Wireless LAN Network Design and Implementation
VerifiedAdded on 2020/02/19
|12
|2496
|31
AI Summary
This assignment delves into the intricacies of designing and implementing wireless local area networks (WLANs). It examines key aspects such as network topology, security protocols, performance optimization, and the advantages WLANs offer businesses. The document emphasizes the importance of scalability, reliability, and user experience in a successful WLAN deployment. It also discusses relevant standards and best practices for ensuring a secure and efficient wireless network environment.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Data Communication 1
CSC00240 – Data Communications and Networks
Submitted By
Course
Professor
Date
CSC00240 – Data Communications and Networks
Submitted By
Course
Professor
Date
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Data Communication 2
Abstract
Wireless local Area Network (WLAN) can be defined as the network that connects the various
networking devices by using radio signals or wireless networking signals. This networking is
considered as financial cost effective and is a perfect solution for remote access. Various
methods can be considered for the implementation of WLAN as various products or vendors are
available. The perfect solution of WLAN must include networking/ hardware devices like
firewall, router, NIC, gateways and various software for the remote access, creating VPN. This
combination helps to implement secure WLAN effectively. Implementing a secured wireless
network is the main challenge for Biomedical Company. This report will focus on physical and
logical designs with topology that can be implemented in Biomedical Company by keeping main
consideration on security on the basis of organizational structure. (Ro, E., 2002).
This framework gives adaptability of operation. Server will be configured with very good
configuration as it can connect as well as maintain with the clients. All other systems except
servers will be configured as clients. As installation of LAN is very expensive for two building,
therefore configuring WLAN will be best solution. It will require very less maintenance and will
be easy to remove any problem. (Iyer, A. & Badgujar, A., 2013).
Abstract
Wireless local Area Network (WLAN) can be defined as the network that connects the various
networking devices by using radio signals or wireless networking signals. This networking is
considered as financial cost effective and is a perfect solution for remote access. Various
methods can be considered for the implementation of WLAN as various products or vendors are
available. The perfect solution of WLAN must include networking/ hardware devices like
firewall, router, NIC, gateways and various software for the remote access, creating VPN. This
combination helps to implement secure WLAN effectively. Implementing a secured wireless
network is the main challenge for Biomedical Company. This report will focus on physical and
logical designs with topology that can be implemented in Biomedical Company by keeping main
consideration on security on the basis of organizational structure. (Ro, E., 2002).
This framework gives adaptability of operation. Server will be configured with very good
configuration as it can connect as well as maintain with the clients. All other systems except
servers will be configured as clients. As installation of LAN is very expensive for two building,
therefore configuring WLAN will be best solution. It will require very less maintenance and will
be easy to remove any problem. (Iyer, A. & Badgujar, A., 2013).

Data Communication 3
Table of Contents
1. Introduction……….............................…..................…..................…..................…… 4
2. Analysis of User Requirements…......….......…..................…..................…............... 5
Business Objective…................…..................…..................…..................…........... 5
Challenge of Network Security…..................…..................…..................….............. 5
Scalability…..................….........…..................…..................…..................…............ 5
Remote Access…..................….…..................…..................…..................…............ 6
Bandwidth Requirement…........…..................…..................…..................…............. 6
3. Description of Network…..................…..................…..................…..................…….. 6
Assumptions…..................…...…..................…..................…..................…............. 6
Network Hardware…...............…..................…..................…..................…............. 7
Network Topology…..................…..................…..................…..................….......... 7
Network Circuit…..................…..................…..................…..................…............... 8
Logical Network Design…..................…..................…..................…..................…. 8
4. Conclusions….................................…..................…..................…..................
….........
9
5. References…..............…..................…..................…..................…..................
…...........
10
Table of Contents
1. Introduction……….............................…..................…..................…..................…… 4
2. Analysis of User Requirements…......….......…..................…..................…............... 5
Business Objective…................…..................…..................…..................…........... 5
Challenge of Network Security…..................…..................…..................….............. 5
Scalability…..................….........…..................…..................…..................…............ 5
Remote Access…..................….…..................…..................…..................…............ 6
Bandwidth Requirement…........…..................…..................…..................…............. 6
3. Description of Network…..................…..................…..................…..................…….. 6
Assumptions…..................…...…..................…..................…..................…............. 6
Network Hardware…...............…..................…..................…..................…............. 7
Network Topology…..................…..................…..................…..................….......... 7
Network Circuit…..................…..................…..................…..................…............... 8
Logical Network Design…..................…..................…..................…..................…. 8
4. Conclusions….................................…..................…..................…..................
….........
