Cybersecurity: Footprinting, Scanning, Enumeration, and Obfuscation Tools
VerifiedAdded on 2023/06/15
|11
|1105
|345
AI Summary
This article covers various cybersecurity techniques such as Footprinting, Scanning, Enumeration, and Obfuscation Tools. It provides insights into Nessus Scanning countermeasures, Nmap NSE Scripting, and Basic Banner Grabbing. Additionally, it includes a case study of a Brute force attack scenario and discusses various obfuscation tools.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CYERSECURITY
CYERSECURITY
Name of the Student
Name of the University
Author Note
CYERSECURITY
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
CYBERSECURITY
Table of Contents
Answer of Question number 1.........................................................................................................3
Footprinting.....................................................................................................................................3
Publicly Available Information...................................................................................................3
Answer of Question number 2.........................................................................................................4
Scanning..........................................................................................................................................4
SYN Scanning.............................................................................................................................5
UDP Scanning.............................................................................................................................5
ACK scanning..............................................................................................................................5
Window Scanning........................................................................................................................5
Answer of Question number 3.........................................................................................................5
Enumeration.....................................................................................................................................5
Nessus Scanning countermeasures..............................................................................................5
Nmap NSE Scripting...................................................................................................................6
Basic Banner Grabbing................................................................................................................6
Answer of Question Number 4........................................................................................................6
Case study of an Attack scenario.....................................................................................................6
Answer of question number 5..........................................................................................................8
Obfuscation Tools............................................................................................................................8
Reference.........................................................................................................................................9
CYBERSECURITY
Table of Contents
Answer of Question number 1.........................................................................................................3
Footprinting.....................................................................................................................................3
Publicly Available Information...................................................................................................3
Answer of Question number 2.........................................................................................................4
Scanning..........................................................................................................................................4
SYN Scanning.............................................................................................................................5
UDP Scanning.............................................................................................................................5
ACK scanning..............................................................................................................................5
Window Scanning........................................................................................................................5
Answer of Question number 3.........................................................................................................5
Enumeration.....................................................................................................................................5
Nessus Scanning countermeasures..............................................................................................5
Nmap NSE Scripting...................................................................................................................6
Basic Banner Grabbing................................................................................................................6
Answer of Question Number 4........................................................................................................6
Case study of an Attack scenario.....................................................................................................6
Answer of question number 5..........................................................................................................8
Obfuscation Tools............................................................................................................................8
Reference.........................................................................................................................................9

2
CYBERSECURITY
CYBERSECURITY
3
CYBERSECURITY
Answer of Question number 1
Footprinting
Whenever browsing or using internet, without user acknowledgement a huge amount of
information is publicly available such as location details, visited website links and employee
informations of companies. To check potential security exposures and what are the information
hackers can access a technique can be used called Footprinting to generate a broad profile of an
organization’s security posture and prevent exploitation (Aviad, Węcel and Abramowicz 2013).
Type of
Footprinting
Sections Control and remove publicly
Available Information
Internet Network locks and subnets, TCP and
UDP
1. Determination of certain
subsidiaries.
2. Proper authorization.
3. Check publicly available
information.
4. WHOIS and DNS Enumeration.
5. DNS interrogation.
6. Network Reconnaissance.
Intranet Internal domain names, Network
protocols
Remote Access VPNs, Telephone Numbers
Extranet Type of connection, Domain names
Publicly Available Information
Sources Explanation Guidance
CYBERSECURITY
Answer of Question number 1
Footprinting
Whenever browsing or using internet, without user acknowledgement a huge amount of
information is publicly available such as location details, visited website links and employee
informations of companies. To check potential security exposures and what are the information
hackers can access a technique can be used called Footprinting to generate a broad profile of an
organization’s security posture and prevent exploitation (Aviad, Węcel and Abramowicz 2013).
Type of
Footprinting
Sections Control and remove publicly
Available Information
Internet Network locks and subnets, TCP and
UDP
1. Determination of certain
subsidiaries.
2. Proper authorization.
3. Check publicly available
information.
