Cybersecurity Challenges in Business: A Research Project
VerifiedAdded on 2024/06/04
|21
|2726
|103
AI Summary
This research project explores the critical role of cybersecurity in modern business operations. It delves into the challenges faced by both small and large enterprises in safeguarding their data and systems from cyber threats. The project examines the advantages of implementing robust cybersecurity measures and analyzes the impact of cybercrime on business operations. Through a comprehensive literature review and a quantitative research approach, the project aims to provide insights into the evolving landscape of cybersecurity and its implications for business success.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

HI6008
Assignment -2
Cybersecurity challenges in business
1 | P a g e
Assignment -2
Cybersecurity challenges in business
1 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Introduction......................................................................................................................................3
Project objective..............................................................................................................................4
Project Scope...................................................................................................................................5
Literature review:.............................................................................................................................6
Research questions and Hypothesis:................................................................................................9
Primary questions:.......................................................................................................................9
Secondary questions:...................................................................................................................9
Research Design............................................................................................................................10
Research methodology...................................................................................................................11
Qualitative Approach.................................................................................................................11
Quantitative Approach...............................................................................................................11
Questionnaire.................................................................................................................................13
Research Limitations.....................................................................................................................17
Time Schedule (Research Plan):....................................................................................................18
Conclusion.....................................................................................................................................20
References......................................................................................................................................21
2 | P a g e
Introduction......................................................................................................................................3
Project objective..............................................................................................................................4
Project Scope...................................................................................................................................5
Literature review:.............................................................................................................................6
Research questions and Hypothesis:................................................................................................9
Primary questions:.......................................................................................................................9
Secondary questions:...................................................................................................................9
Research Design............................................................................................................................10
Research methodology...................................................................................................................11
Qualitative Approach.................................................................................................................11
Quantitative Approach...............................................................................................................11
Questionnaire.................................................................................................................................13
Research Limitations.....................................................................................................................17
Time Schedule (Research Plan):....................................................................................................18
Conclusion.....................................................................................................................................20
References......................................................................................................................................21
2 | P a g e

Introduction
This report introduces to the topic of cybersecurity. In the modern world, cybersecurity is
essential for the successful survival of the business. There are various challenges which are
faced by the business. Cybersecurity is the main challenge in front of the business manager. This
report also shows the objective and scope of the project. Further, this report highlights the
research methodology, timescale, Gantt chart and various other research topics. The most
important challenge in front of the business is with regard to the security of the information. The
entire project is discussed and described in a systematic way.
3 | P a g e
This report introduces to the topic of cybersecurity. In the modern world, cybersecurity is
essential for the successful survival of the business. There are various challenges which are
faced by the business. Cybersecurity is the main challenge in front of the business manager. This
report also shows the objective and scope of the project. Further, this report highlights the
research methodology, timescale, Gantt chart and various other research topics. The most
important challenge in front of the business is with regard to the security of the information. The
entire project is discussed and described in a systematic way.
3 | P a g e

Project objective
The main objective of this research project is specified underneath:
To explain the concept of cybersecurity
To recognize the challenges which are faced by small and large businesses in ensuring
cybersecurity
To evaluate the advantages of cybersecurity in both small and large business
4 | P a g e
The main objective of this research project is specified underneath:
To explain the concept of cybersecurity
To recognize the challenges which are faced by small and large businesses in ensuring
cybersecurity
To evaluate the advantages of cybersecurity in both small and large business
4 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Project Scope
The scope of this project is wide as cybersecurity in itself is a wide term. In the current business
environment, the need for cybersecurity is rising. Today the Internet is one of the fastest budding
infrastructures in business life. Due to these developing technologies, the business entities are
not able to easily safeguard the private information of their clients in a very efficient and
effective way and hence these days the number of cyber crimes is increasing. There is a need for
the business to recognize the cyber challenges.
5 | P a g e
The scope of this project is wide as cybersecurity in itself is a wide term. In the current business
environment, the need for cybersecurity is rising. Today the Internet is one of the fastest budding
infrastructures in business life. Due to these developing technologies, the business entities are
not able to easily safeguard the private information of their clients in a very efficient and
effective way and hence these days the number of cyber crimes is increasing. There is a need for
the business to recognize the cyber challenges.
5 | P a g e

Literature review: Cyber Security Challenges in Business Entities.
According to Gomes, et. al. (2017), Security and Privacy of data will permanently be the best
security measures which any business takes care. In the present world, all the data is sustained in
a cyber or a digital form. Cybercrime is a word for any unlawful activity which utilizes a
computer as its chief means of theft and commission.Cybersecurity is essential for the survival of
the business. Cybersecurity helps in marinating the privacy and security of the client’s
information (Gomes, et. al., 2017).
According to Goel and Jindal (2017), a report by Verizon Data Breach Investigation shows that
61% of hackers hit smaller businesses in 2017 compared to 2016 which was at 53%. Small and
medium enterprises universally known as SMEs are a prime target of cyber-attacks regardless of
them being small as compared to the large enterprises. They SMEs mostly utilize cloud storage
as it assists them to pile their information and is very suitable for them. Cloud storing lets the
information easily available to the companies even on the move and can also act as a backup for
information. The growing angle of cybercrimes consists of crimes which have been made
conceivable by computers, like the distribution of computer viruses and network intrusions, as
well as computer-based deviations of current offenses, like identity terrorism, bullying, theft, and
stalking which have turn out to be an as most important problem to nations and people. In the
common man’s language, cyber-crime can be described as the crime committed by utilizing the
internet and a computer to steal an individual’s identity or trade stalk victims or contraband or
disturb processes with malicious programs (Goel and Jindal, 2017). In the current worlds,
technology is playing the main role in an individual’s life. The cybercrimes will also intensify
along with the technological improvements.
