Computer Security Report: Addressing Cybersecurity for JL Company
VerifiedAdded on 2023/06/03
|13
|2416
|109
Report
AI Summary
This report addresses the cybersecurity vulnerabilities faced by the JL organization, a small accounting firm in Perth, Australia. The firm is experiencing performance issues, malware, and potential cyberattacks. The report identifies key threats such as ransomware, DOS/DDOS attacks, poor passwords, and phishing, detailing their impact and mechanisms. It then explores various methods to mitigate these risks, including encryption, cryptography, firewalls, and antivirus software. A comparative analysis highlights the benefits of encryption and cryptography over alternative solutions, considering cost-effectiveness and data security. The report also provides a breakdown of the costs associated with implementing these security measures and concludes with recommendations for enhancing JL's overall cybersecurity posture. The report emphasizes the importance of proactive security measures to protect the company's data and ensure business continuity.

Running Head: COMPUTER SECURITY
0
Computer Security
0
Computer Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER SECURITY
1
Contents
Introduction...........................................................................................................................................2
Cybersecurity issues..............................................................................................................................2
Ransomware attack...........................................................................................................................2
DOS and DDOS attack........................................................................................................................3
Poor passwords.................................................................................................................................4
Phishing.............................................................................................................................................4
Unprecedented Attacks.....................................................................................................................5
Methods to reduce the cybersecurity issues.........................................................................................6
Encryption method............................................................................................................................6
Cryptography.....................................................................................................................................7
Firewall software...............................................................................................................................8
Antivirus and backup plans................................................................................................................8
Comparison of the chosen solution and alternative solutions...............................................................8
Breakdown of the cost of addressing the security issue........................................................................9
Conclusion...........................................................................................................................................10
References...........................................................................................................................................11
1
Contents
Introduction...........................................................................................................................................2
Cybersecurity issues..............................................................................................................................2
Ransomware attack...........................................................................................................................2
DOS and DDOS attack........................................................................................................................3
Poor passwords.................................................................................................................................4
Phishing.............................................................................................................................................4
Unprecedented Attacks.....................................................................................................................5
Methods to reduce the cybersecurity issues.........................................................................................6
Encryption method............................................................................................................................6
Cryptography.....................................................................................................................................7
Firewall software...............................................................................................................................8
Antivirus and backup plans................................................................................................................8
Comparison of the chosen solution and alternative solutions...............................................................8
Breakdown of the cost of addressing the security issue........................................................................9
Conclusion...........................................................................................................................................10
References...........................................................................................................................................11

COMPUTER SECURITY
2
Introduction
Security of data or information is a very common problem for JL organization
and in the last five years the problem of cybersecurity has increased. The JL
organization started their company with few employees and it provides various kinds of
online services to their customers and currently, only five people are working in this
organization (Abomhara, & Køien, 2015). The main purpose of this report is to
understand the fundamental concept of cybersecurity issues and methods to address
the issues of computer securities. In the last few months, the employees of JL
organization was facing the issue of performance, computer systems were not working
properly and some malware are observed on the server of JL. The employees and
manager of JL Company use D-link wireless routers which are very less secure and
hackers use malicious software to block the networks of JL organization. This report is
divided into four parts such as cybersecurity issues, methods to address these issues, a
comparison between chosen methods and alternative approaches and cost of
technologies or software.
Cybersecurity issues
There are many kinds of cybersecurity issues and threats identified that are
faced by JL organization and their employees:
Ransomware attack
It is a very common security threat and cyber-attack which is a very serious
problem for JL organization. It is a type of virus that attacks human peripheral devices
like computer and mobile (AbouZahr, et al., 2015). In which first hackers send
unwanted signals or mails to JL employees and after that, they collect all relevant data,
for example, IP address and type of data links. Attackers use malware and botnet
process to block the servers of JL and they store all personal information of consumers.
At the end of ransomware attack hackers communicate with consumers and employees
of JL through social Media and demand money to restore back their data. The employees
of JL Company has identified that their data files and computer networks were
corrupted and encrypted by attackers (Buczak, & Guven, 2016). Due to this kind of
cyber issue the performance and efficiency of computer networks are also decreased.
2
Introduction
Security of data or information is a very common problem for JL organization
and in the last five years the problem of cybersecurity has increased. The JL
organization started their company with few employees and it provides various kinds of
online services to their customers and currently, only five people are working in this
organization (Abomhara, & Køien, 2015). The main purpose of this report is to
understand the fundamental concept of cybersecurity issues and methods to address
the issues of computer securities. In the last few months, the employees of JL
organization was facing the issue of performance, computer systems were not working
properly and some malware are observed on the server of JL. The employees and
manager of JL Company use D-link wireless routers which are very less secure and
hackers use malicious software to block the networks of JL organization. This report is
divided into four parts such as cybersecurity issues, methods to address these issues, a
comparison between chosen methods and alternative approaches and cost of
technologies or software.
