Advanced Research: Cybersecurity and Facial Biometric Systems Review
VerifiedAdded on 2023/01/18
|10
|887
|52
Report
AI Summary
This report delves into the application of facial biometric systems within the realm of cybersecurity. It begins by defining cybersecurity and its key elements, followed by an explanation of biometric systems and facial recognition technology. The report then outlines the working process of facial biometric systems, from image capture to facial geometry analysis and authentication. It also presents the advantages, such as increased security and automation, and disadvantages, including data processing concerns and potential image quality issues. The report is supported by a range of references from academic journals and publications, providing a comprehensive overview of the topic.

Cyber security through facial biometric system
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

What is Cyber-security?
The technology which is designed to protect
devices, data or programs from any
unauthorized access is known as cyber-
security. This factor is also termed as IT
security.
The technology which is designed to protect
devices, data or programs from any
unauthorized access is known as cyber-
security. This factor is also termed as IT
security.

Elements of Cyber
Security
The components of cyber security comprises
of following mentioned below:
Security in network
Security in applications
Safety of endpoints
Data reliability
Management of identity
Safety in database
Security in clouding
Mobile safety
Disaster rehabilitation
Education up to end point
Security
The components of cyber security comprises
of following mentioned below:
Security in network
Security in applications
Safety of endpoints
Data reliability
Management of identity
Safety in database
Security in clouding
Mobile safety
Disaster rehabilitation
Education up to end point
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
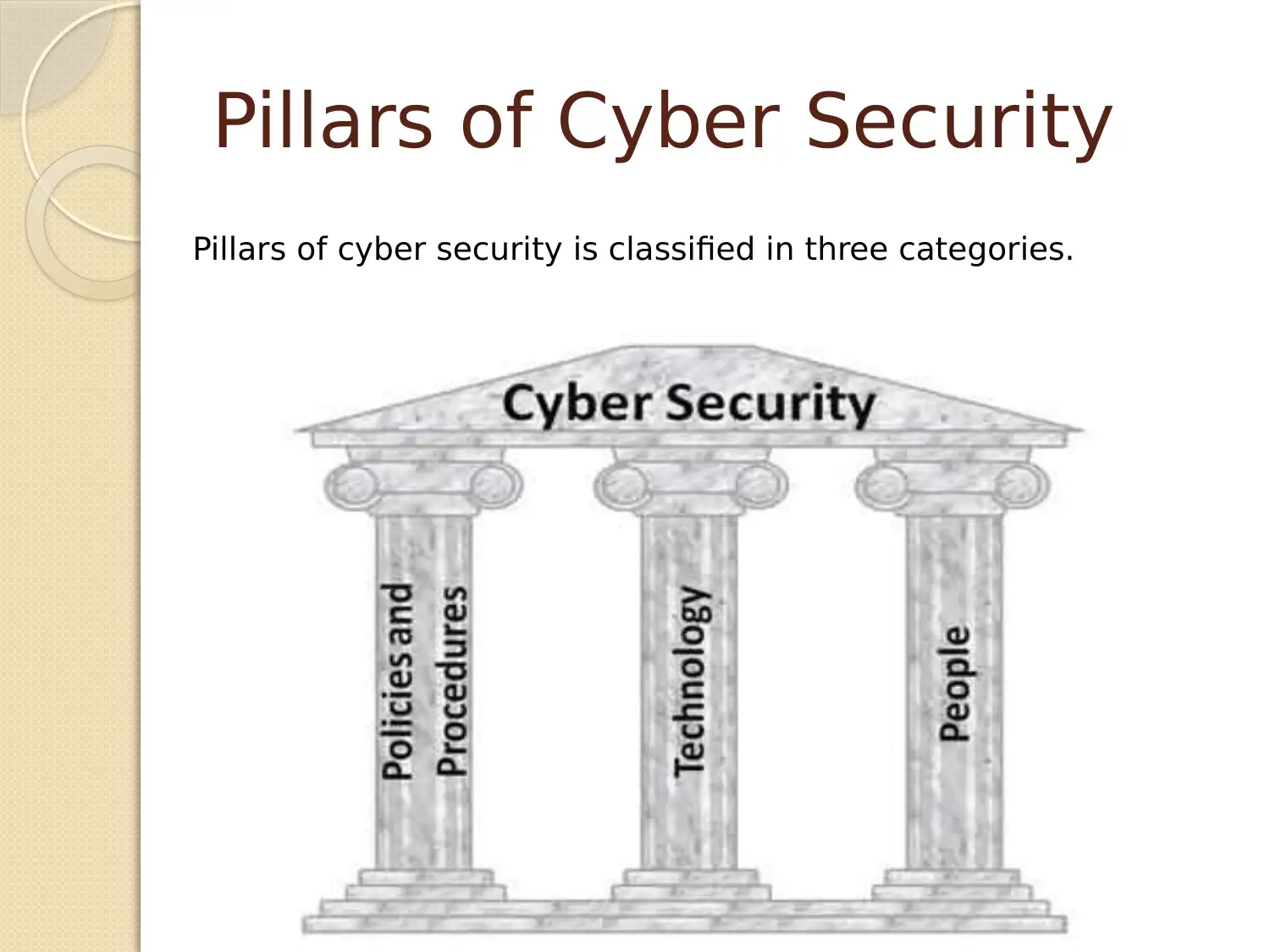
Pillars of Cyber Security
Pillars of cyber security is classified in three categories.
Pillars of cyber security is classified in three categories.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
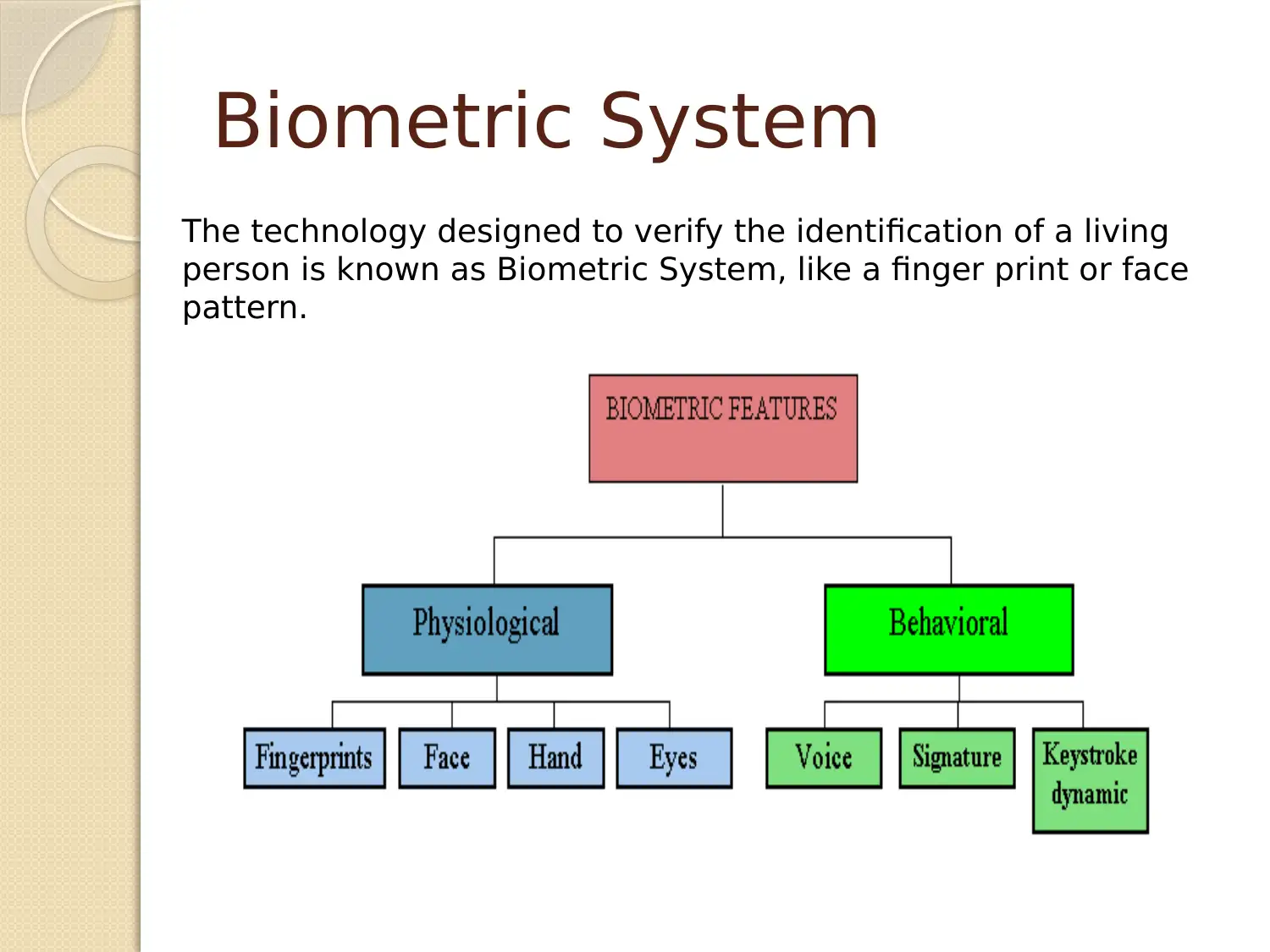
Biometric System
The technology designed to verify the identification of a living
person is known as Biometric System, like a finger print or face
pattern.
The technology designed to verify the identification of a living
