Cybercrime: Trends, Laws, and Law Enforcement Initiatives Report
VerifiedAdded on 2022/11/09
|8
|1753
|341
Report
AI Summary
This report analyzes the current trends in cybercrime, focusing on scams like malware, credit card fraud, data breaches, compromised passwords, and unauthorized access to emails and social media. It explores the impact of these crimes on businesses and individuals, highlighting the importance of cybersecurity. The report delves into specific US laws applicable to cybercrime, including U.S. Code §§ 2701, 2511, 1030, and 1037, detailing their provisions and penalties. It also examines the profiles of cybercriminals, law enforcement initiatives to combat cybercrime, and the range of penalties imposed for these offenses, including fines and imprisonment. The report concludes by emphasizing the need for robust security management, education, and training to mitigate cybercrime risks and protect data and privacy.
Running Head: Cybercrime 0
Cybercrime
Paper
Student name
Cybercrime
Paper
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cybercrime 1
Table of Contents
Introduction.................................................................................................................................................2
Trends in cybercrime...................................................................................................................................4
Conclusion...................................................................................................................................................5
References...................................................................................................................................................6
Table of Contents
Introduction.................................................................................................................................................2
Trends in cybercrime...................................................................................................................................4
Conclusion...................................................................................................................................................5
References...................................................................................................................................................6

Cybercrime 2
Introduction
There are some new trends in cybercrime in the US, which are phishing, social engineering, and
others on the data and information, which has collected from the Internet-of-things (IoT) devices. In
addition, there are many huge impacts of these trends on the business and reparation of an
organization. Cybercrime is a crime in which privacy and security have broken by an attacker for their
personal benefits most of the time.
This paper will explain about the types of frauds, which are associated with cybercrime. It will
discuss about the specific law, which applies to the crime. This paper will include profile for
cybercriminal and law enforcement initiatives to combat cybercrime. It will provide various penalties for
committing cybercrimes.
There are various scams associated with cybercrime. In the case of business, many organization
uses unofficial ways to hack the data of particular organization using malware, malfunctions, and many
other methods. There are main five types of scams, which must avoided by firms, which areas:
1. Malware: it can damage data and other things in a PC, tablet, and smartphone. Therefore,
internet security suite must install on the devices to secure them from cybercrimes
2. Fraud in a credit card: hacker can hack the personal information from the users using
phishing and other methods. Therefore, monitoring services must use by the credit
cardholders.
3. Data breach: it is a type of fraud that is associated with cybercrime. In this scam, hacker can
hack whole databases using malfunctions and DDoS attacks to breach the data and
information from databases.
4. Compromised passwords: it is a process for the security of the system in which hackers used
different methods to theft the passwords. There must be secured and strong passwords for
access to the system.
5. Unauthorized email and social media access: most of the data theft from the social media
sites and email of users. Therefore, it is necessary to use a strong password for securing all
the things.
Introduction
There are some new trends in cybercrime in the US, which are phishing, social engineering, and
others on the data and information, which has collected from the Internet-of-things (IoT) devices. In
addition, there are many huge impacts of these trends on the business and reparation of an
organization. Cybercrime is a crime in which privacy and security have broken by an attacker for their
personal benefits most of the time.
This paper will explain about the types of frauds, which are associated with cybercrime. It will
discuss about the specific law, which applies to the crime. This paper will include profile for
cybercriminal and law enforcement initiatives to combat cybercrime. It will provide various penalties for
committing cybercrimes.
There are various scams associated with cybercrime. In the case of business, many organization
uses unofficial ways to hack the data of particular organization using malware, malfunctions, and many
other methods. There are main five types of scams, which must avoided by firms, which areas:
1. Malware: it can damage data and other things in a PC, tablet, and smartphone. Therefore,
internet security suite must install on the devices to secure them from cybercrimes
2. Fraud in a credit card: hacker can hack the personal information from the users using
phishing and other methods. Therefore, monitoring services must use by the credit
cardholders.
3. Data breach: it is a type of fraud that is associated with cybercrime. In this scam, hacker can
hack whole databases using malfunctions and DDoS attacks to breach the data and
information from databases.
4. Compromised passwords: it is a process for the security of the system in which hackers used
different methods to theft the passwords. There must be secured and strong passwords for
access to the system.