According to Fu, et. al. (2017), Currently more than 60 out of a hundred of total marketable
dealings are done online, so this arena prerequisite a great quality of safety for best and
transparent and transactions. Hence, cybersecurity has to turn out to be one of the latest issues.
The range of cybersecurity is not just restricted to safeguarding the data in Information
Technology industry but also to numerous other areas like cyberspace etc. Even the modern
technologies like net banking, mobile computing, cloud computing, E-commerce etc. also
requires a high level of safety. As these technologies hold lots of significant information on the
6 | P a g e
According to Gomes, et. al. (2017), Security and Privacy of data will permanently be the best
security measures which any business takes care. In the present world, all the data is sustained in
a cyber or a digital form. Cybercrime is a word for any unlawful activity which utilizes a
computer as its chief means of theft and commission.Cybersecurity is essential for the survival of
the business. Cybersecurity helps in marinating the privacy and security of the client’s
information (Gomes, et. al., 2017).
According to Goel and Jindal (2017), a report by Verizon Data Breach Investigation shows that
61% of hackers hit smaller businesses in 2017 compared to 2016 which was at 53%. Small and
medium enterprises universally known as SMEs are a prime target of cyber-attacks regardless of
them being small as compared to the large enterprises. They SMEs mostly utilize cloud storage
as it assists them to pile their information and is very suitable for them. Cloud storing lets the
information easily available to the companies even on the move and can also act as a backup for
information. The growing angle of cybercrimes consists of crimes which have been made
conceivable by computers, like the distribution of computer viruses and network intrusions, as
well as computer-based deviations of current offenses, like identity terrorism, bullying, theft, and
stalking which have turn out to be an as most important problem to nations and people. In the
common man’s language, cyber-crime can be described as the crime committed by utilizing the
internet and a computer to steal an individual’s identity or trade stalk victims or contraband or
disturb processes with malicious programs (Goel and Jindal, 2017). In the current worlds,
technology is playing the main role in an individual’s life. The cybercrimes will also intensify
along with the technological improvements.
According to Fu, et. al. (2017), Currently more than 60 out of a hundred of total marketable
dealings are done online, so this arena prerequisite a great quality of safety for best and
transparent and transactions. Hence, cybersecurity has to turn out to be one of the latest issues.
The range of cybersecurity is not just restricted to safeguarding the data in Information
Technology industry but also to numerous other areas like cyberspace etc. Even the modern
technologies like net banking, mobile computing, cloud computing, E-commerce etc. also
requires a high level of safety. As these technologies hold lots of significant information on the
6 | P a g e

subject of a person their safety has to turn out to be a mandatory thing. Businesses normally have
dissimilar challengers who would do anything to have a high advantage hence can pay hackers to
attempt and gain admission to their challenger's strategy and client’s information (Fu, et. al.,
2017).
According to Coffey (2017), increasing cybersecurity and guarding dire information, security
infrastructures are vital to each state's economic and security well-being. Protecting Internet
users (and making Internet safer) has to turn out to be essential to the growth of new facilities as
well as administrative policy. The battle in contradiction of cybercrime requires a safer and
comprehensive approach. Given that technical processes alone are not able to prevent any crime,
it is precarious that law implementation agencies are permitted to prosecute and investigate
cybercrime effectively. Nowadays many governments and nations are imposing strict rules on
the cyber securities in an order to stop the damage of some significant information to (Coffey,
2017). Every individual should also be competent on this cybersecurity and protect themselves
from these growing cyber crimes
7 | P a g e
dissimilar challengers who would do anything to have a high advantage hence can pay hackers to
attempt and gain admission to their challenger's strategy and client’s information (Fu, et. al.,
2017).
According to Coffey (2017), increasing cybersecurity and guarding dire information, security
infrastructures are vital to each state's economic and security well-being. Protecting Internet
users (and making Internet safer) has to turn out to be essential to the growth of new facilities as
well as administrative policy. The battle in contradiction of cybercrime requires a safer and
comprehensive approach. Given that technical processes alone are not able to prevent any crime,
it is precarious that law implementation agencies are permitted to prosecute and investigate
cybercrime effectively. Nowadays many governments and nations are imposing strict rules on
the cyber securities in an order to stop the damage of some significant information to (Coffey,
2017). Every individual should also be competent on this cybersecurity and protect themselves
from these growing cyber crimes
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Research gap
The gap identified in the research helps in conducting the research in more effective manner.
The first gap of this research is that there is a lack of previous research on the same topic as most
of the research is limited to big business. The second gap which is identified in this research is
that it is not focusing on a particular business type but taking into account all the business
entities. Hence, the gap in the research presents the limitations or drawbacks of the research.
8 | P a g e
The gap identified in the research helps in conducting the research in more effective manner.
The first gap of this research is that there is a lack of previous research on the same topic as most
of the research is limited to big business. The second gap which is identified in this research is
that it is not focusing on a particular business type but taking into account all the business
entities. Hence, the gap in the research presents the limitations or drawbacks of the research.
8 | P a g e

Research questions and Hypothesis:
There are mainly 2 kinds of questions on which this research project is putting attention and they
are:
Primary questions:
Question no. 1: Explain the concept of cybersecurity?
Secondary questions:
Question no. 1: Recognize the challenges which are faced by small and large businesses in
ensuring cybersecurity?
Question no.2: Evaluate the advantages of cybersecurity in both small and large business?
