CP4CS58E: Network Infrastructure and Data Communication for ACME Corp
VerifiedAdded on 2023/06/18
|10
|3157
|346
Report
AI Summary
This report provides a comprehensive network infrastructure solution for ACME Corporation, which has recently acquired offices in the UK, India, and the US. The solution details the operating principles of frequency-used networking devices, their characteristics, and performance, and defines networking standards and communication within the OSI Model. It proposes a network infrastructure solution utilizing routers, switches, and cloud-based servers, emphasizing security recommendations to address ACME Corporation's particular security concerns. The topology diagram, created using Cisco Packet Tracer, visualizes the network infrastructure and connections between the offices and departments. The report evaluates and explains the choices for hardware and software components, including firewalls and antivirus software, to ensure secure and efficient data communication within the organization.

DATA COMMUNICATION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
MAIN BODY..................................................................................................................................1
Operating principles of frequency used networking devices, their characteristics and
performance. Define networking standards and communication with OSI Mode......................1
Network infrastructure solution...................................................................................................2
Topology diagram........................................................................................................................3
Evaluation and explanation of choices for hardware and software such as cloud- based servers
.....................................................................................................................................................4
Discussion of security recommendations as ACME corporation is extremely particular about
security implications....................................................................................................................6
CONCLUSION................................................................................................................................7
REFERENCES................................................................................................................................8
INTRODUCTION...........................................................................................................................1
MAIN BODY..................................................................................................................................1
Operating principles of frequency used networking devices, their characteristics and
performance. Define networking standards and communication with OSI Mode......................1
Network infrastructure solution...................................................................................................2
Topology diagram........................................................................................................................3
Evaluation and explanation of choices for hardware and software such as cloud- based servers
.....................................................................................................................................................4
Discussion of security recommendations as ACME corporation is extremely particular about
security implications....................................................................................................................6
CONCLUSION................................................................................................................................7
REFERENCES................................................................................................................................8

INTRODUCTION
Data communication can be defined as exchange of data between two devices though a
mode of transmission media such as wire, cable etc. In networking data communication is a way
of transmitting digital data or signals from one device to another (Martins and et. al., 2018).
Different networking devices uses different mode of transmitting signals. Today it has become
one of the most important part of every organization there are different kinds of network for
establishing communication and can be done for establishment of communication within
organization and externally outside organization as well. There are three main types of networks
and asper the need and requirement choice of network is made like for internal communication
LAN network is used (Sousa and et. al., 2016). This report will focus upon case study of ACME
Corporation who have recently acquired offices in UK, India, and the US. They need to connect
different offices together. This report will further focus upon explaining Operating principles of
frequency used networking devices, their characteristics and performance, definition of
networking standards and communication with OSI Mode, Network infrastructure solution,
Topology diagram, evaluation and explanation of choices for hardware and software such as
cloud- based servers and discussion of security recommendations as ACME corporation is
extremely particular about security implications.
MAIN BODY
Operating principles of frequency used networking devices, their characteristics and
performance. Define networking standards and communication with OSI Mode
There are many different kinds of networking devices and each of them have their own
operating principles of frequency used by then, their own characteristics and performance. Some
of the most commonly used network devices are: hub, router, switch, bridge, gateway, modem,
repeater, access point. Networking standards are defined rules for data communication that are
required interoperability of networking technology and processes (Govindan and et. al., 2016).
There are two main types of networking standards that are used for communication: first is
formal and second is de facto. One of the most common type of networking standard is OSI
model (Open System Interconnection). OSI is a seven layered model that was developed in late
1970’s that defines communications protocol and computer network protocol design.
Hub: It helps in connecting multiple networking devices together. It operates Physical layer of
the OSI model.
1
Data communication can be defined as exchange of data between two devices though a
mode of transmission media such as wire, cable etc. In networking data communication is a way
of transmitting digital data or signals from one device to another (Martins and et. al., 2018).
Different networking devices uses different mode of transmitting signals. Today it has become
one of the most important part of every organization there are different kinds of network for
establishing communication and can be done for establishment of communication within
organization and externally outside organization as well. There are three main types of networks
and asper the need and requirement choice of network is made like for internal communication
LAN network is used (Sousa and et. al., 2016). This report will focus upon case study of ACME
Corporation who have recently acquired offices in UK, India, and the US. They need to connect
different offices together. This report will further focus upon explaining Operating principles of
frequency used networking devices, their characteristics and performance, definition of
networking standards and communication with OSI Mode, Network infrastructure solution,
Topology diagram, evaluation and explanation of choices for hardware and software such as
cloud- based servers and discussion of security recommendations as ACME corporation is
extremely particular about security implications.