Cybersecurity issues
There are many kinds of cybersecurity issues and threats identified that are
faced by JL organization and their employees:
Ransomware attack
It is a very common security threat and cyber-attack which is a very serious
problem for JL organization. It is a type of virus that attacks human peripheral devices
like computer and mobile (AbouZahr, et al., 2015). In which first hackers send
unwanted signals or mails to JL employees and after that, they collect all relevant data,
for example, IP address and type of data links. Attackers use malware and botnet
process to block the servers of JL and they store all personal information of consumers.
At the end of ransomware attack hackers communicate with consumers and employees
of JL through social Media and demand money to restore back their data. The employees
of JL Company has identified that their data files and computer networks were
corrupted and encrypted by attackers (Buczak, & Guven, 2016). Due to this kind of
cyber issue the performance and efficiency of computer networks are also decreased.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER SECURITY
3
Figure: ransomware attack steps
(Source: Gupta, Agrawal, & Yamaguchi, 2016)
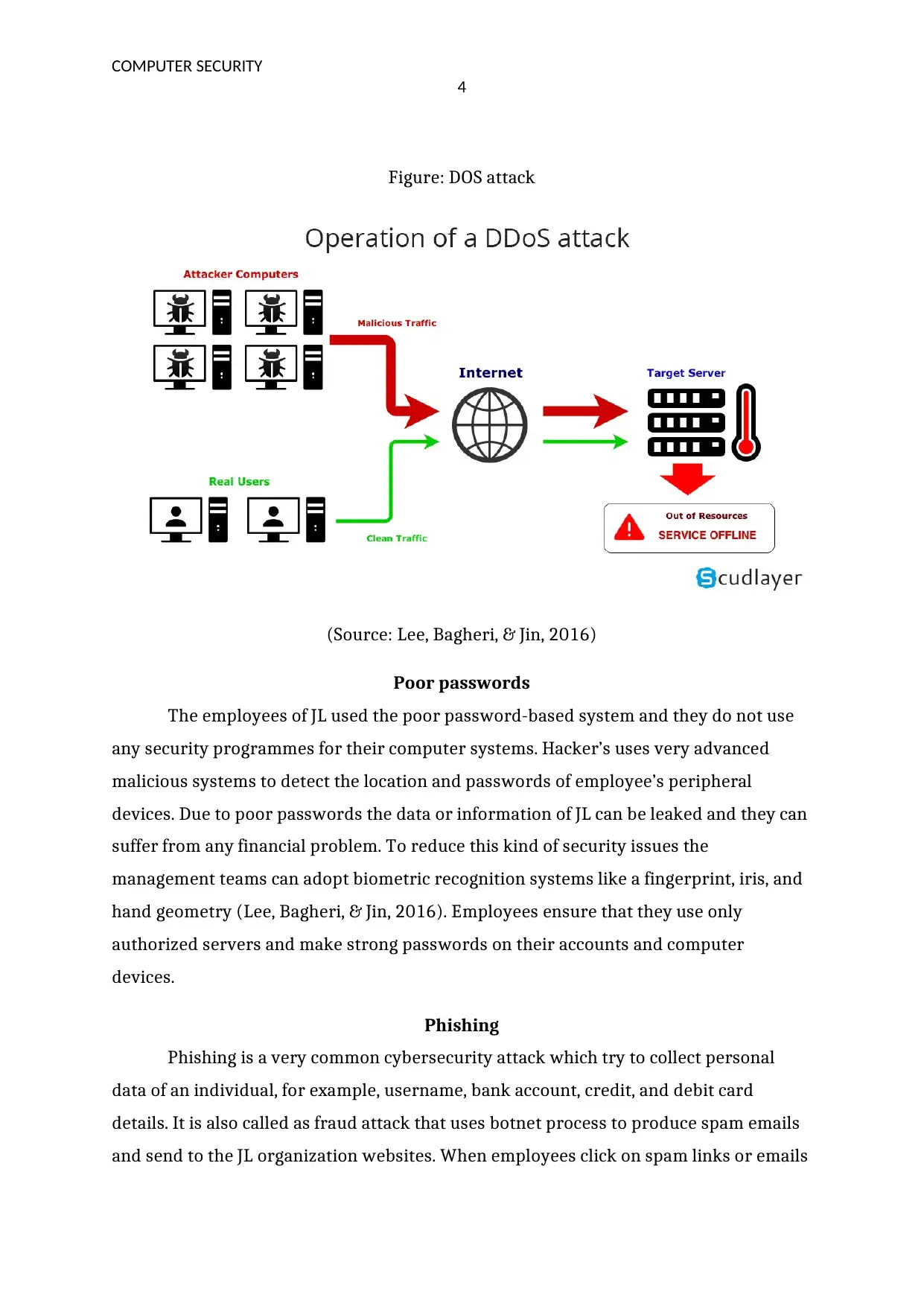
DOS and DDOS attack
DOS is defined as a denial of services attack that is a very serious problem in the
field of computer networks. In which hackers produce a large number of traffic signals
and unwanted data with the help of malware software. JL organization faced the
problem of DOS and DDOS because their employees use unauthorized websites. It is
identified the JL community use wireless networks for communication purpose but they
do not use any security system due to which the problem of DOS attack has occurred. In
DOS attack hackers use flooding process and generate complex algorithm to block the
servers of JL organization.
