Cyber Security: WannaCry Attack Analysis Report, University, 2024
VerifiedAdded on 2022/09/18
|12
|2488
|20
Report
AI Summary
This report provides a comprehensive analysis of the WannaCry ransomware attack, a significant cyber security incident that occurred in 2017. The report begins with an executive summary and table of contents, followed by an introduction that emphasizes the importance of cyber security in preventing unauthorized computer activities, particularly ransomware attacks. The discussion section delves into different types of malware, with a detailed focus on the WannaCry attack, including its operational mechanisms and impact. The report highlights the attack's global consequences, the financial implications, and the devices affected. It also addresses security breaches and mitigation techniques. The conclusion summarizes the key findings, emphasizing the need for backup systems and preventative measures, such as antivirus software and caution against malicious emails. The report includes references to support the analysis.

Running head: CYBER SECURITY
CYBER SECURITY: WannaCry Attack
Name of the Student
Name of the University
Author Note
CYBER SECURITY: WannaCry Attack
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY
Executive Summary:
The cyber security is needed for prevention of the Ransomeware attack. Various malicious
attack has been happened in the cyber world. The following report has been created with the
analysis of Ransomeware attack. WannaCry is one of the famous real life attack which is
happened in the year 2017. WannaCry explanation has been added in the report also.
Executive Summary:
The cyber security is needed for prevention of the Ransomeware attack. Various malicious
attack has been happened in the cyber world. The following report has been created with the
analysis of Ransomeware attack. WannaCry is one of the famous real life attack which is
happened in the year 2017. WannaCry explanation has been added in the report also.

2CYBER SECURITY
Table of Contents
Executive Summary:..................................................................................................................1
Introduction:...............................................................................................................................3
Disscussion.................................................................................................................................3
Malware Types:...............................................................................................................3
WannaCry attack.............................................................................................................7
Conclusion:................................................................................................................................9
Referencing:.............................................................................................................................11
Table of Contents
Executive Summary:..................................................................................................................1
Introduction:...............................................................................................................................3
Disscussion.................................................................................................................................3
Malware Types:...............................................................................................................3
WannaCry attack.............................................................................................................7
Conclusion:................................................................................................................................9
Referencing:.............................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY
Introduction:
Cybersecurity is needed to stop the unauthorized activity on any computer. The
personal to the professional point of view cybersecurity is must be needed. The networks and
the information can be hacked by the hacker, to prevent this kind of situation the
cybersecurity is needed. Secrecy and fidelity removing the malware and preventing it is the
main motto of cyber security. Ransomeware is one type of the malware attack which will be
attacked by the hacker. After attacking the victim, the personal computer will be blocked
through software which will be opened by the decryption key, provided by the hacker
(Mohurle and Patil., 2017). The hacker will ask a considerable amount of money for the
decryption key. In various cases of the malware attack, the attacker will give the time limit
for the money transfer. If the required amount of money is not paid, then the hacker will
misuse the sensitive data or remove the data. The aim of the report is to give a brief
description of the several types of malware attacks. The other portion of the report will
contain a real-life example of the malware attack, which has been hugely affecting a specific
organization (Bossert 2017).
Disscussion
Malware Types:
The 5 pioneer Categories of Ransom Ware persisting in the market are subcategorized as
follows:
1. The deadly category of ransomware that seems to be traditional in the order of
chronology, gaining supremacy in terms of phishing activities, is none other than
Cryptolocker botnet. This made entrain in the cosmopolitan market in the year of
2013 when the region of interest of the cyber predators was to gain unauthorized
access over the restricted property of the organizations in lieu of enormous ransom
Introduction:
Cybersecurity is needed to stop the unauthorized activity on any computer. The
personal to the professional point of view cybersecurity is must be needed. The networks and
the information can be hacked by the hacker, to prevent this kind of situation the
cybersecurity is needed. Secrecy and fidelity removing the malware and preventing it is the
main motto of cyber security. Ransomeware is one type of the malware attack which will be
attacked by the hacker. After attacking the victim, the personal computer will be blocked
through software which will be opened by the decryption key, provided by the hacker
(Mohurle and Patil., 2017). The hacker will ask a considerable amount of money for the
decryption key. In various cases of the malware attack, the attacker will give the time limit
for the money transfer. If the required amount of money is not paid, then the hacker will
misuse the sensitive data or remove the data. The aim of the report is to give a brief
description of the several types of malware attacks. The other portion of the report will
contain a real-life example of the malware attack, which has been hugely affecting a specific
organization (Bossert 2017).