MAIN BODY
Operating principles of frequency used networking devices, their characteristics and
performance. Define networking standards and communication with OSI Mode
There are many different kinds of networking devices and each of them have their own
operating principles of frequency used by then, their own characteristics and performance. Some
of the most commonly used network devices are: hub, router, switch, bridge, gateway, modem,
repeater, access point. Networking standards are defined rules for data communication that are
required interoperability of networking technology and processes (Govindan and et. al., 2016).
There are two main types of networking standards that are used for communication: first is
formal and second is de facto. One of the most common type of networking standard is OSI
model (Open System Interconnection). OSI is a seven layered model that was developed in late
1970’s that defines communications protocol and computer network protocol design.
Hub: It helps in connecting multiple networking devices together. It operates Physical layer of
the OSI model.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Router: It transmit packets to their destination by charting their path through sea of inter
connected networking devices that uses different kinds of networking topologies. They mostly
work at Network layer of the OSI model.
Switch: Main role of switches is to bring improvement within network efficiency. It also focuses
upon reading hardware address of all the incoming packets that are transmitted to them to
appropriate destination (Nikolov and Slavyanov, 2018). They work at either Data Link layer or
the Network layer of the OSI model.
Bridge: Its main use is to connect two or more than two host or network segment together. Its
main use is basically to store and forward frames between different segments that connects
bridge. It works only at Physical and Data Link layers of the OSI model.
Gateway: It is basically works as a translator between networking technologies such as OSI
model and TCP/IP model. But its main work lies between two main layers of OSI model that are
Transport and Session layers of the OSI model. It can perform functions of two or more than two
networking devices such as routes and others.
Modem: its main characteristic is to transmit digital signals over analog telephone lines. For this
first of all digital signals are converted into analog signals. In this transferring of digital data to
and from model is done and is usually connected to computer. Its work is on both the layers of
OSI model that are Physical and Data Link layers (Vijayalakshmi, Desai and Raikar, 2016).
Repeater: its main characteristics is to amplify signals received by them. It is done by repeater by
receiving signals and retransmitting it at higher level or higher power so that signals are strong
enough that they can cover longer distance. They are present at physical layer of OSI model.
Access point: It works at data link layer of OSI model. It is basically used to bridge connection
between standard wired network to wireless devices.
Network infrastructure solution
Network infrastructure can be defined as collection of hardware and software solutions of
an entire network that can help in enabling network connectivity, network operations,
communication, management of entire network. Network infrastructure helps in setting a path
between service users of entire network (Rashid and et. al., 2019). In order to maintain internal
and external communication between two or more than two networks it is extremely important to
develop an effective network that can help in developing a secure network with the help of which
data within organization can be transferred easily.
2
connected networking devices that uses different kinds of networking topologies. They mostly
work at Network layer of the OSI model.
Switch: Main role of switches is to bring improvement within network efficiency. It also focuses
upon reading hardware address of all the incoming packets that are transmitted to them to
appropriate destination (Nikolov and Slavyanov, 2018). They work at either Data Link layer or
the Network layer of the OSI model.
Bridge: Its main use is to connect two or more than two host or network segment together. Its
main use is basically to store and forward frames between different segments that connects
bridge. It works only at Physical and Data Link layers of the OSI model.
Gateway: It is basically works as a translator between networking technologies such as OSI
model and TCP/IP model. But its main work lies between two main layers of OSI model that are
Transport and Session layers of the OSI model. It can perform functions of two or more than two
networking devices such as routes and others.
Modem: its main characteristic is to transmit digital signals over analog telephone lines. For this
first of all digital signals are converted into analog signals. In this transferring of digital data to
and from model is done and is usually connected to computer. Its work is on both the layers of
OSI model that are Physical and Data Link layers (Vijayalakshmi, Desai and Raikar, 2016).
Repeater: its main characteristics is to amplify signals received by them. It is done by repeater by
receiving signals and retransmitting it at higher level or higher power so that signals are strong
enough that they can cover longer distance. They are present at physical layer of OSI model.
Access point: It works at data link layer of OSI model. It is basically used to bridge connection
between standard wired network to wireless devices.
