Cybersecurity Attacks and Methods to Fend Them Off
VerifiedAdded on 2023/01/03
|13
|1538
|36
AI Summary
This document discusses cybersecurity attacks and provides methods to defend against them. It covers different design approaches, network designs, and security aspects. It also includes information on budgeting for cybersecurity measures.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

CYBERSECURITY ATTACKS AND METHODS TO FEND THEM OFF
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Cybersecurity attacks and methods to fend them off
Contents
TABLE 1 (T1): The weekly individual activity..........................................................................................2
TABLE 2 (T2): Group (Darshith, Geetha, Niharika, Anusha, Garry) activities on weekly basis................3
GANT CHART..........................................................................................................................................4
Design approaches................................................................................................................................6
UML diagram....................................................................................................................................6
Use case diagram...............................................................................................................................7
Flow chart..........................................................................................................................................8
Network design.....................................................................................................................................9
Security aspects, hardware aspects and hardware aspects of the network........................................10
Budget.................................................................................................................................................11
References...........................................................................................................................................12
Contents
TABLE 1 (T1): The weekly individual activity..........................................................................................2
TABLE 2 (T2): Group (Darshith, Geetha, Niharika, Anusha, Garry) activities on weekly basis................3
GANT CHART..........................................................................................................................................4
Design approaches................................................................................................................................6
UML diagram....................................................................................................................................6
Use case diagram...............................................................................................................................7
Flow chart..........................................................................................................................................8
Network design.....................................................................................................................................9
Security aspects, hardware aspects and hardware aspects of the network........................................10
Budget.................................................................................................................................................11
References...........................................................................................................................................12
Cybersecurity attacks and methods to fend them off
TABLE 1 (T1): The weekly individual activity
No Activities of every individual Week
Darshith Geetha Niharika Anusha
1 Project topic
was selected
and was
discussed
among
members
Project topic
was selected and
was discussed
among members
Project topic
was selected
and was
discussed
among members
Project topic was
selected and was
discussed among
members
Week 1
2 Was appointed
as the group
leader
Noted down
every point that
was discussed o
the group
Arranged every
communication
made with the
client
Arranged
meetings with the
supervisor
Week 2
3 Assigned
group
members task
to research on
the project
topic.
Researched on
the topic and the
way information
can be collected
from the client
Researched on
the topic and the
way information
can be collected
from the
Researched on
the topic and the
way information
can be collected
from the
Week 3
4 Noted down
relevant
questions the
client is to be
asked
concerning the
issue faced and
suggested to
the group.
Took note on
every response
from the client
for later
compilation.
Conducted a
meeting with
the clients in
order to acquire
information on
the problem
faced.
Noted down
relevant
questions the
client is to be
asked concerning
the issue faced
and suggested to
the group.
Week 4
5 Facilitated the
collection of
data and
ensured the
information
Collected data at
a personal level
before
suggesting
points to the
Collected data
at a personal
level before
suggesting
points to the
Collected data at
a personal level
before suggesting
points to the
group
Week 5
TABLE 1 (T1): The weekly individual activity
No Activities of every individual Week
Darshith Geetha Niharika Anusha
1 Project topic
was selected
and was
discussed
among
members
Project topic
was selected and
was discussed
among members
Project topic
was selected
and was
discussed
among members
Project topic was
selected and was
discussed among
members
Week 1
2 Was appointed
as the group
leader
Noted down
every point that
was discussed o
the group
Arranged every
communication
made with the
client
Arranged
meetings with the
supervisor
Week 2
3 Assigned
group
members task
to research on
the project
topic.
Researched on
the topic and the
way information
can be collected
from the client
Researched on
the topic and the
way information
can be collected
from the
Researched on
the topic and the
way information
can be collected
from the
Week 3
4 Noted down
relevant
questions the
client is to be
asked
concerning the
issue faced and
suggested to
the group.
Took note on
every response
from the client
for later
compilation.
Conducted a
meeting with
the clients in
order to acquire
information on
the problem
faced.
Noted down
relevant
questions the
client is to be
asked concerning
the issue faced
and suggested to
the group.
Week 4
5 Facilitated the
collection of
data and
ensured the
information
Collected data at
a personal level
before
suggesting
points to the
Collected data
at a personal
level before
suggesting
points to the
Collected data at
a personal level
before suggesting
points to the
group
Week 5
Cybersecurity attacks and methods to fend them off
captured is
relevant.
group group
6 Was
responsible for
ensuring
everything was
in order before
submission
Compiled the
information
gathered for it to
be submitted to
lecturer.
Ensured that the
assignment
followed IEE
styling format.
Assisted in
Compiling the
information
gathered for it to
be submitted to
lecturer.
Week 6
7 Ensure that the
group went
through the
lecturer’s
response in
order to design
an
appropriated
way of
problem-
solving.