9
5. References…..............…..................…..................…..................…..................
…...........
10

Data Communication 4
Introduction
A private biomedical 5 star organization, is comprised of 3 story building that are adjacent to
each other. The length of both buildings is about 50 meters whereas width is approximately 15
meters. The distance between both buildings is approximately 40 meters. Their main objective is
to change the existing network into modified system for making it beneficial as the company
grows in terms of number of employees. The existing network is old and that is required to
upgrade. They have an idea for setting two IT rooms having 20 systems. The programmers will
sit in one room whereas Web Designers will sit in other room. The 5 star organization wants to
set virtual machines that needs to be operated online. The organization wants to implement
WAN at the branch offices which are just recently opened. 100 systems will be set up in their
branch offices that can be used for video conferencing with other offices. The new branch office
is 200 km the head office. Hence, all the offices need to be on WLAN for the future
communication.
WLAN is similar to LAN. The only difference between them is the radio signals which are used
as transport medium in spite of wires. The main purpose of WLAN it is connected with the
mobility of the users by implementing it in simple way and easy configuration. The main
challenge in implementing WLAN is its security that also includes its legacy as well as
complexity in its implementation. The enhanced adaptability of Wireless LANs results in the
profitable work groups, better contribution from staff and also satisfies the employees as
implementing WLAN makes staff more flexible and it increases the mobility of staff. (Dr. Singh,
G., 2012).
Introduction
A private biomedical 5 star organization, is comprised of 3 story building that are adjacent to
each other. The length of both buildings is about 50 meters whereas width is approximately 15
meters. The distance between both buildings is approximately 40 meters. Their main objective is
to change the existing network into modified system for making it beneficial as the company
grows in terms of number of employees. The existing network is old and that is required to
upgrade. They have an idea for setting two IT rooms having 20 systems. The programmers will
sit in one room whereas Web Designers will sit in other room. The 5 star organization wants to
set virtual machines that needs to be operated online. The organization wants to implement
WAN at the branch offices which are just recently opened. 100 systems will be set up in their
branch offices that can be used for video conferencing with other offices. The new branch office
is 200 km the head office. Hence, all the offices need to be on WLAN for the future
communication.
WLAN is similar to LAN. The only difference between them is the radio signals which are used
as transport medium in spite of wires. The main purpose of WLAN it is connected with the
mobility of the users by implementing it in simple way and easy configuration. The main
challenge in implementing WLAN is its security that also includes its legacy as well as
complexity in its implementation. The enhanced adaptability of Wireless LANs results in the
profitable work groups, better contribution from staff and also satisfies the employees as
implementing WLAN makes staff more flexible and it increases the mobility of staff. (Dr. Singh,
G., 2012).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Data Communication 5
Analysis of User Requirements
Business Objective
The main objective of the organization is to make network better so that the branch offices can
communicate with the head office of biomedical organization without any interruption. The
organization wants to operate virtual machines online so that employees can have mobility to
work from anywhere. The organization also wants to implement video conferencing so that
branch office can communicate with their head office on very less expenses. The organization
wants to be at the top in their networking. Also, the implemented WLAN should be enough for
future if number of employees’ increases.
Challenge of Network Security
The remote networking system provides access beyond the physical limits of the staff or the
building. Anyone can use the enterprise wireless network. So it is necessary to implement the
effective security to wireless network as the staff can have the rogue access to the enterprise
network without having the knowledge to the management. Dissimilar to wired network systems,
the signal of a remote system can be broadcast to the imparting hubs. A hacker has the ability to
hack the wireless network by intercepting the radio signals. He can also remotely hack the
network from any remote location. So it is necessary to implement a security policy in the
organization to secure the wireless network.
