Exploratory Analysis Report: Data Privacy and Access Concerns
VerifiedAdded on 2023/06/06
|23
|2561
|377
Report
AI Summary
This report presents an exploratory analysis of a survey conducted to assess consumer views on data privacy and access. The survey, administered via Survey Monkey, gathered responses from 62 participants regarding their trust in online brands, satisfaction with data security, and opinions on government responsibility in data protection. The demographic analysis revealed a skew towards younger age groups, indicating a higher engagement with online activities. The study explored factors such as trust in online platforms, satisfaction with data security, and attitudes towards data sharing with government entities. Findings indicated that consumers are concerned about data breaches and are more vigilant about financial data privacy. The analysis utilized factor analysis to identify key components like trust in online security, access to protected data, and awareness about data privacy. The conclusion highlighted consumer concerns regarding the privacy of personal and financial information, emphasizing the need for government regulation and immediate notification of data breaches. The report suggests the need for larger sample sizes for more robust factor reliability and component consistency. This report is an insightful study on the evolving landscape of data privacy concerns and consumer behavior online.

An Exploratory Analysis on Data Privacy and Access
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
Most people opine that data privacy is an important factor, but the interpretation of security is
entirely personal and is hard to define. The continued dominance of the Internet and mobile
applications assess the understanding of privacy. The incessant commercial and social
engagement of the society in the online environment amplifies the risk of data theft. Awareness
about online piracy of personal information during online activities is utmost essential,
particularly while purchasing goods and services.
The present survey was conducted using the Survey Monkey online survey facility. The scholar
intended to interview consumers about their views regarding data privacy and their personal
awareness about the crisis (Aggarwal, and Philip, 2008).
Data Collection
A questionnaire was prepared utilizing the interactive interface of Survey Monkey. Along with
the demographical information (age, and gender), opinions about the present issue was sought.
Questions were arranged in order of convenience of answering. The survey link was shared
through emails, Facebook, and Whatsapp, and was open for two consecutive days. Total 64
responses were obtained in two days, and the scholar closed the survey. One of the responses
was deleted for missing value, and another reply was unreliable due to choice the second option
for all the questions. The data exploration was conducted with 62 valid responses.
Most people opine that data privacy is an important factor, but the interpretation of security is
entirely personal and is hard to define. The continued dominance of the Internet and mobile
applications assess the understanding of privacy. The incessant commercial and social
engagement of the society in the online environment amplifies the risk of data theft. Awareness
about online piracy of personal information during online activities is utmost essential,
particularly while purchasing goods and services.
The present survey was conducted using the Survey Monkey online survey facility. The scholar
intended to interview consumers about their views regarding data privacy and their personal
awareness about the crisis (Aggarwal, and Philip, 2008).
Data Collection
A questionnaire was prepared utilizing the interactive interface of Survey Monkey. Along with
the demographical information (age, and gender), opinions about the present issue was sought.
Questions were arranged in order of convenience of answering. The survey link was shared
through emails, Facebook, and Whatsapp, and was open for two consecutive days. Total 64
responses were obtained in two days, and the scholar closed the survey. One of the responses
was deleted for missing value, and another reply was unreliable due to choice the second option
for all the questions. The data exploration was conducted with 62 valid responses.
Participants’ Demographic
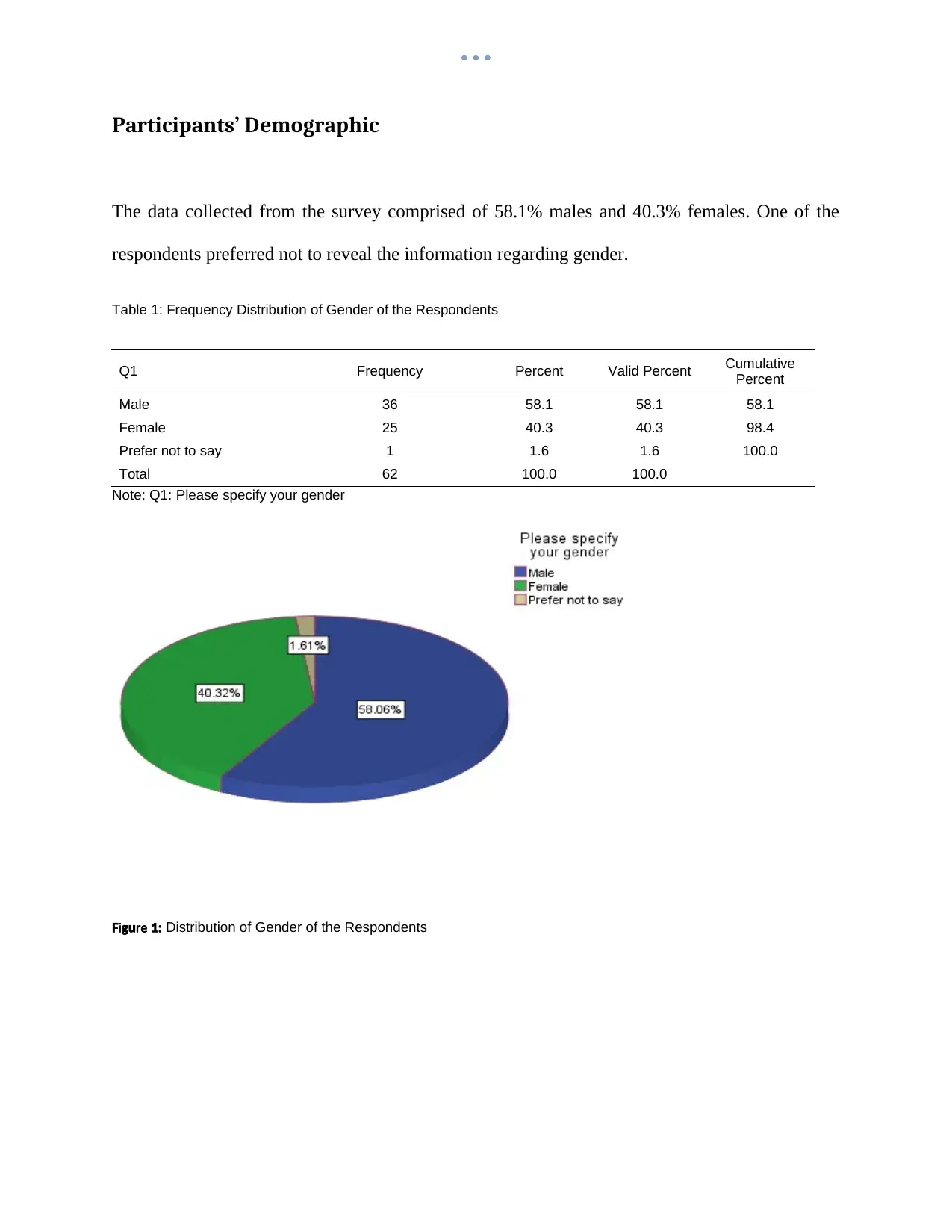
The data collected from the survey comprised of 58.1% males and 40.3% females. One of the
respondents preferred not to reveal the information regarding gender.