Went through
lecturer’s
response and
suggested
different ways to
solve client’s
problems.
Went through
lecturer’s
response and
suggested
different ways
to solve client’s
problems.
Went through
lecturer’s
response and
suggested
different ways to
solve client’s
problems.
Week 7
8 Conducted the
modification
of the design
for more
accuracy and
suitability
Participated in
modifying the
design as per the
lecturer’s
response to
provide high
design
appropriateness
Participated in
modifying the
design as per
the lecturer’s
response to
provide high
design
appropriateness
Participated in
modifying the
design as per the
lecturer’s
response to
provide high
design
appropriateness
Week 8
9 Conducted the
final meeting
of design
report
documentation
and prepared
the group for
Documented the
final project
design report.
Took part in
final project
design
documentation
Took part in final
project design
documentation
Week 9
captured is
relevant.
group group
6 Was
responsible for
ensuring
everything was
in order before
submission
Compiled the
information
gathered for it to
be submitted to
lecturer.
Ensured that the
assignment
followed IEE
styling format.
Assisted in
Compiling the
information
gathered for it to
be submitted to
lecturer.
Week 6
7 Ensure that the
group went
through the
lecturer’s
response in
order to design
an
appropriated
way of
problem-
solving.
Went through
lecturer’s
response and
suggested
different ways to
solve client’s
problems.
Went through
lecturer’s
response and
suggested
different ways
to solve client’s
problems.
Went through
lecturer’s
response and
suggested
different ways to
solve client’s
problems.
Week 7
8 Conducted the
modification
of the design
for more
accuracy and
suitability
Participated in
modifying the
design as per the
lecturer’s
response to
provide high
design
appropriateness
Participated in
modifying the
design as per
the lecturer’s
response to
provide high
design
appropriateness
Participated in
modifying the
design as per the
lecturer’s
response to
provide high
design
appropriateness
Week 8
9 Conducted the
final meeting
of design
report
documentation
and prepared
the group for
Documented the
final project
design report.
Took part in
final project
design
documentation
Took part in final
project design
documentation
Week 9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Cybersecurity attacks and methods to fend them off
presentation.
TABLE 2 (T2): Group (Darshith, Geetha, Niharika, Anusha, Garry) activities on a
weekly basis
No Activity Week
1 The information on the cyber-attack collected
from the clients by the individuals were
gathered and compiled together to come up
with the way forward of the group activity.
Week 1
2 The cyber-attack issues basing on the research
done was analyzed in order to come up with the
best way of information collected from the
client.
Week 2
3 Clients were asked questions basing on the
problems they were experiencing and were
noted down for research.
Week 3
4 A suitable time to meet with the client for an
interview via skype was scheduled.
Week 4
5 A meeting with the client was conducted and
questions on major cyber-attacks affecting
them were asked and the security measures put
in place by the client to protect themselves
from the cyber-attack were identified.
Week 5
6 The information that was collected was
compiled and submitted to the lecturer for
preview.
Week 6
7 Response from the lecturers and supervisors
were worked on in order to come up with the
best design approach to the attacks.
Week 7
8 The design approach that was developed earlier Week 8
presentation.
TABLE 2 (T2): Group (Darshith, Geetha, Niharika, Anusha, Garry) activities on a
weekly basis
No Activity Week
1 The information on the cyber-attack collected
from the clients by the individuals were
gathered and compiled together to come up
with the way forward of the group activity.
Week 1
2 The cyber-attack issues basing on the research
done was analyzed in order to come up with the
best way of information collected from the
client.
Week 2
3 Clients were asked questions basing on the
problems they were experiencing and were
noted down for research.
Week 3
4 A suitable time to meet with the client for an
interview via skype was scheduled.
Week 4
5 A meeting with the client was conducted and
questions on major cyber-attacks affecting
them were asked and the security measures put
in place by the client to protect themselves
from the cyber-attack were identified.
Week 5
6 The information that was collected was
compiled and submitted to the lecturer for
preview.
Week 6
7 Response from the lecturers and supervisors
were worked on in order to come up with the
best design approach to the attacks.
Week 7
8 The design approach that was developed earlier Week 8
Cybersecurity attacks and methods to fend them off
was modified as per the response of the
supervisor.
9 The group members compiled together with the
final documentation on the project and
performed presentation on the same.
