Benefits of Computer Networking in Workplace
VerifiedAdded on 2020/07/22
|16
|4395
|42
AI Summary
The report discusses the benefits of using computer networking to improve communication at work and highlights the importance of a centralized database for storing information about customers and employees. It also touches on the potential risks such as cyber attacks and data redundancy, but notes that these can be mitigated by implementing firewalls and providing staff training.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Data
Communications
Communications
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
INTRODUCTION...........................................................................................................................1
TASK-1 ...........................................................................................................................................1
Benefits of networking ...............................................................................................................1
TASK-2............................................................................................................................................2
a) Logical network diagram for Pine Martin ..............................................................................2
b) The cabling requirement for the design..................................................................................2
c) The function of each infrastructure device.............................................................................4
d) The two specific product that can be used for each infrastructure device..............................5
TASK-3............................................................................................................................................6
a) Actual address and address ranges .........................................................................................6
b) Methods used by different devices.........................................................................................6
TASK-4............................................................................................................................................7
A set of service for the company.................................................................................................7
TASK-5............................................................................................................................................7
Network monitoring tools ..........................................................................................................7
TASK-6............................................................................................................................................8
Security issues that is faced by the company and providing appropriate protection..................8
CONCLUSION ...............................................................................................................................9
REFERENCES ............................................................................................................................10
INTRODUCTION...........................................................................................................................1
TASK-1 ...........................................................................................................................................1
Benefits of networking ...............................................................................................................1
TASK-2............................................................................................................................................2
a) Logical network diagram for Pine Martin ..............................................................................2
b) The cabling requirement for the design..................................................................................2
c) The function of each infrastructure device.............................................................................4
d) The two specific product that can be used for each infrastructure device..............................5
TASK-3............................................................................................................................................6
a) Actual address and address ranges .........................................................................................6
b) Methods used by different devices.........................................................................................6
TASK-4............................................................................................................................................7
A set of service for the company.................................................................................................7
TASK-5............................................................................................................................................7
Network monitoring tools ..........................................................................................................7
TASK-6............................................................................................................................................8
Security issues that is faced by the company and providing appropriate protection..................8
CONCLUSION ...............................................................................................................................9
REFERENCES ............................................................................................................................10

INTRODUCTION
In the data communication the transmission of digital data takes place in between two or
more than two computers and it also allows computers to exchange data. By making use of either
cable media or wireless media the physical connection between networked computing device is
established. The internet is bets known computer network. In data communication the computers
and the communication technologies are being used in order to transfer data from one source to
other and vice-versa. In between two or more nodes it enables the movement of electronic or
digital data (Wu and Shi, 2013. ). The several techniques and technologies are being
incorporated by data communication with primary goal of enabling any form of electronic
communication. The telecommunication, computing networking and radio communication are
technologies that can be sued by data communication in order to transfer data.
Pine Martin Fuels Ltd. provides heating oil in private homes and commercial installations
in UK. This company is facing issues of data inconsistency so in order to overcome this issues
they would network the PCs they have and also hold data centrally. This report will preset the
benefits of networking for this company. Further more this report will also design a proper local
area network for Pine Martin. The appropriate Ipv4 for the network that is designed will also be
allocated in this report.
TASK-1
Benefits of networking
Pine Martin Fuels Ltd. Provides maintenance services for their customers equipment and
also supply heating oil to private homes. The complexity is being faced by the company as all the
data is not hold by PCs and also data is updated in few days. Due to these reasons the customers
are not happy as the data is not delivered on time and the company services is also not so proper.
In order to cope up with these issues this company decided to have the network to their PC's .The
various befits will be provided to the company due to use of networking in the workplace. Some
benefits are as follows-:
Communication – One of the biggest advantage of computer networking is ease of
communication. In between computers it provides a precise, an effective and faster
communication .This makes communication effective. The way of communication between pole
people form same or distinct organization have been improved due to use of computer network
technology (Wang . and Hepsaydir, 2014).. In order to collaborate the activities of work they can
1
In the data communication the transmission of digital data takes place in between two or
more than two computers and it also allows computers to exchange data. By making use of either
cable media or wireless media the physical connection between networked computing device is
established. The internet is bets known computer network. In data communication the computers
and the communication technologies are being used in order to transfer data from one source to
other and vice-versa. In between two or more nodes it enables the movement of electronic or
digital data (Wu and Shi, 2013. ). The several techniques and technologies are being
incorporated by data communication with primary goal of enabling any form of electronic
communication. The telecommunication, computing networking and radio communication are
technologies that can be sued by data communication in order to transfer data.
Pine Martin Fuels Ltd. provides heating oil in private homes and commercial installations
in UK. This company is facing issues of data inconsistency so in order to overcome this issues
they would network the PCs they have and also hold data centrally. This report will preset the
benefits of networking for this company. Further more this report will also design a proper local
area network for Pine Martin. The appropriate Ipv4 for the network that is designed will also be
allocated in this report.
TASK-1
Benefits of networking
Pine Martin Fuels Ltd. Provides maintenance services for their customers equipment and
also supply heating oil to private homes. The complexity is being faced by the company as all the
data is not hold by PCs and also data is updated in few days. Due to these reasons the customers
are not happy as the data is not delivered on time and the company services is also not so proper.