Table 1: Frequency Distribution of Gender of the Respondents
Q1 Frequency Percent Valid Percent Cumulative
Percent
Male 36 58.1 58.1 58.1
Female 25 40.3 40.3 98.4
Prefer not to say 1 1.6 1.6 100.0
Total 62 100.0 100.0
Note: Q1: Please specify your gender
i reF gu 1: Distribution of Gender of the Respondents
The data collected from the survey comprised of 58.1% males and 40.3% females. One of the
respondents preferred not to reveal the information regarding gender.
Table 1: Frequency Distribution of Gender of the Respondents
Q1 Frequency Percent Valid Percent Cumulative
Percent
Male 36 58.1 58.1 58.1
Female 25 40.3 40.3 98.4
Prefer not to say 1 1.6 1.6 100.0
Total 62 100.0 100.0
Note: Q1: Please specify your gender
i reF gu 1: Distribution of Gender of the Respondents
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
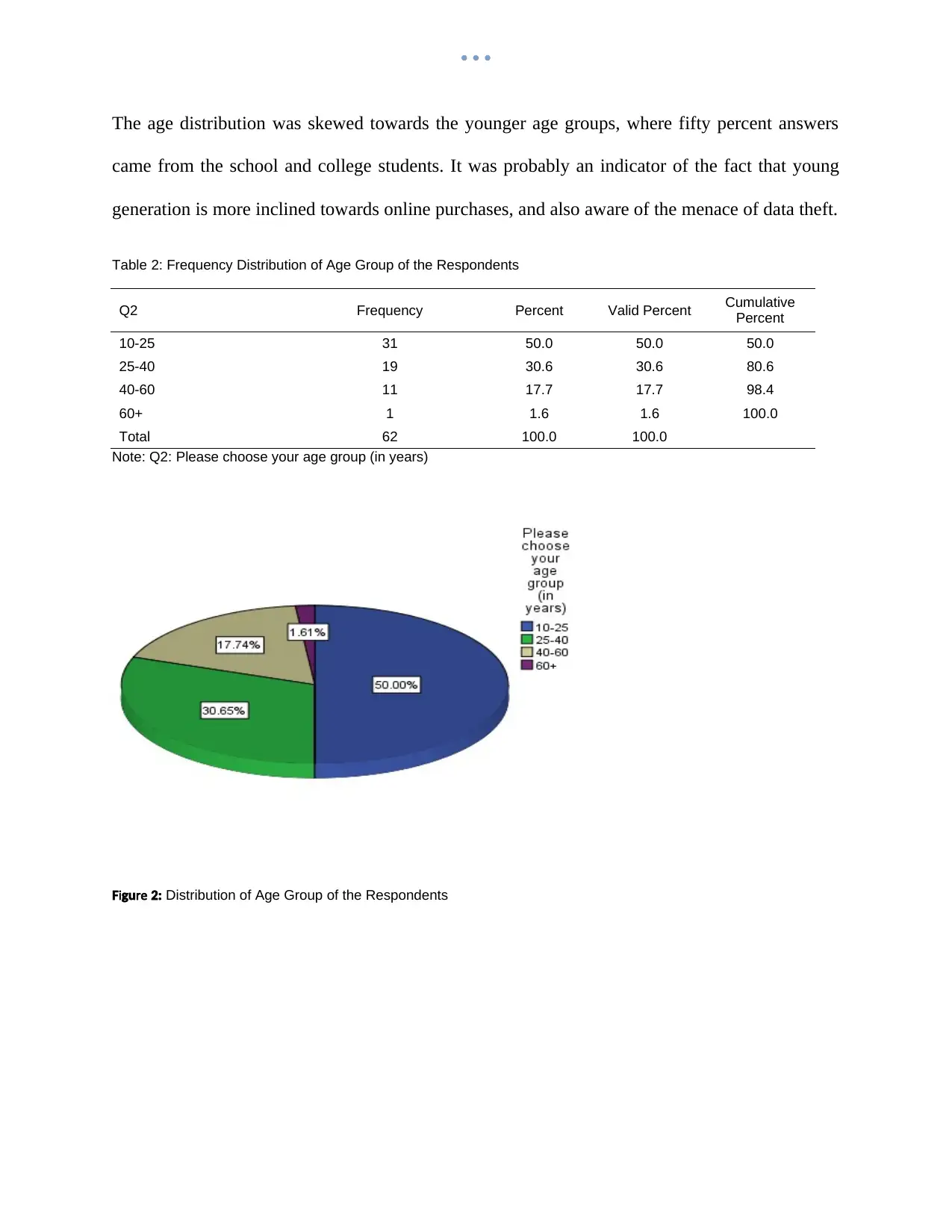
The age distribution was skewed towards the younger age groups, where fifty percent answers
came from the school and college students. It was probably an indicator of the fact that young
generation is more inclined towards online purchases, and also aware of the menace of data theft.
Table 2: Frequency Distribution of Age Group of the Respondents
Q2 Frequency Percent Valid Percent Cumulative
Percent
10-25 31 50.0 50.0 50.0
25-40 19 30.6 30.6 80.6
40-60 11 17.7 17.7 98.4
60+ 1 1.6 1.6 100.0
Total 62 100.0 100.0
Note: Q2: Please choose your age group (in years)
i reF gu 2: Distribution of Age Group of the Respondents
came from the school and college students. It was probably an indicator of the fact that young
generation is more inclined towards online purchases, and also aware of the menace of data theft.
