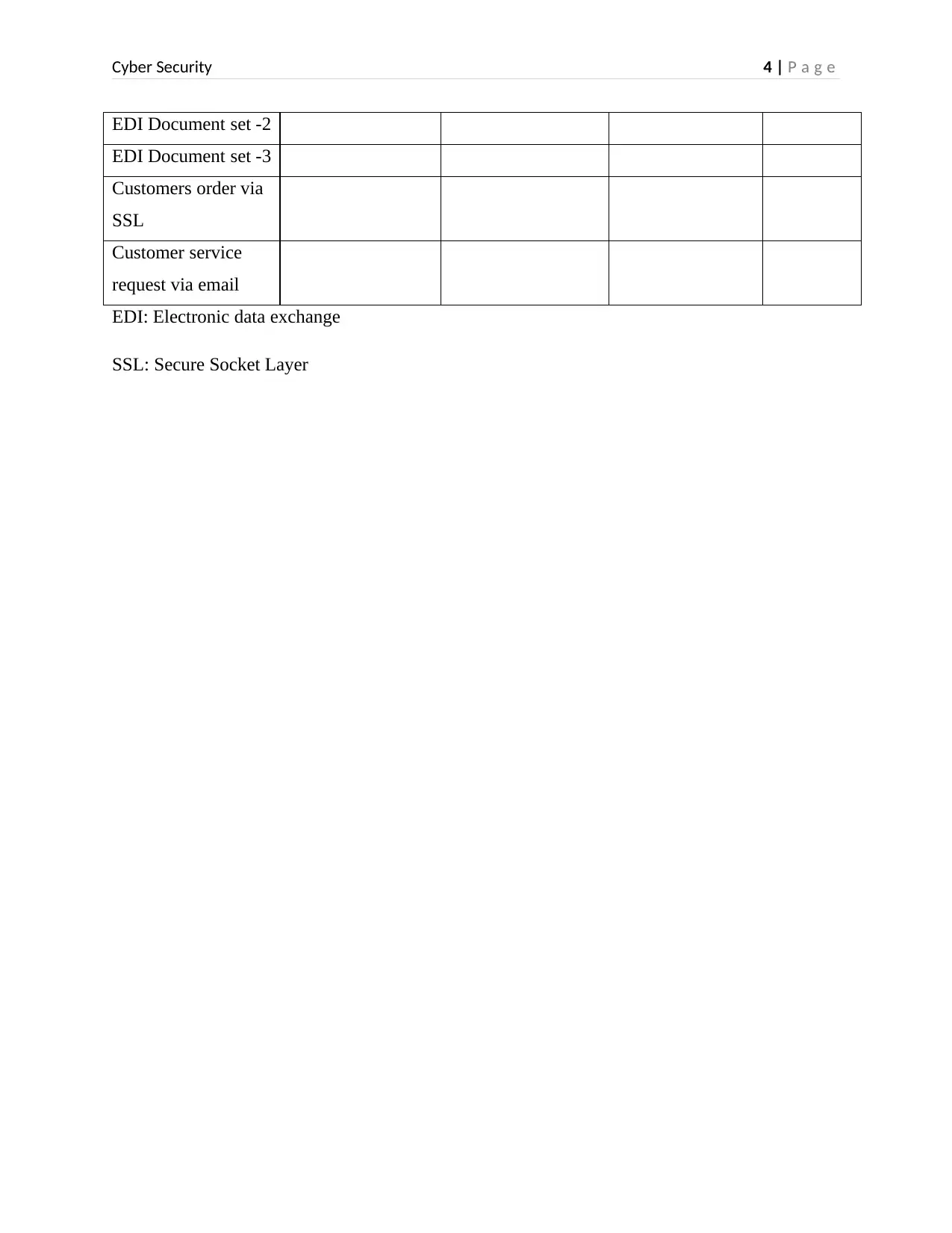
EDI Document set -2
EDI Document set -3
Customers order via
SSL
Customer service
request via email
EDI: Electronic data exchange
SSL: Secure Socket Layer
EDI Document set -2
EDI Document set -3
Customers order via
SSL
Customer service
request via email
EDI: Electronic data exchange
SSL: Secure Socket Layer

Cyber Security 5 | P a g e
TASK - 3
These are the threats for an organization:
Deliberate software attack
Technical hardware failure or errors
Acts of human error or failure
Technological obsolescence
Deliberate acts of theft
In case of information technology, threats are having different types, such as malwares. Cyber
criminals are affect the system working or data of the organization through different processes.
Few examples of threats are:
Malware: these are the malicious softwares, which are having a code. That code is damaging
personal computers and other devices. It could be computer virus, worms, spyware, and Trojan
horse. Hazards are the anything that poses threats to break the security of a computer system or
damage them. It is may be defective hardware, corrupted system files, and hackers. Cyber-
attacks are something like robbery of data or denied access to the computer system. Hackers are
change data of a system or change the access of system. Sometime they demand ransom for
providing access to the system (Sanchez, 2010).
