Improving Application Performance through Semantic Enrichment
VerifiedAdded on 2020/09/03
|23
|4682
|365
AI Summary
This assignment discusses the importance of semantic enrichment and extension in improving application performance. By associating relational databases with input factors, metadata duplication, and semantic enrichment, developers can optimize processes, provide efficient validation, and make improvements in digital content. The top-down and bottom-up approach to database design is also explored, highlighting the benefits of considering customer needs and requirements.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Database implementation
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
PART 2............................................................................................................................................1
TASK 1............................................................................................................................................1
Top down and Bottom up techniques.....................................................................................1
TASK 2............................................................................................................................................3
Entity relationship diagram....................................................................................................3
Conversion of ERD in a set of corresponding relations.........................................................5
Relational database design.....................................................................................................8
TASK 3............................................................................................................................................9
Tables using SQL query language for Books4U....................................................................9
Table Client............................................................................................................................9
Table Books..........................................................................................................................10
Table Transaction ................................................................................................................11
Table SalesVolume...............................................................................................................11
Table ProfitMarginP.............................................................................................................12
TASK 4..........................................................................................................................................13
SQL queries and screenshots................................................................................................13
TASK 5..........................................................................................................................................15
Enriching and extending semantic content of the database..................................................15
How can they improve application performance..................................................................15
REFERENCES..............................................................................................................................17
PART 2............................................................................................................................................1
TASK 1............................................................................................................................................1
Top down and Bottom up techniques.....................................................................................1
TASK 2............................................................................................................................................3
Entity relationship diagram....................................................................................................3
Conversion of ERD in a set of corresponding relations.........................................................5
Relational database design.....................................................................................................8
TASK 3............................................................................................................................................9
Tables using SQL query language for Books4U....................................................................9
Table Client............................................................................................................................9
Table Books..........................................................................................................................10
Table Transaction ................................................................................................................11
Table SalesVolume...............................................................................................................11
Table ProfitMarginP.............................................................................................................12
TASK 4..........................................................................................................................................13
SQL queries and screenshots................................................................................................13
TASK 5..........................................................................................................................................15
Enriching and extending semantic content of the database..................................................15
How can they improve application performance..................................................................15
REFERENCES..............................................................................................................................17
PART 2
TASK 1
Top down and Bottom up techniques
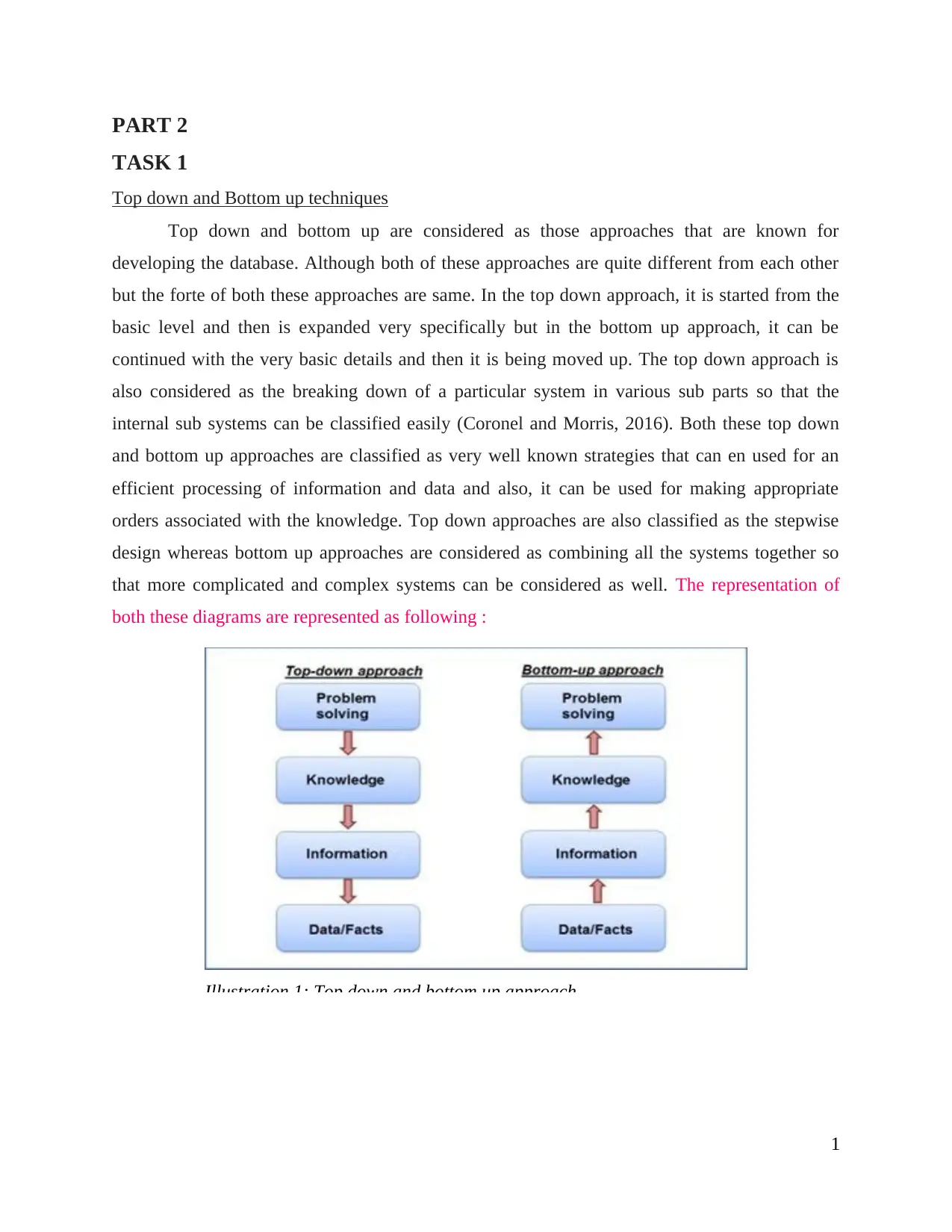
Top down and bottom up are considered as those approaches that are known for
developing the database. Although both of these approaches are quite different from each other
but the forte of both these approaches are same. In the top down approach, it is started from the
basic level and then is expanded very specifically but in the bottom up approach, it can be
continued with the very basic details and then it is being moved up. The top down approach is
also considered as the breaking down of a particular system in various sub parts so that the
internal sub systems can be classified easily (Coronel and Morris, 2016). Both these top down
and bottom up approaches are classified as very well known strategies that can en used for an
efficient processing of information and data and also, it can be used for making appropriate
orders associated with the knowledge. Top down approaches are also classified as the stepwise
design whereas bottom up approaches are considered as combining all the systems together so
that more complicated and complex systems can be considered as well. The representation of
both these diagrams are represented as following :
Illustration 1: Top down and bottom up approach
1
TASK 1
Top down and Bottom up techniques
Top down and bottom up are considered as those approaches that are known for
developing the database. Although both of these approaches are quite different from each other
but the forte of both these approaches are same. In the top down approach, it is started from the
basic level and then is expanded very specifically but in the bottom up approach, it can be
continued with the very basic details and then it is being moved up. The top down approach is
also considered as the breaking down of a particular system in various sub parts so that the
internal sub systems can be classified easily (Coronel and Morris, 2016). Both these top down
and bottom up approaches are classified as very well known strategies that can en used for an
efficient processing of information and data and also, it can be used for making appropriate
orders associated with the knowledge. Top down approaches are also classified as the stepwise
design whereas bottom up approaches are considered as combining all the systems together so
that more complicated and complex systems can be considered as well. The representation of
both these diagrams are represented as following :
Illustration 1: Top down and bottom up approach
1
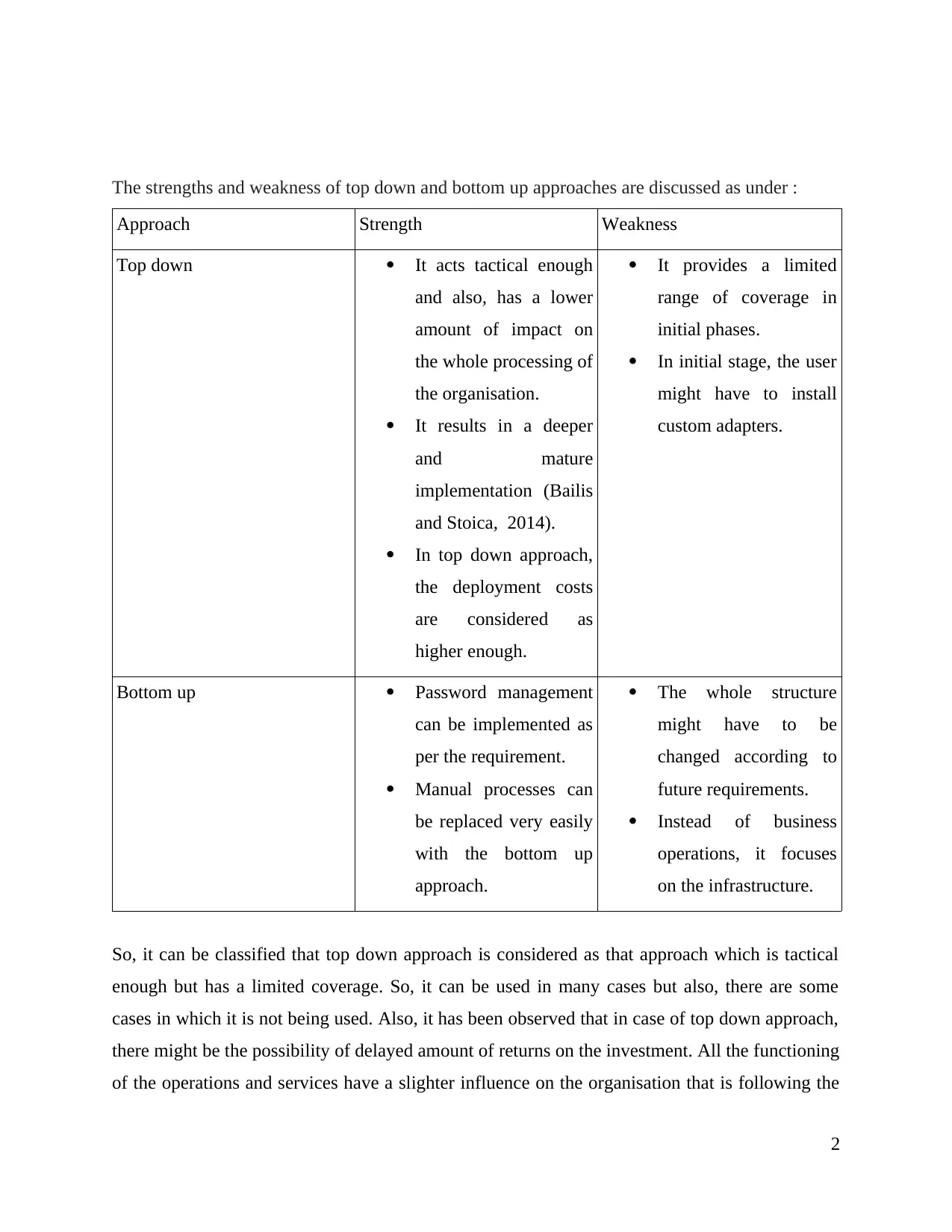
The strengths and weakness of top down and bottom up approaches are discussed as under :
Approach Strength Weakness
Top down It acts tactical enough
and also, has a lower
amount of impact on
the whole processing of
the organisation.
