Cybersecurity Research Proposal: Threats and Mitigation
VerifiedAdded on 2020/04/01
|13
|2250
|197
Report
AI Summary
This research proposal outlines a comprehensive study on cybersecurity, focusing on the risks and challenges organizations face in the digital age. The proposal defines project objectives, which include analyzing cyber threats, identifying critical information structures, and suggesting risk mitigation strategies. It establishes the project scope, emphasizing the identification and mitigation of cyber attack risks, and includes research questions addressing the responsibilities of business owners in mitigating risk and the role of smart grid systems. The literature review highlights the growing concern of cybersecurity and the importance of protecting data from hackers. The research methodology encompasses qualitative and quantitative approaches, detailing data collection processes, sampling methods, and potential research limitations. The proposal also includes a time schedule for project activities and concludes with a summary of the key findings and research directions, with references to relevant academic sources.

Running head: RESEARCH PROPOSAL
Research proposal
Name of the Student:
Name of the University:
Author note:
Research proposal
Name of the Student:
Name of the University:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RESEARCH PROPOSAL
Executive summery
The purpose of this report is to critically evaluate and make a research foundation for further
research. The focus of the previous assignments was to review the cyber crime environments in
some sector where the impact of the crime is high. The project objectives of doing the research
are also discussed. The data collection process and research limitations while doing the research
is opined as suitable. Based on the research method and outlines activity the main tasks are
scheduled in a chart below.
Executive summery
The purpose of this report is to critically evaluate and make a research foundation for further
research. The focus of the previous assignments was to review the cyber crime environments in
some sector where the impact of the crime is high. The project objectives of doing the research
are also discussed. The data collection process and research limitations while doing the research
is opined as suitable. Based on the research method and outlines activity the main tasks are
scheduled in a chart below.

2RESEARCH PROPOSAL
Table of Contents
Introduction......................................................................................................................................3
Project objective..............................................................................................................................3
Project scope....................................................................................................................................3
Research questions...........................................................................................................................4
Literature review..............................................................................................................................4
Research methodology.....................................................................................................................6
Qualitative research and Quantitative research...............................................................................6
Research approach and research design..........................................................................................7
Data collection process....................................................................................................................8
Sampling method and sample size...................................................................................................8
Research limitations.........................................................................................................................8
Time schedule for the project..........................................................................................................9
Conclusions......................................................................................................................................9
References......................................................................................................................................11
Table of Contents
Introduction......................................................................................................................................3
Project objective..............................................................................................................................3
Project scope....................................................................................................................................3
Research questions...........................................................................................................................4
Literature review..............................................................................................................................4
Research methodology.....................................................................................................................6
Qualitative research and Quantitative research...............................................................................6
Research approach and research design..........................................................................................7
Data collection process....................................................................................................................8
Sampling method and sample size...................................................................................................8
Research limitations.........................................................................................................................8
Time schedule for the project..........................................................................................................9
Conclusions......................................................................................................................................9
References......................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3RESEARCH PROPOSAL
Introduction
This text gives a proposal for doing research in the cyber security methods and outlines a
research problem to do research on further (Sauter and Carafano 2012). The project objective
and project scope is also given in the text. The research problem and questions are also given in
the following chapters. The research design and approach to conducting the research in the field
is also outlined in the following discussions. The data collection process and research limitations
while doing the research is opined as suitable. Based on the research method and outlines activity
the main tasks are scheduled in a chart below (Panneerselvam 2014).
Project objective
The preliminary objectives of doing this project is
To analyse the threats that comes from cyber threats in different function of operations
and how to avert them
To identify the most comprehensive critical information structure and provide
suggestions to mitigate the risk that comes from cyber attacks.
To be responsible for fusing instructions and information of different functions of
business
Project scope
The project lies in the recognising and mitigating the risk arises from the cyber attacks in
different organisations. This also takes into consideration about the actions that are taken as
target to destroy the cyber system of any business organisation. The cyber infrastructure must
not be compromised for it will threaten all the system to collapse. The intrusions must be
Introduction
This text gives a proposal for doing research in the cyber security methods and outlines a
research problem to do research on further (Sauter and Carafano 2012). The project objective
and project scope is also given in the text. The research problem and questions are also given in
the following chapters. The research design and approach to conducting the research in the field
is also outlined in the following discussions. The data collection process and research limitations
while doing the research is opined as suitable. Based on the research method and outlines activity
the main tasks are scheduled in a chart below (Panneerselvam 2014).
