Professional Reflection: Enhancing Cybersecurity Training Programs
VerifiedAdded on 2023/06/11
|11
|2711
|444
Report
AI Summary
This report provides a professional reflection on cybersecurity strategies, focusing on training and development programs to mitigate cybercrimes within an organization. It addresses the importance of maintaining viability, integrity, and confidentiality in the face of growing cyber threats. The report uses Gibbs Reflective Cycle to analyze challenges encountered, such as data breaches and loss of customer trust, and discusses the implementation of strategies like risk assessment and Linux server administration to enhance cybersecurity. It highlights the significance of continuous training, collaboration with supervisors and tutors, and the development of essential skills to improve business operations, protect sensitive information, and strengthen the overall cybersecurity framework. The reflection concludes with a professional development plan, outlining actions and resources needed for career advancement in cybersecurity.

Professional Reflection
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
INTRODUCTION...........................................................................................................................3
TASK...............................................................................................................................................4
CONCLUSION................................................................................................................................5
REFERENCES................................................................................................................................6
INTRODUCTION...........................................................................................................................3
TASK...............................................................................................................................................4
CONCLUSION................................................................................................................................5
REFERENCES................................................................................................................................6

INTRODUCTION
Professionalism is known as a formal work of conduct which helps in the better functioning of
the business and this can also impact in the career of any individual. Being professional in the
business is important for maintaining the decorum of the business and this also helps in building
a positive environment in the business. As there are many characteristics for being professional
in the business for the better performance of the business and the individual in the business. AS
this report is basically a professional reflection on the strategies which is related to the
cybersecurity and which is performed and delivered for the better functioning of training and this
can also help the employees for the reduction of the rate in cybercrimes. As Cybercrime is the
important part to be considered in a business as this is against the growing changes for cyber-
attack. As by protecting the employees form this threat can improve the security of the team
members and this can also help in enhancing the performance level of the business. These can be
reduced by training and development of the employees.
Professionalism is known as a formal work of conduct which helps in the better functioning of
the business and this can also impact in the career of any individual. Being professional in the
business is important for maintaining the decorum of the business and this also helps in building
a positive environment in the business. As there are many characteristics for being professional
in the business for the better performance of the business and the individual in the business. AS
this report is basically a professional reflection on the strategies which is related to the
cybersecurity and which is performed and delivered for the better functioning of training and this
can also help the employees for the reduction of the rate in cybercrimes. As Cybercrime is the
important part to be considered in a business as this is against the growing changes for cyber-
attack. As by protecting the employees form this threat can improve the security of the team
members and this can also help in enhancing the performance level of the business. These can be
reduced by training and development of the employees.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

TASK
Reflective practice
As on the organisational context I was facing the issues regarding cybercrimes and it is important
to control in an organisation for the better an effective environment of business as cyber security
is important to be imposed in the business as this helps in the better protection with the
unauthorized data and the networks and technologies presented in the business. As per my
observation there are basically three fundamentals as these are viability, integrity and
confidentiality(Kimani, Oduol, and Langat, 2019). As organisation is requires to provide the best
security to their employees and this can result helpful and also helps in attaining the
organisational aims and objectives of business as in an organisation their various kind of cyber
crimes which is faced by the employees and this can also impact in decreasing the customer base
of the business and this can also impact in the revenue growth of the business. As there are
various breaches which can impact in the business and this can also see on the way of data loss,
leaking and hacking of the data of the clients in the clients in a business as this is considered as
the basic and on going issue in the business which is impacting in the profit of business.
Gibbs Reflective cycle
As this is the model which I usually prefer to use for the organisational problems which is related
to the cyber crimes occurring in business as this model is considered as the better way of
working in an experience as there are various situation which can be applied for managing and
analysing the experience as there are various stages which is involved in this model and this has
helped me in dealing with various situations in the organisations(Nayyar, Jain, and Singh, 2019).