Hypothesis:
The main hypothesis which is well-thought-out in this research project is identified below:
Hypothesis 1: There is a direct relationship between cybercrimes and cybersecurity
Hypothesis 2: Internet is one of the fastest increasing infrastructures in business life
9 | P a g e
There are mainly 2 kinds of questions on which this research project is putting attention and they
are:
Primary questions:
Question no. 1: Explain the concept of cybersecurity?
Secondary questions:
Question no. 1: Recognize the challenges which are faced by small and large businesses in
ensuring cybersecurity?
Question no.2: Evaluate the advantages of cybersecurity in both small and large business?
Hypothesis:
The main hypothesis which is well-thought-out in this research project is identified below:
Hypothesis 1: There is a direct relationship between cybercrimes and cybersecurity
Hypothesis 2: Internet is one of the fastest increasing infrastructures in business life
9 | P a g e

Research Design
The research design which is used in this research is the explanatory research design. The main
idea behind using the explanatory research design is to know the cause and effect relationship
between independent and dependent variables. This research design is the most useful design as
it helps in drawing accurate conclusions and results. A research design is well thought-out to be a
rudimentary plan that leads the assemblage of data and its analysis. Hence, a research design is a
proposal for picking out subjects, investigation sites, and info assemblage processes
10 | P a g e
The research design which is used in this research is the explanatory research design. The main
idea behind using the explanatory research design is to know the cause and effect relationship
between independent and dependent variables. This research design is the most useful design as
it helps in drawing accurate conclusions and results. A research design is well thought-out to be a
rudimentary plan that leads the assemblage of data and its analysis. Hence, a research design is a
proposal for picking out subjects, investigation sites, and info assemblage processes
10 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Research methodology
Research methodology comprised of a sequential range of methods, principles and assumptions
and activities which are undertaken to complete the research. The two prime approaches for
conducting a research in a well-organized manner are qualitative and quantitative approaches.
Research methodology denotes the well-stated theories and approaches for conducting a research
in a well-organized manner. This research is developed by using Quantitative approach.
Qualitative Approach
Qualitative research pursues to express the story of a specific crowd’s experiences in their
individual words and is consequently attentive on the description (while the quantitative research
laid emphases on numbers). Qualitative research inclines to be extra fact-finding in nature,
looking to provide vision into by what means persons (or groups, organizations, etc.)
comprehend features of their domains. The well-made qualitative investigation is extremely
methodical, though, necessitating that investigators prudently record both their annotations and
their familiarities in gathering the information. A connected apprehension is that qualitative
investigation inclines to authorize investigators’ own thoughtfulness of phenomenon. Virtuous
qualitative researcher’s purpose for “saturation” of information, however, which includes
gathering and examining information in an iterative procedure until no new data get up.
Methodically composed, saturated qualitative information arrange for a degree of revelation into
a compound phenomenon which varies intensely from what is delivered through quantitative
examination (Silverman, 2016).
Quantitative Approach
The quantitative approach is considered to be a simple approach as the data is not explained in a
detailed manner. In the quantitative research, the investigators develop hypotheses to conduct the
research easily. Quantitative research is a reliable approach for conducting a research. This
approach is aiming at analysing ideas, describing authenticities, signifying relationships amongst
variables; the questionnaires are used to accumulate quantitative data. The methods which are
employed in quantitative research contain a random sampling of research candidates from the
study. The relationship amongst specific variables is considered in a precise manner by using the
11 | P a g e
Research methodology comprised of a sequential range of methods, principles and assumptions
and activities which are undertaken to complete the research. The two prime approaches for
conducting a research in a well-organized manner are qualitative and quantitative approaches.
Research methodology denotes the well-stated theories and approaches for conducting a research
in a well-organized manner. This research is developed by using Quantitative approach.
Qualitative Approach
Qualitative research pursues to express the story of a specific crowd’s experiences in their
individual words and is consequently attentive on the description (while the quantitative research
laid emphases on numbers). Qualitative research inclines to be extra fact-finding in nature,
looking to provide vision into by what means persons (or groups, organizations, etc.)
comprehend features of their domains. The well-made qualitative investigation is extremely
methodical, though, necessitating that investigators prudently record both their annotations and
their familiarities in gathering the information. A connected apprehension is that qualitative
investigation inclines to authorize investigators’ own thoughtfulness of phenomenon. Virtuous
qualitative researcher’s purpose for “saturation” of information, however, which includes
gathering and examining information in an iterative procedure until no new data get up.
Methodically composed, saturated qualitative information arrange for a degree of revelation into
a compound phenomenon which varies intensely from what is delivered through quantitative
examination (Silverman, 2016).
Quantitative Approach
The quantitative approach is considered to be a simple approach as the data is not explained in a
detailed manner. In the quantitative research, the investigators develop hypotheses to conduct the
research easily. Quantitative research is a reliable approach for conducting a research. This
approach is aiming at analysing ideas, describing authenticities, signifying relationships amongst
variables; the questionnaires are used to accumulate quantitative data. The methods which are
employed in quantitative research contain a random sampling of research candidates from the
study. The relationship amongst specific variables is considered in a precise manner by using the
11 | P a g e

Quantitative approach. The quantitative approach is used when the data is of numerical nature
and is required to be studied in a statistical from. The process of the quantitative approach is
complex and should be followed in a systematic manner. Most of the quantitative research is
from the expected sciences which confirm fairness, generalizability, and trustworthiness
(Williamson and Johanson, 2017).
Sample size and technique
The size of the sample of this research is small. Small sample size helps in getting accurate and
correct information. The sampling technique which is used in this research is a random sampling.
Random sampling technique is not a complex technique.