3
Figure: ransomware attack steps
(Source: Gupta, Agrawal, & Yamaguchi, 2016)
DOS and DDOS attack
DOS is defined as a denial of services attack that is a very serious problem in the
field of computer networks. In which hackers produce a large number of traffic signals
and unwanted data with the help of malware software. JL organization faced the
problem of DOS and DDOS because their employees use unauthorized websites. It is
identified the JL community use wireless networks for communication purpose but they
do not use any security system due to which the problem of DOS attack has occurred. In
DOS attack hackers use flooding process and generate complex algorithm to block the
servers of JL organization.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COMPUTER SECURITY
4
Figure: DOS attack
(Source: Lee, Bagheri, & Jin, 2016)
Poor passwords
The employees of JL used the poor password-based system and they do not use
any security programmes for their computer systems. Hacker’s uses very advanced
malicious systems to detect the location and passwords of employee’s peripheral
devices. Due to poor passwords the data or information of JL can be leaked and they can
suffer from any financial problem. To reduce this kind of security issues the
management teams can adopt biometric recognition systems like a fingerprint, iris, and
hand geometry (Lee, Bagheri, & Jin, 2016). Employees ensure that they use only
authorized servers and make strong passwords on their accounts and computer
devices.
Phishing
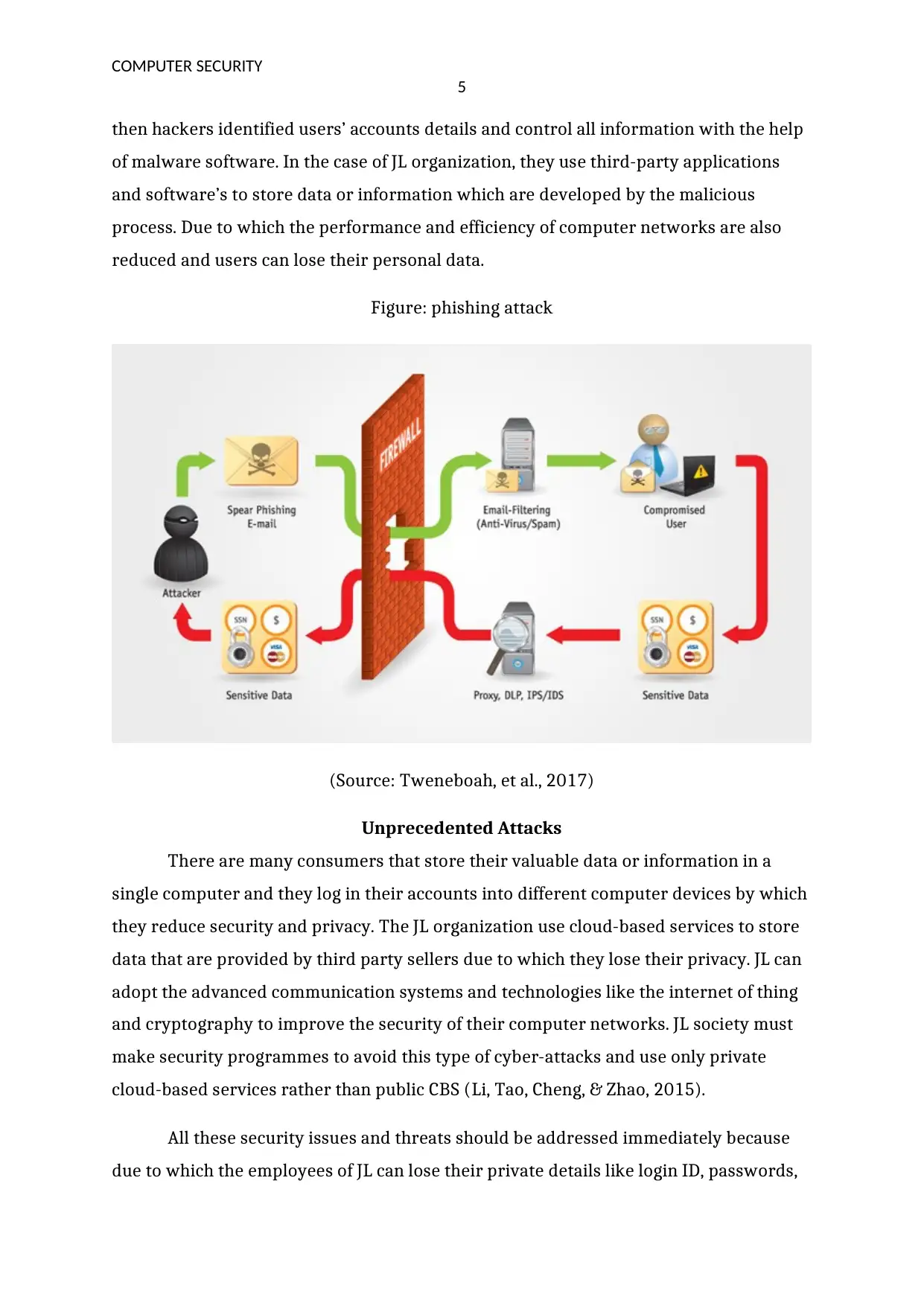
Phishing is a very common cybersecurity attack which try to collect personal
data of an individual, for example, username, bank account, credit, and debit card
details. It is also called as fraud attack that uses botnet process to produce spam emails
and send to the JL organization websites. When employees click on spam links or emails
4
Figure: DOS attack
(Source: Lee, Bagheri, & Jin, 2016)
Poor passwords
The employees of JL used the poor password-based system and they do not use
any security programmes for their computer systems. Hacker’s uses very advanced
malicious systems to detect the location and passwords of employee’s peripheral
devices. Due to poor passwords the data or information of JL can be leaked and they can
suffer from any financial problem. To reduce this kind of security issues the
management teams can adopt biometric recognition systems like a fingerprint, iris, and
hand geometry (Lee, Bagheri, & Jin, 2016). Employees ensure that they use only
authorized servers and make strong passwords on their accounts and computer
devices.
Phishing
Phishing is a very common cybersecurity attack which try to collect personal
data of an individual, for example, username, bank account, credit, and debit card
details. It is also called as fraud attack that uses botnet process to produce spam emails