5. Unauthorized email and social media access: most of the data theft from the social media
sites and email of users. Therefore, it is necessary to use a strong password for securing all
the things.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Cybercrime 3
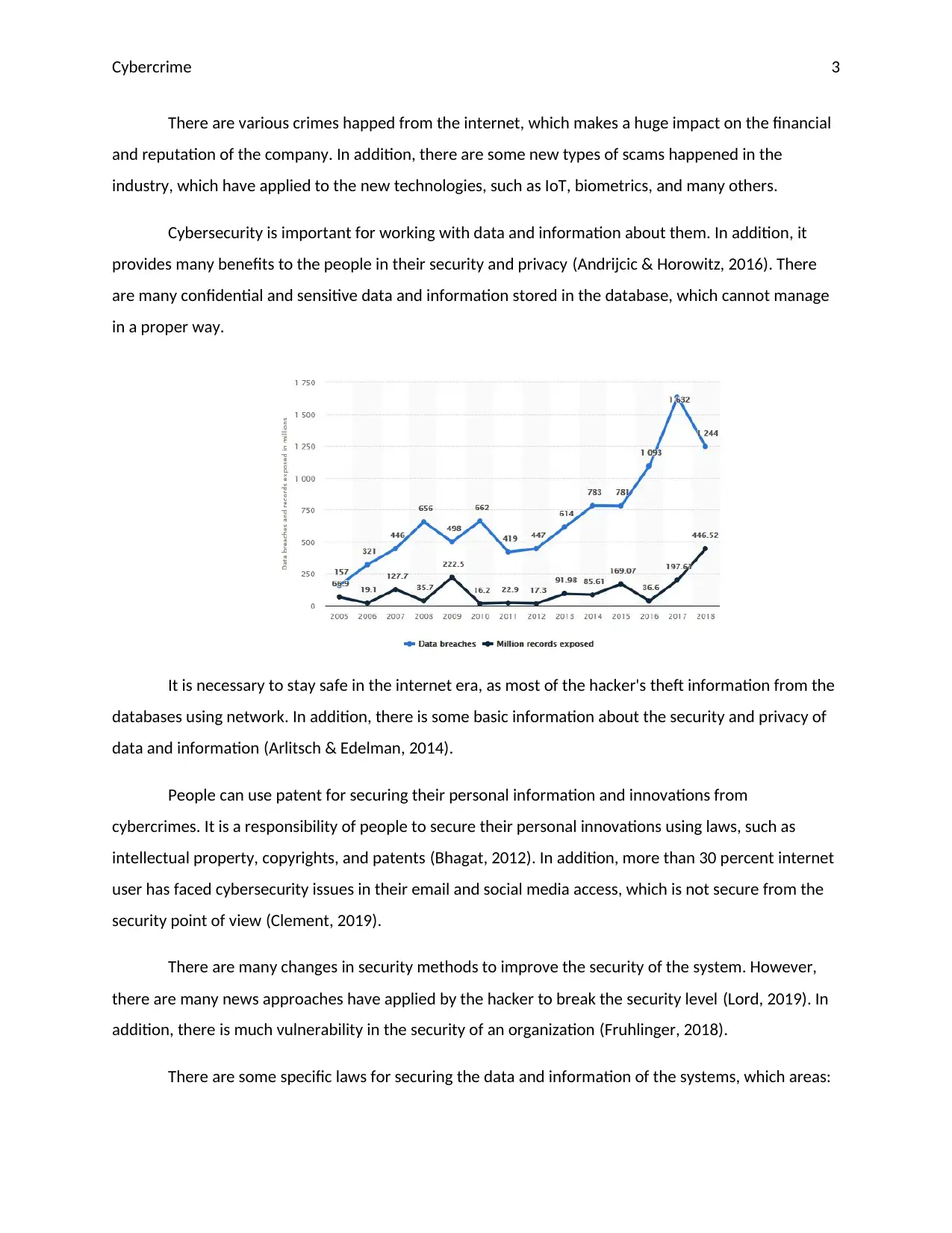
There are various crimes happed from the internet, which makes a huge impact on the financial
and reputation of the company. In addition, there are some new types of scams happened in the
industry, which have applied to the new technologies, such as IoT, biometrics, and many others.
Cybersecurity is important for working with data and information about them. In addition, it
provides many benefits to the people in their security and privacy (Andrijcic & Horowitz, 2016). There
are many confidential and sensitive data and information stored in the database, which cannot manage
in a proper way.
