Cyber Terrorism: Is Sri Lanka Ready?
VerifiedAdded on 2023/06/13
|53
|15191
|297
AI Summary
In this study we will discuss about cyber terrorism and below are the summaries point:-
Cyberterrorism poses a growing threat in Sri Lanka, with an increase in cybercrime activities observed.
Traditional crimes have moved online, including money laundering, child exploitation, fraud, and more.
The government has taken actions to address cyberterrorism, but a comparison with international legislation is necessary.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

RESTRICTED
CYBER TERRORISM; IS SRI LANKA READY?
1
RESTRICTED
CYBER TERRORISM; IS SRI LANKA READY?
1
RESTRICTED
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESTRICTED
CONTENT
1. Chapter One Introduction
2. Chapter Two Problem Statement
Research Hypothesis
Objective
Methods of Data Collection
Limitations
3. Chapter Three Data presenting and analysing
Definition of the cyberterrorism
The major hacking events world has experienced
Sri Lanka’s experiences of cyber terrorism
4. Chapter Four Governments perspective
Sri Lanka’s legislations on cyberterrorism
Action taken by the government
5. Chapter Five Legal background
United States of America’s legislations on
cyberterrorism
Summary of Europe Budapest Convention on
cyberterrorism
2
RESTRICTED
CONTENT
1. Chapter One Introduction
2. Chapter Two Problem Statement
Research Hypothesis
Objective
Methods of Data Collection
Limitations
3. Chapter Three Data presenting and analysing
Definition of the cyberterrorism
The major hacking events world has experienced
Sri Lanka’s experiences of cyber terrorism
4. Chapter Four Governments perspective
Sri Lanka’s legislations on cyberterrorism
Action taken by the government
5. Chapter Five Legal background
United States of America’s legislations on
cyberterrorism
Summary of Europe Budapest Convention on
cyberterrorism
2
RESTRICTED

RESTRICTED
Comparison of Sri Lankan legislation and U.S.A
6. Chapter Six Reccomendation
7. Chapter Seven Conclusion
3
RESTRICTED
Comparison of Sri Lankan legislation and U.S.A
6. Chapter Six Reccomendation
7. Chapter Seven Conclusion
3
RESTRICTED

RESTRICTED
CHAPTER ONE
INTRODUCTION
1. Traditional crime has long ago moved online. Crimes like money laundering, child
pornography, sexual exploitation of children, sale and trafficking of illegal drugs,
prostitution, internet fraud, credit card fraud, illegal gambling, hate propaganda, racism
crimes, intellectual property theft, piracy harassment, stalking threats, extortion identity
theft and many more.
2. Cybercrime is rather a novel aspect of criminal activity to the Sri Lankan society.
With the advancement of information technology and knowledge of computer science in Sri
Lankans, some individuals have turned cybercrime as a mean of acquiring wealth in an
unlawful and undetected manner and also to achieve political and social status. Cybercrime is
mostly committed by the educated youth. There has been an increasing of cybercrime
complains within the last year according to the Sri Lanka, Computer Emergency Response
Team (SLCERT). In the recent past, an increase in the number of cyber-criminal activities in
Sri Lanka had been observed. A representative of SLCERT said that most complaints are
related to hacking of passwords, stealing of information, demanding ransoms in addition to
Facebook and credit card related crimes.
3. In the wake of the recent computer attacks, many have been quick to jump to
conclusions that a new breed of terrorism is on the rise and Sri Lanka must defend itself with
all possible means. As a society we have a vast operational and legal experience and proved
techniques to combat terrorism, but are we ready to fight terrorism in the new arena – cyber
space?
4
RESTRICTED
CHAPTER ONE
INTRODUCTION
1. Traditional crime has long ago moved online. Crimes like money laundering, child
pornography, sexual exploitation of children, sale and trafficking of illegal drugs,
prostitution, internet fraud, credit card fraud, illegal gambling, hate propaganda, racism
crimes, intellectual property theft, piracy harassment, stalking threats, extortion identity
theft and many more.
2. Cybercrime is rather a novel aspect of criminal activity to the Sri Lankan society.
With the advancement of information technology and knowledge of computer science in Sri
Lankans, some individuals have turned cybercrime as a mean of acquiring wealth in an
unlawful and undetected manner and also to achieve political and social status. Cybercrime is
mostly committed by the educated youth. There has been an increasing of cybercrime
complains within the last year according to the Sri Lanka, Computer Emergency Response
Team (SLCERT). In the recent past, an increase in the number of cyber-criminal activities in
Sri Lanka had been observed. A representative of SLCERT said that most complaints are
related to hacking of passwords, stealing of information, demanding ransoms in addition to
Facebook and credit card related crimes.
3. In the wake of the recent computer attacks, many have been quick to jump to
conclusions that a new breed of terrorism is on the rise and Sri Lanka must defend itself with
all possible means. As a society we have a vast operational and legal experience and proved
techniques to combat terrorism, but are we ready to fight terrorism in the new arena – cyber
space?
4
RESTRICTED
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESTRICTED
CHAPTER TWO
PROBLEM STATEMENT
4. This onset of the information-dependent third wave provides opportunities for
spectacular gains and serious losses for individuals, corporations, and states. It is within this
world that the cyber terrorists will operate. In the same manner that terrorists have exploited
widely accepted technology such as dynamite and the airplane (for bombing and hijacking),
they may exploit the tools of the "information age" to bring their case before the citizens of
the world. To defend against a threat, one must understand its critical elements.
5. Cyber terrorism, like "conventional" terrorism, will strive to change the mind of its
intended audience. However, cyber terrorism may utilize a different means to this end. In the
wake of the recent computer attacks, many have been quick to jump to conclusions that a new
breed of terrorism is on the rise and Sri Lanka must defend itself with all possible means. As
a society we have a vast operational and legal experience and proved techniques to face
combat terrorism but we have to know if we are ready to face this new aspect of terrorism.
RESEARCH HYPOTHESIS
6. Sri Lanka is having a high risk in near future in the area of information technology.
This threat has not been a complicated one for the time being but with the availability of
resources and with the developing technology over time, the potential of being attacked
through the means of information technology has increased but our government haven’t acted
in an effective manner to mitigate these risks.
5
RESTRICTED
CHAPTER TWO
PROBLEM STATEMENT
4. This onset of the information-dependent third wave provides opportunities for
spectacular gains and serious losses for individuals, corporations, and states. It is within this
world that the cyber terrorists will operate. In the same manner that terrorists have exploited
widely accepted technology such as dynamite and the airplane (for bombing and hijacking),
they may exploit the tools of the "information age" to bring their case before the citizens of
the world. To defend against a threat, one must understand its critical elements.
5. Cyber terrorism, like "conventional" terrorism, will strive to change the mind of its
intended audience. However, cyber terrorism may utilize a different means to this end. In the
wake of the recent computer attacks, many have been quick to jump to conclusions that a new
breed of terrorism is on the rise and Sri Lanka must defend itself with all possible means. As
a society we have a vast operational and legal experience and proved techniques to face
combat terrorism but we have to know if we are ready to face this new aspect of terrorism.
RESEARCH HYPOTHESIS
6. Sri Lanka is having a high risk in near future in the area of information technology.
This threat has not been a complicated one for the time being but with the availability of
resources and with the developing technology over time, the potential of being attacked
through the means of information technology has increased but our government haven’t acted
in an effective manner to mitigate these risks.
5
RESTRICTED

RESTRICTED
OBJECTIVES
7. The main objective of this research is to analyse the vulnerabilities of Sri Lanka to a
cyber-terrorist attack.
8. Secondary objectives of this research are :
i. To identify the rules and regulations regarding cyber-security
and privacy
ii. To identify the proactive and reactive measures that can be
taken against Cyber Terrorism
METHODS OF DATA COLLECTION
9. The required data for the research were drawn from the following sources;
i. Primary sources -Information collected by interviewing
resource personnel in the relevant field and by distributing a
questionnaire among the selected sample of the population.
ii. Secondary sources -Information was gathered from
relevant books, journals, internet, treaties and conventions and
also international and local enactments of relevance.
LIMITATIONS
i. We have to limit the scope of this research to the
population which is aware about the Information technology.
ii. Secondary data collection has to be limited to the books
available on the relevant field, internet and newspapers.
iii. Difficulties in obtaining information from the required
personal in detail.
6
RESTRICTED
OBJECTIVES
7. The main objective of this research is to analyse the vulnerabilities of Sri Lanka to a
cyber-terrorist attack.
8. Secondary objectives of this research are :
i. To identify the rules and regulations regarding cyber-security
and privacy
ii. To identify the proactive and reactive measures that can be
taken against Cyber Terrorism
METHODS OF DATA COLLECTION
9. The required data for the research were drawn from the following sources;
i. Primary sources -Information collected by interviewing
resource personnel in the relevant field and by distributing a
questionnaire among the selected sample of the population.
ii. Secondary sources -Information was gathered from
relevant books, journals, internet, treaties and conventions and
also international and local enactments of relevance.
LIMITATIONS
i. We have to limit the scope of this research to the
population which is aware about the Information technology.
ii. Secondary data collection has to be limited to the books
available on the relevant field, internet and newspapers.
iii. Difficulties in obtaining information from the required
personal in detail.
6
RESTRICTED

RESTRICTED
CHAPTER THREE
DATA PRESENTING AND ANALYSING
DEFINITION OF THE CYBERTERRORISM
10. The term cyber-terrorism was coined in 1996 by combining the terms cyberspace and
terrorism.(Larry, 2009) Defines cyber terrorism as "The use of computer network tools to
shut down critical national infrastructure (such as energy, transportation, government
operations) or to coerce or intimidate a government or civilian population"
11.The United States Federal Bureau of Investigation (FBI) defines ‘Terrorism’ as the unlawful
use of force or violence, committed by a group(s) of two or more individuals, against persons
or property, to intimidate or coerce a government, the civilian population, or any segment
thereof, in furtherance of political or social objectives”.
12. Former Chief Strategist at Netscape, Kevin Coleman defines cyber terrorism as “The
premeditated use of disruptive activities, or the threat thereof, against computers and/or
networks, with the intention to cause harm or further social, economic, ideological, religious,
political or similar objectives or to intimidate any person in furtherance of such objectives”.
13. It has to be noted that the general public misinterpret hacking as cyber terrorism yet
these two terms has a drastically different meanings. Hacking is the deliberate and
unauthorized access, use, disclosure, and/or taking of electronic data .The computer crime of
hacking is committed when a person wilfully, knowingly, and without authorization or
without reasonable grounds to believe that he or she has such authorization, attempts or
achieves access, communication, examination, or modification of data, computer programs,
or supporting documentation residing or existing internal or external to a
7
RESTRICTED
CHAPTER THREE
DATA PRESENTING AND ANALYSING
DEFINITION OF THE CYBERTERRORISM
10. The term cyber-terrorism was coined in 1996 by combining the terms cyberspace and
terrorism.(Larry, 2009) Defines cyber terrorism as "The use of computer network tools to
shut down critical national infrastructure (such as energy, transportation, government
operations) or to coerce or intimidate a government or civilian population"
11.The United States Federal Bureau of Investigation (FBI) defines ‘Terrorism’ as the unlawful
use of force or violence, committed by a group(s) of two or more individuals, against persons
or property, to intimidate or coerce a government, the civilian population, or any segment
thereof, in furtherance of political or social objectives”.
12. Former Chief Strategist at Netscape, Kevin Coleman defines cyber terrorism as “The
premeditated use of disruptive activities, or the threat thereof, against computers and/or
networks, with the intention to cause harm or further social, economic, ideological, religious,
political or similar objectives or to intimidate any person in furtherance of such objectives”.
13. It has to be noted that the general public misinterpret hacking as cyber terrorism yet
these two terms has a drastically different meanings. Hacking is the deliberate and
unauthorized access, use, disclosure, and/or taking of electronic data .The computer crime of
hacking is committed when a person wilfully, knowingly, and without authorization or
without reasonable grounds to believe that he or she has such authorization, attempts or
achieves access, communication, examination, or modification of data, computer programs,
or supporting documentation residing or existing internal or external to a
7
RESTRICTED
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESTRICTED
14. Computer system or computer network. Computer hacking is the most popular form
of hacking nowadays, especially in the field of computer security, but hacking exists in many
other forms, such as phone hacking, brain hacking, etc. And it's not limited to either of them.
15. Since cyber terrorism covers a vast area of technical aspects it is required to know the
exact differences between the following:
i. Hacker: A term used by some to mean "a clever programmer" and by others,
especially those in popular media, to mean "someone who tries to break into computer
systems."
ii. White hat: A hacker who identifies a security weakness in a computer system
or network but, instead of taking malicious advantage of it, exposes the weakness in a
way that will allow the system's owners to fix the breach before it can be taken
advantage by others.
iii. Black hat: A hacker who breaks into a computer system or network with
malicious intent. Unlike a white hat hacker, the black hat hacker takes advantage of
the break-in, perhaps destroying files or stealing data for some future purpose. The
black hat hacker may also make the exploit known to other hackers and/or the public
without notifying the victim. This gives others the opportunity to exploit the
vulnerability before the organization is able to secure it.
iv. Grey hat : A hacker who exploits a security weakness in a computer system or
product in order to bring the weakness to the attention of the owners. Unlike a black
hat, a grey hat acts without malicious intent. The goal of a grey hat is to improve
system and network security. However, by publicizing vulnerability, the grey hat may
give other hackers the opportunity to exploit it. This differs from the white hat who
alerts system owners and vendors of vulnerability without actually exploiting it in
public.
v. Phishing: An e-mail fraud method in which the perpetrator sends out
legitimate-looking email in an attempt to gather personal and financial information
8
RESTRICTED
14. Computer system or computer network. Computer hacking is the most popular form
of hacking nowadays, especially in the field of computer security, but hacking exists in many
other forms, such as phone hacking, brain hacking, etc. And it's not limited to either of them.
15. Since cyber terrorism covers a vast area of technical aspects it is required to know the
exact differences between the following:
i. Hacker: A term used by some to mean "a clever programmer" and by others,
especially those in popular media, to mean "someone who tries to break into computer
systems."
ii. White hat: A hacker who identifies a security weakness in a computer system
or network but, instead of taking malicious advantage of it, exposes the weakness in a
way that will allow the system's owners to fix the breach before it can be taken
advantage by others.
iii. Black hat: A hacker who breaks into a computer system or network with
malicious intent. Unlike a white hat hacker, the black hat hacker takes advantage of
the break-in, perhaps destroying files or stealing data for some future purpose. The
black hat hacker may also make the exploit known to other hackers and/or the public
without notifying the victim. This gives others the opportunity to exploit the
vulnerability before the organization is able to secure it.
iv. Grey hat : A hacker who exploits a security weakness in a computer system or
product in order to bring the weakness to the attention of the owners. Unlike a black
hat, a grey hat acts without malicious intent. The goal of a grey hat is to improve
system and network security. However, by publicizing vulnerability, the grey hat may
give other hackers the opportunity to exploit it. This differs from the white hat who
alerts system owners and vendors of vulnerability without actually exploiting it in
public.
v. Phishing: An e-mail fraud method in which the perpetrator sends out
legitimate-looking email in an attempt to gather personal and financial information
8
RESTRICTED

RESTRICTED
from recipients. Typically, the messages appear to come from well-known and
trustworthy Web sites. Web sites that are frequently spoofed by phishers
include PayPal, eBay, MSN, Yahoo, BestBuy, and America Online. A phishing
expedition, like the fishing expedition it's named for, is a speculative venture. The
phisher puts the lure hoping to fool at least a few of the prey that encounter the bait.
vi. Rootkit: A collection of tools or programs that enable administrator-level
access to a computer or computer network. Typically, a hacker installs a rootkit on a
computer after first obtaining user-level access, either by exploiting a known
vulnerability or cracking a password. Once the rootkit is installed, it allows the
attacker to mask intrusion and gain root or privileged access to the computer and,
possibly, other machines on the network.
vii. Spam: The use of electronic messaging systems to send unsolicited bulk
messages, especially advertising, indiscriminately. While the most widely recognized
form of spam is e-mail spam, the term is applied to similar abuses in other
media: instant messaging spam, Usenet newsgroup spam, Web search engine
spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging
spam, Internet forum spam, junk fax transmissions, social networking spam, social
spam, television advertising and file sharing network spam.
viii. Spyware: Any technology that aids in gathering information about a person or
organization without their knowledge. On the Internet (where it is sometimes called
a spybot or tracking software), spyware is a programme that is put in someone's
computer to secretly gather information about the user and relay it to advertisers or
other interested parties. Spyware can get in a computer as a software virus or as the
result of installing a new program.
ix. Trojan horse: A program in which malicious or harmful code is contained
inside apparently harmless programme or data in such a way that it can get control
and do its chosen form of damage, such as ruining the file allocation table on
your hard disk. A Trojan horse may be widely redistributed as part of a computer
virus.
9
RESTRICTED
from recipients. Typically, the messages appear to come from well-known and
trustworthy Web sites. Web sites that are frequently spoofed by phishers
include PayPal, eBay, MSN, Yahoo, BestBuy, and America Online. A phishing
expedition, like the fishing expedition it's named for, is a speculative venture. The
phisher puts the lure hoping to fool at least a few of the prey that encounter the bait.
vi. Rootkit: A collection of tools or programs that enable administrator-level
access to a computer or computer network. Typically, a hacker installs a rootkit on a
computer after first obtaining user-level access, either by exploiting a known
vulnerability or cracking a password. Once the rootkit is installed, it allows the
attacker to mask intrusion and gain root or privileged access to the computer and,
possibly, other machines on the network.
vii. Spam: The use of electronic messaging systems to send unsolicited bulk
messages, especially advertising, indiscriminately. While the most widely recognized
form of spam is e-mail spam, the term is applied to similar abuses in other
media: instant messaging spam, Usenet newsgroup spam, Web search engine
spam, spam in blogs, wiki spam, online classified ads spam, mobile phone messaging
spam, Internet forum spam, junk fax transmissions, social networking spam, social
spam, television advertising and file sharing network spam.
viii. Spyware: Any technology that aids in gathering information about a person or
organization without their knowledge. On the Internet (where it is sometimes called
a spybot or tracking software), spyware is a programme that is put in someone's
computer to secretly gather information about the user and relay it to advertisers or
other interested parties. Spyware can get in a computer as a software virus or as the
result of installing a new program.
ix. Trojan horse: A program in which malicious or harmful code is contained
inside apparently harmless programme or data in such a way that it can get control
and do its chosen form of damage, such as ruining the file allocation table on
your hard disk. A Trojan horse may be widely redistributed as part of a computer
virus.
9
RESTRICTED