Reliability and validity of data
The data and information of this research are valid and reliable. The valid information is the one
which can be cross verified and still produces same results while the reliability ensures
consistency throughout the research project (O'Leary, 2017).
12 | P a g e
and is required to be studied in a statistical from. The process of the quantitative approach is
complex and should be followed in a systematic manner. Most of the quantitative research is
from the expected sciences which confirm fairness, generalizability, and trustworthiness
(Williamson and Johanson, 2017).
Sample size and technique
The size of the sample of this research is small. Small sample size helps in getting accurate and
correct information. The sampling technique which is used in this research is a random sampling.
Random sampling technique is not a complex technique.
Reliability and validity of data
The data and information of this research are valid and reliable. The valid information is the one
which can be cross verified and still produces same results while the reliability ensures
consistency throughout the research project (O'Leary, 2017).
12 | P a g e
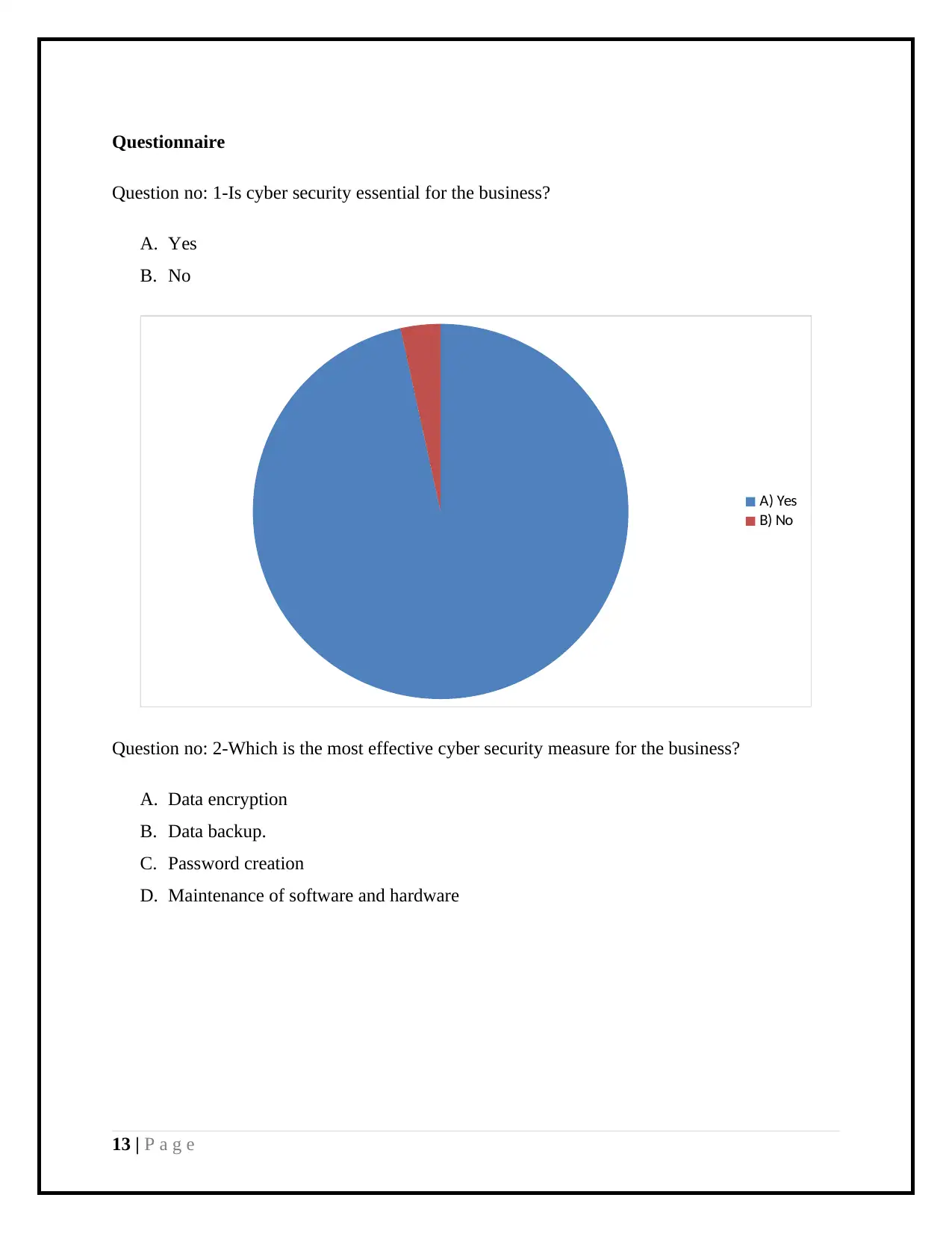
Questionnaire
Question no: 1-Is cyber security essential for the business?
A. Yes
B. No
A) Yes
B) No
Question no: 2-Which is the most effective cyber security measure for the business?
A. Data encryption
B. Data backup.
C. Password creation
D. Maintenance of software and hardware
13 | P a g e
Question no: 1-Is cyber security essential for the business?
A. Yes
B. No
A) Yes
B) No
Question no: 2-Which is the most effective cyber security measure for the business?
A. Data encryption
B. Data backup.
C. Password creation
D. Maintenance of software and hardware
13 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

A. Data encryption
B. Data backup.
C. Password creation
D. Maintenance of software
and hardware
Question no: 3- Which is the most likely challenge that is encountered by the business?
A. Criminals (monetary gain from theft)
B. Spies(concentrating on stealing the information)
C. Hacktivists (cyber attacks for the non-monetary motives)
D. Terrorists (cyber attacks as a custom of non-state warfare).
14 | P a g e
B. Data backup.
C. Password creation
D. Maintenance of software
and hardware
Question no: 3- Which is the most likely challenge that is encountered by the business?