Disscussion
Malware Types:
The 5 pioneer Categories of Ransom Ware persisting in the market are subcategorized as
follows:
1. The deadly category of ransomware that seems to be traditional in the order of
chronology, gaining supremacy in terms of phishing activities, is none other than
Cryptolocker botnet. This made entrain in the cosmopolitan market in the year of
2013 when the region of interest of the cyber predators was to gain unauthorized
access over the restricted property of the organizations in lieu of enormous ransom
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4CYBER SECURITY
(Brewer 2016). This has been facilitated by the Cryptolocker botnet. Strong and
robust encryption algorithms were employed for the purpose of encryption of the
server data of the organization, thereby facilitating the gaining of unauthorized access
over the user data. The decryption of the encrypted data sometimes becomes almost
impossible. As a consequence, even after the dispatch of the ransom, the users failed
to gain their access back over the compromised data, leading to the destruction in the
business policy and loss in the brand image (Kalita 2017).
2. The injection of Wanna cry ransomware in a host system is facilitated through a
dropper. This is equipped with potentials that eventually facilitates the extraction of
the vital and crucial information of the organization resulting in the loss of
confidentiality of the organization. The base code of wanna cry ransomware is not
that rigid and stringent in terms of complexity. Wanna cry is capable enough to
decode the hardcoded URL owing to the incorporation of robust encrypting
algorithms embedded within the structural framework. In the event, the wanna cry
ransomware is incompetent to gain access over the URL, it eventually switches its
zone of interest in gaining access over the subsidiary applications that eventually
instigates and stimulates the inaccessibility of the URL, fetching the extraction of the
confidential information in that way. This sends the pop-up notifications as a
disclaimer of notifying the users to issue the desired ransom and regain their access
back over the compromised information (Cabaj and Mazurczyk., 2016).
3. Among the five variants of ransomware prevailing in contemporary times, Bad rabbit
deserves special mention. The propagation of bad rabbit from the host system to the
subsidiaries is made feasible through the Updates via Adobe Flash Player. This seems
to be beneficial to the users from their perspective point of view initially, as they are
intended to update their software for the purpose of availing better security aspects
(Brewer 2016). This has been facilitated by the Cryptolocker botnet. Strong and
robust encryption algorithms were employed for the purpose of encryption of the
server data of the organization, thereby facilitating the gaining of unauthorized access
over the user data. The decryption of the encrypted data sometimes becomes almost
impossible. As a consequence, even after the dispatch of the ransom, the users failed
to gain their access back over the compromised data, leading to the destruction in the
business policy and loss in the brand image (Kalita 2017).
2. The injection of Wanna cry ransomware in a host system is facilitated through a
dropper. This is equipped with potentials that eventually facilitates the extraction of
the vital and crucial information of the organization resulting in the loss of
confidentiality of the organization. The base code of wanna cry ransomware is not
that rigid and stringent in terms of complexity. Wanna cry is capable enough to
decode the hardcoded URL owing to the incorporation of robust encrypting
algorithms embedded within the structural framework. In the event, the wanna cry
ransomware is incompetent to gain access over the URL, it eventually switches its
zone of interest in gaining access over the subsidiary applications that eventually
instigates and stimulates the inaccessibility of the URL, fetching the extraction of the
confidential information in that way. This sends the pop-up notifications as a
disclaimer of notifying the users to issue the desired ransom and regain their access
back over the compromised information (Cabaj and Mazurczyk., 2016).