Project objective
The preliminary objectives of doing this project is
To analyse the threats that comes from cyber threats in different function of operations
and how to avert them
To identify the most comprehensive critical information structure and provide
suggestions to mitigate the risk that comes from cyber attacks.
To be responsible for fusing instructions and information of different functions of
business
Project scope
The project lies in the recognising and mitigating the risk arises from the cyber attacks in
different organisations. This also takes into consideration about the actions that are taken as
target to destroy the cyber system of any business organisation. The cyber infrastructure must
not be compromised for it will threaten all the system to collapse. The intrusions must be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4RESEARCH PROPOSAL
identified and viewed as a form of root to hacking the confidential data of a particular system.
This is also helpful in supporting the smart grid infrastructure building for cyber security in an
organisation. The also lies in identifying the threats associated with cyber security in today’s
world (Sauter and Carafano 2012). The research will be helpful for companies to point out the
problem and then take steps further to eliminate the risk that it poses to business.
Research questions
Primary questions
What are the risks and challenges involved in cybercrime for an organisation and what is
the responsibility of the owners of the business in mitigating the risk?
Secondary questions
What is smart grid system and how it is useful for systems in organisations?
What process can be adapted by companies in mitigating risk related to cyber-attacks in
their organisations?
Literature review
Cyber security has become a concern for all the industry that has became a part of the
new internet world. The main area of operations are getting affected by the inventions in th
technological world. Business is facing challenges in protecting their data from the hackers and
identified and viewed as a form of root to hacking the confidential data of a particular system.
This is also helpful in supporting the smart grid infrastructure building for cyber security in an
organisation. The also lies in identifying the threats associated with cyber security in today’s
world (Sauter and Carafano 2012). The research will be helpful for companies to point out the
problem and then take steps further to eliminate the risk that it poses to business.
Research questions
Primary questions
What are the risks and challenges involved in cybercrime for an organisation and what is
the responsibility of the owners of the business in mitigating the risk?
Secondary questions
What is smart grid system and how it is useful for systems in organisations?
What process can be adapted by companies in mitigating risk related to cyber-attacks in
their organisations?
Literature review
Cyber security has become a concern for all the industry that has became a part of the
new internet world. The main area of operations are getting affected by the inventions in th
technological world. Business is facing challenges in protecting their data from the hackers and

5RESEARCH PROPOSAL
the reason may be attributed to the cyber security issues (Mackey and Gass 2015). This can also
be attributed to the activities in business that requires safeguarding confidential information.
Networking has become essential for continuing with business operation and building data
application, databases within the domain of procedural measures of security also became
essential. However, these steps are not quite enough for maintaining the security of the business.
The CIIP handbook is supportive in suggesting the companies that how they can build a secure
infrastructure if posed against a problem in dealing with the cyber attacks (Jacobs 2016).
The statistics tells that 80% of the transactional data is nowadays saved in a computers
and is vulnerable to online attackers. Improvement in the system of building firewall for the
system is essential for the companies to protect the company from online attacks (Soomro 2016).
These measures must be incorporated in the system. As the local perception goes, the cyber
attacks are happens to be incidents by accidents but these is a challenge for business
administrations. The calculated cyber attacks are result of cyber conflicts and are sensitive
problem in companies’ perspective. The models that are full proof of the challenges must be used
in this crucial part of protecting data from hacks. Another factor that works around here is the
integrity of the business owner and the quality of goods or service is provided. To gain the
personal and confidential data the online hackers uses the platform like Skrill, Payoneer and
PayPal’s information which may not be secured at all (Jacobs 2016). To combat this kind of
breaches Routine activity theory will be useful. To mitigate the risks business must take the
responsibility to enhance the security measures and takes the following things in consideration.
For example, firewalls and role-based access, Physical separation, encrypt data in HD, identity
management and backing up the data. The most common step is to build a firewall, which is
done by 94% of the organisations.
the reason may be attributed to the cyber security issues (Mackey and Gass 2015). This can also
be attributed to the activities in business that requires safeguarding confidential information.