RESTRICTED
x. Virus:A program or programming code that replicates by being copied or
initiating its copying to another program, computer boot sector or document. Viruses
can be transmitted as attachments to an e-mail note or in a downloaded file, or be
present on a diskette or CD. The immediate source of the e-mail note, downloaded
file, or diskette you've received is usually unaware that it contains a virus. A virus that
replicates itself by resending itself as an e-mail attachment or as part of a network
message is known as a worm.
10
RESTRICTED
x. Virus:A program or programming code that replicates by being copied or
initiating its copying to another program, computer boot sector or document. Viruses
can be transmitted as attachments to an e-mail note or in a downloaded file, or be
present on a diskette or CD. The immediate source of the e-mail note, downloaded
file, or diskette you've received is usually unaware that it contains a virus. A virus that
replicates itself by resending itself as an e-mail attachment or as part of a network
message is known as a worm.
10
RESTRICTED
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESTRICTED
THE MAJOR HACKING EVENTS WORLD EXPERIENCED.
16. Hacking has been around for decades. During the 1960s, the word "hacker" grew to
prominence describing a person with strong computer skills, an extensive understanding of
how computer programs worked, and a driving curiosity about computer systems. Hacking,
however, soon became nearly synonymous with illegal activity. While the first incidents of
hacking dealt with breaking into phone systems, hackers also began diving into computer
systems as technology advanced. Today’s crimes are often financially-motivated fraud. There
are some major hacking incidents that made some of the biggest headlines in history.
17. In 1994 Summer: Russian hackers siphon $10 million from Citibank and transfer the
money to bank accounts around the world. Vladimir Levin, the 30-year-old ringleader, uses
his work laptop after hours to transfer the funds to accounts in Finland and Israel. Levin
stands trial in the United States and is sentenced to three years in prison.
18. In 1996:
i. Hackers alter Web sites of the United States Department of Justice (August),
the CIA (October), and the U.S. Air Force (December).
ii. Canadian hacker group, Brotherhood, breaks into the Canadian Broadcasting
Corporation.
iii. The U.S. General Accounting Office reports that hackers attempted to break
into Defence Department computer files some 250,000 times in 1995 alone.
According to the report about 65 percent of the attempts were successful.
19. In 1997:
i. A 15-year-old Croatian youth penetrates computers at a U.S. Air Force base
in Guam.
ii. First high-profile attacks on Microsoft's Windows NT operating system.
11
RESTRICTED
THE MAJOR HACKING EVENTS WORLD EXPERIENCED.
16. Hacking has been around for decades. During the 1960s, the word "hacker" grew to
prominence describing a person with strong computer skills, an extensive understanding of
how computer programs worked, and a driving curiosity about computer systems. Hacking,
however, soon became nearly synonymous with illegal activity. While the first incidents of
hacking dealt with breaking into phone systems, hackers also began diving into computer
systems as technology advanced. Today’s crimes are often financially-motivated fraud. There
are some major hacking incidents that made some of the biggest headlines in history.
17. In 1994 Summer: Russian hackers siphon $10 million from Citibank and transfer the
money to bank accounts around the world. Vladimir Levin, the 30-year-old ringleader, uses
his work laptop after hours to transfer the funds to accounts in Finland and Israel. Levin
stands trial in the United States and is sentenced to three years in prison.
18. In 1996:
i. Hackers alter Web sites of the United States Department of Justice (August),
the CIA (October), and the U.S. Air Force (December).
ii. Canadian hacker group, Brotherhood, breaks into the Canadian Broadcasting
Corporation.
iii. The U.S. General Accounting Office reports that hackers attempted to break
into Defence Department computer files some 250,000 times in 1995 alone.
According to the report about 65 percent of the attempts were successful.
19. In 1997:
i. A 15-year-old Croatian youth penetrates computers at a U.S. Air Force base
in Guam.
ii. First high-profile attacks on Microsoft's Windows NT operating system.
11
RESTRICTED

RESTRICTED
20. In 1998 :
i. January: Yahoo notifies Internet users that anyone visiting its site in recent
weeks might have downloaded a logic bomb and worm planted by hackers claiming a
"logic bomb" will go off if Kevin Mitnick is not released from prison.
ii. Ethnic Tamil guerrillas swamped Sri Lankan embassies with over 800 e-mails
a day for more than two weeks. The messages read as “We are the Internet Black
Tigers and we're doing this to disrupt your communications.” Intelligence authorities
characterized it as the first known attack by terrorists against a country's IT
infrastructure.
21. In 1999 :
i. Software security goes main stream in the wake of Microsoft's Windows 98
release, year 1999 become a banner for security (and hacking). Hundreds of
advisories and patches were released in response to newly found (and widely
publicized) bugs in Windows and other commercial software products. A host of
security software vendors release anti-hacking products for use on home computers.
ii. The Melissa worm is released and quickly becomes the most costly malware
outbreak to date.
iii. “Level Seven” hacks The U.S Embassy in China's Website and places racist,
anti-government slogans on embassy site in regards to 1998 U.S. embassy bombings.
22. In 2000 the I LOVE YOU worm, also known as VBS/Love letter and Love Bug
worm, is a computer worm written in VB Script. It infected millions of computers worldwide
within a few hours of its release. It is considered to be one of the most damaging worms ever.
It originated in the Philippines; made by an AMA Computer College student for his thesis.
12
RESTRICTED
20. In 1998 :
i. January: Yahoo notifies Internet users that anyone visiting its site in recent
weeks might have downloaded a logic bomb and worm planted by hackers claiming a
"logic bomb" will go off if Kevin Mitnick is not released from prison.
ii. Ethnic Tamil guerrillas swamped Sri Lankan embassies with over 800 e-mails
a day for more than two weeks. The messages read as “We are the Internet Black
Tigers and we're doing this to disrupt your communications.” Intelligence authorities
characterized it as the first known attack by terrorists against a country's IT
infrastructure.
21. In 1999 :
i. Software security goes main stream in the wake of Microsoft's Windows 98
release, year 1999 become a banner for security (and hacking). Hundreds of
advisories and patches were released in response to newly found (and widely
publicized) bugs in Windows and other commercial software products. A host of
security software vendors release anti-hacking products for use on home computers.
ii. The Melissa worm is released and quickly becomes the most costly malware
outbreak to date.
iii. “Level Seven” hacks The U.S Embassy in China's Website and places racist,
anti-government slogans on embassy site in regards to 1998 U.S. embassy bombings.
22. In 2000 the I LOVE YOU worm, also known as VBS/Love letter and Love Bug
worm, is a computer worm written in VB Script. It infected millions of computers worldwide
within a few hours of its release. It is considered to be one of the most damaging worms ever.
It originated in the Philippines; made by an AMA Computer College student for his thesis.
12
RESTRICTED

RESTRICTED
23. In 2001:
i. Microsoft becomes the prominent victim of a new type of hack that attacks
the domain name server. In these denial-of-service attacks (Ddos), the DNS paths that
take users to Microsoft's Web sites are corrupted.
ii. A Dutch cracker releases the Anna Kournikova virus, initiating a wave of
viruses that tempts users to open the infected attachment by promising a sexy picture
of the Russian tennis star.
iii. A computer worm named Code Red worm was observed on the Internet on
July 13, 2001. It attacked computers running server. The Code Red worm was first
discovered and researched by e Eye Digital Security employees. The number of
infected hosts reached 359,000.
24. In 2004:
i. March: Myron Tereshchuk is arrested for attempting to extort $17 million
from patent. Thousands of proprietary MicroPatent documents, confidential customer
data, computer passwords and e-mail addresses. Using an alias of "Brian Ryan" and
signing off as "Wounded Grizzly," he warned that if Mr Videtto ignored his demands,
the information would end up in e-mail boxes worldwide.
ii. North Korea claims to have trained 500 hackers who successfully crack South
Korean, Japanese, and their allies' computer systems.
25. In 2006, Jeanson James Ancheta launches DDoS attacks and subsequent hacking to the Naval
Air Warfare Center in China Lake and the Defense Information Systems Agency.
26. In 2007
i. Estonia faced major cyber terrorist attack that began on 27 April 2007 which
swamped websites of Estonian organizations, including Estonian parliament, banks,
ministries, newspapers and broadcasters. Most of the attacks that had any influence on
13
RESTRICTED
23. In 2001:
i. Microsoft becomes the prominent victim of a new type of hack that attacks
the domain name server. In these denial-of-service attacks (Ddos), the DNS paths that
take users to Microsoft's Web sites are corrupted.
ii. A Dutch cracker releases the Anna Kournikova virus, initiating a wave of
viruses that tempts users to open the infected attachment by promising a sexy picture
of the Russian tennis star.
iii. A computer worm named Code Red worm was observed on the Internet on
July 13, 2001. It attacked computers running server. The Code Red worm was first
discovered and researched by e Eye Digital Security employees. The number of
infected hosts reached 359,000.
24. In 2004:
i. March: Myron Tereshchuk is arrested for attempting to extort $17 million
from patent. Thousands of proprietary MicroPatent documents, confidential customer
data, computer passwords and e-mail addresses. Using an alias of "Brian Ryan" and
signing off as "Wounded Grizzly," he warned that if Mr Videtto ignored his demands,
the information would end up in e-mail boxes worldwide.
ii. North Korea claims to have trained 500 hackers who successfully crack South
Korean, Japanese, and their allies' computer systems.
25. In 2006, Jeanson James Ancheta launches DDoS attacks and subsequent hacking to the Naval
Air Warfare Center in China Lake and the Defense Information Systems Agency.
26. In 2007
i. Estonia faced major cyber terrorist attack that began on 27 April 2007 which
swamped websites of Estonian organizations, including Estonian parliament, banks,
ministries, newspapers and broadcasters. Most of the attacks that had any influence on
13
RESTRICTED
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESTRICTED
the general public were distributed denial of service type attacks ranging from single
individuals using various methods like ping floods to expensive rentals
of botnets usually used for spam distribution. Spamming of bigger news portals
commentaries and defacements including that of the Estonian Reform Party website
also occurred.
ii. A spear phishing incident at the Office of the Secretary of Defence steals
sensitive U.S. defence information, leading to significant changes in identity and
message-source verification at Office of the Secretary of Defence.
iii. United Nations website was hacked by Turkish Hacker Kerem.
27. In 2008
i. Around 20 Chinese hackers claim to have gained access to the world's most
sensitive sites, including The Pentagon. They operate from a bare apartment on a
Chinese island.
ii. Before and during the 2008 South Ossetia War a series of cyber-attacks
flooded the public and private sector websites of South Ossetia, Russia, Georgia and
Azerbaijan. Out of the websites being attacked most of them belonged to the pro
Georgian news agencies and government organizations of Georgia and was subjected
to denial of service (DDOS) attacks. Hackers from Georgia have meanwhile been
blamed for targeting the websites of Russian news outlets and the separatist
government of South Ossetia, which Russia supports.
28. In 2009 the Conficker worm infiltrated millions of PCs worldwide including many
government-level top-security computer networks.
29. In 2010:
i. UN department of safety and security hacked by Turkish hacker
DigitALL(1923Turk)Mirror Link.
ii. The Stuxnet worm is found by VirusBlokAda. Stuxnet was unusual in that
while it spread via Windows computers, its payload targeted just one specific model
and type of SCADA systems. It slowly became clear that it was a cyber-attack on
14
RESTRICTED
the general public were distributed denial of service type attacks ranging from single
individuals using various methods like ping floods to expensive rentals
of botnets usually used for spam distribution. Spamming of bigger news portals
commentaries and defacements including that of the Estonian Reform Party website
also occurred.
ii. A spear phishing incident at the Office of the Secretary of Defence steals
sensitive U.S. defence information, leading to significant changes in identity and
message-source verification at Office of the Secretary of Defence.
iii. United Nations website was hacked by Turkish Hacker Kerem.
27. In 2008
i. Around 20 Chinese hackers claim to have gained access to the world's most
sensitive sites, including The Pentagon. They operate from a bare apartment on a
Chinese island.
ii. Before and during the 2008 South Ossetia War a series of cyber-attacks
flooded the public and private sector websites of South Ossetia, Russia, Georgia and
Azerbaijan. Out of the websites being attacked most of them belonged to the pro
Georgian news agencies and government organizations of Georgia and was subjected
to denial of service (DDOS) attacks. Hackers from Georgia have meanwhile been
blamed for targeting the websites of Russian news outlets and the separatist
government of South Ossetia, which Russia supports.
28. In 2009 the Conficker worm infiltrated millions of PCs worldwide including many
government-level top-security computer networks.
29. In 2010:
i. UN department of safety and security hacked by Turkish hacker
DigitALL(1923Turk)Mirror Link.
ii. The Stuxnet worm is found by VirusBlokAda. Stuxnet was unusual in that
while it spread via Windows computers, its payload targeted just one specific model
and type of SCADA systems. It slowly became clear that it was a cyber-attack on
14
RESTRICTED

RESTRICTED
Iran's nuclear facilities - with most experts believing that Israel was behind it -
perhaps with US help.
15
RESTRICTED
Iran's nuclear facilities - with most experts believing that Israel was behind it -
perhaps with US help.
15
RESTRICTED

RESTRICTED
30. In 2011:
i. Bank of America website hacked by Turkish hacker JeOPaRDY. This time the
FBI accuses him of stealing 85,000 credit card numbers and accounts. Bank officials
say no personal customer bank information is available on that web-page. Only
information about bank products and services.
ii. An "external intrusion" sends the PlayStation Network offline, and
compromises personally identifying information (possibly including credit card
details) of its 77 million accounts, in what is claimed to be one of the five largest data
breaches ever.
iii. Bangladeshi hacker TiGER-M@TE made world record in defacement history
by hacking 700,000 websites in one shot.
iv. The YouTube channel of Sesame Street was hacked, streaming pornographic
content for about 22 minutes.
31. In 2012
i. Saudi hacker, 0xOmar, published over 400,000 credit cards online, and
threatened Israel to release 1 million credit cards in the future. In response to that
incident, an Israeli hacker published over 200 Saudi's credit cards online.
ii. A number of important Turkish Websites were hacked
by F0RTYS3V3N (Turkish Hacker). Google, Yandex, Microsoft, Gmail, Msn,
Hotmail, Paypal Turkish representative offices’s Websites hacked in one shot.
iii. Flame is meant to gather information from infected PCs. As the virus can sniff
out information from input boxes, including passwords hidden by asterisks, record
audio from a connected microphone and take screenshots of applications that the virus
deems important, such as IM programs. It can also collect information about nearby
discoverable Bluetooth devices. The virus then uploads all this information to
command and control servers, of which there are about a dozen scattered around the
world. It is one of the most complex malware with its modules occupying more than
20 MB of code
16
RESTRICTED
30. In 2011:
i. Bank of America website hacked by Turkish hacker JeOPaRDY. This time the
FBI accuses him of stealing 85,000 credit card numbers and accounts. Bank officials
say no personal customer bank information is available on that web-page. Only
information about bank products and services.
ii. An "external intrusion" sends the PlayStation Network offline, and
compromises personally identifying information (possibly including credit card
details) of its 77 million accounts, in what is claimed to be one of the five largest data
breaches ever.
iii. Bangladeshi hacker TiGER-M@TE made world record in defacement history
by hacking 700,000 websites in one shot.
iv. The YouTube channel of Sesame Street was hacked, streaming pornographic
content for about 22 minutes.
31. In 2012
i. Saudi hacker, 0xOmar, published over 400,000 credit cards online, and
threatened Israel to release 1 million credit cards in the future. In response to that
incident, an Israeli hacker published over 200 Saudi's credit cards online.
ii. A number of important Turkish Websites were hacked
by F0RTYS3V3N (Turkish Hacker). Google, Yandex, Microsoft, Gmail, Msn,
Hotmail, Paypal Turkish representative offices’s Websites hacked in one shot.
iii. Flame is meant to gather information from infected PCs. As the virus can sniff
out information from input boxes, including passwords hidden by asterisks, record
audio from a connected microphone and take screenshots of applications that the virus
deems important, such as IM programs. It can also collect information about nearby
discoverable Bluetooth devices. The virus then uploads all this information to
command and control servers, of which there are about a dozen scattered around the
world. It is one of the most complex malware with its modules occupying more than
20 MB of code
16
RESTRICTED
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESTRICTED
.
32. Furthermore ,Hess a German recruited by the Committee for State Security (KGB) to
spy for the Soviets in the 1980s, Hess was tasked with breaking into U.S. military computers
to obtain classified information. From the University of Bremen in Germany, Hess used the
German Datex-P network via satellite link or transatlantic cable to the Tymnet International
Gateway. He was able to eventually attack 400 U.S. military computers, including those at
military installations in Germany and Japan, as well as machines at MIT in Cambridge,
Massachusetts and the OPTIMIS Database at the Pentagon.
33. Scottish hacker Gary McKinnon, who went by the handle Solo, was accused of
hacking to several US military computers in 2001 and 2002. McKinnon allegedly wanted to
know what the government knew about UFOs. Military officials said the damage caused by
McKinnon included the deletion of critical files from operating systems, prompting a shut
down the US Army’s Military District of Washington network of 2,000 computers for 24
hours. McKinnon also allegedly deleted weapons logs at the Earle Naval Weapons Station.
Officials said the cost of cleanup from McKinnon’s hack was over $700,000.
34. In 1996, US hacker Timothy Lloyd planted six lines of malicious software code in the
computer network of Omega Engineering which was a prime supplier of components for
NASA and the US Navy. The code allowed a "logic bomb" to explode that deleted software
running Omega's manufacturing operations. Omega lost $10 million due to the attack.
35. Albert Gonzalez was the convicted ring leader of a group of cyber criminals which,
from 2005 through 2007, stole more than 90 million credit and debit card numbers from TJX
and other retailers, including shoe sellers DSW, OfficeMax, BJs Wholesale Club and Dave &
Buster’s. Gonzalez was also the mastermind behind the hacking that caused the massive
records breach of Heartland Payment Systems in 2008.
36. In 2000, Mafia Boy, whose real identity has been kept under wraps because he is a
minor, hacked into some of the largest sites in the world, including eBay, Amazon and Yahoo
between February 6 and Valentine's Day in 2000. He gained access to 75 computers in 52
networks, and ordered a Denial of Service (DDOS) attack on them. He was arrested in 2000.
17
RESTRICTED
.
32. Furthermore ,Hess a German recruited by the Committee for State Security (KGB) to
spy for the Soviets in the 1980s, Hess was tasked with breaking into U.S. military computers
to obtain classified information. From the University of Bremen in Germany, Hess used the
German Datex-P network via satellite link or transatlantic cable to the Tymnet International
Gateway. He was able to eventually attack 400 U.S. military computers, including those at
military installations in Germany and Japan, as well as machines at MIT in Cambridge,
Massachusetts and the OPTIMIS Database at the Pentagon.
33. Scottish hacker Gary McKinnon, who went by the handle Solo, was accused of
hacking to several US military computers in 2001 and 2002. McKinnon allegedly wanted to
know what the government knew about UFOs. Military officials said the damage caused by
McKinnon included the deletion of critical files from operating systems, prompting a shut
down the US Army’s Military District of Washington network of 2,000 computers for 24
hours. McKinnon also allegedly deleted weapons logs at the Earle Naval Weapons Station.
Officials said the cost of cleanup from McKinnon’s hack was over $700,000.
34. In 1996, US hacker Timothy Lloyd planted six lines of malicious software code in the
computer network of Omega Engineering which was a prime supplier of components for
NASA and the US Navy. The code allowed a "logic bomb" to explode that deleted software
running Omega's manufacturing operations. Omega lost $10 million due to the attack.
35. Albert Gonzalez was the convicted ring leader of a group of cyber criminals which,
from 2005 through 2007, stole more than 90 million credit and debit card numbers from TJX
and other retailers, including shoe sellers DSW, OfficeMax, BJs Wholesale Club and Dave &
Buster’s. Gonzalez was also the mastermind behind the hacking that caused the massive
records breach of Heartland Payment Systems in 2008.
36. In 2000, Mafia Boy, whose real identity has been kept under wraps because he is a
minor, hacked into some of the largest sites in the world, including eBay, Amazon and Yahoo
between February 6 and Valentine's Day in 2000. He gained access to 75 computers in 52
networks, and ordered a Denial of Service (DDOS) attack on them. He was arrested in 2000.
17
RESTRICTED