Network infrastructure solution
Network infrastructure can be defined as collection of hardware and software solutions of
an entire network that can help in enabling network connectivity, network operations,
communication, management of entire network. Network infrastructure helps in setting a path
between service users of entire network (Rashid and et. al., 2019). In order to maintain internal
and external communication between two or more than two networks it is extremely important to
develop an effective network that can help in developing a secure network with the help of which
data within organization can be transferred easily.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

As per the case study of ACME Corporation recently acquired offices in the UK, India,
and the US and each of these offices have three departments i.e., IT, HR and Finance with
different broadcast domains for communicating with each other. So, for connecting all the three
offices together three routers will be used. Each router will be used to connect each office with
other two. Each of these routers will be connected to a common cloud server (database server,
email server etc.) and these services will be connected to internet so that any kind of data or
information can be transferred within organization and outside organization as well in an
accurate manner. Each of these routers will be connected to firewall in order to ensure that data
communication is done in an accurate manner. As each department has three departments do all
the routes will be connected to switches. These switches will be used to switch from one IP
domain to another (connecting all the three departments of offices together) with the help of
Inter-VLAN routing.
So, in this network infrastructure of whole network will be connected to online services
and this servicer will be connected to internet with the help of Wide area network. Then this
servicer will be connected to three routers of each office for maintaining connection between all
the three offices. With the help of wide area network all the three offices though router will be
connected together. Using subnetting techniques all the departments of all the offices will be
divided into subnets and will be connected to switches and routers so that data or information can
be transferred easily and internal or external communication can be established easily. All the
offices will have their own local area network and connection within offices will be established
on the basis of LAN network only.
Topology diagram
Network topology can be defined as a ways of linking nodes of network that are arranged
in such a manner that it connects all the devices within network with each other. Topology
diagram helps in providing a visual representation of a network, devices connected to it,
connection, pathways server connected etc. It allows in visualizing how a network of an
organization is and ways in which devices are connected with each other (Bhardwaj and et. al.,
2016). There are various kinds of tools that can be used for development of topology diagram.
For this topology diagram Cisco packet tracer tool will be used. Packet tracer tool is a cross-
platform visual simulation tool. That was deigned and developed by cisco system that can be
used by users for creation of network topology and for developing or imitating virtual modern
3
and the US and each of these offices have three departments i.e., IT, HR and Finance with
different broadcast domains for communicating with each other. So, for connecting all the three
offices together three routers will be used. Each router will be used to connect each office with
other two. Each of these routers will be connected to a common cloud server (database server,
email server etc.) and these services will be connected to internet so that any kind of data or
information can be transferred within organization and outside organization as well in an
accurate manner. Each of these routers will be connected to firewall in order to ensure that data
communication is done in an accurate manner. As each department has three departments do all
the routes will be connected to switches. These switches will be used to switch from one IP
domain to another (connecting all the three departments of offices together) with the help of
Inter-VLAN routing.
So, in this network infrastructure of whole network will be connected to online services
and this servicer will be connected to internet with the help of Wide area network. Then this
servicer will be connected to three routers of each office for maintaining connection between all
the three offices. With the help of wide area network all the three offices though router will be
connected together. Using subnetting techniques all the departments of all the offices will be
divided into subnets and will be connected to switches and routers so that data or information can
be transferred easily and internal or external communication can be established easily. All the
offices will have their own local area network and connection within offices will be established
on the basis of LAN network only.
Topology diagram
Network topology can be defined as a ways of linking nodes of network that are arranged
in such a manner that it connects all the devices within network with each other. Topology
diagram helps in providing a visual representation of a network, devices connected to it,
connection, pathways server connected etc. It allows in visualizing how a network of an
organization is and ways in which devices are connected with each other (Bhardwaj and et. al.,
2016). There are various kinds of tools that can be used for development of topology diagram.
