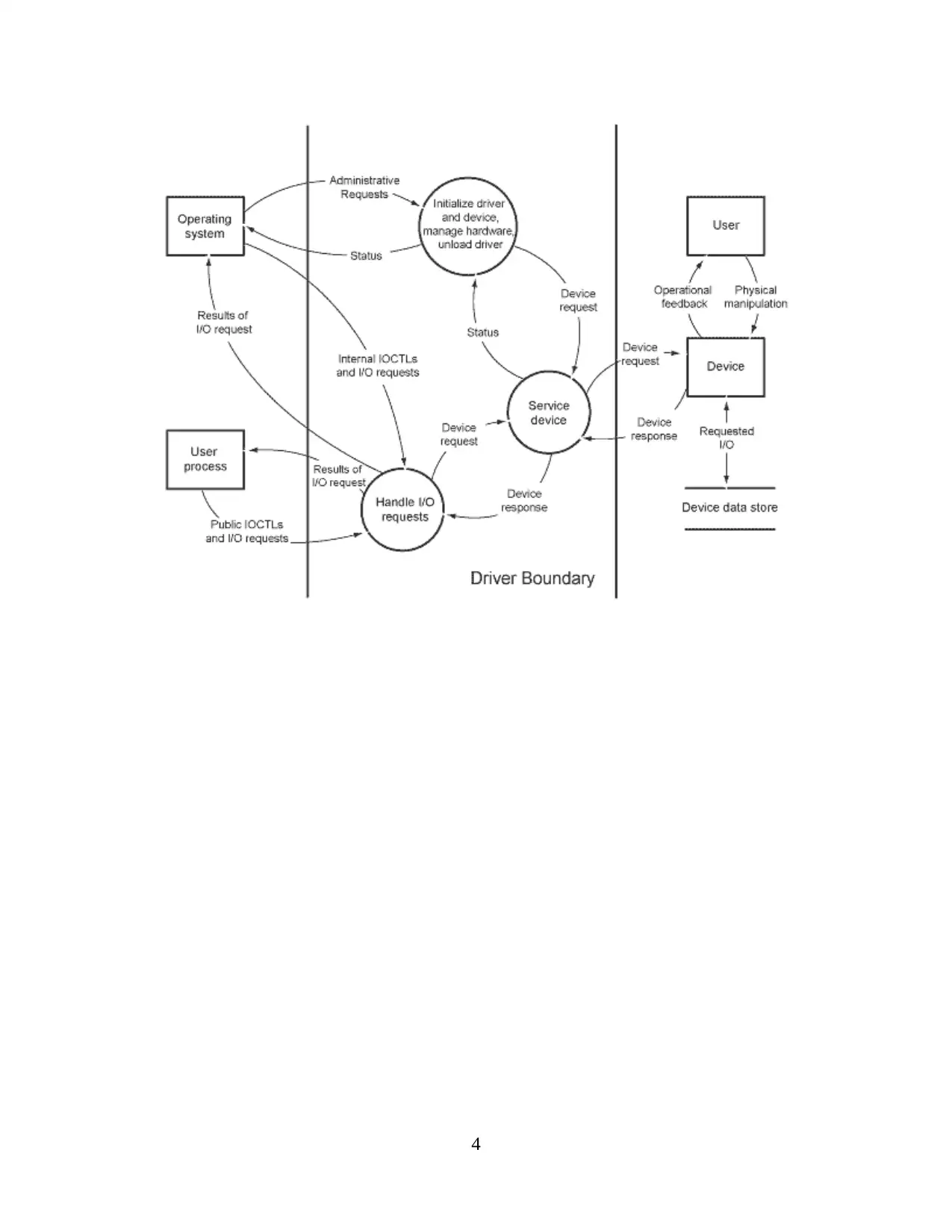
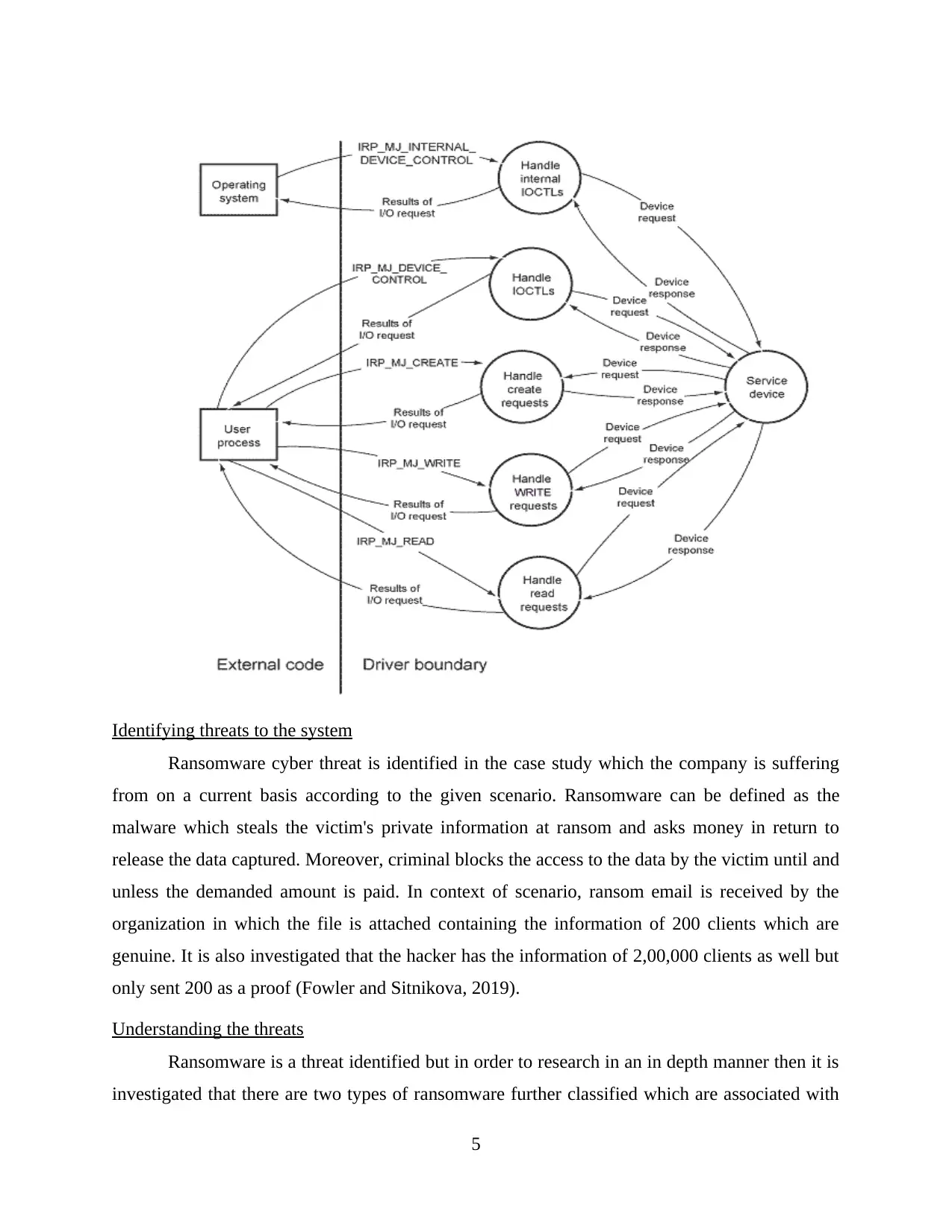
This report covers the investigation about the case study given on cyber threats and cyber security which includes the introduction containing the purpose of report and area of research along with the context of research and concepts of cyber security which is followed by the purpose of drawing the threat model. Report also covers the main body containing the information about the case study which includes the requirements of the case study and data flow diagrams along with the identification of the threats to the systems and understanding of the threats in detail. Moreover, conclusion covers the information related to the findings and recommendations by analysing the whole report so that proper decision making can be done by the organization and also to better understand the concepts of cybersecurity threat model.
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)