Assignment On Data Communications And Networks
Added on 2022-10-04
6 Pages1517 Words20 Views
DATA COMMUNICATIONS AND NETWORKS
Name
Instructor
Institution
Course
City
Date
DATA COMMUNICATION AND NETWORS
Introduction
Name
Instructor
Institution
Course
City
Date
DATA COMMUNICATION AND NETWORS
Introduction

This paper identifies the resources which are needed to set-up and design a
network infrastructure for a new campus for Holmes Institute which is located in
Melbourne. Holmes institute is a five storey shop with school of information
systems, school of cyber security, school of business, and school of fashion. Each of
the four school has two subnets; i.e. the student and staff subnets. In addition, the
institute has over six departments which are student services, higher education.
Finance, human resource, Exam and Accreditation. The institute has expanded to
include two new schools and an IT center. Due to this the institute has purchased
one metro Ethernet connection from HLNET which provides 10 Mbps for both
download and upload.
Part 1: Holmes network design
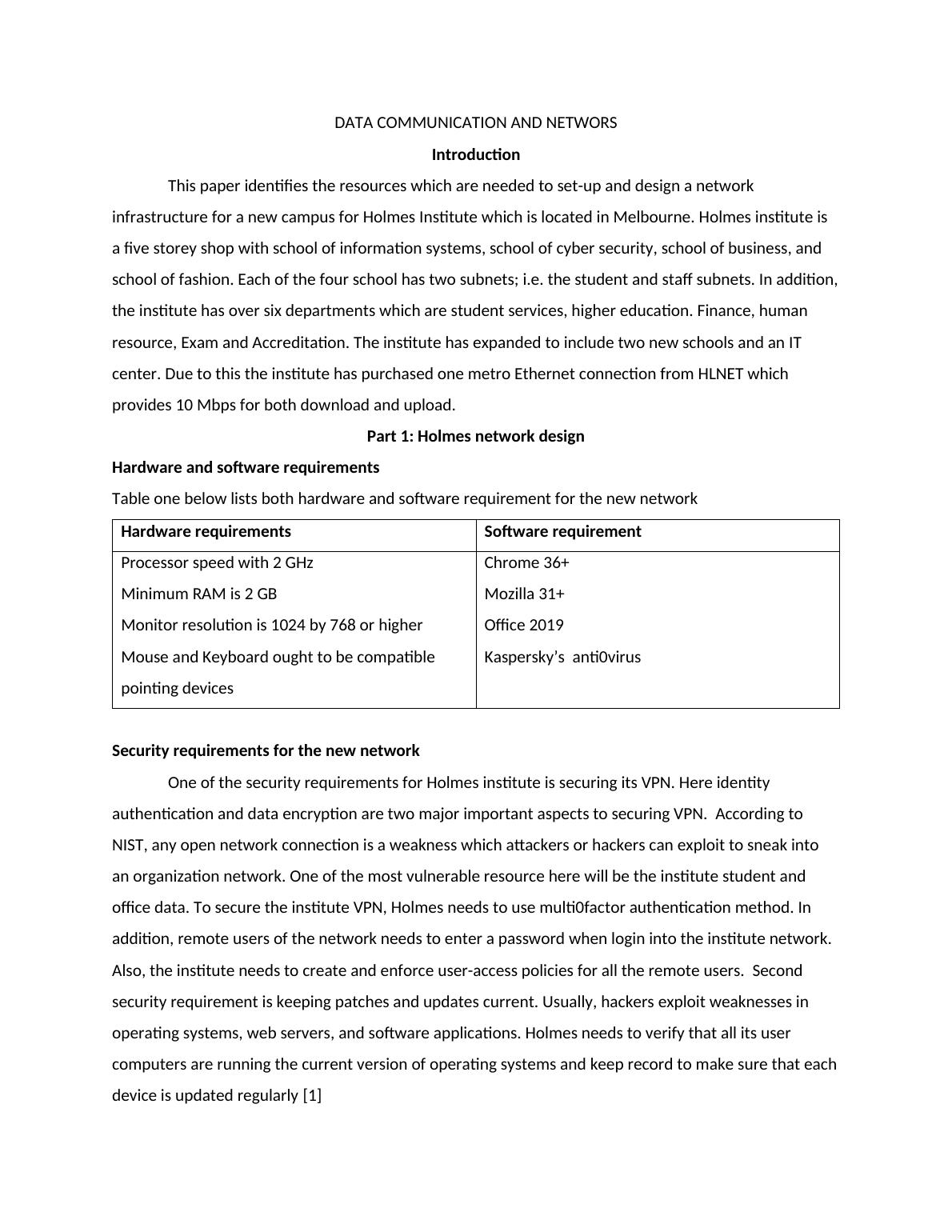
Hardware and software requirements
Table one below lists both hardware and software requirement for the new network
Hardware requirements Software requirement
Processor speed with 2 GHz
Minimum RAM is 2 GB
Monitor resolution is 1024 by 768 or
higher
Mouse and Keyboard ought to be
compatible pointing devices
Chrome 36+
Mozilla 31+
Office 2019
Kaspersky’s anti0virus
Security requirements for the new network
One of the security requirements for Holmes institute is securing its VPN.
Here identity authentication and data encryption are two major important aspects
to securing VPN. According to NIST, any open network connection is a weakness
which attackers or hackers can exploit to sneak into an organization network. One
of the most vulnerable resource here will be the institute student and office data. To
secure the institute VPN, Holmes needs to use multi0factor authentication method.