Week 9
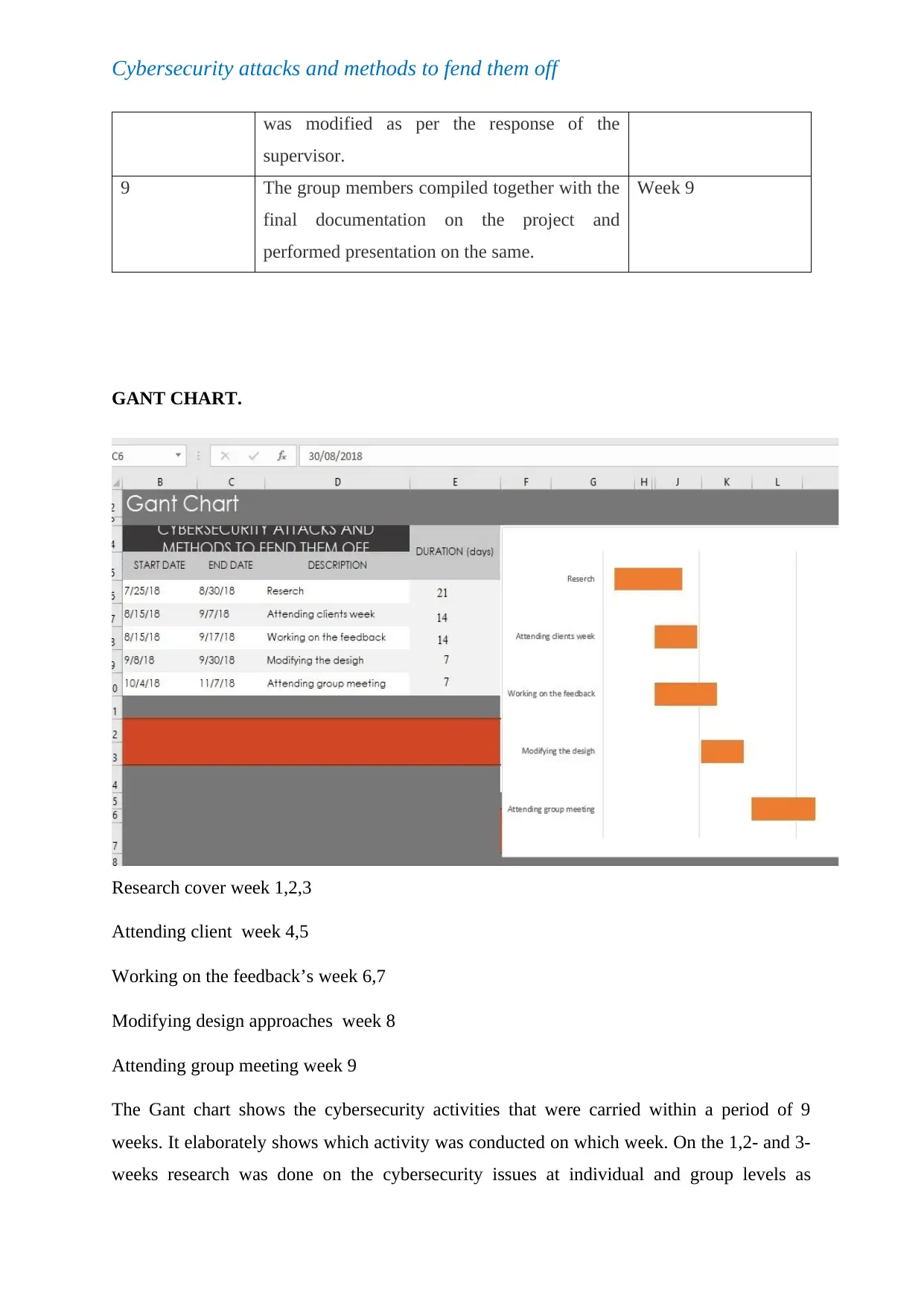
GANT CHART.
Research cover week 1,2,3
Attending client week 4,5
Working on the feedback’s week 6,7
Modifying design approaches week 8
Attending group meeting week 9
The Gant chart shows the cybersecurity activities that were carried within a period of 9
weeks. It elaborately shows which activity was conducted on which week. On the 1,2- and 3-
weeks research was done on the cybersecurity issues at individual and group levels as
was modified as per the response of the
supervisor.
9 The group members compiled together with the
final documentation on the project and
performed presentation on the same.
Week 9
GANT CHART.
Research cover week 1,2,3
Attending client week 4,5
Working on the feedback’s week 6,7
Modifying design approaches week 8
Attending group meeting week 9
The Gant chart shows the cybersecurity activities that were carried within a period of 9
weeks. It elaborately shows which activity was conducted on which week. On the 1,2- and 3-
weeks research was done on the cybersecurity issues at individual and group levels as
Cybersecurity attacks and methods to fend them off
indicated on tables T1 and T2. On the 4 and 5 weeks, the clients were reached out for meeting
in the skype to collect information about the problems they are going through. On the 6- and
7-week feedback from the lectures on the issues submitted were acted upon and later on the 8
weeks the designs modified to provide the appropriate solution to the client. On the last week
9, the group held a meeting and documented a final report on the cybersecurity solution.