In order to cope up with these issues this company decided to have the network to their PC's .The
various befits will be provided to the company due to use of networking in the workplace. Some
benefits are as follows-:
Communication – One of the biggest advantage of computer networking is ease of
communication. In between computers it provides a precise, an effective and faster
communication .This makes communication effective. The way of communication between pole
people form same or distinct organization have been improved due to use of computer network
technology (Wang . and Hepsaydir, 2014).. In order to collaborate the activities of work they can
1

interact in a matter of seconds. In the company that is Pine Martin network computers will serve
as the backbone for the daily communication from top to bottom level of organization. In order
to send messages and emails at faster speed different types of software can be installed. This is
all due to use of computer networking is possible.
Data sharing – The data sharing is also one of other advantage of computer networks. Within a
local network or remote connected network the company can share its data such as documents,
file, accounts information , reports , presentation files , pictures, videos etc. From one location to
other the images , videos etc can be shared more quickly due to use of computer networks.
Instant and multiple accesses – This is one of the benefits of computer network is that is allows
multiple users to access the similar data at the similar time period from same or remote location.
For an instance World Wide Web .From a different location everyone can access a web page and
at the same time can read the same information. The ease of accessibility will be provide by
computer network in the company.
Cost effective – In different ways a lot of cost of any company will be saved due to building of a
computer network. Through the computer networking “uplinks” can be build that will transfer
files and messages immediately to the other people .This will help the organization to reduce
transportation and expense of communication. With the standards of organization will also be
raised as the advanced technologies will be used in networking. The drive efficiency and cost can
be reduced by storing information in one centralised database. By using this with more
customers the staff can deal in less amount of time. This is possible as they have shared access to
customers and product database. From a single sources of information the company will be able
to reduce errors and improve consistency .And on a schedules' basis the data will be back up
form a single point thus ensuring consistency (McNamara, 2014.)..
Remote access- It will also be beneficial for the employees that are working in this company as
they can connect to local network from their work in order to access and edit files. In order to log
in they will only need a interface or network remote IP.
TASK-2
a) Logical network diagram for Pine Martin
2
as the backbone for the daily communication from top to bottom level of organization. In order
to send messages and emails at faster speed different types of software can be installed. This is
all due to use of computer networking is possible.
Data sharing – The data sharing is also one of other advantage of computer networks. Within a
local network or remote connected network the company can share its data such as documents,
file, accounts information , reports , presentation files , pictures, videos etc. From one location to
other the images , videos etc can be shared more quickly due to use of computer networks.
Instant and multiple accesses – This is one of the benefits of computer network is that is allows
multiple users to access the similar data at the similar time period from same or remote location.
For an instance World Wide Web .From a different location everyone can access a web page and
at the same time can read the same information. The ease of accessibility will be provide by
computer network in the company.
Cost effective – In different ways a lot of cost of any company will be saved due to building of a
computer network. Through the computer networking “uplinks” can be build that will transfer
files and messages immediately to the other people .This will help the organization to reduce
transportation and expense of communication. With the standards of organization will also be
raised as the advanced technologies will be used in networking. The drive efficiency and cost can
be reduced by storing information in one centralised database. By using this with more
customers the staff can deal in less amount of time. This is possible as they have shared access to
customers and product database. From a single sources of information the company will be able
to reduce errors and improve consistency .And on a schedules' basis the data will be back up
form a single point thus ensuring consistency (McNamara, 2014.)..
Remote access- It will also be beneficial for the employees that are working in this company as
they can connect to local network from their work in order to access and edit files. In order to log
in they will only need a interface or network remote IP.