As these stages are description as it is the cybercrime issue which is facing by the team members
of the business and next stage is feeling as the employees are not feeling secure with there job by
seeing the increasing cybercrimes in the business as it is increasing in high rates and they are not
unable to manage effectively. As evaluation is the next stage of this model as this involves all the
experience which is collected for the final decision and observation as the majority has resulted
bad for this issue in the business and assisted for the new strategy for the better understanding of
this issue. Next stage is analysation as this is a step in which all the situation make sense for the
better analysation of the issue. After this conclusion is made of the things learned and the
changes made regarding the issues which can impact in the action plan of the business so that
Reflective practice
As on the organisational context I was facing the issues regarding cybercrimes and it is important
to control in an organisation for the better an effective environment of business as cyber security
is important to be imposed in the business as this helps in the better protection with the
unauthorized data and the networks and technologies presented in the business. As per my
observation there are basically three fundamentals as these are viability, integrity and
confidentiality(Kimani, Oduol, and Langat, 2019). As organisation is requires to provide the best
security to their employees and this can result helpful and also helps in attaining the
organisational aims and objectives of business as in an organisation their various kind of cyber
crimes which is faced by the employees and this can also impact in decreasing the customer base
of the business and this can also impact in the revenue growth of the business. As there are
various breaches which can impact in the business and this can also see on the way of data loss,
leaking and hacking of the data of the clients in the clients in a business as this is considered as
the basic and on going issue in the business which is impacting in the profit of business.
Gibbs Reflective cycle
As this is the model which I usually prefer to use for the organisational problems which is related
to the cyber crimes occurring in business as this model is considered as the better way of
working in an experience as there are various situation which can be applied for managing and
analysing the experience as there are various stages which is involved in this model and this has
helped me in dealing with various situations in the organisations(Nayyar, Jain, and Singh, 2019).
As these stages are description as it is the cybercrime issue which is facing by the team members
of the business and next stage is feeling as the employees are not feeling secure with there job by
seeing the increasing cybercrimes in the business as it is increasing in high rates and they are not
unable to manage effectively. As evaluation is the next stage of this model as this involves all the
experience which is collected for the final decision and observation as the majority has resulted
bad for this issue in the business and assisted for the new strategy for the better understanding of
this issue. Next stage is analysation as this is a step in which all the situation make sense for the
better analysation of the issue. After this conclusion is made of the things learned and the