person is known as Biometric System, like a finger print or face
pattern.

Cyber security by Facial Biometric
System
What is Facial Biometric System?
It is a system which is designed in a manner that it
verifies the person with the digital image by
comparing and analyzing the pattern.
System
What is Facial Biometric System?
It is a system which is designed in a manner that it
verifies the person with the digital image by
comparing and analyzing the pattern.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
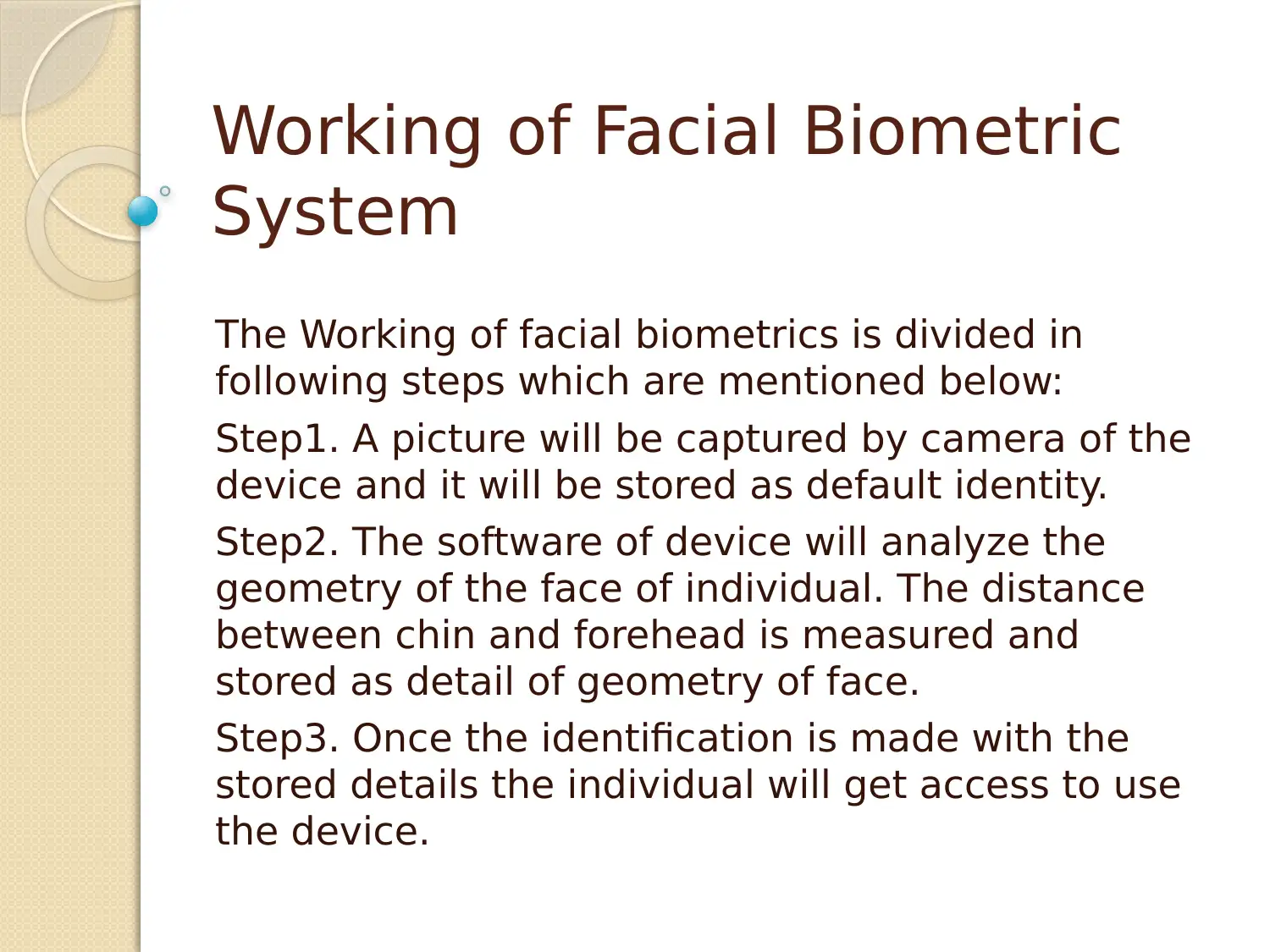
Working of Facial Biometric
System
The Working of facial biometrics is divided in
following steps which are mentioned below:
Step1. A picture will be captured by camera of the
device and it will be stored as default identity.
Step2. The software of device will analyze the
geometry of the face of individual. The distance
between chin and forehead is measured and
stored as detail of geometry of face.
Step3. Once the identification is made with the
stored details the individual will get access to use
the device.
System
The Working of facial biometrics is divided in
following steps which are mentioned below:
Step1. A picture will be captured by camera of the
device and it will be stored as default identity.