TASK-2
a) Logical network diagram for Pine Martin
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
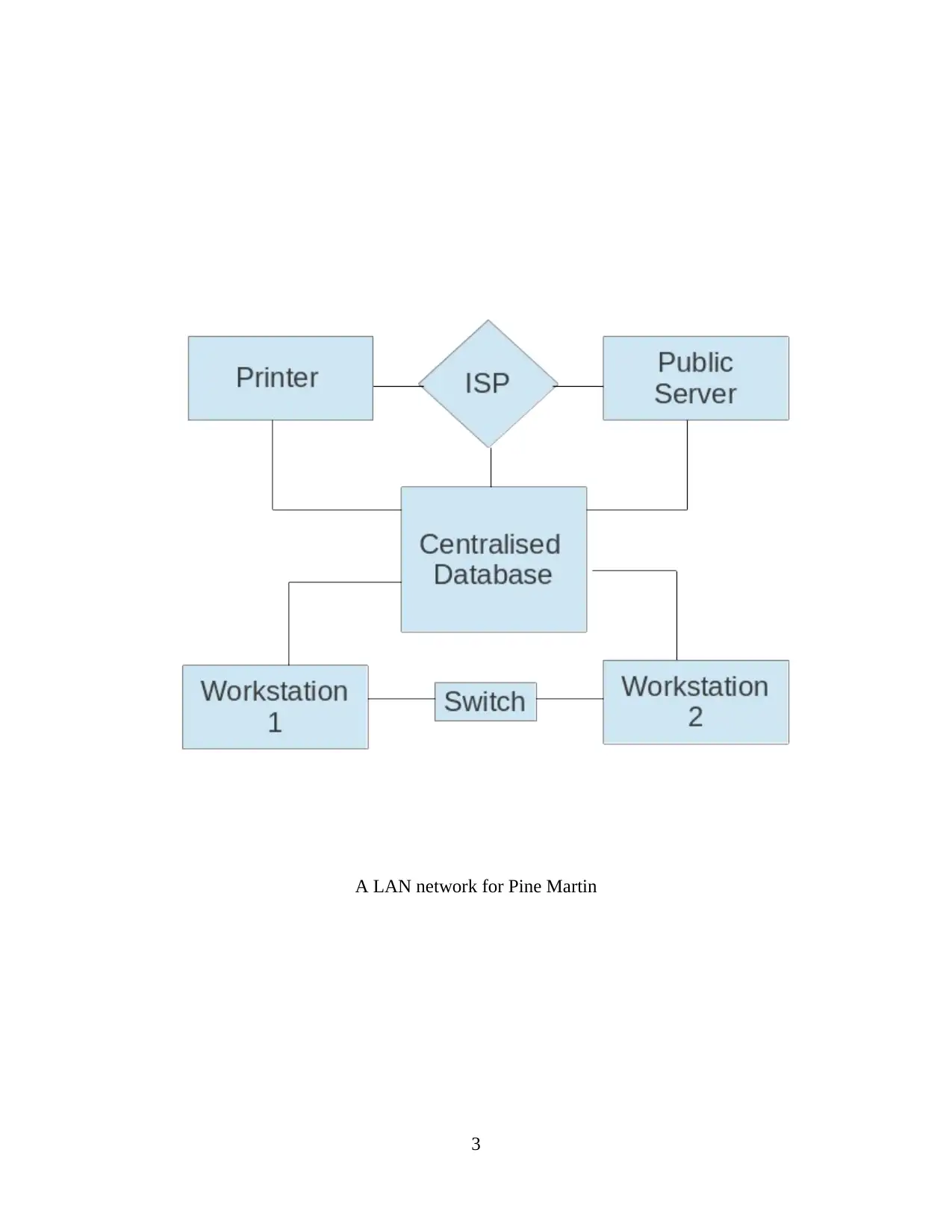
A LAN network for Pine Martin
3
3

b) The cabling requirement for the design
By making use of cables the information can be transferred from one network devise to
another. With the Local area network(LANs) there are several types of cables that can be used.
In some case only one type of cable is been utilized by a network while in some cases variety of
cable types is been used by other networks (Dimitrova and Nord, 2014. ) . Some commonly used
cables can be un- shielded twisted pair cable, shielded twisted pair cable, coaxial cable, fibre
optic cable, wireless LAN etc. In this architecture that is been made for the company Pine Martin
the cable that is been sued is Wireless LAN. Today more and more company's are operating
without cables that is in the wireless mode. The high frequency radio signals are been used in
wireless LAN. In order to interact with workstations, severs or hubs they make use of lasers or
infrared light beams. To send or receive data each workstation and file servers on a wireless
network have some transceiver or antenna. Through cellular phones technology also wireless
communication can take place as for longer distances. In order to connect to LAN wireless
networks are great for allowing portable devices or remote areas. In older building where it is not
possible to install cables wireless networks are also beneficial over there. In order to make sure
standards and interpretability for wireless network the Wi-Fi-alliance is a global organization.
The wireless network are also known as Wi-Fi (Koenig and Zwick, 2013. ). The Ethernet
protocol are been used by Wi-Fi networks. At a standard of 802.11a it provides max speed of
about 54 Mbps with a typical range of about 150 feet. At a stand of 802.11n it provides a max
speed of about 100 Mbps at a typical range of 300+ feet. To unauthorized use wireless networks
are much more susceptible in comparison with cables networks. In order to interact with one
another wireless network make use of radio waves. To secure the networks from unauthorized
wireless use three basic techniques are been used.
Encryption – The strongest encryption is been enabled that is been supported by the device. The
string passwords are been used that contains symbols, numbers and mixed case letters.
Isolation – The wireless router need to be used that places connections on a subnet .This will
secure the data on private networks to go through inert traffic.
Hidden SSID- The service set identifiers(SSID)is been there in every access point that will by
default is broadcast to the client devices so that access point is been discovered by them. The
standard client connection software will bot see the access point by disabling this feature.
4
By making use of cables the information can be transferred from one network devise to
another. With the Local area network(LANs) there are several types of cables that can be used.
In some case only one type of cable is been utilized by a network while in some cases variety of
cable types is been used by other networks (Dimitrova and Nord, 2014. ) . Some commonly used
cables can be un- shielded twisted pair cable, shielded twisted pair cable, coaxial cable, fibre
optic cable, wireless LAN etc. In this architecture that is been made for the company Pine Martin
the cable that is been sued is Wireless LAN. Today more and more company's are operating
without cables that is in the wireless mode. The high frequency radio signals are been used in
wireless LAN. In order to interact with workstations, severs or hubs they make use of lasers or
infrared light beams. To send or receive data each workstation and file servers on a wireless
network have some transceiver or antenna. Through cellular phones technology also wireless
communication can take place as for longer distances. In order to connect to LAN wireless
networks are great for allowing portable devices or remote areas. In older building where it is not
possible to install cables wireless networks are also beneficial over there. In order to make sure
standards and interpretability for wireless network the Wi-Fi-alliance is a global organization.
The wireless network are also known as Wi-Fi (Koenig and Zwick, 2013. ). The Ethernet
protocol are been used by Wi-Fi networks. At a standard of 802.11a it provides max speed of
about 54 Mbps with a typical range of about 150 feet. At a stand of 802.11n it provides a max
speed of about 100 Mbps at a typical range of 300+ feet. To unauthorized use wireless networks
are much more susceptible in comparison with cables networks. In order to interact with one
another wireless network make use of radio waves. To secure the networks from unauthorized
wireless use three basic techniques are been used.
Encryption – The strongest encryption is been enabled that is been supported by the device. The
string passwords are been used that contains symbols, numbers and mixed case letters.
Isolation – The wireless router need to be used that places connections on a subnet .This will
secure the data on private networks to go through inert traffic.