changes made regarding the issues which can impact in the action plan of the business so that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
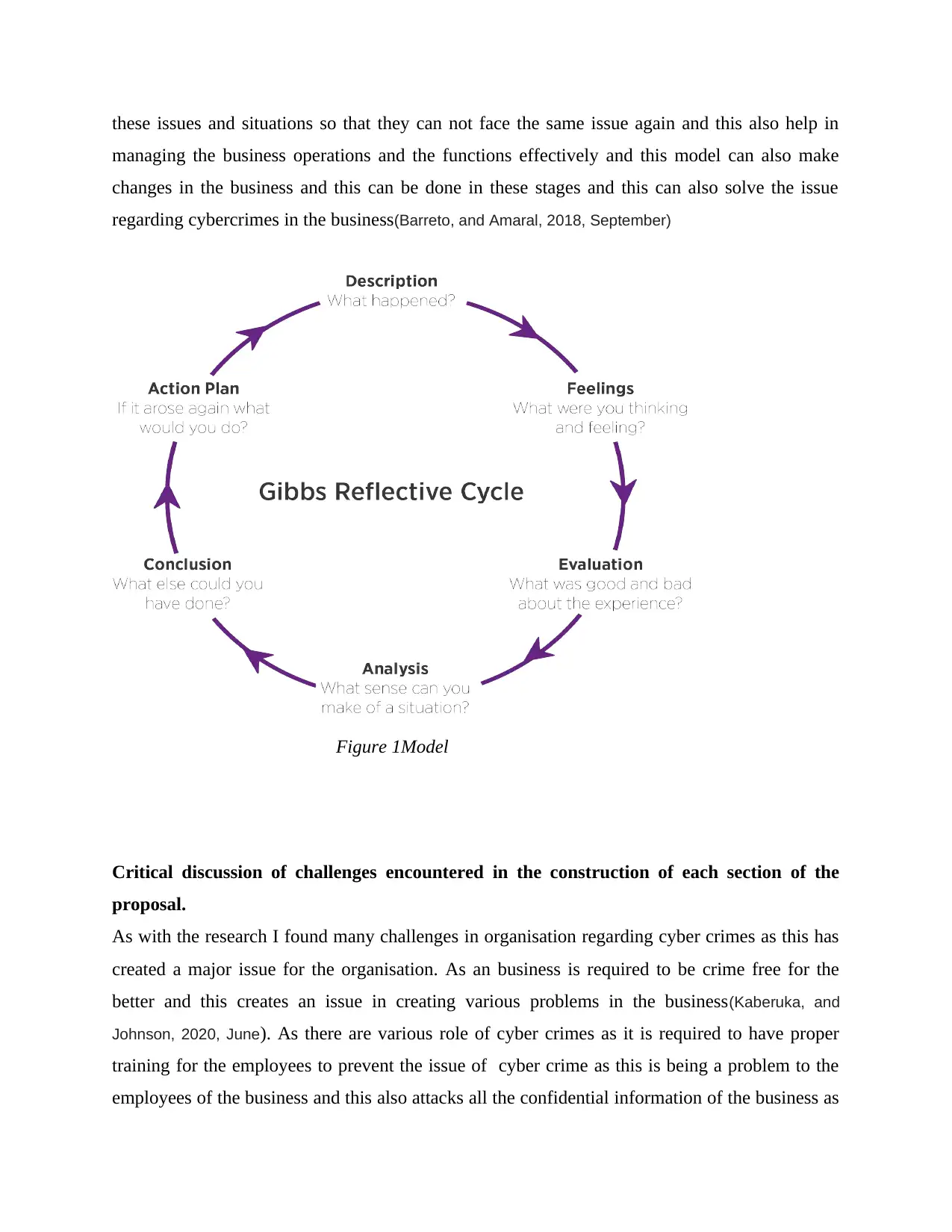
these issues and situations so that they can not face the same issue again and this also help in
managing the business operations and the functions effectively and this model can also make
changes in the business and this can be done in these stages and this can also solve the issue
regarding cybercrimes in the business(Barreto, and Amaral, 2018, September)
Figure 1Model
Critical discussion of challenges encountered in the construction of each section of the
proposal.
As with the research I found many challenges in organisation regarding cyber crimes as this has
created a major issue for the organisation. As an business is required to be crime free for the
better and this creates an issue in creating various problems in the business(Kaberuka, and
Johnson, 2020, June). As there are various role of cyber crimes as it is required to have proper
training for the employees to prevent the issue of cyber crime as this is being a problem to the
employees of the business and this also attacks all the confidential information of the business as
managing the business operations and the functions effectively and this model can also make
changes in the business and this can be done in these stages and this can also solve the issue
regarding cybercrimes in the business(Barreto, and Amaral, 2018, September)
Figure 1Model
Critical discussion of challenges encountered in the construction of each section of the
proposal.
As with the research I found many challenges in organisation regarding cyber crimes as this has
created a major issue for the organisation. As an business is required to be crime free for the
better and this creates an issue in creating various problems in the business(Kaberuka, and
Johnson, 2020, June). As there are various role of cyber crimes as it is required to have proper
training for the employees to prevent the issue of cyber crime as this is being a problem to the
employees of the business and this also attacks all the confidential information of the business as

on the basis if external and internal related information in the information technology as this is
also impacting in the reputation of the business and for this training and development program is
launched for the better and effective formation of the resources and this can also secure the
business from the attacks and the data breaches and this also impacts in the cybersecurity of the
business and this also creates an bad environment and this is also giving an bad experience to the
customers as this can also impact in the information technology as this can occur an stolen
information and also creates an issue for the unauthorized data as this is also impacting in the
business operations and functions and this is also effecting the profitability and productibility
level of business(Culot, Fattori, and Sartor, 2019). The influenced performance can be in the form
of development and management of business. As in an organisation I had faced many issue
regarding the cybercrimes problems facing by the employees of the business and this is also
impacting in the performance of the employees and this is also leading in the decreased level of
productivity(Carnovale, and Yeniyurt, 2021).