RESTRICTED
a. Known by the hacker name c0mrade, Jonathon James was 16 when, in 1999,
he hacked into the Marshall Space Flight Center in Huntsville, Alabama, and
downloaded proprietary software for the International Space Station. The
software supported the International Space Station’s physical environment and
was responsible for critical control of humidity and temperature for living in
space. NASA officials valued the documents stolen by James at around $1.7
million. The incident forced NASA to shut down its computer systems for
three weeks and cost them about $41,000 to fix.
37. In 2002, at age 19, Adrian Lamo hacked into the internal network of the New York
Times and accessed many sensitive records, including an extensive database of op-ed writers
the paper had used in the past. The records contained names and, in some instances, phone
numbers, home addresses and payment history.
38. In early 2011, Antisec group Anonymous got angry when Aaron Barr, at the time the
Chief Executive Officer (CEO) of HB Gary Federal, alluded to plans to reveal the identities
of several Anonymous members at the Security B-Sides conference. In retaliation, the group
compromised the systems of both HB Gary Federal and sister firm HB Gary Inc. Anonymous
then copied and made public thousands of private HB Gary documents, including emails.
39. In one of the first events to really bring “hacktivism” to the attention of the
mainstream press, it was reported that some of the documents stolen by Anonymous revealed
HB Gary Federal was working with Bank Of America(BOA) to respond to Wikileaks’
planned release of BOAs internal documents.
40. The HB Gary documents detailed some planned shady tactics, including launching a “dirty
tricks” campaign against Wikileaks and disrupting a Salon.com reporter who was assumed to
be sympathetic to Wikileaks.
18
RESTRICTED
a. Known by the hacker name c0mrade, Jonathon James was 16 when, in 1999,
he hacked into the Marshall Space Flight Center in Huntsville, Alabama, and
downloaded proprietary software for the International Space Station. The
software supported the International Space Station’s physical environment and
was responsible for critical control of humidity and temperature for living in
space. NASA officials valued the documents stolen by James at around $1.7
million. The incident forced NASA to shut down its computer systems for
three weeks and cost them about $41,000 to fix.
37. In 2002, at age 19, Adrian Lamo hacked into the internal network of the New York
Times and accessed many sensitive records, including an extensive database of op-ed writers
the paper had used in the past. The records contained names and, in some instances, phone
numbers, home addresses and payment history.
38. In early 2011, Antisec group Anonymous got angry when Aaron Barr, at the time the
Chief Executive Officer (CEO) of HB Gary Federal, alluded to plans to reveal the identities
of several Anonymous members at the Security B-Sides conference. In retaliation, the group
compromised the systems of both HB Gary Federal and sister firm HB Gary Inc. Anonymous
then copied and made public thousands of private HB Gary documents, including emails.
39. In one of the first events to really bring “hacktivism” to the attention of the
mainstream press, it was reported that some of the documents stolen by Anonymous revealed
HB Gary Federal was working with Bank Of America(BOA) to respond to Wikileaks’
planned release of BOAs internal documents.
40. The HB Gary documents detailed some planned shady tactics, including launching a “dirty
tricks” campaign against Wikileaks and disrupting a Salon.com reporter who was assumed to
be sympathetic to Wikileaks.
18
RESTRICTED

RESTRICTED
SRI LANKA’S EXPERIENCE OF CYBER TERRORISM.
41. Sri Lanka, for the second time in three years, grabbed the attention of cyber security
experts when a new computer virus started circulating around the globe last week. In its
original form, the virus displays a message box entitled "Mawanella" and copies itself to the
hard disk and thereafter replicates itself, copying the virus code to all out-going email
messages from the infected computer. The virus code is based on the now infamous "Love
Bug" virus, which originated from the Philippines, in 1997.
42. LTTE cyber attack on Sri Lanka Army website. Sri Lankan Army site 'assassinated'
by rebels 'Horrible' and 'gruesome'[1st May 2009] "Sri Lanka Army’s official news wing,
(www.army.lk) has been illegally hacked and technically 'assassinated' by suspected Tiger
terrorists or their proxies, during the wee hours on Friday (1st May), inserting some horrible
and gruesome
43. images," ."This new form of information 'terrorism' is a criminal offence that can be
subjected to prosecution, according to international legal provisions."The attack on
the www.army.lk site sent army technicians scrambling to remove the content. By Friday
afternoon California time, the site appeared to be running normally.
44. Another government website has been hacked by suspected Tiger rebels the
government. Information Department said. The government news portal
www.Lankapuvath.lk has come under a cyber .Attack this morning by the suspected LTTE
hackers.
19
RESTRICTED
SRI LANKA’S EXPERIENCE OF CYBER TERRORISM.
41. Sri Lanka, for the second time in three years, grabbed the attention of cyber security
experts when a new computer virus started circulating around the globe last week. In its
original form, the virus displays a message box entitled "Mawanella" and copies itself to the
hard disk and thereafter replicates itself, copying the virus code to all out-going email
messages from the infected computer. The virus code is based on the now infamous "Love
Bug" virus, which originated from the Philippines, in 1997.
42. LTTE cyber attack on Sri Lanka Army website. Sri Lankan Army site 'assassinated'
by rebels 'Horrible' and 'gruesome'[1st May 2009] "Sri Lanka Army’s official news wing,
(www.army.lk) has been illegally hacked and technically 'assassinated' by suspected Tiger
terrorists or their proxies, during the wee hours on Friday (1st May), inserting some horrible
and gruesome
43. images," ."This new form of information 'terrorism' is a criminal offence that can be
subjected to prosecution, according to international legal provisions."The attack on
the www.army.lk site sent army technicians scrambling to remove the content. By Friday
afternoon California time, the site appeared to be running normally.
44. Another government website has been hacked by suspected Tiger rebels the
government. Information Department said. The government news portal
www.Lankapuvath.lk has come under a cyber .Attack this morning by the suspected LTTE
hackers.
19
RESTRICTED
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESTRICTED
CHAPTER FOUR
GOVERNMENT’S PERSPECTIVE
SRI LANKA’S LEGISLATIONS ON CYBERTERRORISM
45. The law regarding Legal Security and Copy Right Laws in Sri Lanka based on the
English law. Both English law and Sri Lankan laws are having common features in regarding
to the e-media. Furthermore in Sri Lanka there is no any difference between domestic law
and the international law regarding cyber-terrorism.
46. There are several legislations which passed by the Parliament recently.
i. Information and Communication Technology Act (No.27 of 2003)
ii. Evidence (Special Provisions) (Act No.14 of 1995)
iii. Intellectual Property Act (No. 36 of 2003 (Sections related to Copyright)
iv. Electronic Transactions Act (No. 19 of 2006)
v. Computer Crimes Act (No. 24 of 2007)
vi. Payment And Settlement Systems Act, (No. 28 of 2005)
vii. Payment Devices Frauds Act (No.30 of 2006)
viii. These are some major acts which related to cyber crimes.
Information and Communication Technology Act (No.27 of 2003)
47. This act is developed to improve ICT and resolve its disputes efficiently. In UK there
are several laws as Computer Misuse Act (1990), Trade Marks Act (1994), Defamation Act
(1996), Data Protection Act (1998), the Copyright and Related Regulations (1996), Electronic
Communication Act (2000), Telecommunications Regulations (1999), ‘The Consumer
Protection (Distant Selling) Regulations (2000)
20
RESTRICTED
CHAPTER FOUR
GOVERNMENT’S PERSPECTIVE
SRI LANKA’S LEGISLATIONS ON CYBERTERRORISM
45. The law regarding Legal Security and Copy Right Laws in Sri Lanka based on the
English law. Both English law and Sri Lankan laws are having common features in regarding
to the e-media. Furthermore in Sri Lanka there is no any difference between domestic law
and the international law regarding cyber-terrorism.
46. There are several legislations which passed by the Parliament recently.
i. Information and Communication Technology Act (No.27 of 2003)
ii. Evidence (Special Provisions) (Act No.14 of 1995)
iii. Intellectual Property Act (No. 36 of 2003 (Sections related to Copyright)
iv. Electronic Transactions Act (No. 19 of 2006)
v. Computer Crimes Act (No. 24 of 2007)
vi. Payment And Settlement Systems Act, (No. 28 of 2005)
vii. Payment Devices Frauds Act (No.30 of 2006)
viii. These are some major acts which related to cyber crimes.
Information and Communication Technology Act (No.27 of 2003)
47. This act is developed to improve ICT and resolve its disputes efficiently. In UK there
are several laws as Computer Misuse Act (1990), Trade Marks Act (1994), Defamation Act
(1996), Data Protection Act (1998), the Copyright and Related Regulations (1996), Electronic
Communication Act (2000), Telecommunications Regulations (1999), ‘The Consumer
Protection (Distant Selling) Regulations (2000)
20
RESTRICTED

RESTRICTED
48. By this act it establishes a national committee on Information and Communication
Technology of Sri Lanka and to introduce a national policy on ICT and for the preparation of
an action plan.
Intellectual Property Act (No. 36 of 2003 (Sections related to Copyright)
49. We are mainly considering regarding the copy rights sections of this act. According to
the act Copyright means the rights given by law to the creators for their literary and artistic
works. The rights takes two forms
i. economic rights
ii. moral rights.
50. Copyright protects the rights of the authors of literary and artistic works and ensures
them the economic benefits and recognition thereby promoting creativity in literary and
artistic fields and investment. Such creations enhance economic development, education,
culture, and enjoyment of life. When it comes to the Cyber terrorism it deals with the
software matters or any matter which related to computers.
Electronic Transactions Act (No. 19 of 2006)
51. This act deals with the creation and exchange of data messages, electronic documents,
electronic records and other communications in electronic form in Sri Lanka. And it provides
for the appointment of a certification authority and accreditation of certification service
providers.
Computer Crimes Act (No. 24 of 2007)
52. This is an act to provide for the identification of computer crime and to provide the
procedure for the investigation and prevention of such crimes ; and to provide for matters
connected there with and incidental. The Sri Lankan Computer Crimes Act No. 24 of 2007
primarily addresses computer-related crimes and hacking offences. Content related offences
21
RESTRICTED
48. By this act it establishes a national committee on Information and Communication
Technology of Sri Lanka and to introduce a national policy on ICT and for the preparation of
an action plan.
Intellectual Property Act (No. 36 of 2003 (Sections related to Copyright)
49. We are mainly considering regarding the copy rights sections of this act. According to
the act Copyright means the rights given by law to the creators for their literary and artistic
works. The rights takes two forms
i. economic rights
ii. moral rights.
50. Copyright protects the rights of the authors of literary and artistic works and ensures
them the economic benefits and recognition thereby promoting creativity in literary and
artistic fields and investment. Such creations enhance economic development, education,
culture, and enjoyment of life. When it comes to the Cyber terrorism it deals with the
software matters or any matter which related to computers.
Electronic Transactions Act (No. 19 of 2006)
51. This act deals with the creation and exchange of data messages, electronic documents,
electronic records and other communications in electronic form in Sri Lanka. And it provides
for the appointment of a certification authority and accreditation of certification service
providers.
Computer Crimes Act (No. 24 of 2007)
52. This is an act to provide for the identification of computer crime and to provide the
procedure for the investigation and prevention of such crimes ; and to provide for matters
connected there with and incidental. The Sri Lankan Computer Crimes Act No. 24 of 2007
primarily addresses computer-related crimes and hacking offences. Content related offences
21
RESTRICTED

RESTRICTED
are being addressed through a series of changes to the Penal Code and other statutory
provisions.
53. Cultures globally are progressively reliant on information and communication
technologies (ICT) and thus susceptible to risks such as cyber-crime which comprises a
misuse of technological innovation. To deal with this element Sri Lanka introduced the
Computer Crimes Act No. 24 of 2007 which was introduced into functional impact from July
15, 2008. Having done so, it has become necessary to boost potential amongst most all judges
as well as researchers and prosecutors to use this regulation in practice.
54. Apart from offering a better way of life for community the fast growth of ICT
increases essential questions regarding storage space of private details, privacy, data
protection and crime. Computer systems are not only focused for criminal activity but are
also important equipment used in the commission payment of other violations such as fraud,
scams, forgery, damage, removal of business details and ruin of computer features, etc.The
phrase “Computer Crime” is a common phrase used to recognize all criminal offenses or
scammers that are linked with or related to computers and it.
55. Generally computer crime consists of three components. They are:-
i. Computer Related crimes – Computers used as a tool for criminal activity such
as theft, fraud, etc.
ii. Hacking offences – which affects integrity, availability and confidentiality of a
computer system or network (also includes the introduction of viruses, worms etc).
iii. Content related Cyber Crime – where computers together with Internet
resources are used to distribute illegal data. Eg;- Internet based pornography,
criminal copyright infringement
56. Sri Lankan Computer Crime act is content with 38 chapters. All those rules and
regulation are discussed in the Computer Crime Act. Any person who obtains unauthorized
access to a computer or network (Computer hacking and cracking), modification of a
computer or network unlawfully, offences
22
RESTRICTED
are being addressed through a series of changes to the Penal Code and other statutory
provisions.
53. Cultures globally are progressively reliant on information and communication
technologies (ICT) and thus susceptible to risks such as cyber-crime which comprises a
misuse of technological innovation. To deal with this element Sri Lanka introduced the
Computer Crimes Act No. 24 of 2007 which was introduced into functional impact from July
15, 2008. Having done so, it has become necessary to boost potential amongst most all judges
as well as researchers and prosecutors to use this regulation in practice.
54. Apart from offering a better way of life for community the fast growth of ICT
increases essential questions regarding storage space of private details, privacy, data
protection and crime. Computer systems are not only focused for criminal activity but are
also important equipment used in the commission payment of other violations such as fraud,
scams, forgery, damage, removal of business details and ruin of computer features, etc.The
phrase “Computer Crime” is a common phrase used to recognize all criminal offenses or
scammers that are linked with or related to computers and it.
55. Generally computer crime consists of three components. They are:-
i. Computer Related crimes – Computers used as a tool for criminal activity such
as theft, fraud, etc.
ii. Hacking offences – which affects integrity, availability and confidentiality of a
computer system or network (also includes the introduction of viruses, worms etc).
iii. Content related Cyber Crime – where computers together with Internet
resources are used to distribute illegal data. Eg;- Internet based pornography,
criminal copyright infringement
56. Sri Lankan Computer Crime act is content with 38 chapters. All those rules and
regulation are discussed in the Computer Crime Act. Any person who obtains unauthorized
access to a computer or network (Computer hacking and cracking), modification of a
computer or network unlawfully, offences
22
RESTRICTED
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESTRICTED
committed against national security, dealing with data unlawfully obtained illegal
interception of data, using of illegal device, unauthorized disclosure of
information enabling access to a service are the offences defined under sections 3 to 10 of the
Act respectively.It states:
i. The illustrations given in the Act states that for any unauthorised modification
or damage or potential damage to take place, any one of the following should occur –
ii. Impairing the operation of any computer, computer system or the reliability of
any data or information held in any computer; or
iii. Destroying, deleting or corrupting or adding, moving or altering any
information held in any computer;
iv. Making use of a computer service involving computer time and data
processing for the storage or retrieval of data;
v. Introducing a computer program which will have the effect of malfunctioning
of a computer or falsifies the data or any information held in any computer or
computer system (eg:- viruses, worms, etc).
57. Other than that following offences also include in computer crime act. Unauthorized
obtaining of information from a computer or a storage medium; unauthorized use of
computer service and interception of data; selling, importing or distributing any device or
computer access code or password for the commission of offences under the Act; providing
access information to a service without authority or in breach of a contract.
58. Section 15 & 16 of the act describes regarding the investigations in connection with
offences under the same Act. To achieve this objective, the act has been included allowing a
board of professionals to assist the Cops in the research computer crime activity offences. In
terms of the role imagined for
59. professionals they will believe legislation only when their assistance is called for. The
Act encourages the professionals with specific abilities, such as as visiting the scene of crime
for purposes of investigation, to access and analyze computers, data or information organized
in a computer, etc.
23
RESTRICTED
committed against national security, dealing with data unlawfully obtained illegal
interception of data, using of illegal device, unauthorized disclosure of
information enabling access to a service are the offences defined under sections 3 to 10 of the
Act respectively.It states:
i. The illustrations given in the Act states that for any unauthorised modification
or damage or potential damage to take place, any one of the following should occur –
ii. Impairing the operation of any computer, computer system or the reliability of
any data or information held in any computer; or
iii. Destroying, deleting or corrupting or adding, moving or altering any
information held in any computer;
iv. Making use of a computer service involving computer time and data
processing for the storage or retrieval of data;
v. Introducing a computer program which will have the effect of malfunctioning
of a computer or falsifies the data or any information held in any computer or
computer system (eg:- viruses, worms, etc).
57. Other than that following offences also include in computer crime act. Unauthorized
obtaining of information from a computer or a storage medium; unauthorized use of
computer service and interception of data; selling, importing or distributing any device or
computer access code or password for the commission of offences under the Act; providing
access information to a service without authority or in breach of a contract.
58. Section 15 & 16 of the act describes regarding the investigations in connection with
offences under the same Act. To achieve this objective, the act has been included allowing a
board of professionals to assist the Cops in the research computer crime activity offences. In
terms of the role imagined for
59. professionals they will believe legislation only when their assistance is called for. The
Act encourages the professionals with specific abilities, such as as visiting the scene of crime
for purposes of investigation, to access and analyze computers, data or information organized
in a computer, etc.
23
RESTRICTED