Step2. The software of device will analyze the
geometry of the face of individual. The distance
between chin and forehead is measured and
stored as detail of geometry of face.
Step3. Once the identification is made with the
stored details the individual will get access to use
the device.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
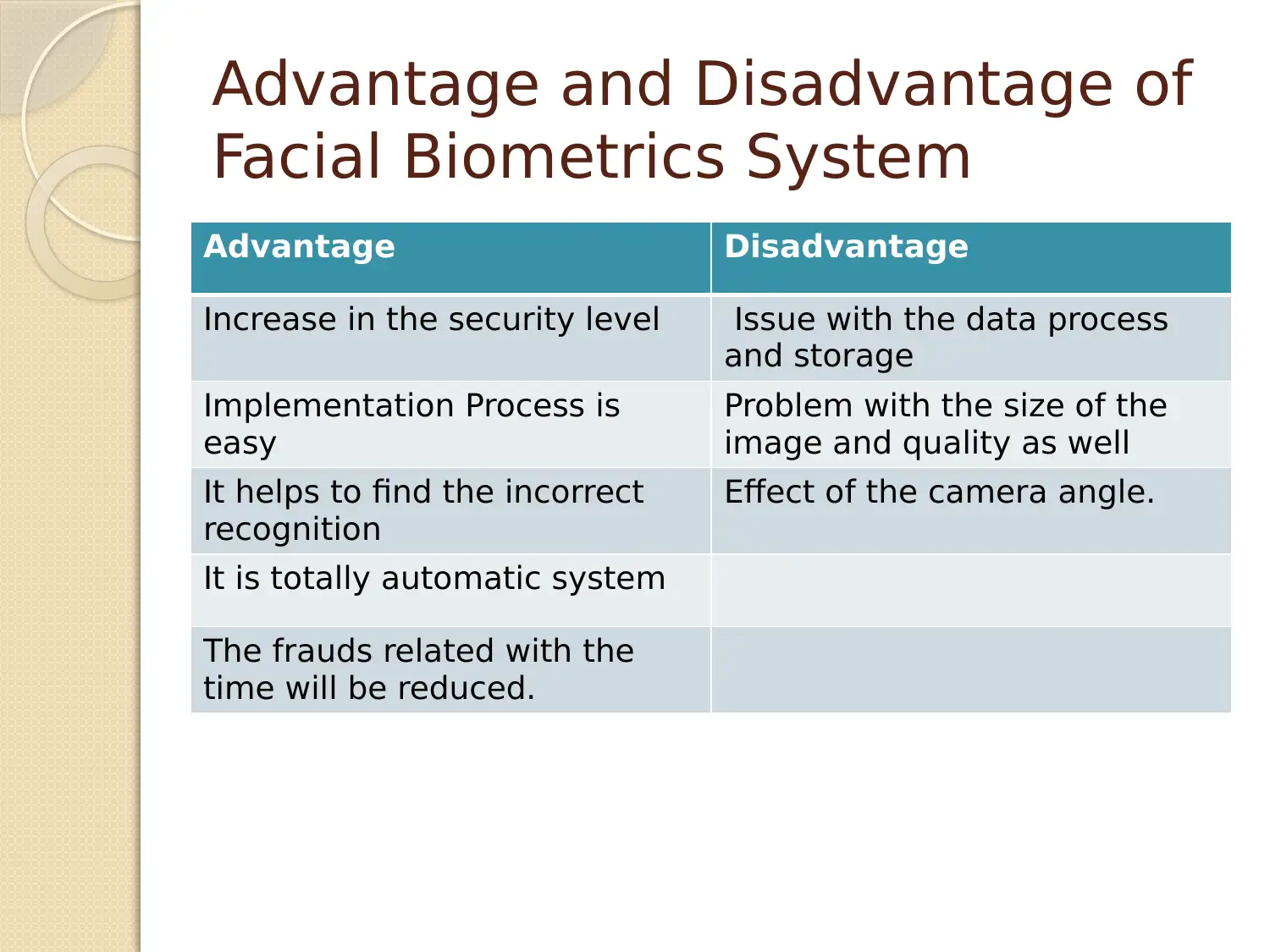
Advantage and Disadvantage of
Facial Biometrics System
Advantage Disadvantage
Increase in the security level Issue with the data process
and storage
Implementation Process is
easy
Problem with the size of the
image and quality as well
It helps to find the incorrect
recognition
Effect of the camera angle.
It is totally automatic system
The frauds related with the
time will be reduced.
Facial Biometrics System
Advantage Disadvantage
Increase in the security level Issue with the data process
and storage
Implementation Process is
easy
Problem with the size of the
image and quality as well
It helps to find the incorrect
recognition
Effect of the camera angle.
It is totally automatic system
The frauds related with the
time will be reduced.

References
Jang-Jaccard, J. and Nepal, S., 2014. A survey of emerging threats in