It results in a deeper
and mature
implementation (Bailis
and Stoica, 2014).
In top down approach,
the deployment costs
are considered as
higher enough.
It provides a limited
range of coverage in
initial phases.
In initial stage, the user
might have to install
custom adapters.
Bottom up Password management
can be implemented as
per the requirement.
Manual processes can
be replaced very easily
with the bottom up
approach.
The whole structure
might have to be
changed according to
future requirements.
Instead of business
operations, it focuses
on the infrastructure.
So, it can be classified that top down approach is considered as that approach which is tactical
enough but has a limited coverage. So, it can be used in many cases but also, there are some
cases in which it is not being used. Also, it has been observed that in case of top down approach,
there might be the possibility of delayed amount of returns on the investment. All the functioning
of the operations and services have a slighter influence on the organisation that is following the
2
Approach Strength Weakness
Top down It acts tactical enough
and also, has a lower
amount of impact on
the whole processing of
the organisation.
It results in a deeper
and mature
implementation (Bailis
and Stoica, 2014).
In top down approach,
the deployment costs
are considered as
higher enough.
It provides a limited
range of coverage in
initial phases.
In initial stage, the user
might have to install
custom adapters.
Bottom up Password management
can be implemented as
per the requirement.
Manual processes can
be replaced very easily
with the bottom up
approach.
The whole structure
might have to be
changed according to
future requirements.
Instead of business
operations, it focuses
on the infrastructure.
So, it can be classified that top down approach is considered as that approach which is tactical
enough but has a limited coverage. So, it can be used in many cases but also, there are some
cases in which it is not being used. Also, it has been observed that in case of top down approach,
there might be the possibility of delayed amount of returns on the investment. All the functioning
of the operations and services have a slighter influence on the organisation that is following the
2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

top down approach. As there are various benefits of the top down approach, there are some
drawbacks as well. The organisation following a top down approach makes a proper and
complete involvement of all the services and operations and that is to be managed by different
applications of the organisation (Hutchison, Kepner and Fuchs, 2015). The initial
implementation using the top down approach is said to be used as a showcase so that it can
further help in investigating the solutions more efficiently and appropriately.
As the top down approach can be classified in benefits and drawbacks, the same way,
bottom up approach can also be classified in the same way. Bottom up approach makes the
return quite early than the top down approaches on investment. Also, the organisation making
involvement of the bottom up approach, it has been observed that usually they tend to get the
benefits in the earlier phase only. So, this can be considered as a beneficial factor for the
organisation. But the fact then which is to ensure that is the organisation should stay on a single
approach only because any sort of fluctuation from one approach to another can make some
affects on the processing speed of the operations and services that are being provided by the
organisation. It thus further helps in maximizing the management skills as well to a huge extent.
Along with the management skills, it also helps in broadening the understanding of the person as
well. As there are some advantages, there are some disadvantages as well such as instead of
keeping its focus on the processing and operations of the business, the bottom up approach refers
to the infrastructure of the existing factors and services. There is also the possibility of the
immediate and urgent modifications to the repository ones and the people that are connected with
the same. But a specialised feature that can be implemented by the help of bottom up approach is
that implementation of passwords can be easily set for a maximum number of users so that the
privacy feature can stay maintained. It is important as well because it is obvious that the systems
of the organisation consists of all the details and information about the employees, services etc.
So, it should not be revealed to any external body. So, for protecting the data and information
from any external or unauthorised person, it helps in implementing the security factors so that the
systems and the data can stay protected of passwords and specific user ID's so that only the
internal authority can have access to the personal information and data. So, it can even assure the
organisation to stay maintained and protected the information and data.
3
drawbacks as well. The organisation following a top down approach makes a proper and
complete involvement of all the services and operations and that is to be managed by different
applications of the organisation (Hutchison, Kepner and Fuchs, 2015). The initial
implementation using the top down approach is said to be used as a showcase so that it can
further help in investigating the solutions more efficiently and appropriately.
As the top down approach can be classified in benefits and drawbacks, the same way,
bottom up approach can also be classified in the same way. Bottom up approach makes the
return quite early than the top down approaches on investment. Also, the organisation making
involvement of the bottom up approach, it has been observed that usually they tend to get the
benefits in the earlier phase only. So, this can be considered as a beneficial factor for the
organisation. But the fact then which is to ensure that is the organisation should stay on a single
approach only because any sort of fluctuation from one approach to another can make some
affects on the processing speed of the operations and services that are being provided by the
organisation. It thus further helps in maximizing the management skills as well to a huge extent.
Along with the management skills, it also helps in broadening the understanding of the person as
well. As there are some advantages, there are some disadvantages as well such as instead of
keeping its focus on the processing and operations of the business, the bottom up approach refers
to the infrastructure of the existing factors and services. There is also the possibility of the
immediate and urgent modifications to the repository ones and the people that are connected with
the same. But a specialised feature that can be implemented by the help of bottom up approach is
that implementation of passwords can be easily set for a maximum number of users so that the
privacy feature can stay maintained. It is important as well because it is obvious that the systems
of the organisation consists of all the details and information about the employees, services etc.
So, it should not be revealed to any external body. So, for protecting the data and information
from any external or unauthorised person, it helps in implementing the security factors so that the
systems and the data can stay protected of passwords and specific user ID's so that only the
internal authority can have access to the personal information and data. So, it can even assure the
organisation to stay maintained and protected the information and data.
3
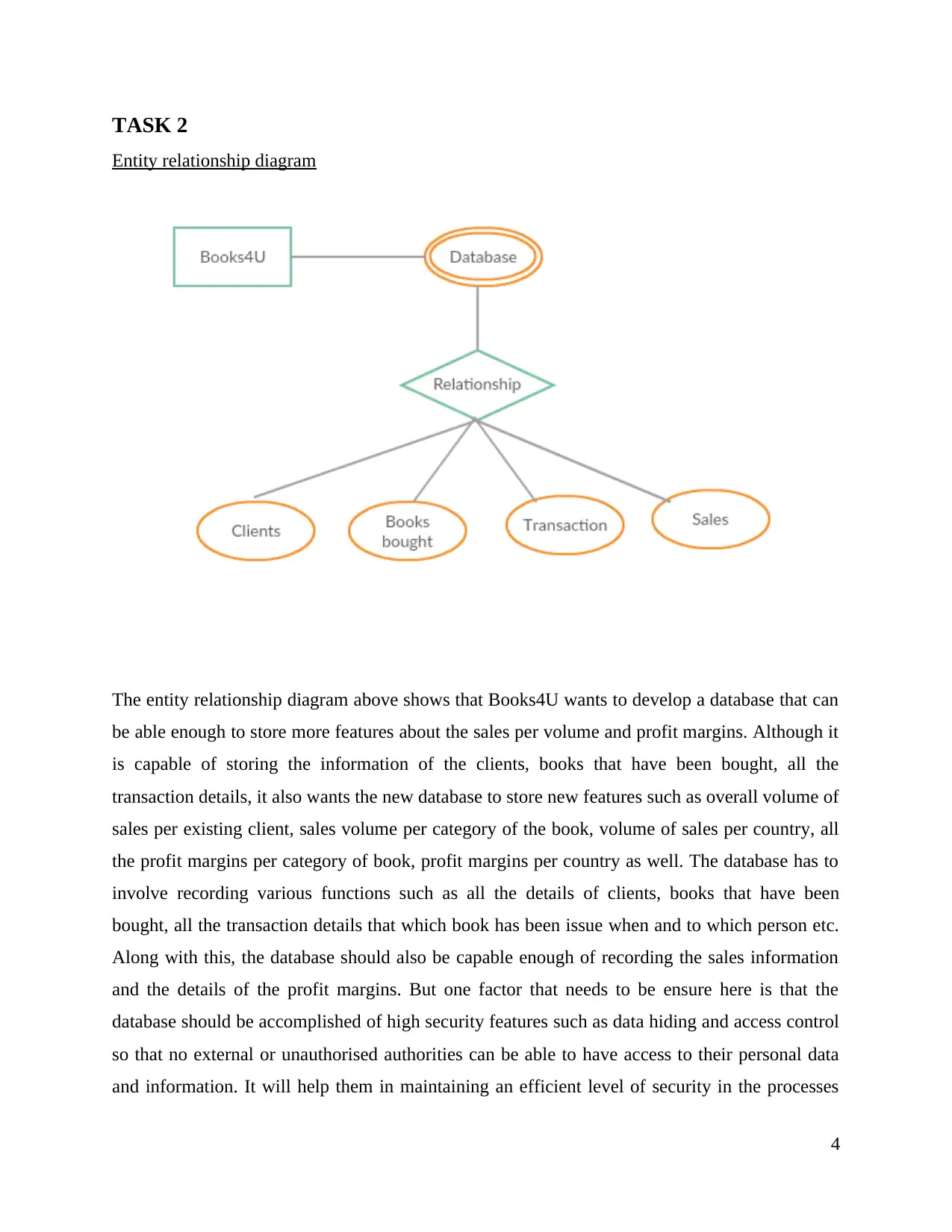
TASK 2
Entity relationship diagram
The entity relationship diagram above shows that Books4U wants to develop a database that can
be able enough to store more features about the sales per volume and profit margins. Although it
is capable of storing the information of the clients, books that have been bought, all the
transaction details, it also wants the new database to store new features such as overall volume of
sales per existing client, sales volume per category of the book, volume of sales per country, all
the profit margins per category of book, profit margins per country as well. The database has to
involve recording various functions such as all the details of clients, books that have been
bought, all the transaction details that which book has been issue when and to which person etc.