Table 2: Frequency Distribution of Age Group of the Respondents
Q2 Frequency Percent Valid Percent Cumulative
Percent
10-25 31 50.0 50.0 50.0
25-40 19 30.6 30.6 80.6
40-60 11 17.7 17.7 98.4
60+ 1 1.6 1.6 100.0
Total 62 100.0 100.0
Note: Q2: Please choose your age group (in years)
i reF gu 2: Distribution of Age Group of the Respondents
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Data Exploration
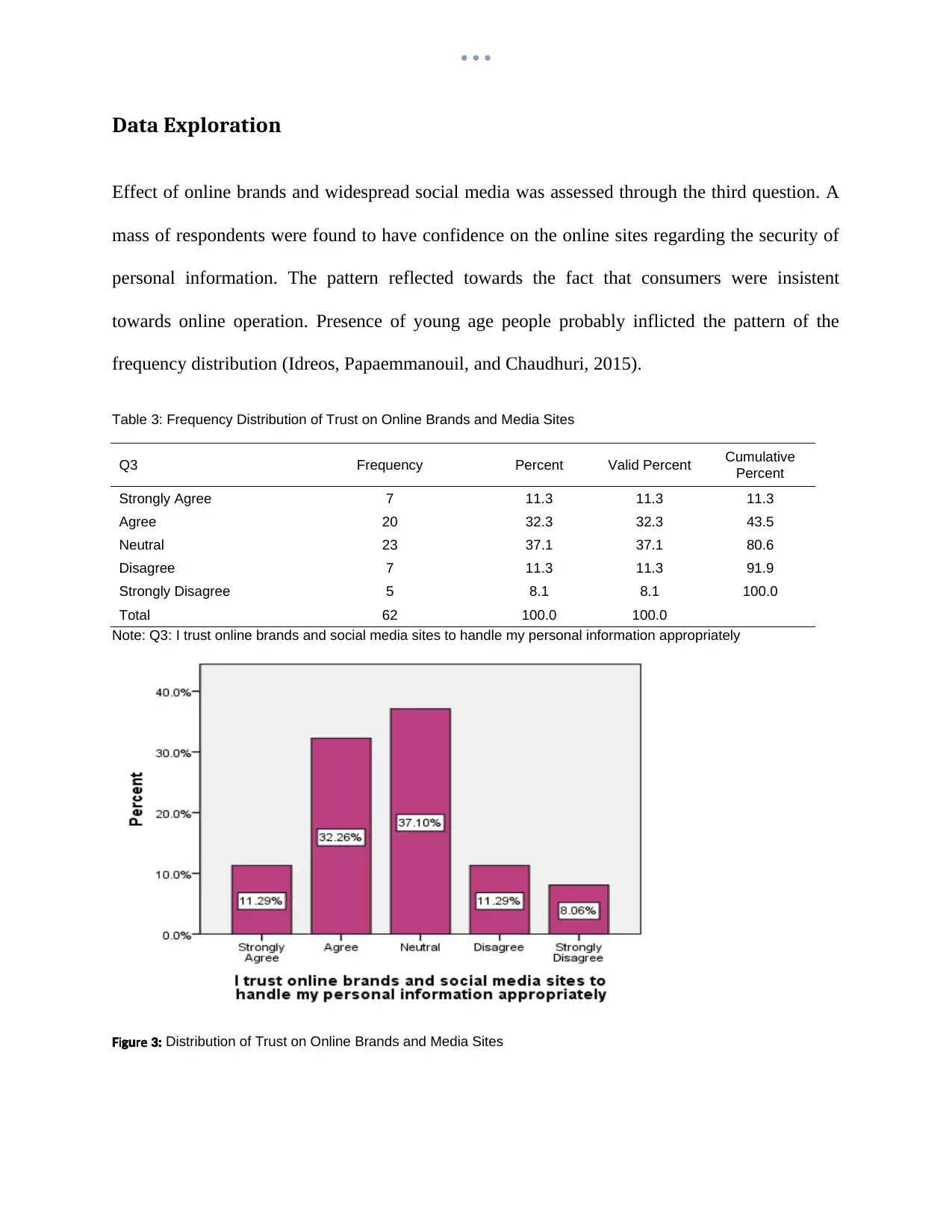
Effect of online brands and widespread social media was assessed through the third question. A
mass of respondents were found to have confidence on the online sites regarding the security of
personal information. The pattern reflected towards the fact that consumers were insistent
towards online operation. Presence of young age people probably inflicted the pattern of the
frequency distribution (Idreos, Papaemmanouil, and Chaudhuri, 2015).
Table 3: Frequency Distribution of Trust on Online Brands and Media Sites
Q3 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 7 11.3 11.3 11.3
Agree 20 32.3 32.3 43.5
Neutral 23 37.1 37.1 80.6
Disagree 7 11.3 11.3 91.9
Strongly Disagree 5 8.1 8.1 100.0
Total 62 100.0 100.0
Note: Q3: I trust online brands and social media sites to handle my personal information appropriately
i reF gu 3: Distribution of Trust on Online Brands and Media Sites
Effect of online brands and widespread social media was assessed through the third question. A
mass of respondents were found to have confidence on the online sites regarding the security of
personal information. The pattern reflected towards the fact that consumers were insistent
towards online operation. Presence of young age people probably inflicted the pattern of the
frequency distribution (Idreos, Papaemmanouil, and Chaudhuri, 2015).
Table 3: Frequency Distribution of Trust on Online Brands and Media Sites
Q3 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 7 11.3 11.3 11.3
Agree 20 32.3 32.3 43.5