4. WHOIS and DNS Enumeration.
5. DNS interrogation.
6. Network Reconnaissance.
Intranet Internal domain names, Network
protocols
Remote Access VPNs, Telephone Numbers
Extranet Type of connection, Domain names
Publicly Available Information
Sources Explanation Guidance
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
CYBERSECURITY
Company Websites Spreadsheets, offline view can be accessed through
mirroring tools Wget for
UNIX and Teleport Pro
for Windowss
Location Details Wired and wireless networks,
mobile or computer
MAC address can be
obtained from Google
Location and Skyhook
Employee Information Employee names, phone
numbers
Can be found through
FaceBook, Linkedin and
Flickr.
Current Events Mergers, Rapid hiring,
Outsourcing
Information can be found
from EDGAR database.
Answer of Question number 2
Scanning
For infracting any system attackers can hamper tracking and attribution and manage exposure of
resources if host or network being compromised. Scanning is use to inspect the potential entry
points attackers would infiltrate (Alsunbul, Le and Tan 2016). By performing a ping sweep the
host status of a specific IP can be identified. Network pinging is the process of transfer traffic to
a destination and examining the outcomes by utilizing ICMP, ARP, UDP and TCP to recognize
if a host is online.
CYBERSECURITY
Company Websites Spreadsheets, offline view can be accessed through
mirroring tools Wget for
UNIX and Teleport Pro
for Windowss
Location Details Wired and wireless networks,
mobile or computer
MAC address can be
obtained from Google
Location and Skyhook
Employee Information Employee names, phone
numbers
Can be found through
FaceBook, Linkedin and
Flickr.
Current Events Mergers, Rapid hiring,
Outsourcing
Information can be found
from EDGAR database.
Answer of Question number 2
Scanning
For infracting any system attackers can hamper tracking and attribution and manage exposure of
resources if host or network being compromised. Scanning is use to inspect the potential entry
points attackers would infiltrate (Alsunbul, Le and Tan 2016). By performing a ping sweep the
host status of a specific IP can be identified. Network pinging is the process of transfer traffic to
a destination and examining the outcomes by utilizing ICMP, ARP, UDP and TCP to recognize
if a host is online.

5
CYBERSECURITY
SYN Scanning
It is another form of TCP scanning generates raw IP packets itself rather use operating
system’s network functions. In SYN scanning the distinct services never receives a connection
however the RST during the handclasp can cause glitches for some network stacks in some
certain device similar to printers.
UDP Scanning
Most UDP port scanner use the absence of a reply to check if a port is open or not.
However if a port is jammed by a firewall this technique will incorrectly report that port is
opened also may affected by ICMP rate limiting.
ACK scanning
It is an unusual scan type and cannot define whether the port is close or open.
Window Scanning
Rarely use because it is outdated nature and also untrustworthy to decide whether a port
is close or open.
Answer of Question number 3
Enumeration
Enumeration is the process to identify services for find weakness in any specific system
and involves active connections to system and directed queries (Basta, Basta and Brown 2013).
Nessus Scanning countermeasures
It implements effective patch to stop susceptibilities from being presented in first place
by using Detection and Prevention Systems (IDS/IPS)
CYBERSECURITY
SYN Scanning
It is another form of TCP scanning generates raw IP packets itself rather use operating
system’s network functions. In SYN scanning the distinct services never receives a connection
however the RST during the handclasp can cause glitches for some network stacks in some
certain device similar to printers.
UDP Scanning
Most UDP port scanner use the absence of a reply to check if a port is open or not.
However if a port is jammed by a firewall this technique will incorrectly report that port is
opened also may affected by ICMP rate limiting.
ACK scanning
It is an unusual scan type and cannot define whether the port is close or open.
Window Scanning
Rarely use because it is outdated nature and also untrustworthy to decide whether a port
is close or open.
Answer of Question number 3
Enumeration
Enumeration is the process to identify services for find weakness in any specific system
and involves active connections to system and directed queries (Basta, Basta and Brown 2013).
Nessus Scanning countermeasures
It implements effective patch to stop susceptibilities from being presented in first place
by using Detection and Prevention Systems (IDS/IPS)

6
CYBERSECURITY
Nmap NSE Scripting
Nmap has the capacity to conduct all types of enumeration activities via the Nmap
Scripting Engine (NSE).