Scalability
With the increase in the growth of WLAN, more systems can have access on the network. It
must be necessary for network administrator to provide some extra access points so that others
Analysis of User Requirements
Business Objective
The main objective of the organization is to make network better so that the branch offices can
communicate with the head office of biomedical organization without any interruption. The
organization wants to operate virtual machines online so that employees can have mobility to
work from anywhere. The organization also wants to implement video conferencing so that
branch office can communicate with their head office on very less expenses. The organization
wants to be at the top in their networking. Also, the implemented WLAN should be enough for
future if number of employees’ increases.
Challenge of Network Security
The remote networking system provides access beyond the physical limits of the staff or the
building. Anyone can use the enterprise wireless network. So it is necessary to implement the
effective security to wireless network as the staff can have the rogue access to the enterprise
network without having the knowledge to the management. Dissimilar to wired network systems,
the signal of a remote system can be broadcast to the imparting hubs. A hacker has the ability to
hack the wireless network by intercepting the radio signals. He can also remotely hack the
network from any remote location. So it is necessary to implement a security policy in the
organization to secure the wireless network.
Scalability
With the increase in the growth of WLAN, more systems can have access on the network. It
must be necessary for network administrator to provide some extra access points so that others

Data Communication 6
users can also have access to the network. So it is necessary for the network administrator to
implement security policy centrally from the server. (Avaya Inc., 2011).
Remote Access
Wireless network (WLAN) should be implemented in such a way that remote users who are
outside the office can have the access to the network in a secure methodology. The best solution
for providing remote access to the outside users is setting VPN which enables users to securely
transmit data over VPN server by having centralized network access. VPN also provides
flexibility to its users as it helps users to carry IP protocols as per IPSec standards. It also helps
to rationalize all its resources in order to avoid any type of waste. It encrypt the data which is
transferred through the network. (Bourdoucen, H., Naamany, A., A., 2009).
Bandwidth Requirement
The transmission capacity of various access points can be set to 10Mbps or more in order to give
enough transmission capacity for the network traffic, whereas the information or packet size to
be sent was set at 1400 bytes. The remote system standard utilized was 802.11n and this was set
as the uniform for all the points. (Ochang, P, A. & Irving, P., 2016).
Description of Network
Assumptions
The various assumptions which needs to assume before implementing WLAN are as following:
The number of network users will expand in future. There must be centralized security system
which must be centralized managed by network administrator. The network must be enough
users can also have access to the network. So it is necessary for the network administrator to
implement security policy centrally from the server. (Avaya Inc., 2011).
Remote Access
Wireless network (WLAN) should be implemented in such a way that remote users who are
outside the office can have the access to the network in a secure methodology. The best solution
for providing remote access to the outside users is setting VPN which enables users to securely
transmit data over VPN server by having centralized network access. VPN also provides
flexibility to its users as it helps users to carry IP protocols as per IPSec standards. It also helps
to rationalize all its resources in order to avoid any type of waste. It encrypt the data which is
transferred through the network. (Bourdoucen, H., Naamany, A., A., 2009).
Bandwidth Requirement
The transmission capacity of various access points can be set to 10Mbps or more in order to give
enough transmission capacity for the network traffic, whereas the information or packet size to
be sent was set at 1400 bytes. The remote system standard utilized was 802.11n and this was set
as the uniform for all the points. (Ochang, P, A. & Irving, P., 2016).
Description of Network
Assumptions
The various assumptions which needs to assume before implementing WLAN are as following:
The number of network users will expand in future. There must be centralized security system
which must be centralized managed by network administrator. The network must be enough

Data Communication 7
efficient in order to deliver appropriate throughput to its users. The quality of audio and video
conferencing must be good. (Finneran, M., 2004).
Network Hardware
The various hardware which are required for successfully implementation of WLAN includes –
switch, router, cisco firewall, laptops, phones, printers etc. Firewalls have been developed with
additional security features like application assessment capacities, which gives the capacity to
inspect, recognize, and check application as well as to treat traffic as indicated by various
policies that depends on various variables. This helps to block unwanted network traffic who
want the unethical access to the entire network of the organization. The firewall secures the
access at various key system points, guaranteeing, for instance, that sales representative can't
access the financial system or payroll of the ERP. (https://www.cisco.com, 2017).