Networking has become essential for continuing with business operation and building data
application, databases within the domain of procedural measures of security also became
essential. However, these steps are not quite enough for maintaining the security of the business.
The CIIP handbook is supportive in suggesting the companies that how they can build a secure
infrastructure if posed against a problem in dealing with the cyber attacks (Jacobs 2016).
The statistics tells that 80% of the transactional data is nowadays saved in a computers
and is vulnerable to online attackers. Improvement in the system of building firewall for the
system is essential for the companies to protect the company from online attacks (Soomro 2016).
These measures must be incorporated in the system. As the local perception goes, the cyber
attacks are happens to be incidents by accidents but these is a challenge for business
administrations. The calculated cyber attacks are result of cyber conflicts and are sensitive
problem in companies’ perspective. The models that are full proof of the challenges must be used
in this crucial part of protecting data from hacks. Another factor that works around here is the
integrity of the business owner and the quality of goods or service is provided. To gain the
personal and confidential data the online hackers uses the platform like Skrill, Payoneer and
PayPal’s information which may not be secured at all (Jacobs 2016). To combat this kind of
breaches Routine activity theory will be useful. To mitigate the risks business must take the
responsibility to enhance the security measures and takes the following things in consideration.
For example, firewalls and role-based access, Physical separation, encrypt data in HD, identity
management and backing up the data. The most common step is to build a firewall, which is
done by 94% of the organisations.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RESEARCH PROPOSAL
Government regulations and laws also works in favour of increasing the punishment of
Cybercrime, though sometimes complicates systems and reverting to the hackers becomes
impossible. With careful intentions and stern steps one must be given careful thought on the
investment of the company in building the cyber security infrastructure. (Sales 2012) The main
thing is to build a strong team. For example, China is known as the user of sophisticated cyber
criminal on large scale. They also prefer to protect the social order, while the social security is
issued at the same time. The reliable power maintenance structure of technologies provides
protection to all system in operation. A built in smart grid is efficient and to control the flow of
information and can be reconstructed (Yan et al. 2014). Different countries are facing different
barriers in using online platform for this security issues. Furthermore, the cost effectiveness is
also beneficial for the small and medium sized companies. It has been proved by recent reforms
in online security that the secure sockets layer certificates are needed for the websites related to
sensitive data, especially the credit card information. Those who are hosting websites, they are
demanding compliance to obtain such certificates from reliable corporations (Sales 2012).
Research methodology
This method includes all the qualitative and quantitative way of doing research. The main
criteria that must be followed is to consider the validity and reliability of the data gathered. The
qualitative approach is known as getting the response in an attitude scale and generalizing the
responds. The quantitative method is more numeric in nature (Panneerselvam 2014).
Qualitative research and Quantitative research
Reliability and validity in qualitative research
Government regulations and laws also works in favour of increasing the punishment of
Cybercrime, though sometimes complicates systems and reverting to the hackers becomes
impossible. With careful intentions and stern steps one must be given careful thought on the
investment of the company in building the cyber security infrastructure. (Sales 2012) The main
thing is to build a strong team. For example, China is known as the user of sophisticated cyber
criminal on large scale. They also prefer to protect the social order, while the social security is
issued at the same time. The reliable power maintenance structure of technologies provides
protection to all system in operation. A built in smart grid is efficient and to control the flow of
information and can be reconstructed (Yan et al. 2014). Different countries are facing different
barriers in using online platform for this security issues. Furthermore, the cost effectiveness is
also beneficial for the small and medium sized companies. It has been proved by recent reforms
in online security that the secure sockets layer certificates are needed for the websites related to
sensitive data, especially the credit card information. Those who are hosting websites, they are
demanding compliance to obtain such certificates from reliable corporations (Sales 2012).
Research methodology
This method includes all the qualitative and quantitative way of doing research. The main
criteria that must be followed is to consider the validity and reliability of the data gathered. The
qualitative approach is known as getting the response in an attitude scale and generalizing the
responds. The quantitative method is more numeric in nature (Panneerselvam 2014).
Qualitative research and Quantitative research
Reliability and validity in qualitative research
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RESEARCH PROPOSAL
In any kind of research, be it qualitative or quantitative the most essential part is to
maintain the reliability and validity of doing the research. Here the data collection process must
be ensured of that. The reliability maintenance is known as the testing and evaluating the data
collected primarily or secondarily (Mackey and Gass 2015). The factors that need to be
considered are neutrality, credibility, applicability, conformability and quality of research and
these are of grave importance in doing research. The two kinds of validity, that are known as the
building blocks of research are the concept validity and construct validity (Panneerselvam 2014).