3. Among the five variants of ransomware prevailing in contemporary times, Bad rabbit
deserves special mention. The propagation of bad rabbit from the host system to the
subsidiaries is made feasible through the Updates via Adobe Flash Player. This seems
to be beneficial to the users from their perspective point of view initially, as they are
intended to update their software for the purpose of availing better security aspects

5CYBER SECURITY
and other beneficial properties acquisition (Chen and Bridges.,2017). Just a single
click of the user on the notification pop up by mistake exposes the intricacies of the
system to the external cyber predators who then are lured to gain unauthorized access
over the confidential data of the organization. In due course of this procedure, the
compromise of the data takes place. The reason behind the competency of bad rabbit
lies in the incorporation of the Mimikatz that is capable of gaining access over the
login credentials like user dominated password and the user id as well(Continella et
al.,2016). The Mimikatz software eventually is directly responsible for the huge
response of the bad rabbit and facilitates its propagation from mother to daughter
systems.
4. Another category of ransom ware that deserves special mention in this regard is the
Cerber. The unique characteristic feature of this software is it is capable of gaining
unauthorized access over the restricted data even in the absence of internet
connectivity. The impact is the virus cannot be mitigated by mere disconnecting the
system from the internet conncectivity(Gates 2018). The propagation procedure is the
attachment of malicious link embedded within the email. Clicking the malicious link
by the user activates the dormant and the3 latent virus and they are boosted to execute
their phishing activities. The encryption of information of the user system is
facilitated through the incorporation of the RC4 and RSA algorithms within the
infrastructure of the virus.
Finally comes the scenario of Crysis ransomware, which is the ultimate to the most
updated version exhibiting the phishing activities. The mode of propagation also bears
a resemblance to the propagation mode of Cerber virus (Mansfield-Devine 2016).
However, the contrast lies in the fact that it is injected into the system through double
and other beneficial properties acquisition (Chen and Bridges.,2017). Just a single
click of the user on the notification pop up by mistake exposes the intricacies of the
system to the external cyber predators who then are lured to gain unauthorized access
over the confidential data of the organization. In due course of this procedure, the
compromise of the data takes place. The reason behind the competency of bad rabbit
lies in the incorporation of the Mimikatz that is capable of gaining access over the
login credentials like user dominated password and the user id as well(Continella et
al.,2016). The Mimikatz software eventually is directly responsible for the huge
response of the bad rabbit and facilitates its propagation from mother to daughter
systems.
4. Another category of ransom ware that deserves special mention in this regard is the
Cerber. The unique characteristic feature of this software is it is capable of gaining
unauthorized access over the restricted data even in the absence of internet
connectivity. The impact is the virus cannot be mitigated by mere disconnecting the
system from the internet conncectivity(Gates 2018). The propagation procedure is the
attachment of malicious link embedded within the email. Clicking the malicious link
by the user activates the dormant and the3 latent virus and they are boosted to execute
their phishing activities. The encryption of information of the user system is
facilitated through the incorporation of the RC4 and RSA algorithms within the
infrastructure of the virus.
Finally comes the scenario of Crysis ransomware, which is the ultimate to the most
updated version exhibiting the phishing activities. The mode of propagation also bears
a resemblance to the propagation mode of Cerber virus (Mansfield-Devine 2016).
However, the contrast lies in the fact that it is injected into the system through double
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBER SECURITY
extension based file formats attached to the email. The consequence is the adoption of
non-executable file formats of the compromised file (Schirrmacher, Ondrus, and Ter
Chian Felix Tan.,2018). This also propagates through the spam emails having the
URL of certain websites, which have virtual existence. Clicking on the URL imparts
the final blow to the nail of the coffin, i.e. the vulnerabilities of the system are thereby
exposed, and the confidential information is compromised eventually in due course of
this entire procedure. Crysis adopts the disguise of beneficial websites that apparently
may seem enticing to the users and in due course of this executes its malicious and
phishing activities. The beneficial applications and programs are Internet Explorer,
Microsoft excel and WinRAR (Martin, Ghafur, Kinross., Hankin, and Darzi,.