Neutral 23 37.1 37.1 80.6
Disagree 7 11.3 11.3 91.9
Strongly Disagree 5 8.1 8.1 100.0
Total 62 100.0 100.0
Note: Q3: I trust online brands and social media sites to handle my personal information appropriately
i reF gu 3: Distribution of Trust on Online Brands and Media Sites
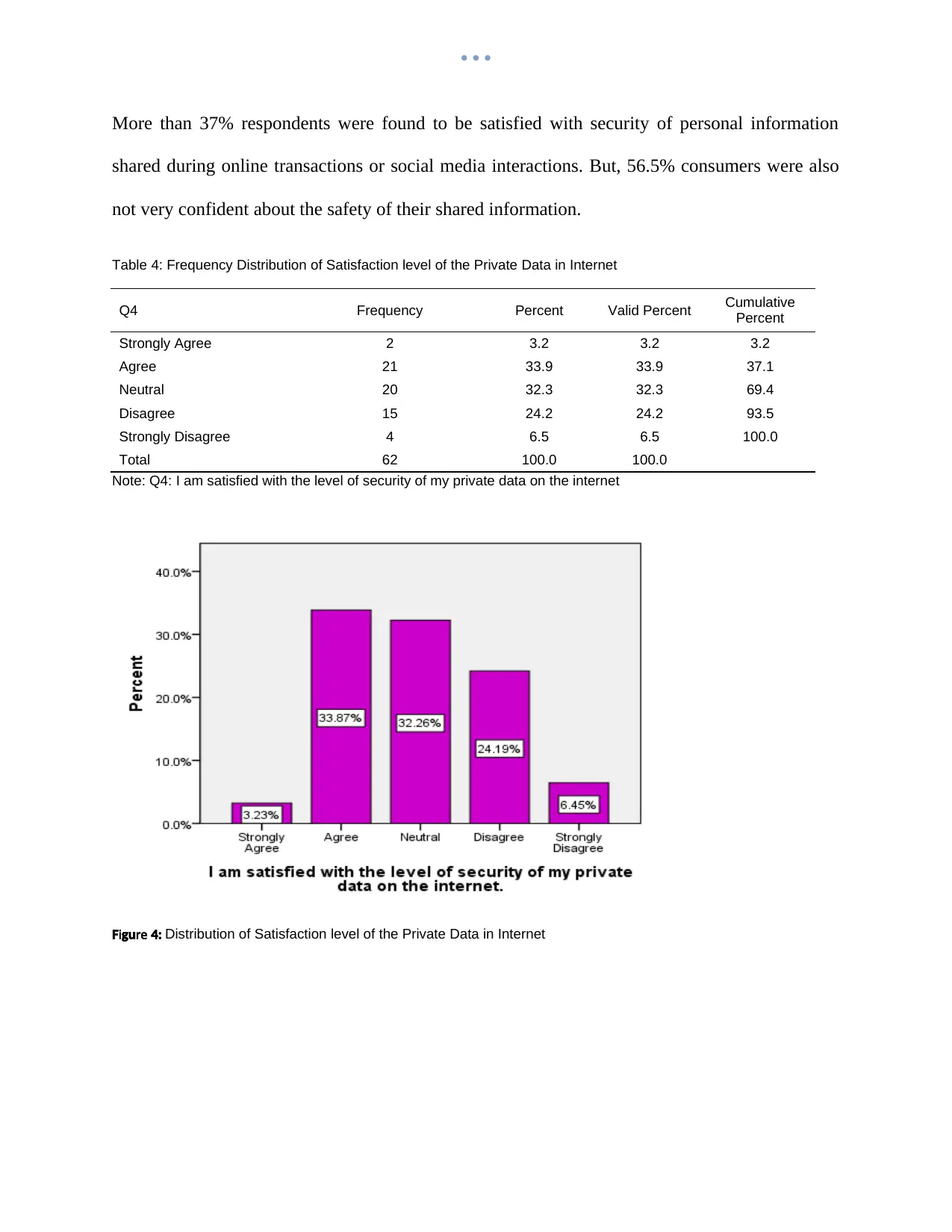
More than 37% respondents were found to be satisfied with security of personal information
shared during online transactions or social media interactions. But, 56.5% consumers were also
not very confident about the safety of their shared information.
Table 4: Frequency Distribution of Satisfaction level of the Private Data in Internet
Q4 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 2 3.2 3.2 3.2
Agree 21 33.9 33.9 37.1
Neutral 20 32.3 32.3 69.4
Disagree 15 24.2 24.2 93.5
Strongly Disagree 4 6.5 6.5 100.0
Total 62 100.0 100.0
Note: Q4: I am satisfied with the level of security of my private data on the internet
i reF gu 4: Distribution of Satisfaction level of the Private Data in Internet
shared during online transactions or social media interactions. But, 56.5% consumers were also
not very confident about the safety of their shared information.
Table 4: Frequency Distribution of Satisfaction level of the Private Data in Internet
Q4 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 2 3.2 3.2 3.2
Agree 21 33.9 33.9 37.1
Neutral 20 32.3 32.3 69.4
Disagree 15 24.2 24.2 93.5
Strongly Disagree 4 6.5 6.5 100.0
Total 62 100.0 100.0
Note: Q4: I am satisfied with the level of security of my private data on the internet
i reF gu 4: Distribution of Satisfaction level of the Private Data in Internet
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
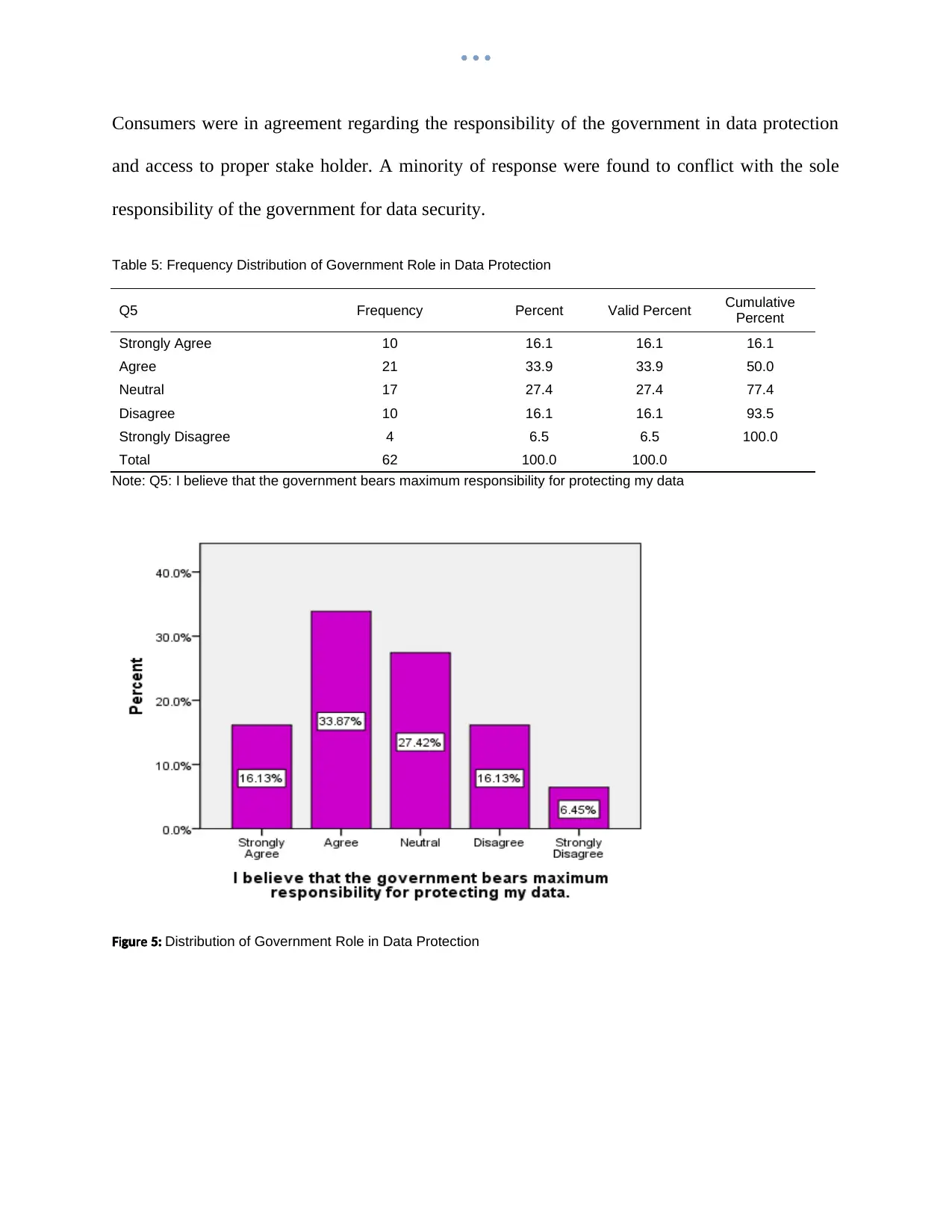
Consumers were in agreement regarding the responsibility of the government in data protection
and access to proper stake holder. A minority of response were found to conflict with the sole
responsibility of the government for data security.