For this topology diagram Cisco packet tracer tool will be used. Packet tracer tool is a cross-
platform visual simulation tool. That was deigned and developed by cisco system that can be
used by users for creation of network topology and for developing or imitating virtual modern
3
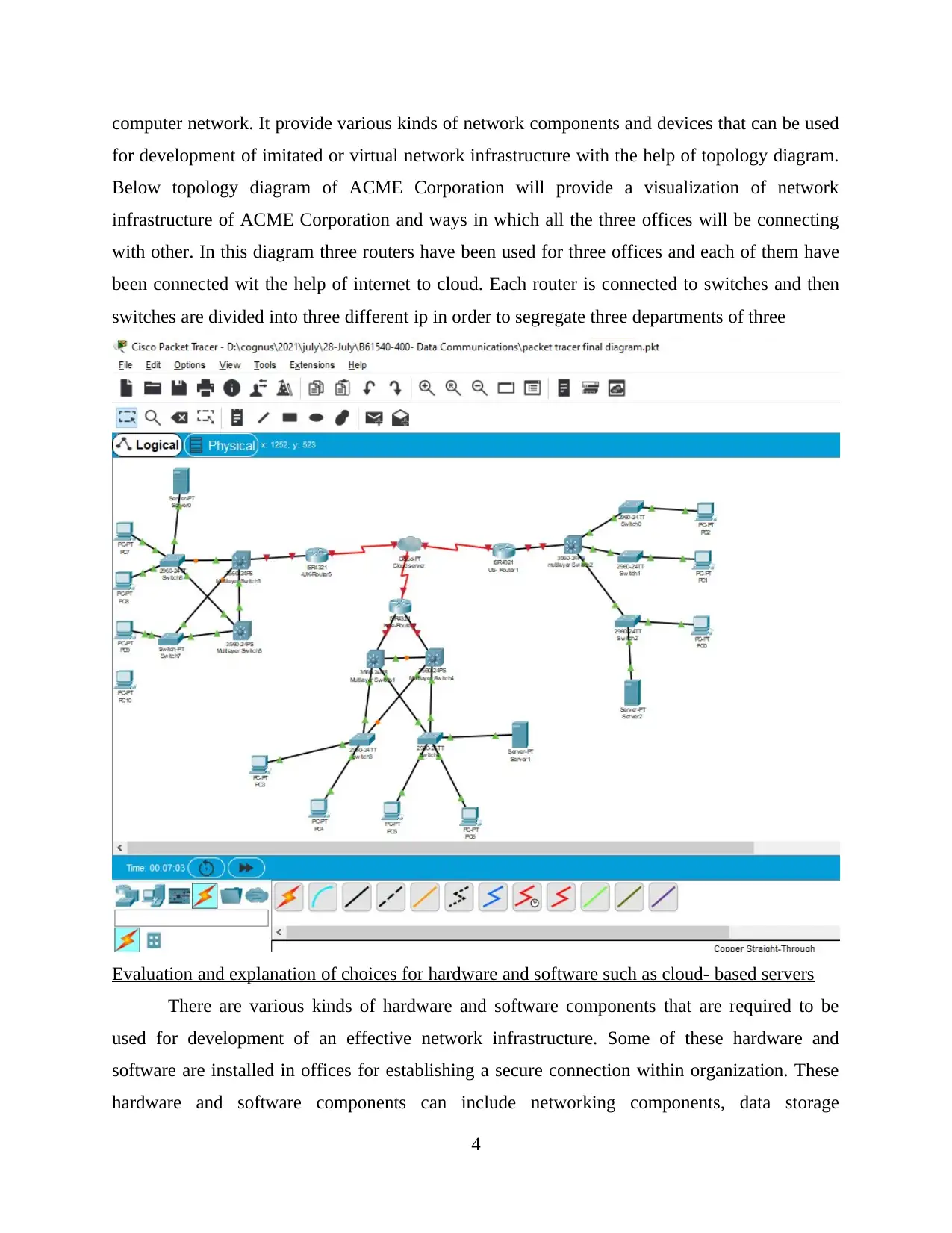
computer network. It provide various kinds of network components and devices that can be used
for development of imitated or virtual network infrastructure with the help of topology diagram.
Below topology diagram of ACME Corporation will provide a visualization of network
infrastructure of ACME Corporation and ways in which all the three offices will be connecting
with other. In this diagram three routers have been used for three offices and each of them have
been connected wit the help of internet to cloud. Each router is connected to switches and then
switches are divided into three different ip in order to segregate three departments of three
Evaluation and explanation of choices for hardware and software such as cloud- based servers
There are various kinds of hardware and software components that are required to be
used for development of an effective network infrastructure. Some of these hardware and
software are installed in offices for establishing a secure connection within organization. These
hardware and software components can include networking components, data storage
4
for development of imitated or virtual network infrastructure with the help of topology diagram.