and send to the JL organization websites. When employees click on spam links or emails
COMPUTER SECURITY
5
then hackers identified users’ accounts details and control all information with the help
of malware software. In the case of JL organization, they use third-party applications
and software’s to store data or information which are developed by the malicious
process. Due to which the performance and efficiency of computer networks are also
reduced and users can lose their personal data.
Figure: phishing attack
(Source: Tweneboah, et al., 2017)
Unprecedented Attacks
There are many consumers that store their valuable data or information in a
single computer and they log in their accounts into different computer devices by which
they reduce security and privacy. The JL organization use cloud-based services to store
data that are provided by third party sellers due to which they lose their privacy. JL can
adopt the advanced communication systems and technologies like the internet of thing
and cryptography to improve the security of their computer networks. JL society must
make security programmes to avoid this type of cyber-attacks and use only private
cloud-based services rather than public CBS (Li, Tao, Cheng, & Zhao, 2015).
All these security issues and threats should be addressed immediately because
due to which the employees of JL can lose their private details like login ID, passwords,
5
then hackers identified users’ accounts details and control all information with the help
of malware software. In the case of JL organization, they use third-party applications
and software’s to store data or information which are developed by the malicious
process. Due to which the performance and efficiency of computer networks are also
reduced and users can lose their personal data.
Figure: phishing attack
(Source: Tweneboah, et al., 2017)
Unprecedented Attacks
There are many consumers that store their valuable data or information in a
single computer and they log in their accounts into different computer devices by which
they reduce security and privacy. The JL organization use cloud-based services to store
data that are provided by third party sellers due to which they lose their privacy. JL can
adopt the advanced communication systems and technologies like the internet of thing
and cryptography to improve the security of their computer networks. JL society must
make security programmes to avoid this type of cyber-attacks and use only private
cloud-based services rather than public CBS (Li, Tao, Cheng, & Zhao, 2015).
All these security issues and threats should be addressed immediately because
due to which the employees of JL can lose their private details like login ID, passwords,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER SECURITY
6
and bank details. Data breach is a very common problem for an organization and it
occurs due to all these security threats and risks.