Critical discussion of your interaction and use of support supervisors/ peers and tutors.
As per the research topic I had observed that all the support and analysed as per the support of
the tutors in the business as this is considered as the important topic which is required to take
into consideration and this can be done by top management and it is proceeded by analysing all
the current issues of the organisation in the meeting as this can also helps in attaining the
organisational goals and objectives effectively by giving training to the employees and this is
also imposed with the meeting with top management and in this it involves all the source of
knowledge and motivation to the employees and as tutors are most helpful and this is created a
proposal for the better maintains and this also helps in developing the changes in the organisation
and in between team members in an effective manner as because of this issue facing by the
employees effecting by cyber crimes and this can be done by proper training and development
program and this can also be resolved by using various strategies which can help in reducing the
rate of the cyber crime in the business as the training of the employees will let them know about
the IT vulnerabilities and the regarding risk as this can impact in reducing the rate of cyber crime
in the business and this can be provided on online which will be more convenient to the
customers and for the better management as by training session and the development it also helps
in encouraging all the standards and this also helps in strengthening all the framework in the
also impacting in the reputation of the business and for this training and development program is
launched for the better and effective formation of the resources and this can also secure the
business from the attacks and the data breaches and this also impacts in the cybersecurity of the
business and this also creates an bad environment and this is also giving an bad experience to the
customers as this can also impact in the information technology as this can occur an stolen
information and also creates an issue for the unauthorized data as this is also impacting in the
business operations and functions and this is also effecting the profitability and productibility
level of business(Culot, Fattori, and Sartor, 2019). The influenced performance can be in the form
of development and management of business. As in an organisation I had faced many issue
regarding the cybercrimes problems facing by the employees of the business and this is also
impacting in the performance of the employees and this is also leading in the decreased level of
productivity(Carnovale, and Yeniyurt, 2021).
Critical discussion of your interaction and use of support supervisors/ peers and tutors.
As per the research topic I had observed that all the support and analysed as per the support of
the tutors in the business as this is considered as the important topic which is required to take
into consideration and this can be done by top management and it is proceeded by analysing all
the current issues of the organisation in the meeting as this can also helps in attaining the
organisational goals and objectives effectively by giving training to the employees and this is
also imposed with the meeting with top management and in this it involves all the source of
knowledge and motivation to the employees and as tutors are most helpful and this is created a
proposal for the better maintains and this also helps in developing the changes in the organisation
and in between team members in an effective manner as because of this issue facing by the
employees effecting by cyber crimes and this can be done by proper training and development
program and this can also be resolved by using various strategies which can help in reducing the
rate of the cyber crime in the business as the training of the employees will let them know about
the IT vulnerabilities and the regarding risk as this can impact in reducing the rate of cyber crime
in the business and this can be provided on online which will be more convenient to the
customers and for the better management as by training session and the development it also helps
in encouraging all the standards and this also helps in strengthening all the framework in the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

business and this also creates an mechanism for protecting the society and also the confidential
information regarding the same and this can also protect the employees from the threat. As in an
organisation it is important to manage all the activities according for the better functioning of the
business operations and this can also help in strengthening the standard of the business and by
training system of the employees helps in securing the ecosystem of the business and this also
strengthens the framework of the business(Idrissi, Mezrioui, and Belmekki, 2019, October). As it is
important to have an story cyber system of eco in the business for developing the better structure
and this can also helps in the authentication, automation and interoperability of the business
effectively(Arora, Manglani, and Choudhary, 2022, March).