To maintain the imperceptivity of conceptions concept validity must be considered at the initial
stage.
Research approach and research design
The main research design of this proposal is to collect data from an identified company
through secondary and primary data collection process. The research approach can be inductive
and deductive in ways (Silverman 2016). Here for this research inductive way of conducting
research is followed, which involves careful observation and going through the data and analysis
of data. The theory selection and hypothesis testing is also part of inductive approach (Flick
2015).
Research design highlights the descriptive or the exploratory way of doing research.
(Mackey and Gass 2015).This research requires more descriptive way of conducting the
research. . Here in this research design, the focus is to collect primary data from the company
and based on the fining and analysis the correct conclusion must be given.
In any kind of research, be it qualitative or quantitative the most essential part is to
maintain the reliability and validity of doing the research. Here the data collection process must
be ensured of that. The reliability maintenance is known as the testing and evaluating the data
collected primarily or secondarily (Mackey and Gass 2015). The factors that need to be
considered are neutrality, credibility, applicability, conformability and quality of research and
these are of grave importance in doing research. The two kinds of validity, that are known as the
building blocks of research are the concept validity and construct validity (Panneerselvam 2014).
To maintain the imperceptivity of conceptions concept validity must be considered at the initial
stage.
Research approach and research design
The main research design of this proposal is to collect data from an identified company
through secondary and primary data collection process. The research approach can be inductive
and deductive in ways (Silverman 2016). Here for this research inductive way of conducting
research is followed, which involves careful observation and going through the data and analysis
of data. The theory selection and hypothesis testing is also part of inductive approach (Flick
2015).
Research design highlights the descriptive or the exploratory way of doing research.
(Mackey and Gass 2015).This research requires more descriptive way of conducting the
research. . Here in this research design, the focus is to collect primary data from the company
and based on the fining and analysis the correct conclusion must be given.

8RESEARCH PROPOSAL
Data collection process
Here the objective of this study requires to collect data on cyber attacks on different
organisations and what are the safety procedures. The secondary sources will suffice to build the
foundation of the research and a company will be identified which uses the smart grid procedure
and follows the routine theory of activity (Silverman 2016).
Sampling method and sample size
The secondary data will be collected from different trusted journal sites and a sampling
will be done probability-sampling method. The primary data will be collected from the company.
A group of managers will be identified and the employees related to the information department
will be questioned prepared in the structured questionnaires section. The survey and direct
structured interview method will be followed (Flick 2015). The managers sample size will be six
and employees’ number will be at least 30. The independent variable for observation will be
cyber attacks rate and dependent will the variable related to security systems of the company
(Panneerselvam 2014).
Research limitations
The budget and time are the main concerns of doing this project though a 10 weeks time
has been given for this research. The journals used may not be recent or verified from reliable
source. The resources to conduct an interview and gathering people for interview may not be as
fruitful as needed. These constraints must be kept in mind and eliminated in the best possible
way (Silverman 2016).
Data collection process
Here the objective of this study requires to collect data on cyber attacks on different
organisations and what are the safety procedures. The secondary sources will suffice to build the
foundation of the research and a company will be identified which uses the smart grid procedure
and follows the routine theory of activity (Silverman 2016).
Sampling method and sample size
The secondary data will be collected from different trusted journal sites and a sampling
will be done probability-sampling method. The primary data will be collected from the company.
A group of managers will be identified and the employees related to the information department
will be questioned prepared in the structured questionnaires section. The survey and direct
structured interview method will be followed (Flick 2015). The managers sample size will be six
and employees’ number will be at least 30. The independent variable for observation will be
cyber attacks rate and dependent will the variable related to security systems of the company
(Panneerselvam 2014).