In addition, remote users of the network needs to enter a password when login into
the institute network. Also, the institute needs to create and enforce user-access
policies for all the remote users. Second security requirement is keeping patches
and updates current. Usually, hackers exploit weaknesses in operating systems,
web servers, and software applications. Holmes needs to verify that all its user
network infrastructure for a new campus for Holmes Institute which is located in
Melbourne. Holmes institute is a five storey shop with school of information
systems, school of cyber security, school of business, and school of fashion. Each of
the four school has two subnets; i.e. the student and staff subnets. In addition, the
institute has over six departments which are student services, higher education.
Finance, human resource, Exam and Accreditation. The institute has expanded to
include two new schools and an IT center. Due to this the institute has purchased
one metro Ethernet connection from HLNET which provides 10 Mbps for both
download and upload.
Part 1: Holmes network design
Hardware and software requirements
Table one below lists both hardware and software requirement for the new network
Hardware requirements Software requirement
Processor speed with 2 GHz
Minimum RAM is 2 GB
Monitor resolution is 1024 by 768 or
higher
Mouse and Keyboard ought to be
compatible pointing devices
Chrome 36+
Mozilla 31+
Office 2019
Kaspersky’s anti0virus
Security requirements for the new network
One of the security requirements for Holmes institute is securing its VPN.
Here identity authentication and data encryption are two major important aspects
to securing VPN. According to NIST, any open network connection is a weakness
which attackers or hackers can exploit to sneak into an organization network. One
of the most vulnerable resource here will be the institute student and office data. To
secure the institute VPN, Holmes needs to use multi0factor authentication method.
In addition, remote users of the network needs to enter a password when login into
the institute network. Also, the institute needs to create and enforce user-access
policies for all the remote users. Second security requirement is keeping patches
and updates current. Usually, hackers exploit weaknesses in operating systems,
web servers, and software applications. Holmes needs to verify that all its user
computers are running the current version of operating systems and keep record to
make sure that each device is updated regularly [1]
Rules in the security policy for the new network
A security policy is a document which states security controls without
specifying the current technologies. A network security policy should always be
applied through-out an organization in a consistent manner. It provides references
for employees to operate their typical activities. For the new institute network, the
institute needs to sign an NDA for each of the student and institute staff about not
disclosing any details about the deployed devices. This rule protects the laid
network devices. Second rule is to regularly apply patches and security updates on
weekly basis, and all services needs to be disabled if they are not in use. This
ensures that all operating systems and applications are up to date. In terms of
internet access, internet access policies should include blocking of all websites
which are deemed inappropriate. Lastly, VPN is there to protect institute data
meaning that it should only be used by the institute staff not the students [2].
Network testing
Network testing is the act of qualitatively and quantitatively measuring the
performance of a computer network. The act tests for records and certain processes
and behaviors of a network. The major objective of network testing is to address
network design faults and any implementation defects. Testing in this case will
include testing functionality of the network, performance, stability, and
interoperability. In addition, testing will assists in evaluating negative and false
positive of network security. It will also assists in profiling and benchmarking
systems and services [3].
Logical diagram
To meet the goals of the institute, this paper will go for Cisco SAFE
architecture for logical design. SAFE design provide the key to simplify cyber
security. The major goal of Cisco SAFE architecture is to provide the bests practices
on implementing and designing a secure network. This type of design uses a
modular approach so as to allow flexibility in a network design and facilitate
troubleshooting and implementation. To implement this design, the institute needs
to take a defense in depth approach, where multiple layers pf protection are
strategically located throughout a network. Specifically the logical topology of the
institute needs to be divided into three functional areas which are enterprise edge,
make sure that each device is updated regularly [1]
Rules in the security policy for the new network
A security policy is a document which states security controls without
specifying the current technologies. A network security policy should always be
applied through-out an organization in a consistent manner. It provides references
for employees to operate their typical activities. For the new institute network, the
institute needs to sign an NDA for each of the student and institute staff about not
disclosing any details about the deployed devices. This rule protects the laid
network devices. Second rule is to regularly apply patches and security updates on
weekly basis, and all services needs to be disabled if they are not in use. This
ensures that all operating systems and applications are up to date. In terms of
internet access, internet access policies should include blocking of all websites
which are deemed inappropriate. Lastly, VPN is there to protect institute data
meaning that it should only be used by the institute staff not the students [2].
Network testing
Network testing is the act of qualitatively and quantitatively measuring the
performance of a computer network. The act tests for records and certain processes
and behaviors of a network. The major objective of network testing is to address
network design faults and any implementation defects. Testing in this case will
include testing functionality of the network, performance, stability, and
interoperability. In addition, testing will assists in evaluating negative and false
positive of network security. It will also assists in profiling and benchmarking
systems and services [3].
Logical diagram
To meet the goals of the institute, this paper will go for Cisco SAFE
architecture for logical design. SAFE design provide the key to simplify cyber
security. The major goal of Cisco SAFE architecture is to provide the bests practices
on implementing and designing a secure network. This type of design uses a
modular approach so as to allow flexibility in a network design and facilitate
troubleshooting and implementation. To implement this design, the institute needs
to take a defense in depth approach, where multiple layers pf protection are
strategically located throughout a network. Specifically the logical topology of the
institute needs to be divided into three functional areas which are enterprise edge,

End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Network Infrastructure Component 2022 Reportlg...
|10
|2182
|17
Access Control TABLE OF CONTENTSlg...
|7
|1683
|344
VPN Technologies and Securitylg...
|9
|2031
|99
Presentation on VPN Networkslg...
|14
|743
|173
Case Study - HTC Contains Certain Security Flawslg...
|4
|521
|11
Network Security: Remote Access, Interconnecting Devices, and WAN Technologieslg...
|9
|1459
|154