(2018)).
Fig 1: Ransomeware types
Source: Brewer (2016)
Wanna Cry attack:
extension based file formats attached to the email. The consequence is the adoption of
non-executable file formats of the compromised file (Schirrmacher, Ondrus, and Ter
Chian Felix Tan.,2018). This also propagates through the spam emails having the
URL of certain websites, which have virtual existence. Clicking on the URL imparts
the final blow to the nail of the coffin, i.e. the vulnerabilities of the system are thereby
exposed, and the confidential information is compromised eventually in due course of
this entire procedure. Crysis adopts the disguise of beneficial websites that apparently
may seem enticing to the users and in due course of this executes its malicious and
phishing activities. The beneficial applications and programs are Internet Explorer,
Microsoft excel and WinRAR (Martin, Ghafur, Kinross., Hankin, and Darzi,.
(2018)).
Fig 1: Ransomeware types
Source: Brewer (2016)
Wanna Cry attack:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY
Description: In the year of 2017 a worldwide cyber-attack has been happened which
is renowned as the WannaCry ransomeware attack. It was happed in the Microsoft operating
systems. The target was to collapse the system of the computer, and demand a huge amount
of money for the decryption key. The demanding amount was huge, and hacker was asking
the money through the Bitcoin crypto currency transfer. The National Security was trying to
detect the hacker. The backdoor investing systems has been made a situation where the
WannaCry attacked easily. It is actually a cyber-attack carried a huge amount of cyber
predators; targeting the Microsoft windows operating system. The collected amount taken by
the attacker was near about $300 for the each victims (Mercaldo, Nardone, Santone and
Visaggio,. (2016, June).
Outcome: The whole world faced a huge problem in this attack. Various organization
and the institutions’ sensitive data has been collapsed with this attack. Some of them has paid
the amount and the other will delete/ format the computer. Those who has the proper backup
in the system, those are not affected. Other organizations has paid a huge amount of money to
get the decryption key. Near about 200000 computers are collapsed with this worm (Gates
2018).
Impact on financial field and devices: The impact of the financial field was huge.
Each and the every victim has to pay near about $300 for the decryption key. That is why the
Description: In the year of 2017 a worldwide cyber-attack has been happened which
is renowned as the WannaCry ransomeware attack. It was happed in the Microsoft operating
systems. The target was to collapse the system of the computer, and demand a huge amount
of money for the decryption key. The demanding amount was huge, and hacker was asking
the money through the Bitcoin crypto currency transfer. The National Security was trying to
detect the hacker. The backdoor investing systems has been made a situation where the
WannaCry attacked easily. It is actually a cyber-attack carried a huge amount of cyber
predators; targeting the Microsoft windows operating system. The collected amount taken by
the attacker was near about $300 for the each victims (Mercaldo, Nardone, Santone and
Visaggio,. (2016, June).
Outcome: The whole world faced a huge problem in this attack. Various organization
and the institutions’ sensitive data has been collapsed with this attack. Some of them has paid
the amount and the other will delete/ format the computer. Those who has the proper backup
in the system, those are not affected. Other organizations has paid a huge amount of money to
get the decryption key. Near about 200000 computers are collapsed with this worm (Gates
2018).
Impact on financial field and devices: The impact of the financial field was huge.
Each and the every victim has to pay near about $300 for the decryption key. That is why the

8CYBER SECURITY
amount was billion dollars, through the bitcoin transfer. All of the attacked devices are
damaged. Near about 200000 computers were corrupted through this process. Some of the
expert consulted to pay the amount for the data loss problem. There were near about 327
payments till the date of 14th June. Near about US$130,634.77 has been transferred to the
hackers account (Yaqoob et al., 2017).