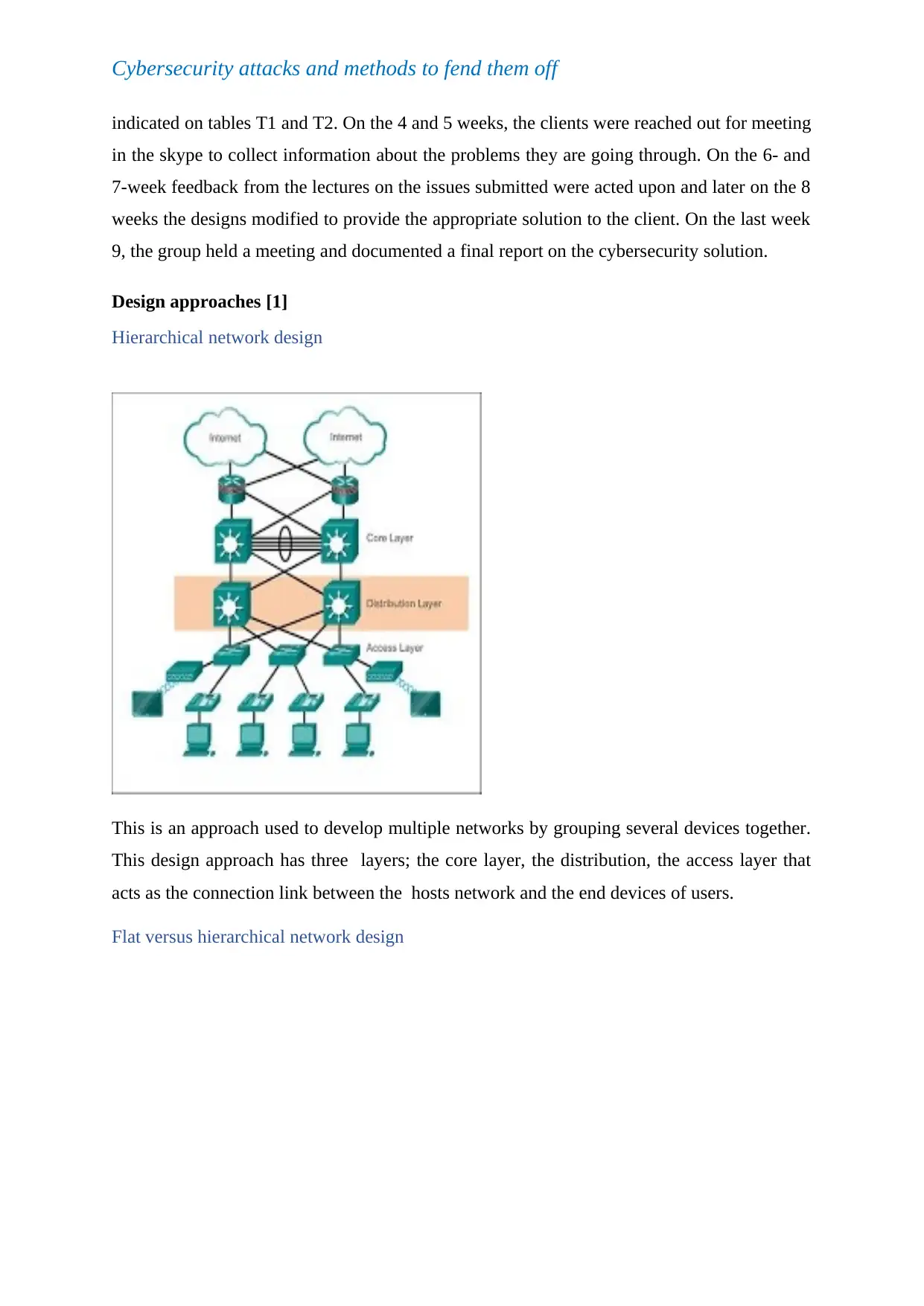
Design approaches [1]
Hierarchical network design
This is an approach used to develop multiple networks by grouping several devices together.
This design approach has three layers; the core layer, the distribution, the access layer that
acts as the connection link between the hosts network and the end devices of users.
Flat versus hierarchical network design
indicated on tables T1 and T2. On the 4 and 5 weeks, the clients were reached out for meeting
in the skype to collect information about the problems they are going through. On the 6- and
7-week feedback from the lectures on the issues submitted were acted upon and later on the 8
weeks the designs modified to provide the appropriate solution to the client. On the last week
9, the group held a meeting and documented a final report on the cybersecurity solution.
Design approaches [1]
Hierarchical network design
This is an approach used to develop multiple networks by grouping several devices together.
This design approach has three layers; the core layer, the distribution, the access layer that
acts as the connection link between the hosts network and the end devices of users.