Along with this, the database should also be capable enough of recording the sales information
and the details of the profit margins. But one factor that needs to be ensure here is that the
database should be accomplished of high security features such as data hiding and access control
so that no external or unauthorised authorities can be able to have access to their personal data
and information. It will help them in maintaining an efficient level of security in the processes
4
Entity relationship diagram
The entity relationship diagram above shows that Books4U wants to develop a database that can
be able enough to store more features about the sales per volume and profit margins. Although it
is capable of storing the information of the clients, books that have been bought, all the
transaction details, it also wants the new database to store new features such as overall volume of
sales per existing client, sales volume per category of the book, volume of sales per country, all
the profit margins per category of book, profit margins per country as well. The database has to
involve recording various functions such as all the details of clients, books that have been
bought, all the transaction details that which book has been issue when and to which person etc.
Along with this, the database should also be capable enough of recording the sales information
and the details of the profit margins. But one factor that needs to be ensure here is that the
database should be accomplished of high security features such as data hiding and access control
so that no external or unauthorised authorities can be able to have access to their personal data
and information. It will help them in maintaining an efficient level of security in the processes
4

and operations of the company, thus maintaining a balance between different variables. The
database in the diagram has been introduced as a multi valued attribute because in this case,
according to the requirement of the Books4U, there are various different factors of the database
that it has to perform. It includes a variety of operations that involves recording the information
about books bought, transactions, sales, profit margins etc. So, as it is accomplishing variety of
operations, it can be considered as multi valued. Also, they want to manage all the credit ratings
of the new as well as existing clients. These features are to be required by Books4U that they
want to implement in the new database. Also, as per the new requirements they want some
specialised features in the database such as data hiding and access control capabilities. Both of
these features are required in order to have a proper control of who can access it and who cannot.
It is very important to maintain the security of the files and all the essential data that is stored in
all the systems of the network.
Conversion of ERD in a set of corresponding relations
As per the requirement of Books4U, they want a specialised database to be designed that can
save a good and a huge quality of information. As it is obvious to save the information and data
about the clients, books bought, transaction etc. It is very important to make sure that the
database is capable enough of involving the sales as well as profit margin details of per volume,
book category etc. Also, this specialised database should have access control features which
means that there should be proper security that ensures that only the authorities can have access
to some part of the data that is personalised. The security should be maintained in a way that the
data may not be accessible to everyone. Also, along with this, it includes a factor that no external
body can attack it. This can be prevented by making involvement of a firewall because in case of
reputed firms, there is a possibility that to let them down or for various other purposes, the
5
database in the diagram has been introduced as a multi valued attribute because in this case,
according to the requirement of the Books4U, there are various different factors of the database
that it has to perform. It includes a variety of operations that involves recording the information
about books bought, transactions, sales, profit margins etc. So, as it is accomplishing variety of
operations, it can be considered as multi valued. Also, they want to manage all the credit ratings
of the new as well as existing clients. These features are to be required by Books4U that they
want to implement in the new database. Also, as per the new requirements they want some
specialised features in the database such as data hiding and access control capabilities. Both of
these features are required in order to have a proper control of who can access it and who cannot.
It is very important to maintain the security of the files and all the essential data that is stored in
all the systems of the network.
Conversion of ERD in a set of corresponding relations
As per the requirement of Books4U, they want a specialised database to be designed that can
save a good and a huge quality of information. As it is obvious to save the information and data
about the clients, books bought, transaction etc. It is very important to make sure that the
database is capable enough of involving the sales as well as profit margin details of per volume,
book category etc. Also, this specialised database should have access control features which
means that there should be proper security that ensures that only the authorities can have access
to some part of the data that is personalised. The security should be maintained in a way that the
data may not be accessible to everyone. Also, along with this, it includes a factor that no external
body can attack it. This can be prevented by making involvement of a firewall because in case of
reputed firms, there is a possibility that to let them down or for various other purposes, the
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

attackers can try to steal their information and data. There are various ways that can be used by
the attackers such as making viruses in form of advertisements, pop ups etc., so the database
should be efficient enough that it involves all the factors essential to deal with such viruses and
do not let them to have any part of data.
6
the attackers such as making viruses in form of advertisements, pop ups etc., so the database
should be efficient enough that it involves all the factors essential to deal with such viruses and
do not let them to have any part of data.
6
As it is clear from the requirement of Books4U that they need a new database which must
be acquiring all the information and data. Although the information about clients, books bought,
transaction etc. have been involved but the basic requirement of them is that they want to include
various new features such as data hiding and access control. These features are must because it is
very important that when their operations and number of services will increase, there might be
the possibility that the attackers can try to steal their data and personal information. So, in that
case, it is very important to make the database secure enough so that no external body can have
access to the personal data and information from the systems of Books4U and also, it will help in
protecting the systems that are also present over the same network.
As per the requirement, the relationship represented is from one to many because there
are various new features that are to be added but all of that will be done from a single database
only. Therefore, it can be considered as one to many relationships in which a single database will
help in involving all the features, whether it is about the details of the customers or the details
regarding the books and transactions.
Taking an example by taking the client table
The primary keys are demonstrated as bold .
ClientName ClientID ClientAddress ClientNoOfBooks
Priti 1 LPStreet 3
Richa 2 UMStreet 2
Tina 3 CRStreet 3
Normalising the table in 3NF form as under :
ClientName ClientID ClientNoOfBooks
Priti 1 3
Richa 2 2
Tina 3 3
7
be acquiring all the information and data. Although the information about clients, books bought,
transaction etc. have been involved but the basic requirement of them is that they want to include
various new features such as data hiding and access control. These features are must because it is
very important that when their operations and number of services will increase, there might be
the possibility that the attackers can try to steal their data and personal information. So, in that
case, it is very important to make the database secure enough so that no external body can have
access to the personal data and information from the systems of Books4U and also, it will help in
protecting the systems that are also present over the same network.
As per the requirement, the relationship represented is from one to many because there
are various new features that are to be added but all of that will be done from a single database
only. Therefore, it can be considered as one to many relationships in which a single database will
help in involving all the features, whether it is about the details of the customers or the details
regarding the books and transactions.
Taking an example by taking the client table
The primary keys are demonstrated as bold .
ClientName ClientID ClientAddress ClientNoOfBooks
Priti 1 LPStreet 3
Richa 2 UMStreet 2
Tina 3 CRStreet 3
Normalising the table in 3NF form as under :
ClientName ClientID ClientNoOfBooks
Priti 1 3
Richa 2 2
Tina 3 3
7
ClientID ClientAddress
1 LPStreet
2 UMStreet
3 CRStreet
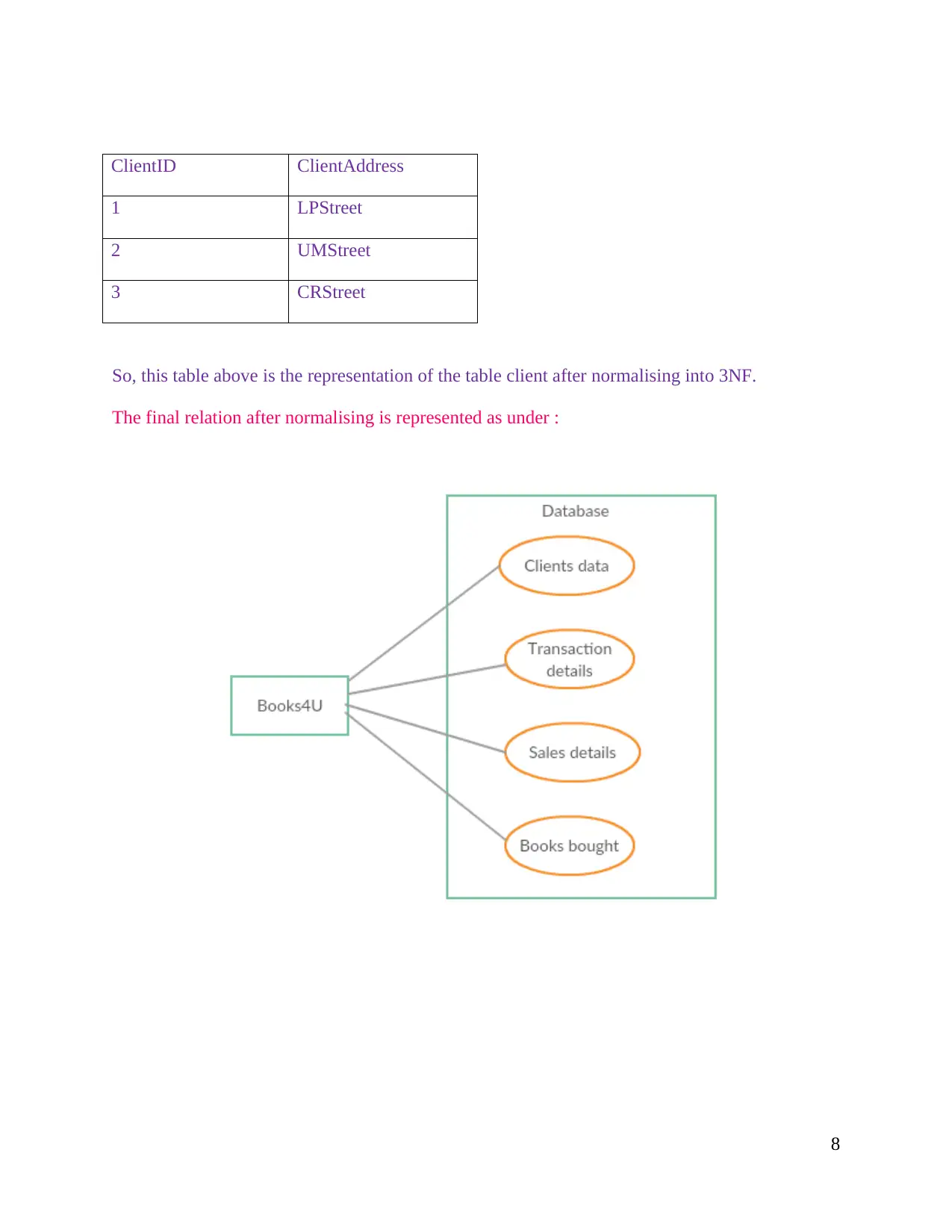
So, this table above is the representation of the table client after normalising into 3NF.