RESTRICTED
60. A panel of experts will be appointed by the Minister-in-charge of the subject of
Science and Technology. Qualifications, experience and remuneration of such experts are
explained in the section 17 of the Act.
61. Section 18 of the act states that such experts called upon to assist any police officer
shall have power to enter any premises along with a police officer not below the rank of a
sub-inspector, access any information system, computer or computer system or any program,
data or information held in such computer to perform any function or to do any such other
thing, require any person to disclose any traffic data, oral examination of any person, do such
other things as may be reasonably required for the purpose of the same Act. Further section
19 & 21 also describe that if preservation of information reasonably required for the purposes
of investigations, expert or Police officer has powers to arrest, search and seize any
information accessible within any premises without a warrant in the course of investigation.
62. Section 23, section 24, section 28 and section 29 is related to the duties of the
investigator. Section 28 provides immunity from legal proceedings against experts (who are
peace officers under the section 29 of the Act) and Police officers appointed for
investigations under the Act.
63. Section 33 of the Act provides where a request is made to the Government of Sri
Lanka, by or on behalf on another Government for the purpose of extradition of the person
accused or convicted of an offence under this Act the Minister shall forthwith notify the
requesting Government of the measures which the Government of Sri Lanka has taken, or
proposed to take to extradite the person for that offence. Rights of non-resident persons
arrested under this Act specified under Section 34 of the Act.
64. Under section 35 of the Computer Crime Act the provisions of the Mutual Assistance
in Criminal Matters Act No. 25 of 2002 are applicable for the investigation and prosecution
of the offences under the Computer Crime Act.
24
RESTRICTED
60. A panel of experts will be appointed by the Minister-in-charge of the subject of
Science and Technology. Qualifications, experience and remuneration of such experts are
explained in the section 17 of the Act.
61. Section 18 of the act states that such experts called upon to assist any police officer
shall have power to enter any premises along with a police officer not below the rank of a
sub-inspector, access any information system, computer or computer system or any program,
data or information held in such computer to perform any function or to do any such other
thing, require any person to disclose any traffic data, oral examination of any person, do such
other things as may be reasonably required for the purpose of the same Act. Further section
19 & 21 also describe that if preservation of information reasonably required for the purposes
of investigations, expert or Police officer has powers to arrest, search and seize any
information accessible within any premises without a warrant in the course of investigation.
62. Section 23, section 24, section 28 and section 29 is related to the duties of the
investigator. Section 28 provides immunity from legal proceedings against experts (who are
peace officers under the section 29 of the Act) and Police officers appointed for
investigations under the Act.
63. Section 33 of the Act provides where a request is made to the Government of Sri
Lanka, by or on behalf on another Government for the purpose of extradition of the person
accused or convicted of an offence under this Act the Minister shall forthwith notify the
requesting Government of the measures which the Government of Sri Lanka has taken, or
proposed to take to extradite the person for that offence. Rights of non-resident persons
arrested under this Act specified under Section 34 of the Act.
64. Under section 35 of the Computer Crime Act the provisions of the Mutual Assistance
in Criminal Matters Act No. 25 of 2002 are applicable for the investigation and prosecution
of the offences under the Computer Crime Act.
24
RESTRICTED

RESTRICTED
65. Provisions under the Mutual Assistance in Criminal Matters Act explain that the
procedure shall be followed to make a request from the authority of a foreign State by Sri
Lankan Authority and vice versa to transfer of evidence, thing, witnesses and accused and the
procedure after complying with such request.
66. Other computer related offences are :
i. Publication of an obscene article electronically may be a criminal offence
under amended section 2 of the Obscene Publication Ordinance, No. 22 of 1983.
ii. Section 286B of the Penal Code (Amendment Act No. 16 of 2006) introduced
the offence as it is a duty of person providing service by computer to prevent sexual
abuse of a child and person who contravenes the same shall be guilty of an offence.
iii. Further, storing or distribution of child phonography by e-mail and the Internet
may be an offence under section 286(c) of the Penal Code (Amendment) No. 22 of
1995 read with provisions under Electronic Transactions Act No. 19 of 2006.
67. However, it is time to bring new amendments to the same law avoiding certain
unnecessary disputes that arise over interpretation of creation of pseudo-photographs under
this Ordinance
68. Chapter 38 of the Intellectual Property Act No.36 of 2003 defines the Offences and
Penalties against violation of Intellectual Property Rights and these provisions are applicable
for Intellectual Property Rights violations in cyber space as well.
69. Under the Sri Lanka Telecommunications Act No. 25 of 1991 'Intrusion',
'interception and disclosure of contents of message' by telecommunication officials, other
than in the course of his duty are offences under sections 52-54 of the Act. "Usage
information" means information relating to the identity of calling subscriber, called
subscriber, date and time of originating of message and the type of message for the purpose
of sections 52 and 54.
25
RESTRICTED
65. Provisions under the Mutual Assistance in Criminal Matters Act explain that the
procedure shall be followed to make a request from the authority of a foreign State by Sri
Lankan Authority and vice versa to transfer of evidence, thing, witnesses and accused and the
procedure after complying with such request.
66. Other computer related offences are :
i. Publication of an obscene article electronically may be a criminal offence
under amended section 2 of the Obscene Publication Ordinance, No. 22 of 1983.
ii. Section 286B of the Penal Code (Amendment Act No. 16 of 2006) introduced
the offence as it is a duty of person providing service by computer to prevent sexual
abuse of a child and person who contravenes the same shall be guilty of an offence.
iii. Further, storing or distribution of child phonography by e-mail and the Internet
may be an offence under section 286(c) of the Penal Code (Amendment) No. 22 of
1995 read with provisions under Electronic Transactions Act No. 19 of 2006.
67. However, it is time to bring new amendments to the same law avoiding certain
unnecessary disputes that arise over interpretation of creation of pseudo-photographs under
this Ordinance
68. Chapter 38 of the Intellectual Property Act No.36 of 2003 defines the Offences and
Penalties against violation of Intellectual Property Rights and these provisions are applicable
for Intellectual Property Rights violations in cyber space as well.
69. Under the Sri Lanka Telecommunications Act No. 25 of 1991 'Intrusion',
'interception and disclosure of contents of message' by telecommunication officials, other
than in the course of his duty are offences under sections 52-54 of the Act. "Usage
information" means information relating to the identity of calling subscriber, called
subscriber, date and time of originating of message and the type of message for the purpose
of sections 52 and 54.
25
RESTRICTED
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESTRICTED
70. Provisions under Code of Criminal Procedure Act No. 19 of 1979 are applicable for
investigations of these offences.The Payment Devices Frauds act was introduced to deal with
fraudulent transactions taken place in connection with electronic devices and similar
provisions relating to Computer Crime Act on procedural matters can be found under the
present Act as well.
71. Offences under this Act are cognizable offences. Section 12 explains on
Confidentiality of information obtained in the course of an investigation. Even though Sri
Lanka currently has Methods on fighting criminal activity like the method against interaction
that increases national hate, the new law is to help deal with these concerns better. And we
still need more exercising and attention.
72. Sri Lanka is completely helpful of the strategy implemented by the authorities of European
countries and is efficiently looking at the alternatives to accede to the meeting. Initial actions
have already been started by the government in this relationship and it is predicted that formal
conversation would started with the Council of European countries for this objective, during
2009.
26
RESTRICTED
70. Provisions under Code of Criminal Procedure Act No. 19 of 1979 are applicable for
investigations of these offences.The Payment Devices Frauds act was introduced to deal with
fraudulent transactions taken place in connection with electronic devices and similar
provisions relating to Computer Crime Act on procedural matters can be found under the
present Act as well.
71. Offences under this Act are cognizable offences. Section 12 explains on
Confidentiality of information obtained in the course of an investigation. Even though Sri
Lanka currently has Methods on fighting criminal activity like the method against interaction
that increases national hate, the new law is to help deal with these concerns better. And we
still need more exercising and attention.
72. Sri Lanka is completely helpful of the strategy implemented by the authorities of European
countries and is efficiently looking at the alternatives to accede to the meeting. Initial actions
have already been started by the government in this relationship and it is predicted that formal
conversation would started with the Council of European countries for this objective, during
2009.
26
RESTRICTED

RESTRICTED
ACTIONS TAKEN BY THE GOVERNMENT
73. With the rapid development of the Internet, many economies are now increasingly
dependent on public network applications such as online banking, online stock trading, e-
business, e-government and e-customs. The protection of the various national information
infrastructures that make up this new and emerging e-economy is critical to a country's
political and economic stability and security. The need to protect these critical national
information infrastructures is also urgent.
74. Attacks on information infrastructures are increasing in frequency, sophistication and
scale. For example, the Code Red II Internet worm integrated characteristics of a computer
virus, Trojan, Worm and Hacking activity to propagate quickly across the Internet and infect
massive numbers of host computers.
75. When discussing the Sri Lankan situation it is a must to gain an idea on the
background.Sri Lanka’s telecommunication regulator is Telecommunication Regulatory
Commission Sri Lanka (TRCSL) and its main objective is to ensure the availability of
advanced and high quality service throughout the country at an affordable price. TRCSL
directly engage with the telecommunication service providers to ensure the aim is being
achieve and also regulates the services given by drafting policies in the field of
telecommunication.
76. Information and Communication Technology Agency of Sri Lanka who is a fully
owned organization of the Sri Lankan government work along with TRCSL in implementing
the policies, building up ICT related infrastructure and ICT training with the aim of building
Sri Lanka A IT savvy country.
77. With funding of the World Bank ICTA is conducting programmes to develop ICT
infrastructure and it has been a major contributor in achieving the country’s development
objectives through the growths related to Connectivity, Accessibility and Content. The
following graph is a clear indication to that. Sri Lanka’s Network Readiness Index has Raised
significantly during the recent past years and comparing it with Pakistan a similar South
Asian developing country Sri Lanka is in a comprehensive status.
27
RESTRICTED
ACTIONS TAKEN BY THE GOVERNMENT
73. With the rapid development of the Internet, many economies are now increasingly
dependent on public network applications such as online banking, online stock trading, e-
business, e-government and e-customs. The protection of the various national information
infrastructures that make up this new and emerging e-economy is critical to a country's
political and economic stability and security. The need to protect these critical national
information infrastructures is also urgent.
74. Attacks on information infrastructures are increasing in frequency, sophistication and
scale. For example, the Code Red II Internet worm integrated characteristics of a computer
virus, Trojan, Worm and Hacking activity to propagate quickly across the Internet and infect
massive numbers of host computers.
75. When discussing the Sri Lankan situation it is a must to gain an idea on the
background.Sri Lanka’s telecommunication regulator is Telecommunication Regulatory
Commission Sri Lanka (TRCSL) and its main objective is to ensure the availability of
advanced and high quality service throughout the country at an affordable price. TRCSL
directly engage with the telecommunication service providers to ensure the aim is being
achieve and also regulates the services given by drafting policies in the field of
telecommunication.
76. Information and Communication Technology Agency of Sri Lanka who is a fully
owned organization of the Sri Lankan government work along with TRCSL in implementing
the policies, building up ICT related infrastructure and ICT training with the aim of building
Sri Lanka A IT savvy country.
77. With funding of the World Bank ICTA is conducting programmes to develop ICT
infrastructure and it has been a major contributor in achieving the country’s development
objectives through the growths related to Connectivity, Accessibility and Content. The
following graph is a clear indication to that. Sri Lanka’s Network Readiness Index has Raised
significantly during the recent past years and comparing it with Pakistan a similar South
Asian developing country Sri Lanka is in a comprehensive status.
27
RESTRICTED

RESTRICTED
78. ICTA also does human resource training in the field of ICT mainly focusing on the
government employees so that they can effectively work along with the evolving ICT related
trends and infrastructure. Through the programmes such as e-Sri Lanka, e-government and e-
society ICTA intends to increase the IT literacy rate of Sri Lanka. These projects have been
successful to some extent as this graph shows there weren’t much development in IT literacy
until around 2004 but with the initiation of these projects the IT literacy of Sri Lanka has seen
a significant growth.
79. These development projects have made a significant change to the society at large and
through this positive transformation there are some unavoidable drawbacks too. The newborn
IT educated younger generation is involving in cyber related crimes more often and due to
this vulnerabilities are growing within the networks To address this urgent need, countries
have established Incident Response Teams and in Sri Lanka the national CERT is the
SLCERT (Sri Lanka Computer Emergency Readiness Team) which is a fully owned
subsidiary of ICTA (Information and Communication Technology of Sri Lanka).
80. A national CERT (Computer Emergency Readiness Team) is an organization which
acts as the focal point for Cyber Security of a nation. It can be taken into consideration as the
most trusted source of advice about the latest threats and vulnerabilities affecting computer
systems and networks and a source of expertise assistance in responding to recovering from
cyber attacks
81. As SLCERT’s mission statement says, it is
i. To be the single and the most trusted point of contact for Information Security
in Sri Lanka.
ii. To protect Information Technology users in the Public and Private Sector
Organizations and the General Public by providing up-to-date information on
potential threats and vulnerabilities and by undertaking computer emergency response
handling services.
iii. To Act as the most authoritative national source for all ICT security related
issues across the nation.
28
RESTRICTED
78. ICTA also does human resource training in the field of ICT mainly focusing on the
government employees so that they can effectively work along with the evolving ICT related
trends and infrastructure. Through the programmes such as e-Sri Lanka, e-government and e-
society ICTA intends to increase the IT literacy rate of Sri Lanka. These projects have been
successful to some extent as this graph shows there weren’t much development in IT literacy
until around 2004 but with the initiation of these projects the IT literacy of Sri Lanka has seen
a significant growth.
79. These development projects have made a significant change to the society at large and
through this positive transformation there are some unavoidable drawbacks too. The newborn
IT educated younger generation is involving in cyber related crimes more often and due to
this vulnerabilities are growing within the networks To address this urgent need, countries
have established Incident Response Teams and in Sri Lanka the national CERT is the
SLCERT (Sri Lanka Computer Emergency Readiness Team) which is a fully owned
subsidiary of ICTA (Information and Communication Technology of Sri Lanka).
80. A national CERT (Computer Emergency Readiness Team) is an organization which
acts as the focal point for Cyber Security of a nation. It can be taken into consideration as the
most trusted source of advice about the latest threats and vulnerabilities affecting computer
systems and networks and a source of expertise assistance in responding to recovering from
cyber attacks
81. As SLCERT’s mission statement says, it is
i. To be the single and the most trusted point of contact for Information Security
in Sri Lanka.
ii. To protect Information Technology users in the Public and Private Sector
Organizations and the General Public by providing up-to-date information on
potential threats and vulnerabilities and by undertaking computer emergency response
handling services.
iii. To Act as the most authoritative national source for all ICT security related
issues across the nation.
28
RESTRICTED
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESTRICTED
iv. To Link with other CERTS and CSIRTS around the world to share the
knowledge and know how relating to Information Security.
82. To achieve its objectives SLCERT has divided its services to
i. Responsive
ii. Awareness
iii. Consultancy
83. One of the main services which are provided by the CERTs are the responsive
services which are being implemented when a report is being submitted by a constituent.
These are services which are triggered by events that are capable of causing adverse effects
on a constituent’s Cyber Systems.
84. This service involves responding to a request or notification by a constituent that an
unusual event has been detected, which may be affecting the performance, availability or
stability of the services or cyber systems belonging to that constituent.
85. There are many types of Incidents. Some typical examples are:
i. Malware (Viruses, Trojans, Backdoors, etc)
ii. Site Defacement
iii. DoS Attack
iv. Phishing
v. System Compromise
vi. Hate/Threat Mail
vii. Identity/Information Theft
86. Sri Lanka CERT|CC will perform steps to identify the Incident and rate the severity of
that Incident. The constituent will then be advised on how to contain the incident and
eradicate the cause. Once the systems are fully recovered, Sri Lanka CERT|CC will submit a
29
RESTRICTED
iv. To Link with other CERTS and CSIRTS around the world to share the
knowledge and know how relating to Information Security.
82. To achieve its objectives SLCERT has divided its services to
i. Responsive
ii. Awareness
iii. Consultancy
83. One of the main services which are provided by the CERTs are the responsive
services which are being implemented when a report is being submitted by a constituent.
These are services which are triggered by events that are capable of causing adverse effects
on a constituent’s Cyber Systems.
84. This service involves responding to a request or notification by a constituent that an
unusual event has been detected, which may be affecting the performance, availability or
stability of the services or cyber systems belonging to that constituent.
85. There are many types of Incidents. Some typical examples are:
i. Malware (Viruses, Trojans, Backdoors, etc)
ii. Site Defacement
iii. DoS Attack
iv. Phishing
v. System Compromise
vi. Hate/Threat Mail
vii. Identity/Information Theft
86. Sri Lanka CERT|CC will perform steps to identify the Incident and rate the severity of
that Incident. The constituent will then be advised on how to contain the incident and
eradicate the cause. Once the systems are fully recovered, Sri Lanka CERT|CC will submit a
29
RESTRICTED

