Enhancing Cyber Security with VPN, SSL and Digital Signatures
VerifiedAdded on 2023/06/08
|10
|1977
|395
AI Summary
This article discusses the importance of cyber security and how VPN, SSL and Digital Signatures can enhance it. It covers topics like authentication, confidentiality, integrity, and more. The article also explains how SSL works and how symmetric algorithms can be used to encrypt data. It concludes with a discussion on how to prevent replay attacks and maintain data security.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CYBER SECURITY
Cyber Security
Name of the student
Name of the university
Author Note
Cyber Security
Name of the student
Name of the university
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
CYBER SECURITY
Table of Contents
Introduction....................................................................................................................2
Authentication................................................................................................................2
Browser and server connection:.................................................................................2
Digital Signatures:......................................................................................................3
Server client checking................................................................................................4
Confidentiality and Integrity..........................................................................................5
Secured Socket Layer.................................................................................................5
Symmetric algorithm:.................................................................................................5
Repay Attack..............................................................................................................6
Conclusion......................................................................................................................7
References......................................................................................................................8
CYBER SECURITY
Table of Contents
Introduction....................................................................................................................2
Authentication................................................................................................................2
Browser and server connection:.................................................................................2
Digital Signatures:......................................................................................................3
Server client checking................................................................................................4
Confidentiality and Integrity..........................................................................................5
Secured Socket Layer.................................................................................................5
Symmetric algorithm:.................................................................................................5
Repay Attack..............................................................................................................6
Conclusion......................................................................................................................7
References......................................................................................................................8

2
CYBER SECURITY
Introduction:
The virtual private network can be explained as the software that is used for the
purpose of enhancing internet security. Virtual private networks helps in the creating added
security by enhancing the private network. The VPN works in top of the browsers in order to
enhance the security. In order to enhance the security the VPN creates a safe zone where the
network is restricted [7]. On the other hand the digital signatures can be explained as the
digital form of a signature which uses the concept of cryptography for encryption. This paper
explains about some of the most enhanced security options that can help the user to make the
internet world safe.
Authentication
Browser and server connection:
The web browsers and the servers communicate in between each other using the
TCP/IP protocols. Further the hypertext transfer protocol helps in the process providing extra
support to the web browsers and providing extra security to the servers. The connection starts
when the user whites or specifies the web address of the website [5]. The browser then
initiates a TCP connections where the browser reaches the server and the finds out the IP
address of website. After the websites IP is checked the browser requests the HTTPS of the
hypertext transfer protocol secured content form the servers. After this the acknowledgement
is done and the content is checked and the webpage is displayed in the browser. This ensures
that there is proper security in the services of the servers and there is no fault regarding this.
CYBER SECURITY
Introduction:
The virtual private network can be explained as the software that is used for the
purpose of enhancing internet security. Virtual private networks helps in the creating added
security by enhancing the private network. The VPN works in top of the browsers in order to
enhance the security. In order to enhance the security the VPN creates a safe zone where the
network is restricted [7]. On the other hand the digital signatures can be explained as the
digital form of a signature which uses the concept of cryptography for encryption. This paper
explains about some of the most enhanced security options that can help the user to make the
internet world safe.
Authentication
Browser and server connection:
The web browsers and the servers communicate in between each other using the
TCP/IP protocols. Further the hypertext transfer protocol helps in the process providing extra
support to the web browsers and providing extra security to the servers. The connection starts
when the user whites or specifies the web address of the website [5]. The browser then
initiates a TCP connections where the browser reaches the server and the finds out the IP
address of website. After the websites IP is checked the browser requests the HTTPS of the
hypertext transfer protocol secured content form the servers. After this the acknowledgement
is done and the content is checked and the webpage is displayed in the browser. This ensures
that there is proper security in the services of the servers and there is no fault regarding this.

3
CYBER SECURITY
(Figure1: Browser Server Communication)
(Source:[9])
Digital Signatures:
The digital signatures are the signatures which are made in the digital form which
helps in the process of the increased security and options. Further this digital signatures are
uniquely encrypted so that these can help in the process of security. This works like there are
certain user signs a using a digital device. The signature is then encrypted using the public
key cryptography format and a hash key is generated for the same [7]. The hash key is then
saved for the future purpose of checking. When there is a need of authentication for the same,
when the user signs a signature a hash key is generated and this hash key is checked with the
previous hash key. If there is a match then the signature is authorised. This digital signatures
helps in the process of checking the security off any system [6]. It is one of the most secured
method for the process of keeping data safe as no 2 signatures can be same. Hence this is one
of the best way for the process of keeping data safe.