A. Criminals (monetary gain from theft)
B. Spies(concentrating on stealing the information)
C. Hacktivists (cyber attacks for the non-monetary motives)
D. Terrorists (cyber attacks as a custom of non-state warfare).
14 | P a g e
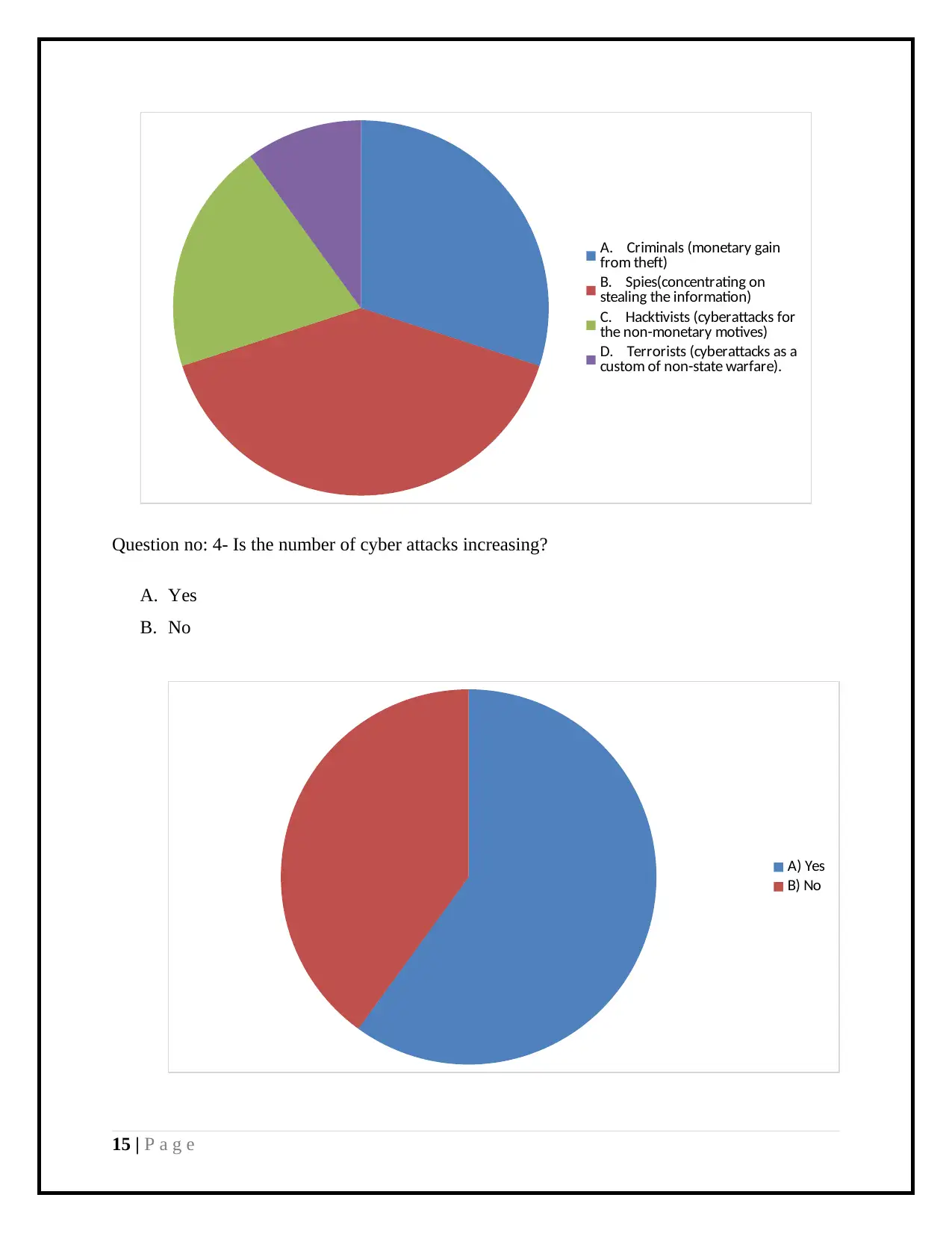
A. Criminals (monetary gain
from theft)
B. Spies(concentrating on
stealing the information)
C. Hacktivists (cyberattacks for
the non-monetary motives)
D. Terrorists (cyberattacks as a
custom of non-state warfare).
Question no: 4- Is the number of cyber attacks increasing?
A. Yes
B. No
A) Yes
B) No
15 | P a g e
from theft)
B. Spies(concentrating on
stealing the information)
C. Hacktivists (cyberattacks for
the non-monetary motives)
D. Terrorists (cyberattacks as a
custom of non-state warfare).
Question no: 4- Is the number of cyber attacks increasing?