RESTRICTED
87. comprehensive Incident Report detailing the nature of the incident, steps taken to
recover from the incident and recommended preventive measures for the future.
88. Since the inception of Sri Lanka CERT in 2006 the rate of incident reporting has
increased rapidly and to prove that in 2010 it was only 151 whereas in 2011 it was 1469 and
all these incidents have been resolved satisfactorily.
30
RESTRICTED
87. comprehensive Incident Report detailing the nature of the incident, steps taken to
recover from the incident and recommended preventive measures for the future.
88. Since the inception of Sri Lanka CERT in 2006 the rate of incident reporting has
increased rapidly and to prove that in 2010 it was only 151 whereas in 2011 it was 1469 and
all these incidents have been resolved satisfactorily.
30
RESTRICTED
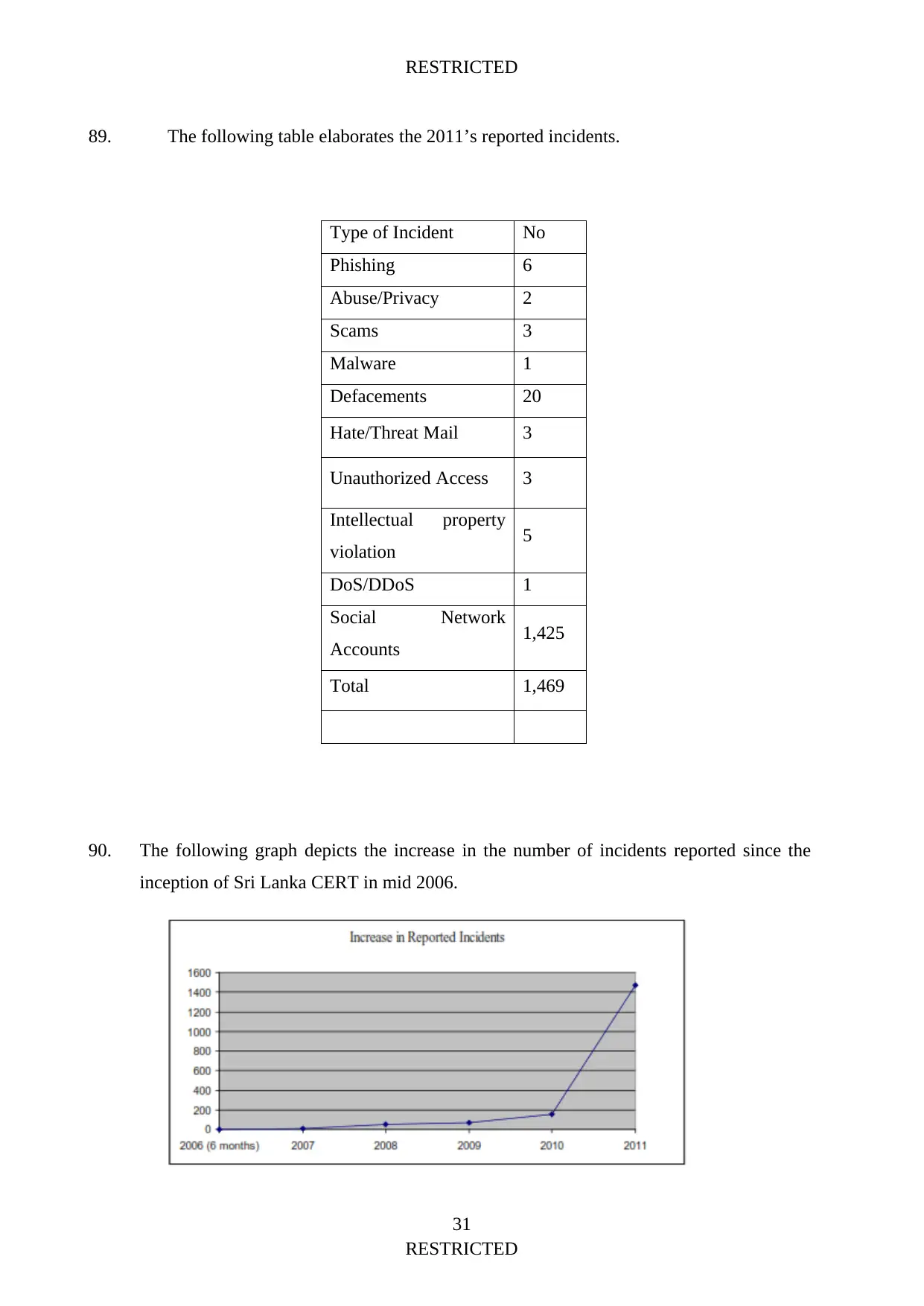
RESTRICTED
89. The following table elaborates the 2011’s reported incidents.
Type of Incident No
Phishing 6
Abuse/Privacy 2
Scams 3
Malware 1
Defacements 20
Hate/Threat Mail 3
Unauthorized Access 3
Intellectual property
violation 5
DoS/DDoS 1
Social Network
Accounts 1,425
Total 1,469
90. The following graph depicts the increase in the number of incidents reported since the
inception of Sri Lanka CERT in mid 2006.
31
RESTRICTED
89. The following table elaborates the 2011’s reported incidents.
Type of Incident No
Phishing 6
Abuse/Privacy 2
Scams 3
Malware 1
Defacements 20
Hate/Threat Mail 3
Unauthorized Access 3
Intellectual property
violation 5
DoS/DDoS 1
Social Network
Accounts 1,425
Total 1,469
90. The following graph depicts the increase in the number of incidents reported since the
inception of Sri Lanka CERT in mid 2006.
31
RESTRICTED
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESTRICTED
91. Another service provided by SLCERT is the awareness services. SLCRT conduct
seminars and workshops in order to enhance the awareness level of the general population
in the field of computer security.
92. What professionals believes is that the security is in the hands of the user itself and
SLCERT always focus on the personal security of the user and to begin with, SLCERT
encourages the user to use genuine software as much as possible to ensure a high level of
security and also provide guidelines to achieve a high level of privacy within the network.
93. Furthermore SLCERT publish news bulletins on its website, radio, TV and newspapers
on the current incidents, the latest trends and the preventive measures that can be taken.
Distributing handouts is another mode of educating the public on the Computer security.
94. SLCERT provides its expertise through consultancy services to the government
organizations, non government organizations, various institutions and individuals. There
they provide technical consultancy through ethical hacking and penetrant testing, and
issues a security certification for the network’s security level. Furthermore they provide
legal consultancy if needed at an incident.
95. Other than these services SLCERT updates a knowledge base which gathers information
on information security. Furthermore SLCERT has established a wing named Bank
Computer Security Information and Readiness Team (Bank CSIRT) where SLCERT act
as an intermediary within the banks and share ideas on latest trends which threaten the
sector.
96. SLCERT is a member of Asia Pacific CERT (APCERT) and coordinate with various
other CERTs situated around the world. Through this they are building a web of trust
among the countries so that an effective response specially when threats originate from
foreign countries and situational awareness can be delivered to the public.
97. In the future SLCERT intends to develop an automated threat alert system to deliver
alerts with no time. Further the SLCERT also intend to develop a Defence CSIRT and
Telco CSIRT where to interconnect similar parties with each other while SLCERT being
the intermediary.
32
RESTRICTED
91. Another service provided by SLCERT is the awareness services. SLCRT conduct
seminars and workshops in order to enhance the awareness level of the general population
in the field of computer security.
92. What professionals believes is that the security is in the hands of the user itself and
SLCERT always focus on the personal security of the user and to begin with, SLCERT
encourages the user to use genuine software as much as possible to ensure a high level of
security and also provide guidelines to achieve a high level of privacy within the network.
93. Furthermore SLCERT publish news bulletins on its website, radio, TV and newspapers
on the current incidents, the latest trends and the preventive measures that can be taken.
Distributing handouts is another mode of educating the public on the Computer security.
94. SLCERT provides its expertise through consultancy services to the government
organizations, non government organizations, various institutions and individuals. There
they provide technical consultancy through ethical hacking and penetrant testing, and
issues a security certification for the network’s security level. Furthermore they provide
legal consultancy if needed at an incident.
95. Other than these services SLCERT updates a knowledge base which gathers information
on information security. Furthermore SLCERT has established a wing named Bank
Computer Security Information and Readiness Team (Bank CSIRT) where SLCERT act
as an intermediary within the banks and share ideas on latest trends which threaten the
sector.
96. SLCERT is a member of Asia Pacific CERT (APCERT) and coordinate with various
other CERTs situated around the world. Through this they are building a web of trust
among the countries so that an effective response specially when threats originate from
foreign countries and situational awareness can be delivered to the public.
97. In the future SLCERT intends to develop an automated threat alert system to deliver
alerts with no time. Further the SLCERT also intend to develop a Defence CSIRT and
Telco CSIRT where to interconnect similar parties with each other while SLCERT being
the intermediary.
32
RESTRICTED

RESTRICTED
CHAPTER FIVE
LEGAL BACKGROUND
UNITED STATES OF AMERICA’S LEGISLATIONS ON
CYBERTERRORISM
98. Cyberspace, as the fifth common domain - after land, sea, air and outer space, is in
great need for coordination, cooperation and legal measures among all nations. A cyberspace
treaty or a set of treaties at the United Nations level, including cyber security and
cybercrime, should be the global framework for peace and justice in cyberspace. Cyberspace
should be a part of the progressive development of International law.
99. The most serious cybercrimes and cyber-attacks of global concern should be
investigated and prosecuted based on international law, and sentenced by an international
Court or Tribunal for cyberspace.
100. According to the definition given by the USA Department of State Cyber terrorism is
"Premeditated politically motivated violence perpetrated against non-combatant targets by
sub-national groups or clandestine agents" .Furthermore The USA National Infrastructure
Protection Center define Cyber Terrorism as the ‘’A criminal act perpetrated by the use of
computers and telecommunications capabilities, resulting in violence, destruction and/or
disruption of services to create fear by causing confusion and uncertainty within a given
population, with the goal of influencing a government or population to conform to particular
political, social or ideological agenda’’
101. When concerning about the Cyber Laws in USA had identified by passing through the
Cybercrime bill that it required authorities to investigate and prosecute individuals for
internet-related crimes such as fraud, hacking and cyber-sex .Also this Act would expand the
US Penal Code Title 18, Chapter 47, Section 1030, on Fraud and related activity in
connection with computers. Also a Bill titled "Fostering a Global Response to
33
RESTRICTED
CHAPTER FIVE
LEGAL BACKGROUND
UNITED STATES OF AMERICA’S LEGISLATIONS ON
CYBERTERRORISM
98. Cyberspace, as the fifth common domain - after land, sea, air and outer space, is in
great need for coordination, cooperation and legal measures among all nations. A cyberspace
treaty or a set of treaties at the United Nations level, including cyber security and
cybercrime, should be the global framework for peace and justice in cyberspace. Cyberspace
should be a part of the progressive development of International law.
99. The most serious cybercrimes and cyber-attacks of global concern should be
investigated and prosecuted based on international law, and sentenced by an international
Court or Tribunal for cyberspace.
100. According to the definition given by the USA Department of State Cyber terrorism is
"Premeditated politically motivated violence perpetrated against non-combatant targets by
sub-national groups or clandestine agents" .Furthermore The USA National Infrastructure
Protection Center define Cyber Terrorism as the ‘’A criminal act perpetrated by the use of
computers and telecommunications capabilities, resulting in violence, destruction and/or
disruption of services to create fear by causing confusion and uncertainty within a given
population, with the goal of influencing a government or population to conform to particular
political, social or ideological agenda’’
101. When concerning about the Cyber Laws in USA had identified by passing through the
Cybercrime bill that it required authorities to investigate and prosecute individuals for
internet-related crimes such as fraud, hacking and cyber-sex .Also this Act would expand the
US Penal Code Title 18, Chapter 47, Section 1030, on Fraud and related activity in
connection with computers. Also a Bill titled "Fostering a Global Response to
33
RESTRICTED

RESTRICTED
Cyber Attacks Act" was introduced in the US Senate on July 10.2009. The section 06 of the
Bill includes as follows:
34
RESTRICTED
Cyber Attacks Act" was introduced in the US Senate on July 10.2009. The section 06 of the
Bill includes as follows:
34
RESTRICTED
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESTRICTED
"Relevant international cyber security agreements focus only on issues relating to cyber
crime and common operating standards and have not been signed by certain countries from
which cyber attacks may be launched."
102. Furthermore the Pentagon has concluded that computer sabotage coming from another
country can constitute an act of war. Recent attacks on the pentagon’s own systems as well as
the sabotaging of Iran’s nuclear program via the stuxnet computer worm- have given new
urge to USA efforts to develop a more formalized approach to cyber-attacks. Under the Senate
Bill Cybercrime offences would include.
i. Offenses against the confidentiality, integrity and availability of computer data
and systems (illegal access, illegal interception, data inference, system interference,
cyber-squatting, misuse of devices)
ii. Computer-related offenses (computer-related forgery, computer-related fraud)
iii. Content-related offenses (cybersex, child pornography, unsolicited
commercial communications, libel)
iv. Under the measure, any person found guilty of the acts in A and B shall be
punished with imprisonment of prison mayor (imprisonment from six to 12
v. years) or a fine of at least P200,000 or an amount depending on the damage
caused or both depending on the court.
103. On the other hand, any person found guilty of cyber-squatting shall be punished with
imprisonment of prison mayor or a fine of not more than P500,000 (or both); any person
found guilty of unsolicited commercial communication with arrest mayor (imprisonment
from one month to six months) or a fine of at least P50,000 but not more than P250,000 (or
both); and any person found guilty of cybersex with imprisonment of prison mayor or a fine
of at least P200,000 but not more than P1 million (or both).
104. Meanwhile, any person found guilty of child pornography shall be punished according
to Republic Act 9775 or the Anti-Child Pornography Act of 2009.Those who aid in the
commission of any of the acts listed shall likewise be punished with imprisonment one degree
lower than that of the main perpetrator of the offense or a penalty of at least P100,000 but not
more than P500,000, or both depending on the court.
35
RESTRICTED
"Relevant international cyber security agreements focus only on issues relating to cyber
crime and common operating standards and have not been signed by certain countries from
which cyber attacks may be launched."
102. Furthermore the Pentagon has concluded that computer sabotage coming from another
country can constitute an act of war. Recent attacks on the pentagon’s own systems as well as
the sabotaging of Iran’s nuclear program via the stuxnet computer worm- have given new
urge to USA efforts to develop a more formalized approach to cyber-attacks. Under the Senate
Bill Cybercrime offences would include.
i. Offenses against the confidentiality, integrity and availability of computer data
and systems (illegal access, illegal interception, data inference, system interference,
cyber-squatting, misuse of devices)
ii. Computer-related offenses (computer-related forgery, computer-related fraud)
iii. Content-related offenses (cybersex, child pornography, unsolicited
commercial communications, libel)
iv. Under the measure, any person found guilty of the acts in A and B shall be
punished with imprisonment of prison mayor (imprisonment from six to 12
v. years) or a fine of at least P200,000 or an amount depending on the damage
caused or both depending on the court.
103. On the other hand, any person found guilty of cyber-squatting shall be punished with
imprisonment of prison mayor or a fine of not more than P500,000 (or both); any person
found guilty of unsolicited commercial communication with arrest mayor (imprisonment
from one month to six months) or a fine of at least P50,000 but not more than P250,000 (or
both); and any person found guilty of cybersex with imprisonment of prison mayor or a fine
of at least P200,000 but not more than P1 million (or both).
104. Meanwhile, any person found guilty of child pornography shall be punished according
to Republic Act 9775 or the Anti-Child Pornography Act of 2009.Those who aid in the
commission of any of the acts listed shall likewise be punished with imprisonment one degree
lower than that of the main perpetrator of the offense or a penalty of at least P100,000 but not
more than P500,000, or both depending on the court.
35
RESTRICTED

RESTRICTED
105. Apart from that there is a separate computer crime and intellectual property section
function under authority of United States Department of Justice the. This Section (CCIPS) is
responsible for implementing the Department's national strategies in combating computer and
intellectual property crimes worldwide. CCIPS prevents, investigates, and prosecutes
computer crimes by working with other government agencies, the private sector, academic
institutions, and foreign counterparts. Section attorneys work to improve the domestic and
international infrastructure-legal, technological, and operational-to pursue network criminals
most effectively.
106. The Section's enforcement responsibilities against intellectual property crimes are
similarly multi-faceted. Intellectual Property (IP) has become one of the principal U.S.
economic engines, and the nation is a target of choice for thieves of material protected by
copyright, trademark, or trade-secret designation. In pursuing all these goals, CCIPS
attorneys regularly run complex investigations, resolve unique legal and investigative issues
raised by emerging computer and telecommunications technologies; litigate cases; provide
litigation support to other prosecutors; train federal, state, and local law enforcement
personnel; comment on and propose legislation; and initiate and participate in international
efforts to combat computer and intellectual property crime.
107. Intellectual property has become a growing concern with cyber law because of how
easy it has become to copy certain media and distribute that media. The intellectual property
that cyber law tries to protect for the most part is music. With the development of the internet
it has become much easier to download, copy, and distribute music against copyright laws.
Copyright infringement is the violation of another person’s copyright of a piece of
intellectual property. It is much easier now to share music files with other people on the
internet illegally. There are sites that have established a fee to legally purchase music over the
internet now. The money collected goes towards the people who created the music as
royalties.
108. Cyber law enforcement is the process of enforcing cyber law. There are illegal
activities that can occur on the internet that are violations of cyber law. This can be child
pornography, cyber stalking, online fraud, cyber scams, hacking, cyber harassment and virus
attacks. Cyber law can help to protect internet users from having their identity stolen over the
36
RESTRICTED
105. Apart from that there is a separate computer crime and intellectual property section
function under authority of United States Department of Justice the. This Section (CCIPS) is
responsible for implementing the Department's national strategies in combating computer and
intellectual property crimes worldwide. CCIPS prevents, investigates, and prosecutes
computer crimes by working with other government agencies, the private sector, academic
institutions, and foreign counterparts. Section attorneys work to improve the domestic and
international infrastructure-legal, technological, and operational-to pursue network criminals
most effectively.
106. The Section's enforcement responsibilities against intellectual property crimes are
similarly multi-faceted. Intellectual Property (IP) has become one of the principal U.S.
economic engines, and the nation is a target of choice for thieves of material protected by
copyright, trademark, or trade-secret designation. In pursuing all these goals, CCIPS
attorneys regularly run complex investigations, resolve unique legal and investigative issues
raised by emerging computer and telecommunications technologies; litigate cases; provide
litigation support to other prosecutors; train federal, state, and local law enforcement
personnel; comment on and propose legislation; and initiate and participate in international
efforts to combat computer and intellectual property crime.
107. Intellectual property has become a growing concern with cyber law because of how
easy it has become to copy certain media and distribute that media. The intellectual property
that cyber law tries to protect for the most part is music. With the development of the internet
it has become much easier to download, copy, and distribute music against copyright laws.
Copyright infringement is the violation of another person’s copyright of a piece of
intellectual property. It is much easier now to share music files with other people on the
internet illegally. There are sites that have established a fee to legally purchase music over the
internet now. The money collected goes towards the people who created the music as
royalties.
108. Cyber law enforcement is the process of enforcing cyber law. There are illegal
activities that can occur on the internet that are violations of cyber law. This can be child
pornography, cyber stalking, online fraud, cyber scams, hacking, cyber harassment and virus
attacks. Cyber law can help to protect internet users from having their identity stolen over the
36
RESTRICTED