The final relation after normalising is represented as under :
8
1 LPStreet
2 UMStreet
3 CRStreet
So, this table above is the representation of the table client after normalising into 3NF.
The final relation after normalising is represented as under :
8
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
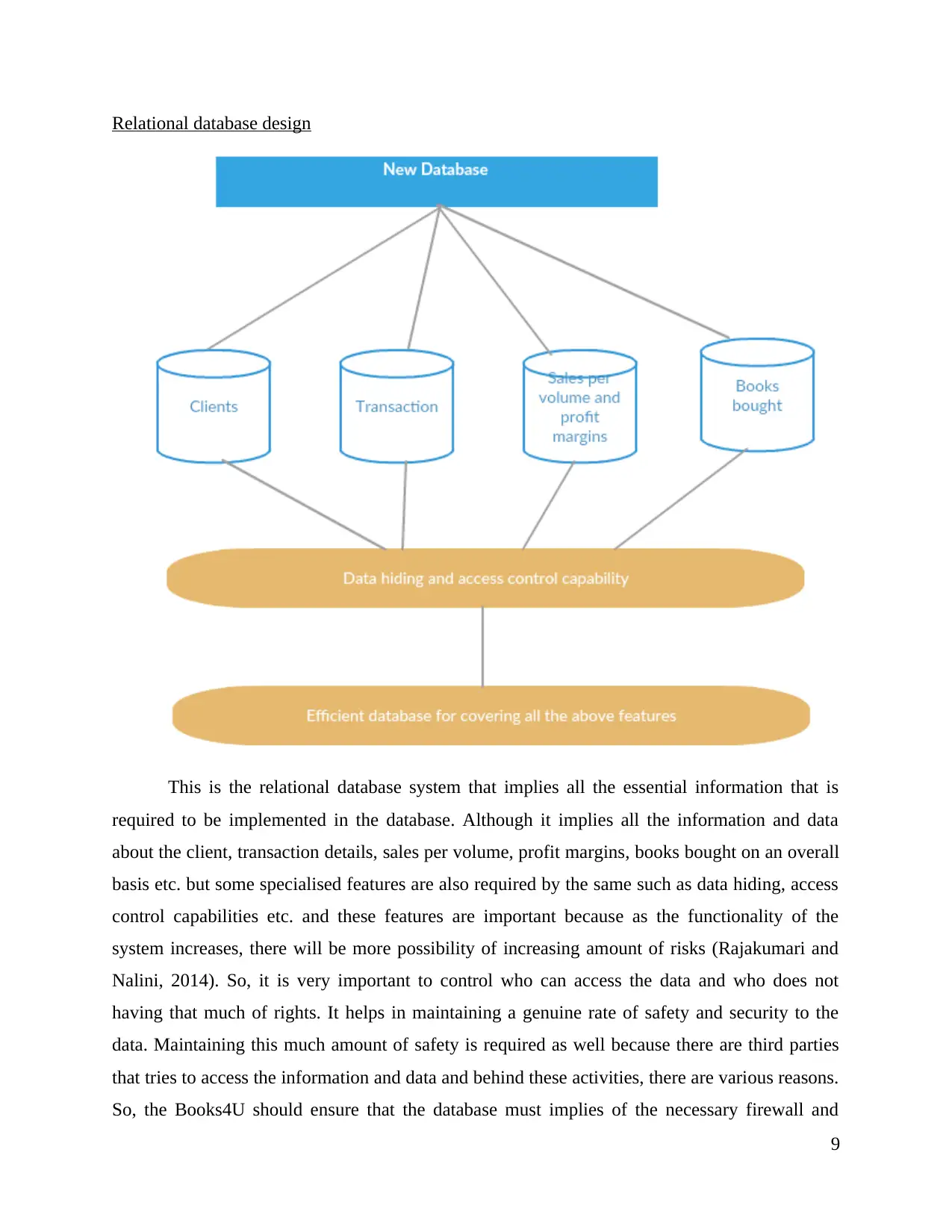
Relational database design
This is the relational database system that implies all the essential information that is
required to be implemented in the database. Although it implies all the information and data
about the client, transaction details, sales per volume, profit margins, books bought on an overall
basis etc. but some specialised features are also required by the same such as data hiding, access
control capabilities etc. and these features are important because as the functionality of the
system increases, there will be more possibility of increasing amount of risks (Rajakumari and
Nalini, 2014). So, it is very important to control who can access the data and who does not
having that much of rights. It helps in maintaining a genuine rate of safety and security to the
data. Maintaining this much amount of safety is required as well because there are third parties
that tries to access the information and data and behind these activities, there are various reasons.
So, the Books4U should ensure that the database must implies of the necessary firewall and
9
This is the relational database system that implies all the essential information that is
required to be implemented in the database. Although it implies all the information and data
about the client, transaction details, sales per volume, profit margins, books bought on an overall
basis etc. but some specialised features are also required by the same such as data hiding, access
control capabilities etc. and these features are important because as the functionality of the
system increases, there will be more possibility of increasing amount of risks (Rajakumari and
Nalini, 2014). So, it is very important to control who can access the data and who does not
having that much of rights. It helps in maintaining a genuine rate of safety and security to the
data. Maintaining this much amount of safety is required as well because there are third parties
that tries to access the information and data and behind these activities, there are various reasons.
So, the Books4U should ensure that the database must implies of the necessary firewall and
9

security features so that no such external body can steal the personal data or information of any
employee. As the operations and services of the book store are increasing, so there is a higher
probability that there can occur more complex and complicated situations. Thus, it is very
important to make the database secure enough that no external body can have any access to their
personal data and information. This will further help in maintaining the database efficient enough
and suitable enough that it acts capable enough of satisfying the basic requirements of Books4U.
TASK 3
Tables using SQL query language for Books4U
Table Client
create table STU52382CLIENT (
STU52382CLIENTID varchar (25),
FName varchar (25),
Address varchar (25),
City varchar (25)DEFAULT 'WALSTREET'
);
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('A', 'Reety', '10Street','TESLA');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('B', 'Supfy', '12Street','CHING');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('C', 'Rechal', '14Street','RESTA');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('D', 'Pesty', '15Street','LONDON');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('E', 'Terry', '16Street','SEPIA');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('F', 'Jerry', '1Street','UK');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('G', 'Lerry', '168Street','SEPIA');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('H', 'Terrial', '162Street','LONDON');
10
employee. As the operations and services of the book store are increasing, so there is a higher
probability that there can occur more complex and complicated situations. Thus, it is very
important to make the database secure enough that no external body can have any access to their
personal data and information. This will further help in maintaining the database efficient enough
and suitable enough that it acts capable enough of satisfying the basic requirements of Books4U.