Hidden SSID- The service set identifiers(SSID)is been there in every access point that will by
default is broadcast to the client devices so that access point is been discovered by them. The
standard client connection software will bot see the access point by disabling this feature.
4

By making use of wireless network the mobility can be provided. As with laptop or
mobile device through the mall, office access will be available. The free access Wi-Fi is been
offered by more and more business today. The setup for wireless network is also fats. By
clicking on connect to a network the wireless network can be connected. The cost of setting up
this network will also be less in comparison with buying and installing cables.
c) The function of each infrastructure device
The local area network that is been designed for this company contain components such as -:
Centralized database
Internet service provider
Switch
Public server
Printer
Workstation 1
Workstation 2
In the centralised database all the other components that is public server, printer , workstation 1 ,
workstation 2 will be connected. All the data and information will be stored on central database.
In a single database at one single location a centralised database system will keep the data.
Against other type of database centralised database hold substantial amount of advantages. Some
of them are as follows-:
By making use of centralised database in this company data integrity and data
redundancy can be reduced. All the data will store in one primary records .The correct
data will be maintained and it will be also be consistent and this data integrity will be
enhanced (A centralised database approach , 2017).
The security of data will also be more than the single storage location represents that
from one place only database can be attacked .
In comparison with other types of database better data preservation will be there as it
often include fault-tolerance setup.
Due to simplicity of having design of single database it can be used easily by end-user .
It will also offer easy data portability and data administration
The use of centralised database is a cost-effective process as the cost of labour, power
supply, maintenance cost etc all will be reduced.
5
mobile device through the mall, office access will be available. The free access Wi-Fi is been
offered by more and more business today. The setup for wireless network is also fats. By
clicking on connect to a network the wireless network can be connected. The cost of setting up
this network will also be less in comparison with buying and installing cables.
c) The function of each infrastructure device
The local area network that is been designed for this company contain components such as -:
Centralized database
Internet service provider
Switch
Public server
Printer
Workstation 1
Workstation 2
In the centralised database all the other components that is public server, printer , workstation 1 ,
workstation 2 will be connected. All the data and information will be stored on central database.
In a single database at one single location a centralised database system will keep the data.
Against other type of database centralised database hold substantial amount of advantages. Some
of them are as follows-:
By making use of centralised database in this company data integrity and data
redundancy can be reduced. All the data will store in one primary records .The correct
data will be maintained and it will be also be consistent and this data integrity will be
enhanced (A centralised database approach , 2017).
The security of data will also be more than the single storage location represents that
from one place only database can be attacked .
In comparison with other types of database better data preservation will be there as it
often include fault-tolerance setup.
Due to simplicity of having design of single database it can be used easily by end-user .
It will also offer easy data portability and data administration
The use of centralised database is a cost-effective process as the cost of labour, power
supply, maintenance cost etc all will be reduced.
5
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

As the data is been stored in one location so it would be easy to change, re-organized and
analysed the data .
From the same location and at the same time all the information can be created. In case if any updation that is been done on any set of data then that updation will be
received immediately by very end-user. The up to date information will be maintained by
centralised database. The designing of centralised database is also not so difficult in
comparison with distributed database as they are based on hierarchical structure.
Internet service provider(ISP)- By making use of ISP the internet service is been provided to th
workstation,printers, public servers and central database. The Internet access is bee provide
through ISP in this organization. The internet access, internet transit,web hosting and collocation
are the internet serveries that is been provided by ISP. In order to connect users to this network
the internet access is been provided by ISP. Through their ISP the internet connected device run
each requests. This mainly done to download web pages and files .
Printer – It is been used in the company in order to print the documents .It is also been connected
to central database as all the information regrading it will be stored their safely. While printing
documents it is been connected to ISP to make available the documents for printing.
Workstation 1 – All the information regarding details of customer, employees and other essential
details are there in it which is connected to central database. The correct information will be
maintained and used by the company due to use of centralised database.
d) The two specific product that can be used for each infrastructure device
Switch – The network is being created by the switches. They can be a valuable asset to
networking. By using switches the speed and the capacity of then toward can be increased. Each
packet in a network is being examined by switches. The benefits of switch are that reduced
collision and isolated traffic thus reliving congestion. The cost of switch is 3 to 5 times the cost
of hub and in comparison to hub the packet processing rakes a longer time (Yan and Tipper,
2013).
Servers – The functionality for other program is being provided by a server. The services such as
sharing of data or resources is being provided by servers. Among multiple clients the services are
being given by them. The multiple clients can be served by a single server and multiple severs
can be used by a single client.
6
analysed the data .
From the same location and at the same time all the information can be created. In case if any updation that is been done on any set of data then that updation will be
received immediately by very end-user. The up to date information will be maintained by
centralised database. The designing of centralised database is also not so difficult in
comparison with distributed database as they are based on hierarchical structure.
Internet service provider(ISP)- By making use of ISP the internet service is been provided to th
workstation,printers, public servers and central database. The Internet access is bee provide
through ISP in this organization. The internet access, internet transit,web hosting and collocation
are the internet serveries that is been provided by ISP. In order to connect users to this network
the internet access is been provided by ISP. Through their ISP the internet connected device run
each requests. This mainly done to download web pages and files .
Printer – It is been used in the company in order to print the documents .It is also been connected
to central database as all the information regrading it will be stored their safely. While printing
documents it is been connected to ISP to make available the documents for printing.