Incidents are the affected computers form the computer virus. They are totally corrupted from
the malware and it will be an incidents. Security threats are so important for the organization. In
case of the security attacks of an organization, there cyber security team is also responsible for
the cyber-attacks. There are so any standards in different countries for cyber security.
Government of Australia is making new policies and laws for the cyber security. They are
helpful for the organizations for preventions of cyber-attacks. There is a way to avoid those
cyber-attacks. Different organizations are providing cyber security facilities to the different
companies. Mainly small businesses are affected from the cyber-attacks, because of less security
(Fruhlinger, 2018).
TASK - 3
These are the threats for an organization:
Deliberate software attack
Technical hardware failure or errors
Acts of human error or failure
Technological obsolescence
Deliberate acts of theft
In case of information technology, threats are having different types, such as malwares. Cyber
criminals are affect the system working or data of the organization through different processes.
Few examples of threats are:
Malware: these are the malicious softwares, which are having a code. That code is damaging
personal computers and other devices. It could be computer virus, worms, spyware, and Trojan
horse. Hazards are the anything that poses threats to break the security of a computer system or
damage them. It is may be defective hardware, corrupted system files, and hackers. Cyber-
attacks are something like robbery of data or denied access to the computer system. Hackers are
change data of a system or change the access of system. Sometime they demand ransom for
providing access to the system (Sanchez, 2010).
Incidents are the affected computers form the computer virus. They are totally corrupted from
the malware and it will be an incidents. Security threats are so important for the organization. In
case of the security attacks of an organization, there cyber security team is also responsible for
the cyber-attacks. There are so any standards in different countries for cyber security.
Government of Australia is making new policies and laws for the cyber security. They are
helpful for the organizations for preventions of cyber-attacks. There is a way to avoid those
cyber-attacks. Different organizations are providing cyber security facilities to the different
companies. Mainly small businesses are affected from the cyber-attacks, because of less security
(Fruhlinger, 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cyber Security 6 | P a g e
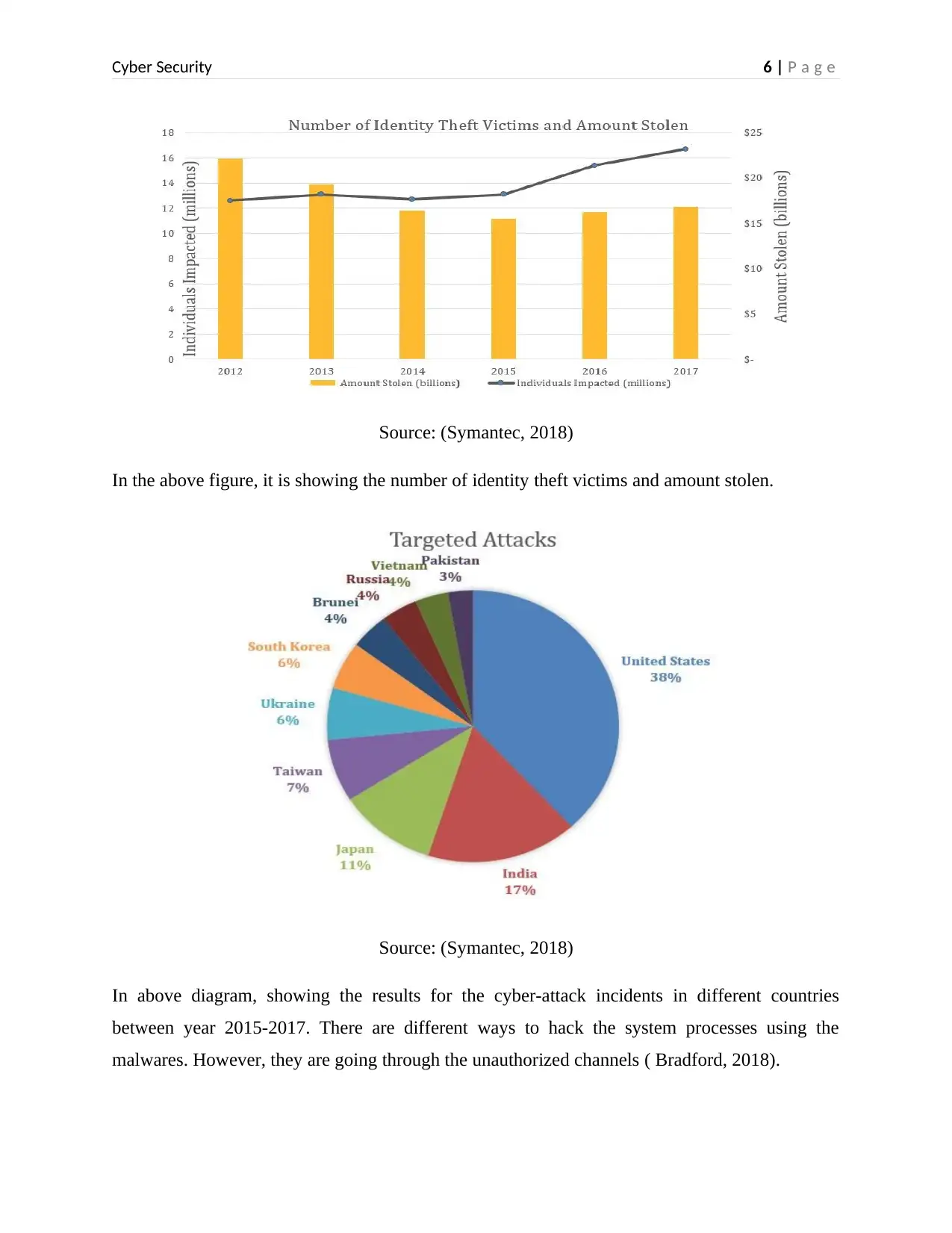
Source: (Symantec, 2018)
In the above figure, it is showing the number of identity theft victims and amount stolen.