TASK 3
Tables using SQL query language for Books4U
Table Client
create table STU52382CLIENT (
STU52382CLIENTID varchar (25),
FName varchar (25),
Address varchar (25),
City varchar (25)DEFAULT 'WALSTREET'
);
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('A', 'Reety', '10Street','TESLA');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('B', 'Supfy', '12Street','CHING');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('C', 'Rechal', '14Street','RESTA');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('D', 'Pesty', '15Street','LONDON');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('E', 'Terry', '16Street','SEPIA');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('F', 'Jerry', '1Street','UK');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('G', 'Lerry', '168Street','SEPIA');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('H', 'Terrial', '162Street','LONDON');
10
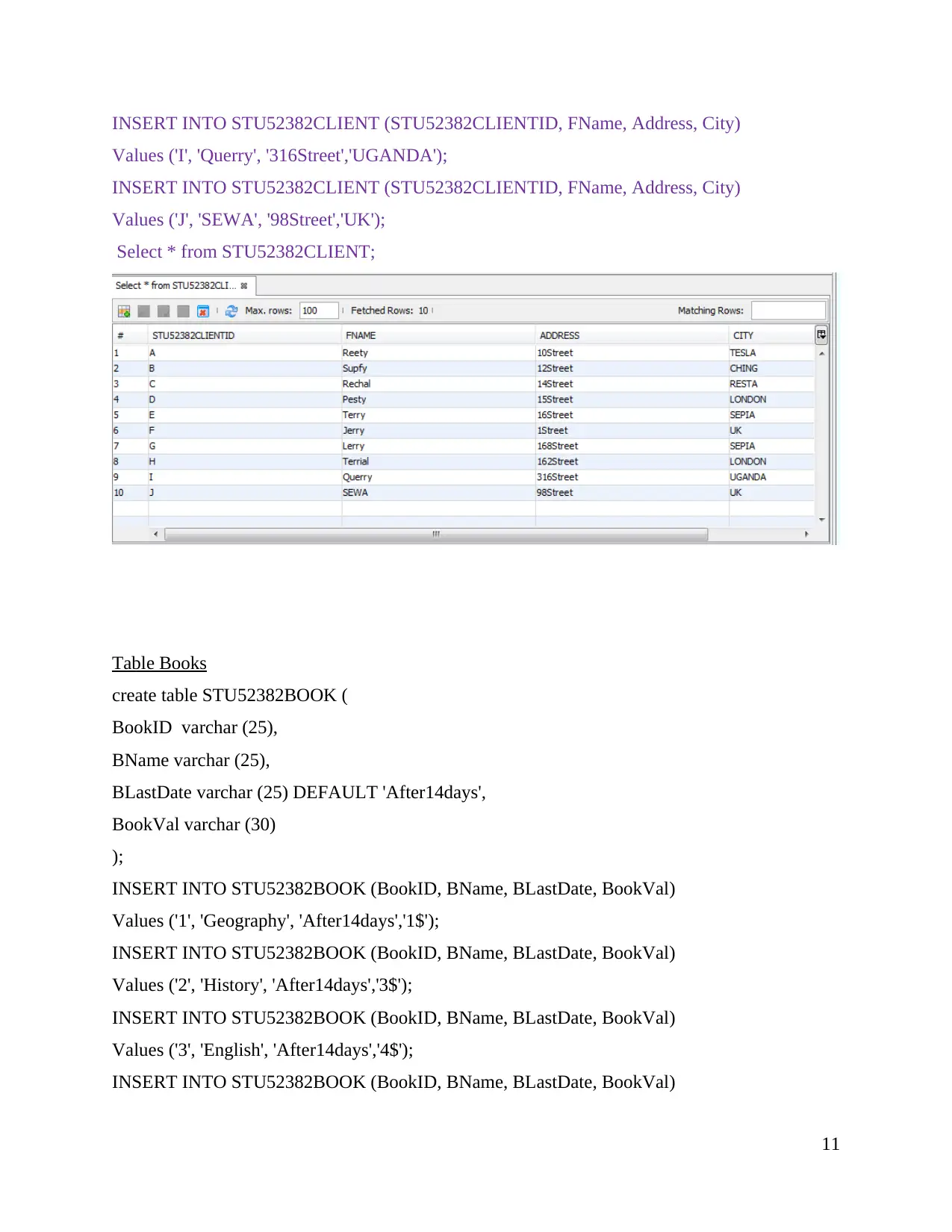
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('I', 'Querry', '316Street','UGANDA');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('J', 'SEWA', '98Street','UK');
Select * from STU52382CLIENT;
Table Books
create table STU52382BOOK (
BookID varchar (25),
BName varchar (25),
BLastDate varchar (25) DEFAULT 'After14days',
BookVal varchar (30)
);
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('1', 'Geography', 'After14days','1$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('2', 'History', 'After14days','3$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('3', 'English', 'After14days','4$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
11
Values ('I', 'Querry', '316Street','UGANDA');
INSERT INTO STU52382CLIENT (STU52382CLIENTID, FName, Address, City)
Values ('J', 'SEWA', '98Street','UK');
Select * from STU52382CLIENT;
Table Books
create table STU52382BOOK (
BookID varchar (25),
BName varchar (25),
BLastDate varchar (25) DEFAULT 'After14days',
BookVal varchar (30)
);
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('1', 'Geography', 'After14days','1$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('2', 'History', 'After14days','3$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('3', 'English', 'After14days','4$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
11
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
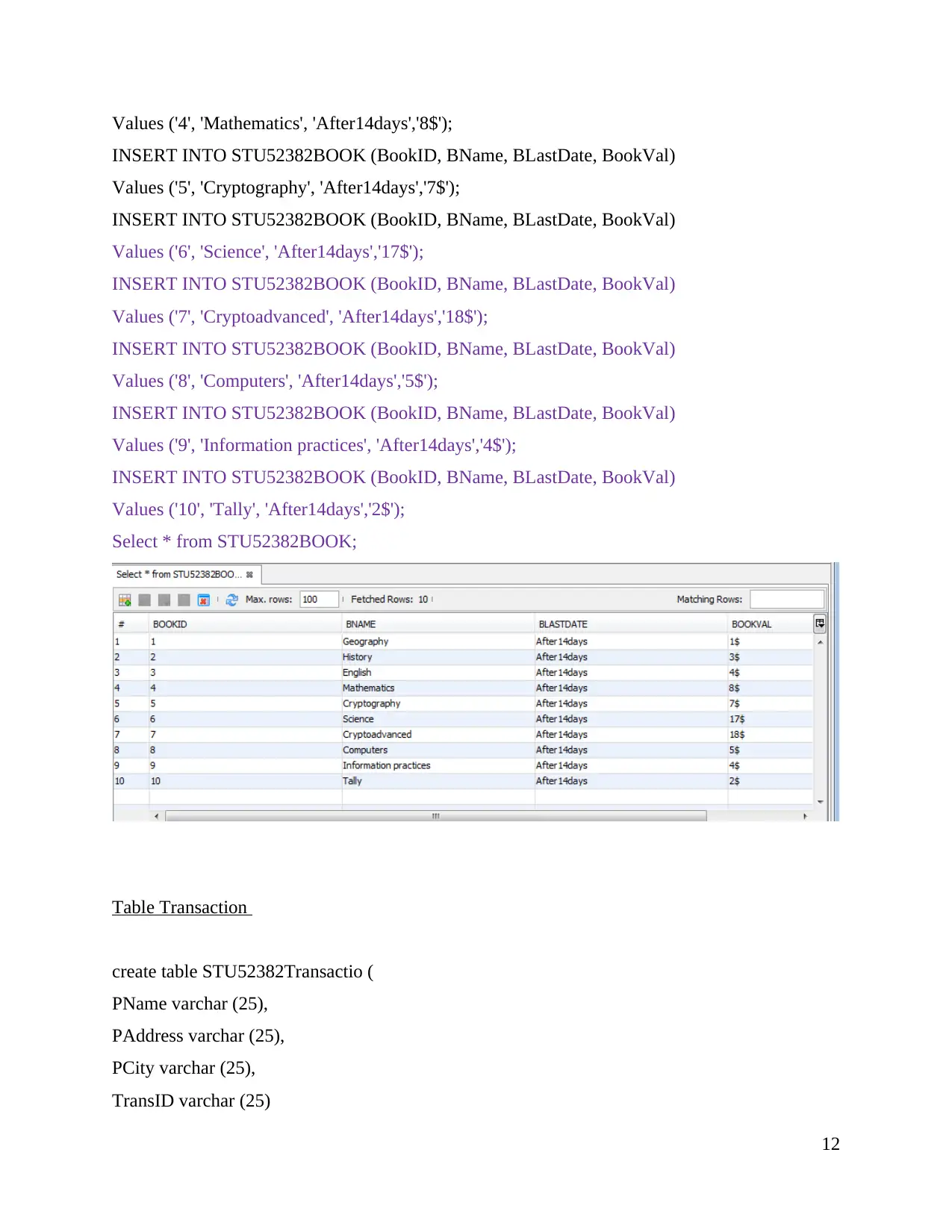
Values ('4', 'Mathematics', 'After14days','8$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('5', 'Cryptography', 'After14days','7$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('6', 'Science', 'After14days','17$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('7', 'Cryptoadvanced', 'After14days','18$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('8', 'Computers', 'After14days','5$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('9', 'Information practices', 'After14days','4$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('10', 'Tally', 'After14days','2$');
Select * from STU52382BOOK;
Table Transaction
create table STU52382Transactio (
PName varchar (25),
PAddress varchar (25),
PCity varchar (25),
TransID varchar (25)
12
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('5', 'Cryptography', 'After14days','7$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('6', 'Science', 'After14days','17$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('7', 'Cryptoadvanced', 'After14days','18$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('8', 'Computers', 'After14days','5$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('9', 'Information practices', 'After14days','4$');
INSERT INTO STU52382BOOK (BookID, BName, BLastDate, BookVal)
Values ('10', 'Tally', 'After14days','2$');
Select * from STU52382BOOK;
Table Transaction
create table STU52382Transactio (
PName varchar (25),
PAddress varchar (25),
PCity varchar (25),
TransID varchar (25)
12
);
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('1', 'Shewn', 'SUStreet','UGANDA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('2', 'Rec', '67Street','SEPIA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('3', 'Rew', '79Street','TESDA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('4', 'Xeg', 'MOStreet','WISDA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('5', 'Rac', 'LPStreet','JUMIA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('6', 'Riy', 'PStreet','UGANDA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('7', 'SHI', 'LStreet','UK');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('8', 'Tiya', 'QWStreet','SEPIA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('9', 'WHIV', 'SXStreet','JUMIA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('10', 'Rac', 'MOStreet','UGANDA');