cybersecurity. Journal of Computer and System Sciences, 80(5), pp.973-993.
Schneidewind, N., 2009. Metrics for mitigating cybersecurity threats to
networks. IEEE Internet Computing, 14(1), pp.64-71.
Peng, S.Y., 2015. Cybersecurity threats and the WTO national security
exceptions. Journal of International Economic Law, 18(2), pp.449-478.
Andreasson, K.J. ed., 2011. Cybersecurity: public sector threats and responses. CRC
press.
Jain, A.K., Ross, A. and Prabhakar, S., 2004. An introduction to biometric
recognition. IEEE Transactions on circuits and systems for video technology, 14(1).
Jain, A., Hong, L. and Pankanti, S., 2000. Biometric identification. Communications of
the ACM, 43(2), pp.90-98.
Jain, A.K., Nandakumar, K. and Nagar, A., 2008. Biometric template security. EURASIP
Journal on advances in signal processing, 2008, p.113.
Prabhakar, S., Pankanti, S. and Jain, A.K., 2003. Biometric recognition: Security and
privacy concerns. IEEE security & privacy, (2), pp.33-42.
Bonsor, K. and Johnson, R., 2001. How facial recognition systems
work. HowStuffWorks. com. Np, 4.
Meenakshi, M., 2013. Real-Time Facial Recognition System—Design, Implementation
and Validation. Journal of Signal Processing Theory and Applications, 1, pp.1-18.