Network Topology
Mesh topology is the best solution for implementing WLAN in order to provide remote access.
Implementing mesh topology is cost effective as well as it provides secure solution for remote
access. It enhances the unique solution for mesh topology and also. Also, it adequately underpins
current systems administration necessities, and establishes the framework for the combination of
business applications. A remote mesh network can be defined as the communication network
which is built by radio hubs which possess two pathways of communication to every hub. It
constructs routes between hubs as required by originating nodes. If a hub wants a route to a goal
for which it doesn't have route, it communicates a route request packet over the network. Nodes
mainly monitor the route request through source IP address and broadcast ID. It is the
efficient in order to deliver appropriate throughput to its users. The quality of audio and video
conferencing must be good. (Finneran, M., 2004).
Network Hardware
The various hardware which are required for successfully implementation of WLAN includes –
switch, router, cisco firewall, laptops, phones, printers etc. Firewalls have been developed with
additional security features like application assessment capacities, which gives the capacity to
inspect, recognize, and check application as well as to treat traffic as indicated by various
policies that depends on various variables. This helps to block unwanted network traffic who
want the unethical access to the entire network of the organization. The firewall secures the
access at various key system points, guaranteeing, for instance, that sales representative can't
access the financial system or payroll of the ERP. (https://www.cisco.com, 2017).
Network Topology
Mesh topology is the best solution for implementing WLAN in order to provide remote access.
Implementing mesh topology is cost effective as well as it provides secure solution for remote
access. It enhances the unique solution for mesh topology and also. Also, it adequately underpins
current systems administration necessities, and establishes the framework for the combination of
business applications. A remote mesh network can be defined as the communication network