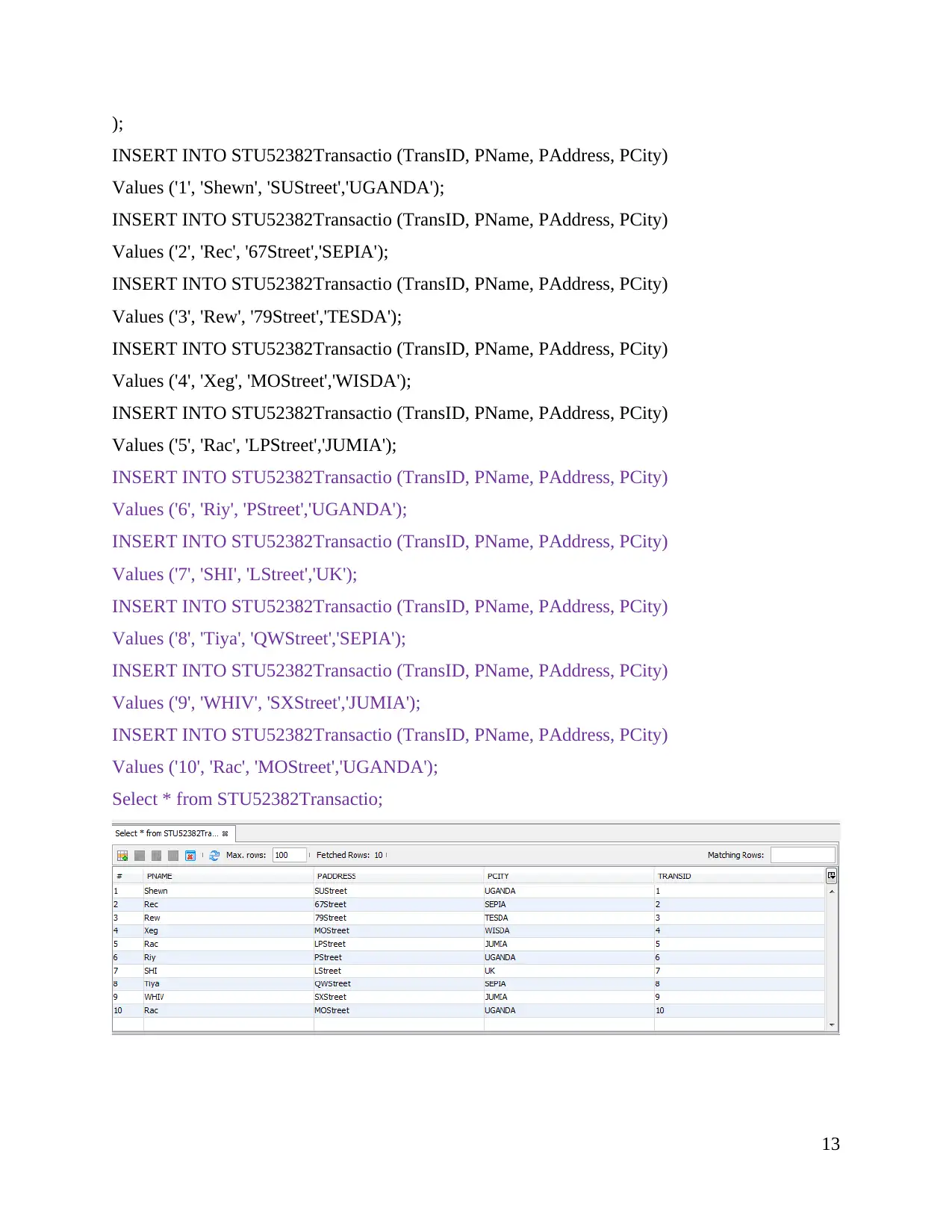
Select * from STU52382Transactio;
13
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('1', 'Shewn', 'SUStreet','UGANDA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('2', 'Rec', '67Street','SEPIA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('3', 'Rew', '79Street','TESDA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('4', 'Xeg', 'MOStreet','WISDA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('5', 'Rac', 'LPStreet','JUMIA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('6', 'Riy', 'PStreet','UGANDA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('7', 'SHI', 'LStreet','UK');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('8', 'Tiya', 'QWStreet','SEPIA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('9', 'WHIV', 'SXStreet','JUMIA');
INSERT INTO STU52382Transactio (TransID, PName, PAddress, PCity)
Values ('10', 'Rac', 'MOStreet','UGANDA');
Select * from STU52382Transactio;
13
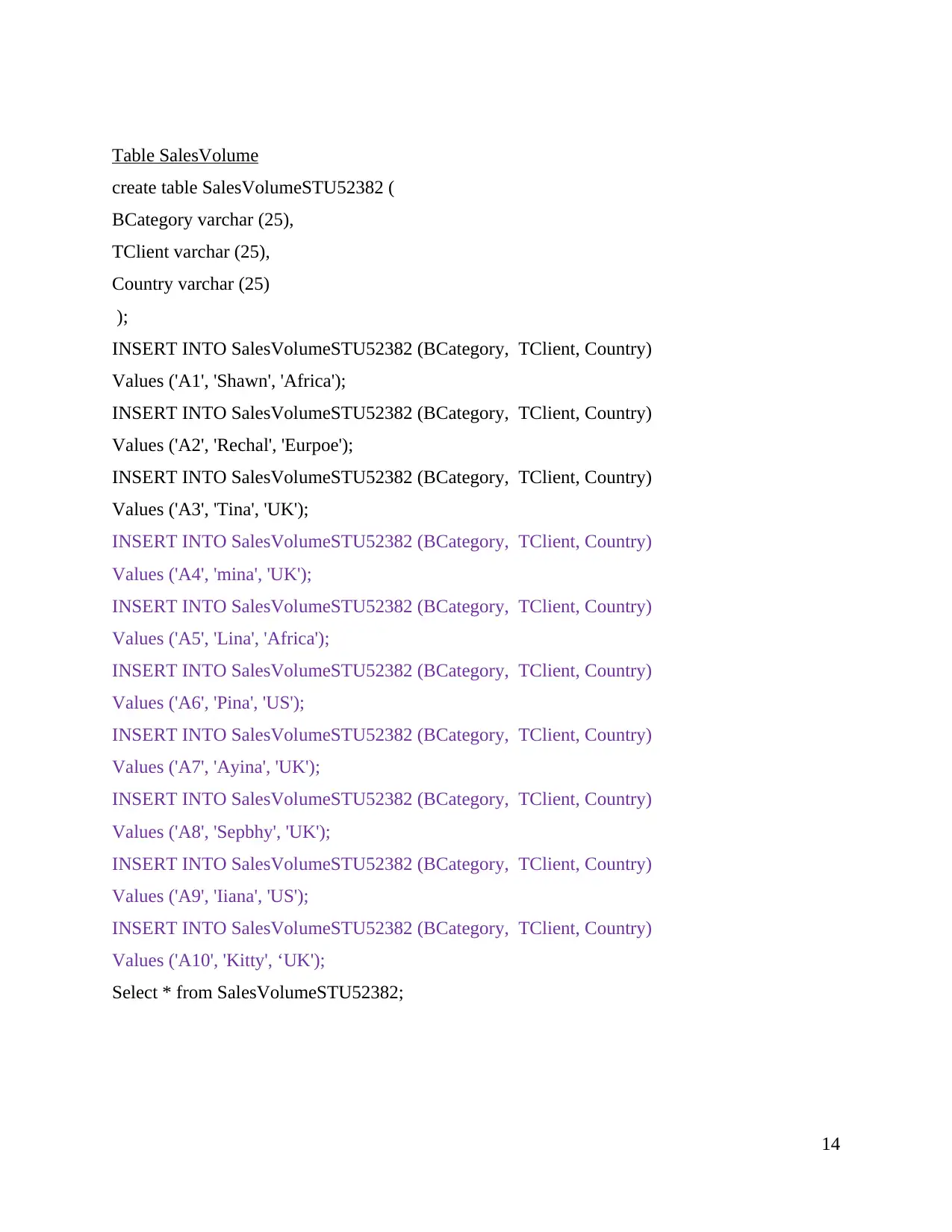
Table SalesVolume
create table SalesVolumeSTU52382 (
BCategory varchar (25),
TClient varchar (25),
Country varchar (25)
);
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A1', 'Shawn', 'Africa');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A2', 'Rechal', 'Eurpoe');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A3', 'Tina', 'UK');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A4', 'mina', 'UK');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A5', 'Lina', 'Africa');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A6', 'Pina', 'US');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A7', 'Ayina', 'UK');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A8', 'Sepbhy', 'UK');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A9', 'Iiana', 'US');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A10', 'Kitty', ‘UK');
Select * from SalesVolumeSTU52382;
14
create table SalesVolumeSTU52382 (
BCategory varchar (25),
TClient varchar (25),
Country varchar (25)
);
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A1', 'Shawn', 'Africa');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A2', 'Rechal', 'Eurpoe');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A3', 'Tina', 'UK');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A4', 'mina', 'UK');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A5', 'Lina', 'Africa');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A6', 'Pina', 'US');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A7', 'Ayina', 'UK');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A8', 'Sepbhy', 'UK');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A9', 'Iiana', 'US');
INSERT INTO SalesVolumeSTU52382 (BCategory, TClient, Country)
Values ('A10', 'Kitty', ‘UK');
Select * from SalesVolumeSTU52382;
14
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
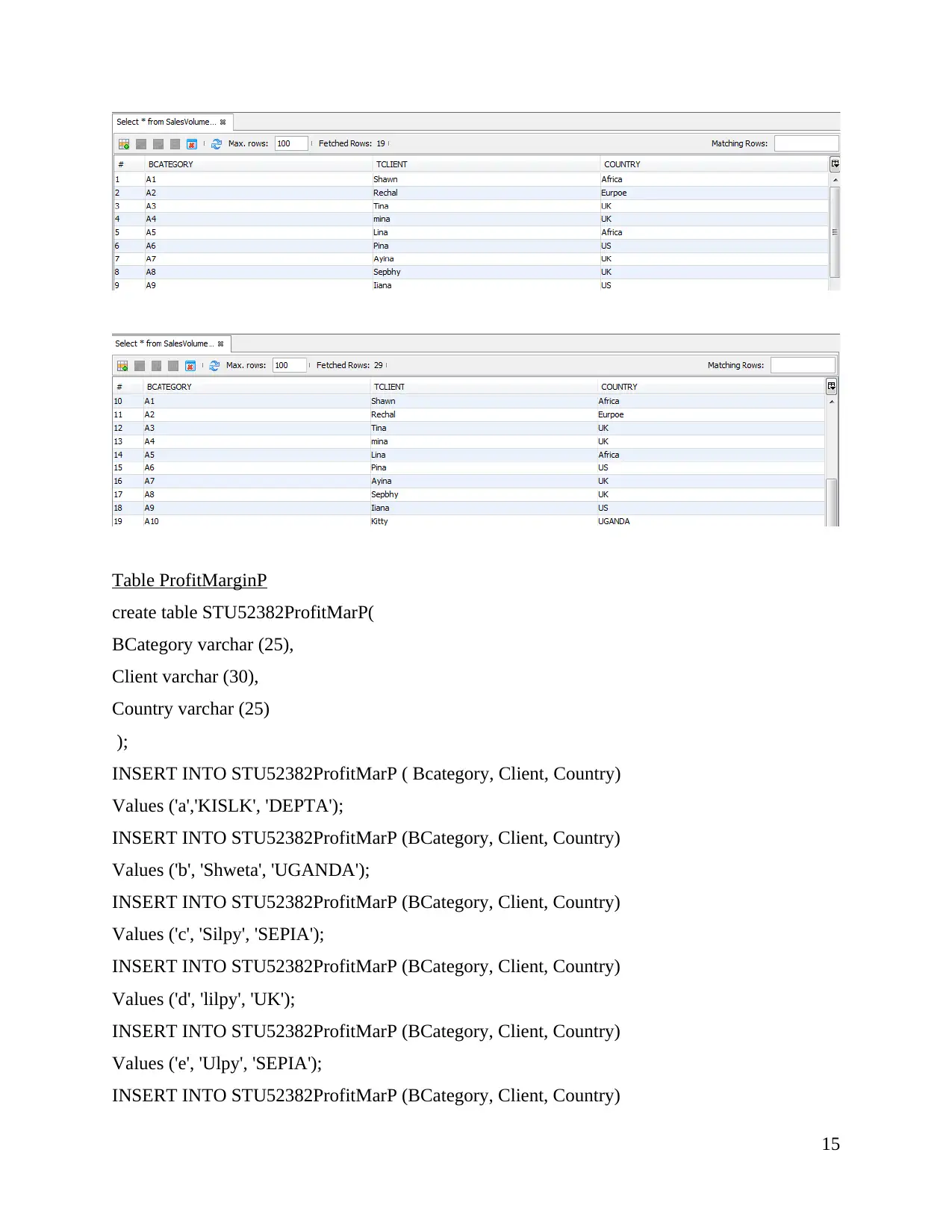
Table ProfitMarginP
create table STU52382ProfitMarP(
BCategory varchar (25),
Client varchar (30),
Country varchar (25)
);
INSERT INTO STU52382ProfitMarP ( Bcategory, Client, Country)
Values ('a','KISLK', 'DEPTA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('b', 'Shweta', 'UGANDA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('c', 'Silpy', 'SEPIA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('d', 'lilpy', 'UK');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('e', 'Ulpy', 'SEPIA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
15
create table STU52382ProfitMarP(
BCategory varchar (25),
Client varchar (30),
Country varchar (25)
);
INSERT INTO STU52382ProfitMarP ( Bcategory, Client, Country)
Values ('a','KISLK', 'DEPTA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('b', 'Shweta', 'UGANDA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('c', 'Silpy', 'SEPIA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('d', 'lilpy', 'UK');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('e', 'Ulpy', 'SEPIA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
15
Values ('f', 'Krishi', 'US');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('g', 'Riya', 'UGANDA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('h', 'Pinu', 'SEPIA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('i', 'Mina', 'UK');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('j', 'Kriti', 'US');