Table 5: Frequency Distribution of Government Role in Data Protection
Q5 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 10 16.1 16.1 16.1
Agree 21 33.9 33.9 50.0
Neutral 17 27.4 27.4 77.4
Disagree 10 16.1 16.1 93.5
Strongly Disagree 4 6.5 6.5 100.0
Total 62 100.0 100.0
Note: Q5: I believe that the government bears maximum responsibility for protecting my data
i reF gu 5: Distribution of Government Role in Data Protection
and access to proper stake holder. A minority of response were found to conflict with the sole
responsibility of the government for data security.
Table 5: Frequency Distribution of Government Role in Data Protection
Q5 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 10 16.1 16.1 16.1
Agree 21 33.9 33.9 50.0
Neutral 17 27.4 27.4 77.4
Disagree 10 16.1 16.1 93.5
Strongly Disagree 4 6.5 6.5 100.0
Total 62 100.0 100.0
Note: Q5: I believe that the government bears maximum responsibility for protecting my data
i reF gu 5: Distribution of Government Role in Data Protection
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
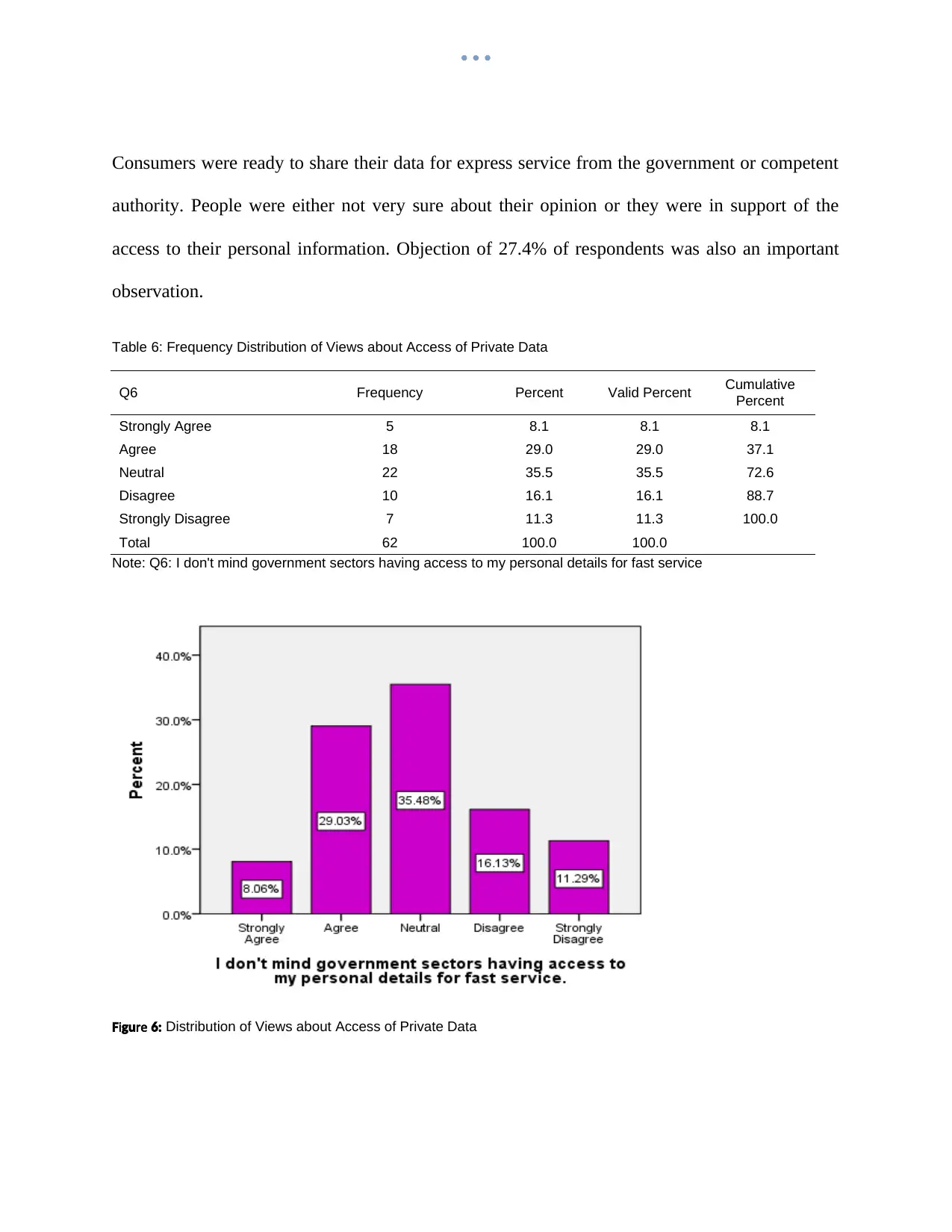
Consumers were ready to share their data for express service from the government or competent
authority. People were either not very sure about their opinion or they were in support of the
access to their personal information. Objection of 27.4% of respondents was also an important
observation.
Table 6: Frequency Distribution of Views about Access of Private Data
Q6 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 5 8.1 8.1 8.1
Agree 18 29.0 29.0 37.1
Neutral 22 35.5 35.5 72.6
Disagree 10 16.1 16.1 88.7
Strongly Disagree 7 11.3 11.3 100.0
Total 62 100.0 100.0
Note: Q6: I don't mind government sectors having access to my personal details for fast service
i reF gu 6: Distribution of Views about Access of Private Data
authority. People were either not very sure about their opinion or they were in support of the
access to their personal information. Objection of 27.4% of respondents was also an important
observation.