Research limitations
The budget and time are the main concerns of doing this project though a 10 weeks time
has been given for this research. The journals used may not be recent or verified from reliable
source. The resources to conduct an interview and gathering people for interview may not be as
fruitful as needed. These constraints must be kept in mind and eliminated in the best possible
way (Silverman 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
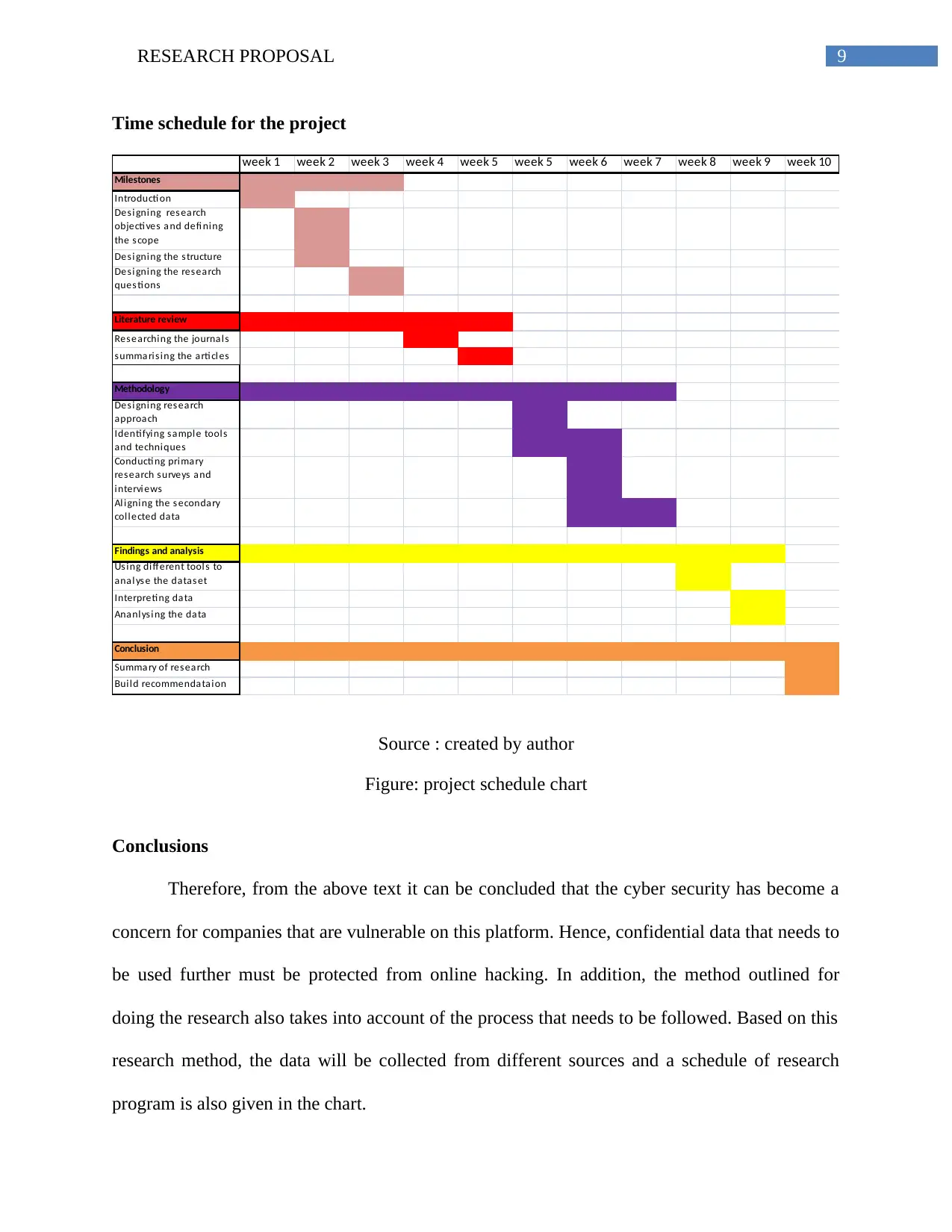
9RESEARCH PROPOSAL
Time schedule for the project
week 1 week 2 week 3 week 4 week 5 week 5 week 6 week 7 week 8 week 9 week 10
Milestones
Introducti on
Des i gni ng res earch
objecti ves a nd defi ni ng
the s cope
Des i gni ng the s tructure
Des i gni ng the res ea rch
ques tions
Literature review
Res earchi ng the journal s
s umma ri si ng the arti cl es
Methodology
Des i gni ng res earch
approach
Identifyi ng s ampl e tool s
and techni ques
Conducti ng pri ma ry
res earch s urveys and
i ntervi ews
Al i gni ng the s econdary
col l ected data
Findings and analysis
Us i ng di fferent tool s to
ana l ys e the datas et
Interpreting da ta
Ana nl ys i ng the data
Conclusion
Summa ry of res ea rch
Bui l d recommendatai on
Source : created by author
Figure: project schedule chart
Conclusions
Therefore, from the above text it can be concluded that the cyber security has become a
concern for companies that are vulnerable on this platform. Hence, confidential data that needs to
be used further must be protected from online hacking. In addition, the method outlined for
doing the research also takes into account of the process that needs to be followed. Based on this
research method, the data will be collected from different sources and a schedule of research
program is also given in the chart.