amount was billion dollars, through the bitcoin transfer. All of the attacked devices are
damaged. Near about 200000 computers were corrupted through this process. Some of the
expert consulted to pay the amount for the data loss problem. There were near about 327
payments till the date of 14th June. Near about US$130,634.77 has been transferred to the
hackers account (Yaqoob et al., 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
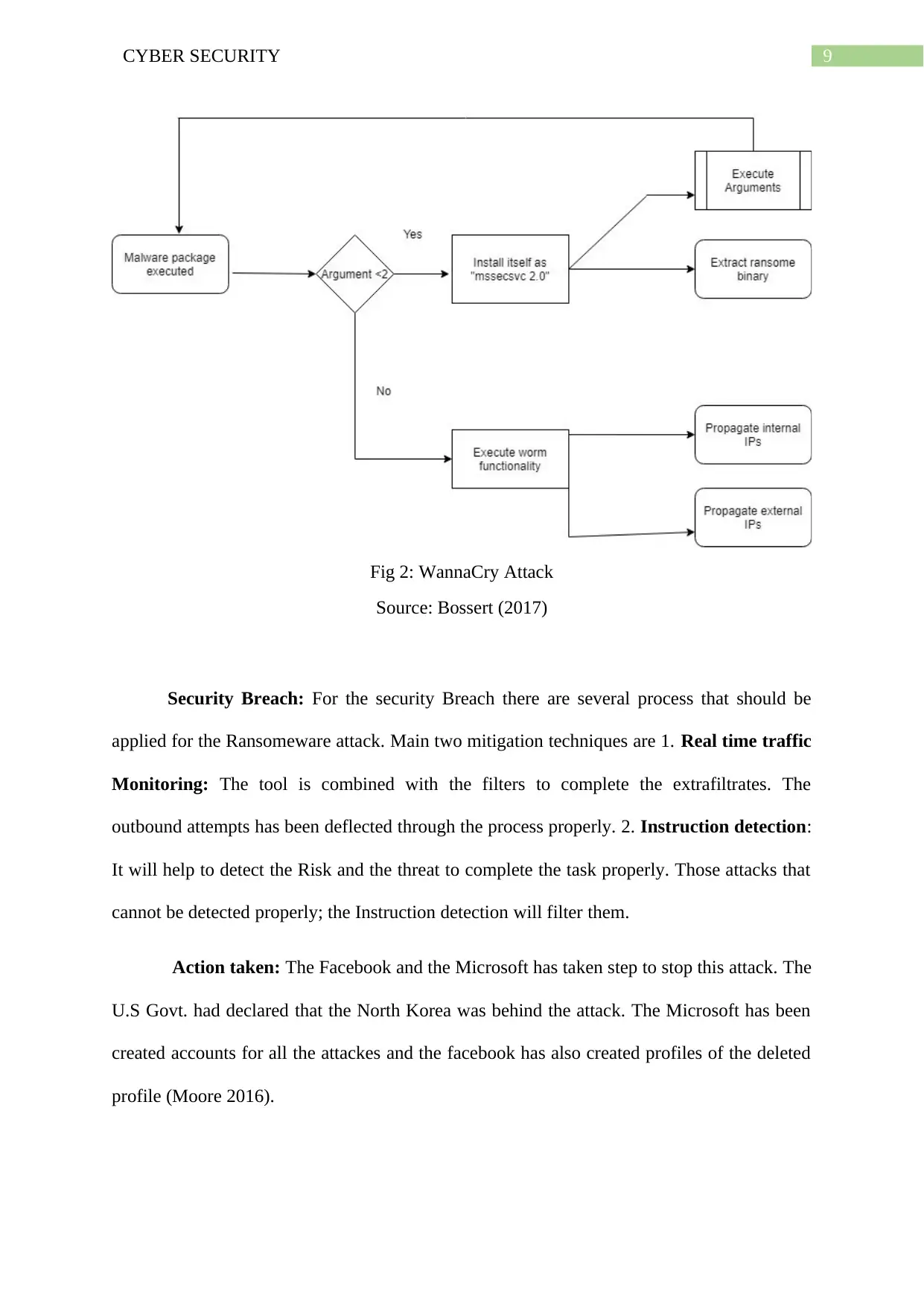
9CYBER SECURITY
Fig 2: WannaCry Attack
Source: Bossert (2017)
Security Breach: For the security Breach there are several process that should be
applied for the Ransomeware attack. Main two mitigation techniques are 1. Real time traffic
Monitoring: The tool is combined with the filters to complete the extrafiltrates. The
outbound attempts has been deflected through the process properly. 2. Instruction detection:
It will help to detect the Risk and the threat to complete the task properly. Those attacks that
cannot be detected properly; the Instruction detection will filter them.