which is built by radio hubs which possess two pathways of communication to every hub. It
constructs routes between hubs as required by originating nodes. If a hub wants a route to a goal
for which it doesn't have route, it communicates a route request packet over the network. Nodes
mainly monitor the route request through source IP address and broadcast ID. It is the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Data Communication 8
progression towards giving high data transmission solution over a particular scope range. It is
stable network topology. (https://www.solwise.co.uk, 2017).
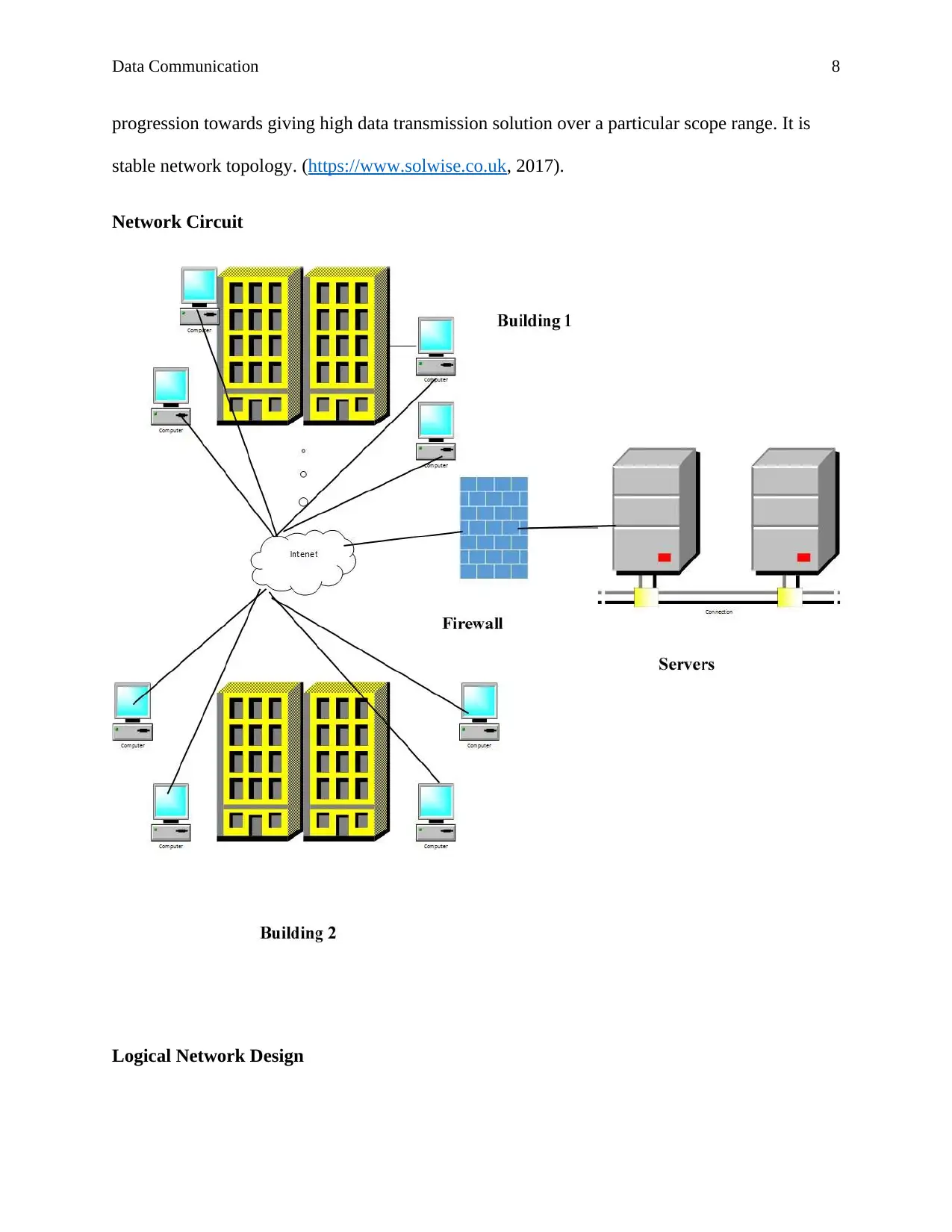
Network Circuit
Logical Network Design
progression towards giving high data transmission solution over a particular scope range. It is
stable network topology. (https://www.solwise.co.uk, 2017).
Network Circuit
Logical Network Design
Data Communication 9
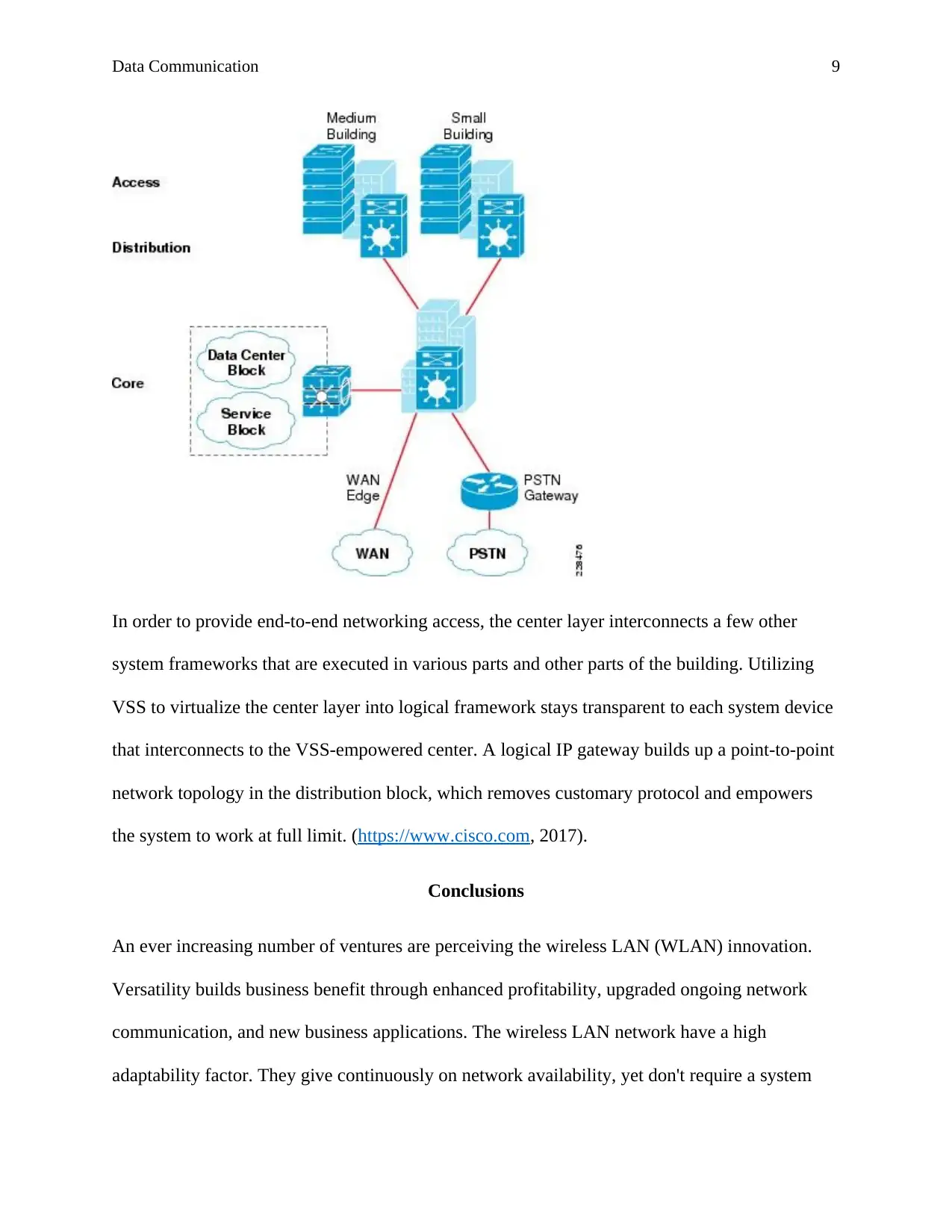
In order to provide end-to-end networking access, the center layer interconnects a few other
system frameworks that are executed in various parts and other parts of the building. Utilizing
VSS to virtualize the center layer into logical framework stays transparent to each system device
that interconnects to the VSS-empowered center. A logical IP gateway builds up a point-to-point
network topology in the distribution block, which removes customary protocol and empowers
the system to work at full limit. (https://www.cisco.com, 2017).
Conclusions
An ever increasing number of ventures are perceiving the wireless LAN (WLAN) innovation.
Versatility builds business benefit through enhanced profitability, upgraded ongoing network
communication, and new business applications. The wireless LAN network have a high
adaptability factor. They give continuously on network availability, yet don't require a system
In order to provide end-to-end networking access, the center layer interconnects a few other
system frameworks that are executed in various parts and other parts of the building. Utilizing
VSS to virtualize the center layer into logical framework stays transparent to each system device
that interconnects to the VSS-empowered center. A logical IP gateway builds up a point-to-point
network topology in the distribution block, which removes customary protocol and empowers