Workstation 1 – All the information regarding details of customer, employees and other essential
details are there in it which is connected to central database. The correct information will be
maintained and used by the company due to use of centralised database.
d) The two specific product that can be used for each infrastructure device
Switch – The network is being created by the switches. They can be a valuable asset to
networking. By using switches the speed and the capacity of then toward can be increased. Each
packet in a network is being examined by switches. The benefits of switch are that reduced
collision and isolated traffic thus reliving congestion. The cost of switch is 3 to 5 times the cost
of hub and in comparison to hub the packet processing rakes a longer time (Yan and Tipper,
2013).
Servers – The functionality for other program is being provided by a server. The services such as
sharing of data or resources is being provided by servers. Among multiple clients the services are
being given by them. The multiple clients can be served by a single server and multiple severs
can be used by a single client.
6

TASK-3
a) Actual address and address ranges
On the network an IP address is a numerical representation that recognizes a specific
interface. In Ipv4 addresses are 32-bit long. The IP stands fir internet protocol and it represents
binary numbers but they are expressed mainly in the form of decimal or hexadecimal. It is doe to
make it easier for reading for humans. The IP address classes can be divided into fiv clases and
they are as follows-:
Class A – 0.0.0.0 – 127.255.255.255
In this the firs doted decimal or first eight bits are network part and the left over is the
host part of the address (Wang . and Hepsaydir, 2014).
Class B- 128.0.0.0- 191.255.255.255
The first bit is set to 1 in all class b networks and the second bit is set to 0.
Class C- 192.0.0.0- 223.255.255.255
In this the fits tow bit are being set as 1 and the third bit is set to 0.
Class D- 224.0.0.0.0 – 239.255.255.255
It is mainly used for multi casting applications. It cannot be used for normal operations of
networking. The firs three bit are been set to 1 and the fourth bit set to 0.
Class E – 240.0.0.0- 255.255.255.255
The firs four bit is set to 1 in the classes E.
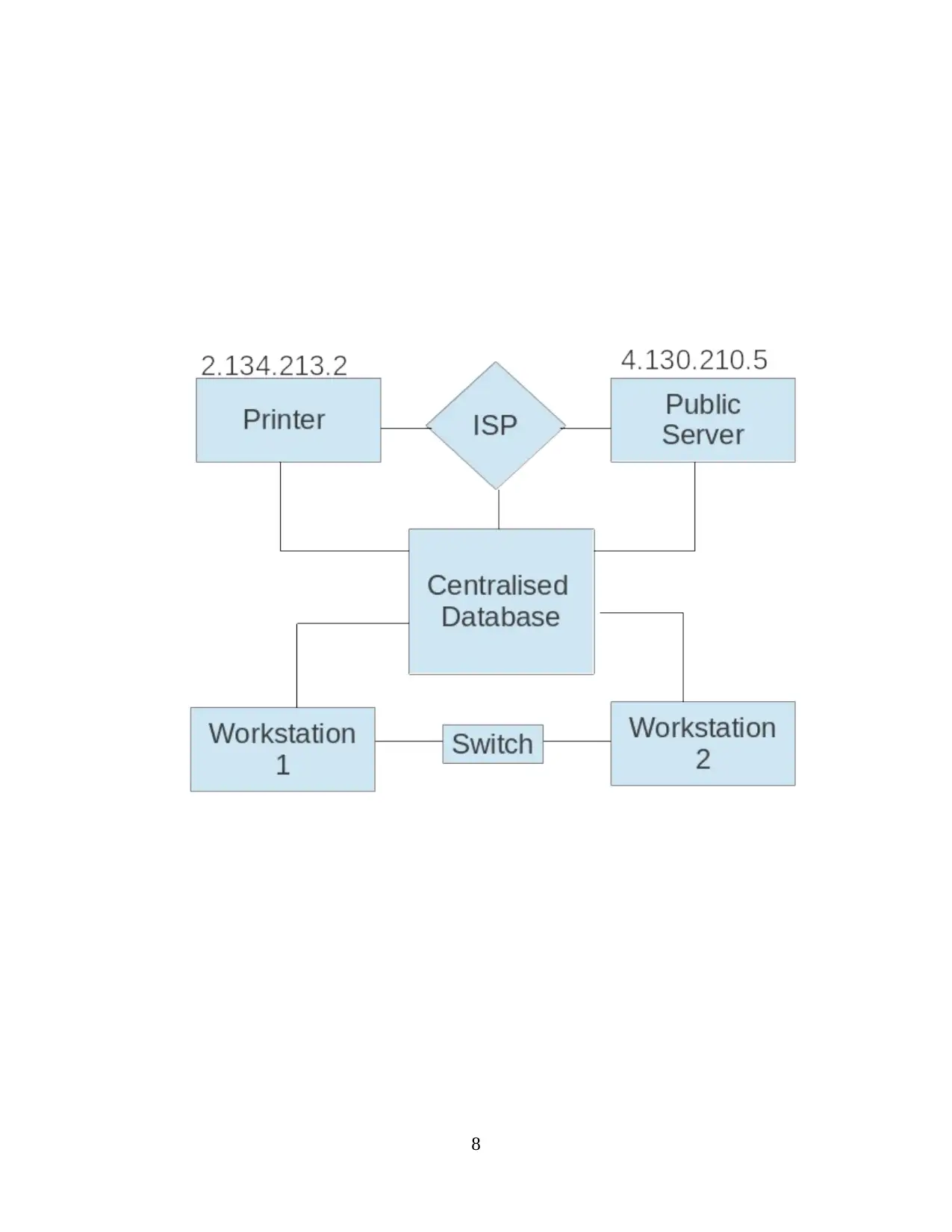
In this diagram that is been made for Pine Martin the class A IP address is being used in order to
communicate with other system. The IP address that is being used by workstation 1 is
2.134.213.2 and the other IP address that is been used is 4.130.210.5
7
a) Actual address and address ranges
On the network an IP address is a numerical representation that recognizes a specific
interface. In Ipv4 addresses are 32-bit long. The IP stands fir internet protocol and it represents
binary numbers but they are expressed mainly in the form of decimal or hexadecimal. It is doe to
make it easier for reading for humans. The IP address classes can be divided into fiv clases and
they are as follows-:
Class A – 0.0.0.0 – 127.255.255.255
In this the firs doted decimal or first eight bits are network part and the left over is the
host part of the address (Wang . and Hepsaydir, 2014).