Below topology diagram of ACME Corporation will provide a visualization of network
infrastructure of ACME Corporation and ways in which all the three offices will be connecting
with other. In this diagram three routers have been used for three offices and each of them have
been connected wit the help of internet to cloud. Each router is connected to switches and then
switches are divided into three different ip in order to segregate three departments of three
Evaluation and explanation of choices for hardware and software such as cloud- based servers
There are various kinds of hardware and software components that are required to be
used for development of an effective network infrastructure. Some of these hardware and
software are installed in offices for establishing a secure connection within organization. These
hardware and software components can include networking components, data storage
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

components, servers, firewall, cloud servicers like SaaS (Lavrova, Poltavtseva and Shtyrkina,
2018).
Some of the most common hardware used in this development of ACME Corporation
network infrastructure are: servers, data centres, data storage, routers, switches, cables, personal
computers and other devices or components. Router is one of the most important devices within
a network infrastructure that helps in connecting devices together as it can route network packets
on the basis of their address to other network or devices (Lavrova, Poltavtseva and Shtyrkina,
2018). In this case routers are used for coupling or connecting three different networks of three
offices together to internet. Three routers are used to connected three offices of ACME
Corporation together. These routers have been basically used to connecting all three branch
offices centrally to one cloud server in order to make data sharing and receiving easy within
organization. Other than this, switches were used within topology diagram within network
infrastructure of ACME Corporation. It was another important hardware used for construction of
network as it helps in connecting multiple devices together. It is used to connect computers,
laptops, servers, printers, wireless devices like mobile etc. together with the network security. It
directly helps connected devices to communicate with each other and share data or information
within each other security. These two were most important hardware that were used in this
network infrastructure to connect devices together. Other than this, servers were also used. Each
office had its own server and were connected to switches.
Some of the most common software used in this development of ACME Corporation
network infrastructure are: web servers, operating system, firewall, other security software’s etc.
Other than this, cloud servers are all useful software that will be used in this network
infrastructure. Firewall is one of the most important things within a network infrastructure as it
helps in providing protection to network from unauthorised access to network. It further helps in
monitoring incoming and outgoing network traffic. Firewall further helps in permitting or
blocking packets on the basis of certain set of rules or conditions. It directly helps in protecting
network from harmful access or data that can damage network or devices connected to network.
ACME Corporation network infrastructure will also be protected with the help of a firewall.
ACME Corporation will also have their own cloud database server where they will be storing all
of their data, they will also be using email cloud server where internal and external emails will be
sent or received by employees and by others. Other than this all the official devices connected to
5
2018).
Some of the most common hardware used in this development of ACME Corporation
network infrastructure are: servers, data centres, data storage, routers, switches, cables, personal
computers and other devices or components. Router is one of the most important devices within
a network infrastructure that helps in connecting devices together as it can route network packets
on the basis of their address to other network or devices (Lavrova, Poltavtseva and Shtyrkina,
2018). In this case routers are used for coupling or connecting three different networks of three
offices together to internet. Three routers are used to connected three offices of ACME
Corporation together. These routers have been basically used to connecting all three branch
offices centrally to one cloud server in order to make data sharing and receiving easy within
organization. Other than this, switches were used within topology diagram within network
infrastructure of ACME Corporation. It was another important hardware used for construction of
network as it helps in connecting multiple devices together. It is used to connect computers,
laptops, servers, printers, wireless devices like mobile etc. together with the network security. It
directly helps connected devices to communicate with each other and share data or information
within each other security. These two were most important hardware that were used in this
network infrastructure to connect devices together. Other than this, servers were also used. Each
office had its own server and were connected to switches.
Some of the most common software used in this development of ACME Corporation
network infrastructure are: web servers, operating system, firewall, other security software’s etc.
Other than this, cloud servers are all useful software that will be used in this network
infrastructure. Firewall is one of the most important things within a network infrastructure as it
helps in providing protection to network from unauthorised access to network. It further helps in
monitoring incoming and outgoing network traffic. Firewall further helps in permitting or
blocking packets on the basis of certain set of rules or conditions. It directly helps in protecting
network from harmful access or data that can damage network or devices connected to network.
ACME Corporation network infrastructure will also be protected with the help of a firewall.
ACME Corporation will also have their own cloud database server where they will be storing all
of their data, they will also be using email cloud server where internal and external emails will be
sent or received by employees and by others. Other than this all the official devices connected to
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

network will also have antivirus so that even if a hacker successfully breaks into network and
tries to hack system or install malware to any device on network then in such case installation of
anti- virus on system and devices will not only help system from malware, virus but will also
help in protecting or securing data on that system or work which is being done on that system.