Jang-Jaccard, J. and Nepal, S., 2014. A survey of emerging threats in
cybersecurity. Journal of Computer and System Sciences, 80(5), pp.973-993.
Schneidewind, N., 2009. Metrics for mitigating cybersecurity threats to
networks. IEEE Internet Computing, 14(1), pp.64-71.
Peng, S.Y., 2015. Cybersecurity threats and the WTO national security
exceptions. Journal of International Economic Law, 18(2), pp.449-478.
Andreasson, K.J. ed., 2011. Cybersecurity: public sector threats and responses. CRC
press.
Jain, A.K., Ross, A. and Prabhakar, S., 2004. An introduction to biometric
recognition. IEEE Transactions on circuits and systems for video technology, 14(1).
Jain, A., Hong, L. and Pankanti, S., 2000. Biometric identification. Communications of
the ACM, 43(2), pp.90-98.
Jain, A.K., Nandakumar, K. and Nagar, A., 2008. Biometric template security. EURASIP
Journal on advances in signal processing, 2008, p.113.
Prabhakar, S., Pankanti, S. and Jain, A.K., 2003. Biometric recognition: Security and
privacy concerns. IEEE security & privacy, (2), pp.33-42.
Bonsor, K. and Johnson, R., 2001. How facial recognition systems
work. HowStuffWorks. com. Np, 4.
Meenakshi, M., 2013. Real-Time Facial Recognition System—Design, Implementation
and Validation. Journal of Signal Processing Theory and Applications, 1, pp.1-18.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

• Lawton, G., 1998. Biometrics: a new era in
security. Computer, (8), pp.16-18.
• Xiao, Q. and Yang, X.D., 2009, March. A facial presence
monitoring system for information security. In 2009 IEEE
Workshop on Computational Intelligence in Biometrics:
Theory, Algorithms, and Applications (pp. 69-76). IEEE.
• Jain, A.K. and Kumar, A., 2012. Biometric recognition: an
overview. In Second generation biometrics: The ethical,
legal and social context (pp. 49-79). Springer, Dordrecht.
• Andreasson, K.J. ed., 2011. Cybersecurity: public sector
threats and responses. CRC press.
• Kemmerer, R.A., 2003, May. Cybersecurity. In Proceedings
of the 25th international conference on Software
engineering (pp. 705-715). IEEE Computer Society.
• Mackey, T.K. and Nayyar, G., 2016. Digital danger: a
review of the global public health, patient safety and
cybersecurity threats posed by illicit online
pharmacies. British medical bulletin, 118(1), pp.110-126.
• Jouini, M., Rabai, L.B.A. and Aissa, A.B., 2014.
Classification of security threats in information
systems. Procedia Computer Science, 32, pp.489-496.
• Nolan, A., 2015. Cybersecurity and information sharing:
Legal challenges and solutions. Congressional Research
Service.
security. Computer, (8), pp.16-18.
• Xiao, Q. and Yang, X.D., 2009, March. A facial presence
monitoring system for information security. In 2009 IEEE
Workshop on Computational Intelligence in Biometrics:
Theory, Algorithms, and Applications (pp. 69-76). IEEE.
• Jain, A.K. and Kumar, A., 2012. Biometric recognition: an
overview. In Second generation biometrics: The ethical,
legal and social context (pp. 49-79). Springer, Dordrecht.
• Andreasson, K.J. ed., 2011. Cybersecurity: public sector
threats and responses. CRC press.
• Kemmerer, R.A., 2003, May. Cybersecurity. In Proceedings
of the 25th international conference on Software
engineering (pp. 705-715). IEEE Computer Society.
• Mackey, T.K. and Nayyar, G., 2016. Digital danger: a
review of the global public health, patient safety and
cybersecurity threats posed by illicit online
pharmacies. British medical bulletin, 118(1), pp.110-126.
• Jouini, M., Rabai, L.B.A. and Aissa, A.B., 2014.
Classification of security threats in information
systems. Procedia Computer Science, 32, pp.489-496.
• Nolan, A., 2015. Cybersecurity and information sharing:
Legal challenges and solutions. Congressional Research
Service.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