CYBER SECURITY
(Figure1: Browser Server Communication)
(Source:[9])
Digital Signatures:
The digital signatures are the signatures which are made in the digital form which
helps in the process of the increased security and options. Further this digital signatures are
uniquely encrypted so that these can help in the process of security. This works like there are
certain user signs a using a digital device. The signature is then encrypted using the public
key cryptography format and a hash key is generated for the same [7]. The hash key is then
saved for the future purpose of checking. When there is a need of authentication for the same,
when the user signs a signature a hash key is generated and this hash key is checked with the
previous hash key. If there is a match then the signature is authorised. This digital signatures
helps in the process of checking the security off any system [6]. It is one of the most secured
method for the process of keeping data safe as no 2 signatures can be same. Hence this is one
of the best way for the process of keeping data safe.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4
CYBER SECURITY
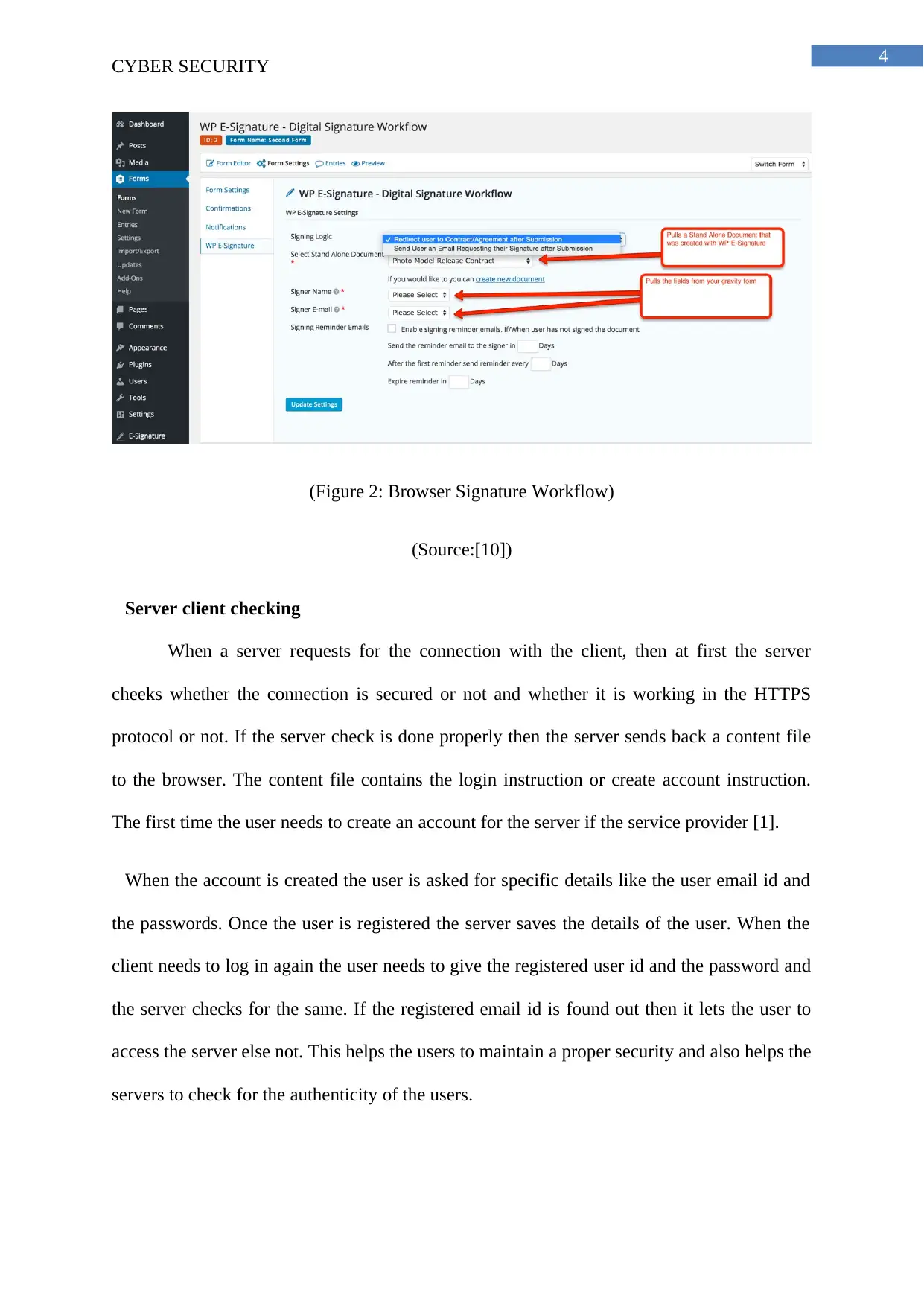
(Figure 2: Browser Signature Workflow)
(Source:[10])
Server client checking
When a server requests for the connection with the client, then at first the server
cheeks whether the connection is secured or not and whether it is working in the HTTPS
protocol or not. If the server check is done properly then the server sends back a content file
to the browser. The content file contains the login instruction or create account instruction.