RESTRICTED
internet, from having their computer records hacked into and from cyber harassment. Cyber
law can be enforced by courts and police officers across the country. If a person violates
109. cyber law they can be subjected to fines and maybe even a jail term. Many police
officers will pose as young teenagers or young children on the internet to help track and arrest
child predators or pedophiles. Cyber law is also monitored and enforced by the United States
Federal Bureau of Investigation.
110. Section 1029, Tittle18, Part1 of the USA Code is about the Fraud and related activity
in connection with access devices .And also Section 1030, Title 18, Part 1 of the USA Code
is about the Fraud and related activity in connection with computers. Also there are some
special provisions in the Cybercrime Legislation in USA.
i. Article 2- Illegal accesses.
ii. Article 3- Illegal interception.
iii. Article4 – Data interference.
iv. Article 5 – System interference.
v. Article 6 –Misuse of devices.
vi. Article 7-Computer related forgery.
vii. Article 8-Computer related fraud.
viii. Article 9-Offences related to the child pornography.
ix. Article 16- Expedited preservation of stored computer data.
x. Article 19- Search and seizure of stored computer data.
xi. Article31- Mutual assistance regarding accessing of stored computer data.
111. Some of the Information Technology Laws established in states of America is that,
Florida Electronic Security Act and Texas Penal Code - Computer Crimes Statute.
Many United States federal agencies oversee the use of information technology. Their
regulations are promulgated in the Code of Federal Regulations of the United States. Over 25
USA agencies have regulations concerning the use of digital and electronic signatures. In
terms of the tort liability of internet service provider and the hosts of internet forums,
Section 230(c) of the Communications Decency Act may provide immunity in the USA.
37
RESTRICTED
internet, from having their computer records hacked into and from cyber harassment. Cyber
law can be enforced by courts and police officers across the country. If a person violates
109. cyber law they can be subjected to fines and maybe even a jail term. Many police
officers will pose as young teenagers or young children on the internet to help track and arrest
child predators or pedophiles. Cyber law is also monitored and enforced by the United States
Federal Bureau of Investigation.
110. Section 1029, Tittle18, Part1 of the USA Code is about the Fraud and related activity
in connection with access devices .And also Section 1030, Title 18, Part 1 of the USA Code
is about the Fraud and related activity in connection with computers. Also there are some
special provisions in the Cybercrime Legislation in USA.
i. Article 2- Illegal accesses.
ii. Article 3- Illegal interception.
iii. Article4 – Data interference.
iv. Article 5 – System interference.
v. Article 6 –Misuse of devices.
vi. Article 7-Computer related forgery.
vii. Article 8-Computer related fraud.
viii. Article 9-Offences related to the child pornography.
ix. Article 16- Expedited preservation of stored computer data.
x. Article 19- Search and seizure of stored computer data.
xi. Article31- Mutual assistance regarding accessing of stored computer data.
111. Some of the Information Technology Laws established in states of America is that,
Florida Electronic Security Act and Texas Penal Code - Computer Crimes Statute.
Many United States federal agencies oversee the use of information technology. Their
regulations are promulgated in the Code of Federal Regulations of the United States. Over 25
USA agencies have regulations concerning the use of digital and electronic signatures. In
terms of the tort liability of internet service provider and the hosts of internet forums,
Section 230(c) of the Communications Decency Act may provide immunity in the USA.
37
RESTRICTED
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESTRICTED
112. Also by enacting the Privacy Act 1974 the congress had found that, "the privacy of
an individual is directly affected by the collection, maintenance, use, and dissemination of
personal information by Federal agencies" and that "the increasing use of computers and
sophisticated information technology, while essential to the efficient operations of the
Government, has greatly magnified the harm to individual privacy that can occur from any
collection, maintenance, use, or dissemination of personal information."
113. Foreign Intelligence Surveillance Act establishes standards and procedures for use of
electronic surveillance to collect "foreign intelligence" within the United States. FISA
overrides the Electronic Communications Privacy Act during investigations when foreign
intelligence is "a significant purpose" of said investigation.
114. Cyber law encompasses the legal issues that are related to the use of inter-networked
information technology. Cyber law is a body of law that governs many areas of law and
regulation including intellectual property, privacy, freedom of expression and jurisdiction.
Cyber law is a difficult and broad range of law to understand. A person using the internet in
the United States could be subject to the cyber laws not only in the United States but also in
other countries. This all depends on what the person in the United States is doing on the
internet in relation to other countries. This is known as jurisdiction and entails the following:
i. The laws of the state/nation in which the user resides
ii. The laws of the state/nation that apply where the server hosting the transaction
is located
iii. The laws of the state/nation which apply to the person or business with whom
the transaction takes place
115. Not all of the laws or regulations regarding cyber law carry over to another state
within the country or even to another country. For instance, what might be illegal on the
internet in one country might be legal in another country and vice versa. There are still
arguments raging today throughout the country about whether or not the internet should be
treated as a physical space or as the internet being a world unto its own. If the internet is
38
RESTRICTED
112. Also by enacting the Privacy Act 1974 the congress had found that, "the privacy of
an individual is directly affected by the collection, maintenance, use, and dissemination of
personal information by Federal agencies" and that "the increasing use of computers and
sophisticated information technology, while essential to the efficient operations of the
Government, has greatly magnified the harm to individual privacy that can occur from any
collection, maintenance, use, or dissemination of personal information."
113. Foreign Intelligence Surveillance Act establishes standards and procedures for use of
electronic surveillance to collect "foreign intelligence" within the United States. FISA
overrides the Electronic Communications Privacy Act during investigations when foreign
intelligence is "a significant purpose" of said investigation.
114. Cyber law encompasses the legal issues that are related to the use of inter-networked
information technology. Cyber law is a body of law that governs many areas of law and
regulation including intellectual property, privacy, freedom of expression and jurisdiction.
Cyber law is a difficult and broad range of law to understand. A person using the internet in
the United States could be subject to the cyber laws not only in the United States but also in
other countries. This all depends on what the person in the United States is doing on the
internet in relation to other countries. This is known as jurisdiction and entails the following:
i. The laws of the state/nation in which the user resides
ii. The laws of the state/nation that apply where the server hosting the transaction
is located
iii. The laws of the state/nation which apply to the person or business with whom
the transaction takes place
115. Not all of the laws or regulations regarding cyber law carry over to another state
within the country or even to another country. For instance, what might be illegal on the
internet in one country might be legal in another country and vice versa. There are still
arguments raging today throughout the country about whether or not the internet should be
treated as a physical space or as the internet being a world unto its own. If the internet is
38
RESTRICTED

RESTRICTED
treated as a physical space then it would be governed by the rules and laws where it is
located. If it is treated as its own world then the internet would self-govern itself.
SUMMARY OF EUROPE BUDAPEST CONVENTION ON
CYBERTERRORISM
116. Currently, the leading international convention on cyber-crime is the Council of
Europe ‘s Convention on Cybercrime , which was signed in Budapest in 2001 and entered
into force in 2004. The Council of Europe, which is not an organ of the European Union, was
founded in 1949 to promote human rights, democracy and the rule of law in Europe. It
current has forty-seven members, including the twenty-seven members of the European
Union and Russia. As at December 2009, the Convention on Cyber-crime had been signed by
forty-six states and ratified by twenty-six. Though the Convention was drafted under the
aegis of the Council of Europe, it is open to signature by non-members. Four non-members
participated in the negotiations of the treaty and signed it (the United States, Canada, Japan
and South Africa), and one non-member has ratified it (the United States). The Convention is
not, therefore, strictly a regional agreement.
117. Yet the fact that it has only been ratified by one non-European state suggests that it
cannot at present be described as a global convention.The Convention lists a number of
crimes which signatories are required to implement in their domestic law, including hacking,
child pornography offenses, and certain offenses related to intellectual property violations. It
also sets out a number of procedural mechanisms which signatories must put in place,
including granting the power to law enforcement authorities to compel Internet Service
Providers to monitor a person’s online activities. Chapter III calls upon signatories to
cooperate to the widest extent possible in the investigation and prosecution of cyber-crime
offenses.
118. Although the term “cybercrime” implies legal activity happening on the Online or
over the world wide web, the opportunity of the Cyber-crime convention goes beyond such
legal violations and also includes legal violations that occur through the use of a computer
and legal violations that involve computers in general. For instance, the Cyber-crime
convention has been formulated by an additional method making any book of improper and
xenophobic propaganda via computer networks a legal activity. Also in this respect, it is
39
RESTRICTED
treated as a physical space then it would be governed by the rules and laws where it is
located. If it is treated as its own world then the internet would self-govern itself.
SUMMARY OF EUROPE BUDAPEST CONVENTION ON
CYBERTERRORISM
116. Currently, the leading international convention on cyber-crime is the Council of
Europe ‘s Convention on Cybercrime , which was signed in Budapest in 2001 and entered
into force in 2004. The Council of Europe, which is not an organ of the European Union, was
founded in 1949 to promote human rights, democracy and the rule of law in Europe. It
current has forty-seven members, including the twenty-seven members of the European
Union and Russia. As at December 2009, the Convention on Cyber-crime had been signed by
forty-six states and ratified by twenty-six. Though the Convention was drafted under the
aegis of the Council of Europe, it is open to signature by non-members. Four non-members
participated in the negotiations of the treaty and signed it (the United States, Canada, Japan
and South Africa), and one non-member has ratified it (the United States). The Convention is
not, therefore, strictly a regional agreement.
117. Yet the fact that it has only been ratified by one non-European state suggests that it
cannot at present be described as a global convention.The Convention lists a number of
crimes which signatories are required to implement in their domestic law, including hacking,
child pornography offenses, and certain offenses related to intellectual property violations. It
also sets out a number of procedural mechanisms which signatories must put in place,
including granting the power to law enforcement authorities to compel Internet Service
Providers to monitor a person’s online activities. Chapter III calls upon signatories to
cooperate to the widest extent possible in the investigation and prosecution of cyber-crime
offenses.
118. Although the term “cybercrime” implies legal activity happening on the Online or
over the world wide web, the opportunity of the Cyber-crime convention goes beyond such
legal violations and also includes legal violations that occur through the use of a computer
and legal violations that involve computers in general. For instance, the Cyber-crime
convention has been formulated by an additional method making any book of improper and
xenophobic propaganda via computer networks a legal activity. Also in this respect, it is
39
RESTRICTED

RESTRICTED
119. worth referring to that although the purposeful law conditions connect with violations
using it, the Cyber-crime convention uses technology-neutral language so that the purposeful
legal law violations may be applied to both current and upcoming technologies involved. This
approach has many advantages, and it may prevent the appearance of legal breaks later on
like the one we are experiencing now concerning cyber-terrorism.
120. The fast improvements in the field of it have a immediate keeping on all segments of
world. The incorporation of telecom and computer, allowing the storage and indication,
regardless of range, of all kinds of interaction reveals a whole range of new opportunities.
These improvements were enhanced by the appearance of details super-highways and
techniques, such as the Online, through which almost anybody will be able to have access to
any electronic details service regardless of where in the world he is situated. By linking to
interaction and details solutions customers create a kind of common area, called "cyber-
space", which is used for genuine requirements but may also be the topic of neglect. These
"cyber-space offences" are either dedicated against the reliability, accessibility, and secrecy
of pcs and telecom techniques or they involve the use of such techniques of their solutions to
make conventional violations. The transborder personality of such violations, e.g. when
dedicated through the Online, is incompatible with the territoriality of nationwide police
officers government bodies.
121. The European Committee on Crime Problems’s specific terms of reference were as
follows:
i. Examine, in the light of Recommendations No R (89) 9 on computer-related
crime and No R (95) 13 concerning problems of criminal procedural law connected
with information technology, in particular the following subjects:
ii. Cyber-space offences, in particular those committed through the use of
telecommunication networks, e.g. the Internet, such as illegal money transactions,
offering illegal services, violation of copyright, as well as those which violate human
dignity and the protection of minors;
iii. Other substantive criminal law issues where a common approach may be
necessary for the purposes of international co-operation such as definitions, sanctions
and responsibility of the actors in cyber-space, including Internet service providers;
40
RESTRICTED
119. worth referring to that although the purposeful law conditions connect with violations
using it, the Cyber-crime convention uses technology-neutral language so that the purposeful
legal law violations may be applied to both current and upcoming technologies involved. This
approach has many advantages, and it may prevent the appearance of legal breaks later on
like the one we are experiencing now concerning cyber-terrorism.
120. The fast improvements in the field of it have a immediate keeping on all segments of
world. The incorporation of telecom and computer, allowing the storage and indication,
regardless of range, of all kinds of interaction reveals a whole range of new opportunities.
These improvements were enhanced by the appearance of details super-highways and
techniques, such as the Online, through which almost anybody will be able to have access to
any electronic details service regardless of where in the world he is situated. By linking to
interaction and details solutions customers create a kind of common area, called "cyber-
space", which is used for genuine requirements but may also be the topic of neglect. These
"cyber-space offences" are either dedicated against the reliability, accessibility, and secrecy
of pcs and telecom techniques or they involve the use of such techniques of their solutions to
make conventional violations. The transborder personality of such violations, e.g. when
dedicated through the Online, is incompatible with the territoriality of nationwide police
officers government bodies.
121. The European Committee on Crime Problems’s specific terms of reference were as
follows:
i. Examine, in the light of Recommendations No R (89) 9 on computer-related
crime and No R (95) 13 concerning problems of criminal procedural law connected
with information technology, in particular the following subjects:
ii. Cyber-space offences, in particular those committed through the use of
telecommunication networks, e.g. the Internet, such as illegal money transactions,
offering illegal services, violation of copyright, as well as those which violate human
dignity and the protection of minors;
iii. Other substantive criminal law issues where a common approach may be
necessary for the purposes of international co-operation such as definitions, sanctions
and responsibility of the actors in cyber-space, including Internet service providers;
40
RESTRICTED
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESTRICTED
iv. The use, including the possibility of transborder use, and the applicability of
coercive powers in a technological environment, e.g. interception of
telecommunications and electronic surveillance of information networks, e.g. via the
Internet, search and seizure in information-processing systems (including Internet
sites), rendering illegal material inaccessible and requiring service providers to
comply with special obligations, taking into account the problems caused by
particular measures of information security, e.g. encryption;
v. The question of jurisdiction in relation to information technology offences,
e.g. to determine the place where the offence was committed (locus delicti) and
which law should accordingly apply, including the problem of ne bis idem in the
case of multiple jurisdictions and the question how to solve positive jurisdiction
conflicts and how to avoid negative jurisdiction conflicts;
vi. Questions of international co-operation in the investigation of cyber-space
offences, in close co-operation with the Committee of Experts on the Operation of
European Conventions in the Penal Field (PC-OC).
122. The Committee should draft a binding legal instrument, as far as possible, on the
items i) – v), with particular emphasis on international questions and, if appropriate,
accessory recommendations regarding specific issues. The Committee may make suggestions
on other issues in the light of technological developments."
123. The Convention, accordingly, contains four chapters:
i. Use of terms
ii. Measures to be taken at domestic level – substantive law and procedural law
iii. International co-operation
iv. Final clauses
41
RESTRICTED
iv. The use, including the possibility of transborder use, and the applicability of
coercive powers in a technological environment, e.g. interception of
telecommunications and electronic surveillance of information networks, e.g. via the
Internet, search and seizure in information-processing systems (including Internet
sites), rendering illegal material inaccessible and requiring service providers to
comply with special obligations, taking into account the problems caused by
particular measures of information security, e.g. encryption;
v. The question of jurisdiction in relation to information technology offences,
e.g. to determine the place where the offence was committed (locus delicti) and
which law should accordingly apply, including the problem of ne bis idem in the
case of multiple jurisdictions and the question how to solve positive jurisdiction
conflicts and how to avoid negative jurisdiction conflicts;
vi. Questions of international co-operation in the investigation of cyber-space
offences, in close co-operation with the Committee of Experts on the Operation of
European Conventions in the Penal Field (PC-OC).
122. The Committee should draft a binding legal instrument, as far as possible, on the
items i) – v), with particular emphasis on international questions and, if appropriate,
accessory recommendations regarding specific issues. The Committee may make suggestions
on other issues in the light of technological developments."
123. The Convention, accordingly, contains four chapters:
i. Use of terms
ii. Measures to be taken at domestic level – substantive law and procedural law
iii. International co-operation
iv. Final clauses
41
RESTRICTED