Source: (Symantec, 2018)
In above diagram, showing the results for the cyber-attack incidents in different countries
between year 2015-2017. There are different ways to hack the system processes using the
malwares. However, they are going through the unauthorized channels ( Bradford, 2018).
Source: (Symantec, 2018)
In the above figure, it is showing the number of identity theft victims and amount stolen.
Source: (Symantec, 2018)
In above diagram, showing the results for the cyber-attack incidents in different countries
between year 2015-2017. There are different ways to hack the system processes using the
malwares. However, they are going through the unauthorized channels ( Bradford, 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cyber Security 7 | P a g e
TASK - 4
Confidentiality of information is a protecting the information of the organization from outside of
the world. It means that information cannot share with the unauthorized parties. In this case,
different things are considered in the information, such as bank account statements, personal
information, credit card numbers, trade secrets, and government records ( Chia, 2012).
Integrity of information means protecting information from hackers and unauthorized persons
inside the system as well as outside. It means right information should transfer to the next party.
It is also playing a major role for data integrity of an organization.
Availability means, authorized person can access the information, when they require it. They are
so many incidents in which an unauthorized person accesses the system and they made changes
in the data, which is so costly for the organization (Kassa, 2017).
There are so many methods for risk assessment of an organization. Especially in the Information
technology based organization. There are so many risks from the cyber-attack, so, there should
be a risk matrix for handling the different risk for the system. There are few priorities for
different threats, hazards, and vulnerabilities of the system.
Threats Ranks
Deliberate software attack 1
Technical hardware failure or errors 3
Acts of human error or failure 2
Technological obsolescence 5
Deliberate acts of theft 4
Source: Author
TASK - 4
Confidentiality of information is a protecting the information of the organization from outside of
the world. It means that information cannot share with the unauthorized parties. In this case,
different things are considered in the information, such as bank account statements, personal
information, credit card numbers, trade secrets, and government records ( Chia, 2012).
Integrity of information means protecting information from hackers and unauthorized persons
inside the system as well as outside. It means right information should transfer to the next party.
It is also playing a major role for data integrity of an organization.
Availability means, authorized person can access the information, when they require it. They are
so many incidents in which an unauthorized person accesses the system and they made changes
in the data, which is so costly for the organization (Kassa, 2017).
There are so many methods for risk assessment of an organization. Especially in the Information
technology based organization. There are so many risks from the cyber-attack, so, there should
be a risk matrix for handling the different risk for the system. There are few priorities for
different threats, hazards, and vulnerabilities of the system.
Threats Ranks
Deliberate software attack 1
Technical hardware failure or errors 3
Acts of human error or failure 2
Technological obsolescence 5
Deliberate acts of theft 4
Source: Author

Cyber Security 8 | P a g e
References
Bradford, L., 2018. What You Need To Know About Cybersecurity In 2018. [Online]
Available at: https://www.forbes.com/sites/laurencebradford/2018/03/30/why-people-should-
learn-about-cybersecurity-in-2018/#7c88f6fe5d00
[Accessed 11 December 2018].
Chia, T., 2012. Confidentiality, Integrity, Availability: The three components of the CIA Triad.
[Online]
Available at: https://security.blogoverflow.com/2012/08/confidentiality-integrity-availability-
the-three-components-of-the-cia-triad/
[Accessed 11 December 2018].