Critical discussion of skills required for the successful construction of the proposal.
As there are various skills which is required for making the cyber security training session to the
employees for the better development and progress and knowledge to the employees(Thakur,
Hayajneh, and Tseng, 2019). As risk assessment is the first skills which is important to be in the
top management for the better results of the skills and management in the business as it is
important the decide the matter and methods which is required for analysing the issue and this
can also result helpful in finding the trouble as this skill basically analyses all the skill set
regarding this issue in identifying and prioritizing the defence system and this can also solve the
risk of the business and can also resolve this in an proactive and effective manner for the better
adjustment of the issue(Mandal, Sabitha, and Mehrotra, 2022). As Linux server administration is
also the skill as this also help in the familiarizing the issue regarding the cyber issue of the
business as this is basically the skill set of framework which helps in the better understanding
and this also helps in adapting the employees of the business as by this skill set they can easily
scan there network and also helps in operating the system of the business effectively and this is
an important skill which can be modified according to the issue and this can also make the
professional working on the cybersecurity tool(Yu, and Guo, 2019, August).
Critical discussion of lessons learnt from the process and strategies to adopt to move
forward.
As by implementing the above strategies and the process of the cybersecurity I have learned that
this could helps in the better functioning of the business operations and the functions which can
information regarding the same and this can also protect the employees from the threat. As in an
organisation it is important to manage all the activities according for the better functioning of the
business operations and this can also help in strengthening the standard of the business and by
training system of the employees helps in securing the ecosystem of the business and this also
strengthens the framework of the business(Idrissi, Mezrioui, and Belmekki, 2019, October). As it is
important to have an story cyber system of eco in the business for developing the better structure
and this can also helps in the authentication, automation and interoperability of the business
effectively(Arora, Manglani, and Choudhary, 2022, March).
Critical discussion of skills required for the successful construction of the proposal.
As there are various skills which is required for making the cyber security training session to the
employees for the better development and progress and knowledge to the employees(Thakur,
Hayajneh, and Tseng, 2019). As risk assessment is the first skills which is important to be in the
top management for the better results of the skills and management in the business as it is
important the decide the matter and methods which is required for analysing the issue and this
can also result helpful in finding the trouble as this skill basically analyses all the skill set
regarding this issue in identifying and prioritizing the defence system and this can also solve the
risk of the business and can also resolve this in an proactive and effective manner for the better
adjustment of the issue(Mandal, Sabitha, and Mehrotra, 2022). As Linux server administration is
also the skill as this also help in the familiarizing the issue regarding the cyber issue of the
business as this is basically the skill set of framework which helps in the better understanding
and this also helps in adapting the employees of the business as by this skill set they can easily
scan there network and also helps in operating the system of the business effectively and this is
an important skill which can be modified according to the issue and this can also make the
professional working on the cybersecurity tool(Yu, and Guo, 2019, August).
Critical discussion of lessons learnt from the process and strategies to adopt to move
forward.
As by implementing the above strategies and the process of the cybersecurity I have learned that
this could helps in the better functioning of the business operations and the functions which can
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
helps in increasing the level of profitability and productibility of the business and this can also
help in operating the functions and protections easily and this can also be done by strategy name
Waracle ltd. As there are various options which can be applied as a solution as this also helps in
ensuring the risk of the business as this eliminates the threat of the business and this can also
increase in the potential output of the business as this can be done by focussing on the skill set
which can solve the issue as this can also prevent the sensitive information as this can also helps
in preventing all the tracking and snooping all the employee data as this can also increase the
brand reputation(Suryotrisongko, and Musashi, 2019, November).
Professional development plan
Actions Resources
required
Planned
start
date
Planned
end
date
Actual
start
date
Actual
end
date
Evidence of
outcome
Review
date
Actions
following
reviews
Career
or
personal
goal
Developing
skills
E
learning
skills
June August July Sept feedbacks Aug success Career
goal
Research
skills
E
learning
module
July sep oct nov reactions oct Goal
oriented
Personal
and
both
career
goal.