RESTRICTED
124. Section 1 of chapter II (substantive law issues) covers both criminalization conditions
and other linked conditions in the area of computer- or computer-related crime: it first
describes 9 offences arranged in 4 different groups, then deals with additional responsibility
and actions against. The following offences are described by the Convention: unlawful
access, unlawful interception, data disturbance, system disturbance, neglect of devices,
computer-related forgery, computer-related scams, violations relevant to child porn and
violations relevant to trademark and neighboring rights.
125. Section 2 of Chapter II (procedural law issues) – the opportunity of which goes
beyond the offences described in chapter 1 in that it relates to any offence dedicated by
means of a computer or the proof of which is in electronic form – decides first the common
circumstances and shields, appropriate to all step-by-step abilities in this chapter. It then sets
out the following step-by-step powers: expedited preservation of stored data; expedited
preservation and partial disclosure of traffic data; production order; search and seizure of
computer data; real-time collection of traffic data; interception of content data. Chapter II
finishes with the legislation circumstances
126. Chapter III contains the conditions concerning conventional and cyber crime-related
common support as well as extradition guidelines. It protects conventional common support
in two situations: where no legal base (treaty, shared regulation, etc.) prevails between events
– in which situation its conditions implement – and where such a base prevails – in which
situation the current agreements also implement to support under this Convention. Computer-
or computer-related criminal activity particular support relates to both circumstances and
protects, subject to extra-conditions, the same range of step-by-step abilities as described in
Chapter II. In addition, chapter III contains a supply on a particular type of trans-border
access to saved data which does not require common support (with approval or where openly
available) and provides for the setting up of a 24/7 network for guaranteeing quick support
among the Parties. Finally, Chapter IV contains the final clauses, which – with certain
exceptions – repeat the standard provisions in Council of Europe treaties.
127. According to article 22 of Europe convention of Cyber-crime there are five different
jurisdiction theories have been applied altogether by courts and governments, all leading to
the ascribing of jurisdiction to one court and adversely affecting other courts’ jurisdiction.
42
RESTRICTED
124. Section 1 of chapter II (substantive law issues) covers both criminalization conditions
and other linked conditions in the area of computer- or computer-related crime: it first
describes 9 offences arranged in 4 different groups, then deals with additional responsibility
and actions against. The following offences are described by the Convention: unlawful
access, unlawful interception, data disturbance, system disturbance, neglect of devices,
computer-related forgery, computer-related scams, violations relevant to child porn and
violations relevant to trademark and neighboring rights.
125. Section 2 of Chapter II (procedural law issues) – the opportunity of which goes
beyond the offences described in chapter 1 in that it relates to any offence dedicated by
means of a computer or the proof of which is in electronic form – decides first the common
circumstances and shields, appropriate to all step-by-step abilities in this chapter. It then sets
out the following step-by-step powers: expedited preservation of stored data; expedited
preservation and partial disclosure of traffic data; production order; search and seizure of
computer data; real-time collection of traffic data; interception of content data. Chapter II
finishes with the legislation circumstances
126. Chapter III contains the conditions concerning conventional and cyber crime-related
common support as well as extradition guidelines. It protects conventional common support
in two situations: where no legal base (treaty, shared regulation, etc.) prevails between events
– in which situation its conditions implement – and where such a base prevails – in which
situation the current agreements also implement to support under this Convention. Computer-
or computer-related criminal activity particular support relates to both circumstances and
protects, subject to extra-conditions, the same range of step-by-step abilities as described in
Chapter II. In addition, chapter III contains a supply on a particular type of trans-border
access to saved data which does not require common support (with approval or where openly
available) and provides for the setting up of a 24/7 network for guaranteeing quick support
among the Parties. Finally, Chapter IV contains the final clauses, which – with certain
exceptions – repeat the standard provisions in Council of Europe treaties.
127. According to article 22 of Europe convention of Cyber-crime there are five different
jurisdiction theories have been applied altogether by courts and governments, all leading to
the ascribing of jurisdiction to one court and adversely affecting other courts’ jurisdiction.
42
RESTRICTED

RESTRICTED
128. Territoriality theory :
The theory that jurisdiction is determined by the place where the offence is committed,
in whole or in part (“territoriality theory”), derives from the Westphalian model of
sovereignty, which is said to include three fundamental principles:
i. exclusive control over the nation’s territory,
ii. non-interference,
iii. equality between States
Although discussed and opposed,9 the model seems to have, at least, a general acceptance in
what concerns theses principles, even if the equality between the States is most of the times
only formal.
129. Nationality theory :
The “nationality theory” is also called “active personality theory” because it deals primarily
with the nationality of the person who committed the offence. Being widely recognized that a
country has almost unlimited control over its nationals said country is considered to have the
right to exercise jurisdiction over those individuals, wherever they are and whatever they do.
Wherever the offence is committed – at home or abroad – the offender probably has better
knowledge of the laws of his own State than of the laws of the other State. Also, an act can be
considered legal in the territory where it was committed whereas it can be considered a crime
in the person’s homeland. The case United States v. Galaxy Sports seems to be a good
example of the application of this theory.
43
RESTRICTED
128. Territoriality theory :
The theory that jurisdiction is determined by the place where the offence is committed,
in whole or in part (“territoriality theory”), derives from the Westphalian model of
sovereignty, which is said to include three fundamental principles:
i. exclusive control over the nation’s territory,
ii. non-interference,
iii. equality between States
Although discussed and opposed,9 the model seems to have, at least, a general acceptance in
what concerns theses principles, even if the equality between the States is most of the times
only formal.
129. Nationality theory :
The “nationality theory” is also called “active personality theory” because it deals primarily
with the nationality of the person who committed the offence. Being widely recognized that a
country has almost unlimited control over its nationals said country is considered to have the
right to exercise jurisdiction over those individuals, wherever they are and whatever they do.
Wherever the offence is committed – at home or abroad – the offender probably has better
knowledge of the laws of his own State than of the laws of the other State. Also, an act can be
considered legal in the territory where it was committed whereas it can be considered a crime
in the person’s homeland. The case United States v. Galaxy Sports seems to be a good
example of the application of this theory.
43
RESTRICTED
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESTRICTED
130. Passive personality theory :
While the “nationality theory” deals with the nationality of the offender, assigning
jurisdiction to his/her homeland courts, its opposite – the “passive personality theory” – is
concerned with the nationality of the victim. The reasons for ascertaining jurisdiction over an
offence are similar for both – the almost unlimited control over a country’s nationals – but are
now seen from the opposite point of view. Thus, when we follow this theory, the courts of the
State to which the victim belongs assume jurisdiction
131. Protective theory :
The “protective theory” (also called “security principle” and “injured forum theory”) is
probably the least used – if ever – of the theories that sanction jurisdiction. Dealing with the
national or international interest injured, this theory permits the assignment of jurisdiction to
the State that sees its interest – whether national or international – in jeopardy because of an
offensive action.
132. Universality theory:
Finally, the “universality theory” is based on the international character of the offence and,
contrary to the other theories, allows every State the claim of jurisdiction over offences, even
if those offences have no direct effect on the asserting State, 34 therefore demanding no
nexus between the State assuming jurisdiction and the offence itself.
44
RESTRICTED
130. Passive personality theory :
While the “nationality theory” deals with the nationality of the offender, assigning
jurisdiction to his/her homeland courts, its opposite – the “passive personality theory” – is
concerned with the nationality of the victim. The reasons for ascertaining jurisdiction over an
offence are similar for both – the almost unlimited control over a country’s nationals – but are
now seen from the opposite point of view. Thus, when we follow this theory, the courts of the
State to which the victim belongs assume jurisdiction
131. Protective theory :
The “protective theory” (also called “security principle” and “injured forum theory”) is
probably the least used – if ever – of the theories that sanction jurisdiction. Dealing with the
national or international interest injured, this theory permits the assignment of jurisdiction to
the State that sees its interest – whether national or international – in jeopardy because of an
offensive action.
132. Universality theory:
Finally, the “universality theory” is based on the international character of the offence and,
contrary to the other theories, allows every State the claim of jurisdiction over offences, even
if those offences have no direct effect on the asserting State, 34 therefore demanding no
nexus between the State assuming jurisdiction and the offence itself.
44
RESTRICTED

RESTRICTED
COMPARISON OF SRI LANKA,N LEGISLATION AND U.S.A
133. There are several legislations which passed by the Parliament recently regarding
computers and cyber-crime
i. Information and Communication Technology Act (No.27 of 2003)
ii. Evidence (Special Provisions) (Act No.14 of 1995)
iii. Intellectual Property Act (No. 36 of 2003 (Sections related to Copyright)
iv. Electronic Transactions Act (No. 19 of 2006)
v. Computer Crimes Act (No. 24 of 2007)
vi. Payment And Settlement Systems Act, (No. 28 of 2005)
vii. Payment Devices Frauds Act (No.30 of 2006)
134. In Sri Lanka we can see that there is no any act or legislation which related to cyber-
terrorism. But in Computer Crimes Act (No. 24 of 2007) it is mentioned some strong points,
but in the act it is not mentioned clearly and we have to interpret as we want.
135. If any person did any cyber terrorism activity the punishment will be Rs. 50 000 or
Rs. 100 000 or imprisonment.Considering about the USA situation it is very much important
to pay attention to the definition provided by the USA administrative authorities. According
to the USA Department of State Cyber terrorism is "Premeditated politically motivated
violence perpetrated against noncombatant targets by sub-national groups or clandestine
agents’’. Further more the USA National Infrastructure Protection Center define Cyber
Terrorism as the ‘’A criminal act perpetrated by the use of computers and
telecommunications capabilities, resulting in violence, destruction and/or disruption of
services to create fear by causing confusion and uncertainty within a given population, with
the goal of influencing a government or population to conform to particular political, social
or ideological agenda’’.
136. Further in detail considering about the legislations which are available, very much
important to highlight the Cyber Crime Bill passed by the senate. According to that Bill it
required to Required authorities to investigate and prosecute individuals for internet-related
45
RESTRICTED
COMPARISON OF SRI LANKA,N LEGISLATION AND U.S.A
133. There are several legislations which passed by the Parliament recently regarding
computers and cyber-crime
i. Information and Communication Technology Act (No.27 of 2003)
ii. Evidence (Special Provisions) (Act No.14 of 1995)
iii. Intellectual Property Act (No. 36 of 2003 (Sections related to Copyright)
iv. Electronic Transactions Act (No. 19 of 2006)
v. Computer Crimes Act (No. 24 of 2007)
vi. Payment And Settlement Systems Act, (No. 28 of 2005)
vii. Payment Devices Frauds Act (No.30 of 2006)
134. In Sri Lanka we can see that there is no any act or legislation which related to cyber-
terrorism. But in Computer Crimes Act (No. 24 of 2007) it is mentioned some strong points,
but in the act it is not mentioned clearly and we have to interpret as we want.
135. If any person did any cyber terrorism activity the punishment will be Rs. 50 000 or
Rs. 100 000 or imprisonment.Considering about the USA situation it is very much important
to pay attention to the definition provided by the USA administrative authorities. According
to the USA Department of State Cyber terrorism is "Premeditated politically motivated
violence perpetrated against noncombatant targets by sub-national groups or clandestine
agents’’. Further more the USA National Infrastructure Protection Center define Cyber
Terrorism as the ‘’A criminal act perpetrated by the use of computers and
telecommunications capabilities, resulting in violence, destruction and/or disruption of
services to create fear by causing confusion and uncertainty within a given population, with
the goal of influencing a government or population to conform to particular political, social
or ideological agenda’’.
136. Further in detail considering about the legislations which are available, very much
important to highlight the Cyber Crime Bill passed by the senate. According to that Bill it
required to Required authorities to investigate and prosecute individuals for internet-related
45
RESTRICTED

RESTRICTED
crimes such as fraud, hacking and cyber sex. And also White House draft this Bill and it
would expand the US Penal Code Title 18, Chapter 47, Section 1030, on Fraud and related
activity in
137. connection with computers. Also the Bill have proposals for cybercrime, including a
series of criminal offences for cyber attacks and confidentiality abuses. The Bill have also
details on critical information security.And the important issue is highlighted from the section
06 of the Cyber Attacks Act.
138. As a new concept the Pentagon has concluded that computer sabotage coming from
another country can constitute an act of war. And also this is new issue rather compare with
other countries. By using this method USA has undergone several successful missions.
139. Apart from that there is a separate computer crime and intellectual property section
function under authority of United States Department of Justice. Implementing the
Department's national strategies in combating computer and intellectual property crimes
worldwide is the responsibility of this section.This section has many roles.It
140. prevents, investigates, and prosecutes computer crimes by working with other
government agencies, the private sector, academic institutions, and foreign counterparts.
141. And also Intellectual property has become a growing concern with cyber law because
of how easy it has become to copy certain media and distribute that media. The intellectual
property that cyber law tries to protect for the most part is music. Copyright infringement is
the violation of another person’s copyright of a piece of intellectual property. It is much
easier now to share music files with other people on the internet illegally. There are sites that
have established a fee to legally purchase music over the internet now. In USA Cyber law can
be enforced by courts and police officers across the country. If a person violates cyber law
they can be subjected to fines and maybe even a jail term. Many
142. police officers will pose as young teenagers or young children on the internet to help
track and arrest child predators or pedophiles. Cyber law is also monitored and enforced by
the United States Federal Bureau of Investigation.
46
RESTRICTED
crimes such as fraud, hacking and cyber sex. And also White House draft this Bill and it
would expand the US Penal Code Title 18, Chapter 47, Section 1030, on Fraud and related
activity in
137. connection with computers. Also the Bill have proposals for cybercrime, including a
series of criminal offences for cyber attacks and confidentiality abuses. The Bill have also
details on critical information security.And the important issue is highlighted from the section
06 of the Cyber Attacks Act.
138. As a new concept the Pentagon has concluded that computer sabotage coming from
another country can constitute an act of war. And also this is new issue rather compare with
other countries. By using this method USA has undergone several successful missions.
139. Apart from that there is a separate computer crime and intellectual property section
function under authority of United States Department of Justice. Implementing the
Department's national strategies in combating computer and intellectual property crimes
worldwide is the responsibility of this section.This section has many roles.It
140. prevents, investigates, and prosecutes computer crimes by working with other
government agencies, the private sector, academic institutions, and foreign counterparts.
141. And also Intellectual property has become a growing concern with cyber law because
of how easy it has become to copy certain media and distribute that media. The intellectual
property that cyber law tries to protect for the most part is music. Copyright infringement is
the violation of another person’s copyright of a piece of intellectual property. It is much
easier now to share music files with other people on the internet illegally. There are sites that
have established a fee to legally purchase music over the internet now. In USA Cyber law can
be enforced by courts and police officers across the country. If a person violates cyber law
they can be subjected to fines and maybe even a jail term. Many
142. police officers will pose as young teenagers or young children on the internet to help
track and arrest child predators or pedophiles. Cyber law is also monitored and enforced by
the United States Federal Bureau of Investigation.
46
RESTRICTED
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

RESTRICTED
143. A person using the internet in the United States could be subject to the cyber laws not
only in the United States but also in other countries. This all depends on what the person in
the United States is doing on the internet in relation to other countries. This is known as
jurisdiction and entails the following:
i. The laws of the state/nation in which the user resides
ii. The laws of the state/nation that apply where the server hosting the transaction
is located
iii. The laws of the state/nation which apply to the person or business with whom
the transaction takes place.
144. Under the measure, any person found guilty of the acts in A and B shall be punished
with imprisonment of prison mayor (imprisonment from six to 12 years) or a fine of at least
P200,000 or an amount depending on the damage caused or both depending on the court.
145. On the other hand, any person found guilty of cyber-squatting shall be punished with
imprisonment of prison mayor or a fine of not more than P500,000 (or both); any person
found guilty of unsolicited commercial communication with arrest mayor (imprisonment
from one month to six months) or a fine of at least P50,000 but not more than P250,000 (or
both); and any person found guilty of cybersex with imprisonment of prison mayor or a fine
of at least P200,000 but not more than P1 million (or both).Meanwhile, any person found
guilty of child pornography shall be punished according to Republic Act 9775 or the Anti-
Child Pornography Act of 2009.
47
RESTRICTED
143. A person using the internet in the United States could be subject to the cyber laws not
only in the United States but also in other countries. This all depends on what the person in
the United States is doing on the internet in relation to other countries. This is known as
jurisdiction and entails the following:
i. The laws of the state/nation in which the user resides
ii. The laws of the state/nation that apply where the server hosting the transaction
is located
iii. The laws of the state/nation which apply to the person or business with whom
the transaction takes place.
144. Under the measure, any person found guilty of the acts in A and B shall be punished
with imprisonment of prison mayor (imprisonment from six to 12 years) or a fine of at least
P200,000 or an amount depending on the damage caused or both depending on the court.
145. On the other hand, any person found guilty of cyber-squatting shall be punished with
imprisonment of prison mayor or a fine of not more than P500,000 (or both); any person
found guilty of unsolicited commercial communication with arrest mayor (imprisonment
from one month to six months) or a fine of at least P50,000 but not more than P250,000 (or
both); and any person found guilty of cybersex with imprisonment of prison mayor or a fine
of at least P200,000 but not more than P1 million (or both).Meanwhile, any person found
guilty of child pornography shall be punished according to Republic Act 9775 or the Anti-
Child Pornography Act of 2009.
47
RESTRICTED