Flat versus hierarchical network design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cybersecurity attacks and methods to fend them off
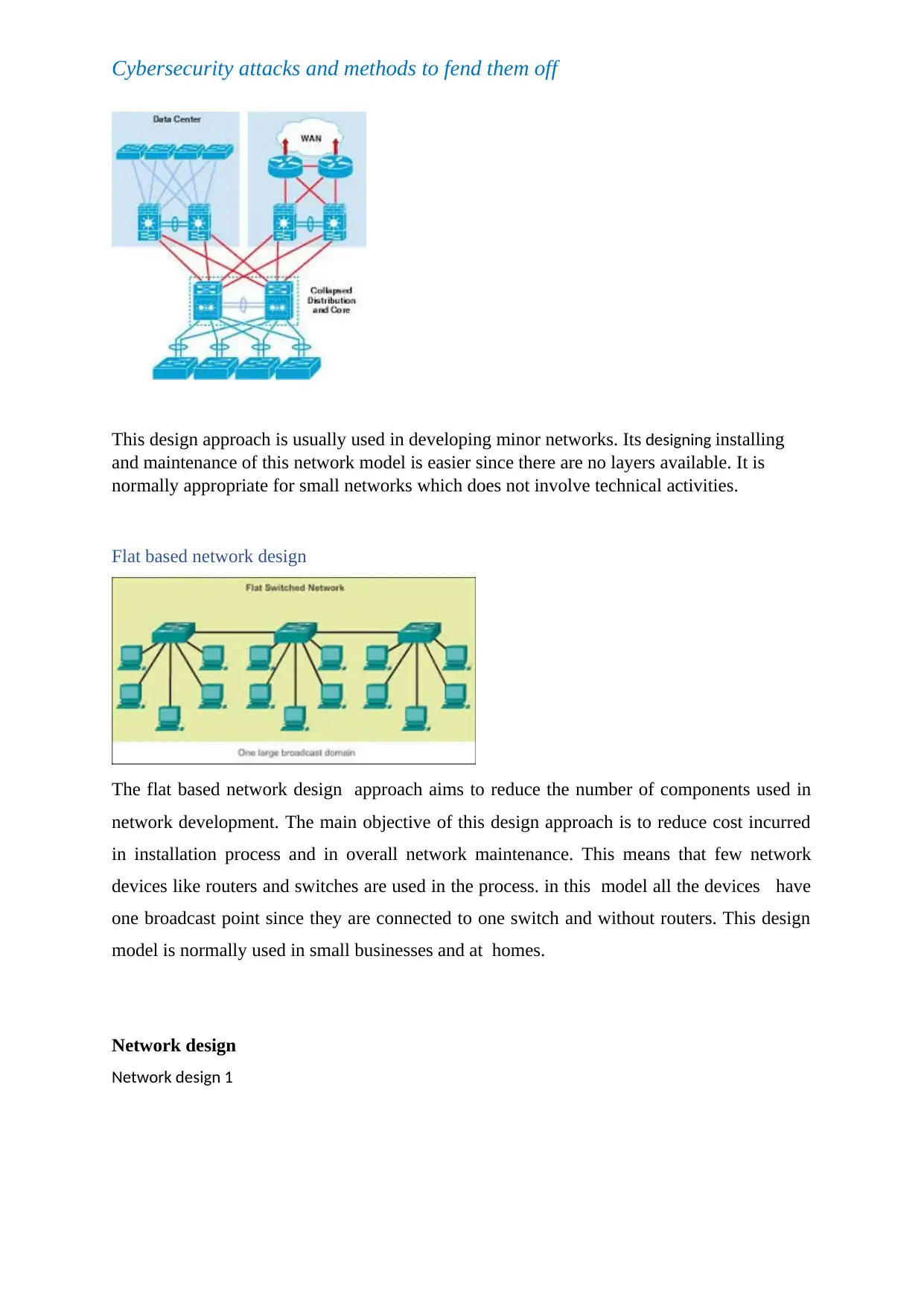
This design approach is usually used in developing minor networks. Its designing installing
and maintenance of this network model is easier since there are no layers available. It is
normally appropriate for small networks which does not involve technical activities.
Flat based network design
The flat based network design approach aims to reduce the number of components used in
network development. The main objective of this design approach is to reduce cost incurred
in installation process and in overall network maintenance. This means that few network
devices like routers and switches are used in the process. in this model all the devices have
one broadcast point since they are connected to one switch and without routers. This design
model is normally used in small businesses and at homes.