Problem
solving
Learning
essentials
jan march feb April Discussion
review
March No
action
Personal
goal
Self
managing
skills
Learning
subject
june august June august Informal
and formal
appraisal
aug No
action
Career
goal
Data
analytics
Module
working
mar may April June Performance
potential
April success Personal
goal
help in operating the functions and protections easily and this can also be done by strategy name
Waracle ltd. As there are various options which can be applied as a solution as this also helps in
ensuring the risk of the business as this eliminates the threat of the business and this can also
increase in the potential output of the business as this can be done by focussing on the skill set
which can solve the issue as this can also prevent the sensitive information as this can also helps
in preventing all the tracking and snooping all the employee data as this can also increase the
brand reputation(Suryotrisongko, and Musashi, 2019, November).
Professional development plan
Actions Resources
required
Planned
start
date
Planned
end
date
Actual
start
date
Actual
end
date
Evidence of
outcome
Review
date
Actions
following
reviews
Career
or
personal
goal
Developing
skills
E
learning
skills
June August July Sept feedbacks Aug success Career
goal
Research
skills
E
learning
module
July sep oct nov reactions oct Goal
oriented
Personal
and
both
career
goal.
Problem
solving
Learning
essentials
jan march feb April Discussion
review
March No
action
Personal
goal
Self
managing
skills
Learning
subject
june august June august Informal
and formal
appraisal
aug No
action
Career
goal
Data
analytics
Module
working
mar may April June Performance
potential
April success Personal
goal

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CONCLUSION
This report has concluded that it is important to focus on the issue regarding the cyber security in
the business which can further helps in better functioning and development of the business
operations as this can helps in better identifying the vulnerabilities of the business and this can
also limits all the risk regarding cyber crimes and this can further help in developing all the
security of the organisation with the effective protocols which can result beneficial and also
gives an advantage to the business. As it is important for the professional to known about the
required part of the business which can further helps the business in gaining success and this also
helps in attaining organisation goal and profit in the business.
This report has concluded that it is important to focus on the issue regarding the cyber security in
the business which can further helps in better functioning and development of the business
operations as this can helps in better identifying the vulnerabilities of the business and this can
also limits all the risk regarding cyber crimes and this can further help in developing all the
security of the organisation with the effective protocols which can result beneficial and also
gives an advantage to the business. As it is important for the professional to known about the
required part of the business which can further helps the business in gaining success and this also
helps in attaining organisation goal and profit in the business.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and Journals
Kimani, K., Oduol, V. and Langat, K., 2019. Cyber security challenges for IoT-based smart grid
networks. International Journal of Critical Infrastructure Protection, 25, pp.36-49.
Nayyar, A., Jain, R and Singh, A., 2019. Cyber security challenges for smart cities. In Driving the
Development, Management, and Sustainability of Cognitive Cities (pp. 27-54). IGI Global.
Barreto, L. and Amaral, A., 2018, September. Smart farming: Cyber security challenges. In 2018
International Conference on Intelligent Systems (IS) (pp. 870-876). IEEE.
Culot, G., Fattori, F and Sartor, M., 2019. Addressing industry 4.0 cybersecurity challenges. IEEE
Engineering Management Review, 47(3), pp.79-86.
Idrissi, O.E., Mezrioui, A. and Belmekki, A., 2019, October. Cyber security challenges and issues of
industrial control systems–some security recommendations. In 2019 IEEE International Smart Cities
Conference (ISC2) (pp. 330-335). IEEE.
Arora, H., Manglani, T and Choudhary, S., 2022, March. Cyber Security Challenges and Trends on
Recent Technologies. In 2022 6th International Conference on Computing Methodologies and
Communication (ICCMC) (pp. 115-118). IEEE.
Mandal, S., Sabitha, A.S. and Mehrotra, D., 2022. A Review for Cyber Security Challenges on Big Data
Using Machine Learning Techniques. In ICT and Data Sciences (pp. 135-148). CRC Press.