Time schedule for the project
week 1 week 2 week 3 week 4 week 5 week 5 week 6 week 7 week 8 week 9 week 10
Milestones
Introducti on
Des i gni ng res earch
objecti ves a nd defi ni ng
the s cope
Des i gni ng the s tructure
Des i gni ng the res ea rch
ques tions
Literature review
Res earchi ng the journal s
s umma ri si ng the arti cl es
Methodology
Des i gni ng res earch
approach
Identifyi ng s ampl e tool s
and techni ques
Conducti ng pri ma ry
res earch s urveys and
i ntervi ews
Al i gni ng the s econdary
col l ected data
Findings and analysis
Us i ng di fferent tool s to
ana l ys e the datas et
Interpreting da ta
Ana nl ys i ng the data
Conclusion
Summa ry of res ea rch
Bui l d recommendatai on
Source : created by author
Figure: project schedule chart
Conclusions
Therefore, from the above text it can be concluded that the cyber security has become a
concern for companies that are vulnerable on this platform. Hence, confidential data that needs to
be used further must be protected from online hacking. In addition, the method outlined for
doing the research also takes into account of the process that needs to be followed. Based on this
research method, the data will be collected from different sources and a schedule of research
program is also given in the chart.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10RESEARCH PROPOSAL
Appendix
Appendix

11RESEARCH PROPOSAL
References
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage.
Jacobs, T., 2016, Industrial-sized Cyber Attacks Threaten the Upstream Sector, Journal of
Petroleum Technology, 68(03), pp.42-50.
Low, S.P. and Ong, J., 2014. Research Design and Methodology. In Project Quality
Management (pp. 69-77). Springer Singapore.
Mackey, A. and Gass, S.M., 2015. Second language research: Methodology and design.
Routledge.
Panneerselvam, R., 2014. Research methodology. PHI Learning Pvt. Ltd..
Sales, N.A., 2012. Regulating cyber-security.
Sauter, M. and Carafano, J., 2012. Homeland Security: A Complete Guide 2/E. McGraw Hill
Professional.
Silverman, D. ed., 2016. Qualitative research. Sage.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016, Information security management needs
more holistic approach: A literature review, International Journal of Information
Management, 36(2), pp.215-225.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research
methods: A guidebook and resource. John Wiley & Sons.
References
Flick, U., 2015. Introducing research methodology: A beginner's guide to doing a research
project. Sage.
Jacobs, T., 2016, Industrial-sized Cyber Attacks Threaten the Upstream Sector, Journal of
Petroleum Technology, 68(03), pp.42-50.
Low, S.P. and Ong, J., 2014. Research Design and Methodology. In Project Quality
Management (pp. 69-77). Springer Singapore.
Mackey, A. and Gass, S.M., 2015. Second language research: Methodology and design.
Routledge.
Panneerselvam, R., 2014. Research methodology. PHI Learning Pvt. Ltd..
Sales, N.A., 2012. Regulating cyber-security.
Sauter, M. and Carafano, J., 2012. Homeland Security: A Complete Guide 2/E. McGraw Hill
Professional.
Silverman, D. ed., 2016. Qualitative research. Sage.
Soomro, Z.A., Shah, M.H. and Ahmed, J., 2016, Information security management needs
more holistic approach: A literature review, International Journal of Information
Management, 36(2), pp.215-225.
Taylor, S.J., Bogdan, R. and DeVault, M., 2015. Introduction to qualitative research
methods: A guidebook and resource. John Wiley & Sons.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