Methods to reduce the cybersecurity issues
Information technology has developed various kinds of techniques and
processes to address the issues and threats of cyber security which are described
below:
Figure: cybersecurity strategies
(Source: Min, Chai, & Han, 2015)
Encryption method
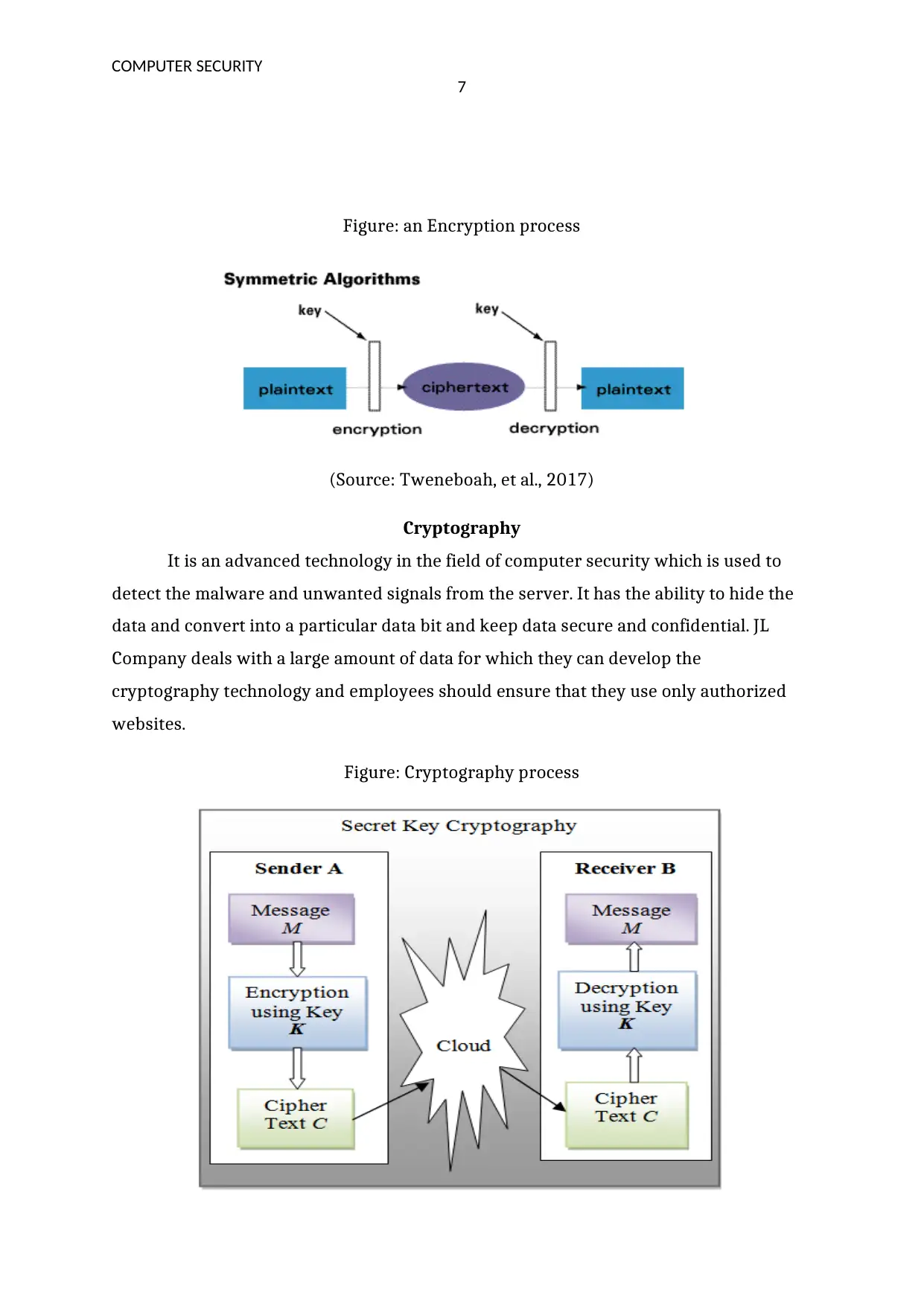
It is one of the most common processes to address security issues and many
organizations use this technology. Hackers use malicious software to block the
computer networks and servers and they collect data. In this technique, the data or
signals converted into a form of code which is transmitted from one source to other. The
main advantage of this process is that hackers are not able to decrypt the input code
without permission and JL organization can adopt this method to improve the privacy of
signals.
6
and bank details. Data breach is a very common problem for an organization and it
occurs due to all these security threats and risks.