ACSC, 2017. Australian Cyber Security Centre. [Online]
Available at: https://www.acsc.gov.au/publications/ACSC_Threat_Report_2017.pdf
[Accessed 12 December 2018].
Arlitsch, K. & Edelman, A., 2014. Staying safe: Cyber security for people and organizations.
Journal of Library Administration, 54(1), pp. 46-56.
Barkly, 2018. 5 Cybersecurity Statistics Every Small Business Should Know in 2018. [Online]
Available at: https://blog.barkly.com/small-business-cybersecurity-statistics-2018
BWISE, 2018. nist cyber security framework. [Online]
Available at: https://www.bwise.com/solutions/frameworks/nist-framework
Fruhlinger, J., 2018. Top cybersecurity facts, figures and statistics for 2018. [Online]
Available at: https://www.csoonline.com/article/3153707/security/top-cybersecurity-facts-
figures-and-statistics.html
[Accessed 11 december 2018].
Kassa, S. G., 2017. IT Asset Valuation, Risk Assessment and Control Implementation Model.
[Online]
References
Bradford, L., 2018. What You Need To Know About Cybersecurity In 2018. [Online]
Available at: https://www.forbes.com/sites/laurencebradford/2018/03/30/why-people-should-
learn-about-cybersecurity-in-2018/#7c88f6fe5d00
[Accessed 11 December 2018].
Chia, T., 2012. Confidentiality, Integrity, Availability: The three components of the CIA Triad.
[Online]
Available at: https://security.blogoverflow.com/2012/08/confidentiality-integrity-availability-
the-three-components-of-the-cia-triad/
[Accessed 11 December 2018].
ACSC, 2017. Australian Cyber Security Centre. [Online]
Available at: https://www.acsc.gov.au/publications/ACSC_Threat_Report_2017.pdf
[Accessed 12 December 2018].
Arlitsch, K. & Edelman, A., 2014. Staying safe: Cyber security for people and organizations.
Journal of Library Administration, 54(1), pp. 46-56.
Barkly, 2018. 5 Cybersecurity Statistics Every Small Business Should Know in 2018. [Online]
Available at: https://blog.barkly.com/small-business-cybersecurity-statistics-2018
BWISE, 2018. nist cyber security framework. [Online]
Available at: https://www.bwise.com/solutions/frameworks/nist-framework
Fruhlinger, J., 2018. Top cybersecurity facts, figures and statistics for 2018. [Online]
Available at: https://www.csoonline.com/article/3153707/security/top-cybersecurity-facts-
figures-and-statistics.html
[Accessed 11 december 2018].
Kassa, S. G., 2017. IT Asset Valuation, Risk Assessment and Control Implementation Model.
[Online]
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security 9 | P a g e
Available at: https://www.isaca.org/Journal/archives/2017/Volume-3/Pages/it-asset-valuation-
risk-assessment-and-control-implementation-model.aspx
[Accessed 11 December 2018].
qgcio.qld.gov.au, 2018. Information Asset (Definition). [Online]
Available at: https://www.qgcio.qld.gov.au/publications/qgcio-glossary/information-asset-
definition
[Accessed 11 December 2018].
Rouse, M., 2013. information asset. [Online]
Available at: https://whatis.techtarget.com/definition/information-assets
[Accessed 12 December 2018].
Sanchez, M., 2010. The 10 most common security threats explained. [Online]
Available at: https://blogs.cisco.com/smallbusiness/the-10-most-common-security-threats-
explained
[Accessed 12 Devember 2018].
Symantec, 2018. 10 cyber security facts and statistics for 2018. [Online]
Available at: https://us.norton.com/internetsecurity-emerging-threats-10-facts-about-todays-
cybersecurity-landscape-that-you-should-know.html
[Accessed 11 December 2018].
Available at: https://www.isaca.org/Journal/archives/2017/Volume-3/Pages/it-asset-valuation-
risk-assessment-and-control-implementation-model.aspx
[Accessed 11 December 2018].
qgcio.qld.gov.au, 2018. Information Asset (Definition). [Online]
Available at: https://www.qgcio.qld.gov.au/publications/qgcio-glossary/information-asset-
definition
[Accessed 11 December 2018].
Rouse, M., 2013. information asset. [Online]
Available at: https://whatis.techtarget.com/definition/information-assets
[Accessed 12 December 2018].
Sanchez, M., 2010. The 10 most common security threats explained. [Online]
Available at: https://blogs.cisco.com/smallbusiness/the-10-most-common-security-threats-
explained
[Accessed 12 Devember 2018].
Symantec, 2018. 10 cyber security facts and statistics for 2018. [Online]
Available at: https://us.norton.com/internetsecurity-emerging-threats-10-facts-about-todays-
cybersecurity-landscape-that-you-should-know.html
[Accessed 11 December 2018].
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