the system to work at full limit. (https://www.cisco.com, 2017).
Conclusions
An ever increasing number of ventures are perceiving the wireless LAN (WLAN) innovation.
Versatility builds business benefit through enhanced profitability, upgraded ongoing network
communication, and new business applications. The wireless LAN network have a high
adaptability factor. They give continuously on network availability, yet don't require a system

Data Communication 10
link. When a better network topology is adopted, it helps to enhance profit of the organization
and also helps to fulfill the customer's goals for flexibility, and execution. One of the destinations
as a system originator should be to enable the customer to develop a couple of philosophies and
techniques for realizing framework organization.
References
Bourdoucen, H., Naamany, A., A. (2009). Impact of Implementing VPN to Secure Wireless
LAN. World Academy of Science, Engineering and Technology 27 2009. Retrieved
from- http://citeseerx.ist.psu.edu/viewdoc/download?
doi=10.1.1.309.2682&rep=rep1&type=pdf
Community College and Vocational Education (CCVE) Design Overview. Retrieved from -
https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Education/CCVE/
CCVE_DG/CCVE_Ch3.html
Deploying secure wireless network services. Avaya Inc. (2011). Retrieved from -
https://www.avaya.com/en/documents/dn5244.pdf?t=0
Dr. Singh, G. (2012). Security Issues in Wireless Local Area Networks (WLAN). Global Journal
of Science Frontier Research Mathematics and Decision Sciences Volume 12 Issue 11
Version 1.0 year 2012. Retrieved from - https://globaljournals.org/GJSFR_Volume12/8-
Security-Issues-in-Wireless-Local-Area.pdf
Finneran, M. (2004). Five critical planning steps for wireless LANs, Step 5: Manageability --
Switching to WLAN switches. Retrieved from -
http://searchnetworking.techtarget.com/tutorial/Five-critical-planning-steps-for-wireless-
LANs-Step-5-Manageability-Switching-to-WLAN-switches
link. When a better network topology is adopted, it helps to enhance profit of the organization
and also helps to fulfill the customer's goals for flexibility, and execution. One of the destinations
as a system originator should be to enable the customer to develop a couple of philosophies and
techniques for realizing framework organization.