A. Yes
B. No
A) Yes
B) No
15 | P a g e
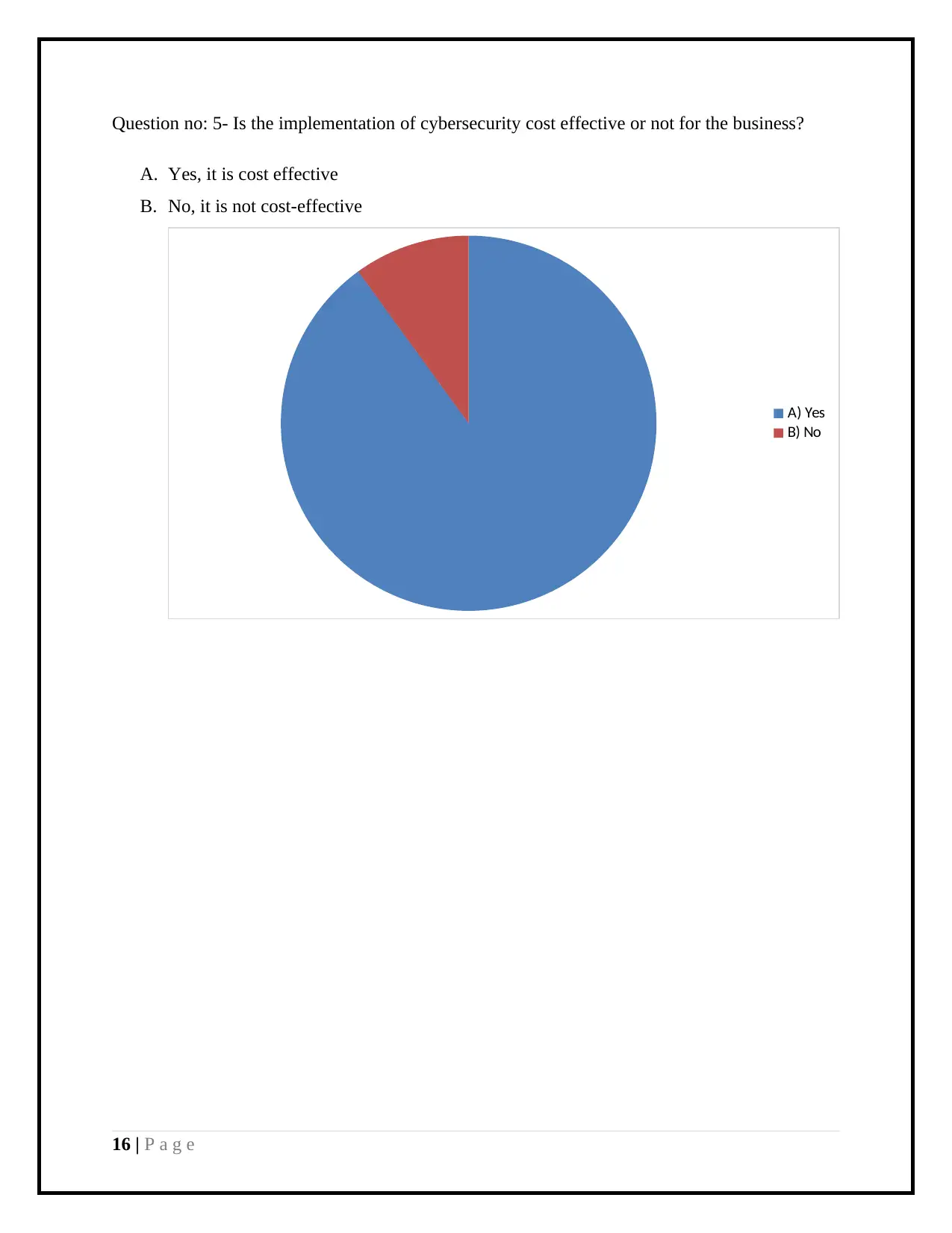
Question no: 5- Is the implementation of cybersecurity cost effective or not for the business?
A. Yes, it is cost effective
B. No, it is not cost-effective
A) Yes
B) No
16 | P a g e
A. Yes, it is cost effective
B. No, it is not cost-effective
A) Yes
B) No
16 | P a g e
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Research Limitations
The limitations which are identified in this research consist of the following:
There is lack of proper information as this research is conducted in a general manner.
there is no experts or professionals opinion
This research suffers from the limitation of personal biasness
Due to the lack of limited time and resources, this research cannot be completed in an
appropriate manner.
All the data cannot be studied as this research has a small sample size (Mertens, 2014).
17 | P a g e
The limitations which are identified in this research consist of the following:
There is lack of proper information as this research is conducted in a general manner.
there is no experts or professionals opinion
This research suffers from the limitation of personal biasness
Due to the lack of limited time and resources, this research cannot be completed in an
appropriate manner.
All the data cannot be studied as this research has a small sample size (Mertens, 2014).