Basic Banner Grabbing
Defined as joining to remote facilities and detecting the output, and it can be shockingly
helpful to remote hackers. It also shut down needless services and limit access to facilities using
network access control (Kostopoulos 2017).
– Telnet (a remote tool build into most operating systems). C:\>telnet
www.example.com 80
– Netcat: slightly more surgical probing tool, “TCP/IP Swiss Army knife”. Nc –v
www.example.com 80
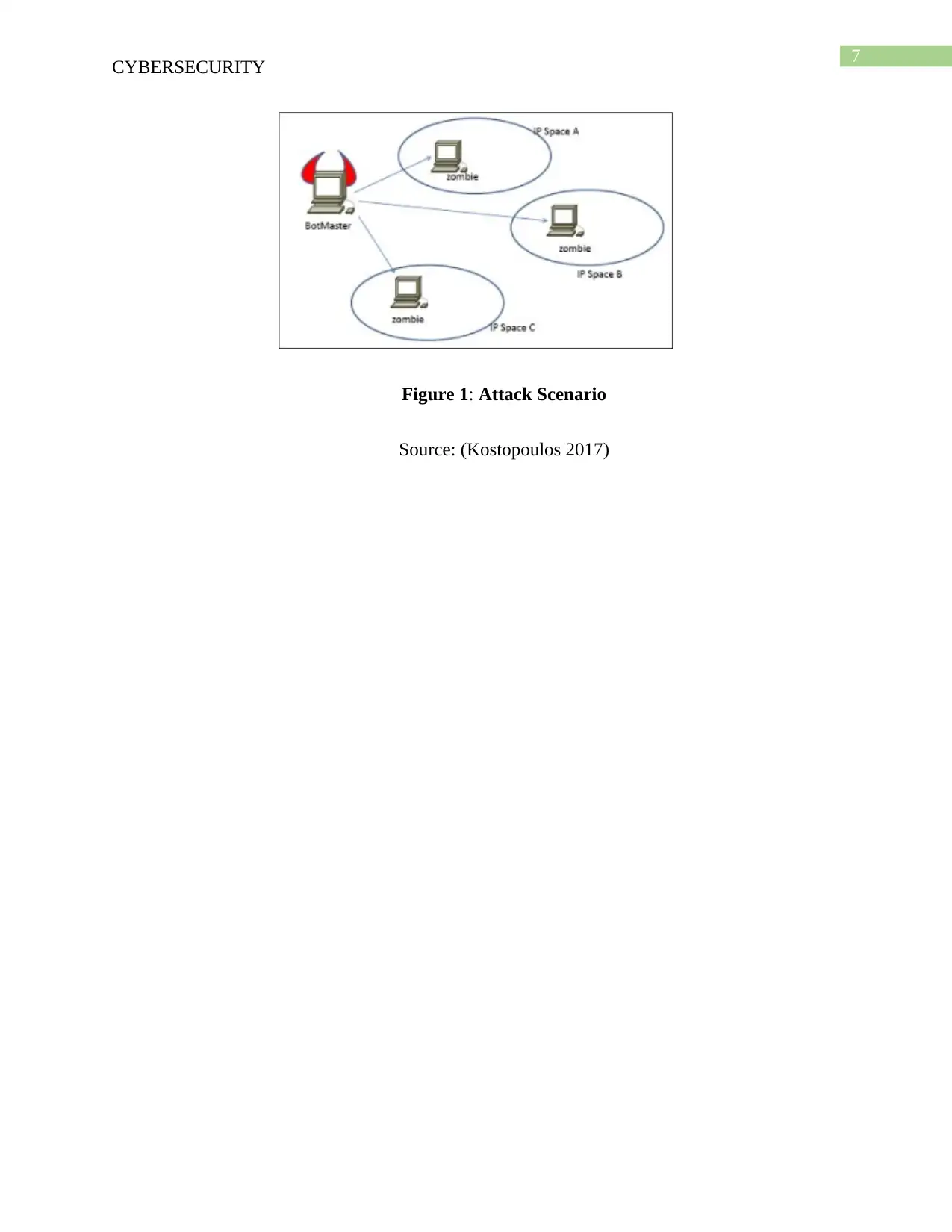
Answer of Question Number 4
Case study of an Attack scenario
The incident of Brute force attack was discovered at a University lab to spread malware
throughout the campus network. After removing the effected machine IT team tried to find the
cause of the causality found that more than 60000 IP packets has been transfer in 3 minute
during the attack.