Select * from STU52382ProfitMarP ;
TASK 4
SQL queries and screenshots
Query
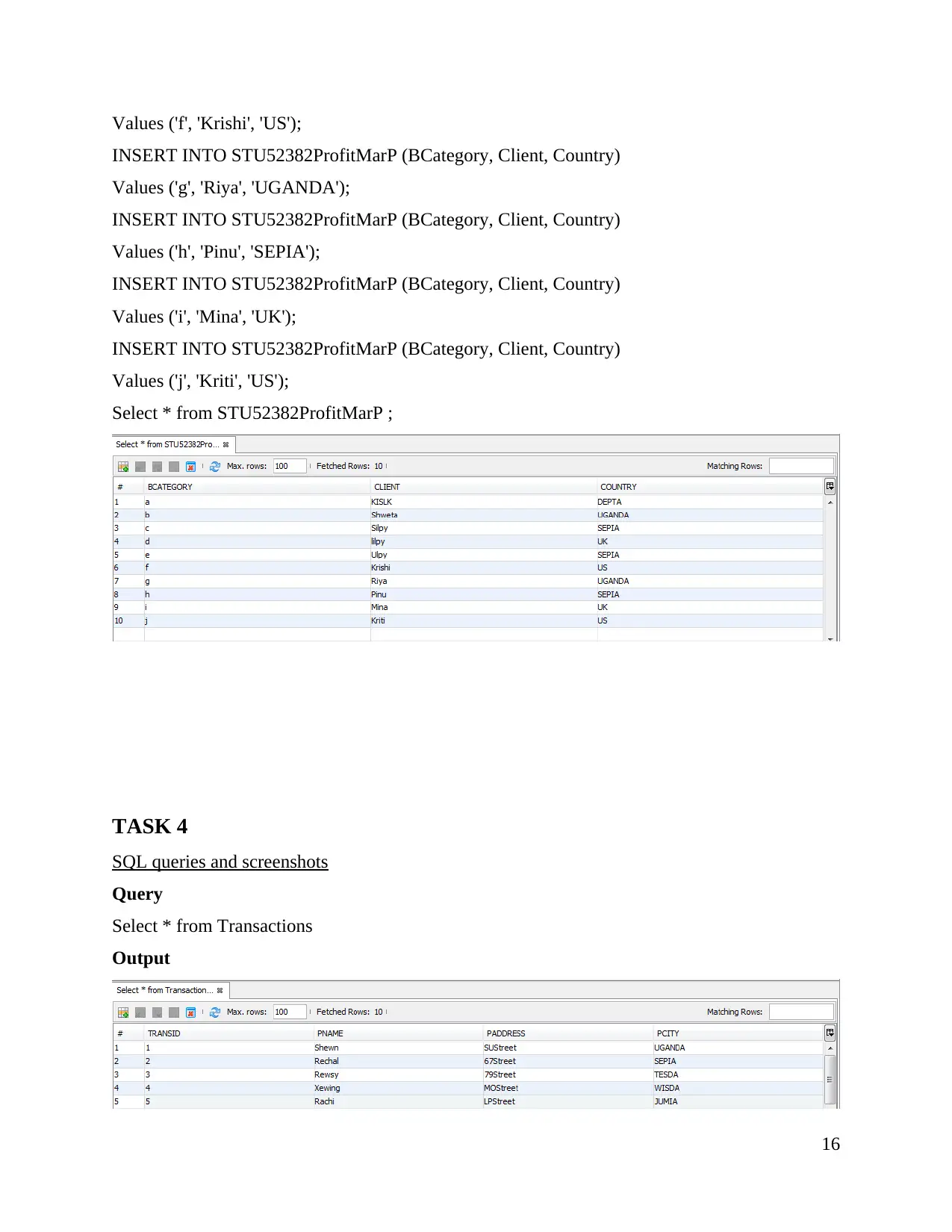
Select * from Transactions
Output
16
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('g', 'Riya', 'UGANDA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('h', 'Pinu', 'SEPIA');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('i', 'Mina', 'UK');
INSERT INTO STU52382ProfitMarP (BCategory, Client, Country)
Values ('j', 'Kriti', 'US');
Select * from STU52382ProfitMarP ;
TASK 4
SQL queries and screenshots
Query
Select * from Transactions
Output
16
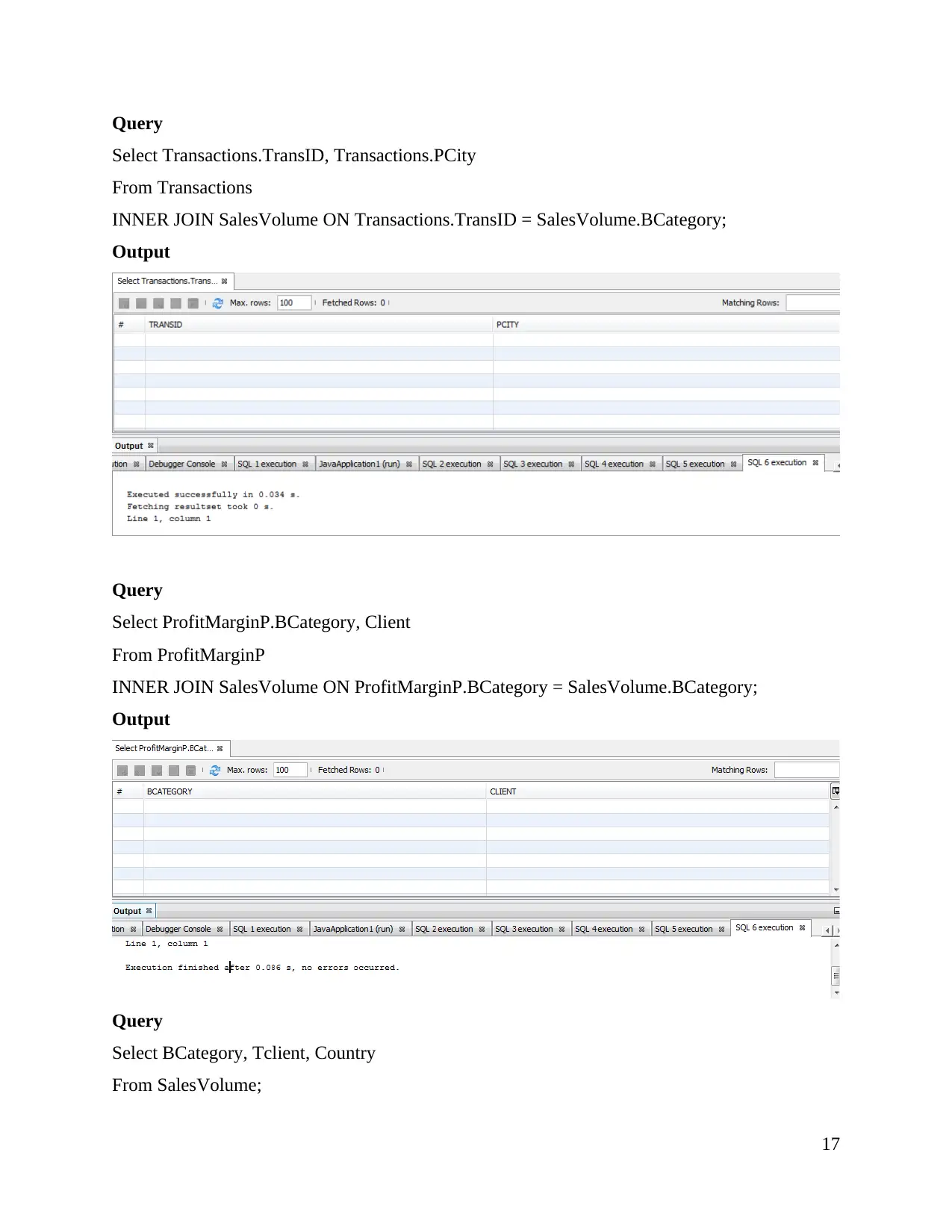
Query
Select Transactions.TransID, Transactions.PCity
From Transactions
INNER JOIN SalesVolume ON Transactions.TransID = SalesVolume.BCategory;
Output
Query
Select ProfitMarginP.BCategory, Client
From ProfitMarginP
INNER JOIN SalesVolume ON ProfitMarginP.BCategory = SalesVolume.BCategory;
Output
Query
Select BCategory, Tclient, Country
From SalesVolume;
17
Select Transactions.TransID, Transactions.PCity
From Transactions
INNER JOIN SalesVolume ON Transactions.TransID = SalesVolume.BCategory;
Output
Query
Select ProfitMarginP.BCategory, Client
From ProfitMarginP
INNER JOIN SalesVolume ON ProfitMarginP.BCategory = SalesVolume.BCategory;
Output
Query
Select BCategory, Tclient, Country
From SalesVolume;
17
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
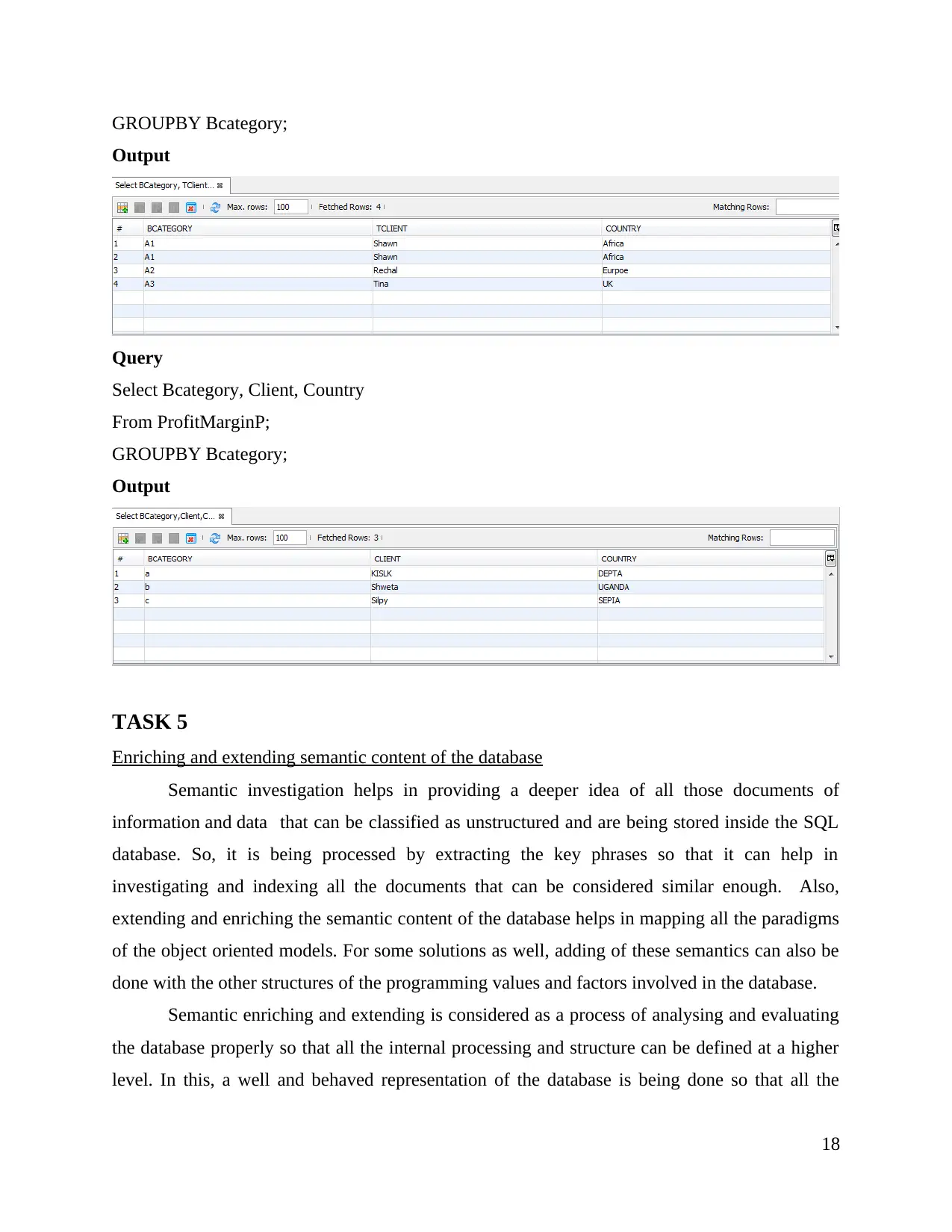
GROUPBY Bcategory;
Output
Query
Select Bcategory, Client, Country
From ProfitMarginP;
GROUPBY Bcategory;
Output
TASK 5
Enriching and extending semantic content of the database
Semantic investigation helps in providing a deeper idea of all those documents of
information and data that can be classified as unstructured and are being stored inside the SQL
database. So, it is being processed by extracting the key phrases so that it can help in
investigating and indexing all the documents that can be considered similar enough. Also,
extending and enriching the semantic content of the database helps in mapping all the paradigms
of the object oriented models. For some solutions as well, adding of these semantics can also be
done with the other structures of the programming values and factors involved in the database.
Semantic enriching and extending is considered as a process of analysing and evaluating
the database properly so that all the internal processing and structure can be defined at a higher
level. In this, a well and behaved representation of the database is being done so that all the
18
Output
Query
Select Bcategory, Client, Country
From ProfitMarginP;
GROUPBY Bcategory;
Output
TASK 5
Enriching and extending semantic content of the database
Semantic investigation helps in providing a deeper idea of all those documents of
information and data that can be classified as unstructured and are being stored inside the SQL
database. So, it is being processed by extracting the key phrases so that it can help in
investigating and indexing all the documents that can be considered similar enough. Also,
extending and enriching the semantic content of the database helps in mapping all the paradigms
of the object oriented models. For some solutions as well, adding of these semantics can also be
done with the other structures of the programming values and factors involved in the database.
Semantic enriching and extending is considered as a process of analysing and evaluating
the database properly so that all the internal processing and structure can be defined at a higher
level. In this, a well and behaved representation of the database is being done so that all the
18

hidden semantics can explicit. So, it is very important to enrich and extend the semantic content
of the database. It helps in taking the input as a relational database and also makes a duplicate
copy of the same so that it might be used in future if required.
How can they improve application performance
As semantic enrichment and extending associates a relational database that is relational
takes the factors such as input, makes duplicates of the metadata and thus, finally enriches with a
huge rate of semantics possible as well (Harrington, 2016). Thus, they can be classified as better
options for improving the overall performance of the applications. Also, semantic content can
help in making various improvements in the digital content of the specified operations. Thus, it