Table 6: Frequency Distribution of Views about Access of Private Data
Q6 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 5 8.1 8.1 8.1
Agree 18 29.0 29.0 37.1
Neutral 22 35.5 35.5 72.6
Disagree 10 16.1 16.1 88.7
Strongly Disagree 7 11.3 11.3 100.0
Total 62 100.0 100.0
Note: Q6: I don't mind government sectors having access to my personal details for fast service
i reF gu 6: Distribution of Views about Access of Private Data
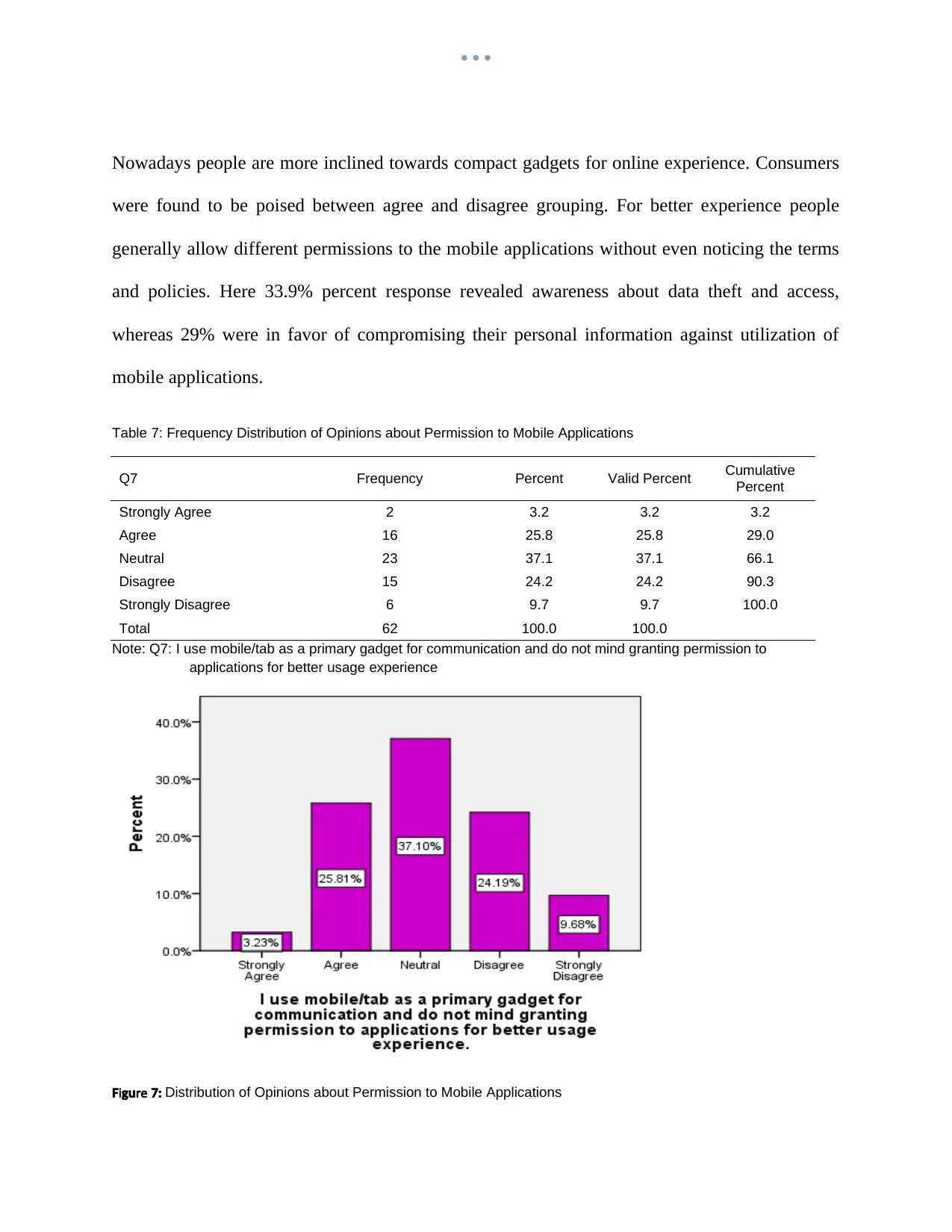
Nowadays people are more inclined towards compact gadgets for online experience. Consumers
were found to be poised between agree and disagree grouping. For better experience people
generally allow different permissions to the mobile applications without even noticing the terms
and policies. Here 33.9% percent response revealed awareness about data theft and access,
whereas 29% were in favor of compromising their personal information against utilization of
mobile applications.
Table 7: Frequency Distribution of Opinions about Permission to Mobile Applications
Q7 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 2 3.2 3.2 3.2
Agree 16 25.8 25.8 29.0
Neutral 23 37.1 37.1 66.1
Disagree 15 24.2 24.2 90.3
Strongly Disagree 6 9.7 9.7 100.0
Total 62 100.0 100.0
Note: Q7: I use mobile/tab as a primary gadget for communication and do not mind granting permission to
applications for better usage experience
i reF gu 7: Distribution of Opinions about Permission to Mobile Applications
were found to be poised between agree and disagree grouping. For better experience people
generally allow different permissions to the mobile applications without even noticing the terms
and policies. Here 33.9% percent response revealed awareness about data theft and access,
whereas 29% were in favor of compromising their personal information against utilization of
mobile applications.
Table 7: Frequency Distribution of Opinions about Permission to Mobile Applications