References
Bourdoucen, H., Naamany, A., A. (2009). Impact of Implementing VPN to Secure Wireless
LAN. World Academy of Science, Engineering and Technology 27 2009. Retrieved
from- http://citeseerx.ist.psu.edu/viewdoc/download?
doi=10.1.1.309.2682&rep=rep1&type=pdf
Community College and Vocational Education (CCVE) Design Overview. Retrieved from -
https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Education/CCVE/
CCVE_DG/CCVE_Ch3.html
Deploying secure wireless network services. Avaya Inc. (2011). Retrieved from -
https://www.avaya.com/en/documents/dn5244.pdf?t=0
Dr. Singh, G. (2012). Security Issues in Wireless Local Area Networks (WLAN). Global Journal
of Science Frontier Research Mathematics and Decision Sciences Volume 12 Issue 11
Version 1.0 year 2012. Retrieved from - https://globaljournals.org/GJSFR_Volume12/8-
Security-Issues-in-Wireless-Local-Area.pdf
Finneran, M. (2004). Five critical planning steps for wireless LANs, Step 5: Manageability --
Switching to WLAN switches. Retrieved from -
http://searchnetworking.techtarget.com/tutorial/Five-critical-planning-steps-for-wireless-
LANs-Step-5-Manageability-Switching-to-WLAN-switches
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Data Communication 11
Iyer, A. & Badgujar, A. (2013). Voice and Video over Wireless LAN. International Journal of
Scientific and Research Publications, Volume 3, Issue 9, September 2013. Retrieved
from - http://www.ijsrp.org/research-paper-0913/ijsrp-p21106.pdf
Ochang, P, A. & Irving, P. (2016). Performance Analysis of Wireless Network Throughput and
Security Protocol Integration. International Journal of Future Generation Communication
and Networking Vol. 9, No. 1 (2016), pp. 71-78. Retrieved from -
http://www.sersc.org/journals/IJFGCN/vol9_no1/7.pdf
Outdoor wireless including linking buildings and wide area coverage. Retrieved from -
https://www.solwise.co.uk/downloads/files/linking-buildings-using-wireless.pdf
Ro, E. (2002). Wireless Local Area Network Proposal. CAO - ITS. Retrieved from -
http://www.csun.edu/~esr46044/Documents/WLAN_Sacto.pdf
Wireless and Network Security Integration Solution Design Guide. Retrieved from -
https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Mobility/secwlandg20/
sw2dg/ch6_2_SPMb.html
Iyer, A. & Badgujar, A. (2013). Voice and Video over Wireless LAN. International Journal of
Scientific and Research Publications, Volume 3, Issue 9, September 2013. Retrieved
from - http://www.ijsrp.org/research-paper-0913/ijsrp-p21106.pdf
Ochang, P, A. & Irving, P. (2016). Performance Analysis of Wireless Network Throughput and
Security Protocol Integration. International Journal of Future Generation Communication
and Networking Vol. 9, No. 1 (2016), pp. 71-78. Retrieved from -
http://www.sersc.org/journals/IJFGCN/vol9_no1/7.pdf
Outdoor wireless including linking buildings and wide area coverage. Retrieved from -
https://www.solwise.co.uk/downloads/files/linking-buildings-using-wireless.pdf
Ro, E. (2002). Wireless Local Area Network Proposal. CAO - ITS. Retrieved from -
http://www.csun.edu/~esr46044/Documents/WLAN_Sacto.pdf
Wireless and Network Security Integration Solution Design Guide. Retrieved from -
https://www.cisco.com/c/en/us/td/docs/solutions/Enterprise/Mobility/secwlandg20/
sw2dg/ch6_2_SPMb.html

Data Communication 12
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