RESTRICTED
CHAPTER SIX
RECCOMENDATION
146. Cyber crimes in Sri Lanka has made a major topic due to various reasons, most
effecting reason is the lack of implementation of already enacted policies and regulations
which is being put up to regulate the illegal activities in cyberspace and the mitigate the
misconducts but in Sri Lanka most of them are being ignored by the law enforcement
authorities and due to that criminals are acting without any consent.
147. The use of pirated copies of software is another reason to face with numerous kinds of
attacks. These pirated copies creates an easy access to the criminals to extract the user’s
personal data and it also let the computer to be a zombie without the knowledge of the user
and these devices with illegal software creates loopholes and vulnerabilities in the networks
which can ultimately lead to catastrophic destructions. As Sri Lanka’s majority does not pay
keen attention to use legal software as they are expensive the government with working in
hand with software producers should take an initiation to introduce low price editions of
software or the government should encourage in the use of open source software.
148. When an incident is being reported to SLCERT they conduct digital forensics relating
to the crime and they should handover the evidence to the Computer Crime Division of the
Police to proceed with the arrests and legal actions. This transfer of authority has created an
easy getaway to the criminals as it is a lengthy process. Appointing an liaison officer to the
Computer Crime Division would enable a smooth functioning among the two parties.
149. IT related education should also cover the area of correct use of internet and should
educate on individual security and privacy in-order to make the user more secure. This
should happen especially to the government sector employees as the expansion of the
government network, the network is prone to attacks very often and any person with careless
usage would eventually build vulnerabilities which would make an easy access to any
criminal.
150. Present public awareness programmes are not enough to educate the general
population as most of them are being conducted targeting on organizations. SLCERT is the
national face of cyber security but their contribution to the awareness programmes is very
48
RESTRICTED
CHAPTER SIX
RECCOMENDATION
146. Cyber crimes in Sri Lanka has made a major topic due to various reasons, most
effecting reason is the lack of implementation of already enacted policies and regulations
which is being put up to regulate the illegal activities in cyberspace and the mitigate the
misconducts but in Sri Lanka most of them are being ignored by the law enforcement
authorities and due to that criminals are acting without any consent.
147. The use of pirated copies of software is another reason to face with numerous kinds of
attacks. These pirated copies creates an easy access to the criminals to extract the user’s
personal data and it also let the computer to be a zombie without the knowledge of the user
and these devices with illegal software creates loopholes and vulnerabilities in the networks
which can ultimately lead to catastrophic destructions. As Sri Lanka’s majority does not pay
keen attention to use legal software as they are expensive the government with working in
hand with software producers should take an initiation to introduce low price editions of
software or the government should encourage in the use of open source software.
148. When an incident is being reported to SLCERT they conduct digital forensics relating
to the crime and they should handover the evidence to the Computer Crime Division of the
Police to proceed with the arrests and legal actions. This transfer of authority has created an
easy getaway to the criminals as it is a lengthy process. Appointing an liaison officer to the
Computer Crime Division would enable a smooth functioning among the two parties.
149. IT related education should also cover the area of correct use of internet and should
educate on individual security and privacy in-order to make the user more secure. This
should happen especially to the government sector employees as the expansion of the
government network, the network is prone to attacks very often and any person with careless
usage would eventually build vulnerabilities which would make an easy access to any
criminal.
150. Present public awareness programmes are not enough to educate the general
population as most of them are being conducted targeting on organizations. SLCERT is the
national face of cyber security but their contribution to the awareness programmes is very
48
RESTRICTED

RESTRICTED
low. The awareness programmes should be attractive to the general public in a manner
which would
educate the public without any effort. They should be in a sense of a brand promotion
campaign and Television advertisements should be telecasted at peak hours of usage.
151. The liability of the Government to make sure that nationwide systems are protected
and have not been occupied. To accomplish this, the countries internet actions need to be
harmonized both on an institutional stage and region and provincial stages and this has to be
led by the top organization for internet protection in Sri Lanka CERT.
152. Legal systems and the legislature to pay attention to areas in which it has particular
impact, such as defending crucial facilities and managing legal framework, as well as
managing and working with business customer protection comfort.
153. The nationwide protection plan should be prolonged to include the internet protection
plan that protects the duration and depth of the nation in order to take the concept to the
people that internet protection is suitable with individual privileges and comfort and
independence of conversation.
154. The nationwide protection and protection plan to play a larger part in the internet
protection in Sri Lanka. This plan must also ensure that army functions and similar tasks are
secured against internet problems. Cyber protection should be made an effective ability of
the nation as a whole. It is essential that Sri Lanka uses its highly effective neighbors to
organize actions between these countries.
155. it is essential for authorities to work with the privet sector because a majority of the
facilities is in personal hands. All developed countries have determined this and work with
the privet sector and essential is that the privet sector in come back should reciprocate
similarly.
49
RESTRICTED
low. The awareness programmes should be attractive to the general public in a manner
which would
educate the public without any effort. They should be in a sense of a brand promotion
campaign and Television advertisements should be telecasted at peak hours of usage.
151. The liability of the Government to make sure that nationwide systems are protected
and have not been occupied. To accomplish this, the countries internet actions need to be
harmonized both on an institutional stage and region and provincial stages and this has to be
led by the top organization for internet protection in Sri Lanka CERT.
152. Legal systems and the legislature to pay attention to areas in which it has particular
impact, such as defending crucial facilities and managing legal framework, as well as
managing and working with business customer protection comfort.
153. The nationwide protection plan should be prolonged to include the internet protection
plan that protects the duration and depth of the nation in order to take the concept to the
people that internet protection is suitable with individual privileges and comfort and
independence of conversation.
154. The nationwide protection and protection plan to play a larger part in the internet
protection in Sri Lanka. This plan must also ensure that army functions and similar tasks are
secured against internet problems. Cyber protection should be made an effective ability of
the nation as a whole. It is essential that Sri Lanka uses its highly effective neighbors to
organize actions between these countries.
155. it is essential for authorities to work with the privet sector because a majority of the
facilities is in personal hands. All developed countries have determined this and work with
the privet sector and essential is that the privet sector in come back should reciprocate
similarly.
49
RESTRICTED
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESTRICTED
CHAPTER SEVEN
CONCLUSION
156. Even if a country is not greatly affected by cyber terrorism, the country should still
create solutions regarding this issue, because eventually it will affect everyone. Look into
the countries past actions and see if it has done anything to combat this issue. If our country
has, use this to base our solutions off but do not have our past actions as our only solution.
Education is a solution, and is often overused. It is not suggested to use this as a solution but
if we plan on using this solution, we need to know how we are going to educate people,
who’s going to pay for it, how we are going to educate on an International basis, and where
all the resources are going to come from. We have to be very precise if we want to use
education as a solution.
157. Security programs have also been used in the past to combat cyber terrorism. These
programs have been used effectively but are aware that they do not protect against every
threat of cyber terrorism. New threats are created every day that programs can be unaware
of. Mainly our solutions need to be in-depth and comprehensive. Don’t just find solutions
that would work in an ideal world, but find some that could be used in today’s world. Know
how our solutions are going to be implemented and what resources we will use to implement
them. Be thorough in our search for solutions.
158. Cyber-terrorism is a complex issue that is vital for information security specialists and
to some extent the society to recognize. One must be conscious of all of its characteristics in
order to better evaluate how and where the "terrorists" are likely to attack our approach.
What makes this subject
159. significant is that a cyber-terrorist attack is comparatively very easy and economical
to instigate. For that reason, it can from anywhere in the world, at any time, and, more
importantly, the stakes of this cat and mouse game are can be quite high. In view of the fact
that it is only a matter of time before a system is attacked, one must stay alert and share the
knowledge obtained so that we can help protect ourselves at a personal, business, and
national level.
50
RESTRICTED
CHAPTER SEVEN
CONCLUSION
156. Even if a country is not greatly affected by cyber terrorism, the country should still
create solutions regarding this issue, because eventually it will affect everyone. Look into
the countries past actions and see if it has done anything to combat this issue. If our country
has, use this to base our solutions off but do not have our past actions as our only solution.
Education is a solution, and is often overused. It is not suggested to use this as a solution but
if we plan on using this solution, we need to know how we are going to educate people,
who’s going to pay for it, how we are going to educate on an International basis, and where
all the resources are going to come from. We have to be very precise if we want to use
education as a solution.
157. Security programs have also been used in the past to combat cyber terrorism. These
programs have been used effectively but are aware that they do not protect against every
threat of cyber terrorism. New threats are created every day that programs can be unaware
of. Mainly our solutions need to be in-depth and comprehensive. Don’t just find solutions
that would work in an ideal world, but find some that could be used in today’s world. Know
how our solutions are going to be implemented and what resources we will use to implement
them. Be thorough in our search for solutions.
158. Cyber-terrorism is a complex issue that is vital for information security specialists and
to some extent the society to recognize. One must be conscious of all of its characteristics in
order to better evaluate how and where the "terrorists" are likely to attack our approach.
What makes this subject
159. significant is that a cyber-terrorist attack is comparatively very easy and economical
to instigate. For that reason, it can from anywhere in the world, at any time, and, more
importantly, the stakes of this cat and mouse game are can be quite high. In view of the fact
that it is only a matter of time before a system is attacked, one must stay alert and share the
knowledge obtained so that we can help protect ourselves at a personal, business, and
national level.
50
RESTRICTED

RESTRICTED
160. The problem of cyber terrorism is multilateral having varied facets and dimensions.
Its solution requires rigorous application of energy and resources. It must be noted that law
is always seven steps behind the technology. This is so because we have a tendency to make
laws when the problem reaches at its zenith. We do not appreciate the need of the hour till
the problem takes a precarious dimension. At that stage it is always very difficult, if not
impossible, to deal with that problem. This is more so in case of offences and violations
involving information technology.
161. One of the arguments, which is always advanced to justify this stand of non-
enactment is that “the measures suggested are not adequate to deal with the problem”. It
must be appreciated that “something is better than nothing”. The ultimate solution to any
problem is not to enact a plethora of statutes but their rigorous and dedicated enforcement.
The courts may apply the existing laws in a progressive, updating and purposive manner. It
must be appreciated that it is not the “enactment” of a law but the desire, will and efforts to
accept and enforce it in its true letter and spirit, which can confer the most strongest, secure
and safest protection for any purpose. The enforcement of these rights requires a “qualitative
effort” and not a “quantitative effort”. Thus, till a law dealing expressly with cyber terrorism
is enacted, we must not feel shy and hesitant to use the existing provisions.
162. The technology evolvement in Sri Lanka is impressive and most of the latest
technologies are introduced to Sri Lanka sometimes even before other countries in the
region. The corporate sector in Sri Lanka has also incorporated IT in to their operations.
Today in most of the organizations/offices both the government and private sector, the
operation heavily relies on the computers and IT. Recent rumours about “a computer
manipulation to change the election results” clearly elaborate the gravity of a “DoS” attack if
occurred on Sri Lanka. The Examination Department of Sri Lanka uses its website to
publish the results of all the key examinations held in Sri Lanka such as the GCE (O/L) and
GCE (A/L). Just imagine what will happen if there is a cyber-attack to that server or the
website.
163. During the Eelam War what if there was a cyber-attack to our defence websites? If
you can recollect the propaganda campaign carried out by the pro LTTE groups in cyber
51
RESTRICTED
160. The problem of cyber terrorism is multilateral having varied facets and dimensions.
Its solution requires rigorous application of energy and resources. It must be noted that law
is always seven steps behind the technology. This is so because we have a tendency to make
laws when the problem reaches at its zenith. We do not appreciate the need of the hour till
the problem takes a precarious dimension. At that stage it is always very difficult, if not
impossible, to deal with that problem. This is more so in case of offences and violations
involving information technology.
161. One of the arguments, which is always advanced to justify this stand of non-
enactment is that “the measures suggested are not adequate to deal with the problem”. It
must be appreciated that “something is better than nothing”. The ultimate solution to any
problem is not to enact a plethora of statutes but their rigorous and dedicated enforcement.
The courts may apply the existing laws in a progressive, updating and purposive manner. It
must be appreciated that it is not the “enactment” of a law but the desire, will and efforts to
accept and enforce it in its true letter and spirit, which can confer the most strongest, secure
and safest protection for any purpose. The enforcement of these rights requires a “qualitative
effort” and not a “quantitative effort”. Thus, till a law dealing expressly with cyber terrorism
is enacted, we must not feel shy and hesitant to use the existing provisions.
162. The technology evolvement in Sri Lanka is impressive and most of the latest
technologies are introduced to Sri Lanka sometimes even before other countries in the
region. The corporate sector in Sri Lanka has also incorporated IT in to their operations.
Today in most of the organizations/offices both the government and private sector, the
operation heavily relies on the computers and IT. Recent rumours about “a computer
manipulation to change the election results” clearly elaborate the gravity of a “DoS” attack if
occurred on Sri Lanka. The Examination Department of Sri Lanka uses its website to
publish the results of all the key examinations held in Sri Lanka such as the GCE (O/L) and
GCE (A/L). Just imagine what will happen if there is a cyber-attack to that server or the
website.
163. During the Eelam War what if there was a cyber-attack to our defence websites? If
you can recollect the propaganda campaign carried out by the pro LTTE groups in cyber
51
RESTRICTED

RESTRICTED
space with regards to the false reports carried out by the Channel-4 News in UK, it is clearly
visible how effective cyberspace can be used as a tool for promoting cyber terrorism and
how dangerous and disastrous it can be if used or manipulated by wrong hands. But our
cyber security systems were strong enough and were well secured.
164. Our computer security experts are well trained and recently Sri Lanka played a key
role in the regional cybercrime fighting drill conducted by the Asia Pacific Computer
Emergency Response Team (APCERT) which involved 14 countries in the region. Sri
Lankan Computer Emergency Response Team (SLCERT) is a body composed of a group of
computer experts which handles computer security incidents in Sri Lanka. Up to date there
were no major incidents with regards to the cyber-attacks in Sri Lanka even though there
were few computer frauds reported. Even though this is the situation we need to get ready
for cyber terrorism and increase our capacity of technology to fight this new crime in this
21st century.
52
RESTRICTED
space with regards to the false reports carried out by the Channel-4 News in UK, it is clearly
visible how effective cyberspace can be used as a tool for promoting cyber terrorism and
how dangerous and disastrous it can be if used or manipulated by wrong hands. But our
cyber security systems were strong enough and were well secured.
164. Our computer security experts are well trained and recently Sri Lanka played a key
role in the regional cybercrime fighting drill conducted by the Asia Pacific Computer
Emergency Response Team (APCERT) which involved 14 countries in the region. Sri
Lankan Computer Emergency Response Team (SLCERT) is a body composed of a group of
computer experts which handles computer security incidents in Sri Lanka. Up to date there
were no major incidents with regards to the cyber-attacks in Sri Lanka even though there
were few computer frauds reported. Even though this is the situation we need to get ready
for cyber terrorism and increase our capacity of technology to fight this new crime in this
21st century.
52
RESTRICTED
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
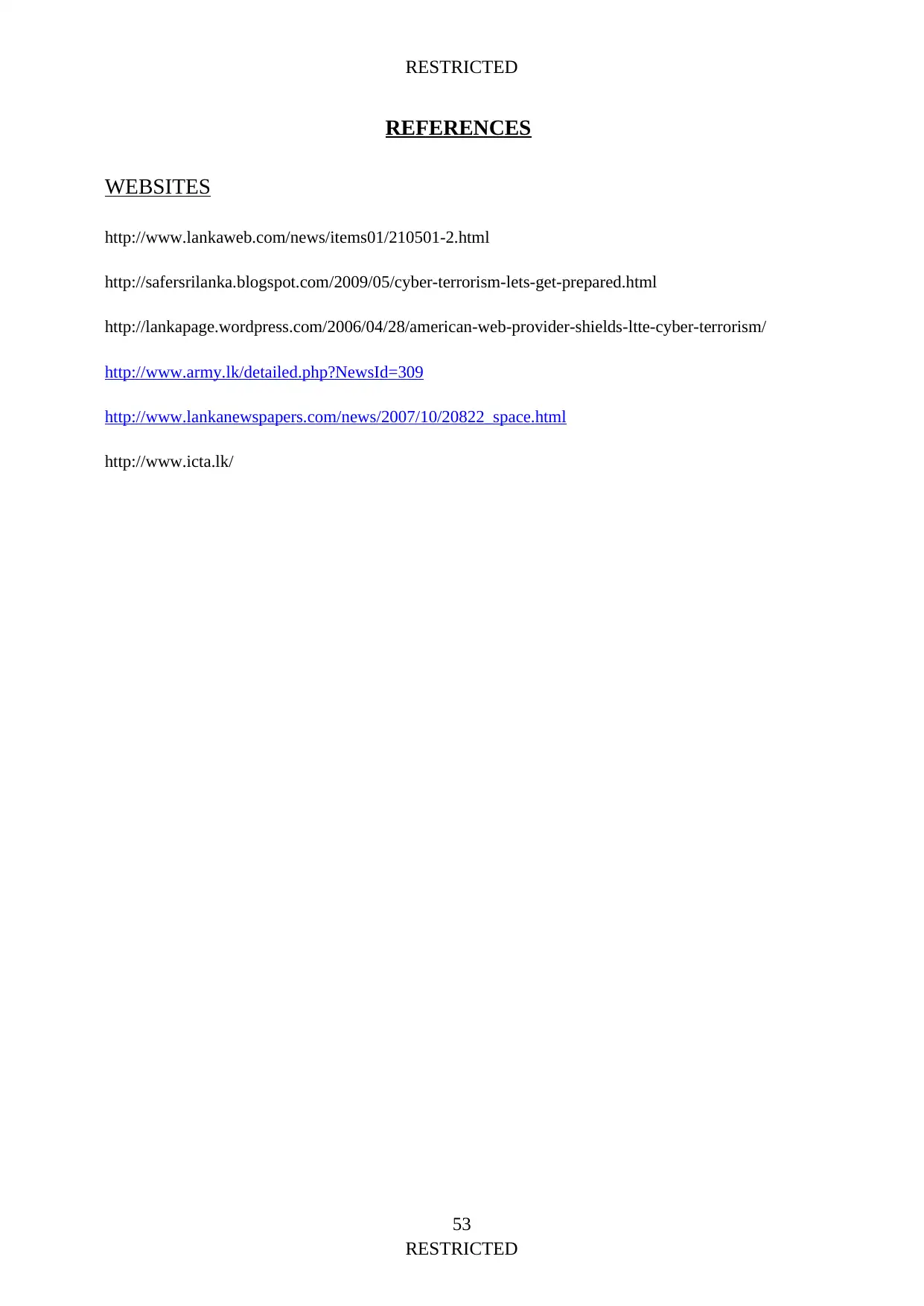
RESTRICTED
REFERENCES
WEBSITES
http://www.lankaweb.com/news/items01/210501-2.html
http://safersrilanka.blogspot.com/2009/05/cyber-terrorism-lets-get-prepared.html
http://lankapage.wordpress.com/2006/04/28/american-web-provider-shields-ltte-cyber-terrorism/
http://www.army.lk/detailed.php?NewsId=309
http://www.lankanewspapers.com/news/2007/10/20822_space.html
http://www.icta.lk/
53
RESTRICTED
REFERENCES
WEBSITES
http://www.lankaweb.com/news/items01/210501-2.html
http://safersrilanka.blogspot.com/2009/05/cyber-terrorism-lets-get-prepared.html
http://lankapage.wordpress.com/2006/04/28/american-web-provider-shields-ltte-cyber-terrorism/
http://www.army.lk/detailed.php?NewsId=309
http://www.lankanewspapers.com/news/2007/10/20822_space.html
http://www.icta.lk/
53
RESTRICTED
1 out of 53
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.