Q7 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 2 3.2 3.2 3.2
Agree 16 25.8 25.8 29.0
Neutral 23 37.1 37.1 66.1
Disagree 15 24.2 24.2 90.3
Strongly Disagree 6 9.7 9.7 100.0
Total 62 100.0 100.0
Note: Q7: I use mobile/tab as a primary gadget for communication and do not mind granting permission to
applications for better usage experience
i reF gu 7: Distribution of Opinions about Permission to Mobile Applications
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
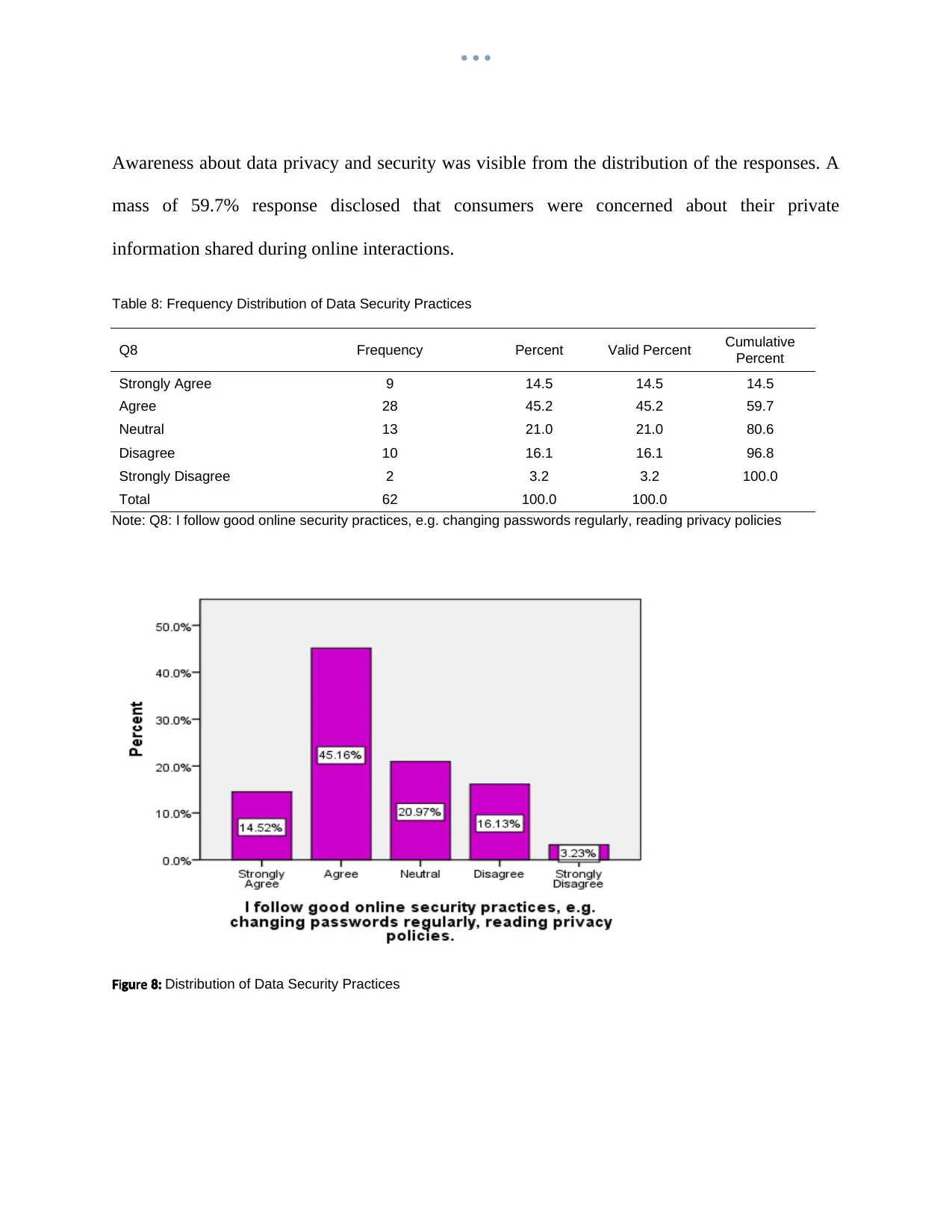
Awareness about data privacy and security was visible from the distribution of the responses. A
mass of 59.7% response disclosed that consumers were concerned about their private
information shared during online interactions.
Table 8: Frequency Distribution of Data Security Practices
Q8 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 9 14.5 14.5 14.5
Agree 28 45.2 45.2 59.7
Neutral 13 21.0 21.0 80.6
Disagree 10 16.1 16.1 96.8
Strongly Disagree 2 3.2 3.2 100.0
Total 62 100.0 100.0
Note: Q8: I follow good online security practices, e.g. changing passwords regularly, reading privacy policies
i reF gu 8: Distribution of Data Security Practices
mass of 59.7% response disclosed that consumers were concerned about their private
information shared during online interactions.
Table 8: Frequency Distribution of Data Security Practices
Q8 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 9 14.5 14.5 14.5
Agree 28 45.2 45.2 59.7
Neutral 13 21.0 21.0 80.6
Disagree 10 16.1 16.1 96.8
Strongly Disagree 2 3.2 3.2 100.0
Total 62 100.0 100.0
Note: Q8: I follow good online security practices, e.g. changing passwords regularly, reading privacy policies
i reF gu 8: Distribution of Data Security Practices
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
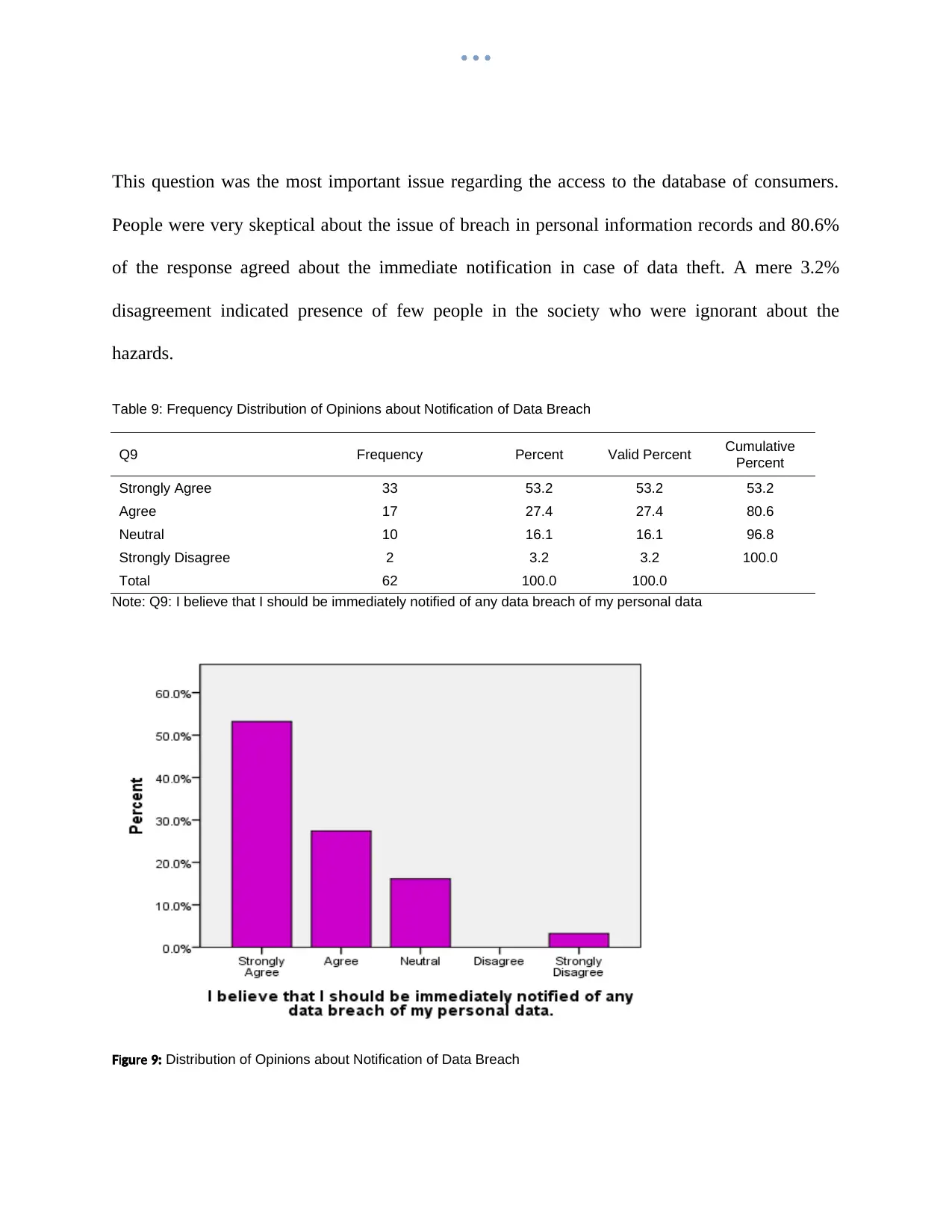
This question was the most important issue regarding the access to the database of consumers.