17 | P a g e
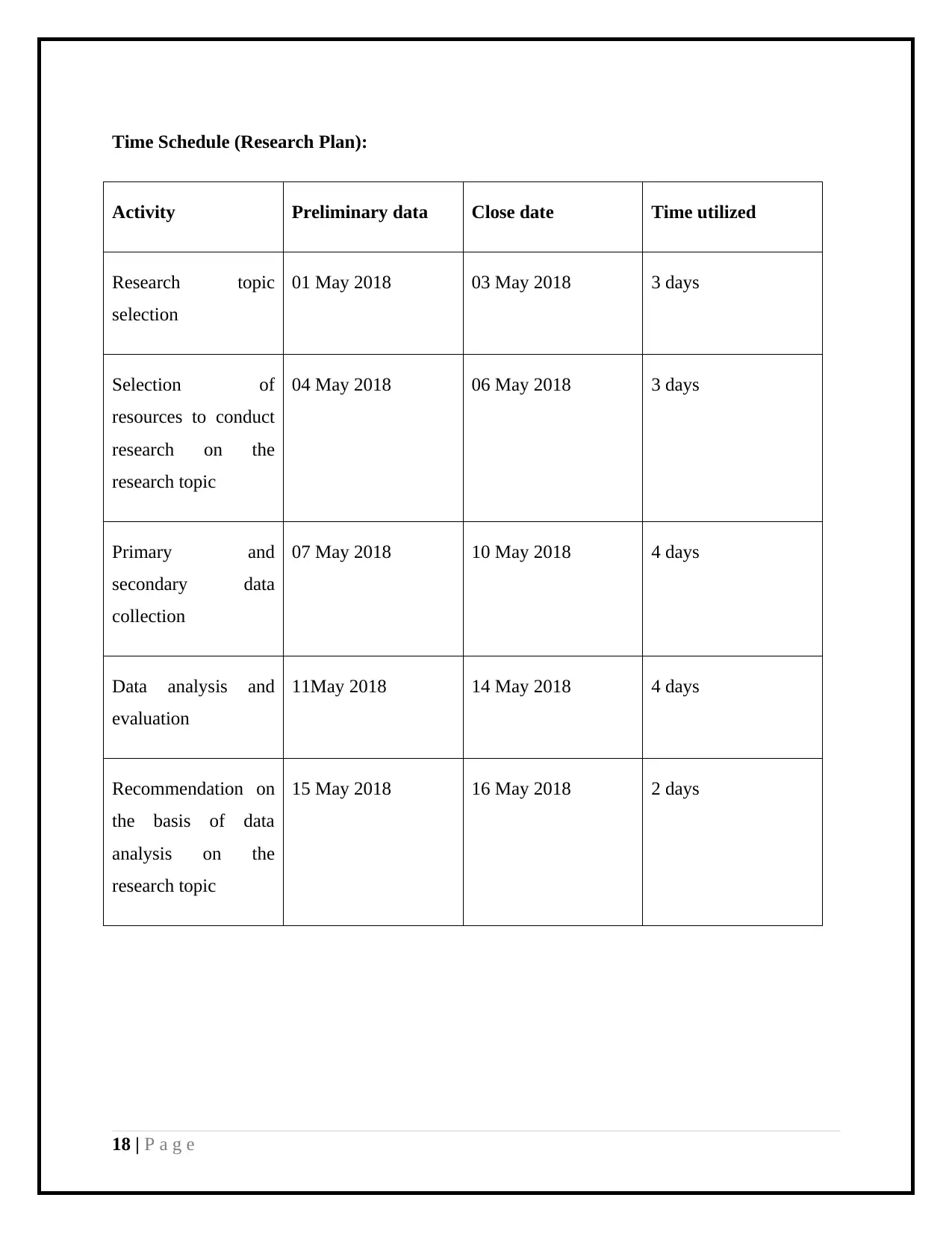
Time Schedule (Research Plan):
Activity Preliminary data Close date Time utilized
Research topic
selection
01 May 2018 03 May 2018 3 days
Selection of
resources to conduct
research on the
research topic
04 May 2018 06 May 2018 3 days
Primary and
secondary data
collection
07 May 2018 10 May 2018 4 days
Data analysis and
evaluation
11May 2018 14 May 2018 4 days
Recommendation on
the basis of data
analysis on the
research topic
15 May 2018 16 May 2018 2 days
18 | P a g e
Activity Preliminary data Close date Time utilized
Research topic
selection
01 May 2018 03 May 2018 3 days
Selection of
resources to conduct
research on the
research topic
04 May 2018 06 May 2018 3 days
Primary and
secondary data
collection
07 May 2018 10 May 2018 4 days
Data analysis and
evaluation
11May 2018 14 May 2018 4 days
Recommendation on
the basis of data
analysis on the
research topic
15 May 2018 16 May 2018 2 days
18 | P a g e
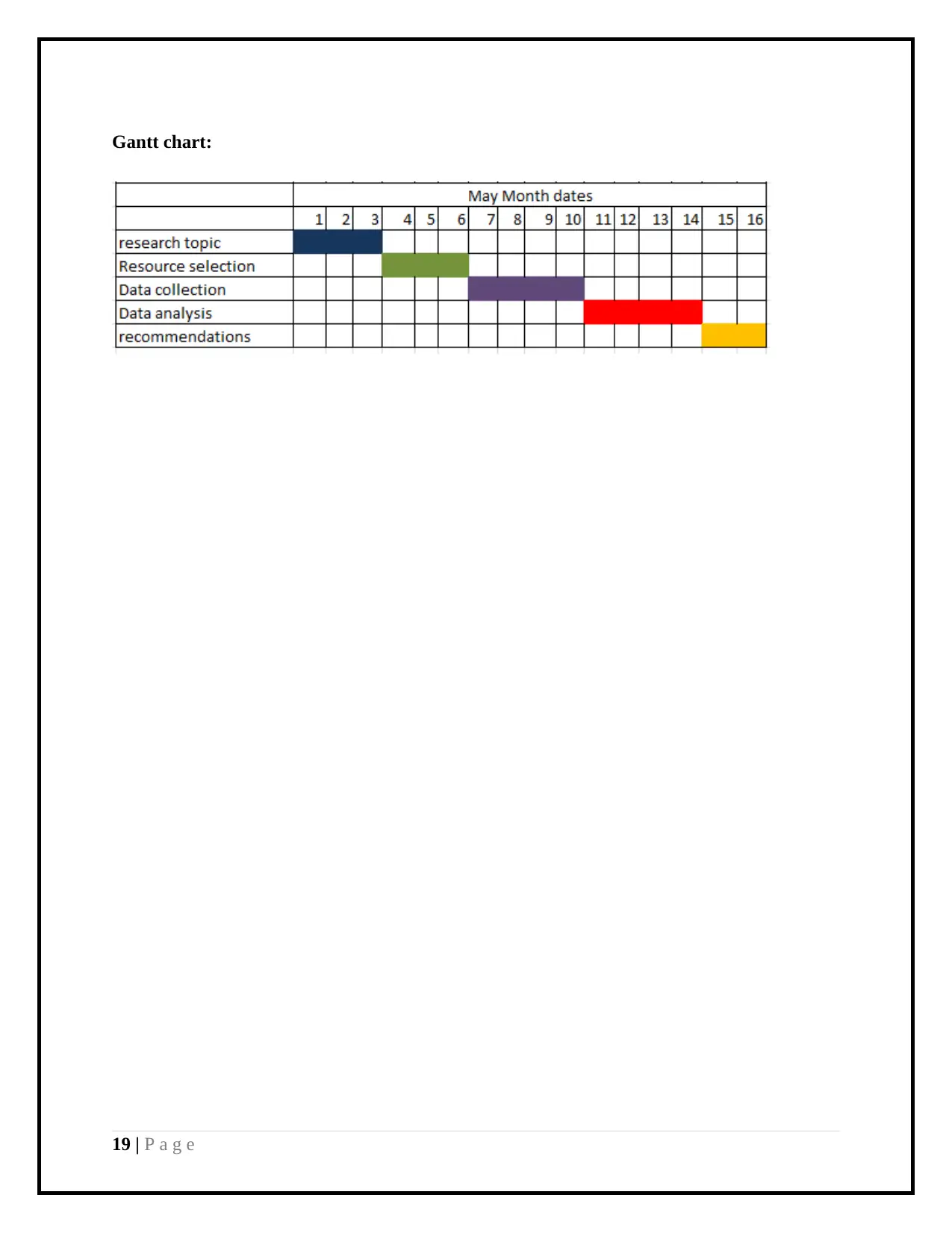
Gantt chart:
19 | P a g e
19 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Conclusion
From the above report, it can be concluded that cybersecurity plays a crucial part in the SME.
There are numerous challenges which are faced by the business. The most important loss is the
loss of data and privacy of the consumers. To overcome these losses or challenges it is important
for the business houses to invest in cybersecurity. Proper infrastructure, software’s and experts
must be hired and purchased by the company to minimize the number of cyber-attacks which are
faced by the business. A good firewall must be set up for the website to avoid cyber-attacks.
20 | P a g e
From the above report, it can be concluded that cybersecurity plays a crucial part in the SME.
There are numerous challenges which are faced by the business. The most important loss is the
loss of data and privacy of the consumers. To overcome these losses or challenges it is important
for the business houses to invest in cybersecurity. Proper infrastructure, software’s and experts
must be hired and purchased by the company to minimize the number of cyber-attacks which are
faced by the business. A good firewall must be set up for the website to avoid cyber-attacks.
20 | P a g e

References
Coffey, J. W. (2017). Ameliorating Sources of Human Error in CyberSecurity:
Technological and Human-Centered Approaches. In The 8th International Multi-
Conference on Complexity, Informatics and Cybernetics, Pensacola (pp. 85-88).