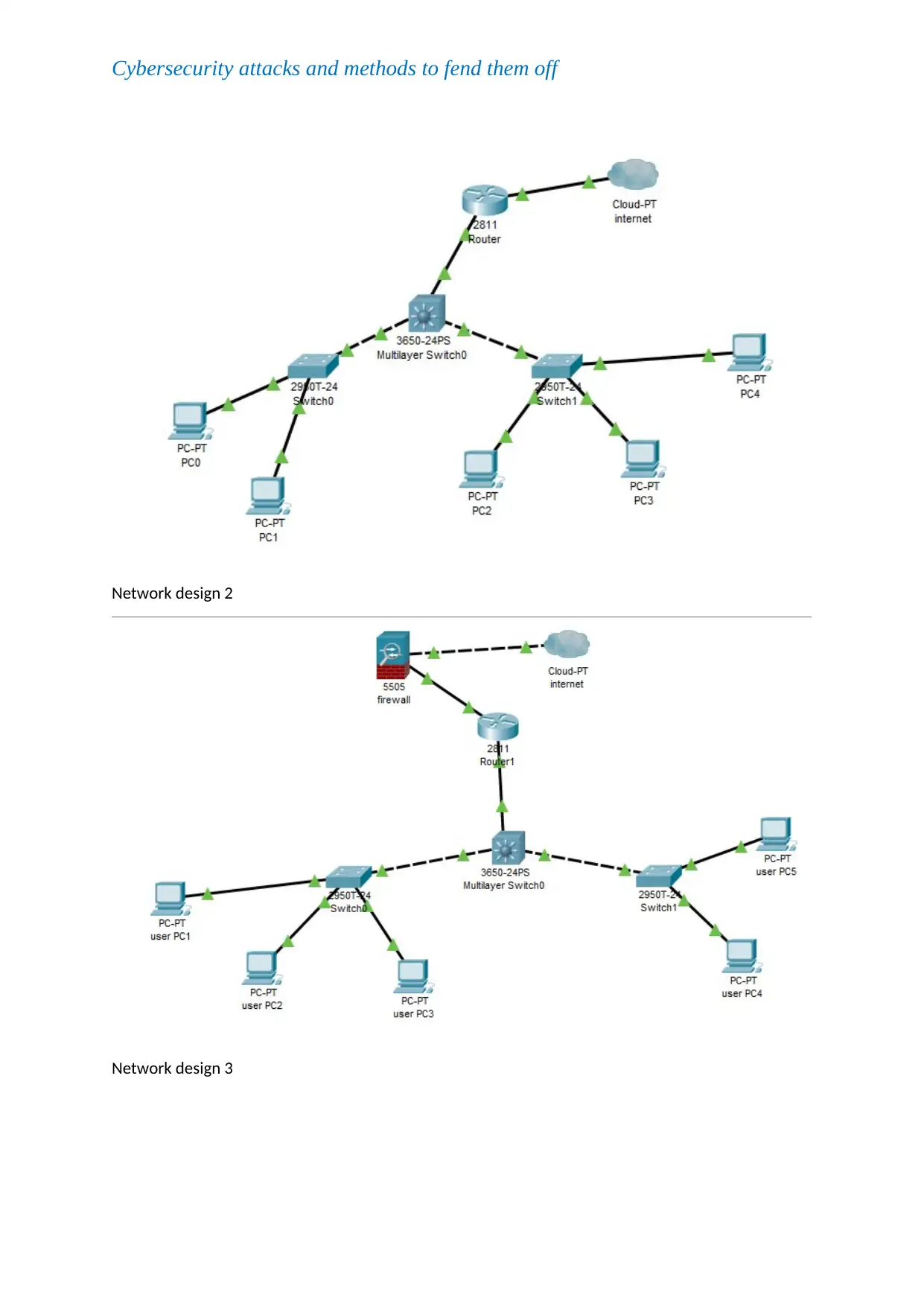
Network design
Network design 1
This design approach is usually used in developing minor networks. Its designing installing
and maintenance of this network model is easier since there are no layers available. It is
normally appropriate for small networks which does not involve technical activities.
Flat based network design
The flat based network design approach aims to reduce the number of components used in
network development. The main objective of this design approach is to reduce cost incurred
in installation process and in overall network maintenance. This means that few network
devices like routers and switches are used in the process. in this model all the devices have
one broadcast point since they are connected to one switch and without routers. This design
model is normally used in small businesses and at homes.