CYBERSECURITY
Nmap NSE Scripting
Nmap has the capacity to conduct all types of enumeration activities via the Nmap
Scripting Engine (NSE).
Basic Banner Grabbing
Defined as joining to remote facilities and detecting the output, and it can be shockingly
helpful to remote hackers. It also shut down needless services and limit access to facilities using
network access control (Kostopoulos 2017).
– Telnet (a remote tool build into most operating systems). C:\>telnet
www.example.com 80
– Netcat: slightly more surgical probing tool, “TCP/IP Swiss Army knife”. Nc –v
www.example.com 80
Answer of Question Number 4
Case study of an Attack scenario
The incident of Brute force attack was discovered at a University lab to spread malware
throughout the campus network. After removing the effected machine IT team tried to find the
cause of the causality found that more than 60000 IP packets has been transfer in 3 minute
during the attack.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
7
CYBERSECURITY
Figure 1: Attack Scenario
Source: (Kostopoulos 2017)
CYBERSECURITY
Figure 1: Attack Scenario
Source: (Kostopoulos 2017)
8
CYBERSECURITY
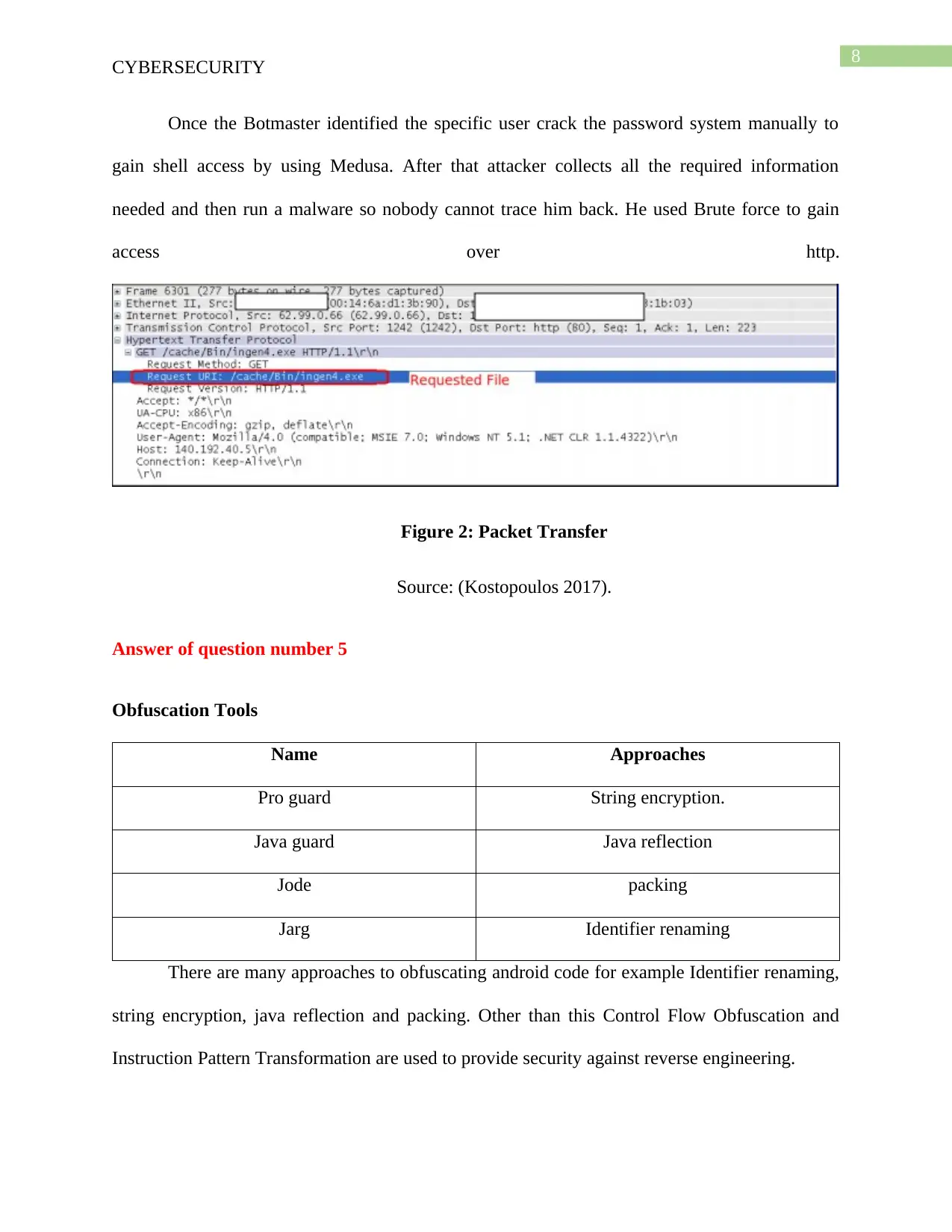
Once the Botmaster identified the specific user crack the password system manually to
gain shell access by using Medusa. After that attacker collects all the required information
needed and then run a malware so nobody cannot trace him back. He used Brute force to gain
access over http.
Figure 2: Packet Transfer
Source: (Kostopoulos 2017).
Answer of question number 5
Obfuscation Tools
Name Approaches
Pro guard String encryption.
Java guard Java reflection
Jode packing
Jarg Identifier renaming
There are many approaches to obfuscating android code for example Identifier renaming,
string encryption, java reflection and packing. Other than this Control Flow Obfuscation and
Instruction Pattern Transformation are used to provide security against reverse engineering.
CYBERSECURITY
Once the Botmaster identified the specific user crack the password system manually to