Fu, K., Kohno, T., Lopresti, D., Mynatt, E., Nahrstedt, K., Patel, S., & Zorn, B.
(2017). Safety, Security, and Privacy Threats Posed by Accelerating Trends in the
Internet of Things. Technical Report. Computing Community Consortium. http://cra.
org/ccc/wp-content/uploads/sites/2/2017/02/Safety-Security-and-Privacy-Threats-in-IoT.
pdf.
Goel, S. and Jindal, A., 2017. Evolving Cyber Security Challenges to the Smart Grid
Landscape.
Gomes, J.F., Iivari, M., Ahokangas, P., Isotalo, L. and Niemelä, R., 2017. Cybersecurity
Business Models for IoT-Mobile Device Management Services in Futures Digital
Hospitals. Journal of ICT Standardization, 5(1), pp.107-128.
Mertens, D. M., 2014. Research and evaluation in education and psychology: Integrating
diversity with quantitative, qualitative, and mixed methods. Sage publications.
O'Leary, Z., 2017. The essential guide to doing your research project. Sage.
Silverman, D. ed., 2016. Qualitative research. Sage.
Williamson, K. and Johanson, G. eds., 2017. Research Methods: Information, Systems,
and Contexts. Chandos Publishing.
21 | P a g e
Coffey, J. W. (2017). Ameliorating Sources of Human Error in CyberSecurity:
Technological and Human-Centered Approaches. In The 8th International Multi-
Conference on Complexity, Informatics and Cybernetics, Pensacola (pp. 85-88).
Fu, K., Kohno, T., Lopresti, D., Mynatt, E., Nahrstedt, K., Patel, S., & Zorn, B.
(2017). Safety, Security, and Privacy Threats Posed by Accelerating Trends in the
Internet of Things. Technical Report. Computing Community Consortium. http://cra.
org/ccc/wp-content/uploads/sites/2/2017/02/Safety-Security-and-Privacy-Threats-in-IoT.
pdf.
Goel, S. and Jindal, A., 2017. Evolving Cyber Security Challenges to the Smart Grid
Landscape.
Gomes, J.F., Iivari, M., Ahokangas, P., Isotalo, L. and Niemelä, R., 2017. Cybersecurity
Business Models for IoT-Mobile Device Management Services in Futures Digital
Hospitals. Journal of ICT Standardization, 5(1), pp.107-128.
Mertens, D. M., 2014. Research and evaluation in education and psychology: Integrating
diversity with quantitative, qualitative, and mixed methods. Sage publications.
O'Leary, Z., 2017. The essential guide to doing your research project. Sage.
Silverman, D. ed., 2016. Qualitative research. Sage.
Williamson, K. and Johanson, G. eds., 2017. Research Methods: Information, Systems,
and Contexts. Chandos Publishing.
21 | P a g e
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