Class B- 128.0.0.0- 191.255.255.255
The first bit is set to 1 in all class b networks and the second bit is set to 0.
Class C- 192.0.0.0- 223.255.255.255
In this the fits tow bit are being set as 1 and the third bit is set to 0.
Class D- 224.0.0.0.0 – 239.255.255.255
It is mainly used for multi casting applications. It cannot be used for normal operations of
networking. The firs three bit are been set to 1 and the fourth bit set to 0.
Class E – 240.0.0.0- 255.255.255.255
The firs four bit is set to 1 in the classes E.
In this diagram that is been made for Pine Martin the class A IP address is being used in order to
communicate with other system. The IP address that is being used by workstation 1 is
2.134.213.2 and the other IP address that is been used is 4.130.210.5
7
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

b) Methods used by different devices
On the internet an IP address is an address that is being given to a device. By the internet
service provider the IP address is being assigned the static or dynamic IP address is being given
by the ISP (McNamara, 2014.).
Static IP- By the ISP a static IP address is being assigned permanently. Even if the computer
reboots this IP address will not change. To a server hosting website a static IP address is being
assigned. It is mainly good for web serves as the address does not change.
Dynamic IP address – By the ISP a dynamic IP address is assigned dynamically. The IP address
is assigned dynamically by ISP each time when the computer is being rebooted. In comparison
to static IP address it is cheaper and more private is being given as IP address changes.
TASK-4
A set of service for the company
The company can make use of e-mail and domain name service(DNS) in order to run
their network.
Domain name service (DNS)- It can be used by the company in order to resolve human readable
host name into machine readable IP address. For an instance it converts host names such as
www.dyn.com into machine readable form like 203.12.247.114.The other information such as
domain names is also been given by DNS. For the internet DNS is like a phone book. When any
user visit any web page such as http://www.dyne.com in a browser,the DNS is being used by the
computer in order to get IP address of the website. By the use of DNS the user is being directed
to the correct website (Kuzlu, Pipattanasomporn and Rahman, 2014). For the company it is
necessary as all it can view the right website with use of DNS. It converts human readable form
into machine readable form so that user is directed towards the website that they want to visit.
E-mails – By making use of this the company can exchange message with people or customer
through electronic data. It can be useful in the business as in comparison with traditional post it
is been delivered at extremely faster speed. When making use of broadband it is cheaper. In the
company it can be used to make communication better and effective. The better coordination
with customers, suppliers and business partners can be made through e-mails. The productivity
can be increased due to use of e-mails.
9
On the internet an IP address is an address that is being given to a device. By the internet
service provider the IP address is being assigned the static or dynamic IP address is being given
by the ISP (McNamara, 2014.).
Static IP- By the ISP a static IP address is being assigned permanently. Even if the computer
reboots this IP address will not change. To a server hosting website a static IP address is being
assigned. It is mainly good for web serves as the address does not change.
Dynamic IP address – By the ISP a dynamic IP address is assigned dynamically. The IP address
is assigned dynamically by ISP each time when the computer is being rebooted. In comparison
to static IP address it is cheaper and more private is being given as IP address changes.
TASK-4
A set of service for the company
The company can make use of e-mail and domain name service(DNS) in order to run
their network.
Domain name service (DNS)- It can be used by the company in order to resolve human readable
host name into machine readable IP address. For an instance it converts host names such as
www.dyn.com into machine readable form like 203.12.247.114.The other information such as
domain names is also been given by DNS. For the internet DNS is like a phone book. When any
user visit any web page such as http://www.dyne.com in a browser,the DNS is being used by the
computer in order to get IP address of the website. By the use of DNS the user is being directed
to the correct website (Kuzlu, Pipattanasomporn and Rahman, 2014). For the company it is
necessary as all it can view the right website with use of DNS. It converts human readable form
into machine readable form so that user is directed towards the website that they want to visit.
E-mails – By making use of this the company can exchange message with people or customer
through electronic data. It can be useful in the business as in comparison with traditional post it
is been delivered at extremely faster speed. When making use of broadband it is cheaper. In the
company it can be used to make communication better and effective. The better coordination
with customers, suppliers and business partners can be made through e-mails. The productivity
can be increased due to use of e-mails.
9

TASK-5
Network monitoring tools
The network monitoring tools that can be used by the company are as follows-:
Nagios – In the year 1999 it was first launched. By Nagios enterprise it is being sponsored.
Through sales of its commercial products and services it supports the community. In order to
make sure that systems, functions, business process are properly functioning nagios monitors the
complete IT infrastructure (Koenig and Zwick, 2013. ). If there is any failure Nagios make alert
technical staff about the issues. This is done so that remedy process are structured .This will
reduce the effect on business process, end-users or customers. The applications, servers,
operating systems are being monitored by this networking tools (Nagios networking tool ,
2017). By making use of powerful script API it provides easy in-house monitoring. The
infrastructure outrages are being detected faster (Wu and Shi, 2013. ). Via emails or SMS alerts
can be given to technical staff .The thousands of nodes is monitored. It is an open source
software so it is free and is also released under GPL licence.