It is necessary to stay safe in the internet era, as most of the hacker's theft information from the
databases using network. In addition, there is some basic information about the security and privacy of
data and information (Arlitsch & Edelman, 2014).
People can use patent for securing their personal information and innovations from
cybercrimes. It is a responsibility of people to secure their personal innovations using laws, such as
intellectual property, copyrights, and patents (Bhagat, 2012). In addition, more than 30 percent internet
user has faced cybersecurity issues in their email and social media access, which is not secure from the
security point of view (Clement, 2019).
There are many changes in security methods to improve the security of the system. However,
there are many news approaches have applied by the hacker to break the security level (Lord, 2019). In
addition, there is much vulnerability in the security of an organization (Fruhlinger, 2018).
There are some specific laws for securing the data and information of the systems, which areas:
There are various crimes happed from the internet, which makes a huge impact on the financial
and reputation of the company. In addition, there are some new types of scams happened in the
industry, which have applied to the new technologies, such as IoT, biometrics, and many others.
Cybersecurity is important for working with data and information about them. In addition, it
provides many benefits to the people in their security and privacy (Andrijcic & Horowitz, 2016). There
are many confidential and sensitive data and information stored in the database, which cannot manage
in a proper way.
It is necessary to stay safe in the internet era, as most of the hacker's theft information from the
databases using network. In addition, there is some basic information about the security and privacy of
data and information (Arlitsch & Edelman, 2014).
People can use patent for securing their personal information and innovations from
cybercrimes. It is a responsibility of people to secure their personal innovations using laws, such as
intellectual property, copyrights, and patents (Bhagat, 2012). In addition, more than 30 percent internet
user has faced cybersecurity issues in their email and social media access, which is not secure from the
security point of view (Clement, 2019).
There are many changes in security methods to improve the security of the system. However,
there are many news approaches have applied by the hacker to break the security level (Lord, 2019). In
addition, there is much vulnerability in the security of an organization (Fruhlinger, 2018).
There are some specific laws for securing the data and information of the systems, which areas:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cybercrime 4
U.S. Code § 2701 – Unlawful access to stored communications
There is some specific information about various things. In the case of communication, there is a
specific rule, which has applied in unlawful access to stored communications. Perpetrators who, with
none authorization, deliberately get right of entry to a facility that offers electronic conversation
offerings or get past the ordinary authorization process to access the facility just to gain, adjust, or save
(Leonhardt, 2018).
U.S. Code § 2511 – Interception and disclosure of wire, oral, or electronic communications
prohibited
This law protects wire, oral and electronic conversation interception of cybercriminals. In
addition, there are important factors of these laws for the cyber criminals. The government can punish
those cybercriminal for 5 years (Gravrock, 2019).
U.S. Code § 1030 – Fraud and related activity in connection with computers
the provision punishes people who get right of entry to a pc without authorization or in excess
of authorization specifically by means of obtaining non-public and touchy statistics from U.S.
government departments or companies’ computers. The government can punish the cryber crimincal
for online fraud for 25 years in the US (Lord, 2019).
U.S. Code § 1037 – Fraud and related activity in connection with electronic mail
It applies to all people worried in interstate or foreign commerce that accesses a secured
computer without authorization. There are huge impacts of email hacking on the people as well as
others. therefore, the government can penalize criminal based on their evidences. Perpetrators and
accessories to the crime will be punished with an exceptional and/or dispatched to prison for not
greater than 3 years as much as 5 years (Tripwire, 2017).
Trends in cybercrime
There are various types of cybercrimes, which depends on the particular area and its
consequences. In addition, there are some issues in the security of personal information at various
places on the internet, such as email, social sites, and many others (Rivner, 2018).
U.S. Code § 2701 – Unlawful access to stored communications
There is some specific information about various things. In the case of communication, there is a
specific rule, which has applied in unlawful access to stored communications. Perpetrators who, with
none authorization, deliberately get right of entry to a facility that offers electronic conversation
offerings or get past the ordinary authorization process to access the facility just to gain, adjust, or save
(Leonhardt, 2018).
U.S. Code § 2511 – Interception and disclosure of wire, oral, or electronic communications
prohibited
This law protects wire, oral and electronic conversation interception of cybercriminals. In
addition, there are important factors of these laws for the cyber criminals. The government can punish
those cybercriminal for 5 years (Gravrock, 2019).