The first time the user needs to create an account for the server if the service provider [1].
When the account is created the user is asked for specific details like the user email id and
the passwords. Once the user is registered the server saves the details of the user. When the
client needs to log in again the user needs to give the registered user id and the password and
the server checks for the same. If the registered email id is found out then it lets the user to
access the server else not. This helps the users to maintain a proper security and also helps the
servers to check for the authenticity of the users.
CYBER SECURITY
(Figure 2: Browser Signature Workflow)
(Source:[10])
Server client checking
When a server requests for the connection with the client, then at first the server
cheeks whether the connection is secured or not and whether it is working in the HTTPS
protocol or not. If the server check is done properly then the server sends back a content file
to the browser. The content file contains the login instruction or create account instruction.
The first time the user needs to create an account for the server if the service provider [1].
When the account is created the user is asked for specific details like the user email id and
the passwords. Once the user is registered the server saves the details of the user. When the
client needs to log in again the user needs to give the registered user id and the password and
the server checks for the same. If the registered email id is found out then it lets the user to
access the server else not. This helps the users to maintain a proper security and also helps the
servers to check for the authenticity of the users.

5
CYBER SECURITY
Confidentiality and Integrity
Secured Socket Layer
The SSL or the secured socket layer can be explained as a standard that is used for the
purpose of the establishing encrypted lines in-between the web servers and the web browsers
for the purpose of the online communication [3]. The SSL helps in the process of the creating
a certificate for the purpose of the providing extra security. The SSL and the TSL provides
the users with the authentication, identification and the confidentiality and maintaining proper
integrity. The authentication helps in the process of the authenticating the user that is to check
whether to check if the user is correct or not [2]. These are done using the processes of the
cryptography and hence reduces the chances of the any threat from the world.
Symmetric algorithm:
The symmetric algorithm can be explained as the process in which a single key is
used for the both the purpose of the encryption and decryption. This is not one of the best
way for the process of the security in the public domain but can help in the process of the
security in the private transactions. The hash algorithms can be explained as the process of
the encrypting a certain message using the process of the cryptography. This is one of the
most secured thing that can be done in order to enhance the security of the servers. The hash
keys are using in the symmetric connections hence ensures that there is proper security
maintained in the transactions. [4] Further with the use of the hash keys there are no chances
on of any hacking as these keys are very much tough to get hacked.
CYBER SECURITY
Confidentiality and Integrity
Secured Socket Layer
The SSL or the secured socket layer can be explained as a standard that is used for the
purpose of the establishing encrypted lines in-between the web servers and the web browsers
for the purpose of the online communication [3]. The SSL helps in the process of the creating
a certificate for the purpose of the providing extra security. The SSL and the TSL provides
the users with the authentication, identification and the confidentiality and maintaining proper
integrity. The authentication helps in the process of the authenticating the user that is to check
whether to check if the user is correct or not [2]. These are done using the processes of the
cryptography and hence reduces the chances of the any threat from the world.
Symmetric algorithm:
The symmetric algorithm can be explained as the process in which a single key is
used for the both the purpose of the encryption and decryption. This is not one of the best
way for the process of the security in the public domain but can help in the process of the
security in the private transactions. The hash algorithms can be explained as the process of
the encrypting a certain message using the process of the cryptography. This is one of the
most secured thing that can be done in order to enhance the security of the servers. The hash
keys are using in the symmetric connections hence ensures that there is proper security
maintained in the transactions. [4] Further with the use of the hash keys there are no chances
on of any hacking as these keys are very much tough to get hacked.