Methods to reduce the cybersecurity issues
Information technology has developed various kinds of techniques and
processes to address the issues and threats of cyber security which are described
below:
Figure: cybersecurity strategies
(Source: Min, Chai, & Han, 2015)
Encryption method
It is one of the most common processes to address security issues and many
organizations use this technology. Hackers use malicious software to block the
computer networks and servers and they collect data. In this technique, the data or
signals converted into a form of code which is transmitted from one source to other. The
main advantage of this process is that hackers are not able to decrypt the input code
without permission and JL organization can adopt this method to improve the privacy of
signals.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COMPUTER SECURITY
7
Figure: an Encryption process
(Source: Tweneboah, et al., 2017)
Cryptography
It is an advanced technology in the field of computer security which is used to
detect the malware and unwanted signals from the server. It has the ability to hide the
data and convert into a particular data bit and keep data secure and confidential. JL
Company deals with a large amount of data for which they can develop the
cryptography technology and employees should ensure that they use only authorized
websites.
Figure: Cryptography process
7
Figure: an Encryption process
(Source: Tweneboah, et al., 2017)
Cryptography
It is an advanced technology in the field of computer security which is used to
detect the malware and unwanted signals from the server. It has the ability to hide the
data and convert into a particular data bit and keep data secure and confidential. JL
Company deals with a large amount of data for which they can develop the
cryptography technology and employees should ensure that they use only authorized
websites.
Figure: Cryptography process

COMPUTER SECURITY
8
(Source: Safa, Von & Furnell, 2016)
Firewall software
Firewall is a type of security application which is developed to avoid malware
and cyber-attacks and it identifies the traffic signals from computer networks. In the
case of JL management team can purchase the firewall software and download into their
computer devices to block the malware signals.
Figure: Firewall versus antivirus
(Source: Tsai, et al., 2015)
Antivirus and backup plans
Antivirus is a process to analyze and controls the malware attacks and many
organizations use this step to reduce the DDOS attacks. The main advantage of this
process is that employees can identify the fraud emails and messages after that they can
block the networks of malicious software’s. Backup plan is also an important step and
cloud computing is a modern method that can be adopted by JL.
8
(Source: Safa, Von & Furnell, 2016)
Firewall software
Firewall is a type of security application which is developed to avoid malware
and cyber-attacks and it identifies the traffic signals from computer networks. In the
case of JL management team can purchase the firewall software and download into their
computer devices to block the malware signals.
Figure: Firewall versus antivirus
(Source: Tsai, et al., 2015)
Antivirus and backup plans
Antivirus is a process to analyze and controls the malware attacks and many
organizations use this step to reduce the DDOS attacks. The main advantage of this
process is that employees can identify the fraud emails and messages after that they can
block the networks of malicious software’s. Backup plan is also an important step and
cloud computing is a modern method that can be adopted by JL.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER SECURITY
9
Comparison of the chosen solution and alternative solutions
For the security of JL organization, there are main two technologies can be used,
for example, encryption and cryptography which secure the information from the
attackers. Moreover, if the data or information is lost the attackers ate not able to access
the accounts of users and JL can take their benefits to secure data. As compared to other
alternative solution the encryption is very popular techniques in the field of computer
security (Sharma, & Rawat, 2015). This process is more effective and very low cost
rather than alternative solution due to this advantage JL can adopt this process and it
converts signals into a code which cannot be read by any hacker. It provides security to
users data at the time of transmission and at receiver side decryption process is used to
convert code into original information. Cryptography is the latest security process that
can be used along with the encryption process because it has the capability to identify
the malware and fraud signals as compared to an alternative process.