People were very skeptical about the issue of breach in personal information records and 80.6%
of the response agreed about the immediate notification in case of data theft. A mere 3.2%
disagreement indicated presence of few people in the society who were ignorant about the
hazards.
Table 9: Frequency Distribution of Opinions about Notification of Data Breach
Q9 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 33 53.2 53.2 53.2
Agree 17 27.4 27.4 80.6
Neutral 10 16.1 16.1 96.8
Strongly Disagree 2 3.2 3.2 100.0
Total 62 100.0 100.0
Note: Q9: I believe that I should be immediately notified of any data breach of my personal data
i reF gu 9: Distribution of Opinions about Notification of Data Breach
People were very skeptical about the issue of breach in personal information records and 80.6%
of the response agreed about the immediate notification in case of data theft. A mere 3.2%
disagreement indicated presence of few people in the society who were ignorant about the
hazards.
Table 9: Frequency Distribution of Opinions about Notification of Data Breach
Q9 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 33 53.2 53.2 53.2
Agree 17 27.4 27.4 80.6
Neutral 10 16.1 16.1 96.8
Strongly Disagree 2 3.2 3.2 100.0
Total 62 100.0 100.0
Note: Q9: I believe that I should be immediately notified of any data breach of my personal data
i reF gu 9: Distribution of Opinions about Notification of Data Breach
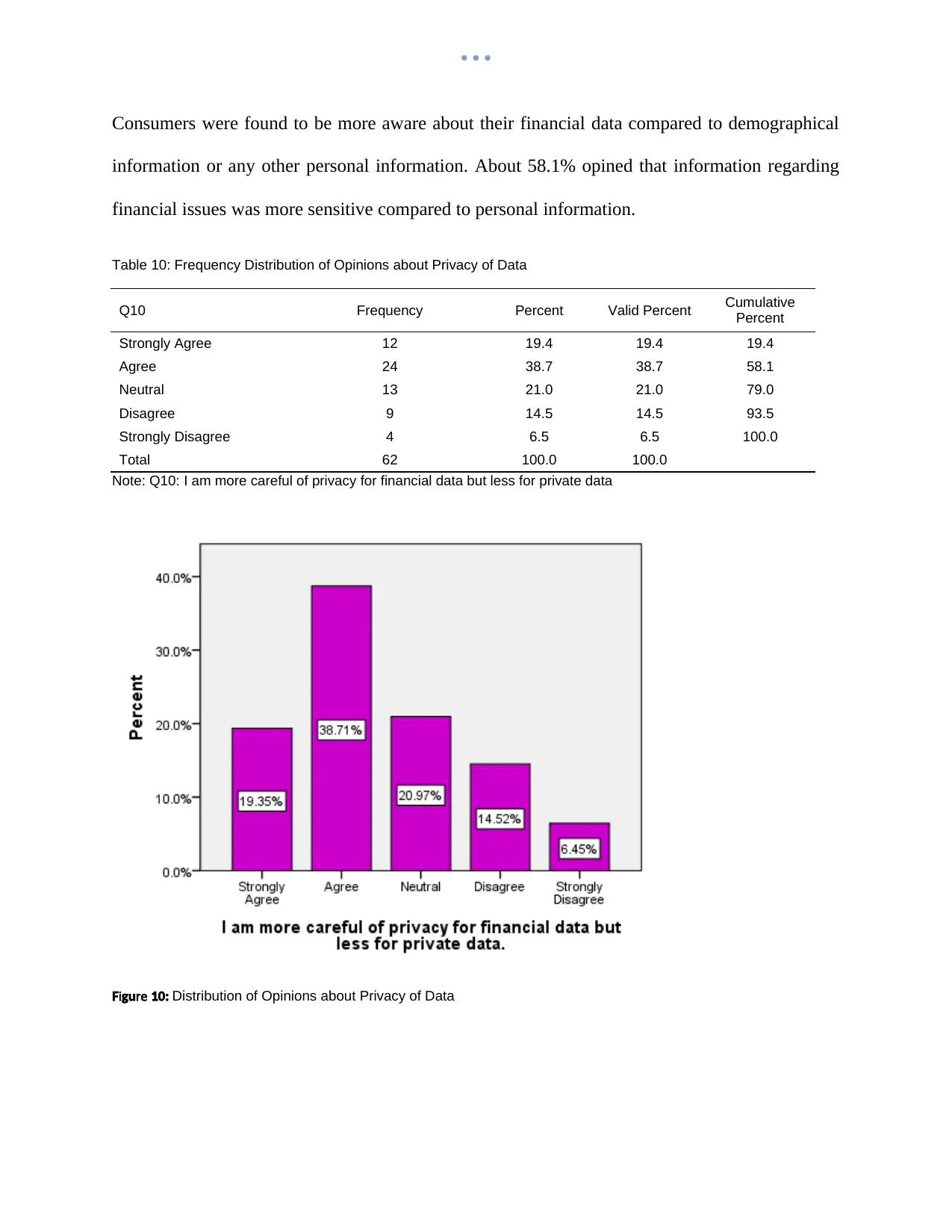
Consumers were found to be more aware about their financial data compared to demographical
information or any other personal information. About 58.1% opined that information regarding
financial issues was more sensitive compared to personal information.
Table 10: Frequency Distribution of Opinions about Privacy of Data
Q10 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 12 19.4 19.4 19.4
Agree 24 38.7 38.7 58.1
Neutral 13 21.0 21.0 79.0
Disagree 9 14.5 14.5 93.5
Strongly Disagree 4 6.5 6.5 100.0
Total 62 100.0 100.0
Note: Q10: I am more careful of privacy for financial data but less for private data
i reF gu 10: Distribution of Opinions about Privacy of Data
information or any other personal information. About 58.1% opined that information regarding
financial issues was more sensitive compared to personal information.
Table 10: Frequency Distribution of Opinions about Privacy of Data
Q10 Frequency Percent Valid Percent Cumulative
Percent
Strongly Agree 12 19.4 19.4 19.4
Agree 24 38.7 38.7 58.1
Neutral 13 21.0 21.0 79.0
Disagree 9 14.5 14.5 93.5
Strongly Disagree 4 6.5 6.5 100.0
Total 62 100.0 100.0
Note: Q10: I am more careful of privacy for financial data but less for private data
i reF gu 10: Distribution of Opinions about Privacy of Data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