6
CYBER SECURITY
(Figure 3: Browser Hash details)
Source: [2]
Repay Attack
The repay attack which is also known as the payback attacks can be explained as a
form of network attack in which the authenticated data transmission is frequently repeated or
delayed. It can be carried out using the intercepting the transmitting data through a network
channel. This can be explained as one of the most dangerous form of attack that is made in
the network sources. This helps the hackers to access the information that is being transferred
and then send false data to the source [9]. This can be reduced by sending encrypted data to
the sources and hence reduce the chances of any such risk. Using the SSL or the secured
socket layer is one of the other major use of this where the user data can be encrypted suing
the symmetrical or the asymmetrical use of the data and hence reduce the chances of this type
of the risk. The encryption process stops the hacker from accessing the data hence the data
cannot be used.
CYBER SECURITY
(Figure 3: Browser Hash details)
Source: [2]
Repay Attack
The repay attack which is also known as the payback attacks can be explained as a
form of network attack in which the authenticated data transmission is frequently repeated or
delayed. It can be carried out using the intercepting the transmitting data through a network
channel. This can be explained as one of the most dangerous form of attack that is made in
the network sources. This helps the hackers to access the information that is being transferred
and then send false data to the source [9]. This can be reduced by sending encrypted data to
the sources and hence reduce the chances of any such risk. Using the SSL or the secured
socket layer is one of the other major use of this where the user data can be encrypted suing
the symmetrical or the asymmetrical use of the data and hence reduce the chances of this type
of the risk. The encryption process stops the hacker from accessing the data hence the data
cannot be used.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CYBER SECURITY
Further the use of the secured layer socket connections helps the user to locate of
there is any break in the journey of the data [8]. One of the other major way through which
this can be reduced is the use of the timestamp and hence reduces the chances of data losses.
This is one of the major form of attack that is often made in order to steal data but with the
advancement of the network security thus type of attacks are often reduced.
Conclusion;
Thus, concluding the topic it can be said that the VPN is one of the most secured thing
that can be used for the purpose of the ensuring the security of the network. The VPN can be
used for the purpose of the creating a secured filed where the data packets that are sent or
received can easily be monitored. Further the SSL or the secured layer security is one of the
other major thing that can be used for the purpose of the security of the devices. The SSL is
one of the most secured thing that can be used for the purpose of the ensuring proper security
to the devices.
CYBER SECURITY
Further the use of the secured layer socket connections helps the user to locate of
there is any break in the journey of the data [8]. One of the other major way through which
this can be reduced is the use of the timestamp and hence reduces the chances of data losses.
This is one of the major form of attack that is often made in order to steal data but with the
advancement of the network security thus type of attacks are often reduced.
Conclusion;
Thus, concluding the topic it can be said that the VPN is one of the most secured thing
that can be used for the purpose of the ensuring the security of the network. The VPN can be
used for the purpose of the creating a secured filed where the data packets that are sent or
received can easily be monitored. Further the SSL or the secured layer security is one of the
other major thing that can be used for the purpose of the security of the devices. The SSL is
one of the most secured thing that can be used for the purpose of the ensuring proper security
to the devices.

8
CYBER SECURITY
References
[1] Das, M. Swami, and A. Govardhan. "QoS web service Security Access Control case study
using HTTP Secured Socket Layer Approach." In Proceedings of the The International
Conference on Engineering & MIS 2015, p. 59. ACM, 2015.
[2] Daman, Repu, and Manish M. Tripathi. "Encryption Tools for Secured Health Data in
Public Cloud." International Journal of Innovative Science, Engineering & Technology 2, no.
11 (2015).
[3] Yan, Ling, Matt Hicks, Korey Winslow, Cynthia Comella, Christy Ludlow, H. A. Jinnah,
Ami R. Rosen, Laura Wright, Wendy R. Galpern, and Joel S. Perlmutter. "Secured web-
based video repository for multicenter studies." Parkinsonism & related disorders 21, no. 4
(2015): 366-371.
[4] Kishore, Neetu, and Seema Sharma. "Secured Data Migration from Enterprise to Cloud
Storage-Analytical Survey." BVICAM's International Journal of Information Technology 8,
no. 1 (2016).