U.S. Code § 1030 – Fraud and related activity in connection with computers
the provision punishes people who get right of entry to a pc without authorization or in excess
of authorization specifically by means of obtaining non-public and touchy statistics from U.S.
government departments or companies’ computers. The government can punish the cryber crimincal
for online fraud for 25 years in the US (Lord, 2019).
U.S. Code § 1037 – Fraud and related activity in connection with electronic mail
It applies to all people worried in interstate or foreign commerce that accesses a secured
computer without authorization. There are huge impacts of email hacking on the people as well as
others. therefore, the government can penalize criminal based on their evidences. Perpetrators and
accessories to the crime will be punished with an exceptional and/or dispatched to prison for not
greater than 3 years as much as 5 years (Tripwire, 2017).
Trends in cybercrime
There are various types of cybercrimes, which depends on the particular area and its
consequences. In addition, there are some issues in the security of personal information at various
places on the internet, such as email, social sites, and many others (Rivner, 2018).
Cybercrime 5
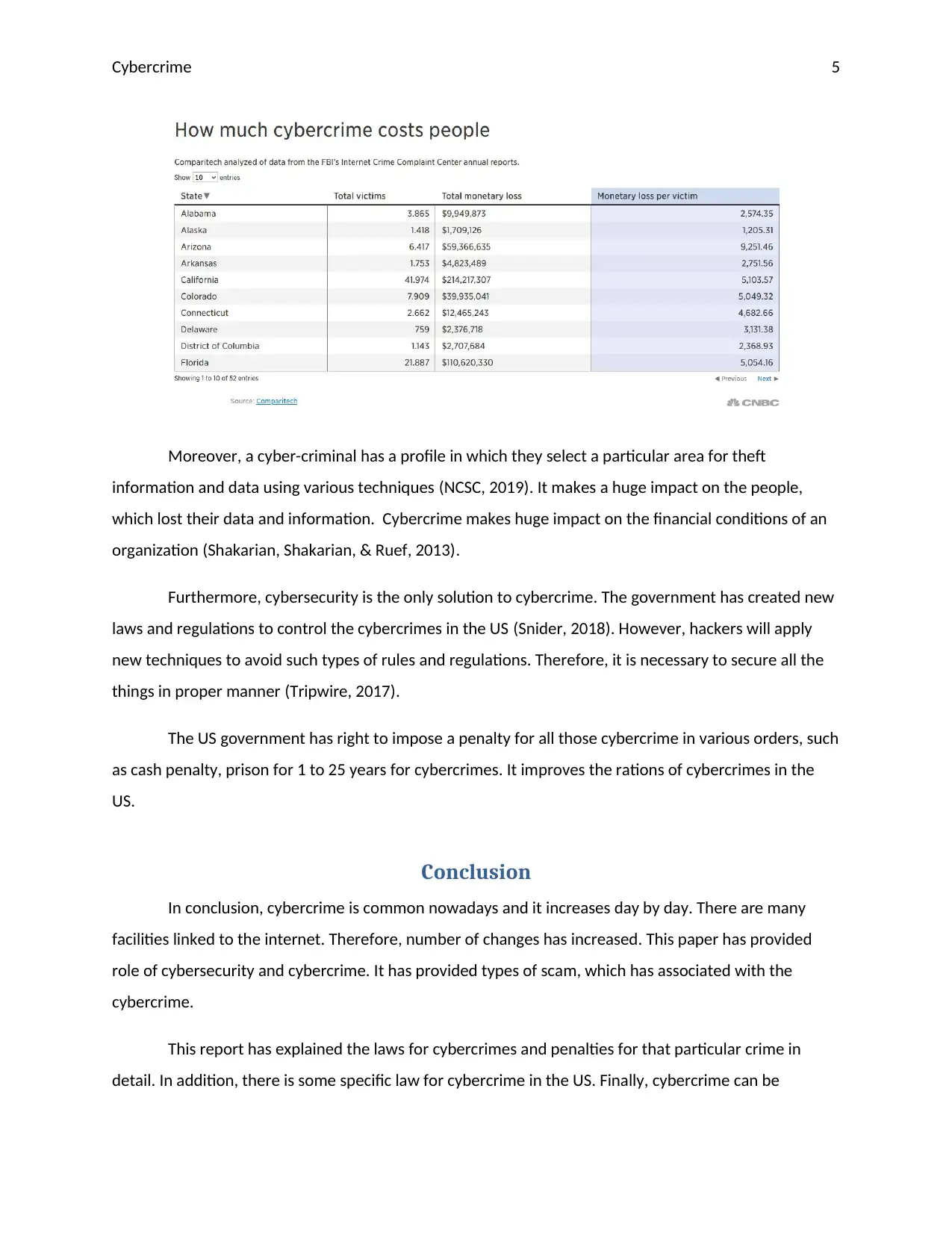
Moreover, a cyber-criminal has a profile in which they select a particular area for theft
information and data using various techniques (NCSC, 2019). It makes a huge impact on the people,
which lost their data and information. Cybercrime makes huge impact on the financial conditions of an
organization (Shakarian, Shakarian, & Ruef, 2013).