can prove beneficial enough in improving the complete performance of the applications on an
overall basis. It can help in optimizing as the processes inside it that are being used cannot be
considered as trivial. Also, another feature that should be ensured is that the pages involved
should be capable enough of satisfying the needs and requirements of the customers. It can be
very easily achieved by differentiating and investigating for different factors that should be
modified to an extent. It includes providing various options for different sizes and styles.
Interacting with customers can also be considered as an efficient option because it helps in an
efficient validation that can further act responsible enough in improving the overall performance
of the database. There are various factors associated with the enrichment and extending of the
semantic content and these involves taking the input first, copying the same including all its
factors and operations etc. The last step is the enrichment of the semantics which is being
implemented by considering all these factors in a way that it can seem beneficial enough for
storing and performing different functions in the database. Thus, it can be concluded that it can
actually help in making improvements in the application performance of the database that is
being used.
19
of the database. It helps in taking the input as a relational database and also makes a duplicate
copy of the same so that it might be used in future if required.
How can they improve application performance
As semantic enrichment and extending associates a relational database that is relational
takes the factors such as input, makes duplicates of the metadata and thus, finally enriches with a
huge rate of semantics possible as well (Harrington, 2016). Thus, they can be classified as better
options for improving the overall performance of the applications. Also, semantic content can
help in making various improvements in the digital content of the specified operations. Thus, it
can prove beneficial enough in improving the complete performance of the applications on an
overall basis. It can help in optimizing as the processes inside it that are being used cannot be
considered as trivial. Also, another feature that should be ensured is that the pages involved
should be capable enough of satisfying the needs and requirements of the customers. It can be
very easily achieved by differentiating and investigating for different factors that should be
modified to an extent. It includes providing various options for different sizes and styles.
Interacting with customers can also be considered as an efficient option because it helps in an
efficient validation that can further act responsible enough in improving the overall performance
of the database. There are various factors associated with the enrichment and extending of the
semantic content and these involves taking the input first, copying the same including all its
factors and operations etc. The last step is the enrichment of the semantics which is being
implemented by considering all these factors in a way that it can seem beneficial enough for
storing and performing different functions in the database. Thus, it can be concluded that it can
actually help in making improvements in the application performance of the database that is
being used.
19

REFERENCES
Books and Journals
Coronel, C. and Morris, S., 2016. Database systems: design, implementation, & management.
Cengage Learning.
Rajakumari, S. B. and Nalini, C., 2014. An efficient data mining dataset preparation using
aggregation in relational database. Indian Journal of Science and Technology, 7(S5),
pp.44-46.
Harrington, J. L., 2016. Relational database design and implementation. Morgan Kaufmann.
Hutchison, D., Kepner, J. and Fuchs, A., 2015, September. Graphulo implementation of server-
side sparse matrix multipPART 1
20
Books and Journals
Coronel, C. and Morris, S., 2016. Database systems: design, implementation, & management.
Cengage Learning.
Rajakumari, S. B. and Nalini, C., 2014. An efficient data mining dataset preparation using
aggregation in relational database. Indian Journal of Science and Technology, 7(S5),
pp.44-46.
Harrington, J. L., 2016. Relational database design and implementation. Morgan Kaufmann.
Hutchison, D., Kepner, J. and Fuchs, A., 2015, September. Graphulo implementation of server-
side sparse matrix multipPART 1
20
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

21
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