Yu, X. and Guo, H., 2019, August. A survey on IIoT security. In 2019 IEEE VTS Asia Pacific Wireless
Communications Symposium (APWCS) (pp. 1-5). IEEE.
Suryotrisongko, H. and Musashi, Y., 2019, November. Review of cybersecurity research topics, taxonomy
and challenges: Interdisciplinary perspective. In 2019 IEEE 12th Conference on Service-Oriented
Computing and Applications (SOCA) (pp. 162-167). IEEE.
Thakur, K., Hayajneh, T. and Tseng, J., 2019. Cyber security in social media: challenges and the way
forward. IT Professional, 21(2), pp.41-49.
Carnovale, S. and Yeniyurt, S. eds., 2021. Cyber Security And Supply Chain Management: Risks,
Challenges, And Solutions (Vol. 1). World Scientific.
Kaberuka, J. and Johnson, C., 2020, June. Adapting STPA-sec for Socio-technical Cyber Security
Challenges in Emerging Nations: A Case Study in Risk Management for Rwandan Health Care. In 2020
International Conference on Cyber Security and Protection of Digital Services (Cyber Security) (pp. 1-9).
IEEE.
Books and Journals
Kimani, K., Oduol, V. and Langat, K., 2019. Cyber security challenges for IoT-based smart grid
networks. International Journal of Critical Infrastructure Protection, 25, pp.36-49.
Nayyar, A., Jain, R and Singh, A., 2019. Cyber security challenges for smart cities. In Driving the
Development, Management, and Sustainability of Cognitive Cities (pp. 27-54). IGI Global.
Barreto, L. and Amaral, A., 2018, September. Smart farming: Cyber security challenges. In 2018
International Conference on Intelligent Systems (IS) (pp. 870-876). IEEE.
Culot, G., Fattori, F and Sartor, M., 2019. Addressing industry 4.0 cybersecurity challenges. IEEE
Engineering Management Review, 47(3), pp.79-86.
Idrissi, O.E., Mezrioui, A. and Belmekki, A., 2019, October. Cyber security challenges and issues of
industrial control systems–some security recommendations. In 2019 IEEE International Smart Cities
Conference (ISC2) (pp. 330-335). IEEE.
Arora, H., Manglani, T and Choudhary, S., 2022, March. Cyber Security Challenges and Trends on
Recent Technologies. In 2022 6th International Conference on Computing Methodologies and
Communication (ICCMC) (pp. 115-118). IEEE.
Mandal, S., Sabitha, A.S. and Mehrotra, D., 2022. A Review for Cyber Security Challenges on Big Data
Using Machine Learning Techniques. In ICT and Data Sciences (pp. 135-148). CRC Press.
Yu, X. and Guo, H., 2019, August. A survey on IIoT security. In 2019 IEEE VTS Asia Pacific Wireless
Communications Symposium (APWCS) (pp. 1-5). IEEE.
Suryotrisongko, H. and Musashi, Y., 2019, November. Review of cybersecurity research topics, taxonomy
and challenges: Interdisciplinary perspective. In 2019 IEEE 12th Conference on Service-Oriented
Computing and Applications (SOCA) (pp. 162-167). IEEE.
Thakur, K., Hayajneh, T. and Tseng, J., 2019. Cyber security in social media: challenges and the way
forward. IT Professional, 21(2), pp.41-49.
Carnovale, S. and Yeniyurt, S. eds., 2021. Cyber Security And Supply Chain Management: Risks,
Challenges, And Solutions (Vol. 1). World Scientific.
Kaberuka, J. and Johnson, C., 2020, June. Adapting STPA-sec for Socio-technical Cyber Security
Challenges in Emerging Nations: A Case Study in Risk Management for Rwandan Health Care. In 2020
International Conference on Cyber Security and Protection of Digital Services (Cyber Security) (pp. 1-9).
IEEE.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