Advances IP scanner- The network devices on the network can be detected easily by advance IP
scanner. It is also fast in detecting network devices. By making use of this the common sevices
such as HTTP, FTP can also be connected on the remote machine. On the machine the installer
allows installing the application. In order to analyse LAN it is free and reliable network scanner.
All the network dives are being represented by the program. To the shared folders the access is
been given . It generally provides a user-friendly interface. All the computers in wireless local
network is been located by this scanners in just few seconds. To the shared folders and FTP
servers it provides easy access (Gungor and Hancke, 2013).
TASK-6
Security issues that is faced by the company and providing appropriate protection
The issues that will be faced by the company related to the new network will be as
follows-:
In case if the central database is been attacked by some attacker than all the necessary
information or data about the customer or employees will be lost. As the entire company
is dependent in central database so a lot of damage will be faced in case of any cyber
attacks. In these cyber attacks all the necessary information of the company is being
attacked by the attacker. Due to this the company may face loss both financially and also
10
Network monitoring tools
The network monitoring tools that can be used by the company are as follows-:
Nagios – In the year 1999 it was first launched. By Nagios enterprise it is being sponsored.
Through sales of its commercial products and services it supports the community. In order to
make sure that systems, functions, business process are properly functioning nagios monitors the
complete IT infrastructure (Koenig and Zwick, 2013. ). If there is any failure Nagios make alert
technical staff about the issues. This is done so that remedy process are structured .This will
reduce the effect on business process, end-users or customers. The applications, servers,
operating systems are being monitored by this networking tools (Nagios networking tool ,
2017). By making use of powerful script API it provides easy in-house monitoring. The
infrastructure outrages are being detected faster (Wu and Shi, 2013. ). Via emails or SMS alerts
can be given to technical staff .The thousands of nodes is monitored. It is an open source
software so it is free and is also released under GPL licence.
Advances IP scanner- The network devices on the network can be detected easily by advance IP
scanner. It is also fast in detecting network devices. By making use of this the common sevices
such as HTTP, FTP can also be connected on the remote machine. On the machine the installer
allows installing the application. In order to analyse LAN it is free and reliable network scanner.
All the network dives are being represented by the program. To the shared folders the access is
been given . It generally provides a user-friendly interface. All the computers in wireless local
network is been located by this scanners in just few seconds. To the shared folders and FTP
servers it provides easy access (Gungor and Hancke, 2013).
TASK-6
Security issues that is faced by the company and providing appropriate protection
The issues that will be faced by the company related to the new network will be as
follows-:
In case if the central database is been attacked by some attacker than all the necessary
information or data about the customer or employees will be lost. As the entire company
is dependent in central database so a lot of damage will be faced in case of any cyber
attacks. In these cyber attacks all the necessary information of the company is being
attacked by the attacker. Due to this the company may face loss both financially and also
10

in terms of reputation. The company will also loose its customer as they will think that
security is not so up to the mark at this company. There are many attacks that is being
taking place(Dimitrova and Nord, 2014. ) .The various cyber attacks can be pharming,
phishing, viruses, malware etc. All these can have negative impact on the network and
the essential information can be leaked to rival companies or their party that can be
dangerous or harmful for the company.
Due to use of centralized database there are high chances that data redundancy will be
there. In this the same data is stored again and again .So a lot of space is been taken by
the same data. A lot of confusion is also created due to data redundancy and when
updation is being done at that time there is a lot of confusion that is being faced.
To all these issues related to security that is being faced can be over come by the following
ways-:
The company can establish security polices for Bring Your Own devise BYOD. Against cyber
attacks the organization can safeguard itself by following these steps-:
Identify – The full inventory of most valuable assets can be conducted (Boudet and Leiserowitz,
2014).
Protect- In order to defend against a cyber attacks implement the protective measure that need to
be implemented.
Detected- The security system need to be setup and the team need to en informed about the
incident.
Respond- In order to maintain operations of business in short terms have an incidence report.
Firewall- The company can make use of firewall in order to provide security to the new network
that is been developed. In case of nay attacks, it will secure the network. It will act as a barrier
between trusted and untrusted network.
Training to employees – In case of any data redundancy the training need to be given to the
employees in order to handle this issues. The team also need to be taught that spam and phishing
e-mails can download bugs onto devices and also the attackers will also be allowed to eter all
files. The training need to be given to them on order to discover suspicious activity and deal with
it immediately (Asadi, Wang and Mancuso, 2014).
11
security is not so up to the mark at this company. There are many attacks that is being
taking place(Dimitrova and Nord, 2014. ) .The various cyber attacks can be pharming,
phishing, viruses, malware etc. All these can have negative impact on the network and
the essential information can be leaked to rival companies or their party that can be
dangerous or harmful for the company.
Due to use of centralized database there are high chances that data redundancy will be
there. In this the same data is stored again and again .So a lot of space is been taken by
the same data. A lot of confusion is also created due to data redundancy and when
updation is being done at that time there is a lot of confusion that is being faced.
To all these issues related to security that is being faced can be over come by the following
ways-:
The company can establish security polices for Bring Your Own devise BYOD. Against cyber
attacks the organization can safeguard itself by following these steps-:
Identify – The full inventory of most valuable assets can be conducted (Boudet and Leiserowitz,
2014).