Network design
Network design 1
Cybersecurity attacks and methods to fend them off
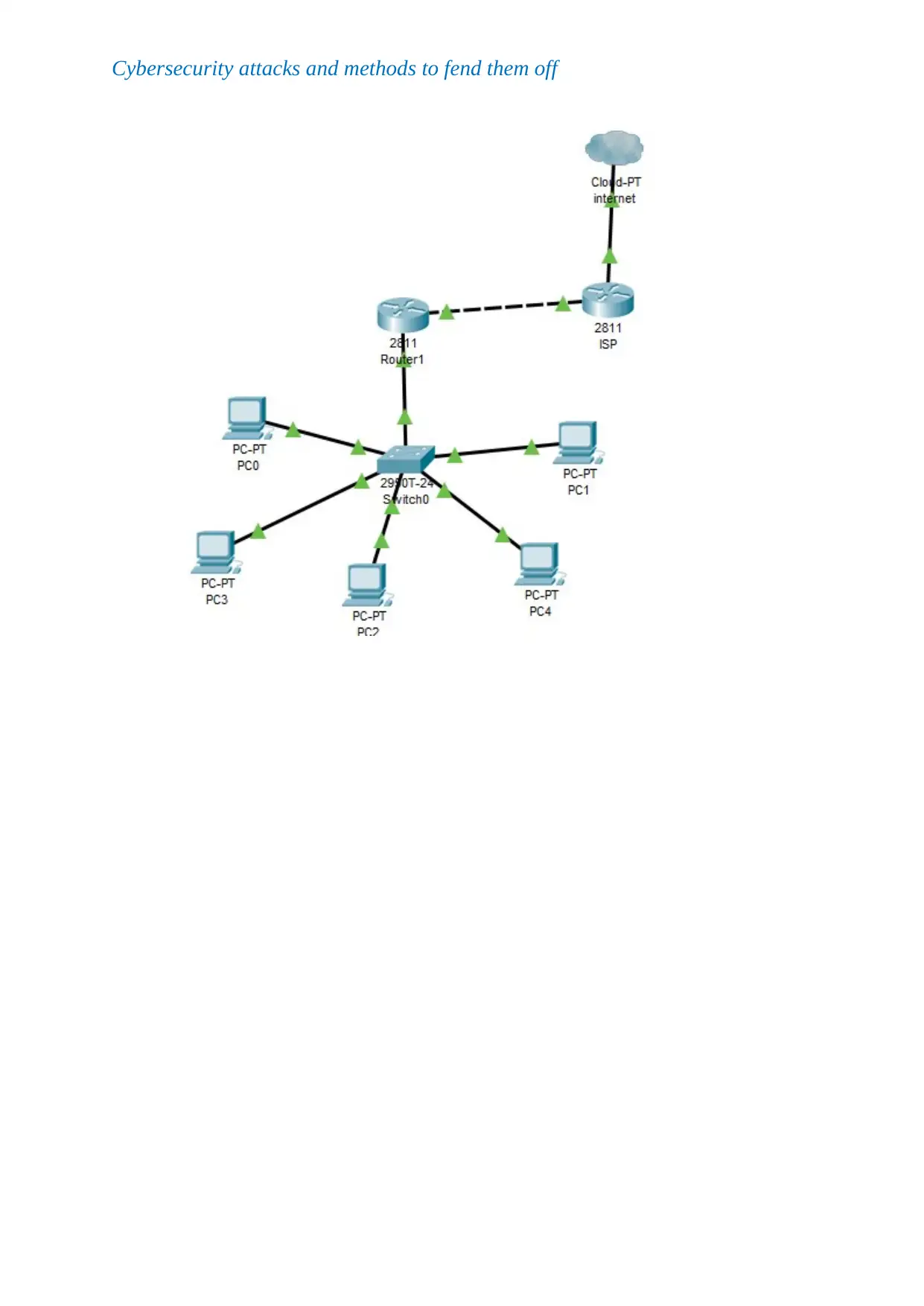
Network design 2
Network design 3
Network design 2
Network design 3
Cybersecurity attacks and methods to fend them off
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Cybersecurity attacks and methods to fend them off
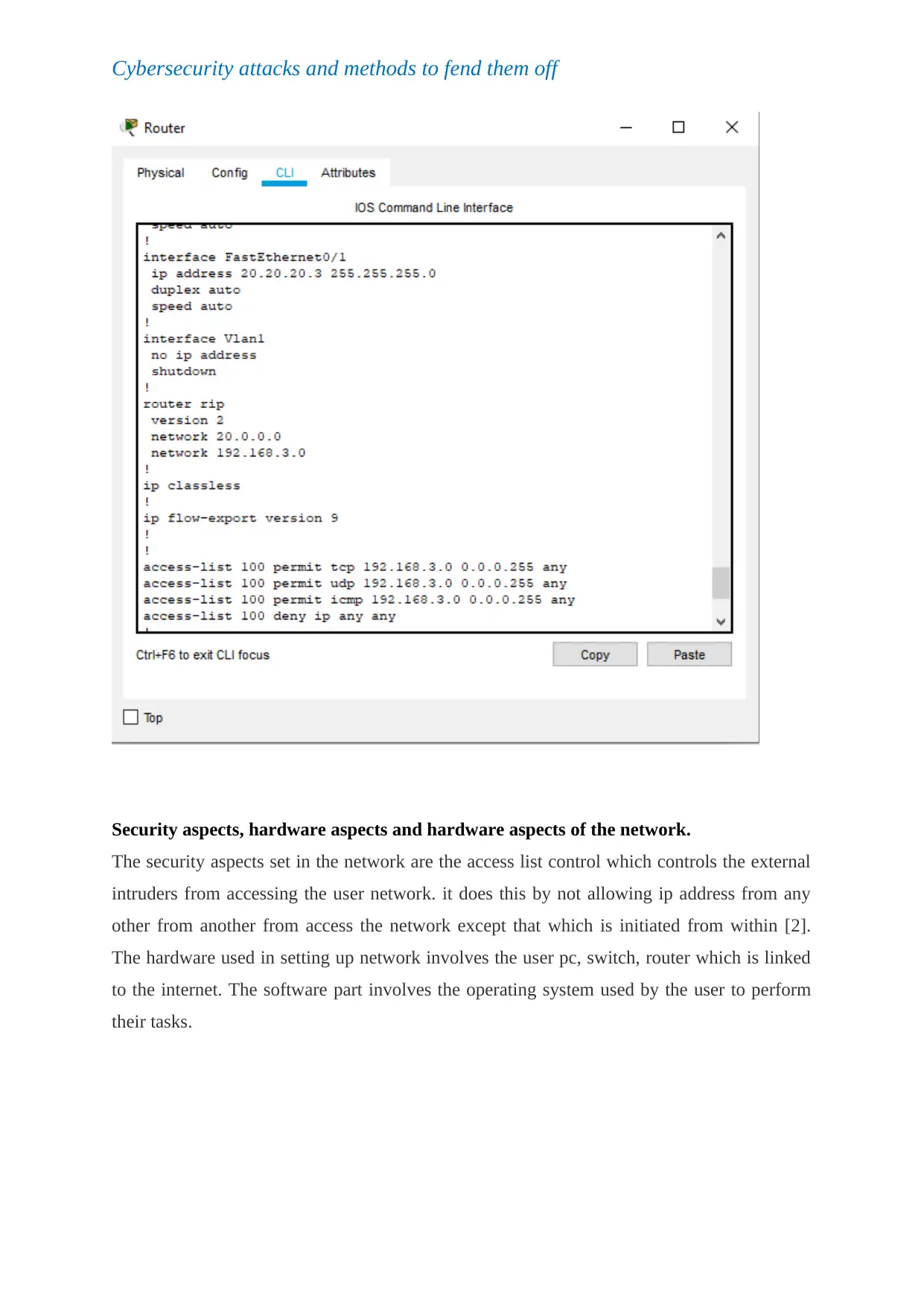
Security aspects, hardware aspects and hardware aspects of the network.
The security aspects set in the network are the access list control which controls the external
intruders from accessing the user network. it does this by not allowing ip address from any
other from another from access the network except that which is initiated from within [2].
The hardware used in setting up network involves the user pc, switch, router which is linked
to the internet. The software part involves the operating system used by the user to perform
their tasks.
Security aspects, hardware aspects and hardware aspects of the network.
The security aspects set in the network are the access list control which controls the external
intruders from accessing the user network. it does this by not allowing ip address from any
other from another from access the network except that which is initiated from within [2].
The hardware used in setting up network involves the user pc, switch, router which is linked
to the internet. The software part involves the operating system used by the user to perform