[5] Nugroho, Hary, Ega Dian Pramesta, and Cholifah Sulistin Angraeni. "Implementasi
Virtual Private Network Openstack Terkoneksi Dengan Virtual Private Network Mikrotik
Untuk Komunikasi Data Lebih Aman." Journal ICT 8, no. 15 (2017).
[6] Yoo, Youngho, Reza Azarderakhsh, Amir Jalali, David Jao, and Vladimir Soukharev. "A
post-quantum digital signature scheme based on supersingular isogenies." In International
Conference on Financial Cryptography and Data Security, pp. 163-181. Springer, Cham,
2017.
[7] Ducas, Léo, Eike Kiltz, Tancrède Lepoint, Vadim Lyubashevsky, Peter Schwabe, Gregor
Seiler, and Damien Stehlé. "CRYSTALS-Dilithium: a lattice-based digital signature
CYBER SECURITY
References
[1] Das, M. Swami, and A. Govardhan. "QoS web service Security Access Control case study
using HTTP Secured Socket Layer Approach." In Proceedings of the The International
Conference on Engineering & MIS 2015, p. 59. ACM, 2015.
[2] Daman, Repu, and Manish M. Tripathi. "Encryption Tools for Secured Health Data in
Public Cloud." International Journal of Innovative Science, Engineering & Technology 2, no.
11 (2015).
[3] Yan, Ling, Matt Hicks, Korey Winslow, Cynthia Comella, Christy Ludlow, H. A. Jinnah,
Ami R. Rosen, Laura Wright, Wendy R. Galpern, and Joel S. Perlmutter. "Secured web-
based video repository for multicenter studies." Parkinsonism & related disorders 21, no. 4
(2015): 366-371.
[4] Kishore, Neetu, and Seema Sharma. "Secured Data Migration from Enterprise to Cloud
Storage-Analytical Survey." BVICAM's International Journal of Information Technology 8,
no. 1 (2016).
[5] Nugroho, Hary, Ega Dian Pramesta, and Cholifah Sulistin Angraeni. "Implementasi
Virtual Private Network Openstack Terkoneksi Dengan Virtual Private Network Mikrotik
Untuk Komunikasi Data Lebih Aman." Journal ICT 8, no. 15 (2017).
[6] Yoo, Youngho, Reza Azarderakhsh, Amir Jalali, David Jao, and Vladimir Soukharev. "A
post-quantum digital signature scheme based on supersingular isogenies." In International
Conference on Financial Cryptography and Data Security, pp. 163-181. Springer, Cham,
2017.
[7] Ducas, Léo, Eike Kiltz, Tancrède Lepoint, Vadim Lyubashevsky, Peter Schwabe, Gregor
Seiler, and Damien Stehlé. "CRYSTALS-Dilithium: a lattice-based digital signature

9
CYBER SECURITY
scheme." IACR Transactions on Cryptographic Hardware and Embedded Systems 2018, no.
1 (2018): 238-268.
[8] Beullens, Ward, and S. Blackburn. "Practical attacks against the Walnut digital signature
scheme." Preprint. Available at https://eprint. iacr. org/2018/318/20180404 153741 (2018).
[9] Bennett, Charles H., and Gilles Brassard. "Quantum cryptography: Public key distribution
and coin tossing." Theor. Comput. Sci. 560, no. P1 (2014): 7-11.
[10] Bos, Joppe W., Craig Costello, Michael Naehrig, and Douglas Stebila. "Post-quantum
key exchange for the TLS protocol from the ring learning with errors problem." In Security
and Privacy (SP), 2015 IEEE Symposium on, pp. 553-570. IEEE, 2015.
CYBER SECURITY
scheme." IACR Transactions on Cryptographic Hardware and Embedded Systems 2018, no.
1 (2018): 238-268.
[8] Beullens, Ward, and S. Blackburn. "Practical attacks against the Walnut digital signature
scheme." Preprint. Available at https://eprint. iacr. org/2018/318/20180404 153741 (2018).
[9] Bennett, Charles H., and Gilles Brassard. "Quantum cryptography: Public key distribution
and coin tossing." Theor. Comput. Sci. 560, no. P1 (2014): 7-11.
[10] Bos, Joppe W., Craig Costello, Michael Naehrig, and Douglas Stebila. "Post-quantum
key exchange for the TLS protocol from the ring learning with errors problem." In Security
and Privacy (SP), 2015 IEEE Symposium on, pp. 553-570. IEEE, 2015.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