gain shell access by using Medusa. After that attacker collects all the required information
needed and then run a malware so nobody cannot trace him back. He used Brute force to gain
access over http.
Figure 2: Packet Transfer
Source: (Kostopoulos 2017).
Answer of question number 5
Obfuscation Tools
Name Approaches
Pro guard String encryption.
Java guard Java reflection
Jode packing
Jarg Identifier renaming
There are many approaches to obfuscating android code for example Identifier renaming,
string encryption, java reflection and packing. Other than this Control Flow Obfuscation and
Instruction Pattern Transformation are used to provide security against reverse engineering.

9
CYBERSECURITY
CYBERSECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CYBERSECURITY
Reference
Alsunbul, S., Le, P. and Tan, J., 2013, July. A Defense Security Approach for Infrastructures
against Hacking. In Trust, Security and Privacy in Computing and Communications (TrustCom),
2013 12th IEEE International Conference on (pp. 1600-1606). IEEE.
Aviad, A.E., Węcel, K. and Abramowicz, W., 2016. A Semantic Approach to Modelling of
Cybersecurity Domain. Journal of Information Warfare, 15(1), pp.91-X.
Basta, A., Basta, N. and Brown, M., 2013. Computer security and penetration testing. Cengage
Learning.
Kostopoulos, G., 2017. Cyberspace and cybersecurity. CRC Press.
CYBERSECURITY
Reference
Alsunbul, S., Le, P. and Tan, J., 2013, July. A Defense Security Approach for Infrastructures
against Hacking. In Trust, Security and Privacy in Computing and Communications (TrustCom),
2013 12th IEEE International Conference on (pp. 1600-1606). IEEE.
Aviad, A.E., Węcel, K. and Abramowicz, W., 2016. A Semantic Approach to Modelling of
Cybersecurity Domain. Journal of Information Warfare, 15(1), pp.91-X.
Basta, A., Basta, N. and Brown, M., 2013. Computer security and penetration testing. Cengage
Learning.
Kostopoulos, G., 2017. Cyberspace and cybersecurity. CRC Press.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