their tasks.
Cybersecurity attacks and methods to fend them off
Budget
Budget No Item Quantity specification Amount
1 Desktop
computer
5 4GB RAM,
500GB ROM
$1500
2 Router 1 Cisco router $100
3 Switch 3 2950-24 $150
4 Human labor 5 Human personnel $1000
5 OS 5 Microsoft
operating system
$500
TOTAL $4000
Budget
Budget No Item Quantity specification Amount
1 Desktop
computer
5 4GB RAM,
500GB ROM
$1500
2 Router 1 Cisco router $100
3 Switch 3 2950-24 $150
4 Human labor 5 Human personnel $1000
5 OS 5 Microsoft
operating system
$500
TOTAL $4000

Cybersecurity attacks and methods to fend them off
References
[1]. K. Swan and S. Zou, Interdisciplinary approaches to product design, innovation, &
branding in international marketing. Bingley, U.K.: Emerald, 2012.
[2]. C. Gentile, D. Griffith, and M. Souryal, "Wireless network deployment in the smart
grid: Design and evaluation issues", IEEE Network, vol. 26, no. 6, pp. 48-53, 2012.
Available: 10.1109/mnet.2012.6375893.
References
[1]. K. Swan and S. Zou, Interdisciplinary approaches to product design, innovation, &
branding in international marketing. Bingley, U.K.: Emerald, 2012.
[2]. C. Gentile, D. Griffith, and M. Souryal, "Wireless network deployment in the smart
grid: Design and evaluation issues", IEEE Network, vol. 26, no. 6, pp. 48-53, 2012.
Available: 10.1109/mnet.2012.6375893.
1 out of 13
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.