Breakdown of the cost of addressing the security issue
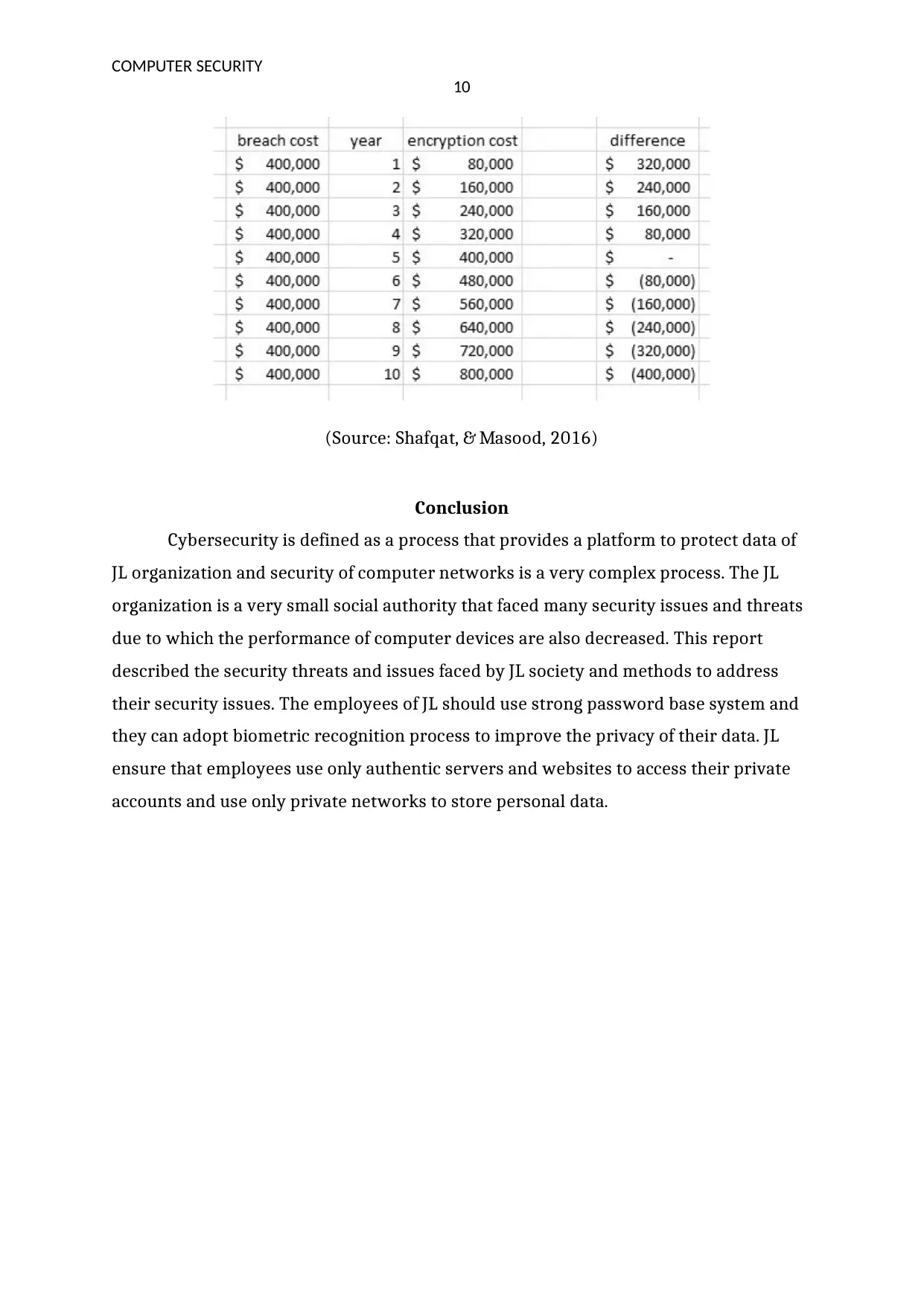
To reduce the issues and threats of cyber security the JL organization can adopt
security programmes and steps. The cost of using the network security systems the JL
community requires around 1200 dollar in which 50% cost is used for installation and
development of security and rest of money is used for maintenance and establishment
purpose. Around 30 to 70 dollars are used for security applications and software’s like
antivirus and firewall systems. The amount requires for encryption process for JL
organization is not fixed because it is completely depended upon the size of data and
networks.
Figure: a cost of implementing the encryption technology
9
Comparison of the chosen solution and alternative solutions
For the security of JL organization, there are main two technologies can be used,
for example, encryption and cryptography which secure the information from the
attackers. Moreover, if the data or information is lost the attackers ate not able to access
the accounts of users and JL can take their benefits to secure data. As compared to other
alternative solution the encryption is very popular techniques in the field of computer
security (Sharma, & Rawat, 2015). This process is more effective and very low cost
rather than alternative solution due to this advantage JL can adopt this process and it
converts signals into a code which cannot be read by any hacker. It provides security to
users data at the time of transmission and at receiver side decryption process is used to
convert code into original information. Cryptography is the latest security process that
can be used along with the encryption process because it has the capability to identify
the malware and fraud signals as compared to an alternative process.
Breakdown of the cost of addressing the security issue
To reduce the issues and threats of cyber security the JL organization can adopt
security programmes and steps. The cost of using the network security systems the JL
community requires around 1200 dollar in which 50% cost is used for installation and
development of security and rest of money is used for maintenance and establishment
purpose. Around 30 to 70 dollars are used for security applications and software’s like
antivirus and firewall systems. The amount requires for encryption process for JL
organization is not fixed because it is completely depended upon the size of data and
networks.