Furthermore, cybersecurity is the only solution to cybercrime. The government has created new
laws and regulations to control the cybercrimes in the US (Snider, 2018). However, hackers will apply
new techniques to avoid such types of rules and regulations. Therefore, it is necessary to secure all the
things in proper manner (Tripwire, 2017).
The US government has right to impose a penalty for all those cybercrime in various orders, such
as cash penalty, prison for 1 to 25 years for cybercrimes. It improves the rations of cybercrimes in the
US.
Conclusion
In conclusion, cybercrime is common nowadays and it increases day by day. There are many
facilities linked to the internet. Therefore, number of changes has increased. This paper has provided
role of cybersecurity and cybercrime. It has provided types of scam, which has associated with the
cybercrime.
This report has explained the laws for cybercrimes and penalties for that particular crime in
detail. In addition, there is some specific law for cybercrime in the US. Finally, cybercrime can be
Moreover, a cyber-criminal has a profile in which they select a particular area for theft
information and data using various techniques (NCSC, 2019). It makes a huge impact on the people,
which lost their data and information. Cybercrime makes huge impact on the financial conditions of an
organization (Shakarian, Shakarian, & Ruef, 2013).
Furthermore, cybersecurity is the only solution to cybercrime. The government has created new
laws and regulations to control the cybercrimes in the US (Snider, 2018). However, hackers will apply
new techniques to avoid such types of rules and regulations. Therefore, it is necessary to secure all the
things in proper manner (Tripwire, 2017).
The US government has right to impose a penalty for all those cybercrime in various orders, such
as cash penalty, prison for 1 to 25 years for cybercrimes. It improves the rations of cybercrimes in the
US.
Conclusion
In conclusion, cybercrime is common nowadays and it increases day by day. There are many
facilities linked to the internet. Therefore, number of changes has increased. This paper has provided
role of cybersecurity and cybercrime. It has provided types of scam, which has associated with the
cybercrime.
This report has explained the laws for cybercrimes and penalties for that particular crime in
detail. In addition, there is some specific law for cybercrime in the US. Finally, cybercrime can be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cybercrime 6
controlled using proper security management programs, education, and training. It will improve the
privacy and security in the system.
References
Andrijcic, E., & Horowitz, B. (2016). A Macro Economic Framework for Evaluation of Cyber Security Risks‐
Related to Protection of Intellectual Property. Risk analysis, 26(4), 907-923.
Arlitsch, K., & Edelman, A. (2014). Staying safe: Cyber security for people and organizations. Journal of
Library Administration, 54(1), 46-56. Retrieved from
https://www.tandfonline.com/doi/abs/10.1080/01930826.2014.893116?journalCode=wjla20
Bhagat, B. (2012). Patent No. 13/016,999. U. S.
Clement, J. (2019, August 4). U.S. consumers and cyber crime - Statistics & Facts . Retrieved from
https://www.statista.com: https://www.statista.com/topics/2588/us-consumers-and-cyber-
crime/
Fruhlinger, J. (2018). Top cybersecurity facts, figures and statistics for 2018. Retrieved december 11,
2018, from https://www.csoonline.com/article/3153707/security/top-cybersecurity-facts-
figures-and-statistics.html
Gravrock, E. v. (2019, March 4). Here are the biggest cybercrime trends of 2019. Retrieved from
https://www.weforum.org: https://www.weforum.org/agenda/2019/03/here-are-the-biggest-
cybercrime-trends-of-2019/
Leonhardt, M. (2018, December 6). This map shows where in the US cyber crime costs people the most.