Discussion of security recommendations as ACME corporation is extremely particular about
security implications
In order to security develop network infrastructure it is extremely important for ACME
corporation to focus upon security of network, data uploaded or downloaded though network or
to protect devices or system connected to network in an appropriate manner. Some of the main
security recommendations that are important for ACME corporation to be focused and adhered
for protecting their network completely have been explained below in detailed manner. Some of
the main security implications or recommendations are as follows:
First of all, administrative privileges will be set for authorised person so that only that
authorised person will have authority to install or update software, add a new device to
network, restrict a person from logging in to network etc. this will directly help in restricting
an unauthorised person from logging in to the network so that network can be protected
(Lavrova, Poltavtseva and Shtyrkina, 2018).
Installation of firewall will be done. Firewall will work as a wall for network so that
unauthorised access to network, installation of malware or virus to any of the system
connected to network. If any unknown packet is set to network is trying to enter a network
that can increase risk to network, then firewall will directly block that packet and will protect
the network. It is one of the most appropriate and accurate security solutions that can help in
protecting network.
Continuous monitoring of network is another security implication which is required to be
focused upon because it will help administrator to monitor whether any kind of unauthorised
access to network is being done or not and if any kind of such unauthorised attempts are
being done then it can be blocked or restricted (Lavrova, Poltavtseva and Shtyrkina, 2018).
Implementation of intrusion detection and prevention system to network can also help an
organization to monitor their employees, guest or customers who have logged in to network
and this system further helps in ensuing that network accessed by customers or guest is
completely separate from organization’s internal network.
6
tries to hack system or install malware to any device on network then in such case installation of
anti- virus on system and devices will not only help system from malware, virus but will also
help in protecting or securing data on that system or work which is being done on that system.
Discussion of security recommendations as ACME corporation is extremely particular about
security implications
In order to security develop network infrastructure it is extremely important for ACME
corporation to focus upon security of network, data uploaded or downloaded though network or
to protect devices or system connected to network in an appropriate manner. Some of the main
security recommendations that are important for ACME corporation to be focused and adhered
for protecting their network completely have been explained below in detailed manner. Some of
the main security implications or recommendations are as follows:
First of all, administrative privileges will be set for authorised person so that only that
authorised person will have authority to install or update software, add a new device to
network, restrict a person from logging in to network etc. this will directly help in restricting
an unauthorised person from logging in to the network so that network can be protected
(Lavrova, Poltavtseva and Shtyrkina, 2018).
Installation of firewall will be done. Firewall will work as a wall for network so that
unauthorised access to network, installation of malware or virus to any of the system
connected to network. If any unknown packet is set to network is trying to enter a network
that can increase risk to network, then firewall will directly block that packet and will protect
the network. It is one of the most appropriate and accurate security solutions that can help in
protecting network.
Continuous monitoring of network is another security implication which is required to be
focused upon because it will help administrator to monitor whether any kind of unauthorised
access to network is being done or not and if any kind of such unauthorised attempts are
being done then it can be blocked or restricted (Lavrova, Poltavtseva and Shtyrkina, 2018).
Implementation of intrusion detection and prevention system to network can also help an
organization to monitor their employees, guest or customers who have logged in to network
and this system further helps in ensuing that network accessed by customers or guest is
completely separate from organization’s internal network.
6

Encryption of login id and password of employees for logging on network should be stored
in encrypted form so that it cannot be hacked or accessed by unauthorized users and
organization can remain sure that their network is being used or accessed by an authorised
person only.
CONCLUSION
From the above report it has been identified that data is one of the most important things
within an organization and in order to operate from more than one location it becomes extremely
important for organizations to develop their own network infrastructure. In order to develop an
appropriate secure network infrastructure, it is extremely important to identify network
components that will be used for developing a secure an appropriate network infrastructure that
can connect different offices of an organization present at different location both nationally or
internationally. It is also important to understand what type of network will be used to establish
connection (LAN, MAN and WAN), and components including hardware and software
components like server, routers, switches, firewall, cloud servers etc. It has also been identified
that different organizations have different network infrastructure as per their needs and
requirements. It has also been identified in order to use a network infrastructure it is extremely
important ensure that, that network is secure and data sending or receiving through that network
is also secure. For this all kinds of securities should be applied to network such as firewall,
hardening network devices, limiting access to network with the help of user id and password so
that only authorised users can also connect to network and send or receive data or information
from that network.