Figure: a cost of implementing the encryption technology
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COMPUTER SECURITY
10
(Source: Shafqat, & Masood, 2016)
Conclusion
Cybersecurity is defined as a process that provides a platform to protect data of
JL organization and security of computer networks is a very complex process. The JL
organization is a very small social authority that faced many security issues and threats
due to which the performance of computer devices are also decreased. This report
described the security threats and issues faced by JL society and methods to address
their security issues. The employees of JL should use strong password base system and
they can adopt biometric recognition process to improve the privacy of their data. JL
ensure that employees use only authentic servers and websites to access their private
accounts and use only private networks to store personal data.
10
(Source: Shafqat, & Masood, 2016)
Conclusion
Cybersecurity is defined as a process that provides a platform to protect data of
JL organization and security of computer networks is a very complex process. The JL
organization is a very small social authority that faced many security issues and threats
due to which the performance of computer devices are also decreased. This report
described the security threats and issues faced by JL society and methods to address
their security issues. The employees of JL should use strong password base system and
they can adopt biometric recognition process to improve the privacy of their data. JL
ensure that employees use only authentic servers and websites to access their private
accounts and use only private networks to store personal data.

COMPUTER SECURITY
11
References
Abomhara, M., & Køien, G. M. (2015). Cybersecurity and the internet of things:
vulnerabilities, threats, intruders and attacks. Journal of Cyber Security, 4(1), 65-
88.
AbouZahr, C., De Savigny, D., Mikkelsen, L., Steel, P. W., Lozano, R., Nichols, E., ... & Lopez,
A. D. (2015). Civil registration and vital statistics: progress in the data revolution
for counting and accountability. The Lancet, 386(10001), 1373-1385.
Buczak, A. L., & Guven, E. (2016). A survey of data mining and machine learning
methods for cybersecurity intrusion detection. IEEE Communications Surveys &
Tutorials, 18(2), 1153-1176.
Gupta, B., Agrawal, D. P., & Yamaguchi, S. (Eds.). (2016). Handbook of research on
modern cryptographic solutions for computer and cybersecurity. IGI Global.
Lee, J., Bagheri, B., & Jin, C. (2016). Introduction to cyber manufacturing. Manufacturing
Letters, 8, 11-15.
Li, J., Tao, F., Cheng, Y., & Zhao, L. (2015). Big data in product lifecycle management. The
International Journal of Advanced Manufacturing Technology, 81(1-4), 667-684.
Min, K. S., Chai, S. W., & Han, M. (2015). An international comparative study on
cybersecurity strategy. International Journal of Security and Its Applications, 9(2),
13-20.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance
model in organizations. Computers & Security, 56, 70-82.
Shafqat, N., & Masood, A. (2016). Comparative analysis of various national cybersecurity
strategies. International Journal of Computer Science and Information
Security, 14(1), 129.
Sharma, R. K., & Rawat, D. B. (2015). Advances on security threats and countermeasures
for cognitive radio networks: A survey. IEEE Communications Surveys &
Tutorials, 17(2), 1023-1043.
11
References
Abomhara, M., & Køien, G. M. (2015). Cybersecurity and the internet of things:
vulnerabilities, threats, intruders and attacks. Journal of Cyber Security, 4(1), 65-
88.
AbouZahr, C., De Savigny, D., Mikkelsen, L., Steel, P. W., Lozano, R., Nichols, E., ... & Lopez,
A. D. (2015). Civil registration and vital statistics: progress in the data revolution
for counting and accountability. The Lancet, 386(10001), 1373-1385.
Buczak, A. L., & Guven, E. (2016). A survey of data mining and machine learning
methods for cybersecurity intrusion detection. IEEE Communications Surveys &
Tutorials, 18(2), 1153-1176.
Gupta, B., Agrawal, D. P., & Yamaguchi, S. (Eds.). (2016). Handbook of research on
modern cryptographic solutions for computer and cybersecurity. IGI Global.
Lee, J., Bagheri, B., & Jin, C. (2016). Introduction to cyber manufacturing. Manufacturing
Letters, 8, 11-15.
Li, J., Tao, F., Cheng, Y., & Zhao, L. (2015). Big data in product lifecycle management. The
International Journal of Advanced Manufacturing Technology, 81(1-4), 667-684.
Min, K. S., Chai, S. W., & Han, M. (2015). An international comparative study on
cybersecurity strategy. International Journal of Security and Its Applications, 9(2),
13-20.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy compliance
model in organizations. Computers & Security, 56, 70-82.
Shafqat, N., & Masood, A. (2016). Comparative analysis of various national cybersecurity
strategies. International Journal of Computer Science and Information
Security, 14(1), 129.
Sharma, R. K., & Rawat, D. B. (2015). Advances on security threats and countermeasures
for cognitive radio networks: A survey. IEEE Communications Surveys &
Tutorials, 17(2), 1023-1043.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