Retrieved from https://www.cnbc.com: https://www.cnbc.com/2018/12/06/this-map-shows-
where-in-the-us-cyber-crime-costs-people-the-most.html
Lord, N. (2019). What is Cyber Security? Definition, Best Practices & More. Retrieved August 18, 2019,
from https://digitalguardian.com/blog/what-cyber-security
controlled using proper security management programs, education, and training. It will improve the
privacy and security in the system.
References
Andrijcic, E., & Horowitz, B. (2016). A Macro Economic Framework for Evaluation of Cyber Security Risks‐
Related to Protection of Intellectual Property. Risk analysis, 26(4), 907-923.
Arlitsch, K., & Edelman, A. (2014). Staying safe: Cyber security for people and organizations. Journal of
Library Administration, 54(1), 46-56. Retrieved from
https://www.tandfonline.com/doi/abs/10.1080/01930826.2014.893116?journalCode=wjla20
Bhagat, B. (2012). Patent No. 13/016,999. U. S.
Clement, J. (2019, August 4). U.S. consumers and cyber crime - Statistics & Facts . Retrieved from
https://www.statista.com: https://www.statista.com/topics/2588/us-consumers-and-cyber-
crime/
Fruhlinger, J. (2018). Top cybersecurity facts, figures and statistics for 2018. Retrieved december 11,
2018, from https://www.csoonline.com/article/3153707/security/top-cybersecurity-facts-
figures-and-statistics.html
Gravrock, E. v. (2019, March 4). Here are the biggest cybercrime trends of 2019. Retrieved from
https://www.weforum.org: https://www.weforum.org/agenda/2019/03/here-are-the-biggest-
cybercrime-trends-of-2019/
Leonhardt, M. (2018, December 6). This map shows where in the US cyber crime costs people the most.
Retrieved from https://www.cnbc.com: https://www.cnbc.com/2018/12/06/this-map-shows-
where-in-the-us-cyber-crime-costs-people-the-most.html
Lord, N. (2019). What is Cyber Security? Definition, Best Practices & More. Retrieved August 18, 2019,
from https://digitalguardian.com/blog/what-cyber-security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cybercrime 7
NCSC. (2019). The National Cyber Security Centre. Retrieved March 14, 2019, from
https://www.ncsc.gov.uk/
Rivner, U. (2018, December 14). 2019 Predictions - 10 Cybercrime Trends to Expect in the New Year.
Retrieved from https://www.biocatch.com: https://www.biocatch.com/blog/2019-predictions-
10-cybercrime-trends
Shakarian, P., Shakarian, J., & Ruef, A. (2013). Introduction to cyber-warfare: A multidisciplinary
approach. Newnes.
Snider, M. (2018, December 28). Your data was probably stolen in cyberattack in 2018 – and you should
care. Retrieved from www.usatoday.com:
https://www.usatoday.com/story/money/2018/12/28/data-breaches-2018-billions-hit-growing-
number-cyberattacks/2413411002/
Tripwire. (2017, November 22). Cybercrime Laws: What Internet Fraud Victims Need to Know. Retrieved
from https://www.tripwire.com: https://www.tripwire.com/state-of-security/security-
awareness/cybercrime-laws-what-internet-fraud-victims-need-to-know/
NCSC. (2019). The National Cyber Security Centre. Retrieved March 14, 2019, from
https://www.ncsc.gov.uk/
Rivner, U. (2018, December 14). 2019 Predictions - 10 Cybercrime Trends to Expect in the New Year.
Retrieved from https://www.biocatch.com: https://www.biocatch.com/blog/2019-predictions-
10-cybercrime-trends
Shakarian, P., Shakarian, J., & Ruef, A. (2013). Introduction to cyber-warfare: A multidisciplinary
approach. Newnes.
Snider, M. (2018, December 28). Your data was probably stolen in cyberattack in 2018 – and you should
care. Retrieved from www.usatoday.com:
https://www.usatoday.com/story/money/2018/12/28/data-breaches-2018-billions-hit-growing-
number-cyberattacks/2413411002/
Tripwire. (2017, November 22). Cybercrime Laws: What Internet Fraud Victims Need to Know. Retrieved
from https://www.tripwire.com: https://www.tripwire.com/state-of-security/security-
awareness/cybercrime-laws-what-internet-fraud-victims-need-to-know/
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