Protect- In order to defend against a cyber attacks implement the protective measure that need to
be implemented.
Detected- The security system need to be setup and the team need to en informed about the
incident.
Respond- In order to maintain operations of business in short terms have an incidence report.
Firewall- The company can make use of firewall in order to provide security to the new network
that is been developed. In case of nay attacks, it will secure the network. It will act as a barrier
between trusted and untrusted network.
Training to employees – In case of any data redundancy the training need to be given to the
employees in order to handle this issues. The team also need to be taught that spam and phishing
e-mails can download bugs onto devices and also the attackers will also be allowed to eter all
files. The training need to be given to them on order to discover suspicious activity and deal with
it immediately (Asadi, Wang and Mancuso, 2014).
11
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CONCLUSION
Thus summing up the above report it can be concluded that by making use computer
networking the communication can be made effective at workplace and also it is a cost-effective
process. The centralized database can be used in which all the information about customers and
employees will be stored and in comparison with other database it requires less costs. The
business such as cyber attacks,data redundancy can be faced due to new network. It can over
come by making of firewalls and also by giving training to staff at workplace.
12
Thus summing up the above report it can be concluded that by making use computer
networking the communication can be made effective at workplace and also it is a cost-effective
process. The centralized database can be used in which all the information about customers and
employees will be stored and in comparison with other database it requires less costs. The
business such as cyber attacks,data redundancy can be faced due to new network. It can over
come by making of firewalls and also by giving training to staff at workplace.
12

REFERENCES
Books and journals
Asadi, A., Wang, Q. and Mancuso, V., 2014. A survey on device-to-device communication in
cellular networks. IEEE Communications Surveys & Tutorials. 16(4). pp.1801-1819.
Boudet, H. and Leiserowitz, A., 2014. “Fracking” controversy and communication: Using
national survey data to understand public perceptions of hydraulic fracturing. Energy
Policy. 65. pp.57-67.
Dimitrova, D.V. and Nord, L.W., 2014. The effects of digital media on political knowledge and
participation in election campaigns: Evidence from panel data. Communication Research.
41(1), pp.95-118.
Gungor, V.C. and Hancke, G.P., 2013. A survey on smart grid potential applications and
communication requirements. IEEE Transactions on Industrial Informatics. 9(1). pp.28-
42.
Koenig, S. and Zwick, T., 2013. Wireless sub-THz communication system with high data
rate. Nature Photonics. 7(12). pp.977-981.
Kuzlu, M., Pipattanasomporn, M. and Rahman, S., 2014. Communication network requirements
for major smart grid applications in HAN, NAN and WAN. Computer Networks. 67.
pp.74-88.
McNamara, J.E., 2014. Technical aspects of data communication. Digital Press.
Wang, C.X. and Hepsaydir, E., 2014. Cellular architecture and key technologies for 5G wireless
communication networks. IEEE Communications Magazine. 52(2). pp.122-130.
Wu, J. and Shi, L., 2013. Event-based sensor data scheduling: Trade-off between communication
rate and estimation quality. IEEE Transactions on automatic control. 58(4). pp.1041-
1046.
Yan, Y. and Tipper, D., 2013. A survey on smart grid communication infrastructures:
Motivations, requirements and challenges. IEEE communications surveys & tutorials.
15(1). pp.5-20.
Online
13
Books and journals
Asadi, A., Wang, Q. and Mancuso, V., 2014. A survey on device-to-device communication in
cellular networks. IEEE Communications Surveys & Tutorials. 16(4). pp.1801-1819.
Boudet, H. and Leiserowitz, A., 2014. “Fracking” controversy and communication: Using
national survey data to understand public perceptions of hydraulic fracturing. Energy
Policy. 65. pp.57-67.
Dimitrova, D.V. and Nord, L.W., 2014. The effects of digital media on political knowledge and
participation in election campaigns: Evidence from panel data. Communication Research.
41(1), pp.95-118.
Gungor, V.C. and Hancke, G.P., 2013. A survey on smart grid potential applications and
communication requirements. IEEE Transactions on Industrial Informatics. 9(1). pp.28-
42.
Koenig, S. and Zwick, T., 2013. Wireless sub-THz communication system with high data
rate. Nature Photonics. 7(12). pp.977-981.
Kuzlu, M., Pipattanasomporn, M. and Rahman, S., 2014. Communication network requirements
for major smart grid applications in HAN, NAN and WAN. Computer Networks. 67.
pp.74-88.
McNamara, J.E., 2014. Technical aspects of data communication. Digital Press.
Wang, C.X. and Hepsaydir, E., 2014. Cellular architecture and key technologies for 5G wireless
communication networks. IEEE Communications Magazine. 52(2). pp.122-130.
Wu, J. and Shi, L., 2013. Event-based sensor data scheduling: Trade-off between communication
rate and estimation quality. IEEE Transactions on automatic control. 58(4). pp.1041-
1046.
Yan, Y. and Tipper, D., 2013. A survey on smart grid communication infrastructures:
Motivations, requirements and challenges. IEEE communications surveys & tutorials.
15(1). pp.5-20.
Online
13

A centralised database approach . 2017. [Online] Available through:
<https://www.ukessays.com/essays/information-technology/a-centralized-database-
approach.php/>.
Nagios networking tool . 2017. [Online] Available through: <https://www.nagios.org/>.
14
<https://www.ukessays.com/essays/information-technology/a-centralized-database-
approach.php/>.
Nagios networking tool . 2017. [Online] Available through: <https://www.nagios.org/>.
14
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