Action taken: The Facebook and the Microsoft has taken step to stop this attack. The
U.S Govt. had declared that the North Korea was behind the attack. The Microsoft has been
created accounts for all the attackes and the facebook has also created profiles of the deleted
profile (Moore 2016).
Fig 2: WannaCry Attack
Source: Bossert (2017)
Security Breach: For the security Breach there are several process that should be
applied for the Ransomeware attack. Main two mitigation techniques are 1. Real time traffic
Monitoring: The tool is combined with the filters to complete the extrafiltrates. The
outbound attempts has been deflected through the process properly. 2. Instruction detection:
It will help to detect the Risk and the threat to complete the task properly. Those attacks that
cannot be detected properly; the Instruction detection will filter them.
Action taken: The Facebook and the Microsoft has taken step to stop this attack. The
U.S Govt. had declared that the North Korea was behind the attack. The Microsoft has been
created accounts for all the attackes and the facebook has also created profiles of the deleted
profile (Moore 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER SECURITY
Conclusion:
The report has been made through the rough concept of the cyber-attack, which has
been created a benchmark in the past industry. The selected attack was a very famous attack-
WannaCry. A huge amount of organization has been affected by the attack in the year 2017.
That is why it can be concluded that each and every unit of backup is needed to prevent this
kind of worm. Now it is said that Facebook and Microsoft have created such protection that
data hacking is impossible. But still, there has a Risk against any type of systems. The types
of the Ransomeware attack has been described, and nature is also explained. So it can be said
that if the user follower the proper antivirus and avoid the malicious emails, then it can be
avoided.
Referencing:
Bossert, T. P. (2017). It’s official: North Korea is behind WannaCry. The Wall Street
Journal.
Brewer, R. (2016). Ransomware attacks: detection, prevention and cure. Network
Security, 2016(9), 5-9.
Cabaj, K., & Mazurczyk, W. (2016). Using software-defined networking for ransomware
mitigation: the case of cryptowall. Ieee Network, 30(6), 14-20.
Chen, Q., & Bridges, R. A. (2017, December). Automated behavioral analysis of malware: A
case study of wannacry ransomware. In 2017 16th IEEE International Conference on
Machine Learning and Applications (ICMLA) (pp. 454-460). IEEE.
Continella, A., Guagnelli, A., Zingaro, G., De Pasquale, G., Barenghi, A., Zanero, S., &
Maggi, F. (2016, December). ShieldFS: a self-healing, ransomware-aware filesystem.
Conclusion:
The report has been made through the rough concept of the cyber-attack, which has
been created a benchmark in the past industry. The selected attack was a very famous attack-
WannaCry. A huge amount of organization has been affected by the attack in the year 2017.
That is why it can be concluded that each and every unit of backup is needed to prevent this
kind of worm. Now it is said that Facebook and Microsoft have created such protection that
data hacking is impossible. But still, there has a Risk against any type of systems. The types
of the Ransomeware attack has been described, and nature is also explained. So it can be said
that if the user follower the proper antivirus and avoid the malicious emails, then it can be
avoided.
Referencing:
Bossert, T. P. (2017). It’s official: North Korea is behind WannaCry. The Wall Street
Journal.
Brewer, R. (2016). Ransomware attacks: detection, prevention and cure. Network
Security, 2016(9), 5-9.
