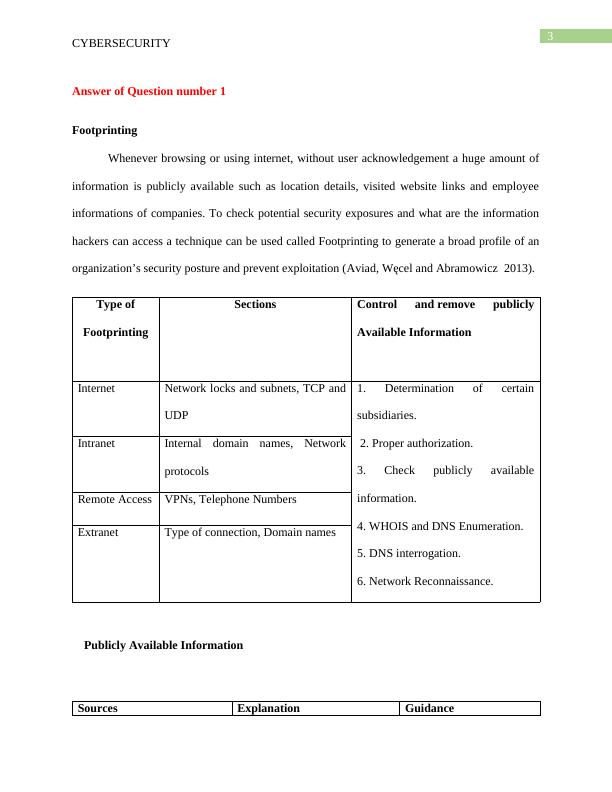
Cybersecurity: Footprinting, Scanning, Enumeration, and Obfuscation Tools
Identify steps to control and remove sensitive publicly available information based on the Site Security Handbook guidance.
11 Pages1105 Words345 Views
Added on 2023-06-15
About This Document
This article covers various cybersecurity techniques such as Footprinting, Scanning, Enumeration, and Obfuscation Tools. It provides insights into Nessus Scanning countermeasures, Nmap NSE Scripting, and Basic Banner Grabbing. Additionally, it includes a case study of a Brute force attack scenario and discusses various obfuscation tools.
Cybersecurity: Footprinting, Scanning, Enumeration, and Obfuscation Tools
Identify steps to control and remove sensitive publicly available information based on the Site Security Handbook guidance.
Added on 2023-06-15
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Cyber Security - Assignment PDF
|8
|2242
|71
Performing Vulnerability Scan on Network
|12
|769
|44
Networking - Penetration Testing ( Scanning and Enumeration)
|4
|452
|34
Flooding attack Detection using Anomaly Techniques with Wireshark
|53
|13458
|342
COIT20261 Network Routing and Switching Term 1, 2019
|7
|2019
|65
The OSI and TCP/IP Models (PDF)
|9
|1512
|110