7
in encrypted form so that it cannot be hacked or accessed by unauthorized users and
organization can remain sure that their network is being used or accessed by an authorised
person only.
CONCLUSION
From the above report it has been identified that data is one of the most important things
within an organization and in order to operate from more than one location it becomes extremely
important for organizations to develop their own network infrastructure. In order to develop an
appropriate secure network infrastructure, it is extremely important to identify network
components that will be used for developing a secure an appropriate network infrastructure that
can connect different offices of an organization present at different location both nationally or
internationally. It is also important to understand what type of network will be used to establish
connection (LAN, MAN and WAN), and components including hardware and software
components like server, routers, switches, firewall, cloud servers etc. It has also been identified
that different organizations have different network infrastructure as per their needs and
requirements. It has also been identified in order to use a network infrastructure it is extremely
important ensure that, that network is secure and data sending or receiving through that network
is also secure. For this all kinds of securities should be applied to network such as firewall,
hardening network devices, limiting access to network with the help of user id and password so
that only authorised users can also connect to network and send or receive data or information
from that network.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCES
Books and Journals
Bhardwaj, A., and et. al., 2016. Design a resilient network infrastructure security policy
framework. Indian Journal of Science and Technology, 9(19), pp.1-8.
Govindan, R., and et. al., 2016, August. Evolve or die: High-availability design principles drawn
from googles network infrastructure. In Proceedings of the 2016 ACM SIGCOMM
Conference (pp. 58-72).
Lavrova, D., Poltavtseva, M. and Shtyrkina, A., 2018, May. Security analysis of cyber-physical
systems network infrastructure. In 2018 IEEE Industrial Cyber-Physical Systems
(ICPS) (pp. 818-823). IEEE.
Martins, V.F., and et. al., 2018. Implementing a data network infrastructure course using a
problem-based learning methodology. Journal of Information Systems Engineering &
Management, 3(2), p.10.
Nikolov, L. and Slavyanov, V., 2018. Network infrastructure for cybersecurity analysis.
In International scientific conference.
Rashid, N.A., and et. al., 2019. Cisco Packet Tracer Simulation as effective pedagogy in
computer networking course.
Sousa, B., and et. al., 2016. Toward a fully cloudified mobile network infrastructure. IEEE
Transactions on Network and Service Management, 13(3), pp.547-563.
Vijayalakshmi, M., Desai, P. and Raikar, M.M., 2016, December. Packet tracer simulation tool
as pedagogy to enhance learning of computer network concepts. In 2016 IEEE 4th
International Conference on MOOCs, Innovation and Technology in Education
(MITE) (pp. 71-76). IEEE.
8
Books and Journals
Bhardwaj, A., and et. al., 2016. Design a resilient network infrastructure security policy
framework. Indian Journal of Science and Technology, 9(19), pp.1-8.
Govindan, R., and et. al., 2016, August. Evolve or die: High-availability design principles drawn
from googles network infrastructure. In Proceedings of the 2016 ACM SIGCOMM
Conference (pp. 58-72).
Lavrova, D., Poltavtseva, M. and Shtyrkina, A., 2018, May. Security analysis of cyber-physical
systems network infrastructure. In 2018 IEEE Industrial Cyber-Physical Systems
(ICPS) (pp. 818-823). IEEE.
Martins, V.F., and et. al., 2018. Implementing a data network infrastructure course using a
problem-based learning methodology. Journal of Information Systems Engineering &
Management, 3(2), p.10.
Nikolov, L. and Slavyanov, V., 2018. Network infrastructure for cybersecurity analysis.
In International scientific conference.
Rashid, N.A., and et. al., 2019. Cisco Packet Tracer Simulation as effective pedagogy in
computer networking course.
Sousa, B., and et. al., 2016. Toward a fully cloudified mobile network infrastructure. IEEE
Transactions on Network and Service Management, 13(3), pp.547-563.
Vijayalakshmi, M., Desai, P. and Raikar, M.M., 2016, December. Packet tracer simulation tool
as pedagogy to enhance learning of computer network concepts. In 2016 IEEE 4th
International Conference on MOOCs, Innovation and Technology in Education
(MITE) (pp. 71-76). IEEE.
8
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