Cabaj, K., & Mazurczyk, W. (2016). Using software-defined networking for ransomware
mitigation: the case of cryptowall. Ieee Network, 30(6), 14-20.
Chen, Q., & Bridges, R. A. (2017, December). Automated behavioral analysis of malware: A
case study of wannacry ransomware. In 2017 16th IEEE International Conference on
Machine Learning and Applications (ICMLA) (pp. 454-460). IEEE.
Continella, A., Guagnelli, A., Zingaro, G., De Pasquale, G., Barenghi, A., Zanero, S., &
Maggi, F. (2016, December). ShieldFS: a self-healing, ransomware-aware filesystem.

11CYBER SECURITY
In Proceedings of the 32nd Annual Conference on Computer Security
Applications (pp. 336-347). ACM.
Gates, D. (2018). Boeing hit by WannaCry virus, but says attack caused little damage. Seattle
Times, https://www. seattletimes. com/business/boeingaerospace/boeing-hit-by-
wannacry-virus-fears-it-couldcripple-some-jet-production.
Kalita, E. (2017). WannaCry Ransomware Attack: Protect Yourself from WannaCry
Ransomware Cyber Risk and Cyber War.
Mansfield-Devine, S. (2016). Ransomware: taking businesses hostage. Network
Security, 2016(10), 8-17.
Mansfield-Devine, S. (2017). Ransomware: the most popular form of attack. Computer
Fraud & Security, 2017(10), 15-20.
Martin, G., Ghafur, S., Kinross, J., Hankin, C., & Darzi, A. (2018). WannaCry—a year on.
Mercaldo, F., Nardone, V., Santone, A., & Visaggio, C. A. (2016, June). Ransomware steals
your phone. formal methods rescue it. In International Conference on Formal
Techniques for Distributed Objects, Components, and Systems (pp. 212-221).
Springer, Cham.
Mohurle, S., & Patil, M. (2017). A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
Moore, C. (2016, August). Detecting ransomware with honeypot techniques. In 2016
Cybersecurity and Cyberforensics Conference (CCC) (pp. 77-81). IEEE.
Schirrmacher, N. B., Ondrus, J., & Ter Chian Felix Tan. (2018). Towards a Response to
Ransomware: Examining Digital Capabilities of the WannaCry Attack. In PACIS (p.
210).
In Proceedings of the 32nd Annual Conference on Computer Security
Applications (pp. 336-347). ACM.
Gates, D. (2018). Boeing hit by WannaCry virus, but says attack caused little damage. Seattle
Times, https://www. seattletimes. com/business/boeingaerospace/boeing-hit-by-
wannacry-virus-fears-it-couldcripple-some-jet-production.
Kalita, E. (2017). WannaCry Ransomware Attack: Protect Yourself from WannaCry
Ransomware Cyber Risk and Cyber War.
Mansfield-Devine, S. (2016). Ransomware: taking businesses hostage. Network
Security, 2016(10), 8-17.
Mansfield-Devine, S. (2017). Ransomware: the most popular form of attack. Computer
Fraud & Security, 2017(10), 15-20.
Martin, G., Ghafur, S., Kinross, J., Hankin, C., & Darzi, A. (2018). WannaCry—a year on.
Mercaldo, F., Nardone, V., Santone, A., & Visaggio, C. A. (2016, June). Ransomware steals
your phone. formal methods rescue it. In International Conference on Formal
Techniques for Distributed Objects, Components, and Systems (pp. 212-221).
Springer, Cham.
Mohurle, S., & Patil, M. (2017). A brief study of wannacry threat: Ransomware attack
2017. International Journal of Advanced Research in Computer Science, 8(5).
Moore, C. (2016, August). Detecting ransomware with honeypot techniques. In 2016
Cybersecurity and Cyberforensics Conference (CCC) (pp. 77-81). IEEE.
Schirrmacher, N. B., Ondrus, J., & Ter Chian Felix Tan. (2018). Towards a Response to
Ransomware: Examining Digital Capabilities of the WannaCry Attack. In PACIS (p.
210).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




